Assignment | RISK REPORT FOR ABC FITNESS GYM.
VerifiedAdded on 2022/09/30
|10
|2445
|22
Assignment
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

RISK REPORT FOR ABC FITNESS GYM
Risk report for ABC Fitness Gym
a. Your Full Name: Please fill
b. Your Student ID: Please fill
c. Subject Code: Please fill
d. Assessment Item Number and Name: Please fill
Page 0 of 10
Risk report for ABC Fitness Gym
a. Your Full Name: Please fill
b. Your Student ID: Please fill
c. Subject Code: Please fill
d. Assessment Item Number and Name: Please fill
Page 0 of 10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RISK REPORT FOR ABC FITNESS GYM
Executive Summary
Started in the year 1997, ABC fitness gym has two different categories, such as the
employers and the employees. The subscription rates of the members keep on changing every
moment, there are gym tours which are being conducted for new members of this gym. There
are IT systems which is there in this gym which aims to provide services like membership
renewal, ensuring safety and health requirements while recruiting new members, maintaining
a competitive advantage due to the presence of the other gyms. The organizational data are
the prime assets of this gym, which is very much vulnerable to numerous categories of data
security threats such as the botnet attacks and phishing emails. These security threats have to
be secured in the first place using firewalls and IDS so that the organizational growth is
maintained in this gym.
Page 1 of 10
Executive Summary
Started in the year 1997, ABC fitness gym has two different categories, such as the
employers and the employees. The subscription rates of the members keep on changing every
moment, there are gym tours which are being conducted for new members of this gym. There
are IT systems which is there in this gym which aims to provide services like membership
renewal, ensuring safety and health requirements while recruiting new members, maintaining
a competitive advantage due to the presence of the other gyms. The organizational data are
the prime assets of this gym, which is very much vulnerable to numerous categories of data
security threats such as the botnet attacks and phishing emails. These security threats have to
be secured in the first place using firewalls and IDS so that the organizational growth is
maintained in this gym.
Page 1 of 10

RISK REPORT FOR ABC FITNESS GYM
Table of Contents
1. Introduction............................................................................................................................3
2. Risk assessment......................................................................................................................3
2.1 Identification of assets, threats and impact on IT Control Framework............................3
2.2 Existing industry risk recommendations for the project..................................................3
2.3 Mitigate the risks and impact on the organisation...........................................................4
2.4 Tabular description of the risks in ABC Corporation......................................................4
5. Protection mechanisms...........................................................................................................5
5.1 Safe guards.......................................................................................................................5
5.2 Tools and technologies.....................................................................................................6
5.3 Culture..............................................................................................................................6
5.4 People...............................................................................................................................6
6. Gap analysis..........................................................................................................................6
7. Recommendations..................................................................................................................7
8 Six principles of IS..................................................................................................................7
9. Conclusion..............................................................................................................................7
10. References............................................................................................................................9
Page 2 of 10
Table of Contents
1. Introduction............................................................................................................................3
2. Risk assessment......................................................................................................................3
2.1 Identification of assets, threats and impact on IT Control Framework............................3
2.2 Existing industry risk recommendations for the project..................................................3
2.3 Mitigate the risks and impact on the organisation...........................................................4
2.4 Tabular description of the risks in ABC Corporation......................................................4
5. Protection mechanisms...........................................................................................................5
5.1 Safe guards.......................................................................................................................5
5.2 Tools and technologies.....................................................................................................6
5.3 Culture..............................................................................................................................6
5.4 People...............................................................................................................................6
6. Gap analysis..........................................................................................................................6
7. Recommendations..................................................................................................................7
8 Six principles of IS..................................................................................................................7
9. Conclusion..............................................................................................................................7
10. References............................................................................................................................9
Page 2 of 10

RISK REPORT FOR ABC FITNESS GYM
1. Introduction
Risk report is very much important for any commercial business in order to identify
the mitigation strategy for each of the identified risks. There are numerous categories of data
security risks which exist in the fitness gyms, such as phishing emails and botnet attacks
(Yan, 2018). The prime determination of this report is to produce a comprehensive risk
report, this report shall also discuss a few protection mechanisms which can be very much
useful to address those risks.
