Network Security Report: Cryptographic Algorithms and Network Design
VerifiedAdded on 2023/04/20
|16
|2776
|371
Report
AI Summary
This report, prepared for a Bachelor of Information Technology course (BIT243), delves into the critical aspects of network security. It begins with an executive summary and introduction, emphasizing the necessity of robust network design to combat cyber-attacks and protect confidential data. The report explores key concepts of OSI security architecture, including cryptographic algorithms such as symmetric and asymmetric key cryptography (DES, RSA). It covers various security techniques, including public key encryption, authentication, access controls, digital signatures, and identity management. The report details the design and implementation of prevention and detection systems, focusing on firewalls and Instruction Detection Systems (IDS), and includes an analysis and evaluation of these security measures. The report provides a comprehensive solution for securing a network, analyzing the need for such measures and the effectiveness of various security techniques. Finally, it concludes by summarizing the discussed topics and reiterating the importance of network security in the modern era, especially in protecting sensitive organizational data. The report also includes references to support the findings.
Ruining Head: Network Security 0
Network Security
Report
Student name
Network Security
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network Security 1
Executive Summary:
In this report, key concepts of OSI security architecture will discuss including cryptographic
algorithms. It will explain about design and implementation of prevention and detection system
using common security standards and protocols, such as IPsec, and many others.
XYZ retails ltd is a company that has up to 100 computer systems. This report will provide
network design with security techniques, such as public key encryption, authentication, access
controls, digital signatures, and identity management.
Executive Summary:
In this report, key concepts of OSI security architecture will discuss including cryptographic
algorithms. It will explain about design and implementation of prevention and detection system
using common security standards and protocols, such as IPsec, and many others.
XYZ retails ltd is a company that has up to 100 computer systems. This report will provide
network design with security techniques, such as public key encryption, authentication, access
controls, digital signatures, and identity management.

Network Security 2
Introduction:
Data communication is highly required to communicate between different systems. Network is
basic need of a company in present era. There are many things that are based on the computer
systems, such as billing, sales, marketing, and many others. This report will design network
architecture with high security to protect computer networks from cyber-attacks (Bradford,
2018).
Cyber security is necessary because most of the organizations are having their 20 percent
confidential data on the computer systems. Therefore, it is necessary to make them secure form
the cyber-attacks. In this report, key concepts of OSI security design will discuss including
cryptographic algorithms. It will explain about design and implementation of prevention and
detection system using common security standards and protocols, such as IPsec, and many others
(Cowley, 2012).
Authentication provides a security to a system and it is a way to make data and information
secure from the hackers and cyber-attacks. This report will provide network design with security
techniques, such as public key encryption, authentication, access controls, digital signatures,
and identity management ( Dosal, 2018).
Requirements:
Computer network requires many things to secure unauthenticated access from outside of the
network as well as internal access. To design and implement security policies in server and
firewalls, system requires security techniques, such as digital signature, authentication, access
control, public key encryption, and identity management ( Schilling , 2017). Cryptographic
algorithms are very helpful in security of a network. It is a best way to encrypt the data to
prevent from attackers. There are many cryptographic algorithms, which are making secure users
data from attackers in a public network (Dye, et al., 2007).
XYZ retails ltd can implement secure architecture for their organization. It requires basic
algorithm, such as symmetric and asymmetric algorithms. It is a way to secure resources and
data from unauthorized users. They will require digital signature to secure confidential data of
Introduction:
Data communication is highly required to communicate between different systems. Network is
basic need of a company in present era. There are many things that are based on the computer
systems, such as billing, sales, marketing, and many others. This report will design network
architecture with high security to protect computer networks from cyber-attacks (Bradford,
2018).
Cyber security is necessary because most of the organizations are having their 20 percent
confidential data on the computer systems. Therefore, it is necessary to make them secure form
the cyber-attacks. In this report, key concepts of OSI security design will discuss including
cryptographic algorithms. It will explain about design and implementation of prevention and
detection system using common security standards and protocols, such as IPsec, and many others
(Cowley, 2012).
Authentication provides a security to a system and it is a way to make data and information
secure from the hackers and cyber-attacks. This report will provide network design with security
techniques, such as public key encryption, authentication, access controls, digital signatures,
and identity management ( Dosal, 2018).
Requirements:
Computer network requires many things to secure unauthenticated access from outside of the
network as well as internal access. To design and implement security policies in server and
firewalls, system requires security techniques, such as digital signature, authentication, access
control, public key encryption, and identity management ( Schilling , 2017). Cryptographic
algorithms are very helpful in security of a network. It is a best way to encrypt the data to
prevent from attackers. There are many cryptographic algorithms, which are making secure users
data from attackers in a public network (Dye, et al., 2007).
XYZ retails ltd can implement secure architecture for their organization. It requires basic
algorithm, such as symmetric and asymmetric algorithms. It is a way to secure resources and
data from unauthorized users. They will require digital signature to secure confidential data of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Network Security 3
their business and other things. It is a basic thing to secure confidential information from cyber-
attacks. They will require firewalls and IDS/IPS to secure their network (Forouzan, 2007).
