Engineering and Computing Master of Science
6 Pages4182 Words211 Views
Added on 2019-09-25
Engineering and Computing Master of Science
Added on 2019-09-25
ShareRelated Documents
RSA AlgorithmFunctionalities andMathematical Implementation OfSSL-VPN Architecture for Multimedia IndustryChanaka Lasantha NanayakakraFaculty of Science, Engineering and ComputingMaster of Science Network and Information SecurityKingston University UK, Student ID: K1658833chanaka.lasantha@gmail.comAbstract—The SSL VPN is the major technology in the currentVPN market as a one of the best technology under opensourceworld instead of compilated called OpenVPN. The Oldest IPSecVPN technology too complex for correctly implement as well lessof security strength weakness and expensiveness are the majornegative drawback of the IPSec VPN Technology. IPSec has toomany required optional parameters configurations to become tosecured working condition and since it was implemented bysome non-expert professions regarding on IPSec domain. Inadditionally IPSec preconfigured to operates over kernelworkspace by facilitating some of cybercriminal society tomistakenly allowed attack by exposing over catastrophic failure.OpenVPN is always avoiding the unwanted complexitycompared to IPSec VPN technology to taking SSL/TLSmechanism with cryptographic libraries provides much betterfunctionalities in simplest lightweight package successfully.OpenVPN is pioneeras real SSL VPN enforcer to other SSLVPN products byfacilitation the same operational functionalitiestowards into the IPSecsector. Therefore, the OpenVPN is basedon SSL/TSL concept into the reality of implementation, it alsobased on RSA Algorithm with Additional Technologies.Therefor the key concerned area isfocusedintotheRSAAlgorithm.INDEXTERMSIntroduction, Technical and Mathematical Philosophy ofRSA, Key Distribution of SSL-VPN, RSA Algorithm Integratedin SSL-VPN, RSA Encryption AlgorithmFunctionality,Mathematical Evaluation of Encryption and Decryption,Example of RSA Encryption and Decryption, The ExtendedEuclidean Algorithm Definition, Practical ProtectionIllustration and Secureness of RSA, Key Creation andExchange, Hashing Methodology with HMAC of SSL-VPN,Conclusion.I.INTRODUCTIONThisreportillustratedhowtofunctionRSAAlgorithmusingevaluating, the true pattern of encryption and decryption inSSL based VPN mechanisms. The major risk is to deliveringkeys amount sender and receiver sides by protecting cyber-attacks, therefore the public key cryptography mechanismcame into the seen, the whatever data have been encrypted by public keycan possible to decrypted only applying receiver side privatekey to obtain the real massage [1]. There is way to send the sessionkey using digital locker called envelope with specialtechnology such as either Diffie-Hellman or Elliptic Curvemethodology. the public key technology take place to generatea sheared key, which is only correspondents allowed to createcertain secret value where can use used act as session key. Mainly in Publickey cryptography support to overcome key distributiondifficulties and this methodology focused on two maincryptography critical issues, authentication and nonrepudiationover secured tunnel. Data and Identity sections are protected [2].with someone who need authentication over the electronicworld,andattheotherhandnonrepudiationprevents on unknownpeoples, Therefore the digital signature was came into theoperation to mitigate issues of above mentioned circumstance.Figure 1: SSL Operation Illustration.SSL-VPN (Secure Socket Layer Virtual Private Network)Systems are mainly used to interconnected between one ormore private endpoints by encrypting internet traffics towardsinto the protected tunnel, also that very impossible to makeeavesdropping attacks theoretically [3]. none application basedtunneling grants to established a tunnel in between two or moregeographical sites, that allowed one LAN networktointercommunicatewithanotherLANnetworkoverwiderrangeof accessibility.SSL-VPN is factorized on RSA Algorithm. The RSA algorithm

