Mobi-Cloud: Routing Data in Mobile Cloud Computing Networks Report
VerifiedAdded on 2019/12/18
|29
|8314
|317
Report
AI Summary
This report presents a detailed analysis of Mobi-Cloud, a novel mobile cloud computing network designed to enhance secure communication and data routing in mobile ad hoc networks. The introduction highlights the limitations of existing mobile cloud models and emphasizes the need for a new architecture to support computationally intensive tasks and address security concerns. The report introduces the Mobi-Cloud architecture, which transforms mobile nodes into service nodes leveraging cloud computing for virtualization, security, and trust management. Key components of the architecture include Software Agents (SAs), Virtual Trusted and Provisioning Domains (VTaPDs), Hub Managers (NMs), Extended Semi-Shadow Pictures (ESSIs), and the Mobi-Cloud Asset and Application Manager (RAM). The report further explores Mobi-Cloud's security services, including identity, key, and secure data access policy management, along with its setting-aware routing and risk assessment capabilities. The report also discusses potential application scenarios, such as proficient communication, security and administration disconnection, and defer resistance correspondence situations. Finally, the report concludes with a discussion of future research directions and open issues in the field of mobile cloud computing and secure ad hoc networks.

Routing Data in Mobile Cloud Computing Networking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction.................................................................................................................................................3
Related Work...............................................................................................................................................6
Mobi-cloud Architecture.............................................................................................................................7
Mobi-Cloud Security Services Architecture................................................................................................8
Mobi-Cloud Architecture:.......................................................................................................................8
Asset Disconnection:.............................................................................................................................11
Information Get To Control:..................................................................................................................12
Mobi-Cloud Trust Management................................................................................................................13
Setting Mindful Routing:...........................................................................................................................18
New Mobi-Cloud Application Scenarios...................................................................................................20
Proficient Communication Situation:........................................................................................................21
Security and Administration Disconnection Situation:..............................................................................22
Defer Resistance Correspondence Situation:.............................................................................................23
Discussion and Future Research Directions...............................................................................................23
References.................................................................................................................................................26
Introduction.................................................................................................................................................3
Related Work...............................................................................................................................................6
Mobi-cloud Architecture.............................................................................................................................7
Mobi-Cloud Security Services Architecture................................................................................................8
Mobi-Cloud Architecture:.......................................................................................................................8
Asset Disconnection:.............................................................................................................................11
Information Get To Control:..................................................................................................................12
Mobi-Cloud Trust Management................................................................................................................13
Setting Mindful Routing:...........................................................................................................................18
New Mobi-Cloud Application Scenarios...................................................................................................20
Proficient Communication Situation:........................................................................................................21
Security and Administration Disconnection Situation:..............................................................................22
Defer Resistance Correspondence Situation:.............................................................................................23
Discussion and Future Research Directions...............................................................................................23
References.................................................................................................................................................26

Introduction
The utilization of mobiles to build up impromptu correspondence frameworks is a reasonable
arrangement that gives worldwide network to bolster a wide scope of uses. With the
advancement of remote get to innovations, for example, 3/4G, LTE, furthermore, WiMax,
mobiles can access the system center over longer separations and bigger transmission capacities.
This permits for extremely viable correspondence between mobiles what's more, the cloud
framework. Another administration design is important to address the prerequisites of clients in
their exceptional operational condition and make new versatile applications. All in all, portable
clients can profit incredibly from cloud administrations for computationally serious data
preparing and gathering, for example, data look, information handling, information mining,
organize status observing, field detecting, and so forth. Be that as it may, existing portable cloud
benefit display works for the most part one directional.
For instance, shopper hardware gadgets can utilize the cloud as a figuring and data asset.
Operations can be outsourced to the cloud, however the cloud has little control over the CE
gadgets. The target of our exploration is to utilize a methodical approach to explore both
distributed computing and versatile impromptu systems (mobile ad hoc networks) advances so as
to comprehend the capacity of distributed computing for securing mobile ad hoc network
applications. This examination article is introduced as a position paper to highlight look into
bearings and conceivable answers for improving secure portable processing utilizing distributed
computing.