2. Risk assessment
2.1 Identification of assets, threats and impact on IT Control Framework
The organizational data in terms of the data of the employees and the customer data
are one of the most significant assets of this gym (Jabez & Muthukumar, 2015). The other
asset of this gym are the gym equipment such as the weight machines, and cardiovascular
machines.
The prime threat of this gym is the data security threats regarding the organizational
data. There are other categories of threats associated with this fitness centre in terms of the
injuries due to tripping over the wires, risk of electrocution, liquidity risks, the presence of
longer curtains can be the other significant risk associated with this gym (Zhang, 2018). The
prime vulnerability of this gym is maintaining the customer data and the employee data on
the server. Data security threats like ransomware and phishing mails can have a direct impact
on the control framework used by this gym (Teixeira et al., 2015). The internal control
framework which is there in this gym can be negatively affected due to these above
mentioned threats.
2.2 Existing industry risk recommendations for the project
The different categories of industry threats which might have an impact on the
organizational assets of ABC fitness gym are disaster-related issues, injuries from the fitness
centre, breaching of the consumer data, liability coming from the trainers and the gym
members.
2.3 Mitigate the risks and impact on the organisation
The organizational target of this fitness gym can be achieved only if the identified
risks are mitigated in an organized manner so that these risks cannot crop up in the near
future. The business growth of this gym is very much depended in the mitigation procedure
Page 3 of 10
1. Introduction
Risk report is very much important for any commercial business in order to identify
the mitigation strategy for each of the identified risks. There are numerous categories of data
security risks which exist in the fitness gyms, such as phishing emails and botnet attacks
(Yan, 2018). The prime determination of this report is to produce a comprehensive risk
report, this report shall also discuss a few protection mechanisms which can be very much
useful to address those risks.
2. Risk assessment
2.1 Identification of assets, threats and impact on IT Control Framework
The organizational data in terms of the data of the employees and the customer data
are one of the most significant assets of this gym (Jabez & Muthukumar, 2015). The other
asset of this gym are the gym equipment such as the weight machines, and cardiovascular
machines.
The prime threat of this gym is the data security threats regarding the organizational
data. There are other categories of threats associated with this fitness centre in terms of the
injuries due to tripping over the wires, risk of electrocution, liquidity risks, the presence of
longer curtains can be the other significant risk associated with this gym (Zhang, 2018). The
prime vulnerability of this gym is maintaining the customer data and the employee data on
the server. Data security threats like ransomware and phishing mails can have a direct impact
on the control framework used by this gym (Teixeira et al., 2015). The internal control
framework which is there in this gym can be negatively affected due to these above
mentioned threats.
2.2 Existing industry risk recommendations for the project
The different categories of industry threats which might have an impact on the
organizational assets of ABC fitness gym are disaster-related issues, injuries from the fitness
centre, breaching of the consumer data, liability coming from the trainers and the gym
members.
2.3 Mitigate the risks and impact on the organisation
The organizational target of this fitness gym can be achieved only if the identified
risks are mitigated in an organized manner so that these risks cannot crop up in the near
future. The business growth of this gym is very much depended in the mitigation procedure
Page 3 of 10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
RISK REPORT FOR ABC FITNESS GYM
of each of the risks (Kang et al., 2015). Maintaining the reputation of the business is directly
associated with the risk mitigation procedure of this business.
