Design and Implementation of Secure Wireless Network (MN603)
VerifiedAdded on 2023/06/04
|10
|2409
|121
Project
AI Summary
This project focuses on designing and implementing a secure enterprise wireless network, a crucial requirement in modern network engineering. The project emphasizes the use of WPA2 and RADIUS servers to establish a safe wireless network, incorporating considerations for ethical implications. The design includes the use of Boson Netsim for practical implementation and analysis, including aspects of verification, authorization, and confidentiality. The report explores the advantages of dynamic WIDS and WIPS for proactive threat management. The project also covers implementation steps, including software updates, firewall implementation, antivirus software, and IDS/IPS. Furthermore, the report details the testing phase, utilizing ping configurations within Boson Netsim, and concludes by summarizing the key aspects of the project and its successful completion.
Network and Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1 Introduction.......................................................................................................................2
2 Ethical Implications..........................................................................................................3
3 Secure Enterprise Wireless Network Design..................................................................3
4 Analysis of Secure Enterprise Wireless Network..........................................................5
5 Implementation of Secure Enterprise Wireless Network.............................................6
6 Testing................................................................................................................................7
7 Conclusion.........................................................................................................................8
References.................................................................................................................................9
1
1 Introduction.......................................................................................................................2
2 Ethical Implications..........................................................................................................3
3 Secure Enterprise Wireless Network Design..................................................................3
4 Analysis of Secure Enterprise Wireless Network..........................................................5
5 Implementation of Secure Enterprise Wireless Network.............................................6
6 Testing................................................................................................................................7
7 Conclusion.........................................................................................................................8
References.................................................................................................................................9
1

1 Introduction
Primary objective of this project is to make a protected endeavour wireless network, as
it is the basic requirement for the current network engineering. This network is utilized to
help the cell phones and provides high network availability. The enterprise network security
is the insurance of a network that associates with the frameworks, centralized servers, and
the devices such as the cell phones and tablets inside the endeavour. The organizations,
colleges, governments, and different other areas utilizes the job of the networks to help in
interfacing data with their clients and individuals. As the network develops in size, many-
sided quality, security concerns likewise increases. Utilizing the dynamic WIDS and WIPS
empowers arrangement of overseers to make and implement wireless security, by checking,
identifying, and relieving the potential dangers. Both, WIDS and WIPS will identify and
naturally detach the unapproved devices. WIDS provides the capacity to naturally screen
and distinguish the nearness of any unapproved, bad access points, whereas the WIPS
conveys the counter measures for recognizing the dangers. Some regular dangers regulated
by WIPS are, maverick access, misconfigured passages, customer misassociation,
unapproved affiliation, man-in-the-middle attacks, unprepared networks, Media Access
Control, honeypot and desirable twin attacks, and denial of-services assaults.
This task utilizes the two servers namely, RADIUS server and WPA2 Server. These two
server are utilized to deliver safe wireless network. The WPA2 incorporates the utilized
wireless verification of client’s tasks interactions for arrangement administrations. The
RADIUS server designs the procedure of two accesses that are utilized for data encryption.
The client’s working arrangement is related to designing the procedure encryption and
settings of IEEE802.1x. At last, it associates safe working wireless network. The utilization of
WPA2 and RADIUS server is utilized for developing protected wireless network for the
enterprise. Then, the business wireless plan for the protected tasks are worked on, by
utilizing Boson Netsim. At that point, differentiate and actualize the safe working of the
wireless network. Finally, test the developed network, by utilizing the ping network present
on the Boson Netsim. All the above mentioned aspects will be broken down and exhibited in
detail.