We exhibit another mobile ad hoc network correspondence system named Mobi-Cloud that will
on a very basic level change the exploration and advancement of secure mobile ad hoc network
innovations. Besides, we will recognize various open research issues that will give direction for
The utilization of mobiles to build up impromptu correspondence frameworks is a reasonable
arrangement that gives worldwide network to bolster a wide scope of uses. With the
advancement of remote get to innovations, for example, 3/4G, LTE, furthermore, WiMax,
mobiles can access the system center over longer separations and bigger transmission capacities.
This permits for extremely viable correspondence between mobiles what's more, the cloud
framework. Another administration design is important to address the prerequisites of clients in
their exceptional operational condition and make new versatile applications. All in all, portable
clients can profit incredibly from cloud administrations for computationally serious data
preparing and gathering, for example, data look, information handling, information mining,
organize status observing, field detecting, and so forth. Be that as it may, existing portable cloud
benefit display works for the most part one directional.
For instance, shopper hardware gadgets can utilize the cloud as a figuring and data asset.
Operations can be outsourced to the cloud, however the cloud has little control over the CE
gadgets. The target of our exploration is to utilize a methodical approach to explore both
distributed computing and versatile impromptu systems (mobile ad hoc networks) advances so as
to comprehend the capacity of distributed computing for securing mobile ad hoc network
applications. This examination article is introduced as a position paper to highlight look into
bearings and conceivable answers for improving secure portable processing utilizing distributed
computing.
We exhibit another mobile ad hoc network correspondence system named Mobi-Cloud that will
on a very basic level change the exploration and advancement of secure mobile ad hoc network
innovations. Besides, we will recognize various open research issues that will give direction for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the distributed computing and mobile ad hoc network examine groups to growing new answers
for secure portable processing.
Building a dependable mobile ad hoc network correspondence framework is a standout amongst
the most difficult research issues of versatile figuring. This is brought on for the most part by two
between related research issues: (1) the security of existing mobile ad hoc network framework
needs between operability bolster in a heterogeneous correspondence condition. Specialized
gadgets having a place with distinctive regulatory spaces with various correspondences what's
more, calculation abilities make convention plan to a great degree troublesome. This issue is
normally brought about by the instability in the security setup of interchanges associates amid
trust foundation. For instance, versatile substances may utilize distinctive personality space,
cryptographic parameters, and dwell in various managerial spaces. (2) mobile ad hoc network
versatility has a critical affect on the security and correspondence execution identifying with area
following, correspondence protection, unwavering quality also, survivability. Instability
presented by versatility produces flighty between meeting length, transmission rates, and areas.
In this way, the mobile ad hoc network operations require a thorough approach concentrating on
hazard evaluation with deference to security and correspondence prerequisites.
Mobi-Cloud changes customary mobile ad hoc networks into another benefit situated
correspondence engineering. Mobi-Cloud changes every versatile hub from a customary entirely
layer structured correspondence hub into an administration hub (SN). Every SN can be utilized
as a specialist co-op or an administration specialist concurring its ability, e.g., accessible
calculation what's more, correspondence abilities to bolster a specific administration. This
approach takes most extreme favorable position of every versatile hub in the framework by using
distributed computing advancements. To decrease the vulnerability brought on by portability, we
for secure portable processing.
Building a dependable mobile ad hoc network correspondence framework is a standout amongst
the most difficult research issues of versatile figuring. This is brought on for the most part by two
between related research issues: (1) the security of existing mobile ad hoc network framework
needs between operability bolster in a heterogeneous correspondence condition. Specialized
gadgets having a place with distinctive regulatory spaces with various correspondences what's
more, calculation abilities make convention plan to a great degree troublesome. This issue is
normally brought about by the instability in the security setup of interchanges associates amid
trust foundation. For instance, versatile substances may utilize distinctive personality space,
cryptographic parameters, and dwell in various managerial spaces. (2) mobile ad hoc network
versatility has a critical affect on the security and correspondence execution identifying with area
following, correspondence protection, unwavering quality also, survivability. Instability
presented by versatility produces flighty between meeting length, transmission rates, and areas.
In this way, the mobile ad hoc network operations require a thorough approach concentrating on
hazard evaluation with deference to security and correspondence prerequisites.
