Network System Project: Risk Register, Cost Baseline, and Funding
VerifiedAdded on 2020/04/07
|7
|900
|55
Report
AI Summary
This report presents a comprehensive analysis of a network system project, focusing on three key areas: the risk register, cost baseline, and funding requirements. The risk register identifies potential threats and opportunities, detailing their likelihood, impact, and mitigation strategies. The cost baseline outlines the resources needed for each project activity, broken down by phases and tasks, with associated costs. Finally, the funding requirements section specifies the necessary funding amounts across different project phases, including initiation, design, development, execution, and closure, along with management reserves. The report includes tables summarizing the risk register, cost baseline, and funding requirements, and provides references to support the analysis. This report helps understand the critical aspects of project management, including risk mitigation, cost control, and financial planning.

Running head: Planning paper 1
NETWORK SYSTEM RISK REGISTER, COST BASELINE AND FUNDING
REQUIREMENTS
Submitted by
Affiliation
Supervisor’s name
Date of submission
NETWORK SYSTEM RISK REGISTER, COST BASELINE AND FUNDING
REQUIREMENTS
Submitted by
Affiliation
Supervisor’s name
Date of submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Planning paper 2
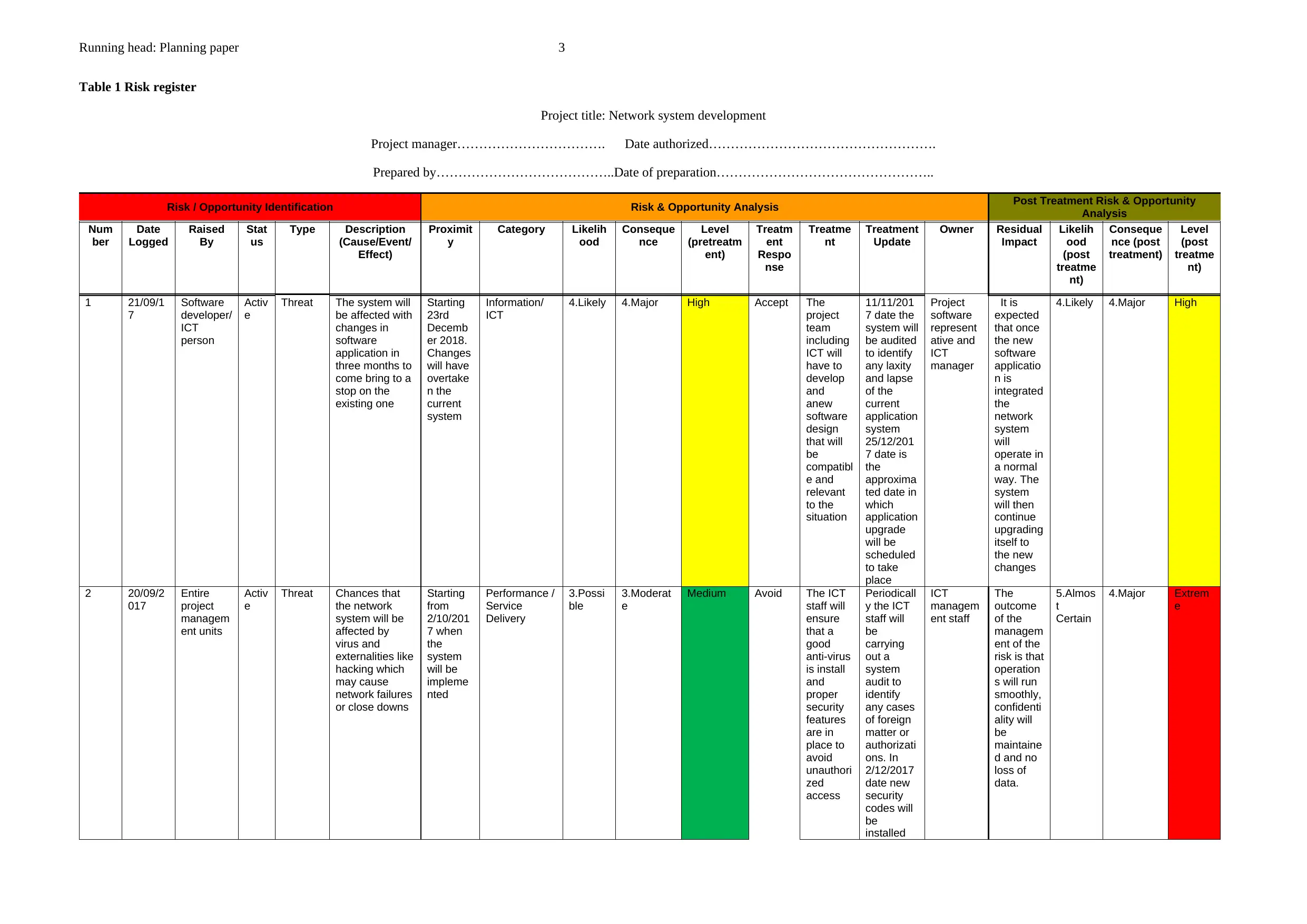
1.0. Risk register
The risk register represents a record of how risks will be managed or mitigated in a project
(Andrew, 2014). The risk register for the network system development is generated in order to
mitigate any risks originating from the project implementation. Table 1 shows a summary of risk
register for the network system project.
1.0. Risk register
The risk register represents a record of how risks will be managed or mitigated in a project
(Andrew, 2014). The risk register for the network system development is generated in order to
mitigate any risks originating from the project implementation. Table 1 shows a summary of risk
register for the network system project.
Running head: Planning paper 3
Table 1 Risk register
Project title: Network system development