2
Primary objective of this project is to make a protected endeavour wireless network, as
it is the basic requirement for the current network engineering. This network is utilized to
help the cell phones and provides high network availability. The enterprise network security
is the insurance of a network that associates with the frameworks, centralized servers, and
the devices such as the cell phones and tablets inside the endeavour. The organizations,
colleges, governments, and different other areas utilizes the job of the networks to help in
interfacing data with their clients and individuals. As the network develops in size, many-
sided quality, security concerns likewise increases. Utilizing the dynamic WIDS and WIPS
empowers arrangement of overseers to make and implement wireless security, by checking,
identifying, and relieving the potential dangers. Both, WIDS and WIPS will identify and
naturally detach the unapproved devices. WIDS provides the capacity to naturally screen
and distinguish the nearness of any unapproved, bad access points, whereas the WIPS
conveys the counter measures for recognizing the dangers. Some regular dangers regulated
by WIPS are, maverick access, misconfigured passages, customer misassociation,
unapproved affiliation, man-in-the-middle attacks, unprepared networks, Media Access
Control, honeypot and desirable twin attacks, and denial of-services assaults.
This task utilizes the two servers namely, RADIUS server and WPA2 Server. These two
server are utilized to deliver safe wireless network. The WPA2 incorporates the utilized
wireless verification of client’s tasks interactions for arrangement administrations. The
RADIUS server designs the procedure of two accesses that are utilized for data encryption.
The client’s working arrangement is related to designing the procedure encryption and
settings of IEEE802.1x. At last, it associates safe working wireless network. The utilization of
WPA2 and RADIUS server is utilized for developing protected wireless network for the
enterprise. Then, the business wireless plan for the protected tasks are worked on, by
utilizing Boson Netsim. At that point, differentiate and actualize the safe working of the
wireless network. Finally, test the developed network, by utilizing the ping network present
on the Boson Netsim. All the above mentioned aspects will be broken down and exhibited in
detail.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
2 Ethical Implications
Moral issue on the remote system realization can come to everybody for
accommodation and has less than ideal setup. The remote system accessibility of various
moral issues are like, insurance of security for the brisk consuming, and the majority of the
points to design the destiny of predictable remote system on the world. The primary issue
is, access to the territory of individual sifting information. Let us consider the issues of the
region security of the customer or the zone of a section. With everything taken into account,
breaking to passages is used to go with things like, get to the Adult locales or to fill
contamination in the system, to take the monetary adjustments of the money taking and
the experience of hacking [1]. This gives the dynamic encryption of the abnormal state
security given for various key encryptions like, shared key authentication, open system