Mobi-Cloud changes customary mobile ad hoc networks into another benefit situated
correspondence engineering. Mobi-Cloud changes every versatile hub from a customary entirely
layer structured correspondence hub into an administration hub (SN). Every SN can be utilized
as a specialist co-op or an administration specialist concurring its ability, e.g., accessible
calculation what's more, correspondence abilities to bolster a specific administration. This
approach takes most extreme favorable position of every versatile hub in the framework by using
distributed computing advancements. To decrease the vulnerability brought on by portability, we
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

fuse each SN into the Mobi-Cloud as a virtualized part. Every SN is reflected to at least one
Extended Semi-Shadow Pictures (ESSIs) in the cloud with a specific end goal to address the
correspondence what's more, calculation insufficiencies of mobile. We take note of that ESSI can
be separated from a virtual picture" in that an ESSI can be a correct clone, a halfway clone, or an
picture containing amplified elements of the physical gadget. In expansion, the ESSIs make a
virtualized mobile ad hoc network directing and correspondence layer that can help the physical
portable hubs what's more, expand accessibility of inescapable registering administrations for
every portable client. The principle commitments of this exploration paper are outlined as takes
after:
Mobi-Cloud underpins the mobile ad hoc network elements of data dispersal, steering,
restriction, and trust administration.
Mobi-Cloud receives distributed computing innovation to make a virtualized domain for
mobile ad hoc network operations in different administration provisioning areas as per
the criticality of mobile ad hoc network administrations and comparing security
necessities.
Mobi-Cloud gives a major trust display including personality administration, key
administration, and security information get to approach requirement that can be utilized
to create future portable applications.
Mobi-Cloud underpins the mobile ad hoc network operations through inquire about on
setting mindful hazard evaluation utilizing correspondence furthermore, execution
measurements of every portable hub under relating security necessities. This will permit
us to utilize the Mobi-Cloud to review different execution and security issues of mobile
ad hoc network and create helpful information.
Extended Semi-Shadow Pictures (ESSIs) in the cloud with a specific end goal to address the
correspondence what's more, calculation insufficiencies of mobile. We take note of that ESSI can
be separated from a virtual picture" in that an ESSI can be a correct clone, a halfway clone, or an
picture containing amplified elements of the physical gadget. In expansion, the ESSIs make a
virtualized mobile ad hoc network directing and correspondence layer that can help the physical
portable hubs what's more, expand accessibility of inescapable registering administrations for
every portable client. The principle commitments of this exploration paper are outlined as takes
after:
Mobi-Cloud underpins the mobile ad hoc network elements of data dispersal, steering,
restriction, and trust administration.
Mobi-Cloud receives distributed computing innovation to make a virtualized domain for
mobile ad hoc network operations in different administration provisioning areas as per
the criticality of mobile ad hoc network administrations and comparing security
necessities.
Mobi-Cloud gives a major trust display including personality administration, key
administration, and security information get to approach requirement that can be utilized
to create future portable applications.
Mobi-Cloud underpins the mobile ad hoc network operations through inquire about on
setting mindful hazard evaluation utilizing correspondence furthermore, execution
measurements of every portable hub under relating security necessities. This will permit
us to utilize the Mobi-Cloud to review different execution and security issues of mobile
ad hoc network and create helpful information.

Whatever is left of this paper is masterminded as takes after: In Section II, we introduce late
research in both distributed computing and secure mobile ad hoc network correspondence. The
itemized portrayal of Mobi-Cloud is exhibited in Section III. In Section IV, we exhibit new
applications that can be upheld by utilizing Mobi-Cloud. At last, we condense the proposed
arrangement and exhibit open research issues in Section V.
Related Work
In this segment, we introduced related work in two zones: security in distributed computing and
secure mobile ad hoc network correspondence utilizing distributed computing. Distributed
computing is another plan of action centering on asset on-request, pay-as-you-go, and utility
computing [1]. Distributed computing can be extensively classified as framework as-an
administration (IaaS), stage as-an administration (PaaS), and programming as-an administration
(SaaS). Basic research issues for distributed computing, for example, calculation offloading,
remote execution, and element sythesis have been widely talked about in past writing. A few
drew closer have been proposed on upgrading security of Clouds themselves, for example,
framework security [2] in view of TCG/TPM [3], secure outsourcing [4], [5], [6], [7], cloud web
security [8], [9], asset administration and confinement [10], [11], and protection [12], [13].
Late research have been centered around distributed computing for mobiles [14], [15], [14], [16].
Distributed computing for mobiles has a noteworthy advantage in that it empowers running
applications between asset obliged gadgets and Web based Clouds. Besides, asset obliged
gadgets can outsource calculation/correspondence/asset escalated operations to the cloud.