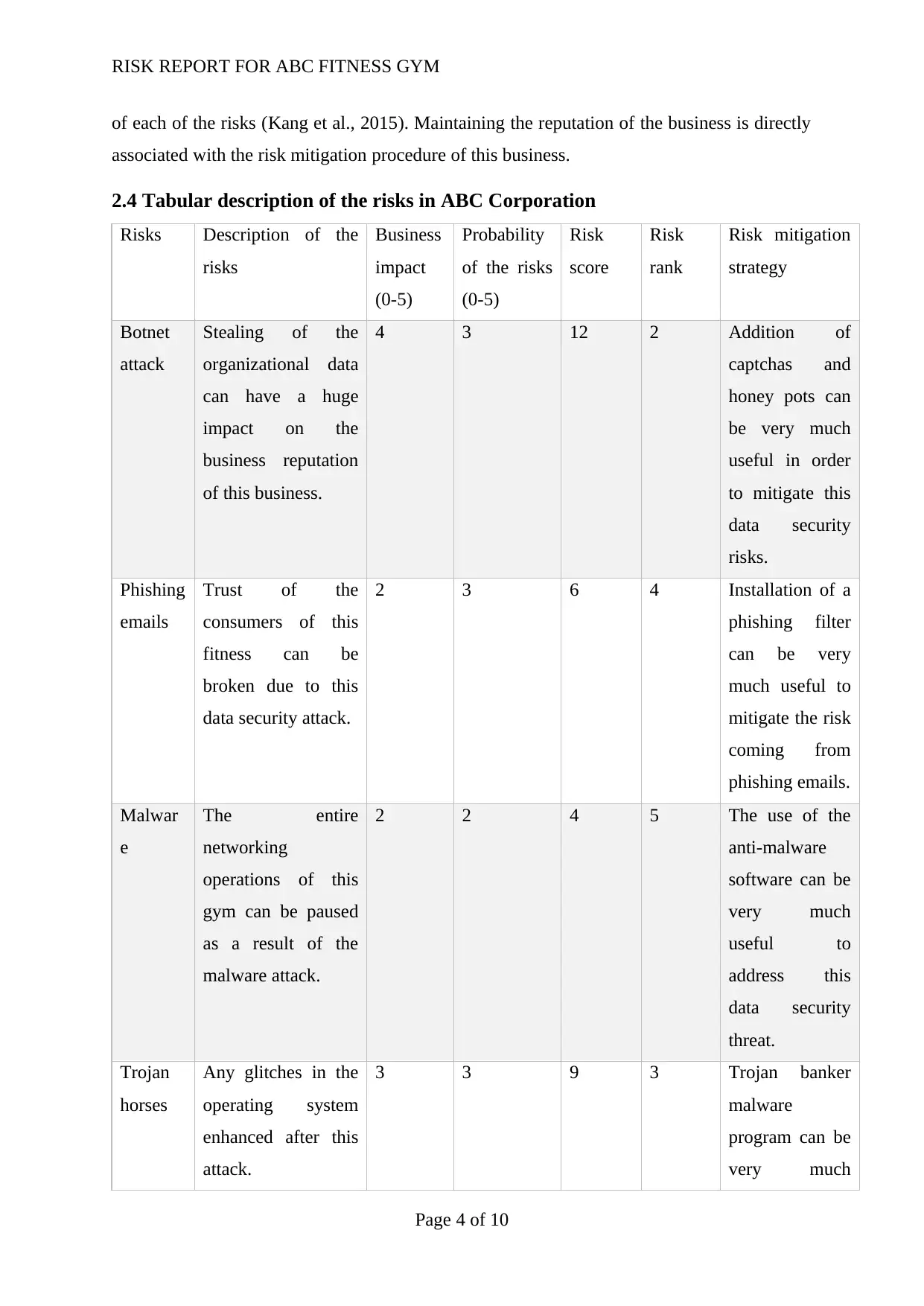
2.4 Tabular description of the risks in ABC Corporation
Risks Description of the
risks
Business
impact
(0-5)
Probability
of the risks
(0-5)
Risk
score
Risk
rank
Risk mitigation
strategy
Botnet
attack
Stealing of the
organizational data
can have a huge
impact on the
business reputation
of this business.
