Cybersecurity: Analysis of Secure Network Design Project
VerifiedAdded on 2022/10/11
|29
|5551
|13
Project
AI Summary
This project analyzes a secure network design for a medium-sized organization with a DMZ, web server, and remote access server. The analysis focuses on a denial-of-service (DoS) attack, specifically addressing SYN flood and ICMP flood attacks. The project details the vulnerabilities within the network, including potential misconfigurations of the firewall, the use of unmanaged switches, and compromised vendor credentials. The solution proposes several mitigation strategies, including proper firewall configuration, intrusion detection system (IDS) rules, internet service provider (ISP) intervention, reverse proxy implementation, and web application firewall (WAF) deployment to prevent DoS attacks and protect the web server from malicious traffic. The project emphasizes the importance of a layered security approach to safeguard network resources and ensure service availability. The project also addresses the concept of a compromised vendor's access to the network and how that can lead to a DoS attack.

1
Secure network
Student’s Name:
Institution Affiliation
Secure network
Student’s Name:
Institution Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Abstract
Intrusion detection system target recognizing assaults against PC frameworks and systems or, in
general, against data frameworks. For sure, it is di cult to give provably verify informationffi
systems and to keep up them in such a safe state during their lifetime and use. Sometimes, legacy
or operational limitations don't permit the definition of a completely secure data system.
Therefore, interruption location frameworks have the assignment of observing the use of such
frameworks to detect any nebulous vision of unreliable states. They distinguish endeavors and
dynamic abuse either by authentic clients of the data frameworks or by outer gatherings to
manhandle their benefits or adventure security vulnerabilities. This paper is the first in a two-
section arrangement; it presents the ideas utilized in interruption recognition systems around a
scientific classification. As associations go on the web, various favorable circumstances are
acknowledged and accordingly, scholarly institutions have not been deserted in this move.
Introduction
Denial of Service (DoS) assaults is exceptionally normal in the realm of the web today.
Expanding pace of such assaults has made servers and system gadgets on the web at more
serious hazard than any time in recent memory. Because of a similar reason, associations and
individuals conveying enormous servers and information on the web are presently making more
noteworthy arrangements and speculations to be secure and protect themselves against various
digital assaults including Denial of Service. The conventional design of the World Wide Web is
helpless against genuine sorts of dangers including DoS assaults. The aggressors are currently
speedier in propelling such assaults since they have advanced and mechanized DoS assault
Abstract
Intrusion detection system target recognizing assaults against PC frameworks and systems or, in
general, against data frameworks. For sure, it is di cult to give provably verify informationffi
systems and to keep up them in such a safe state during their lifetime and use. Sometimes, legacy
or operational limitations don't permit the definition of a completely secure data system.
Therefore, interruption location frameworks have the assignment of observing the use of such
frameworks to detect any nebulous vision of unreliable states. They distinguish endeavors and
dynamic abuse either by authentic clients of the data frameworks or by outer gatherings to
manhandle their benefits or adventure security vulnerabilities. This paper is the first in a two-
section arrangement; it presents the ideas utilized in interruption recognition systems around a
scientific classification. As associations go on the web, various favorable circumstances are
acknowledged and accordingly, scholarly institutions have not been deserted in this move.
Introduction
Denial of Service (DoS) assaults is exceptionally normal in the realm of the web today.
Expanding pace of such assaults has made servers and system gadgets on the web at more
serious hazard than any time in recent memory. Because of a similar reason, associations and
individuals conveying enormous servers and information on the web are presently making more
noteworthy arrangements and speculations to be secure and protect themselves against various
digital assaults including Denial of Service. The conventional design of the World Wide Web is
helpless against genuine sorts of dangers including DoS assaults. The aggressors are currently
speedier in propelling such assaults since they have advanced and mechanized DoS assault

3
devices accessible which require insignificant human exertion. The assault plans to deny or
debase typical administrations for genuine clients by sending colossal traffic to the person in
question (machines or systems) to debilitate administrations, association limit or the data
transmission. The given contextual analysis is all about the denial of service assault which is led
from the organization's seller arrange. The authentic clients have whined that they are not ready
to get to the webserver and it is exceptionally moderate. The primer examination recommended
there is a denial of service assault from the seller's system who is keeping up the web server via
online access.