CloneCloud [17] concentrates on execution growth with less thought on client inclination or
gadget status. Samsung has proposed the idea of flexible applications which can offload
segments of utilizations from mobiles to cloud [18]. Oberheide et al. [19] show a system that
research in both distributed computing and secure mobile ad hoc network correspondence. The
itemized portrayal of Mobi-Cloud is exhibited in Section III. In Section IV, we exhibit new
applications that can be upheld by utilizing Mobi-Cloud. At last, we condense the proposed
arrangement and exhibit open research issues in Section V.
Related Work
In this segment, we introduced related work in two zones: security in distributed computing and
secure mobile ad hoc network correspondence utilizing distributed computing. Distributed
computing is another plan of action centering on asset on-request, pay-as-you-go, and utility
computing [1]. Distributed computing can be extensively classified as framework as-an
administration (IaaS), stage as-an administration (PaaS), and programming as-an administration
(SaaS). Basic research issues for distributed computing, for example, calculation offloading,
remote execution, and element sythesis have been widely talked about in past writing. A few
drew closer have been proposed on upgrading security of Clouds themselves, for example,
framework security [2] in view of TCG/TPM [3], secure outsourcing [4], [5], [6], [7], cloud web
security [8], [9], asset administration and confinement [10], [11], and protection [12], [13].
Late research have been centered around distributed computing for mobiles [14], [15], [14], [16].
Distributed computing for mobiles has a noteworthy advantage in that it empowers running
applications between asset obliged gadgets and Web based Clouds. Besides, asset obliged
gadgets can outsource calculation/correspondence/asset escalated operations to the cloud.
CloneCloud [17] concentrates on execution growth with less thought on client inclination or
gadget status. Samsung has proposed the idea of flexible applications which can offload
segments of utilizations from mobiles to cloud [18]. Oberheide et al. [19] show a system that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

outsources the counter infection administrations from mobiles to a cloud. Goayl and Carter
propose a safe digital scrounging system for asset compelled gadgets [20]. Existing versatile
cloud arrangements are restricted and concentrate exclusively on upgrading the ability mobile on
an individual premise.
Mobi-cloud Architecture
In this Section, we first portray the Mobi-Cloud engineering (appeared in Figure 1) and its
support for security benefit provisioning, asset and security disengagement, and the joining of
handling and operations of cloud and mobile ad hoc networks. We then portray a few
