Enhanced OpenVPN Frame Structure
VerifiedAdded on 2019/09/25
|6
|4182
|211
Report
AI Summary
The assignment content discusses the implementation of OpenVPN, a virtual private network (VPN) solution that provides two tunneling modes: TCP and UDP. The enhanced security features of OpenVPN include public key infrastructure authentication and multi-factor authentication. Additionally, the OpenSSL encryption mechanism is used to encrypt data and authenticate peers. The RSA algorithm is also discussed as a strong encryption mechanism that can be used for secure communication. However, it is noted that the RSA algorithm may be vulnerable to attacks if the Riemann hypothesis is solved.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

RSA Algorithm Functionalities and Mathematical Implementation Of
SSL-VPN Architecture for Multimedia Industry
Chanaka Lasantha Nanayakakra
Faculty of Science, Engineering and Computing
Master of Science Network and Information Security
Kingston University UK, Student ID: K1658833
chanaka.lasantha@gmail.com
Abstract—The SSL VPN is the major technology in the current
VPN market as a one of the best technology under opensource
world instead of compilated called OpenVPN. The Oldest IPSec
VPN technology too complex for correctly implement as well less
of security strength weakness and expensiveness are the major
negative drawback of the IPSec VPN Technology. IPSec has too
many required optional parameters configurations to become to
secured working condition and since it was implemented by
some non-expert professions regarding on IPSec domain. In
additionally IPSec preconfigured to operates over kernel
workspace by facilitating some of cybercriminal society to
mistakenly allowed attack by exposing over catastrophic failure.
OpenVPN is always avoiding the unwanted complexity
compared to IPSec VPN technology to taking SSL/TLS
mechanism with cryptographic libraries provides much better
functionalities in simplest lightweight package successfully.
OpenVPN is pioneer as real SSL VPN enforcer to other SSL
VPN products by facilitation the same operational functionalities
towards into the IPSec sector. Therefore, the OpenVPN is based
on SSL/TSL concept into the reality of implementation, it also
based on RSA Algorithm with Additional Technologies.
Therefor the key concerned area is focused into the RSA
Algorithm.
INDEX TERMS
Introduction, Technical and Mathematical Philosophy of
RSA, Key Distribution of SSL-VPN, RSA Algorithm Integrated
in SSL-VPN, RSA Encryption Algorithm Functionality,
Mathematical Evaluation of Encryption and Decryption,
Example of RSA Encryption and Decryption, The Extended
Euclidean Algorithm Definition, Practical Protection
Illustration and Secureness of RSA, Key Creation and
Exchange, Hashing Methodology with HMAC of SSL-VPN,
C on c lu sio n .
I. INTRODUCTION
This report illustrated how to function RSA Algorithm using
evaluating, the true pattern of encryption and decryption in
SSL based VPN mechanisms. The major risk is to delivering
keys amount sender and receiver sides by protecting cyber-
attacks, therefore the public key cryptography mechanism
came into the
seen, the whatever data have been encrypted by public key
can possible to decrypted only applying receiver side private
key to
obtain the real massage [1]. There is way to send the session
key using digital locker called envelope with special
technology such as either Diffie-Hellman or Elliptic Curve
methodology. the public key technology take place to generate
a sheared key, which is only correspondents allowed to create
certain secret
value where can use used act as session key. Mainly in Public
key cryptography support to overcome key distribution
difficulties and this methodology focused on two main
cryptography critical issues, authentication and nonrepudiation
over secured tunnel. Data and Identity sections are protected [2].
with someone who need authentication over the electronic world,
and at the other hand nonrepudiation prevents on unknown
peoples, Therefore the digital signature was came into the
operation to mitigate issues of above mentioned circumstance.
Figure 1: SSL Operation Illustration.
SSL-VPN (Secure Socket Layer Virtual Private Network)
Systems are mainly used to interconnected between one or
more private endpoints by encrypting internet traffics towards
into the protected tunnel, also that very impossible to make
eavesdropping attacks theoretically [3]. none application based
tunneling grants to established a tunnel in between two or more
geographical sites, that allowed one LAN network to
intercommunicate with another LAN network over wider range
of accessibility.
SSL-VPN is factorized on RSA Algorithm. The RSA algorithm
SSL-VPN Architecture for Multimedia Industry
Chanaka Lasantha Nanayakakra
Faculty of Science, Engineering and Computing
Master of Science Network and Information Security
Kingston University UK, Student ID: K1658833
chanaka.lasantha@gmail.com
Abstract—The SSL VPN is the major technology in the current
VPN market as a one of the best technology under opensource
world instead of compilated called OpenVPN. The Oldest IPSec
VPN technology too complex for correctly implement as well less
of security strength weakness and expensiveness are the major
negative drawback of the IPSec VPN Technology. IPSec has too
many required optional parameters configurations to become to
secured working condition and since it was implemented by
some non-expert professions regarding on IPSec domain. In
additionally IPSec preconfigured to operates over kernel
workspace by facilitating some of cybercriminal society to
mistakenly allowed attack by exposing over catastrophic failure.
OpenVPN is always avoiding the unwanted complexity
compared to IPSec VPN technology to taking SSL/TLS
mechanism with cryptographic libraries provides much better
functionalities in simplest lightweight package successfully.
OpenVPN is pioneer as real SSL VPN enforcer to other SSL
VPN products by facilitation the same operational functionalities
towards into the IPSec sector. Therefore, the OpenVPN is based
on SSL/TSL concept into the reality of implementation, it also
based on RSA Algorithm with Additional Technologies.
Therefor the key concerned area is focused into the RSA
Algorithm.
INDEX TERMS
Introduction, Technical and Mathematical Philosophy of
RSA, Key Distribution of SSL-VPN, RSA Algorithm Integrated
in SSL-VPN, RSA Encryption Algorithm Functionality,
Mathematical Evaluation of Encryption and Decryption,
Example of RSA Encryption and Decryption, The Extended
Euclidean Algorithm Definition, Practical Protection
Illustration and Secureness of RSA, Key Creation and
Exchange, Hashing Methodology with HMAC of SSL-VPN,
C on c lu sio n .
I. INTRODUCTION
This report illustrated how to function RSA Algorithm using
evaluating, the true pattern of encryption and decryption in
SSL based VPN mechanisms. The major risk is to delivering
keys amount sender and receiver sides by protecting cyber-
attacks, therefore the public key cryptography mechanism
came into the
seen, the whatever data have been encrypted by public key
can possible to decrypted only applying receiver side private
key to
obtain the real massage [1]. There is way to send the session
key using digital locker called envelope with special
technology such as either Diffie-Hellman or Elliptic Curve
methodology. the public key technology take place to generate
a sheared key, which is only correspondents allowed to create
certain secret
value where can use used act as session key. Mainly in Public
key cryptography support to overcome key distribution
difficulties and this methodology focused on two main
cryptography critical issues, authentication and nonrepudiation
over secured tunnel. Data and Identity sections are protected [2].
with someone who need authentication over the electronic world,
and at the other hand nonrepudiation prevents on unknown
peoples, Therefore the digital signature was came into the
operation to mitigate issues of above mentioned circumstance.