Solution Design
Secure network is first requirement of an organization. However, no one is secure from cyber-
attacks, as hacker’s uses new techniques for hacking computer systems and network of an
organization. There are many security techniques, which makes a network secure form the cyber-
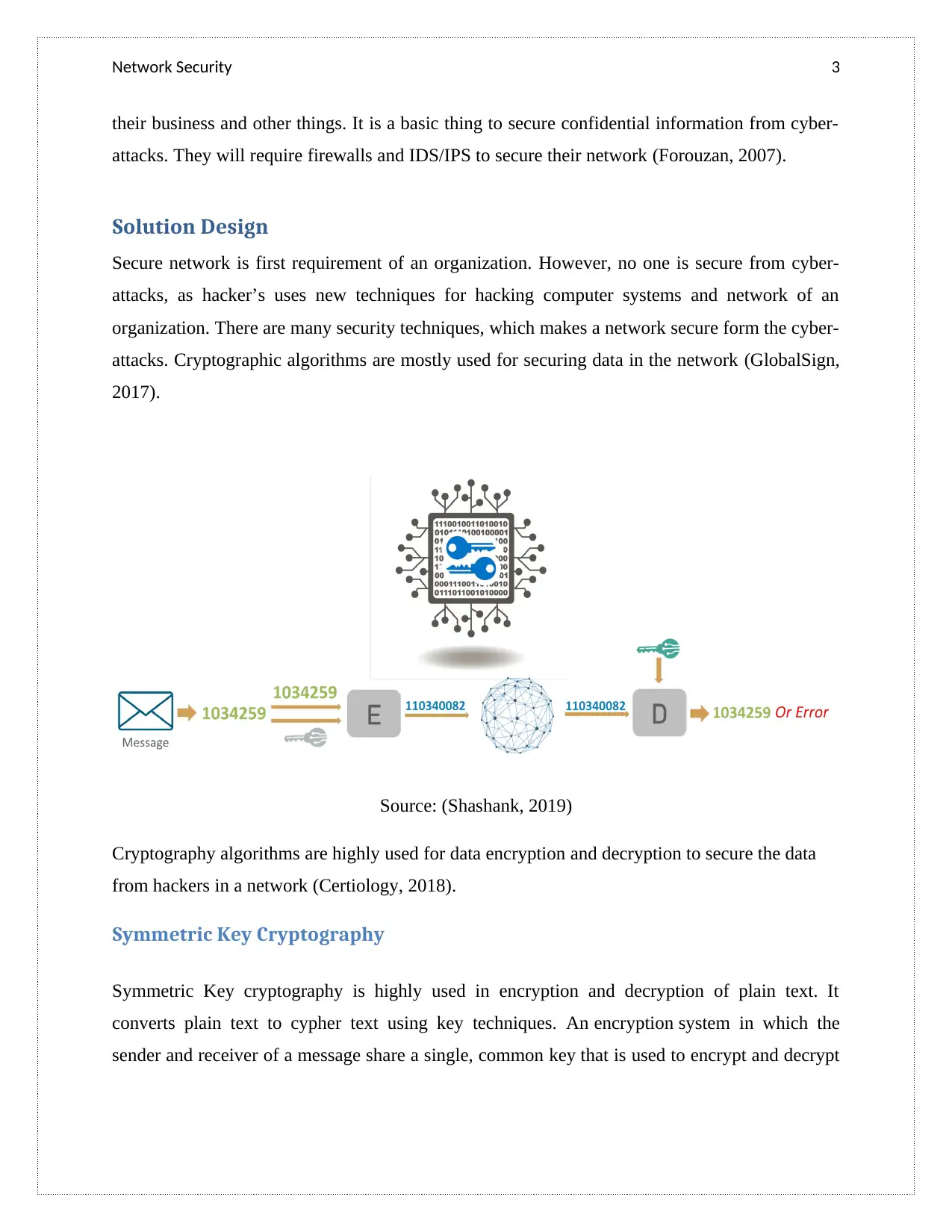
attacks. Cryptographic algorithms are mostly used for securing data in the network (GlobalSign,
2017).
Source: (Shashank, 2019)
Cryptography algorithms are highly used for data encryption and decryption to secure the data
from hackers in a network (Certiology, 2018).