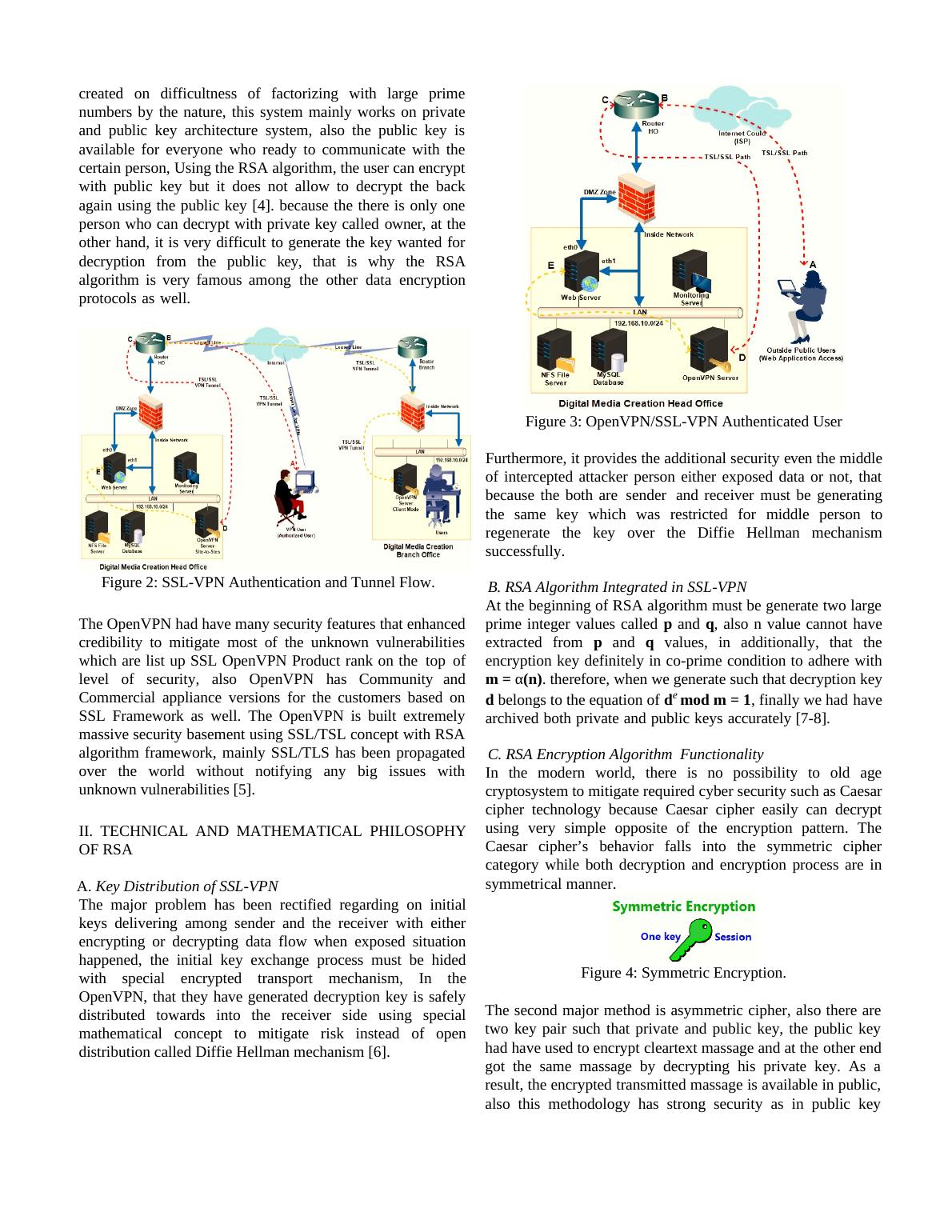
created on difficultness of factorizing with large primenumbers by the nature, this system mainly works on privateand public key architecture system, also the public key isavailable for everyone who ready to communicate with thecertain person, Using the RSA algorithm, the user can encryptwith public key but it does not allow to decrypt the backagain using the public key [4]. because the there is only oneperson who can decrypt with private key called owner, at theother hand, it is very difficult to generate the key wanted fordecryptionfrom the public key, that is why the RSAalgorithm is very famous amongtheotherdataencryptionprotocolsaswell.Figure 2: SSL-VPN Authentication and Tunnel Flow.The OpenVPN had have many security features that enhancedcredibility to mitigate most of the unknown vulnerabilitieswhich are list up SSL OpenVPN Product rank on thetopoflevelofsecurity,alsoOpenVPNhasCommunityandCommercial appliance versions for the customers based onSSL Framework as well. The OpenVPN is built extremelymassive security basement using SSL/TSL concept with RSAalgorithm framework, mainly SSL/TLS has been propagatedover the world without notifying any big issues withunknown vulnerabilities [5].II. TECHNICAL AND MATHEMATICAL PHILOSOPHYOF RSAA. Key Distribution of SSL-VPNThe major problem has been rectified regarding on initialkeys delivering among sender and the receiver with eitherencrypting or decrypting data flow when exposed situationhappened, the initial key exchange process must be hidedwith special encrypted transport mechanism, In theOpenVPN, that they have generated decryption key is safelydistributed towards into the receiver side using specialmathematical concept to mitigate risk instead of opendistribution called Diffie Hellman mechanism [6].Figure 3: OpenVPN/SSL-VPN Authenticated UserFurthermore, it provides the additional security even the middleof intercepted attacker person either exposed data or not, thatbecause the both aresenderandreceiver must be generatingthe same key which was restricted formiddlepersontoregeneratethekeyovertheDiffieHellman mechanismsuccessfully. B. RSA Algorithm Integrated in SSL-VPNAt the beginning of RSA algorithm must be generate two largeprime integer values called p and q, also n value cannot haveextracted from p and q values, in additionally, that theencryption key definitely in co-prime condition to adhere withm = α(n). therefore, when we generate such that decryption keyd belongs to the equation of de mod m = 1, finally we hadhavearchivedbothprivateandpublickeysaccurately [7-8]. C. RSA Encryption AlgorithmFunctionalityIn the modern world, there is no possibility to old agecryptosystem to mitigate required cyber security such as Caesarcipher technology because Caesar cipher easily can decryptusing very simple opposite of the encryption pattern. TheCaesar cipher’s behavior falls into the symmetric ciphercategory while both decryption and encryption process are insymmetrical manner.Figure 4: Symmetric Encryption.The second major method is asymmetric cipher, also there aretwo key pair such that private and public key, the public keyhad have used to encrypt cleartext massage and at theother endgot the same massage by decrypting his private key. As aresult, the encrypted transmitted massage is available in public,also this methodology has strong security as in public key