Figure 1: SSL Operation Illustration.
SSL-VPN (Secure Socket Layer Virtual Private Network)
Systems are mainly used to interconnected between one or
more private endpoints by encrypting internet traffics towards
into the protected tunnel, also that very impossible to make
eavesdropping attacks theoretically [3]. none application based
tunneling grants to established a tunnel in between two or more
geographical sites, that allowed one LAN network to
intercommunicate with another LAN network over wider range
of accessibility.
SSL-VPN is factorized on RSA Algorithm. The RSA algorithm
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
created on difficultness of factorizing with large prime
numbers by the nature, this system mainly works on private
and public key architecture system, also the public key is
available for everyone who ready to communicate with the
certain person, Using the RSA algorithm, the user can encrypt
with public key but it does not allow to decrypt the back
again using the public key [4]. because the there is only one
person who can decrypt with private key called owner, at the
other hand, it is very difficult to generate the key wanted for
decryption from the public key, that is why the RSA
algorithm is very famous among the other data encryption
protocols as well.
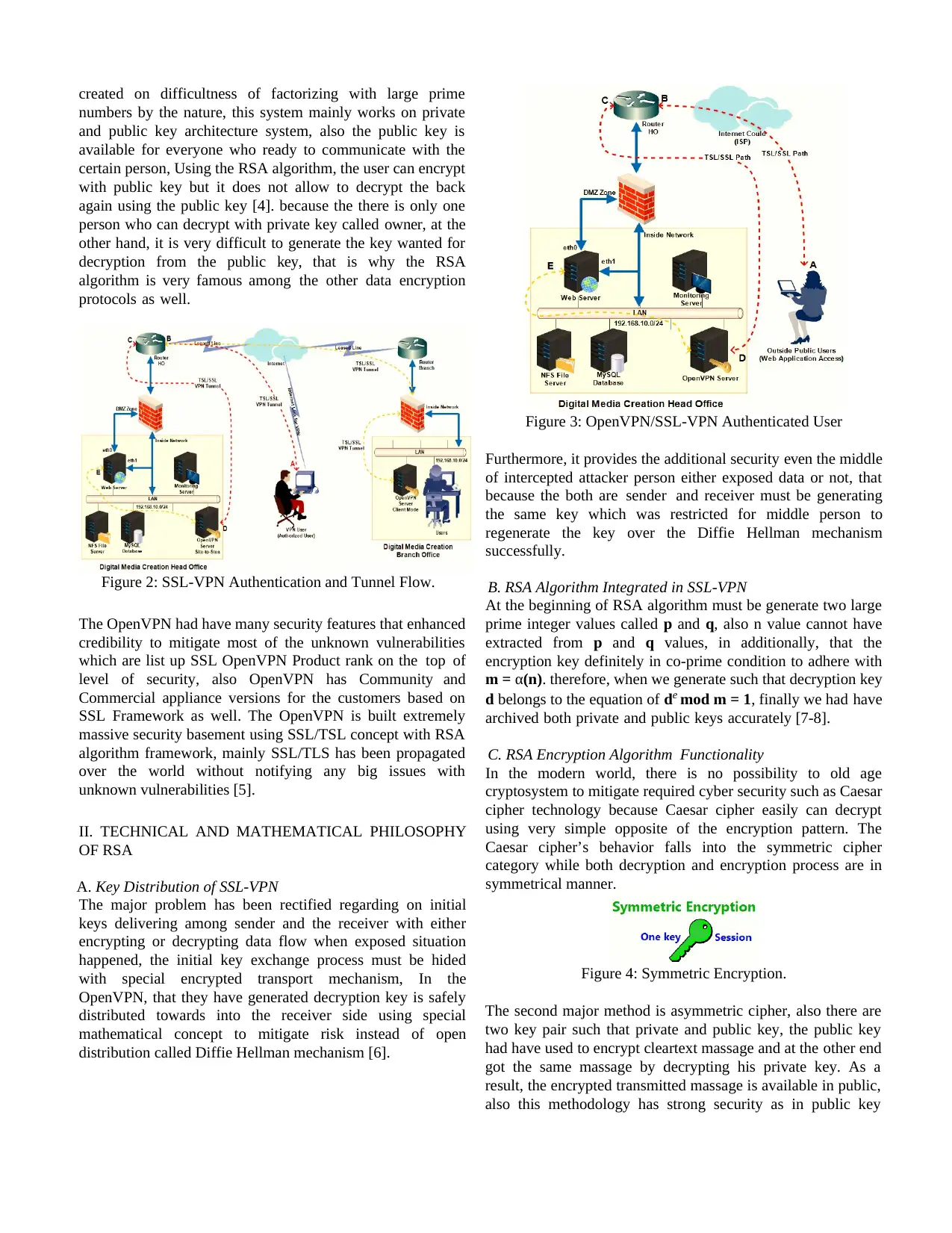
Figure 2: SSL-VPN Authentication and Tunnel Flow.
The OpenVPN had have many security features that enhanced
credibility to mitigate most of the unknown vulnerabilities
which are list up SSL OpenVPN Product rank on the top of
level of security, also OpenVPN has Community and
Commercial appliance versions for the customers based on
SSL Framework as well. The OpenVPN is built extremely
massive security basement using SSL/TSL concept with RSA
algorithm framework, mainly SSL/TLS has been propagated
over the world without notifying any big issues with
unknown vulnerabilities [5].
II. TECHNICAL AND MATHEMATICAL PHILOSOPHY
OF RSA
A. Key Distribution of SSL-VPN
The major problem has been rectified regarding on initial
keys delivering among sender and the receiver with either
encrypting or decrypting data flow when exposed situation
happened, the initial key exchange process must be hided
with special encrypted transport mechanism, In the
OpenVPN, that they have generated decryption key is safely
distributed towards into the receiver side using special
mathematical concept to mitigate risk instead of open
distribution called Diffie Hellman mechanism [6].
Figure 3: OpenVPN/SSL-VPN Authenticated User
Furthermore, it provides the additional security even the middle
of intercepted attacker person either exposed data or not, that
because the both are sender and receiver must be generating
the same key which was restricted for middle person to
regenerate the key over the Diffie Hellman mechanism
successfully.