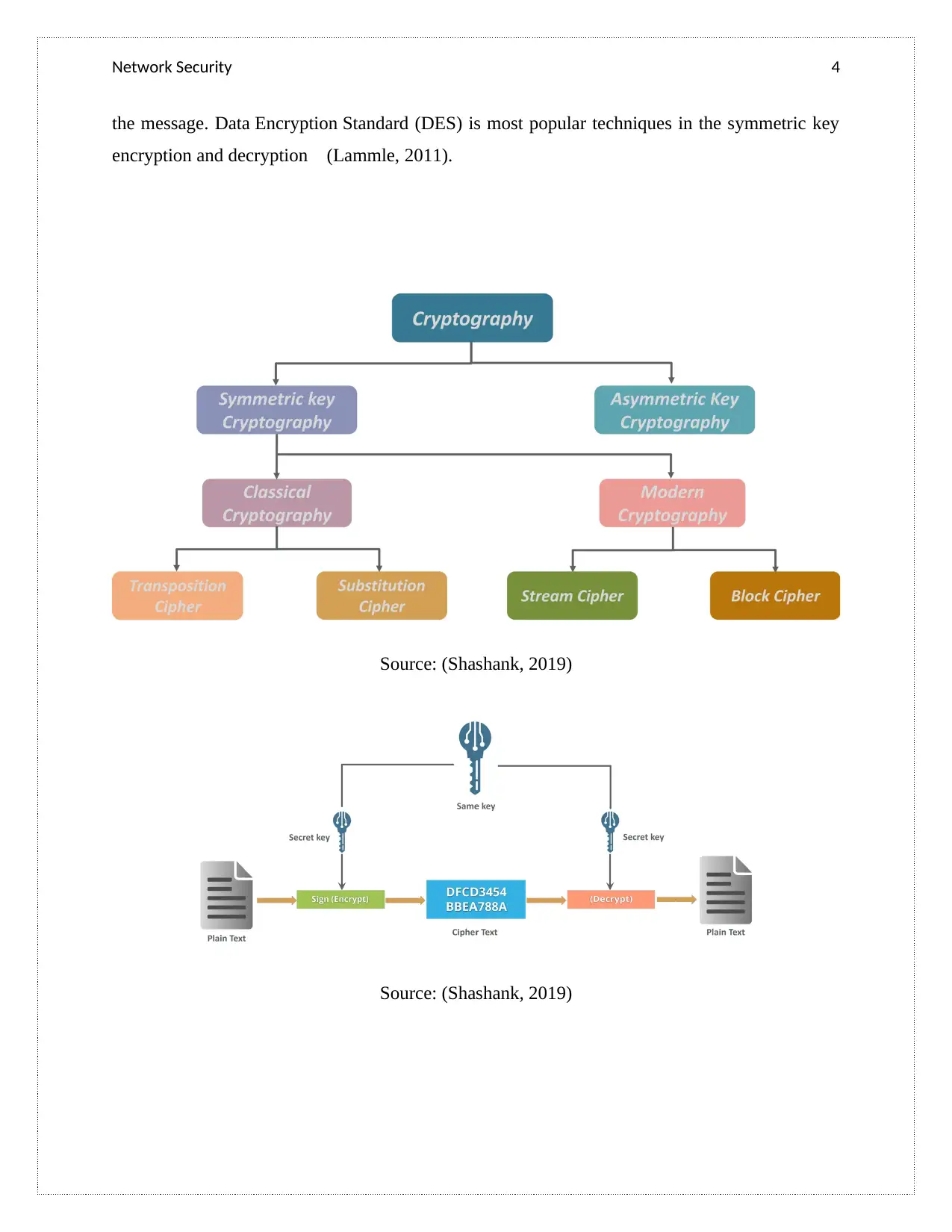
Symmetric Key Cryptography
Symmetric Key cryptography is highly used in encryption and decryption of plain text. It
converts plain text to cypher text using key techniques. An encryption system in which the
sender and receiver of a message share a single, common key that is used to encrypt and decrypt
their business and other things. It is a basic thing to secure confidential information from cyber-
attacks. They will require firewalls and IDS/IPS to secure their network (Forouzan, 2007).
Solution Design
Secure network is first requirement of an organization. However, no one is secure from cyber-
attacks, as hacker’s uses new techniques for hacking computer systems and network of an
organization. There are many security techniques, which makes a network secure form the cyber-
attacks. Cryptographic algorithms are mostly used for securing data in the network (GlobalSign,
2017).
Source: (Shashank, 2019)
Cryptography algorithms are highly used for data encryption and decryption to secure the data
from hackers in a network (Certiology, 2018).
Symmetric Key Cryptography
Symmetric Key cryptography is highly used in encryption and decryption of plain text. It
converts plain text to cypher text using key techniques. An encryption system in which the
sender and receiver of a message share a single, common key that is used to encrypt and decrypt
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network Security 4
the message. Data Encryption Standard (DES) is most popular techniques in the symmetric key
encryption and decryption (Lammle, 2011).
Source: (Shashank, 2019)
Source: (Shashank, 2019)
the message. Data Encryption Standard (DES) is most popular techniques in the symmetric key
encryption and decryption (Lammle, 2011).
Source: (Shashank, 2019)
Source: (Shashank, 2019)

Network Security 5
Transposition Ciphers
It is best way to secure plain text from attacker. Cryptography algorithms are most popular way
to secure data and information of an organization. Transposition cipher is methods of encryption
in which the positions held by units of plaintext are shifted according to a regular system.
Therefore, the cipher text constitutes a permutation of the plaintext. It makes it more secure and
safe from cyber-attacks.
That is, the order of the units is changed (the plaintext is reordered). Mathematically, an
objective function is used on the characters’ positions to encrypt and an inverse function to
decrypt.
Example:
Source: (Shashank, 2019)
Substitution Cipher
Method of encryption by which units of plaintext are replaced with cipher text, according to a
fixed system; the “units” may be single letters, pairs of letters, triplets of letters, mixtures of the
above, and so forth.
Transposition Ciphers
It is best way to secure plain text from attacker. Cryptography algorithms are most popular way
to secure data and information of an organization. Transposition cipher is methods of encryption
in which the positions held by units of plaintext are shifted according to a regular system.
Therefore, the cipher text constitutes a permutation of the plaintext. It makes it more secure and
safe from cyber-attacks.
That is, the order of the units is changed (the plaintext is reordered). Mathematically, an
objective function is used on the characters’ positions to encrypt and an inverse function to
decrypt.