4 3 12 2 Addition of
captchas and
honey pots can
be very much
useful in order
to mitigate this
data security
risks.
Phishing
emails
Trust of the
consumers of this
fitness can be
broken due to this
data security attack.
2 3 6 4 Installation of a
phishing filter
can be very
much useful to
mitigate the risk
coming from
phishing emails.
Malwar
e
The entire
networking
operations of this
gym can be paused
as a result of the
malware attack.
2 2 4 5 The use of the
anti-malware
software can be
very much
useful to
address this
data security
threat.
Trojan
horses
Any glitches in the
operating system
enhanced after this
attack.
3 3 9 3 Trojan banker
malware
program can be
very much
Page 4 of 10
of each of the risks (Kang et al., 2015). Maintaining the reputation of the business is directly
associated with the risk mitigation procedure of this business.
2.4 Tabular description of the risks in ABC Corporation
Risks Description of the
risks
Business
impact
(0-5)
Probability
of the risks
(0-5)
Risk
score
Risk
rank
Risk mitigation
strategy
Botnet
attack
Stealing of the
organizational data
can have a huge
impact on the
business reputation
of this business.
4 3 12 2 Addition of
captchas and
honey pots can
be very much
useful in order
to mitigate this
data security
risks.
Phishing
emails
Trust of the
consumers of this
fitness can be
broken due to this
data security attack.
2 3 6 4 Installation of a
phishing filter
can be very
much useful to
mitigate the risk
coming from
phishing emails.
Malwar
e
The entire
networking
operations of this
gym can be paused
as a result of the
malware attack.
2 2 4 5 The use of the
anti-malware
software can be
very much
useful to
address this
data security
threat.
Trojan
horses
Any glitches in the
operating system
enhanced after this
attack.
3 3 9 3 Trojan banker
malware
program can be
very much
Page 4 of 10
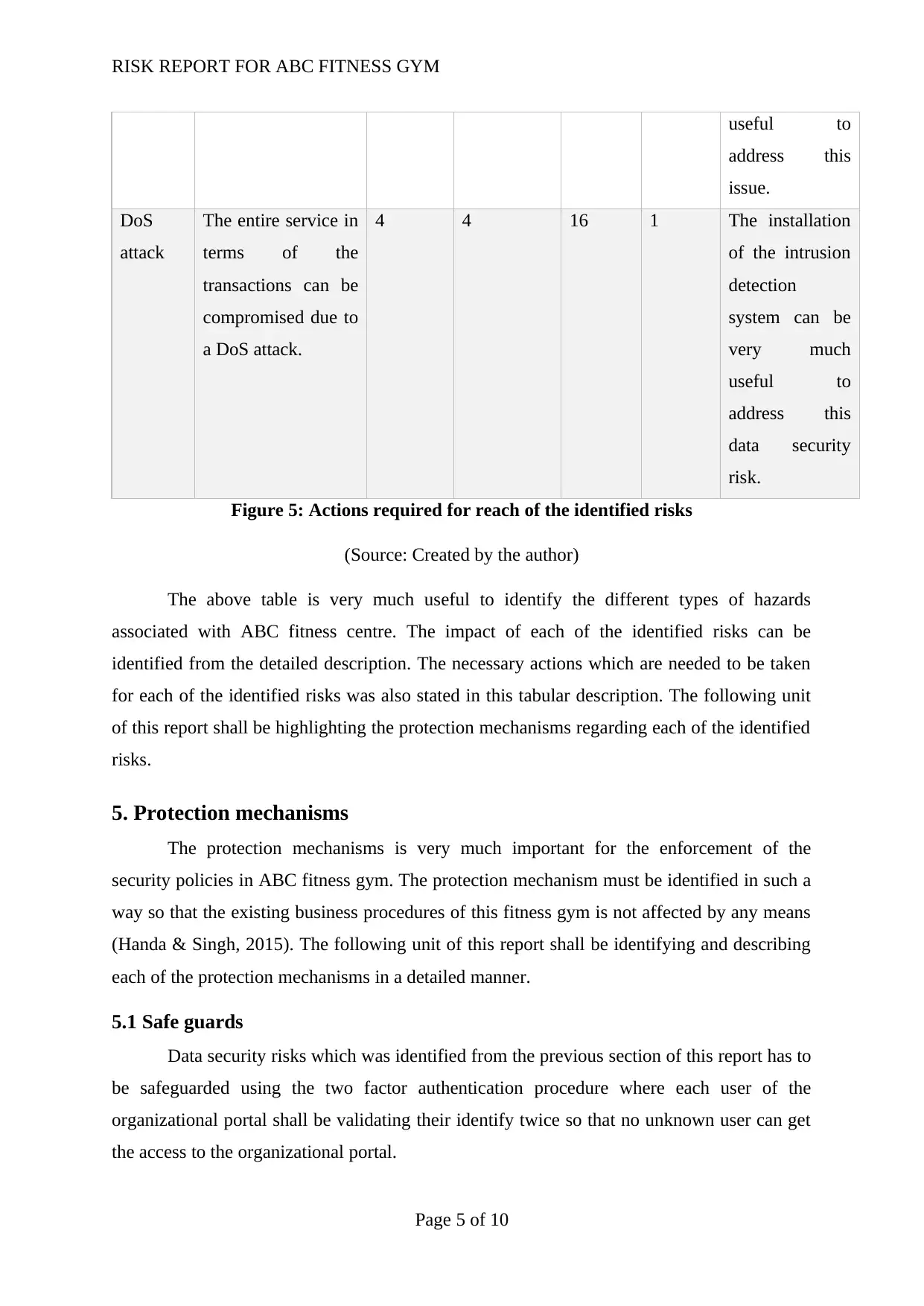
RISK REPORT FOR ABC FITNESS GYM
useful to
address this
issue.
DoS
attack
The entire service in
terms of the
transactions can be
compromised due to
a DoS attack.
4 4 16 1 The installation
of the intrusion
detection
system can be
very much
useful to
address this