B. RSA Algorithm Integrated in SSL-VPN
At the beginning of RSA algorithm must be generate two large
prime integer values called p and q, also n value cannot have
extracted from p and q values, in additionally, that the
encryption key definitely in co-prime condition to adhere with
m = α(n). therefore, when we generate such that decryption key
d belongs to the equation of de mod m = 1, finally we had have
archived both private and public keys accurately [7-8].
C. RSA Encryption Algorithm Functionality
In the modern world, there is no possibility to old age
cryptosystem to mitigate required cyber security such as Caesar
cipher technology because Caesar cipher easily can decrypt
using very simple opposite of the encryption pattern. The
Caesar cipher’s behavior falls into the symmetric cipher
category while both decryption and encryption process are in
symmetrical manner.
Figure 4: Symmetric Encryption.
The second major method is asymmetric cipher, also there are
two key pair such that private and public key, the public key
had have used to encrypt cleartext massage and at the other end
got the same massage by decrypting his private key. As a
result, the encrypted transmitted massage is available in public,
also this methodology has strong security as in public key
numbers by the nature, this system mainly works on private
and public key architecture system, also the public key is
available for everyone who ready to communicate with the
certain person, Using the RSA algorithm, the user can encrypt
with public key but it does not allow to decrypt the back
again using the public key [4]. because the there is only one
person who can decrypt with private key called owner, at the
other hand, it is very difficult to generate the key wanted for
decryption from the public key, that is why the RSA
algorithm is very famous among the other data encryption
protocols as well.
Figure 2: SSL-VPN Authentication and Tunnel Flow.
The OpenVPN had have many security features that enhanced
credibility to mitigate most of the unknown vulnerabilities
which are list up SSL OpenVPN Product rank on the top of
level of security, also OpenVPN has Community and
Commercial appliance versions for the customers based on
SSL Framework as well. The OpenVPN is built extremely
massive security basement using SSL/TSL concept with RSA
algorithm framework, mainly SSL/TLS has been propagated
over the world without notifying any big issues with
unknown vulnerabilities [5].
II. TECHNICAL AND MATHEMATICAL PHILOSOPHY
OF RSA
A. Key Distribution of SSL-VPN
The major problem has been rectified regarding on initial
keys delivering among sender and the receiver with either
encrypting or decrypting data flow when exposed situation
happened, the initial key exchange process must be hided
with special encrypted transport mechanism, In the
OpenVPN, that they have generated decryption key is safely
distributed towards into the receiver side using special
mathematical concept to mitigate risk instead of open
distribution called Diffie Hellman mechanism [6].
Figure 3: OpenVPN/SSL-VPN Authenticated User
Furthermore, it provides the additional security even the middle
of intercepted attacker person either exposed data or not, that
because the both are sender and receiver must be generating
the same key which was restricted for middle person to
regenerate the key over the Diffie Hellman mechanism
successfully.
B. RSA Algorithm Integrated in SSL-VPN
At the beginning of RSA algorithm must be generate two large
prime integer values called p and q, also n value cannot have
extracted from p and q values, in additionally, that the
encryption key definitely in co-prime condition to adhere with
m = α(n). therefore, when we generate such that decryption key
d belongs to the equation of de mod m = 1, finally we had have
archived both private and public keys accurately [7-8].
C. RSA Encryption Algorithm Functionality
In the modern world, there is no possibility to old age
cryptosystem to mitigate required cyber security such as Caesar
cipher technology because Caesar cipher easily can decrypt
using very simple opposite of the encryption pattern. The
Caesar cipher’s behavior falls into the symmetric cipher
category while both decryption and encryption process are in
symmetrical manner.
Figure 4: Symmetric Encryption.
The second major method is asymmetric cipher, also there are
two key pair such that private and public key, the public key
had have used to encrypt cleartext massage and at the other end
got the same massage by decrypting his private key. As a
result, the encrypted transmitted massage is available in public,
also this methodology has strong security as in public key

encryption category.
Figure 5: Asymmetric Encryption.
The RSA encryption methodology specially based on some
special properties of prime numbers. The Known sample
prime numbers are such as 2, 3, 5, 7, . . .etc., are categorized
into the special prime numbers which are greater than 1 and
further expression also impossible as a natural smaller
number, also a prime integer number is a natural vale greater
than one and including only positive factors. In additionally
every natural integer which are greater than one can
factorized into a product of each prime numbers [9].
Furthermore, that there are infinitely most of prime numbers.
Using a computer, it is relatively easy to find lots of large
prime numbers. At present, however, it is much difficult to
find the prime number factorization of a very large number.
This is what makes RSA encryption so hard to crack [10]. It
is much difficult to reevaluate factorization of a very large
prime either integer or number, also that special enhanced
property take place the strength of anti-crack situation.
Simply that feature lift up RSA encryption methodology
which is very difficult to crack by cyber-attack.
Figure 6: SSL Tunnel.
D. Mathematical Evaluation of Encryption and Decryption
The major component of RSA can be classified such as n, e
and d and recommended for choosing two very large primes.
Second step is to calculate ϕ, in additionally to choosing
exponents values on e and d.
Formula for n is n = p * q
So, calculate ϕ using Euler Totient Function as follows,
Formula for ϕ is x ϕ mod =1
Therefore ϕ = (p-1) (q-1) must be evaluated [11].
Where ϕ must not shear a factor with e Choosing component
e and d and it must be small e, greater than 2, let e =3.
Therefore, the valve of d need to evaluate (Inverse of e mode
ϕ).
e * d mod ϕ = 1, so p = 5, q = 1, e = 7.
therefore n = p * q =>55 and ϕ = (p-1) (q-1) =>40.
When p = 5, q = 11, e = 7, n = 55, ϕ = 40 and d =?
Got the equation 7 * d mod 40 = 1
RSA Calculation Steps:
Step 1
φ = 0, e = 7
40 / 7 = 5
φ = 40, e = 1
40/1 = 40
Step 2
40
5 * 7 = 35
40
5 * 1 = 5
Step 3
40
7
(40-35) = 5
40
1
(40-5) = 35
Step 4
7
5
(7-5) = 2
1
35
(1-35) = -34
Step 5
7
5
2
1
35
-34 mod 40
Step 6
5 divides
2 is equal to 2
35
6
Step 7
5
2 * 2 = 4
35
6
Step 8
5
2
(5 – 4) = 1
35
6
(35 -12) = 23 = d
Table 1: RSA Calculations.
According to the answers evaluated from qauation has been
found the Pubic key and Private key So, p =5, q =11, e = 7,
n = 55, φ = 40, d = 23 and it said 7 * 23 mod 40 = 1
Therefore the commopnenet of the Public key are e = 7,
n = 53 with the component of Private key d = 23.