Cyberattack in an organization
The denial of service attack
The denial of service assault is utilized to take every one of the assets of the PC or site with the
goal that authentic clients can't get to that specific site or machine. It is likewise an assault on the
accessibility of the CIA group of three. DoS assaults take commonly one of two structures, they
either flood the administrations of the webserver or crash it;
1. Flooding attacks. includes the age of fake messages to expand traffic on the system for
devouring server's or system's assets(Kenkre, Pai, & Colaco, 2015).
a) SYN flood attack. An SYN flood assault is a sort of denying of-administration assault which
plans to make a server not accessible to real traffic by expending all accessible server data.
How it works
devices accessible which require insignificant human exertion. The assault plans to deny or
debase typical administrations for genuine clients by sending colossal traffic to the person in
question (machines or systems) to debilitate administrations, association limit or the data
transmission. The given contextual analysis is all about the denial of service assault which is led
from the organization's seller arrange. The authentic clients have whined that they are not ready
to get to the webserver and it is exceptionally moderate. The primer examination recommended
there is a denial of service assault from the seller's system who is keeping up the web server via
online access.
Cyberattack in an organization
The denial of service attack
The denial of service assault is utilized to take every one of the assets of the PC or site with the
goal that authentic clients can't get to that specific site or machine. It is likewise an assault on the
accessibility of the CIA group of three. DoS assaults take commonly one of two structures, they
either flood the administrations of the webserver or crash it;
1. Flooding attacks. includes the age of fake messages to expand traffic on the system for
devouring server's or system's assets(Kenkre, Pai, & Colaco, 2015).
a) SYN flood attack. An SYN flood assault is a sort of denying of-administration assault which