administrations that can help both cloud and mobile ad hoc network to accomplish the proposed
framework level functionalities, for example, personality administration, key administration,
strategy implementation, what's more, setting mindful steering and hazard appraisal.
propose a safe digital scrounging system for asset compelled gadgets [20]. Existing versatile
cloud arrangements are restricted and concentrate exclusively on upgrading the ability mobile on
an individual premise.
Mobi-cloud Architecture
In this Section, we first portray the Mobi-Cloud engineering (appeared in Figure 1) and its
support for security benefit provisioning, asset and security disengagement, and the joining of
handling and operations of cloud and mobile ad hoc networks. We then portray a few
administrations that can help both cloud and mobile ad hoc network to accomplish the proposed
framework level functionalities, for example, personality administration, key administration,
strategy implementation, what's more, setting mindful steering and hazard appraisal.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
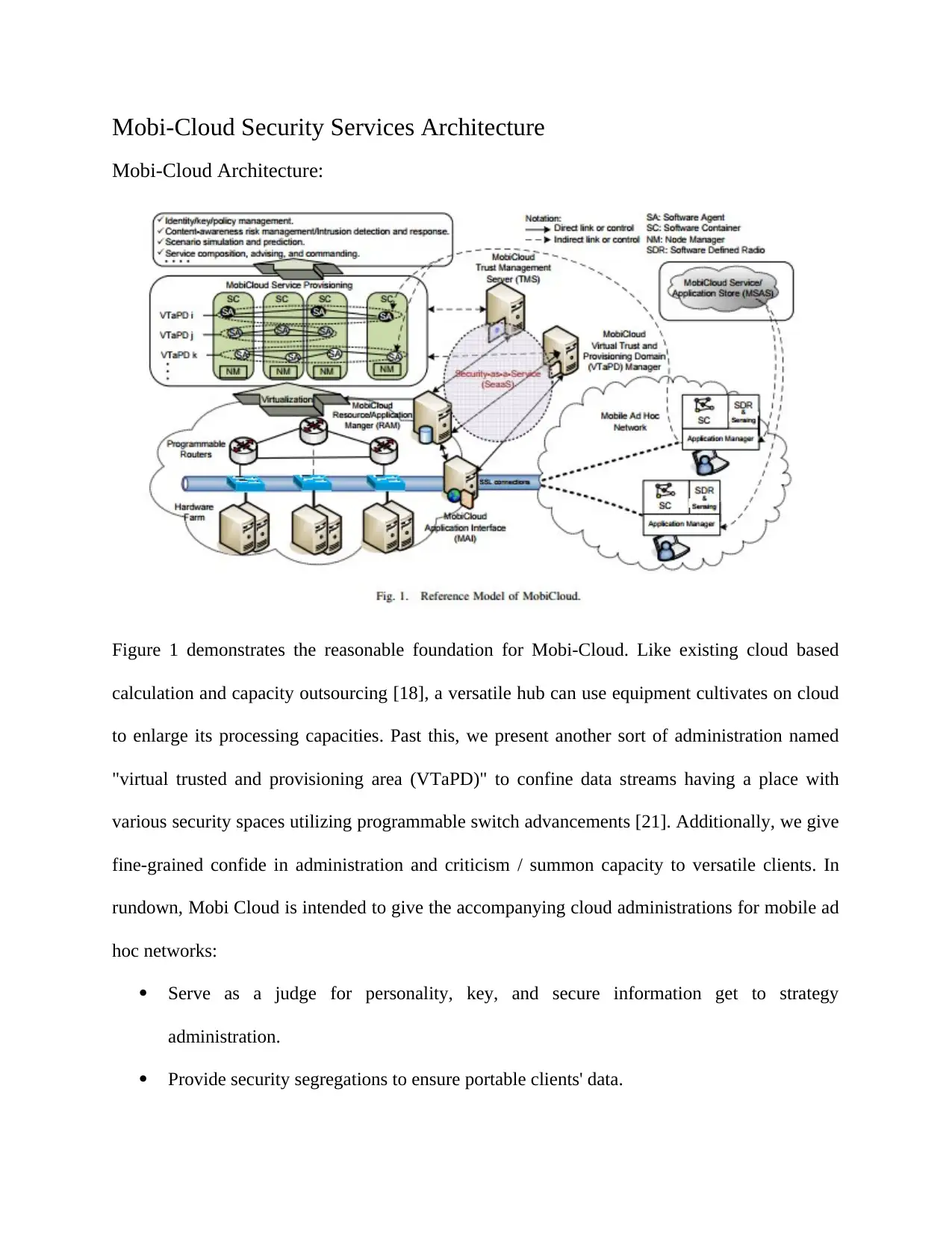
Mobi-Cloud Security Services Architecture
Mobi-Cloud Architecture:
Figure 1 demonstrates the reasonable foundation for Mobi-Cloud. Like existing cloud based
calculation and capacity outsourcing [18], a versatile hub can use equipment cultivates on cloud
to enlarge its processing capacities. Past this, we present another sort of administration named
"virtual trusted and provisioning area (VTaPD)" to confine data streams having a place with
various security spaces utilizing programmable switch advancements [21]. Additionally, we give
fine-grained confide in administration and criticism / summon capacity to versatile clients. In
rundown, Mobi Cloud is intended to give the accompanying cloud administrations for mobile ad
hoc networks:
Serve as a judge for personality, key, and secure information get to strategy
administration.
Provide security segregations to ensure portable clients' data.
Mobi-Cloud Architecture:
Figure 1 demonstrates the reasonable foundation for Mobi-Cloud. Like existing cloud based
calculation and capacity outsourcing [18], a versatile hub can use equipment cultivates on cloud
to enlarge its processing capacities. Past this, we present another sort of administration named
"virtual trusted and provisioning area (VTaPD)" to confine data streams having a place with
various security spaces utilizing programmable switch advancements [21]. Additionally, we give
fine-grained confide in administration and criticism / summon capacity to versatile clients. In
rundown, Mobi Cloud is intended to give the accompanying cloud administrations for mobile ad
hoc networks:
Serve as a judge for personality, key, and secure information get to strategy
administration.
Provide security segregations to ensure portable clients' data.