Project manager……………………………. Date authorized…………………………………………….
Prepared by…………………………………..Date of preparation…………………………………………..
Risk / Opportunity Identification Risk & Opportunity Analysis Post Treatment Risk & Opportunity
Analysis
Num
ber
Date
Logged
Raised
By
Stat
us
Type Description
(Cause/Event/
Effect)
Proximit
y
Category Likelih
ood
Conseque
nce
Level
(pretreatm
ent)
Treatm
ent
Respo
nse
Treatme
nt
Treatment
Update
Owner Residual
Impact
Likelih
ood
(post
treatme
nt)
Conseque
nce (post
treatment)
Level
(post
treatme
nt)
1 21/09/1
7
Software
developer/
ICT
person
Activ
e
Threat The system will
be affected with
changes in
software
application in
three months to
come bring to a
stop on the
existing one
Starting
23rd
Decemb
er 2018.
Changes
will have
overtake
n the
current
system
Information/
ICT
4.Likely 4.Major High Accept The
project
team
including
ICT will
have to
develop
and
anew
software
design
that will
be
compatibl
e and
relevant
to the
situation
11/11/201
7 date the
system will
be audited
to identify
any laxity
and lapse
of the
current
application
system
25/12/201
7 date is
the
approxima
ted date in
which
application
upgrade
will be
scheduled
to take
place
Project
software
represent
ative and
ICT
manager
It is
expected
that once
the new
software
applicatio
n is
integrated
the
network
system
will
operate in
a normal
way. The
system
will then
continue
upgrading
itself to
the new
changes
4.Likely 4.Major High
2 20/09/2
017
Entire
project
managem
ent units
Activ
e
Threat Chances that
the network
system will be
affected by
virus and
externalities like
hacking which
may cause
network failures
or close downs
Starting
from
2/10/201
7 when
the
system
will be
impleme
nted
Performance /
Service
Delivery
3.Possi
ble
3.Moderat
e
Medium Avoid The ICT
staff will
ensure
that a
good
anti-virus
is install
and
proper
security
features
are in
place to
avoid
unauthori
zed
access
Periodicall
y the ICT
staff will
be
carrying
out a
system
audit to
identify
any cases
of foreign
matter or
authorizati
ons. In
2/12/2017
date new
security
codes will
be
installed
ICT
managem
ent staff
The
outcome
of the
managem
ent of the
risk is that
operation
s will run
smoothly,
confidenti
ality will
be
maintaine
d and no
loss of
data.