plans to make a server not accessible to real traffic by expending all accessible server data.
How it works
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
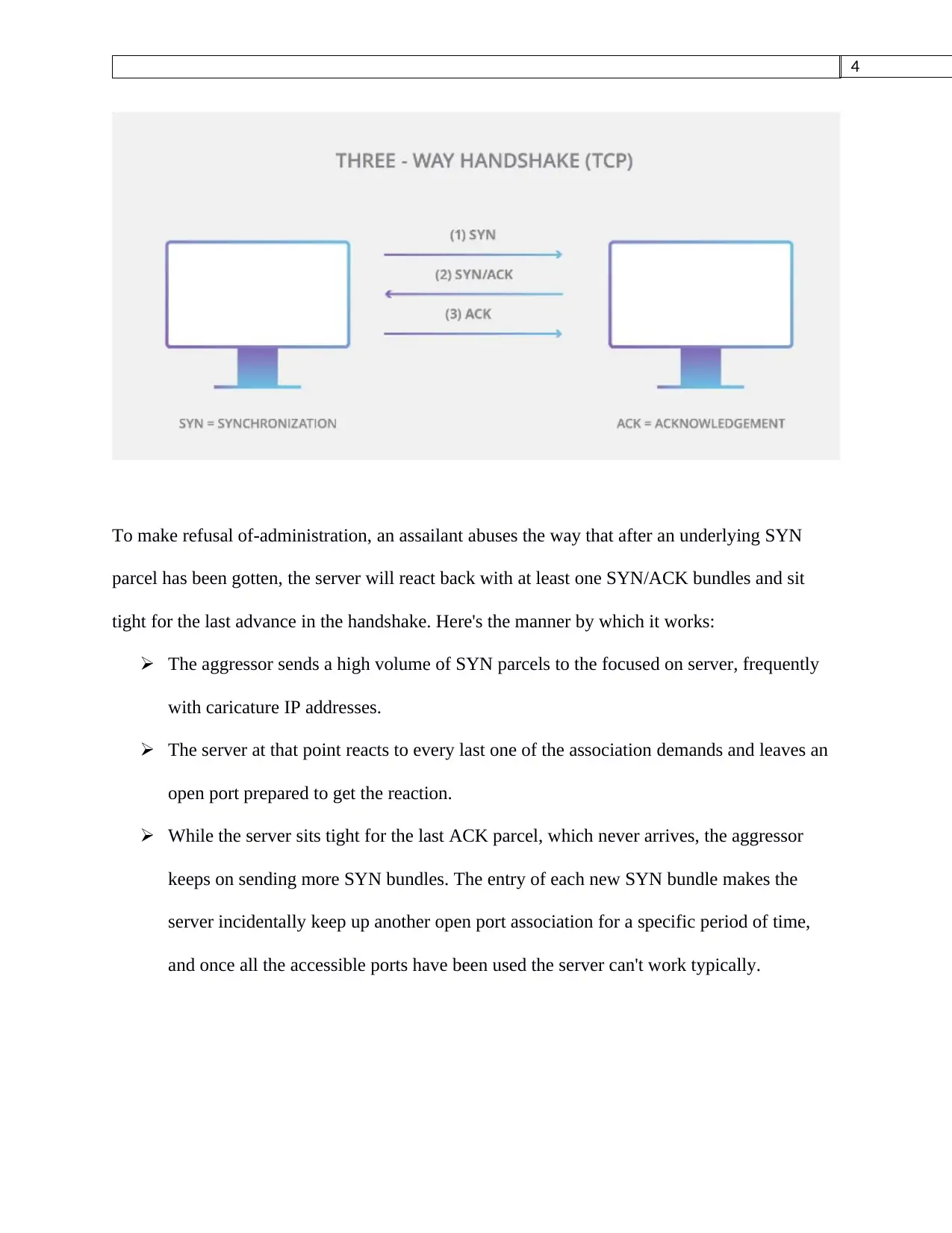
To make refusal of-administration, an assailant abuses the way that after an underlying SYN
parcel has been gotten, the server will react back with at least one SYN/ACK bundles and sit
tight for the last advance in the handshake. Here's the manner by which it works:
The aggressor sends a high volume of SYN parcels to the focused on server, frequently
with caricature IP addresses.
The server at that point reacts to every last one of the association demands and leaves an
open port prepared to get the reaction.
While the server sits tight for the last ACK parcel, which never arrives, the aggressor
keeps on sending more SYN bundles. The entry of each new SYN bundle makes the
server incidentally keep up another open port association for a specific period of time,
and once all the accessible ports have been used the server can't work typically.
To make refusal of-administration, an assailant abuses the way that after an underlying SYN
parcel has been gotten, the server will react back with at least one SYN/ACK bundles and sit
tight for the last advance in the handshake. Here's the manner by which it works:
The aggressor sends a high volume of SYN parcels to the focused on server, frequently
with caricature IP addresses.
The server at that point reacts to every last one of the association demands and leaves an
open port prepared to get the reaction.
While the server sits tight for the last ACK parcel, which never arrives, the aggressor
keeps on sending more SYN bundles. The entry of each new SYN bundle makes the
server incidentally keep up another open port association for a specific period of time,
and once all the accessible ports have been used the server can't work typically.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
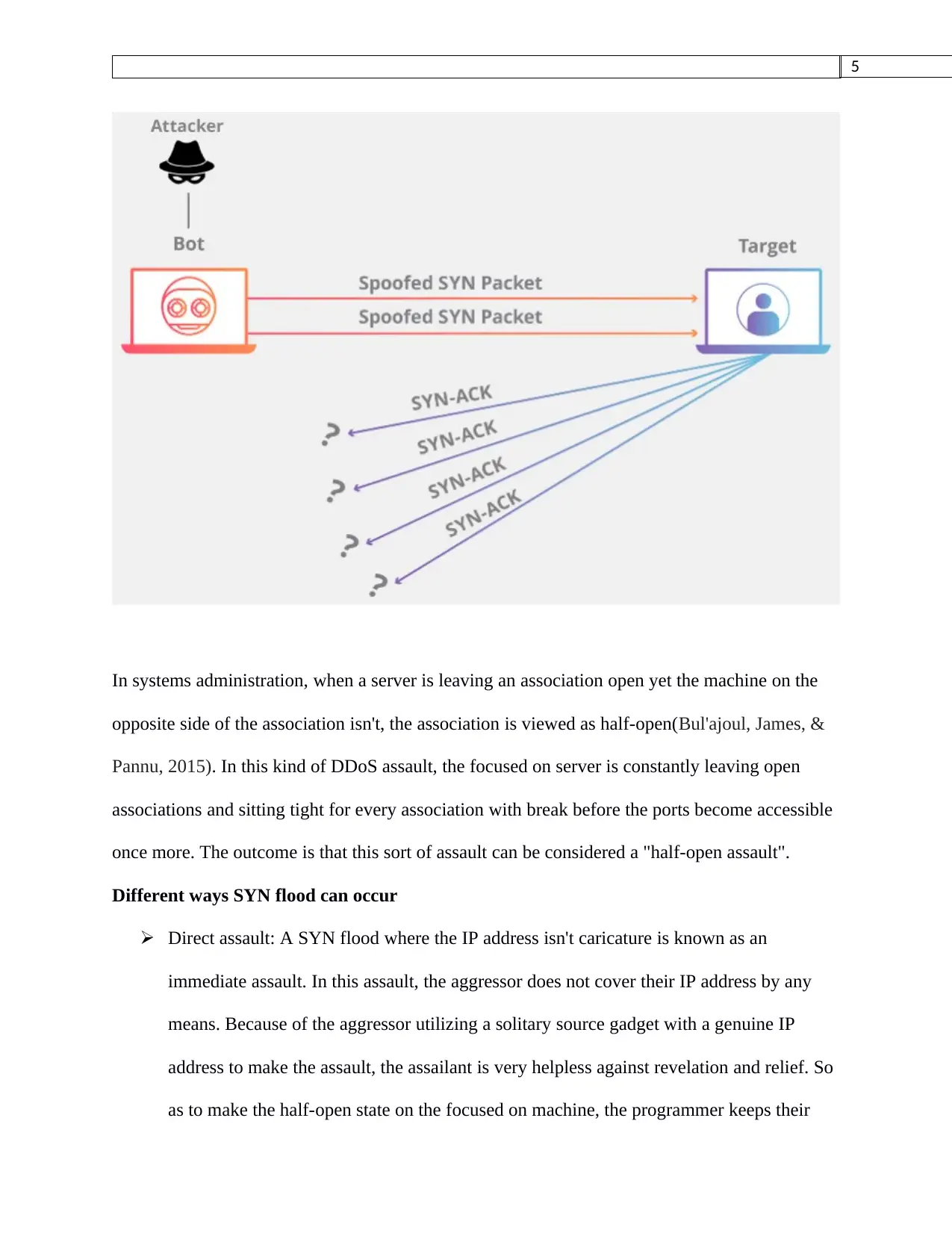
In systems administration, when a server is leaving an association open yet the machine on the