data security
risk.
Figure 5: Actions required for reach of the identified risks
(Source: Created by the author)
The above table is very much useful to identify the different types of hazards
associated with ABC fitness centre. The impact of each of the identified risks can be
identified from the detailed description. The necessary actions which are needed to be taken
for each of the identified risks was also stated in this tabular description. The following unit
of this report shall be highlighting the protection mechanisms regarding each of the identified
risks.
5. Protection mechanisms
The protection mechanisms is very much important for the enforcement of the
security policies in ABC fitness gym. The protection mechanism must be identified in such a
way so that the existing business procedures of this fitness gym is not affected by any means
(Handa & Singh, 2015). The following unit of this report shall be identifying and describing
each of the protection mechanisms in a detailed manner.
5.1 Safe guards
Data security risks which was identified from the previous section of this report has to
be safeguarded using the two factor authentication procedure where each user of the
organizational portal shall be validating their identify twice so that no unknown user can get
the access to the organizational portal.
Page 5 of 10
useful to
address this
issue.
DoS
attack
The entire service in
terms of the
transactions can be
compromised due to
a DoS attack.
4 4 16 1 The installation
of the intrusion
detection
system can be
very much
useful to
address this
data security
risk.
Figure 5: Actions required for reach of the identified risks
(Source: Created by the author)
The above table is very much useful to identify the different types of hazards
associated with ABC fitness centre. The impact of each of the identified risks can be
identified from the detailed description. The necessary actions which are needed to be taken
for each of the identified risks was also stated in this tabular description. The following unit
of this report shall be highlighting the protection mechanisms regarding each of the identified
risks.