Monitor mobile ad hoc network status for hazard evaluations, interruption location and
reaction.
Simulate situations and foresee future mobile ad hoc network circumstances for basic
leadership.
Provide benefit organization and applications for versatile gadgets.
Presently, we portray the usefulness and properties of each part of Figure 1. Mobi-Cloud utilizes
Software Agents (SAs) (i.e., application parts) to interface the cloud administrations also,
mobiles. A similar SA can keep running on both the mobile and the cloud stages
correspondingly. Each gadget can have various SAs for various cloud administrations then again
mobile ad hoc networkS, which are overseen by application supervisor of the gadget. Every
gadget likewise gives detecting information about the gadget itself, (for example, processor sort,
use, battery state, furthermore, area with GPS bolster), and about the neighboring portable hubs,
(for example, neighbor's character or addresses, interface quality, neighboring spans, and so on.),
which are overseen by the sensor director.
On the cloud side, the Mobi-Cloud Application Interface (MAI) sends out administrations that
can be devoured by to portable gadgets. Likewise, the MAI additionally give interfaces to
VTaPD director and Resource and Application Manager (Slam). Center product based
arrangements are required when the cloud segments don't utilize online interfaces. A few novel
cloud segments and developments are proposed for Mobi-Cloud. We present programmable
switches that can be used to make different VTaPDs. VTaPDs are made basically for
disengaging data stream and get to control by making numerous virtual areas. There are two
fundamental purposes behind numerous virtual areas: (1) security, a client's gadget may run
various applications at various security areas, e.g., its concurrent correspondence with two
reaction.
Simulate situations and foresee future mobile ad hoc network circumstances for basic
leadership.
Provide benefit organization and applications for versatile gadgets.
Presently, we portray the usefulness and properties of each part of Figure 1. Mobi-Cloud utilizes
Software Agents (SAs) (i.e., application parts) to interface the cloud administrations also,
mobiles. A similar SA can keep running on both the mobile and the cloud stages
correspondingly. Each gadget can have various SAs for various cloud administrations then again
mobile ad hoc networkS, which are overseen by application supervisor of the gadget. Every
gadget likewise gives detecting information about the gadget itself, (for example, processor sort,
use, battery state, furthermore, area with GPS bolster), and about the neighboring portable hubs,
(for example, neighbor's character or addresses, interface quality, neighboring spans, and so on.),
which are overseen by the sensor director.
On the cloud side, the Mobi-Cloud Application Interface (MAI) sends out administrations that
can be devoured by to portable gadgets. Likewise, the MAI additionally give interfaces to
VTaPD director and Resource and Application Manager (Slam). Center product based
arrangements are required when the cloud segments don't utilize online interfaces. A few novel
cloud segments and developments are proposed for Mobi-Cloud. We present programmable
switches that can be used to make different VTaPDs. VTaPDs are made basically for
disengaging data stream and get to control by making numerous virtual areas. There are two
fundamental purposes behind numerous virtual areas: (1) security, a client's gadget may run
various applications at various security areas, e.g., its concurrent correspondence with two
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

people with from managerial spaces; and (2) setting mindfulness, it might be important to
separate administrations for various nearby and organize settings. For instance, Mobi-Cloud can
reproduce the operations of the mobile ad hoc networks utilizing distinctive framework
parameters then again courses choice calculations to think about various methodologies for using
distributed computing and correspondence assets.
This approach gives a far reaching review of mobile ad hoc network operations and gives data to
mobiles and framework chiefs for basic leadership. In each VTaPD, at least one SAs are utilized
for each ESSI. A Hub Manager (NM) is in charge of dealing with the stacking furthermore,
emptying of SAs in the ESSI. The ESSI additionally gives extra capacities past the elements of a
mobile. For instance, the cloud will have the capacity to run benefits that are not accessible in
mobile ad hoc networks, for example, seek, information mining, media preparing, trust pre-
foundation (e.g., certification trade what's more, building up security enters ahead of time), and
so on. The Mobi-Cloud Asset and Application Manager (RAM) builds VTaPDs when it is
coordinated by Mobi-Cloud VTaPD supervisor also, Mobi-Cloud Trust Manager Server (TMS).
They frame the center for giving Security-as-a-Service (SeaaS). With SeaaS, Mobi-Cloud can
offer security benefit creation ability as per solicitations from portable applications.