opposite side of the association isn't, the association is viewed as half-open(Bul'ajoul, James, &
Pannu, 2015). In this kind of DDoS assault, the focused on server is constantly leaving open
associations and sitting tight for every association with break before the ports become accessible
once more. The outcome is that this sort of assault can be considered a "half-open assault".
Different ways SYN flood can occur
Direct assault: A SYN flood where the IP address isn't caricature is known as an
immediate assault. In this assault, the aggressor does not cover their IP address by any
means. Because of the aggressor utilizing a solitary source gadget with a genuine IP
address to make the assault, the assailant is very helpless against revelation and relief. So
as to make the half-open state on the focused on machine, the programmer keeps their
In systems administration, when a server is leaving an association open yet the machine on the
opposite side of the association isn't, the association is viewed as half-open(Bul'ajoul, James, &
Pannu, 2015). In this kind of DDoS assault, the focused on server is constantly leaving open
associations and sitting tight for every association with break before the ports become accessible
once more. The outcome is that this sort of assault can be considered a "half-open assault".
Different ways SYN flood can occur
Direct assault: A SYN flood where the IP address isn't caricature is known as an
immediate assault. In this assault, the aggressor does not cover their IP address by any
means. Because of the aggressor utilizing a solitary source gadget with a genuine IP
address to make the assault, the assailant is very helpless against revelation and relief. So
as to make the half-open state on the focused on machine, the programmer keeps their

6
machine from reacting to the server's SYN-ACK bundles. This is regularly accomplished
by firewall decides that quit active parcels other than SYN bundles or by sifting through
any approaching SYN-ACK parcels before they arrive at the vindictive clients machine.