Example:
Source: (Shashank, 2019)
Substitution Cipher
Method of encryption by which units of plaintext are replaced with cipher text, according to a
fixed system; the “units” may be single letters, pairs of letters, triplets of letters, mixtures of the
above, and so forth.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
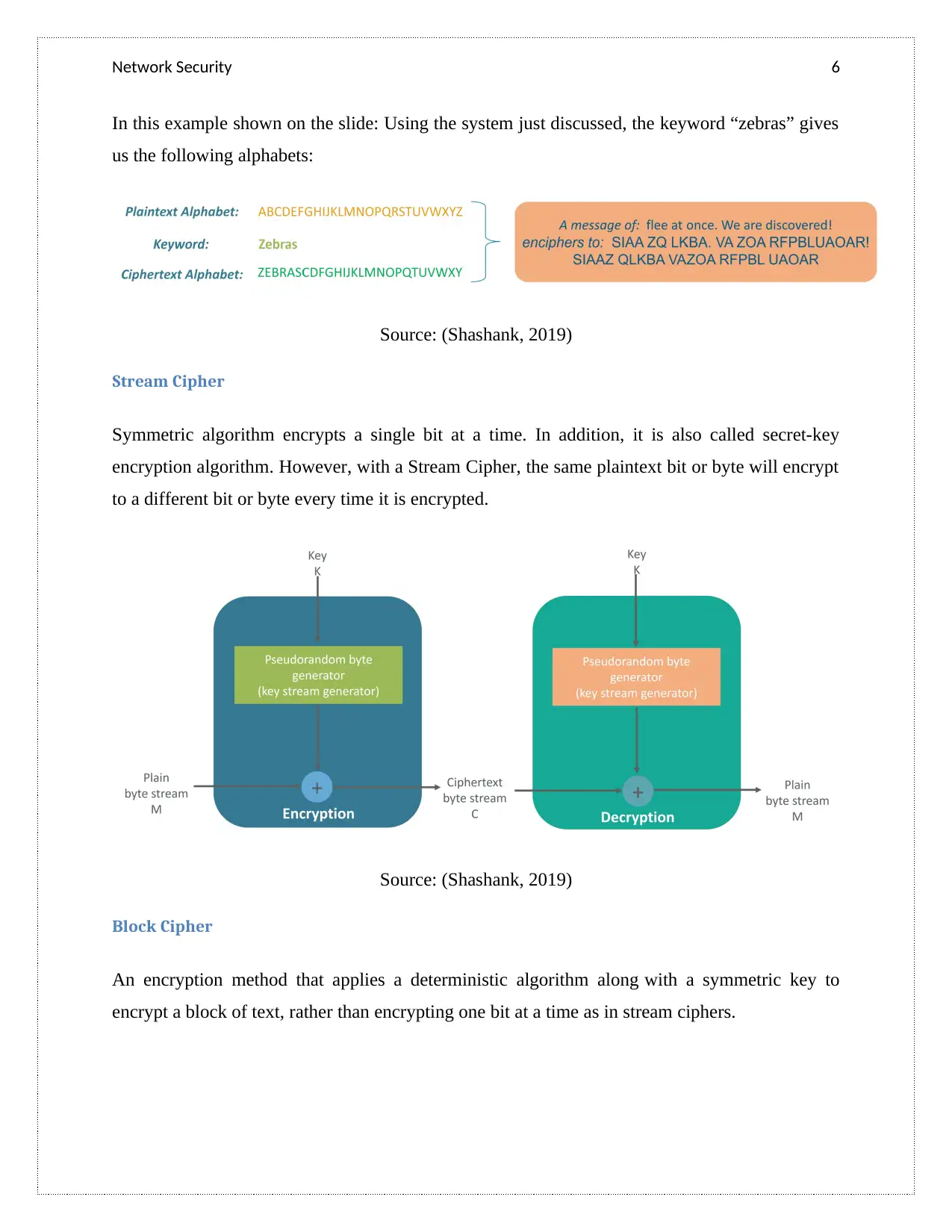
Network Security 6
In this example shown on the slide: Using the system just discussed, the keyword “zebras” gives
us the following alphabets:
Source: (Shashank, 2019)
Stream Cipher
Symmetric algorithm encrypts a single bit at a time. In addition, it is also called secret-key
encryption algorithm. However, with a Stream Cipher, the same plaintext bit or byte will encrypt
to a different bit or byte every time it is encrypted.
Source: (Shashank, 2019)
Block Cipher
An encryption method that applies a deterministic algorithm along with a symmetric key to
encrypt a block of text, rather than encrypting one bit at a time as in stream ciphers.
In this example shown on the slide: Using the system just discussed, the keyword “zebras” gives
us the following alphabets:
Source: (Shashank, 2019)
Stream Cipher
Symmetric algorithm encrypts a single bit at a time. In addition, it is also called secret-key
encryption algorithm. However, with a Stream Cipher, the same plaintext bit or byte will encrypt
to a different bit or byte every time it is encrypted.