5.Almos
t
Certain
4.Major Extrem
e
Table 1 Risk register
Project title: Network system development
Project manager……………………………. Date authorized…………………………………………….
Prepared by…………………………………..Date of preparation…………………………………………..
Risk / Opportunity Identification Risk & Opportunity Analysis Post Treatment Risk & Opportunity
Analysis
Num
ber
Date
Logged
Raised
By
Stat
us
Type Description
(Cause/Event/
Effect)
Proximit
y
Category Likelih
ood
Conseque
nce
Level
(pretreatm
ent)
Treatm
ent
Respo
nse
Treatme
nt
Treatment
Update
Owner Residual
Impact
Likelih
ood
(post
treatme
nt)
Conseque
nce (post
treatment)
Level
(post
treatme
nt)
1 21/09/1
7
Software
developer/
ICT
person
Activ
e
Threat The system will
be affected with
changes in
software
application in
three months to
come bring to a
stop on the
existing one
Starting
23rd
Decemb
er 2018.
Changes
will have
overtake
n the
current
system
Information/
ICT
4.Likely 4.Major High Accept The
project
team
including
ICT will
have to
develop
and
anew
software
design
that will
be
compatibl
e and
relevant
to the
situation
11/11/201
7 date the
system will
be audited
to identify
any laxity
and lapse
of the
current
application
system
25/12/201
7 date is
the
approxima
ted date in
which
application
upgrade
will be
scheduled
to take
place
Project
software
represent
ative and
ICT
manager
It is
expected
that once
the new
software
applicatio
n is
integrated
the
network
system
will
operate in
a normal
way. The
system
will then
continue
upgrading
itself to
the new
changes
4.Likely 4.Major High
2 20/09/2
017
Entire
project
managem
ent units
Activ
e
Threat Chances that
the network
system will be
affected by
virus and
externalities like
hacking which
may cause
network failures
or close downs
Starting
from
2/10/201
7 when
the
system
will be
impleme
nted
Performance /
Service
Delivery
3.Possi
ble
3.Moderat
e
Medium Avoid The ICT