authentication and unified confirmation. In Shared key Authentication, the check get to, is
done by the response to a test with the entry which is known as test and response. In Open
system Authentication, the procedure SSID is used for Authentication if the SSID is known,
access can be surrendered. In Unified confirmation, a server is used for the approval if the
centre point is affirmed then nobody can get to the system.
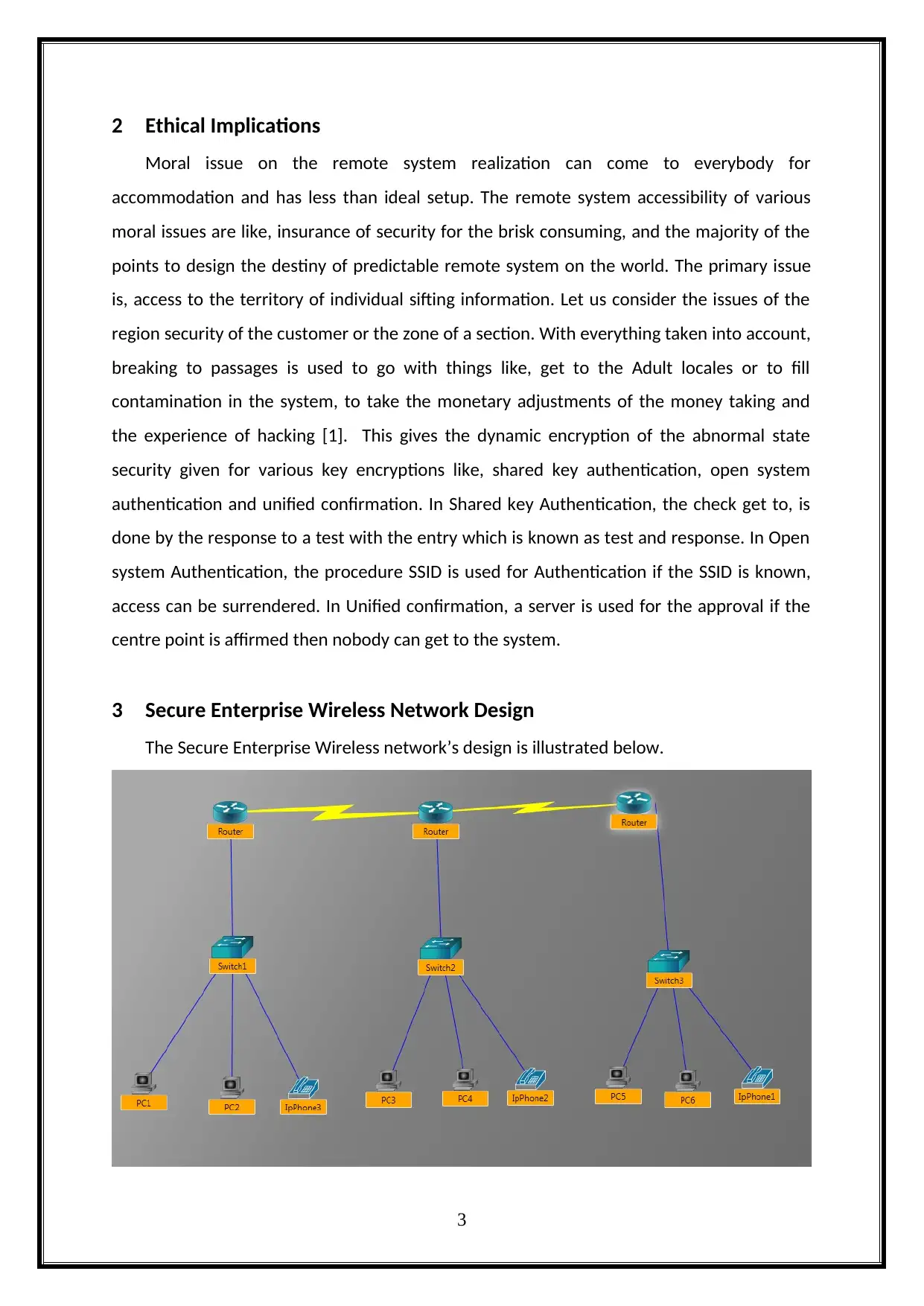
3 Secure Enterprise Wireless Network Design
The Secure Enterprise Wireless network’s design is illustrated below.
3
Moral issue on the remote system realization can come to everybody for
accommodation and has less than ideal setup. The remote system accessibility of various
moral issues are like, insurance of security for the brisk consuming, and the majority of the
points to design the destiny of predictable remote system on the world. The primary issue
is, access to the territory of individual sifting information. Let us consider the issues of the
region security of the customer or the zone of a section. With everything taken into account,
breaking to passages is used to go with things like, get to the Adult locales or to fill
contamination in the system, to take the monetary adjustments of the money taking and
the experience of hacking [1]. This gives the dynamic encryption of the abnormal state
security given for various key encryptions like, shared key authentication, open system
authentication and unified confirmation. In Shared key Authentication, the check get to, is
done by the response to a test with the entry which is known as test and response. In Open
system Authentication, the procedure SSID is used for Authentication if the SSID is known,
access can be surrendered. In Unified confirmation, a server is used for the approval if the
centre point is affirmed then nobody can get to the system.
3 Secure Enterprise Wireless Network Design
The Secure Enterprise Wireless network’s design is illustrated below.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The creation of the enterprise security network that interfaces the structures, unified
servers, and contraptions like mobile phones and tablets inside an undertaking is
represented. Organizations, schools, governments, and diverse components use tasks of the
systems to help interface their customers’ information to the connected people. As systems
developed in size are multifaceted in nature, the security concerns are high. Such as the
wired systems, which have solid security devices. For instance, firewalls, intrusion detection
system, content channels and antivirus and against malware area program remote systems
give remote access that can be defenceless against access [2]. Since they may don't have
indistinct securities from the wired systems, the remote systems and devices can respect
the accumulation of assaults expected to the big businesses which must be organized. An
entrance to the aggressors an undertaking system through the remote access to coordinate
pernicious activities including packet sniffing, secret key stealing, and man-in-the-middle
assaults. These assaults could postpone the direct methodology, or even harm the working
structure. Consider these additional acknowledged methods to help guard the tasks of the
Wi-Fi systems:
1. Send WIDS and a remote interruption counteractive action organize (WIPS) on each
system.