Practically speaking this technique is utilized once in a while (if at any point), as
moderation is genuinely clear – simply hinder the IP address of each malevolent
framework(Aburomman, & Reaz, 2016). On the off chance that the assailant is utilizing a
botnet, for example, the Mirai botnet they won't think about concealing the IP of the
contaminated gadget(Moustafa, Slay, 2015, November).
Mock Attack: A malignant client can likewise parody the IP address on each SYN parcel
they send so as to hinder moderation endeavors and make their character increasingly
hard to find. While the parcels might be mock, those bundles can conceivably be
followed back to their source. It's hard to do this kind of analyst work however it's
certainly feasible, particularly if Internet specialist co-ops (ISPs) are eager to
help(Agarwal, Singh, Jyoti, Vishwanath, & Prashanth, 2016).
Conveyed assault (DDoS): If an assault is made utilizing a botnet the probability of
following the assault back to its source is low. For an additional degree of jumbling, an
aggressor may have each circulated gadget likewise parody the IP addresses from which
it sends bundles. On the off chance that the aggressor is utilizing a botnet, for example,
the Mirai botnet, they for the most part won't think about covering the IP of the tainted
gadget(Aziz, 2016).
Direct assault: A SYN flood where the IP address isn't caricature is known as an immediate
machine from reacting to the server's SYN-ACK bundles. This is regularly accomplished
by firewall decides that quit active parcels other than SYN bundles or by sifting through
any approaching SYN-ACK parcels before they arrive at the vindictive clients machine.
Practically speaking this technique is utilized once in a while (if at any point), as
moderation is genuinely clear – simply hinder the IP address of each malevolent
framework(Aburomman, & Reaz, 2016). On the off chance that the assailant is utilizing a
botnet, for example, the Mirai botnet they won't think about concealing the IP of the
contaminated gadget(Moustafa, Slay, 2015, November).
Mock Attack: A malignant client can likewise parody the IP address on each SYN parcel
they send so as to hinder moderation endeavors and make their character increasingly
hard to find. While the parcels might be mock, those bundles can conceivably be
followed back to their source. It's hard to do this kind of analyst work however it's
certainly feasible, particularly if Internet specialist co-ops (ISPs) are eager to
help(Agarwal, Singh, Jyoti, Vishwanath, & Prashanth, 2016).
Conveyed assault (DDoS): If an assault is made utilizing a botnet the probability of
following the assault back to its source is low. For an additional degree of jumbling, an
aggressor may have each circulated gadget likewise parody the IP addresses from which
it sends bundles. On the off chance that the aggressor is utilizing a botnet, for example,
the Mirai botnet, they for the most part won't think about covering the IP of the tainted
gadget(Aziz, 2016).
Direct assault: A SYN flood where the IP address isn't caricature is known as an immediate
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
assault. In this assault, the aggressor does not cover their IP address by any means. Because of
the aggressor utilizing a solitary source gadget with a genuine IP address to make the assault, the
assailant is very helpless against revelation and relief(Agarwal, Singh, Jyoti, Vishwanath, &
Prashanth, 2016). So as to make the half-open state on the focused on machine, the programmer
keeps their machine from reacting to the server's SYN-ACK bundles. This is regularly
accomplished by firewall decides that quit active parcels other than SYN bundles or by sifting
through any approaching SYN-ACK parcels before they arrive at the vindictive clients machine.
Practically speaking this technique is utilized once in a while (if at any point), as moderation is
genuinely clear – simply hinder the IP address of each malevolent framework. On the off chance
that the assailant is utilizing a botnet, for example, the Mirai botnet they won't think about
concealing the IP of the contaminated gadget(Honig, Howard, Eskin, & Stolfo, 2016).
Mock Attack: A malignant client can likewise parody the IP address on each SYN parcel they
send so as to hinder moderation endeavors and make their character increasingly hard to find.