5. Protection mechanisms
The protection mechanisms is very much important for the enforcement of the
security policies in ABC fitness gym. The protection mechanism must be identified in such a
way so that the existing business procedures of this fitness gym is not affected by any means
(Handa & Singh, 2015). The following unit of this report shall be identifying and describing
each of the protection mechanisms in a detailed manner.
5.1 Safe guards
Data security risks which was identified from the previous section of this report has to
be safeguarded using the two factor authentication procedure where each user of the
organizational portal shall be validating their identify twice so that no unknown user can get
the access to the organizational portal.
Page 5 of 10

RISK REPORT FOR ABC FITNESS GYM
5.2 Tools and technologies
The deployment of the PKI services, penetration testing procedures, installation of the
intrusion detection system and firewalls can be very much useful in order to deal with the
threats coming from each of those data security threats (Chang & Ramachandran, 2015).
Encryption technology can play a huge role in order to protect the organizational data from
the data security threats, this technology can be very much useful to restrict the entry of any
outsiders in the organizational network of this fitness gym (Farnaaz & Jabbar, 2016). Tools
such as the Nmap and Wireshark can be very much useful to deal with the data security
issues in ABC fitness gym.
5.3 Culture
Maintaining a corporate culture can be very much useful to mitigate each of the risks
identified in the previous unit of this report (Duque & bin Omar, 2015). Conduction of the
auditing process on a daily basis can be very much useful to address each of the risks in the
technology environment of ABC Corporation (Almorsy, Grundy & Müller, 2016). The
induction training and orientation training can be very much useful for each of the
stakeholders of this business to understand the threats and its impact on this business as well.
5.4 People
Risk assessments must be carried out by each of the stakeholders associated with the
business and it can be very much useful to identify the mitigation procedure of each of the
risks (Bertino & Ferrari, 2018). Formation of an online community can be very much useful
in order to deal with each the data security risks, as the stakeholders can interact among
themselves in order to sort any confusions or queries about the data security issues.
6. Gap analysis
There is a gap which is not being discussed in this report which is the threat coming
from inside the gym. It can be said that the former employees of the gym, contractors, service
providers or any of the business associate of this gym can be a huge source of concern
regarding the maintenance of the data security in ABC fitness gym. Negligence and the lack
of knowledge about the data security threats are the other areas which is needed to be focused
in order to preserve the confidentiality of the organizational data.
7. Recommendations
The list of recommendations for ABC fitness gym are listed as followings:
Page 6 of 10
5.2 Tools and technologies
The deployment of the PKI services, penetration testing procedures, installation of the
intrusion detection system and firewalls can be very much useful in order to deal with the
threats coming from each of those data security threats (Chang & Ramachandran, 2015).
Encryption technology can play a huge role in order to protect the organizational data from
the data security threats, this technology can be very much useful to restrict the entry of any
outsiders in the organizational network of this fitness gym (Farnaaz & Jabbar, 2016). Tools
such as the Nmap and Wireshark can be very much useful to deal with the data security
issues in ABC fitness gym.
5.3 Culture
Maintaining a corporate culture can be very much useful to mitigate each of the risks
identified in the previous unit of this report (Duque & bin Omar, 2015). Conduction of the
auditing process on a daily basis can be very much useful to address each of the risks in the
technology environment of ABC Corporation (Almorsy, Grundy & Müller, 2016). The
induction training and orientation training can be very much useful for each of the
stakeholders of this business to understand the threats and its impact on this business as well.
5.4 People
Risk assessments must be carried out by each of the stakeholders associated with the
business and it can be very much useful to identify the mitigation procedure of each of the
risks (Bertino & Ferrari, 2018). Formation of an online community can be very much useful
in order to deal with each the data security risks, as the stakeholders can interact among
themselves in order to sort any confusions or queries about the data security issues.
6. Gap analysis
There is a gap which is not being discussed in this report which is the threat coming
from inside the gym. It can be said that the former employees of the gym, contractors, service
providers or any of the business associate of this gym can be a huge source of concern
regarding the maintenance of the data security in ABC fitness gym. Negligence and the lack
of knowledge about the data security threats are the other areas which is needed to be focused
in order to preserve the confidentiality of the organizational data.