2. Guarantee existing equipment is free from vulnerabilities.
3. Utilize existing tools that can be securely masterminded [3].
4. Guarantee all apparatus meets (FIPS) 140-2 for encryption and consistence.
5. Guarantee consistence with the most current National Institute of Standards and
Technology.
6. Set up the multifaceted affirmation for accessing your system. In case this isn't
possible, consider other secure methods which suggests a single shared mystery
word, for instance, Active Directory advantage approval or an elective technique to
make multifaceted affirmation into your system.
7. Utilize Extensible Authentication Protocol-Transport Layer Security support based
procedures to stay the entire affirmation trade and correspondence.
8. Utilize Counter Mode Cipher Block Chaining Message Authentication Code Protocol,
a type of AES encryption used by the Wireless Application Protocol 2. In case
possible, use more incredible encryption progressions that conforms to FIPS 140-2 as
they are created and embraced.
4
servers, and contraptions like mobile phones and tablets inside an undertaking is
represented. Organizations, schools, governments, and diverse components use tasks of the
systems to help interface their customers’ information to the connected people. As systems
developed in size are multifaceted in nature, the security concerns are high. Such as the
wired systems, which have solid security devices. For instance, firewalls, intrusion detection
system, content channels and antivirus and against malware area program remote systems
give remote access that can be defenceless against access [2]. Since they may don't have
indistinct securities from the wired systems, the remote systems and devices can respect
the accumulation of assaults expected to the big businesses which must be organized. An
entrance to the aggressors an undertaking system through the remote access to coordinate
pernicious activities including packet sniffing, secret key stealing, and man-in-the-middle
assaults. These assaults could postpone the direct methodology, or even harm the working
structure. Consider these additional acknowledged methods to help guard the tasks of the
Wi-Fi systems:
1. Send WIDS and a remote interruption counteractive action organize (WIPS) on each
system.
2. Guarantee existing equipment is free from vulnerabilities.
3. Utilize existing tools that can be securely masterminded [3].
4. Guarantee all apparatus meets (FIPS) 140-2 for encryption and consistence.
5. Guarantee consistence with the most current National Institute of Standards and
Technology.
6. Set up the multifaceted affirmation for accessing your system. In case this isn't
possible, consider other secure methods which suggests a single shared mystery
word, for instance, Active Directory advantage approval or an elective technique to
make multifaceted affirmation into your system.
7. Utilize Extensible Authentication Protocol-Transport Layer Security support based
procedures to stay the entire affirmation trade and correspondence.
8. Utilize Counter Mode Cipher Block Chaining Message Authentication Code Protocol,
a type of AES encryption used by the Wireless Application Protocol 2. In case
possible, use more incredible encryption progressions that conforms to FIPS 140-2 as
they are created and embraced.
4

9. Actualize a guest Wi-Fi mastermind that is separate from the standard compose. Use
switches with various SSIDs or attract distinctive remote detachment features to
ensure that legitimate information isn't available to guest mastermind development
or by interfacing with various remote separation features.
4 Analysis of Secure Enterprise Wireless Network
Verification and Authorization
The business wireless system development task is proposed of WPA endeavour
standard, which is generally called as WAP-802.IX. It is used as an authenticator of the
supplicant and for server approval. The supplicant is a client contraption that is responsible
for making sales to the WLAN, by offering accreditations to the authenticator. The
enterprise access to the authenticator is a typically interface with the server confirmation,
through RADIUS or IAS realized tradition, to affirm the approval of the client. The assault
includes deriding the targeted system and gives better banner than the client in genuine
section, with a particular true objective to play out a Man-In-The-Middle assault among the
clients and the system establishment. Directly the TLS tunnel is adequately secure and isn’t
easily attackable [4].