While the parcels might be mock, those bundles can conceivably be followed back to their
source. It's hard to do this kind of analyst work however it's certainly feasible, particularly if
Internet specialist co-ops (ISPs) are eager to help(Yang, Xu, Gao, Yuan, McLaughlin, & Sezer,
2016).
Conveyed assault (DDoS): If an assault is made utilizing a botnet the probability of following the
assault back to its source is low. For an additional degree of jumbling, an aggressor may have
each circulated gadget likewise parody the IP addresses from which it sends bundles. On the off
chance that the aggressor is utilizing a botnet, for example, the Mirai botnet, they for the most
assault. In this assault, the aggressor does not cover their IP address by any means. Because of
the aggressor utilizing a solitary source gadget with a genuine IP address to make the assault, the
assailant is very helpless against revelation and relief(Agarwal, Singh, Jyoti, Vishwanath, &
Prashanth, 2016). So as to make the half-open state on the focused on machine, the programmer
keeps their machine from reacting to the server's SYN-ACK bundles. This is regularly
accomplished by firewall decides that quit active parcels other than SYN bundles or by sifting
through any approaching SYN-ACK parcels before they arrive at the vindictive clients machine.
Practically speaking this technique is utilized once in a while (if at any point), as moderation is
genuinely clear – simply hinder the IP address of each malevolent framework. On the off chance
that the assailant is utilizing a botnet, for example, the Mirai botnet they won't think about
concealing the IP of the contaminated gadget(Honig, Howard, Eskin, & Stolfo, 2016).
Mock Attack: A malignant client can likewise parody the IP address on each SYN parcel they
send so as to hinder moderation endeavors and make their character increasingly hard to find.
While the parcels might be mock, those bundles can conceivably be followed back to their
source. It's hard to do this kind of analyst work however it's certainly feasible, particularly if
Internet specialist co-ops (ISPs) are eager to help(Yang, Xu, Gao, Yuan, McLaughlin, & Sezer,
2016).
Conveyed assault (DDoS): If an assault is made utilizing a botnet the probability of following the
assault back to its source is low. For an additional degree of jumbling, an aggressor may have