7. Recommendations
The list of recommendations for ABC fitness gym are listed as followings:
Page 6 of 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK REPORT FOR ABC FITNESS GYM
An advanced intrusion detection system must be installed in the networking switches
of this gym.
Extensive training sessions can be very much useful to educate the stakeholders of
this business regarding the impacts of the data security threats.
8 Six principles of IS
The six principles of Information Security which has to be considered in the
technological environment of ABC Corporation are as followings:
Confidentiality: Confidentiality organizational data has to be maintained in the first
place (Snapp et al., 2017).
Privacy: Privacy of the business transactions initiated by the consumers of this
business has to be maintained.
Quality: The gym tour must be conducted in such a way so that none of the details of
the gym is leaked and the QoS of the gym is maintained.
Availability: The subscription rates of this gym must not be exposed to anyone who
is not associated with this gym (Bertino, 2016).
Trustworthiness: The equipment used in the gym must be regularly checked and
Integrity: The integrity of each of the business data has to be maintained so that
transparency is maintained in the entire business procedure.
9. Conclusion
Organizational data are the most significant assets of ABC fitness gym. There are
different categories of data security threats which can have a direct impact on the growth and
reputation of ABC fitness gym such as the botnet attack, phishing mails, DoS attack and
Trojan horses. The additional of captchas and phishing filters can be very much useful to
address the risks coming from botnet attacks and phishing emails. Anti-malware software and
Trojan banker can be very much significant in order to mitigate the threat coming from
malware and Trojan horses. The intrusion detection system can play a huge in order to
address the threat coming from DoS attacks.
Page 7 of 10
An advanced intrusion detection system must be installed in the networking switches
of this gym.
Extensive training sessions can be very much useful to educate the stakeholders of
this business regarding the impacts of the data security threats.
8 Six principles of IS
The six principles of Information Security which has to be considered in the
technological environment of ABC Corporation are as followings:
Confidentiality: Confidentiality organizational data has to be maintained in the first
place (Snapp et al., 2017).
Privacy: Privacy of the business transactions initiated by the consumers of this
business has to be maintained.
Quality: The gym tour must be conducted in such a way so that none of the details of
the gym is leaked and the QoS of the gym is maintained.
Availability: The subscription rates of this gym must not be exposed to anyone who
is not associated with this gym (Bertino, 2016).
Trustworthiness: The equipment used in the gym must be regularly checked and
Integrity: The integrity of each of the business data has to be maintained so that
transparency is maintained in the entire business procedure.
9. Conclusion
Organizational data are the most significant assets of ABC fitness gym. There are
different categories of data security threats which can have a direct impact on the growth and
reputation of ABC fitness gym such as the botnet attack, phishing mails, DoS attack and
Trojan horses. The additional of captchas and phishing filters can be very much useful to
address the risks coming from botnet attacks and phishing emails. Anti-malware software and
Trojan banker can be very much significant in order to mitigate the threat coming from
malware and Trojan horses. The intrusion detection system can play a huge in order to
address the threat coming from DoS attacks.
Page 7 of 10

RISK REPORT FOR ABC FITNESS GYM
10. References
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Bertino, E., & Ferrari, E. (2018). Big data security and privacy. In A Comprehensive Guide
Through the Italian Database Research Over the Last 25 Years (pp. 425-439).
Springer, Cham.
Chang, V., & Ramachandran, M. (2015). Towards achieving data security with the cloud
computing adoption framework. IEEE Transactions on Services Computing, 9(1),
138-151.
Handa, K., & Singh, U. (2015). Data security in cloud computing using encryption and
steganography. International Journal of Computer Science and Mobile Computing,
4(5), 786-791.