Confidentiality
The basic strategies for the data and the certification uncovered to the customer of
unapproved encoding sums transmitting to essentially indistinct between the transmit wired
system of the course encryption data is irrelevant without the approval. As, it could be an
unapproved customer on the system themselves gives the key of the data that is
disentangle [5].
Integrity
The wireless system however indicates the air bundles of the data are caught, viably
by vindictive of changed customers. The systems are highly unprotected against the attacks
of data. In any case, that the best approach used is the wired systems present strategies of
the parcels.
Availability
5
switches with various SSIDs or attract distinctive remote detachment features to
ensure that legitimate information isn't available to guest mastermind development
or by interfacing with various remote separation features.
4 Analysis of Secure Enterprise Wireless Network
Verification and Authorization
The business wireless system development task is proposed of WPA endeavour
standard, which is generally called as WAP-802.IX. It is used as an authenticator of the
supplicant and for server approval. The supplicant is a client contraption that is responsible
for making sales to the WLAN, by offering accreditations to the authenticator. The
enterprise access to the authenticator is a typically interface with the server confirmation,
through RADIUS or IAS realized tradition, to affirm the approval of the client. The assault
includes deriding the targeted system and gives better banner than the client in genuine
section, with a particular true objective to play out a Man-In-The-Middle assault among the
clients and the system establishment. Directly the TLS tunnel is adequately secure and isn’t
easily attackable [4].
Confidentiality
The basic strategies for the data and the certification uncovered to the customer of
unapproved encoding sums transmitting to essentially indistinct between the transmit wired
system of the course encryption data is irrelevant without the approval. As, it could be an
unapproved customer on the system themselves gives the key of the data that is
disentangle [5].
Integrity
The wireless system however indicates the air bundles of the data are caught, viably
by vindictive of changed customers. The systems are highly unprotected against the attacks
of data. In any case, that the best approach used is the wired systems present strategies of
the parcels.
Availability
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The wired system expected the attacker related to the system, by one means or
another, before dispatching such a trap is physically connected wireless systems, an
antivirus inside the system limits the entry of the trap. For example, strike.
5 Implementation of Secure Enterprise Wireless Network
The implementation of secure enterprise wireless network consists of the following aspects.
To expand system security, automated software updates must be empowered in
every single PC and system devices. Typically, the firmware and working frameworks
consequently introduce the imperative updates [6].
Make use of a firewall that could keep the hackers away from accessing the users’
system. Firewall controls and channels all the system correspondences. Actualizing other
venture security arrangements alongside the firewalls can separate systems, to keep certain
information stream [7].
Your PCs can get infected from spam, USBs, CDs and by the documents downloaded
from the Internet. As there are various new viruses that are introduced each day, thus
antivirus software must be refreshed occasionally. Antivirus helps to recognize the virus and
in some cases it evacuates the virus too. As indicated by the experience of big business
organize security organization experts; there are various types of antivirus available in the
market.
Utilize IDS-IPS. IDS, IPS provides organize security benefits that empowers the
interruption identification and interruption counteractive actions. IDS/IPS proactively
recognizes the complex activity [8]. VLAN is a technique for making free sensible systems
inside the PC’s set up. The PC system can have different virtual systems. VLAN is one of the
critical venture set up security arrangements that has gaps in system gatherings of clients in
a genuine physical system, into legitimate fragmented systems.
An entrance control rundown or ACL is used for executing the legitimate security.
ACL is one of the venture established security arrangement that can help to decide the
fitting access consents for the system assets. ACL channels arranges the activity and just
permits the organize movement in some conditions.
Actualize the network security solutions, for example, IPsec (Internet Protocol
Security) for encryption. IPsec is an arrangement of conventions that are utilized for secure
6
another, before dispatching such a trap is physically connected wireless systems, an
antivirus inside the system limits the entry of the trap. For example, strike.
5 Implementation of Secure Enterprise Wireless Network
The implementation of secure enterprise wireless network consists of the following aspects.
To expand system security, automated software updates must be empowered in
every single PC and system devices. Typically, the firmware and working frameworks
consequently introduce the imperative updates [6].