Source: (Shashank, 2019)
Block Cipher
An encryption method that applies a deterministic algorithm along with a symmetric key to
encrypt a block of text, rather than encrypting one bit at a time as in stream ciphers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
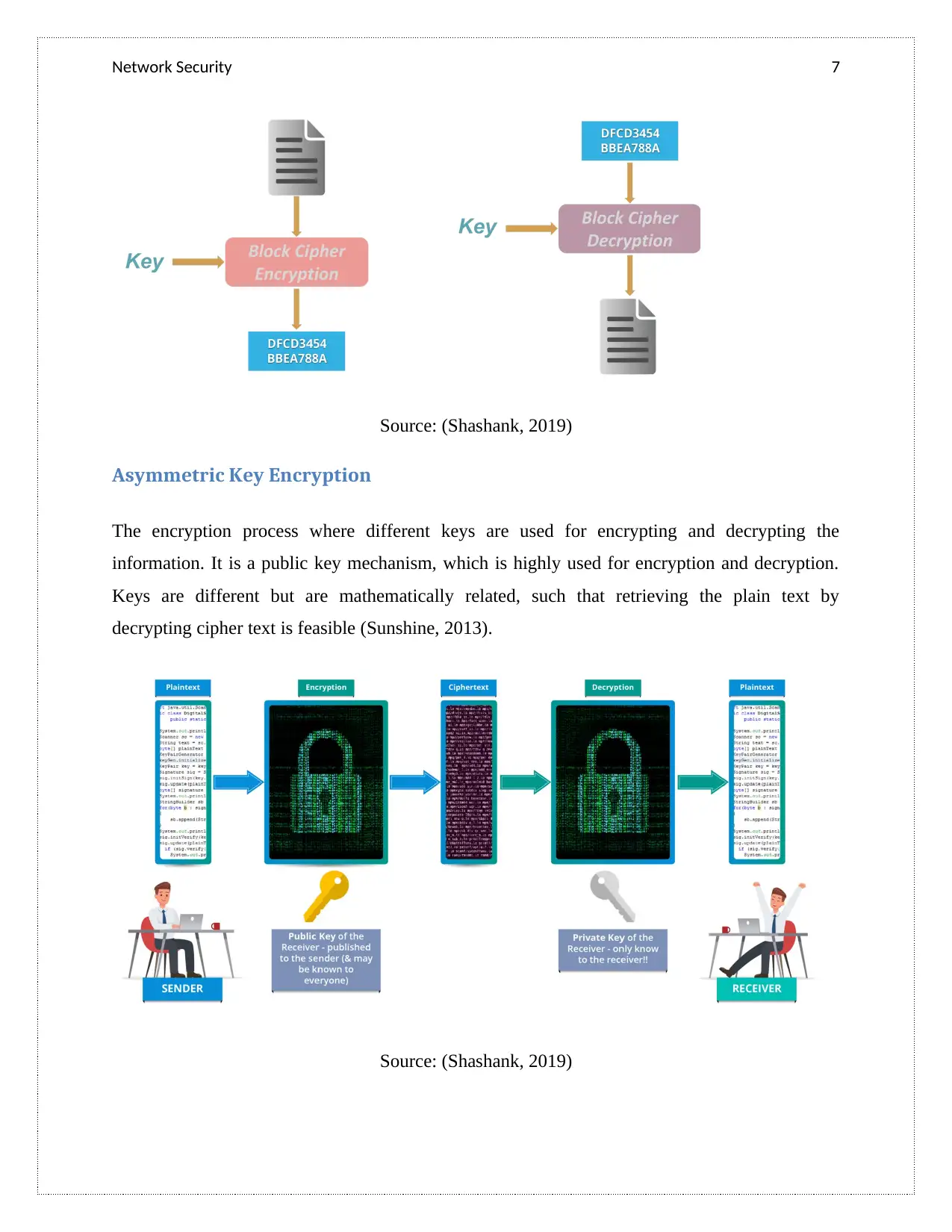
Network Security 7
Source: (Shashank, 2019)
Asymmetric Key Encryption
The encryption process where different keys are used for encrypting and decrypting the
information. It is a public key mechanism, which is highly used for encryption and decryption.
Keys are different but are mathematically related, such that retrieving the plain text by
decrypting cipher text is feasible (Sunshine, 2013).
Source: (Shashank, 2019)
Source: (Shashank, 2019)
Asymmetric Key Encryption
The encryption process where different keys are used for encrypting and decrypting the
information. It is a public key mechanism, which is highly used for encryption and decryption.
Keys are different but are mathematically related, such that retrieving the plain text by
decrypting cipher text is feasible (Sunshine, 2013).