each circulated gadget likewise parody the IP addresses from which it sends bundles. On the off
chance that the aggressor is utilizing a botnet, for example, the Mirai botnet, they for the most
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8
part won't think about covering the IP of the tainted gadget.
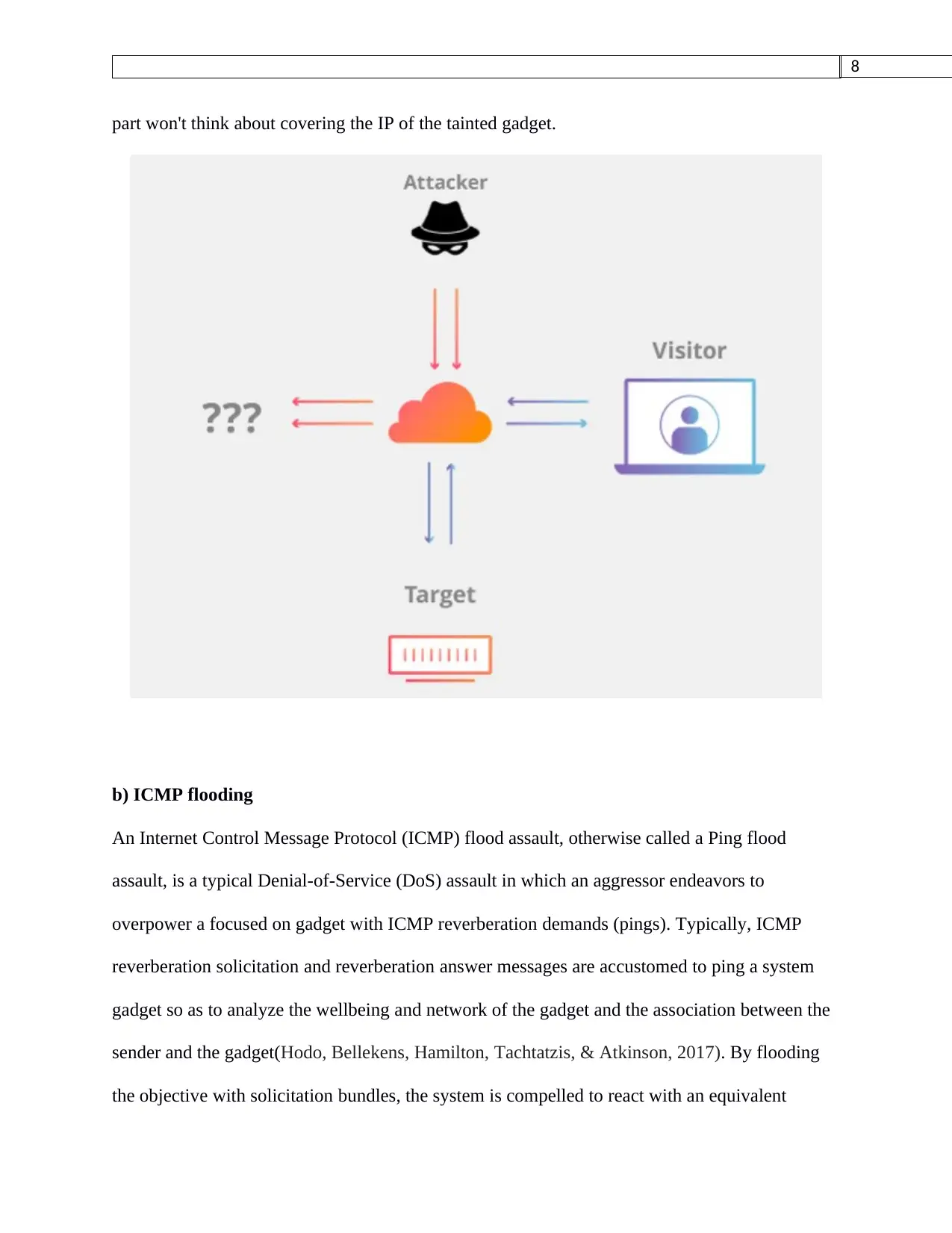
b) ICMP flooding
An Internet Control Message Protocol (ICMP) flood assault, otherwise called a Ping flood
assault, is a typical Denial-of-Service (DoS) assault in which an aggressor endeavors to
overpower a focused on gadget with ICMP reverberation demands (pings). Typically, ICMP
reverberation solicitation and reverberation answer messages are accustomed to ping a system
gadget so as to analyze the wellbeing and network of the gadget and the association between the
sender and the gadget(Hodo, Bellekens, Hamilton, Tachtatzis, & Atkinson, 2017). By flooding
the objective with solicitation bundles, the system is compelled to react with an equivalent
part won't think about covering the IP of the tainted gadget.
b) ICMP flooding
An Internet Control Message Protocol (ICMP) flood assault, otherwise called a Ping flood
assault, is a typical Denial-of-Service (DoS) assault in which an aggressor endeavors to
overpower a focused on gadget with ICMP reverberation demands (pings). Typically, ICMP
reverberation solicitation and reverberation answer messages are accustomed to ping a system
gadget so as to analyze the wellbeing and network of the gadget and the association between the
sender and the gadget(Hodo, Bellekens, Hamilton, Tachtatzis, & Atkinson, 2017). By flooding
the objective with solicitation bundles, the system is compelled to react with an equivalent

9
number of answer parcels. This makes the objective become out of reach to ordinary
traffic(Mahajan, Adagale, & Sahare, 2016).
Others sorts of ICMP solicitation assaults may include custom instruments or code, for example,
hping and scapy. Assault traffic that exudes from various gadgets is viewed as Distributed-
Denial-of-Service (DDoS) assault. In this sort of assault, both approaching and active channels
of the system are overpowering, expending noteworthy transfer speed and bringing about a
forswearing of administration(Daramas, Pattarakitsophon, Eiumtrakul, Tantidham, &
Tamkittikhun, 2016, May).