Kang, R., Dabbish, L., Fruchter, N., & Kiesler, S. (2015). “My Data Just Goes Everywhere:”
User Mental Models of the Internet and Implications for Privacy and Security. In
Eleventh Symposium On Usable Privacy and Security ({SOUPS} 2015) (pp. 39-52).
Teixeira, A., Shames, I., Sandberg, H., & Johansson, K. H. (2015). A secure control
framework for resource-limited adversaries. Automatica, 51, 135-148.
Yan, G. (2018). Research on the Operation and Development of Sports Fitness Industry
Based on Internet Plus Era.
Jabez, J., & Muthukumar, B. (2015). Intrusion detection system (IDS): anomaly detection
using outlier detection approach. Procedia Computer Science, 48, 338-346.
Farnaaz, N., & Jabbar, M. A. (2016). Random forest modeling for network intrusion
detection system. Procedia Computer Science, 89, 213-217.
Duque, S., & bin Omar, M. N. (2015). Using data mining algorithms for developing a model
for intrusion detection system (IDS). Procedia Computer Science, 61, 46-51.
Snapp, S. R., Brentano, J., Dias, G., Goan, T. L., Heberlein, L. T., Ho, C. L., & Levitt, K. N.
(2017). DIDS (distributed intrusion detection system)-motivation, architecture, and an
early prototype.
Page 8 of 10
10. References
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Bertino, E., & Ferrari, E. (2018). Big data security and privacy. In A Comprehensive Guide
Through the Italian Database Research Over the Last 25 Years (pp. 425-439).
Springer, Cham.
Chang, V., & Ramachandran, M. (2015). Towards achieving data security with the cloud
computing adoption framework. IEEE Transactions on Services Computing, 9(1),
138-151.
Handa, K., & Singh, U. (2015). Data security in cloud computing using encryption and
steganography. International Journal of Computer Science and Mobile Computing,
4(5), 786-791.
Kang, R., Dabbish, L., Fruchter, N., & Kiesler, S. (2015). “My Data Just Goes Everywhere:”
User Mental Models of the Internet and Implications for Privacy and Security. In
Eleventh Symposium On Usable Privacy and Security ({SOUPS} 2015) (pp. 39-52).
Teixeira, A., Shames, I., Sandberg, H., & Johansson, K. H. (2015). A secure control
framework for resource-limited adversaries. Automatica, 51, 135-148.
Yan, G. (2018). Research on the Operation and Development of Sports Fitness Industry
Based on Internet Plus Era.
Jabez, J., & Muthukumar, B. (2015). Intrusion detection system (IDS): anomaly detection
using outlier detection approach. Procedia Computer Science, 48, 338-346.
Farnaaz, N., & Jabbar, M. A. (2016). Random forest modeling for network intrusion
detection system. Procedia Computer Science, 89, 213-217.
Duque, S., & bin Omar, M. N. (2015). Using data mining algorithms for developing a model
for intrusion detection system (IDS). Procedia Computer Science, 61, 46-51.
Snapp, S. R., Brentano, J., Dias, G., Goan, T. L., Heberlein, L. T., Ho, C. L., & Levitt, K. N.
(2017). DIDS (distributed intrusion detection system)-motivation, architecture, and an
early prototype.
Page 8 of 10

RISK REPORT FOR ABC FITNESS GYM
Bertino, E. (2016, March). Data Security and Privacy in the IoT. In EDBT (Vol. 2016, pp. 1-
3).
Zhang, D. (2018, October). Big data security and privacy protection. In 8th International
Conference on Management and Computer Science (ICMCS 2018). Atlantis Press.
Page 9 of 10
Bertino, E. (2016, March). Data Security and Privacy in the IoT. In EDBT (Vol. 2016, pp. 1-
3).
Zhang, D. (2018, October). Big data security and privacy protection. In 8th International
Conference on Management and Computer Science (ICMCS 2018). Atlantis Press.
Page 9 of 10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