Source: (Shashank, 2019)
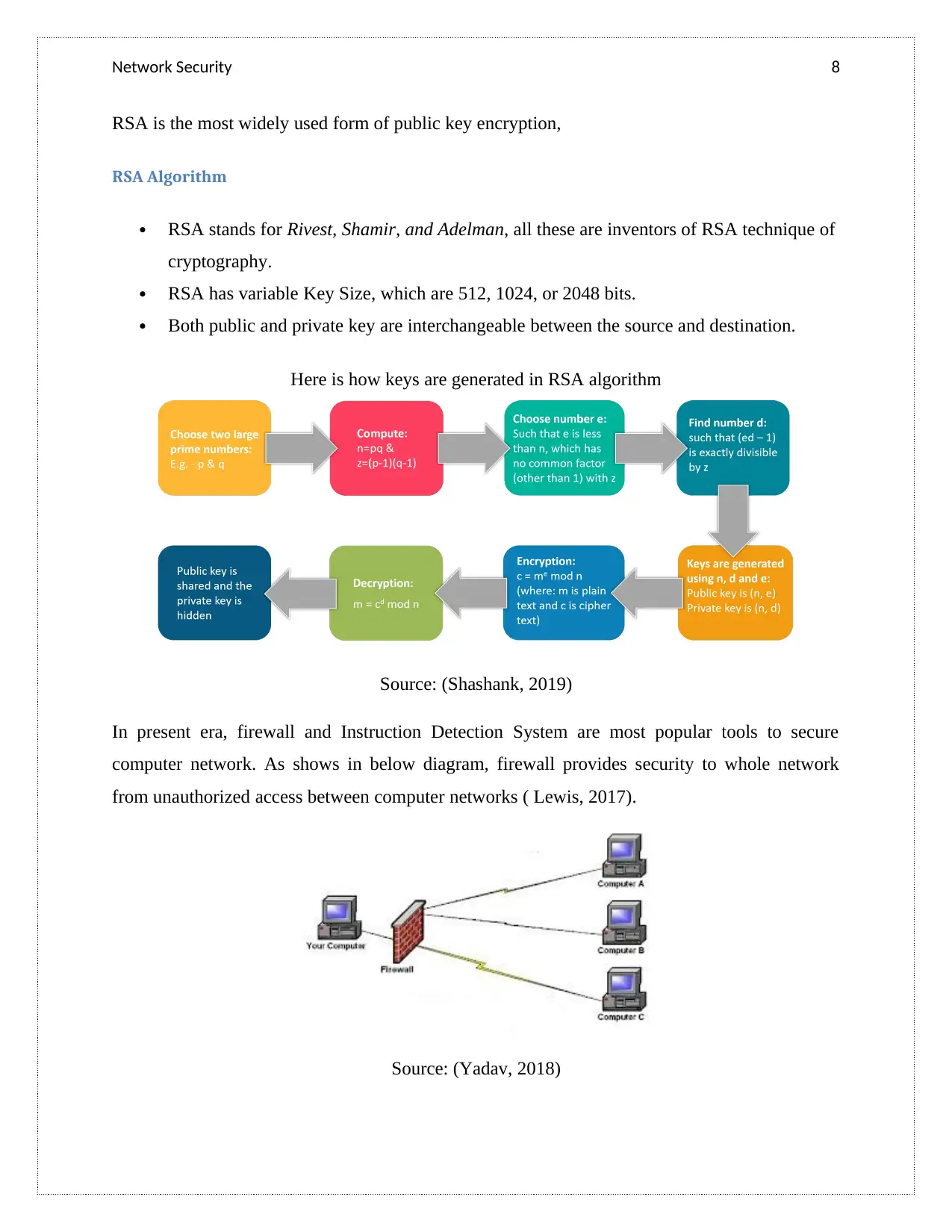
Network Security 8
RSA is the most widely used form of public key encryption,
RSA Algorithm
RSA stands for Rivest, Shamir, and Adelman, all these are inventors of RSA technique of
cryptography.
RSA has variable Key Size, which are 512, 1024, or 2048 bits.
Both public and private key are interchangeable between the source and destination.
Here is how keys are generated in RSA algorithm
Source: (Shashank, 2019)
In present era, firewall and Instruction Detection System are most popular tools to secure
computer network. As shows in below diagram, firewall provides security to whole network
from unauthorized access between computer networks ( Lewis, 2017).
Source: (Yadav, 2018)
RSA is the most widely used form of public key encryption,
RSA Algorithm
RSA stands for Rivest, Shamir, and Adelman, all these are inventors of RSA technique of
cryptography.
RSA has variable Key Size, which are 512, 1024, or 2048 bits.
Both public and private key are interchangeable between the source and destination.
Here is how keys are generated in RSA algorithm
Source: (Shashank, 2019)
In present era, firewall and Instruction Detection System are most popular tools to secure
computer network. As shows in below diagram, firewall provides security to whole network
from unauthorized access between computer networks ( Lewis, 2017).
Source: (Yadav, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Security 9
A firewall is used to forward some packets and filter others and it is a hardware device, which is
installed between the core network of organization and public network. It is a hardware device
with a special type of software, which is filter all the packets based on the security polices of
firewalls. It monitors the flow of data and control in network. It will decide about the packet to
forward towards their destinations (prospects.ac.uk, 2018).
It works based on two methodologies, which are as:
1. Allow any traffic in network except all those packets, which are specified restricted in
firewall configuration. Therefore, it is so necessary to configure firewall to secure
network.
2. Deny any packet or traffic, which does not, matches network criteria that are specified by
the network layer.
Security policies are used to determine the traffic type and it should allowed into network or
not. Firewall is checked the information of a packet, such as source address, destination
address, and ports. Firewall uses complex rules to secure network from unauthorized packets
and malicious functions (Techdonut, 2018).
There are many types of firewalls are available in the market to secure a network from cyber-
attacks, such as data breaches, ransomware, malfunctions and many others (Jacobs, 2016).