staff will
ensure
that a
good
anti-virus
is install
and
proper
security
features
are in
place to
avoid
unauthori
zed
access
Periodicall
y the ICT
staff will
be
carrying
out a
system
audit to
identify
any cases
of foreign
matter or
authorizati
ons. In
2/12/2017
date new
security
codes will
be
installed
ICT
managem
ent staff
The
outcome
of the
managem
ent of the
risk is that
operation
s will run
smoothly,
confidenti
ality will
be
maintaine
d and no
loss of
data.
5.Almos
t
Certain
4.Major Extrem
e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: Planning paper 4
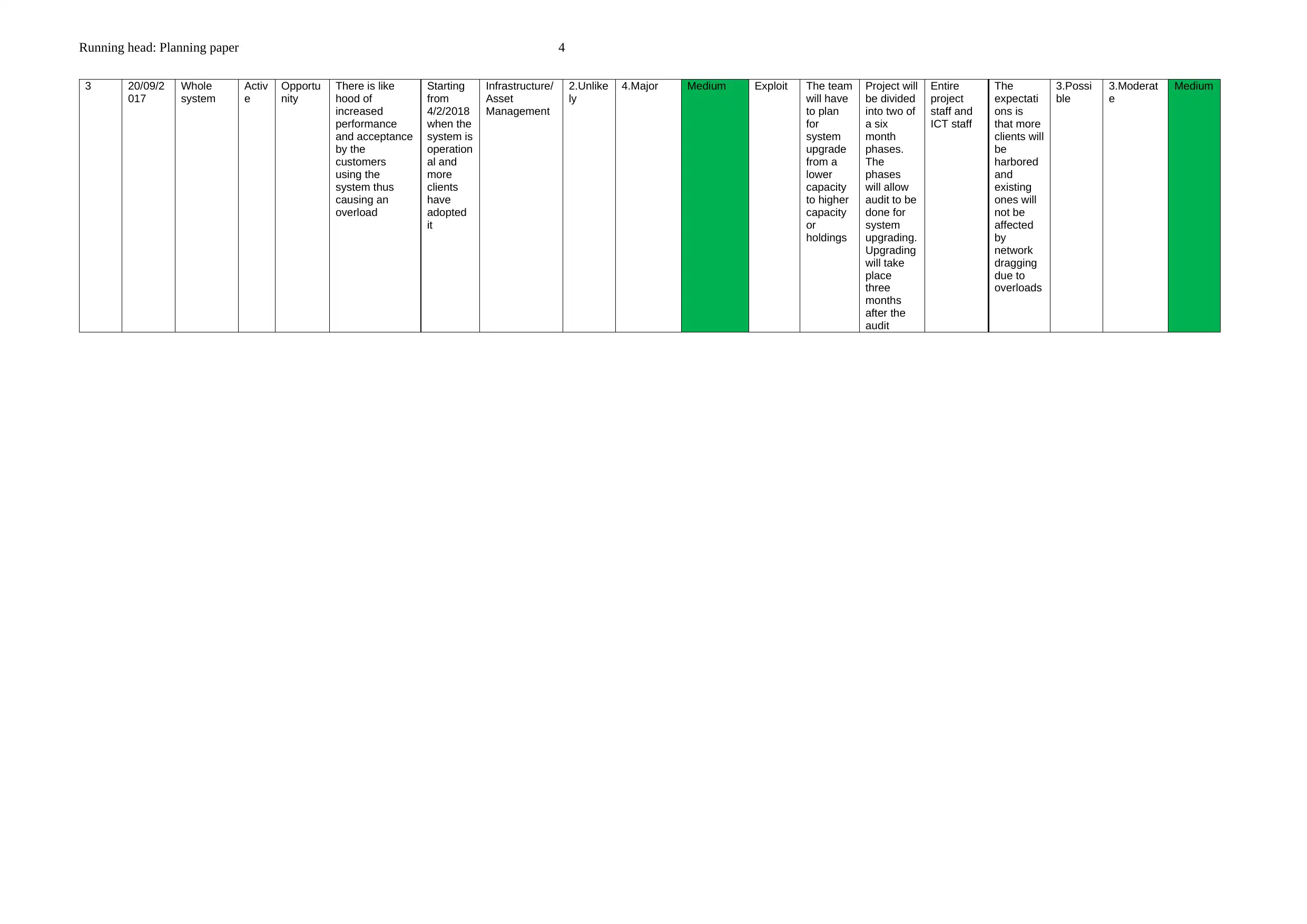
3 20/09/2
017
Whole
system
Activ
e
Opportu
nity
There is like
hood of
increased
performance
and acceptance
by the
customers
using the
system thus
causing an
overload
Starting
from
4/2/2018
when the
system is
operation
al and
more
clients
have
adopted
it
Infrastructure/
Asset
Management
2.Unlike
ly
4.Major Medium Exploit The team
will have
to plan
for
system
upgrade
from a
lower
capacity
to higher
capacity
or
holdings
Project will
be divided
into two of
a six
month
phases.
The
phases
will allow
audit to be
done for
system
upgrading.
Upgrading
will take
place
three
months
after the
audit
Entire
project
staff and
ICT staff
The
expectati
ons is
that more
clients will
be
harbored
and
existing
ones will
not be
affected
by
network
dragging
due to
overloads
3.Possi
ble
3.Moderat
e
Medium
3 20/09/2
017
Whole
system
Activ
e
Opportu
nity
There is like
hood of
increased
performance
and acceptance
by the
customers
using the
system thus
causing an
overload
Starting
from
4/2/2018
when the
system is
operation
al and
more
clients
have
adopted
it
Infrastructure/
Asset
Management
2.Unlike
ly
4.Major Medium Exploit The team
will have
to plan
for
system
upgrade
from a
lower
capacity
to higher
capacity
or
holdings
Project will
be divided
into two of
a six
month
phases.