E. Security Clarifications and Conditions of RSA Algorithm
The RSA Algorithm had used exponential mathematical
expressions on whole concept, the plaintext is always chunk
into blocks including binary values as n. in additionally the
chunked block size must be either less than or equal to the
log2(n). The Encryption and Decryption forms are included
with plaintext block M with ciphertext block called C as
follows,
C = Me mod n
M = Cd mod n = (Me )d mod n = Med mod n
Therefore, the both of sender and receiver (Bob and Alice)
must be known the valve of n, also the sender already knows
the certain value of e, in additionally receiver also known the
Figure 5: Asymmetric Encryption.
The RSA encryption methodology specially based on some
special properties of prime numbers. The Known sample
prime numbers are such as 2, 3, 5, 7, . . .etc., are categorized
into the special prime numbers which are greater than 1 and
further expression also impossible as a natural smaller
number, also a prime integer number is a natural vale greater
than one and including only positive factors. In additionally
every natural integer which are greater than one can
factorized into a product of each prime numbers [9].
Furthermore, that there are infinitely most of prime numbers.
Using a computer, it is relatively easy to find lots of large
prime numbers. At present, however, it is much difficult to
find the prime number factorization of a very large number.
This is what makes RSA encryption so hard to crack [10]. It
is much difficult to reevaluate factorization of a very large
prime either integer or number, also that special enhanced
property take place the strength of anti-crack situation.
Simply that feature lift up RSA encryption methodology
which is very difficult to crack by cyber-attack.
Figure 6: SSL Tunnel.
D. Mathematical Evaluation of Encryption and Decryption
The major component of RSA can be classified such as n, e
and d and recommended for choosing two very large primes.
Second step is to calculate ϕ, in additionally to choosing
exponents values on e and d.
Formula for n is n = p * q
So, calculate ϕ using Euler Totient Function as follows,
Formula for ϕ is x ϕ mod =1
Therefore ϕ = (p-1) (q-1) must be evaluated [11].
Where ϕ must not shear a factor with e Choosing component
e and d and it must be small e, greater than 2, let e =3.
Therefore, the valve of d need to evaluate (Inverse of e mode
ϕ).
e * d mod ϕ = 1, so p = 5, q = 1, e = 7.
therefore n = p * q =>55 and ϕ = (p-1) (q-1) =>40.
When p = 5, q = 11, e = 7, n = 55, ϕ = 40 and d =?
Got the equation 7 * d mod 40 = 1
RSA Calculation Steps:
Step 1
φ = 0, e = 7
40 / 7 = 5
φ = 40, e = 1
40/1 = 40
Step 2
40
5 * 7 = 35
40
5 * 1 = 5
Step 3
40
7
(40-35) = 5
40
1
(40-5) = 35
Step 4
7
5
(7-5) = 2
1
35
(1-35) = -34
Step 5
7
5
2
1
35
-34 mod 40
Step 6
5 divides
2 is equal to 2
35
6
Step 7
5
2 * 2 = 4
35
6
Step 8
5
2
(5 – 4) = 1
35
6
(35 -12) = 23 = d
Table 1: RSA Calculations.
According to the answers evaluated from qauation has been
found the Pubic key and Private key So, p =5, q =11, e = 7,
n = 55, φ = 40, d = 23 and it said 7 * 23 mod 40 = 1
Therefore the commopnenet of the Public key are e = 7,
n = 53 with the component of Private key d = 23.
E. Security Clarifications and Conditions of RSA Algorithm
The RSA Algorithm had used exponential mathematical
expressions on whole concept, the plaintext is always chunk
into blocks including binary values as n. in additionally the
chunked block size must be either less than or equal to the
log2(n). The Encryption and Decryption forms are included
with plaintext block M with ciphertext block called C as
follows,
C = Me mod n
M = Cd mod n = (Me )d mod n = Med mod n
Therefore, the both of sender and receiver (Bob and Alice)
must be known the valve of n, also the sender already knows
the certain value of e, in additionally receiver also known the
valve of d to initialized the message flow [12]. As a result, the
above scenario called public key encryption having the
private key d, n and public key e, n.
F. The Extended Euclidean Algorithm Definition
The Euclidean algorithm is the major active methodology in
RSA algorithm, The RSA algorithm used integers a and b in
the extended Euclidean algorithm to calculate greatest
common divisor (GCD Values), by satisfying, that there are
two additional integers x and y into the equation [13].
ax + by = d
Therefore d = gcd (a, b)
G. Practical Protection Illustration and Secureness of RSA
Most peoples who specialized and realistic cryptanalyst
asking, is that RSA algorithm strongly enough in front of
cyber-attack. Actually, specialized cryptanalyst can harmful
partially on RSA algorithm using super computer cluster
but not accurately possible to do that, brute-force attacker
sometime gets a chance to crack the massage, but it does
not mean that the entire encryption scheme possible to
exposed.
Figure 7: Illustration of Avoid middle attacker attempts.
In additionally, the other hand probabilistic approach scenario
will take a change to obtain a one key from out of million,
m o s t of the time it is very differ to say that the RSA
algorithm is breakable without proven evidence. Therefore,
the RSA algorithm strongly protected from cyber-attacks.
As a result, The Hash integrity check has been implemented
to verify integrity of original sender’s message content, also
digital signature also in an operation to verify total
protection of the encrypted tunnel. According to the above
image, the middle attacker was failing to obtain e vale and
finally it’s become false attack.
According to the above image, to prove how RSA
algorithm strongly enough when a cryptanalyst attacker
obtaining decryption key from the public key where
generated, and the attacker is trying to intruder in order to
steal the certain decryption key.
Therefore, to take care of attack from threat assets, that they
need strong physical security, that’s why some encryption
devices, must be separated from rest of the critical IT assets
which are related to RSA algorithm mechanism, also it must
generate decryption and encryption key pair and does not
printout decryption key, even when the owner requested.
Finally, administration IT security professional will delete the
decryption key when they sense abnormal attempts for intrusion
if occurred.