These are types of firewalls:
Packet-Filter Firewall
Hardware Firewall
Application Gateways
Software Firewall
Stateful Packet-Inspection (SPI)
Proxy Firewall
Circuit-Level Gateways
A firewall is used to forward some packets and filter others and it is a hardware device, which is
installed between the core network of organization and public network. It is a hardware device
with a special type of software, which is filter all the packets based on the security polices of
firewalls. It monitors the flow of data and control in network. It will decide about the packet to
forward towards their destinations (prospects.ac.uk, 2018).
It works based on two methodologies, which are as:
1. Allow any traffic in network except all those packets, which are specified restricted in
firewall configuration. Therefore, it is so necessary to configure firewall to secure
network.
2. Deny any packet or traffic, which does not, matches network criteria that are specified by
the network layer.
Security policies are used to determine the traffic type and it should allowed into network or
not. Firewall is checked the information of a packet, such as source address, destination
address, and ports. Firewall uses complex rules to secure network from unauthorized packets
and malicious functions (Techdonut, 2018).
There are many types of firewalls are available in the market to secure a network from cyber-
attacks, such as data breaches, ransomware, malfunctions and many others (Jacobs, 2016).
These are types of firewalls:
Packet-Filter Firewall
Hardware Firewall
Application Gateways
Software Firewall
Stateful Packet-Inspection (SPI)
Proxy Firewall
Circuit-Level Gateways
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
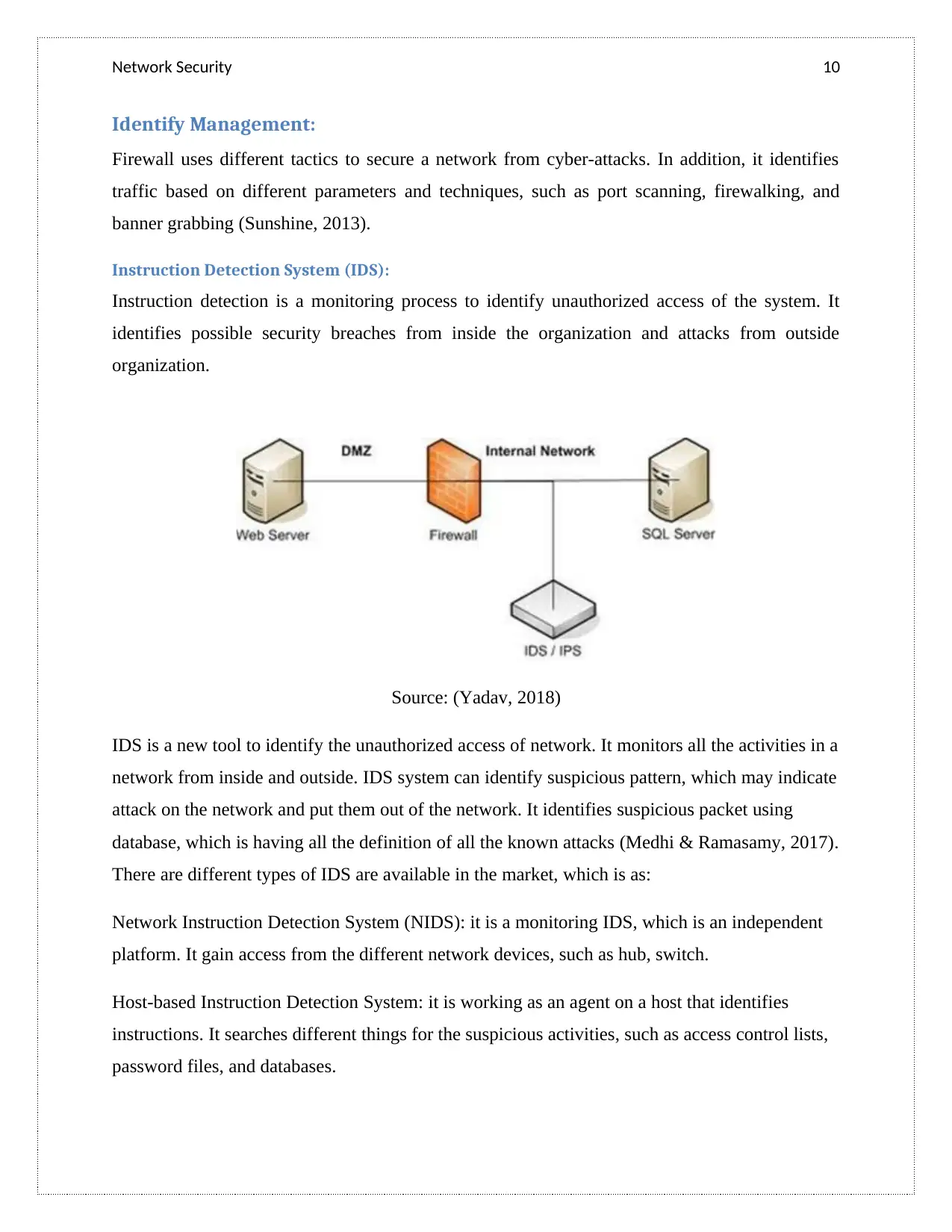
Network Security 10
Identify Management:
Firewall uses different tactics to secure a network from cyber-attacks. In addition, it identifies
traffic based on different parameters and techniques, such as port scanning, firewalking, and
banner grabbing (Sunshine, 2013).
Instruction Detection System (IDS):
Instruction detection is a monitoring process to identify unauthorized access of the system. It
identifies possible security breaches from inside the organization and attacks from outside
organization.
