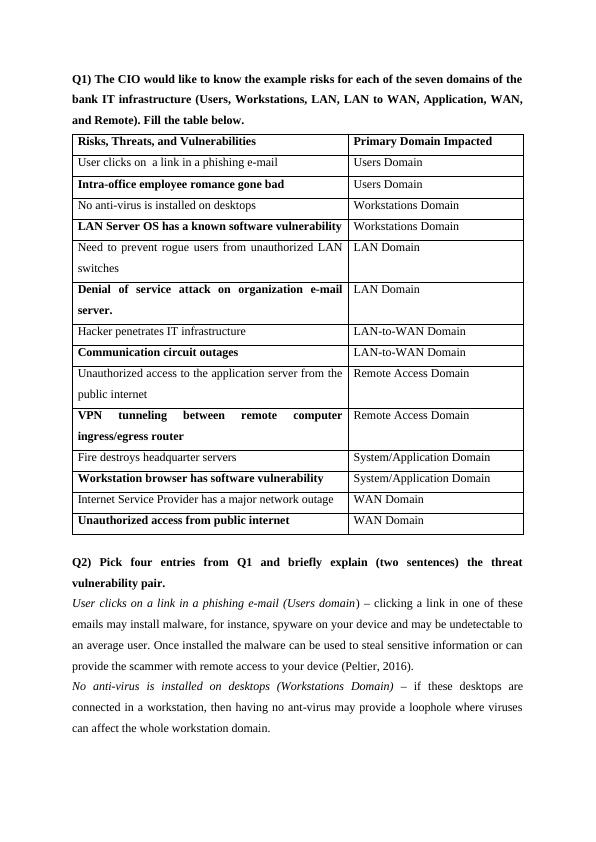
Risks, Threats, and Vulnerabilities in Bank IT Infrastructure
Added on 2023-04-22
3 Pages803 Words366 Views
End of preview
Want to access all the pages? Upload your documents or become a member.
Risk Assessment for Information Security and Risk Management
|7
|1064
|150
Ethical Hacking: Methodology, Tools and Penetration Testing
|17
|1703
|348
Home Network Vulnerabilities
|5
|858
|297