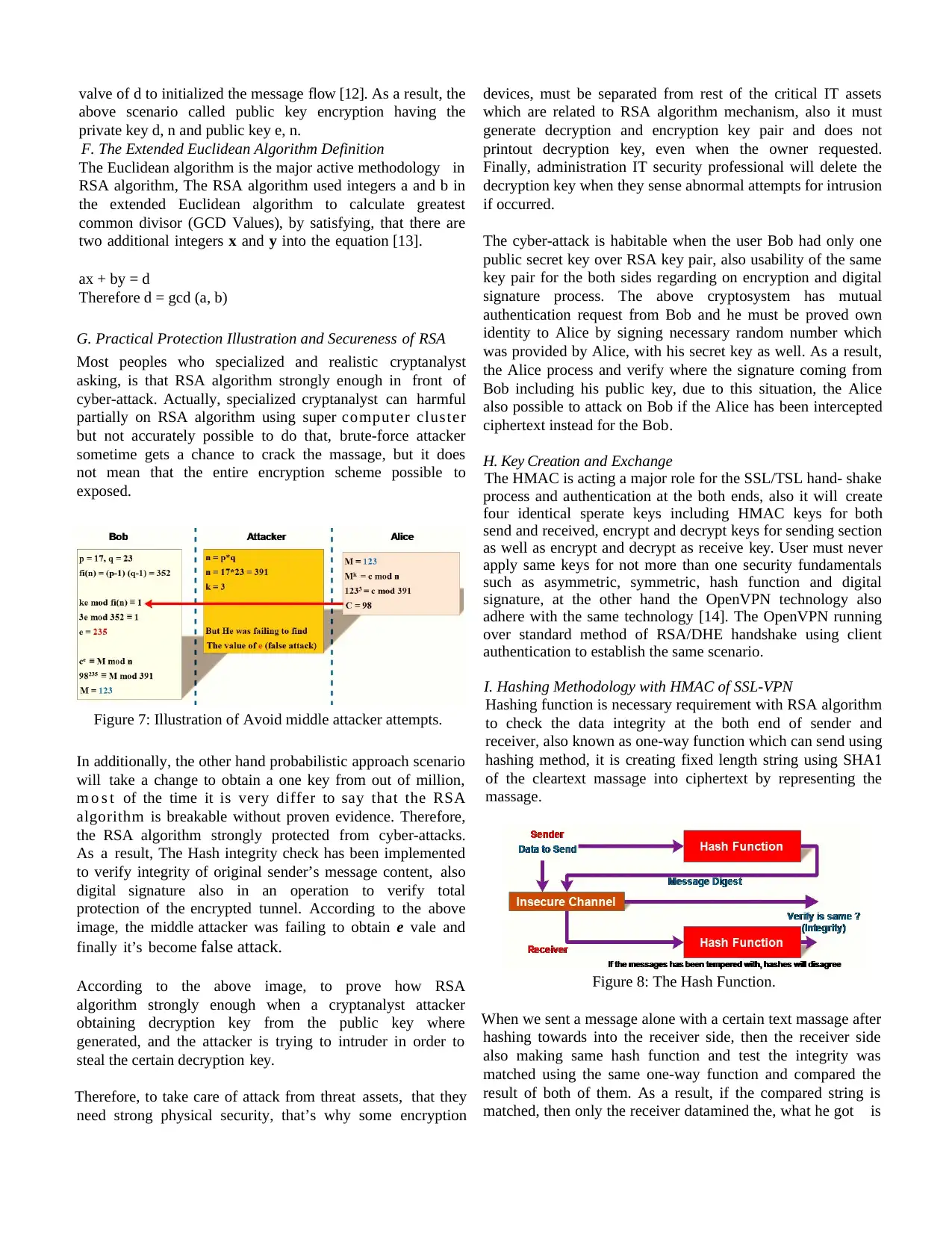
The cyber-attack is habitable when the user Bob had only one
public secret key over RSA key pair, also usability of the same
key pair for the both sides regarding on encryption and digital
signature process. The above cryptosystem has mutual
authentication request from Bob and he must be proved own
identity to Alice by signing necessary random number which
was provided by Alice, with his secret key as well. As a result,
the Alice process and verify where the signature coming from
Bob including his public key, due to this situation, the Alice
also possible to attack on Bob if the Alice has been intercepted
ciphertext instead for the Bob.
H. Key Creation and Exchange
The HMAC is acting a major role for the SSL/TSL hand- shake
process and authentication at the both ends, also it will create
four identical sperate keys including HMAC keys for both
send and received, encrypt and decrypt keys for sending section
as well as encrypt and decrypt as receive key. User must never
apply same keys for not more than one security fundamentals
such as asymmetric, symmetric, hash function and digital
signature, at the other hand the OpenVPN technology also
adhere with the same technology [14]. The OpenVPN running
over standard method of RSA/DHE handshake using client
authentication to establish the same scenario.
I. Hashing Methodology with HMAC of SSL-VPN
Hashing function is necessary requirement with RSA algorithm
to check the data integrity at the both end of sender and
receiver, also known as one-way function which can send using
hashing method, it is creating fixed length string using SHA1
of the cleartext massage into ciphertext by representing the
massage.
Figure 8: The Hash Function.
When we sent a message alone with a certain text massage after
hashing towards into the receiver side, then the receiver side
also making same hash function and test the integrity was
matched using the same one-way function and compared the
result of both of them. As a result, if the compared string is
matched, then only the receiver datamined the, what he got is
above scenario called public key encryption having the
private key d, n and public key e, n.
F. The Extended Euclidean Algorithm Definition
The Euclidean algorithm is the major active methodology in
RSA algorithm, The RSA algorithm used integers a and b in
the extended Euclidean algorithm to calculate greatest
common divisor (GCD Values), by satisfying, that there are
two additional integers x and y into the equation [13].
ax + by = d
Therefore d = gcd (a, b)
G. Practical Protection Illustration and Secureness of RSA
Most peoples who specialized and realistic cryptanalyst
asking, is that RSA algorithm strongly enough in front of
cyber-attack. Actually, specialized cryptanalyst can harmful
partially on RSA algorithm using super computer cluster
but not accurately possible to do that, brute-force attacker
sometime gets a chance to crack the massage, but it does
not mean that the entire encryption scheme possible to
exposed.
Figure 7: Illustration of Avoid middle attacker attempts.
In additionally, the other hand probabilistic approach scenario
will take a change to obtain a one key from out of million,
m o s t of the time it is very differ to say that the RSA
algorithm is breakable without proven evidence. Therefore,
the RSA algorithm strongly protected from cyber-attacks.
As a result, The Hash integrity check has been implemented
to verify integrity of original sender’s message content, also
digital signature also in an operation to verify total
protection of the encrypted tunnel. According to the above
image, the middle attacker was failing to obtain e vale and
finally it’s become false attack.
According to the above image, to prove how RSA
algorithm strongly enough when a cryptanalyst attacker
obtaining decryption key from the public key where
generated, and the attacker is trying to intruder in order to
steal the certain decryption key.
Therefore, to take care of attack from threat assets, that they
need strong physical security, that’s why some encryption
devices, must be separated from rest of the critical IT assets
which are related to RSA algorithm mechanism, also it must
generate decryption and encryption key pair and does not
printout decryption key, even when the owner requested.
Finally, administration IT security professional will delete the
decryption key when they sense abnormal attempts for intrusion
if occurred.