The
phases
will allow
audit to be
done for
system
upgrading.
Upgrading
will take
place
three
months
after the
audit
Entire
project
staff and
ICT staff
The
expectati
ons is
that more
clients will
be
harbored
and
existing
ones will
not be
affected
by
network
dragging
due to
overloads
3.Possi
ble
3.Moderat
e
Medium
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: Planning paper 5
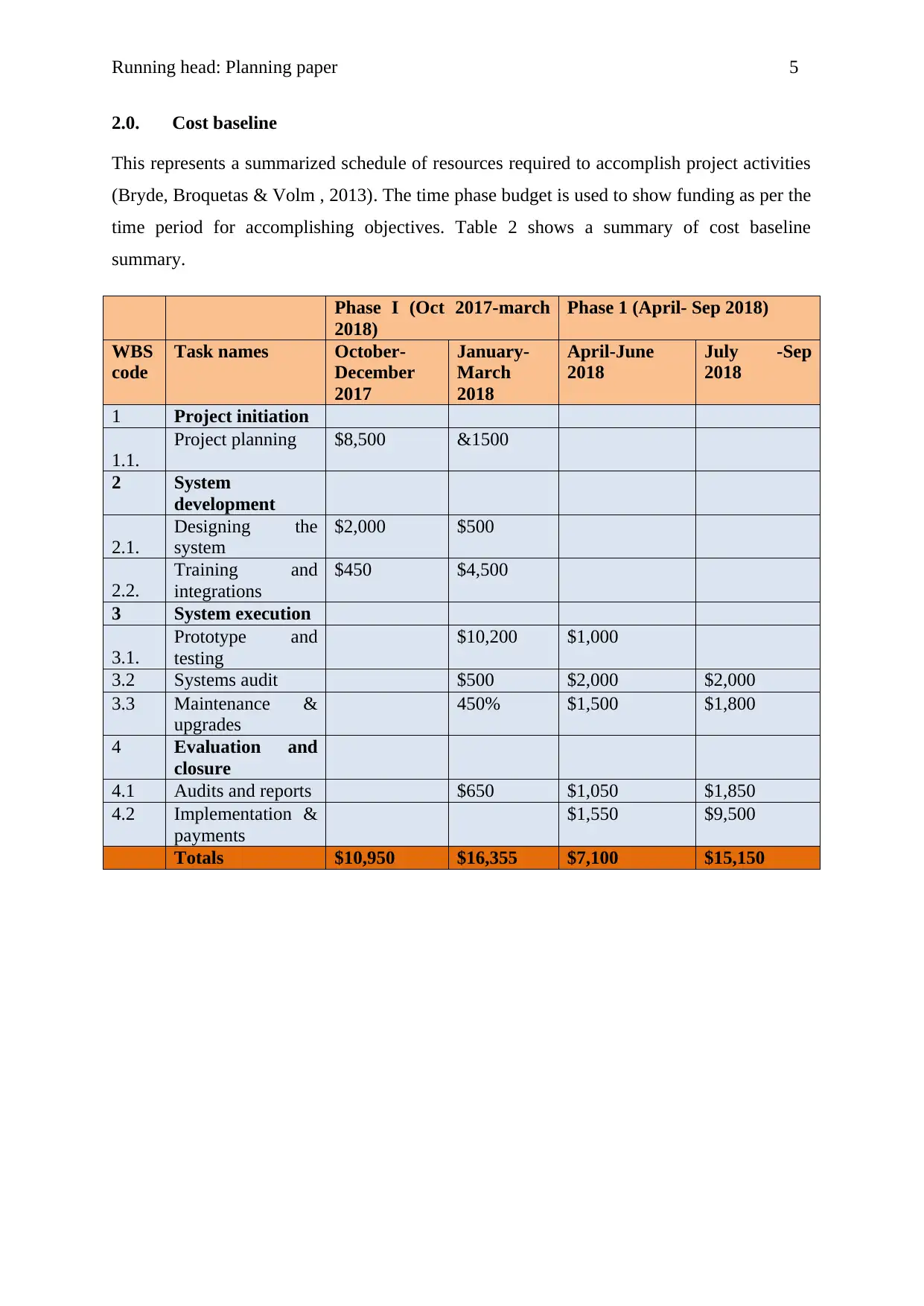
2.0. Cost baseline
This represents a summarized schedule of resources required to accomplish project activities
(Bryde, Broquetas & Volm , 2013). The time phase budget is used to show funding as per the
time period for accomplishing objectives. Table 2 shows a summary of cost baseline
summary.