Make use of a firewall that could keep the hackers away from accessing the users’
system. Firewall controls and channels all the system correspondences. Actualizing other
venture security arrangements alongside the firewalls can separate systems, to keep certain
information stream [7].
Your PCs can get infected from spam, USBs, CDs and by the documents downloaded
from the Internet. As there are various new viruses that are introduced each day, thus
antivirus software must be refreshed occasionally. Antivirus helps to recognize the virus and
in some cases it evacuates the virus too. As indicated by the experience of big business
organize security organization experts; there are various types of antivirus available in the
market.
Utilize IDS-IPS. IDS, IPS provides organize security benefits that empowers the
interruption identification and interruption counteractive actions. IDS/IPS proactively
recognizes the complex activity [8]. VLAN is a technique for making free sensible systems
inside the PC’s set up. The PC system can have different virtual systems. VLAN is one of the
critical venture set up security arrangements that has gaps in system gatherings of clients in
a genuine physical system, into legitimate fragmented systems.
An entrance control rundown or ACL is used for executing the legitimate security.
ACL is one of the venture established security arrangement that can help to decide the
fitting access consents for the system assets. ACL channels arranges the activity and just
permits the organize movement in some conditions.
Actualize the network security solutions, for example, IPsec (Internet Protocol
Security) for encryption. IPsec is an arrangement of conventions that are utilized for secure
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

interchanges at the system layer and at the vehicle layer such as both TCP and UDP. IPsec
helps in verification and encryption of information bundles [9].
Introduce RADIUS, TFTP servers relying upon the business prerequisites with the
other venture established security administrations and arrangements. Empower the logs
server, which will empower you to record all the system movements.
6 Testing
Ping configuration is represented below [10].
7 Conclusion
The objective of this project is successfully makes the protected working wireless
network, as it is the basic requirement for the current network engineering. This network is
utilized to help the cell phones and provides high network availability. As the networks
develop in size and various many-sided quality and security concerns relatively increases. It
is believed that utilizing the dynamic WIDS and WIPS empowers arrangement of overseers
to make and implement wireless security, by checking, identifying, and relieving the
potential dangers. It is further noted that RADIUS and WPA2 Servers are used for this task,
for safe wireless network. It is mainly associated to provide safe working wireless network.
At last, the developed network is tested with the help of ping network present on the Boson
Netsim.
7
helps in verification and encryption of information bundles [9].
Introduce RADIUS, TFTP servers relying upon the business prerequisites with the
other venture established security administrations and arrangements. Empower the logs
server, which will empower you to record all the system movements.
6 Testing
Ping configuration is represented below [10].
7 Conclusion
The objective of this project is successfully makes the protected working wireless
network, as it is the basic requirement for the current network engineering. This network is
utilized to help the cell phones and provides high network availability. As the networks
develop in size and various many-sided quality and security concerns relatively increases. It
is believed that utilizing the dynamic WIDS and WIPS empowers arrangement of overseers
to make and implement wireless security, by checking, identifying, and relieving the
potential dangers. It is further noted that RADIUS and WPA2 Servers are used for this task,
for safe wireless network. It is mainly associated to provide safe working wireless network.
At last, the developed network is tested with the help of ping network present on the Boson
Netsim.
7

References
[1]"Securing Enterprise Wireless Networks | US-CERT", Us-cert.gov, 2018. [Online].
Available: https://www.us-cert.gov/ncas/tips/ST18-247. [Accessed: 02- Oct- 2018].
[2]"Wireless Security: How to Deploy WPA2-Enterprise", business.com, 2018. [Online].
Available: https://www.business.com/articles/deploying-wpa2-enterprise-encryption/.
[Accessed: 02- Oct- 2018].
[3]"Enterprise wireless LAN security: 802.11 and seamless wireless
roaming", SearchNetworking, 2018. [Online]. Available:
https://searchnetworking.techtarget.com/tutorial/Enterprise-wireless-LAN-security-
80211-and-seamless-wireless-roaming. [Accessed: 02- Oct- 2018].