Source: (Yadav, 2018)
IDS is a new tool to identify the unauthorized access of network. It monitors all the activities in a
network from inside and outside. IDS system can identify suspicious pattern, which may indicate
attack on the network and put them out of the network. It identifies suspicious packet using
database, which is having all the definition of all the known attacks (Medhi & Ramasamy, 2017).
There are different types of IDS are available in the market, which is as:
Network Instruction Detection System (NIDS): it is a monitoring IDS, which is an independent
platform. It gain access from the different network devices, such as hub, switch.
Host-based Instruction Detection System: it is working as an agent on a host that identifies
instructions. It searches different things for the suspicious activities, such as access control lists,
password files, and databases.
Identify Management:
Firewall uses different tactics to secure a network from cyber-attacks. In addition, it identifies
traffic based on different parameters and techniques, such as port scanning, firewalking, and
banner grabbing (Sunshine, 2013).
Instruction Detection System (IDS):
Instruction detection is a monitoring process to identify unauthorized access of the system. It
identifies possible security breaches from inside the organization and attacks from outside
organization.
Source: (Yadav, 2018)
IDS is a new tool to identify the unauthorized access of network. It monitors all the activities in a
network from inside and outside. IDS system can identify suspicious pattern, which may indicate
attack on the network and put them out of the network. It identifies suspicious packet using
database, which is having all the definition of all the known attacks (Medhi & Ramasamy, 2017).
There are different types of IDS are available in the market, which is as:
Network Instruction Detection System (NIDS): it is a monitoring IDS, which is an independent
platform. It gain access from the different network devices, such as hub, switch.
Host-based Instruction Detection System: it is working as an agent on a host that identifies
instructions. It searches different things for the suspicious activities, such as access control lists,
password files, and databases.

Network Security 11
Perimeter Instruction Detection System (PIDS): it triggered an alarm, when it finds any
malicious or suspicious activity in the network.
VM-based Instruction Detection System (VMIDS): it is a virtual monitoring system to identify
suspicious activities in a network it is useful in monitor overall activities in a network
Instruction Prevention System:
It is a detection program, which detect the anomaly in the network. It informed about the
suspicious activity to the concerned person to take action against that activities. It makes a
database about the irregular activities in the network (Tanenbaum, 2014).
Analysis and Evaluation:
In this report, key concepts of OSI security architecture are analysed including cryptographic
algorithms, such as asymmetric and symmetric algorithms. It has analyzed about the design and
implementation of firewalls, instruction detection system, and instruction prevention systems to
secure network of XYZ retails ltd. It has evaluated that security is highly required to secure the
data and information of XYZ retails ltd. This report has provided a solution to secure network of
XYZ retails ltd. It evaluates effective uses of security techniques, such as public key encryption,
digital signature, identity management, access control, and authentication. Firewall configuration
is set the security policies, which provides access to only authenticated users in their network.
Computer network is basic need of an organization in present time. There are many things that
are based on the computer systems, such as billing, sales, marketing, and many others. This
report will design network architecture with high security to protect computer networks from
cyber-attacks. Security is a first concern in present time in case of computer network because of
confidential data and information. OSI is a layered architecture with seven layers and each layer
has a dedicated work. In addition, security is a main concern in few layers, such as network layer
and application layer. A network has many layers of security to detect and prevent from cyber-
attacks.
In addition, information security systems are requires high security from different types of cyber-
attacks and these technologies are helpful for resolving different security issues in the network.
Most of the companies are having their data on the cloud and person computer systems.
Perimeter Instruction Detection System (PIDS): it triggered an alarm, when it finds any
malicious or suspicious activity in the network.
VM-based Instruction Detection System (VMIDS): it is a virtual monitoring system to identify
suspicious activities in a network it is useful in monitor overall activities in a network
Instruction Prevention System:
It is a detection program, which detect the anomaly in the network. It informed about the
suspicious activity to the concerned person to take action against that activities. It makes a
database about the irregular activities in the network (Tanenbaum, 2014).
Analysis and Evaluation:
In this report, key concepts of OSI security architecture are analysed including cryptographic
algorithms, such as asymmetric and symmetric algorithms. It has analyzed about the design and
implementation of firewalls, instruction detection system, and instruction prevention systems to
secure network of XYZ retails ltd. It has evaluated that security is highly required to secure the
data and information of XYZ retails ltd. This report has provided a solution to secure network of
XYZ retails ltd. It evaluates effective uses of security techniques, such as public key encryption,
digital signature, identity management, access control, and authentication. Firewall configuration
is set the security policies, which provides access to only authenticated users in their network.
Computer network is basic need of an organization in present time. There are many things that
are based on the computer systems, such as billing, sales, marketing, and many others. This
report will design network architecture with high security to protect computer networks from
cyber-attacks. Security is a first concern in present time in case of computer network because of
confidential data and information. OSI is a layered architecture with seven layers and each layer
has a dedicated work. In addition, security is a main concern in few layers, such as network layer
and application layer. A network has many layers of security to detect and prevent from cyber-
attacks.
In addition, information security systems are requires high security from different types of cyber-
attacks and these technologies are helpful for resolving different security issues in the network.
Most of the companies are having their data on the cloud and person computer systems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