Phase I (Oct 2017-march
2018)
Phase 1 (April- Sep 2018)
WBS
code
Task names October-
December
2017
January-
March
2018
April-June
2018
July -Sep
2018
1 Project initiation
1.1.
Project planning $8,500 &1500
2 System
development
2.1.
Designing the
system
$2,000 $500
2.2.
Training and
integrations
$450 $4,500
3 System execution
3.1.
Prototype and
testing
$10,200 $1,000
3.2 Systems audit $500 $2,000 $2,000
3.3 Maintenance &
upgrades
450% $1,500 $1,800
4 Evaluation and
closure
4.1 Audits and reports $650 $1,050 $1,850
4.2 Implementation &
payments
$1,550 $9,500
Totals $10,950 $16,355 $7,100 $15,150
2.0. Cost baseline
This represents a summarized schedule of resources required to accomplish project activities
(Bryde, Broquetas & Volm , 2013). The time phase budget is used to show funding as per the
time period for accomplishing objectives. Table 2 shows a summary of cost baseline
summary.
Phase I (Oct 2017-march
2018)
Phase 1 (April- Sep 2018)
WBS
code
Task names October-
December
2017
January-
March
2018
April-June
2018
July -Sep
2018
1 Project initiation
1.1.
Project planning $8,500 &1500
2 System
development
2.1.
Designing the
system
$2,000 $500
2.2.
Training and
integrations
$450 $4,500
3 System execution
3.1.
Prototype and
testing
$10,200 $1,000
3.2 Systems audit $500 $2,000 $2,000
3.3 Maintenance &
upgrades
450% $1,500 $1,800
4 Evaluation and
closure
4.1 Audits and reports $650 $1,050 $1,850
4.2 Implementation &
payments
$1,550 $9,500
Totals $10,950 $16,355 $7,100 $15,150
Running head: Planning paper 6
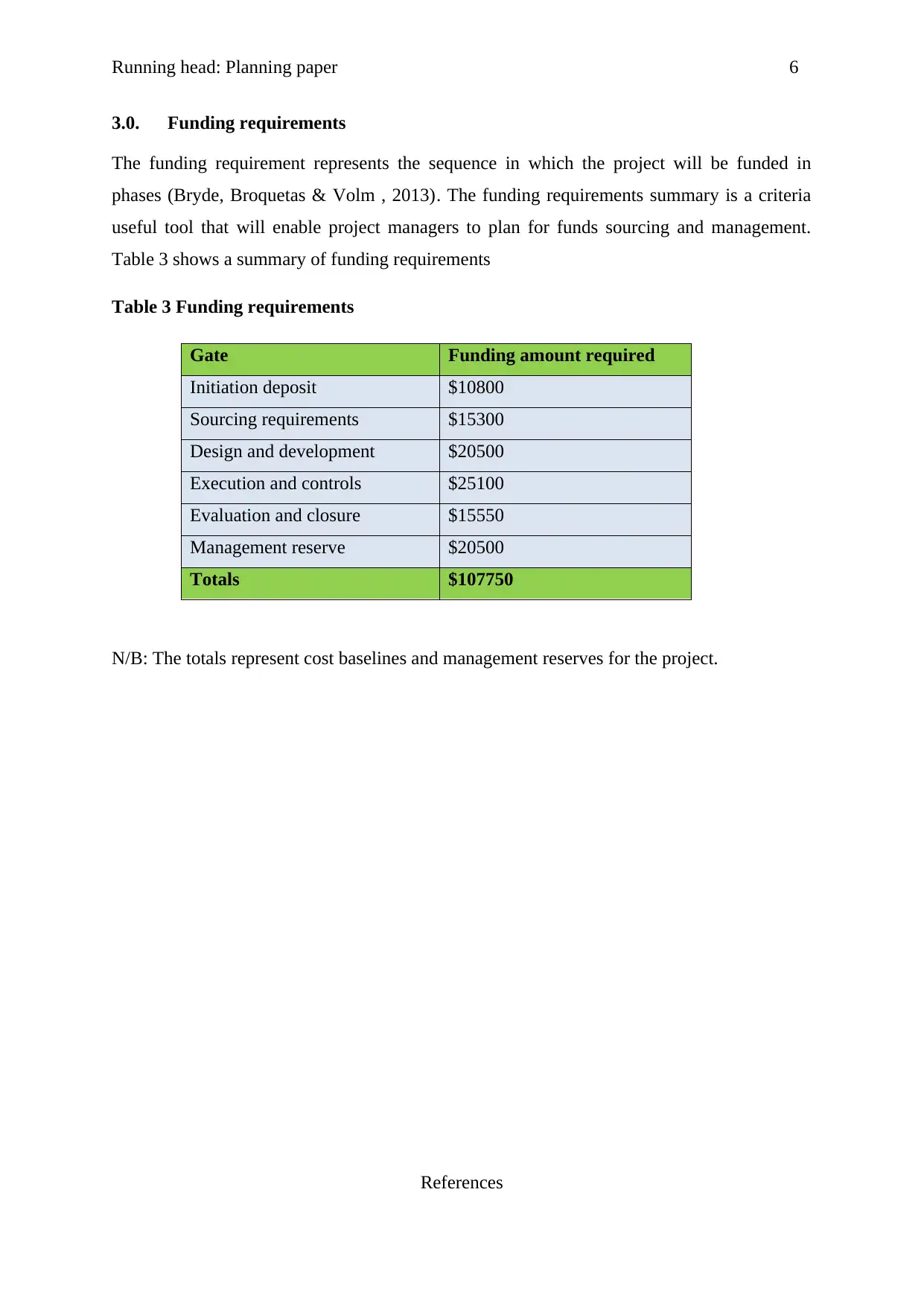
3.0. Funding requirements
The funding requirement represents the sequence in which the project will be funded in
phases (Bryde, Broquetas & Volm , 2013). The funding requirements summary is a criteria