The cyber-attack is habitable when the user Bob had only one
public secret key over RSA key pair, also usability of the same
key pair for the both sides regarding on encryption and digital
signature process. The above cryptosystem has mutual
authentication request from Bob and he must be proved own
identity to Alice by signing necessary random number which
was provided by Alice, with his secret key as well. As a result,
the Alice process and verify where the signature coming from
Bob including his public key, due to this situation, the Alice
also possible to attack on Bob if the Alice has been intercepted
ciphertext instead for the Bob.
H. Key Creation and Exchange
The HMAC is acting a major role for the SSL/TSL hand- shake
process and authentication at the both ends, also it will create
four identical sperate keys including HMAC keys for both
send and received, encrypt and decrypt keys for sending section
as well as encrypt and decrypt as receive key. User must never
apply same keys for not more than one security fundamentals
such as asymmetric, symmetric, hash function and digital
signature, at the other hand the OpenVPN technology also
adhere with the same technology [14]. The OpenVPN running
over standard method of RSA/DHE handshake using client
authentication to establish the same scenario.
I. Hashing Methodology with HMAC of SSL-VPN
Hashing function is necessary requirement with RSA algorithm
to check the data integrity at the both end of sender and
receiver, also known as one-way function which can send using
hashing method, it is creating fixed length string using SHA1
of the cleartext massage into ciphertext by representing the
massage.
Figure 8: The Hash Function.
When we sent a message alone with a certain text massage after
hashing towards into the receiver side, then the receiver side
also making same hash function and test the integrity was
matched using the same one-way function and compared the
result of both of them. As a result, if the compared string is
matched, then only the receiver datamined the, what he got is
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
correct content from the proper route path called checking
data integrity of a RSA based crypto system.
In Specifically, a cryptanalyst cyber attacker just removing
hash valve what the sender transmitted towards into the
receiver as the man in middle attacker, also an attacker
modifying the content of the message with embodying new
hash strings into them. To mitigate this situation HMAC has
been introduced, therefore before inject the certain message
through the one-way function, at the initially must be included
secret key in front of the content. The key is fully hashes
independently with message section to mitigate hash valve
modifying attack using HMAC.
Figure 9: Hash Function with HMAC Illustration.
As a result, the transmitted message is received by the receiver
the destination end of the tunnel, the content of the message is
opened by receiver. The attached HMAC key is in the in-front
of message, in additionally the same HMAC key must be
exchanged between the receiver and sender through Diffie-
Hellman methodology. But when the cryptanalyst cyber
attacker has changed the message content with new hashes,
that because both sender and receiver are well known their
original HMAC hash key [15]. Finally, they can have
identified, the receiver message was not coming from the
original sender and reject it.
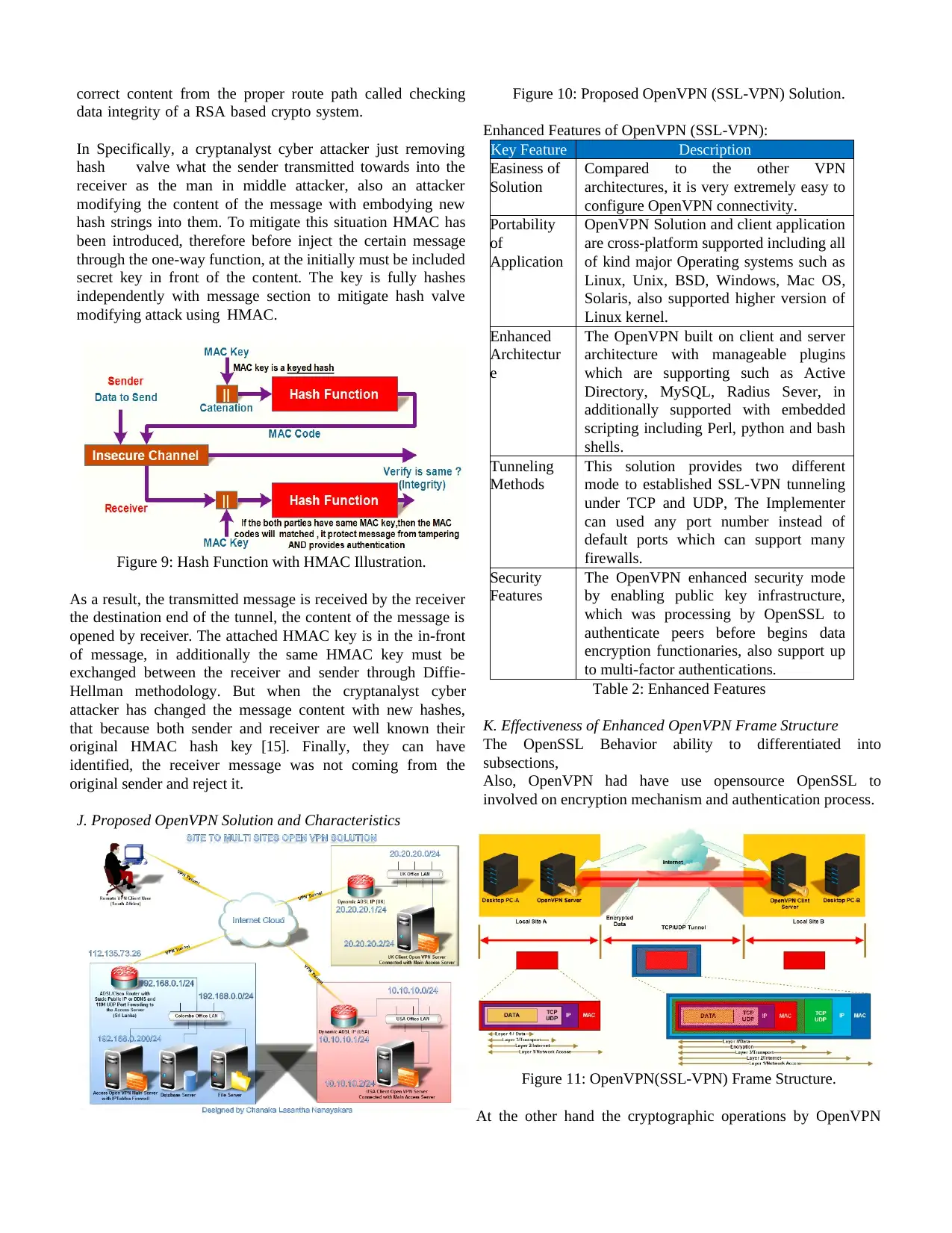
J. Proposed OpenVPN Solution and Characteristics
Figure 10: Proposed OpenVPN (SSL-VPN) Solution.
Enhanced Features of OpenVPN (SSL-VPN):
Key Feature Description
Easiness of
Solution
Compared to the other VPN
architectures, it is very extremely easy to
configure OpenVPN connectivity.
Portability
of
Application
OpenVPN Solution and client application
are cross-platform supported including all
of kind major Operating systems such as
Linux, Unix, BSD, Windows, Mac OS,
Solaris, also supported higher version of
Linux kernel.