[4]"Securing Your Wireless Network", Consumer Information, 2018. [Online]. Available:
https://www.consumer.ftc.gov/articles/0013-securing-your-wireless-network.
[Accessed: 02- Oct- 2018].
[5]"Deploying WPA2-Enterprise Wi-Fi Security in Small Businesses", TechGenix, 2018.
[Online]. Available: http://techgenix.com/deploying-wpa2-enterprise-wi-fi-security-
small-businesses/. [Accessed: 02- Oct- 2018].
[6]E. Geier, "5 Ways to Secure Wi-Fi Networks", Network World, 2018. [Online]. Available:
https://www.networkworld.com/article/3224539/mobile-wireless/5-ways-to-secure-
wi-fi-networks.html. [Accessed: 02- Oct- 2018].
[7]"How to implement network security in enterprise network?", Information Security
Newspaper, 2018. [Online]. Available:
http://www.securitynewspaper.com/2016/03/23/implement-network-security-
enterprise-network/. [Accessed: 02- Oct- 2018].
[8]"Wireless Networks Security Privacy And Ethical Issues Computer Science
Essay", UKEssays, 2018. [Online]. Available:
https://www.ukessays.com/essays/computer-science/wireless-networks-security-
privacy-and-ethical-issues-computer-science-essay.php. [Accessed: 02- Oct- 2018].
8
[1]"Securing Enterprise Wireless Networks | US-CERT", Us-cert.gov, 2018. [Online].
Available: https://www.us-cert.gov/ncas/tips/ST18-247. [Accessed: 02- Oct- 2018].
[2]"Wireless Security: How to Deploy WPA2-Enterprise", business.com, 2018. [Online].
Available: https://www.business.com/articles/deploying-wpa2-enterprise-encryption/.
[Accessed: 02- Oct- 2018].
[3]"Enterprise wireless LAN security: 802.11 and seamless wireless
roaming", SearchNetworking, 2018. [Online]. Available:
https://searchnetworking.techtarget.com/tutorial/Enterprise-wireless-LAN-security-
80211-and-seamless-wireless-roaming. [Accessed: 02- Oct- 2018].
[4]"Securing Your Wireless Network", Consumer Information, 2018. [Online]. Available:
https://www.consumer.ftc.gov/articles/0013-securing-your-wireless-network.
[Accessed: 02- Oct- 2018].
[5]"Deploying WPA2-Enterprise Wi-Fi Security in Small Businesses", TechGenix, 2018.
[Online]. Available: http://techgenix.com/deploying-wpa2-enterprise-wi-fi-security-
small-businesses/. [Accessed: 02- Oct- 2018].
[6]E. Geier, "5 Ways to Secure Wi-Fi Networks", Network World, 2018. [Online]. Available:
https://www.networkworld.com/article/3224539/mobile-wireless/5-ways-to-secure-
wi-fi-networks.html. [Accessed: 02- Oct- 2018].
[7]"How to implement network security in enterprise network?", Information Security
Newspaper, 2018. [Online]. Available:
http://www.securitynewspaper.com/2016/03/23/implement-network-security-
enterprise-network/. [Accessed: 02- Oct- 2018].
[8]"Wireless Networks Security Privacy And Ethical Issues Computer Science
Essay", UKEssays, 2018. [Online]. Available:
https://www.ukessays.com/essays/computer-science/wireless-networks-security-
privacy-and-ethical-issues-computer-science-essay.php. [Accessed: 02- Oct- 2018].
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[9]J. Geier, "Wireless LAN Implications, Problems, and Solutions > Security
Vulnerabilities", Ciscopress.com, 2018. [Online]. Available:
http://www.ciscopress.com/articles/article.asp?p=2351131. [Accessed: 02- Oct- 2018].
[10]Y. Xiao, X. Shen and D. Du, Wireless network security. New York: Springer, 2011.
9
Vulnerabilities", Ciscopress.com, 2018. [Online]. Available:
http://www.ciscopress.com/articles/article.asp?p=2351131. [Accessed: 02- Oct- 2018].
[10]Y. Xiao, X. Shen and D. Du, Wireless network security. New York: Springer, 2011.
9
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