In our SeaaS benefit display, the VTaPD director plays the focal part since it gathers setting
mindfulness data from the mobile ad hoc network, (for example, gadget detecting qualities, area,
and neighboring gadget status) and utilized it for interruption discovery what's more, hazard
administration. The Mobi-Cloud TMS is the Trust Expert (TA) for Mobi-Cloud. It handles the
property based key dispersion and repudiation. It gives personality look and league
administrations for mobiles having a place with numerous managerial areas. It additionally
separate administrations for various nearby and organize settings. For instance, Mobi-Cloud can
reproduce the operations of the mobile ad hoc networks utilizing distinctive framework
parameters then again courses choice calculations to think about various methodologies for using
distributed computing and correspondence assets.
This approach gives a far reaching review of mobile ad hoc network operations and gives data to
mobiles and framework chiefs for basic leadership. In each VTaPD, at least one SAs are utilized
for each ESSI. A Hub Manager (NM) is in charge of dealing with the stacking furthermore,
emptying of SAs in the ESSI. The ESSI additionally gives extra capacities past the elements of a
mobile. For instance, the cloud will have the capacity to run benefits that are not accessible in
mobile ad hoc networks, for example, seek, information mining, media preparing, trust pre-
foundation (e.g., certification trade what's more, building up security enters ahead of time), and
so on. The Mobi-Cloud Asset and Application Manager (RAM) builds VTaPDs when it is
coordinated by Mobi-Cloud VTaPD supervisor also, Mobi-Cloud Trust Manager Server (TMS).
They frame the center for giving Security-as-a-Service (SeaaS). With SeaaS, Mobi-Cloud can
offer security benefit creation ability as per solicitations from portable applications.
In our SeaaS benefit display, the VTaPD director plays the focal part since it gathers setting
mindfulness data from the mobile ad hoc network, (for example, gadget detecting qualities, area,
and neighboring gadget status) and utilized it for interruption discovery what's more, hazard
administration. The Mobi-Cloud TMS is the Trust Expert (TA) for Mobi-Cloud. It handles the
property based key dispersion and repudiation. It gives personality look and league
administrations for mobiles having a place with numerous managerial areas. It additionally
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

performs approach checking and requirement capacities to give a bound together trust
administration framework for Mobi-Cloud.
At last, the Mobi-Cloud Service and Application Store (MSAS) fills in as the storehouse for SAs
and applications. At the point when benefit creation is required, the MSAS will introduce the
required SAs or applications through the MAI. For instance, at the point when a mobile needs to
converse with another gadget utilizing distinctive recurrence groups, the Software Defined Radio
(SDR) requirements to introduce another driver and the hub needs another confirmation module.
In this situation, the SAs for the new drivers and confirmation module will be introduced. This
operation needs coordinated efforts amongst TMS and MSAS.
Secure Isolation through VTaPDs: VTaPDs are built up to give information get to control and
data insurance. We should take note of that the structure may not require / suggest the division of
the authoritative space into VTaPDs. In the accompanying subsection, we will address the cloud
asset disconnection and security seclusion.
Asset Disconnection:
The real authoritative work is taken care of by the Mobi-Cloud VTaPD chief. Each hub that has a
place with a specific VTaPD will have the entire directing data for VTaPD in which it lives, yet
not others. Every hub can live an alternate physical framework. Every hub would need to bolster
our interchanges structure which incorporates secure gathering correspondence to sending
information to all the ESSIs in the same VTaPD. The transfer speed for a correspondence
connection can be isolated by utilizing distinctive encryption/unscrambling / validation keys.
Favorable position of the Mobi-Cloud structure that gives organize virtualization through
numerous VTaPDs is that it encourages prioritization of basic/crisis benefits in a system. For
instance, utilizing the proposed virtualization approach, organized and ordinary benefit classes
can be characterized utilizing distinctive VTaPDs. They can have the same physical mobile ad
administration framework for Mobi-Cloud.
At last, the Mobi-Cloud Service and Application Store (MSAS) fills in as the storehouse for SAs
and applications. At the point when benefit creation is required, the MSAS will introduce the
required SAs or applications through the MAI. For instance, at the point when a mobile needs to
converse with another gadget utilizing distinctive recurrence groups, the Software Defined Radio
(SDR) requirements to introduce another driver and the hub needs another confirmation module.