Enhanced
Architectur
e
The OpenVPN built on client and server
architecture with manageable plugins
which are supporting such as Active
Directory, MySQL, Radius Sever, in
additionally supported with embedded
scripting including Perl, python and bash
shells.
Tunneling
Methods
This solution provides two different
mode to established SSL-VPN tunneling
under TCP and UDP, The Implementer
can used any port number instead of
default ports which can support many
firewalls.
Security
Features
The OpenVPN enhanced security mode
by enabling public key infrastructure,
which was processing by OpenSSL to
authenticate peers before begins data
encryption functionaries, also support up
to multi-factor authentications.
Table 2: Enhanced Features
K. Effectiveness of Enhanced OpenVPN Frame Structure
The OpenSSL Behavior ability to differentiated into
subsections,
Also, OpenVPN had have use opensource OpenSSL to
involved on encryption mechanism and authentication process.
Figure 11: OpenVPN(SSL-VPN) Frame Structure.
At the other hand the cryptographic operations by OpenVPN
data integrity of a RSA based crypto system.
In Specifically, a cryptanalyst cyber attacker just removing
hash valve what the sender transmitted towards into the
receiver as the man in middle attacker, also an attacker
modifying the content of the message with embodying new
hash strings into them. To mitigate this situation HMAC has
been introduced, therefore before inject the certain message
through the one-way function, at the initially must be included
secret key in front of the content. The key is fully hashes
independently with message section to mitigate hash valve
modifying attack using HMAC.
Figure 9: Hash Function with HMAC Illustration.
As a result, the transmitted message is received by the receiver
the destination end of the tunnel, the content of the message is
opened by receiver. The attached HMAC key is in the in-front
of message, in additionally the same HMAC key must be
exchanged between the receiver and sender through Diffie-
Hellman methodology. But when the cryptanalyst cyber
attacker has changed the message content with new hashes,
that because both sender and receiver are well known their
original HMAC hash key [15]. Finally, they can have
identified, the receiver message was not coming from the
original sender and reject it.
J. Proposed OpenVPN Solution and Characteristics
Figure 10: Proposed OpenVPN (SSL-VPN) Solution.
Enhanced Features of OpenVPN (SSL-VPN):
Key Feature Description
Easiness of
Solution
Compared to the other VPN
architectures, it is very extremely easy to
configure OpenVPN connectivity.
Portability
of
Application
OpenVPN Solution and client application
are cross-platform supported including all
of kind major Operating systems such as
Linux, Unix, BSD, Windows, Mac OS,
Solaris, also supported higher version of
Linux kernel.
Enhanced
Architectur
e
The OpenVPN built on client and server
architecture with manageable plugins
which are supporting such as Active
Directory, MySQL, Radius Sever, in
additionally supported with embedded
scripting including Perl, python and bash
shells.
Tunneling
Methods
This solution provides two different
mode to established SSL-VPN tunneling
under TCP and UDP, The Implementer
can used any port number instead of
default ports which can support many
firewalls.
Security
Features
The OpenVPN enhanced security mode
by enabling public key infrastructure,
which was processing by OpenSSL to
authenticate peers before begins data
encryption functionaries, also support up
to multi-factor authentications.
Table 2: Enhanced Features
K. Effectiveness of Enhanced OpenVPN Frame Structure
The OpenSSL Behavior ability to differentiated into
subsections,
Also, OpenVPN had have use opensource OpenSSL to
involved on encryption mechanism and authentication process.
Figure 11: OpenVPN(SSL-VPN) Frame Structure.
At the other hand the cryptographic operations by OpenVPN

architecture has wider range of algorithms including
Symmetric algorithms, x.509 based Certificates and HMAC
based Hash function [17].
III. CONCLUSION
RSA is a very strong encryption mechanism compared to
other algorithms, The RSA algorithm architecture with public
key cryptography system which allows secured tunnel inter
communication including Digital signature and it was
protected due to the nature of very difficult factorizing with
large numbers, also most of the experts recently trying to break
the algorithm but it was failed attempts to break RSA, due to
strong factorization techniques, in additionally no body have
been succeeded.
Therefore, the RSA algorithm bit slower compared with other
cryptographic systems. At the other hand RSA generally used
to securely transmitted, the required keys towards less secured
destination, but by the observation RSA is can categorized as
faster algorithm, but some issues are existing sometimes
potentially damage RSA security mechanism due to timing
attacks and few problems with initial key distribution
situations, in additionally the Diffie-Hellman algorithm is have
an ability to mitigate the mentions issue as well, also the only
drawback is such device implementing RSA had have much
more software and hardware based devices that can counter
either types of cyber-attacks or eavesdropping attacks.
There is a very major threat to the RSA by the solution of
Riemann hypothesis, but since that Riemann hypothesis did not
proven the ability or not. The current development process of
Riemann hypothesis relatively stagnant concept. However,
when if the Riemann hypothesis were found, then the RSA
algorithm can be brake easily by exposing prime number of the
algorithm architecture [16]. Since few years back, some
experts’ mathematicians who recently inventing extended
versions theory and cryptanalysis of RSA algorithm instead of
existing RSA mechanism to face cyber treats will be coming in
future time.
REFERENCES
[1] W.K. Chen, SSL & TLS Essentials. Danvers, Canada:
Jhon Willy & Sons, 2000, pp. 39-40.
[2] S. Thomas. SSL & TLS Essentials. Danvers, Canada:
Jhon Willy & Sons, 2000, pp. 164-165.
[3] OpenVPN LTD, "Does OpenVPN support IPSec or
PPTP," openvpn.net, para. 1, AUG. 28, 2017. [Online].
Available: https://openvpn.net/index.php/open-source/339-
why-ssl-vpn.html. [Accessed: Nov. 10, 2017].
[4] S. Thomas. SSL & TLS Essentials. Danvers, Canada:
Jhon Willy & Sons, 2000, pp. 168-171.
[5] OpenVPN LTD, "Introduction to OpenVPN,"
openvpn.net, para. 8-25, AUG. 28, 2004. [Online]. Available:
https://openvpn.net/papers/openvpn-101.pdf. [Accessed: Nov.
11, 2017].
[6] Cisco Systems Inc, "Sockets Layer (SSL) VPN
Technology Overview," cisco.com, para. 2-8, March. 31,
2008. [Online]. Available:
https://www.cisco.com/c/dam/en/us/products/collateral/securit
y/ios-sslvpn/IOS_SSL_VPN_TDM_v8-jz-an.pdf. [Accessed:
Nov. 11, 2017].