encryption category.Figure 5: Asymmetric Encryption.The RSA encryption methodology specially based on somespecialpropertiesofprimenumbers.TheKnownsampleprime numbers are such as 2, 3, 5, 7, . . .etc., are categorizedinto the special prime numbers which are greater than 1 andfurther expression also impossible as a natural smallernumber, also a prime integer number is a natural vale greaterthan one and including only positive factors. In additionallyevery natural integerwhicharegreaterthanonecanfactorizedintoaproduct of each prime numbers [9].Furthermore, that there are infinitely most of prime numbers.Using a computer, it is relatively easy to find lots oflargeprimenumbers.Atpresent,however,itismuchdifficulttofind the prime number factorization of a very large number.This is what makes RSA encryption so hard to crack [10]. Itis much difficult to reevaluate factorization of a very largeprime either integer or number, also that special enhancedproperty take place the strength of anti-crack situation.Simply that feature lift up RSA encryption methodologywhich is very difficult to crack bycyber-attack.Figure 6: SSL Tunnel.D. Mathematical Evaluation of Encryption and DecryptionThe major component of RSA can be classified such as n, eand d and recommended for choosing two very large primes.Second step is to calculate φ, in additionally to choosingexponents values on e and d.Formula for n is n = p * q So, calculate φusing Euler Totient Function as follows,Formula for φ is x φ mod =1Therefore φ = (p-1) (q-1) must be evaluated [11].Where φ must not shear a factor with e Choosing componente and d and it must be small e, greater than 2, let e =3.Therefore, the valve of d need to evaluate (Inverse of e modeφ). e * d mod φ = 1, so p = 5, q = 1, e = 7. therefore n = p * q =>55 and φ = (p-1) (q-1)=>40.When p = 5, q = 11, e = 7, n = 55, φ = 40 and d =?Got the equation 7 * d mod 40 = 1RSA Calculation Steps:Step 1φ = 0, e = 740 / 7 = 5φ = 40, e = 140/1 = 40Step 2405 * 7 = 35405 * 1 = 5Step 3407(40-35) = 5401(40-5) = 35Step 475(7-5) = 2135(1-35) = -34Step 5752135-34 mod 40Step 65 divides2 is equal to 2356Step 752 * 2 = 4356Step 852(5 – 4) = 1356(35 -12) = 23 = dTable 1: RSA Calculations.According to the answers evaluated from qauation has been found the Pubic key and Private key So, p =5, q =11, e = 7,n = 55, φ = 40, d = 23 and it said 7 * 23 mod 40 = 1 Therefore the commopnenet of the Public key are e = 7, n = 53 with the component of Private key d = 23.E. Security Clarifications and Conditions ofRSAAlgorithmThe RSA Algorithm had usedexponential mathematicalexpressions on whole concept, the plaintext isalwayschunkintoblocksincludingbinaryvaluesasn.inadditionallythechunkedblocksizemustbeeitherlessthanorequaltothelog2(n). The Encryption and Decryption formsareincludedwith plaintextblockMwithciphertextblockcalledCasfollows,C = Me mod nM = Cd mod n = (Me )d mod n = Med mod nTherefore, the both of sender and receiver (Bob and Alice)must be known the valve of n, also the sender already knowsthe certain value of e, in additionally receiver also known the

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Cryptography and Security Protocols for Data Protection - Deskliblg...
|6
|1420
|320
Application of SSL/VPNlg...
|11
|2172
|1
Importance of VPN in Organizationslg...
|21
|2348
|481
Types of VPN and Encryption Techniqueslg...
|13
|2690
|49
Paper | Implementation Design for Data Encryption & Decryptionlg...
|7
|2263
|227
Virtual Private Network (VPN) | Literature Reviewlg...
|6
|926
|72