In this situation, the SAs for the new drivers and confirmation module will be introduced. This
operation needs coordinated efforts amongst TMS and MSAS.
Secure Isolation through VTaPDs: VTaPDs are built up to give information get to control and
data insurance. We should take note of that the structure may not require / suggest the division of
the authoritative space into VTaPDs. In the accompanying subsection, we will address the cloud
asset disconnection and security seclusion.
Asset Disconnection:
The real authoritative work is taken care of by the Mobi-Cloud VTaPD chief. Each hub that has a
place with a specific VTaPD will have the entire directing data for VTaPD in which it lives, yet
not others. Every hub can live an alternate physical framework. Every hub would need to bolster
our interchanges structure which incorporates secure gathering correspondence to sending
information to all the ESSIs in the same VTaPD. The transfer speed for a correspondence
connection can be isolated by utilizing distinctive encryption/unscrambling / validation keys.
Favorable position of the Mobi-Cloud structure that gives organize virtualization through
numerous VTaPDs is that it encourages prioritization of basic/crisis benefits in a system. For
instance, utilizing the proposed virtualization approach, organized and ordinary benefit classes
can be characterized utilizing distinctive VTaPDs. They can have the same physical mobile ad

hoc network however organized in view of the VTaPD. mobile ad hoc network operations and
interchanges can be relocated into the cloud when distributed correspondence is under anxiety
either from lacking data transfer capacity or assaults.
Information Get To Control:
Notwithstanding the confinement gave by VTaPD benefit space, Mobi-Cloud additionally needs
to coordinate information get to control and data detachment utilizing a cryptography based
approach. Other than the conventional security concerns (i.e., confirmation, approval, review and
so on.), extra security dangers are presented by portable clients who share a similar application
occasion and assets. In cloud related writing, these alluded to as multi-inhabitant situations. Each
portable client's ESSI can be considered as his/her tenure in the Mobi-Cloud. In the multi-
inhabitant condition, information get to control is a standout amongst the most basic security
worries that should be tended to. Information detachment components counteract clients from
getting to assets having a place with different inhabitants. There are for the most part two sorts of
get to control detachment designs: understood channel and express consent. Chong et al. [22]
acquainted how with apply these two examples into a multitenant information demonstrate. We
additionally sum up the two examples to give get to control to different assets:
Implicit Filter Based Access Control Isolation: In this design, when one inhabitant
solicitations to get to shared assets, a typical stage level record (i.e., the ESSI personality
with comparing SA and cloud asset demands) is assigned to deal with this demand. The
designated record is shared by each of the occupants and has the benefits to get to assets
of every one of the inhabitants. Be that as it may, the key of this system is to certainly
form an inhabitant situated channel that will be utilized to keep one client from tapping
into assets of different occupants. This can be accomplished by utilizing a cryptography-
interchanges can be relocated into the cloud when distributed correspondence is under anxiety
either from lacking data transfer capacity or assaults.
Information Get To Control:
Notwithstanding the confinement gave by VTaPD benefit space, Mobi-Cloud additionally needs
to coordinate information get to control and data detachment utilizing a cryptography based
approach. Other than the conventional security concerns (i.e., confirmation, approval, review and
so on.), extra security dangers are presented by portable clients who share a similar application
occasion and assets. In cloud related writing, these alluded to as multi-inhabitant situations. Each
portable client's ESSI can be considered as his/her tenure in the Mobi-Cloud. In the multi-
inhabitant condition, information get to control is a standout amongst the most basic security
worries that should be tended to. Information detachment components counteract clients from
getting to assets having a place with different inhabitants. There are for the most part two sorts of
get to control detachment designs: understood channel and express consent. Chong et al. [22]
acquainted how with apply these two examples into a multitenant information demonstrate. We
additionally sum up the two examples to give get to control to different assets:
Implicit Filter Based Access Control Isolation: In this design, when one inhabitant
solicitations to get to shared assets, a typical stage level record (i.e., the ESSI personality
with comparing SA and cloud asset demands) is assigned to deal with this demand. The
designated record is shared by each of the occupants and has the benefits to get to assets
of every one of the inhabitants. Be that as it may, the key of this system is to certainly
form an inhabitant situated channel that will be utilized to keep one client from tapping
into assets of different occupants. This can be accomplished by utilizing a cryptography-
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 29
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