[7] OpenVPN LTD, "Introduction to OpenVPN,"
openvpn.net, para. 1-10, AUG. 28, 2004. [Online]. Available:
https://openvpn.net/papers/openvpn-101.pdf. [Accessed: Nov.
11, 2017].
[8] S. Burnett, and S. Paine, RSA Security’s Official Guide to
Cryptography. Osborne, United States: McGraw-Hill
Companies, 2001, pp. 121-124.
[9] M. Evans, RSA Encryption. Melbourne, Australia: La
Trobe University, 2011, pp. 4-5.
[10] H. Delfs, and H. Knebl, Introduction to Cryptography
Principles and Applications. Nürnberg, Germany: Technische
Hochschule Nürnberg, 2015, pp. 58-60.
[11] S. Burnett, and S. Paine, RSA Security’s Official Guide
to Cryptography. Osborne, United States: McGraw-Hill
Companies, 2001, pp. 121-128.
[12] W. Stalling, Cryptography and Network Security
Principles and Practice. Upper Saddle River, USA: Pearson
Education, 2014, pp. 265.
[13] B. Preneel, Understanding Cryptography. Berlin,
Germany: Springer LTD, 2010, pp. 171-177.
[14] B. Preneel, Understanding Cryptography. Berlin,
Germany: Springer LTD, 2010, pp. 332-336.
[15] W. Stalling, Cryptography and Network Security
Principles and Practice. Upper Saddle River, USA: Pearson
Education, 2014, pp. 369-371.
[16] W. Stalling, Cryptography and Network Security
Principles and Practice. Upper Saddle River, USA: Pearson
Education, 2014, pp. 372.
[17] OSTIF Org, "OpenVPN 2.4.0 Security Assessment,"
ostif.org, para. 7-43, MAY. 10, 2017. [Online]. Available:
https://ostif.org/wp-content/uploads/2017/05/OpenVPN1.2fin
al.pdf. [Accessed: Nov. 15, 2017].
Symmetric algorithms, x.509 based Certificates and HMAC
based Hash function [17].
III. CONCLUSION
RSA is a very strong encryption mechanism compared to
other algorithms, The RSA algorithm architecture with public
key cryptography system which allows secured tunnel inter
communication including Digital signature and it was
protected due to the nature of very difficult factorizing with
large numbers, also most of the experts recently trying to break
the algorithm but it was failed attempts to break RSA, due to
strong factorization techniques, in additionally no body have
been succeeded.
Therefore, the RSA algorithm bit slower compared with other
cryptographic systems. At the other hand RSA generally used
to securely transmitted, the required keys towards less secured
destination, but by the observation RSA is can categorized as
faster algorithm, but some issues are existing sometimes
potentially damage RSA security mechanism due to timing
attacks and few problems with initial key distribution
situations, in additionally the Diffie-Hellman algorithm is have
an ability to mitigate the mentions issue as well, also the only
drawback is such device implementing RSA had have much
more software and hardware based devices that can counter
either types of cyber-attacks or eavesdropping attacks.
There is a very major threat to the RSA by the solution of
Riemann hypothesis, but since that Riemann hypothesis did not
proven the ability or not. The current development process of
Riemann hypothesis relatively stagnant concept. However,
when if the Riemann hypothesis were found, then the RSA
algorithm can be brake easily by exposing prime number of the
algorithm architecture [16]. Since few years back, some
experts’ mathematicians who recently inventing extended
versions theory and cryptanalysis of RSA algorithm instead of
existing RSA mechanism to face cyber treats will be coming in
future time.
REFERENCES
[1] W.K. Chen, SSL & TLS Essentials. Danvers, Canada:
Jhon Willy & Sons, 2000, pp. 39-40.
[2] S. Thomas. SSL & TLS Essentials. Danvers, Canada:
Jhon Willy & Sons, 2000, pp. 164-165.
[3] OpenVPN LTD, "Does OpenVPN support IPSec or
PPTP," openvpn.net, para. 1, AUG. 28, 2017. [Online].
Available: https://openvpn.net/index.php/open-source/339-
why-ssl-vpn.html. [Accessed: Nov. 10, 2017].
[4] S. Thomas. SSL & TLS Essentials. Danvers, Canada:
Jhon Willy & Sons, 2000, pp. 168-171.
[5] OpenVPN LTD, "Introduction to OpenVPN,"
openvpn.net, para. 8-25, AUG. 28, 2004. [Online]. Available:
https://openvpn.net/papers/openvpn-101.pdf. [Accessed: Nov.
11, 2017].
[6] Cisco Systems Inc, "Sockets Layer (SSL) VPN
Technology Overview," cisco.com, para. 2-8, March. 31,
2008. [Online]. Available:
https://www.cisco.com/c/dam/en/us/products/collateral/securit
y/ios-sslvpn/IOS_SSL_VPN_TDM_v8-jz-an.pdf. [Accessed:
Nov. 11, 2017].
[7] OpenVPN LTD, "Introduction to OpenVPN,"
openvpn.net, para. 1-10, AUG. 28, 2004. [Online]. Available:
https://openvpn.net/papers/openvpn-101.pdf. [Accessed: Nov.
11, 2017].
[8] S. Burnett, and S. Paine, RSA Security’s Official Guide to
Cryptography. Osborne, United States: McGraw-Hill
Companies, 2001, pp. 121-124.
[9] M. Evans, RSA Encryption. Melbourne, Australia: La
Trobe University, 2011, pp. 4-5.
[10] H. Delfs, and H. Knebl, Introduction to Cryptography
Principles and Applications. Nürnberg, Germany: Technische
Hochschule Nürnberg, 2015, pp. 58-60.
[11] S. Burnett, and S. Paine, RSA Security’s Official Guide
to Cryptography. Osborne, United States: McGraw-Hill
Companies, 2001, pp. 121-128.
[12] W. Stalling, Cryptography and Network Security
Principles and Practice. Upper Saddle River, USA: Pearson
Education, 2014, pp. 265.
[13] B. Preneel, Understanding Cryptography. Berlin,
Germany: Springer LTD, 2010, pp. 171-177.
[14] B. Preneel, Understanding Cryptography. Berlin,
Germany: Springer LTD, 2010, pp. 332-336.
[15] W. Stalling, Cryptography and Network Security
Principles and Practice. Upper Saddle River, USA: Pearson
Education, 2014, pp. 369-371.
[16] W. Stalling, Cryptography and Network Security
Principles and Practice. Upper Saddle River, USA: Pearson
Education, 2014, pp. 372.
[17] OSTIF Org, "OpenVPN 2.4.0 Security Assessment,"
ostif.org, para. 7-43, MAY. 10, 2017. [Online]. Available:
https://ostif.org/wp-content/uploads/2017/05/OpenVPN1.2fin
al.pdf. [Accessed: Nov. 15, 2017].
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