useful tool that will enable project managers to plan for funds sourcing and management.
Table 3 shows a summary of funding requirements
Table 3 Funding requirements
Gate Funding amount required
Initiation deposit $10800
Sourcing requirements $15300
Design and development $20500
Execution and controls $25100
Evaluation and closure $15550
Management reserve $20500
Totals $107750
N/B: The totals represent cost baselines and management reserves for the project.
References
3.0. Funding requirements
The funding requirement represents the sequence in which the project will be funded in
phases (Bryde, Broquetas & Volm , 2013). The funding requirements summary is a criteria
useful tool that will enable project managers to plan for funds sourcing and management.
Table 3 shows a summary of funding requirements
Table 3 Funding requirements
Gate Funding amount required
Initiation deposit $10800
Sourcing requirements $15300
Design and development $20500
Execution and controls $25100
Evaluation and closure $15550
Management reserve $20500
Totals $107750
N/B: The totals represent cost baselines and management reserves for the project.
References
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Planning paper 7
Andrew, F. (2014). Effects of risk management in projects. New York: Mc Graw Hill.
Bryde, Broquetas & Volm . (2013). The project benefits of building information modelling.
International Journal of project management, 31(7), 971-980.
Andrew, F. (2014). Effects of risk management in projects. New York: Mc Graw Hill.
Bryde, Broquetas & Volm . (2013). The project benefits of building information modelling.
International Journal of project management, 31(7), 971-980.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