Assumptions in the network provided
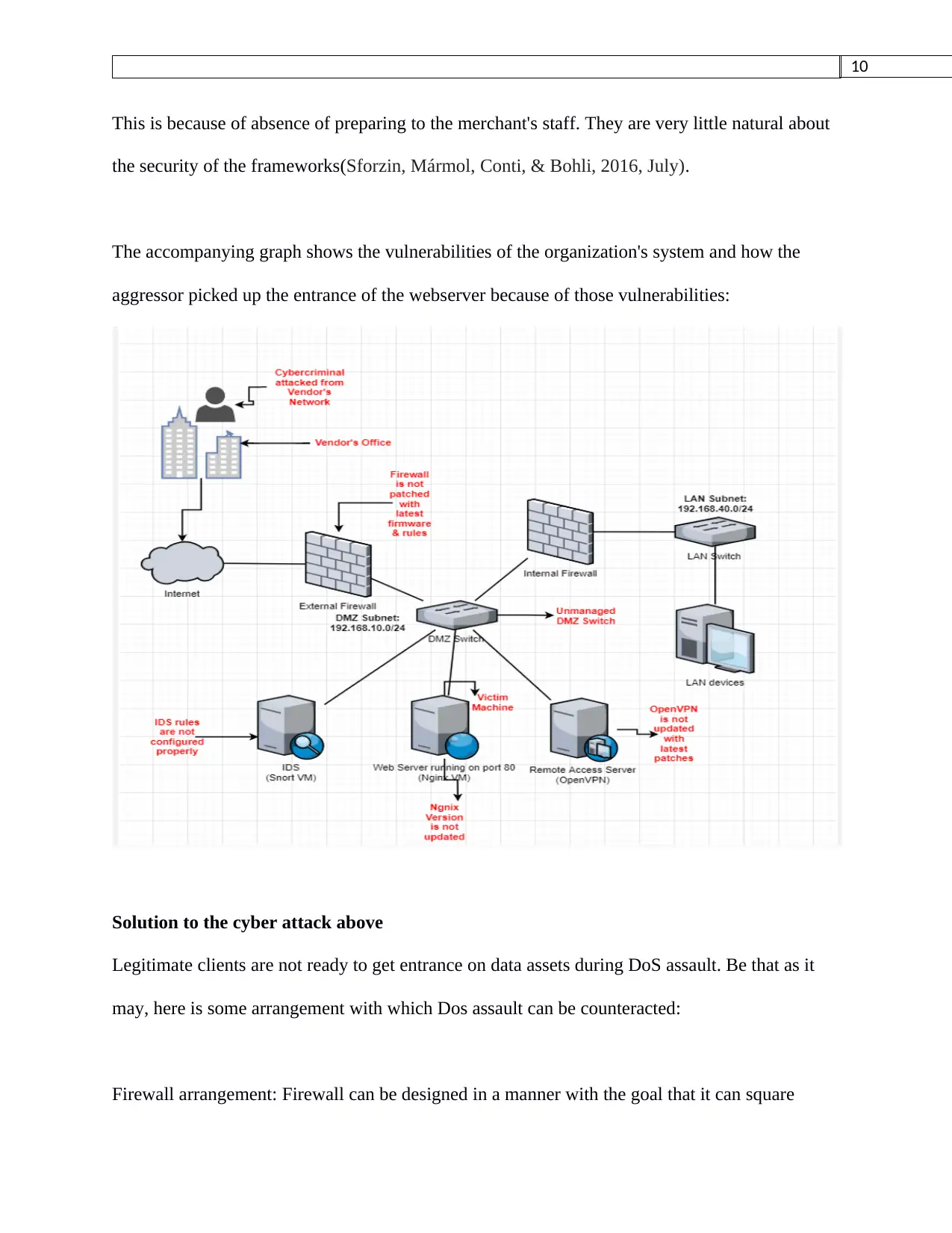
a) Organization's firewall is not configured properly, not fixed to the most recent firmware and
guidelines are additionally not designed appropriately. The most generally perceived firewall
course of action that leaves systems in peril is neglecting to set up early on firewall rules. Exactly
when firewalls are from the start set up, they are consistently left in an 'any to any' status, which
means traffic can develop out of and go to any objective(Gopal, Clark, Wolrich, & Feghali,
2016).
2. They are utilizing the unmanaged switch which is profoundly helpless against the system
assault. On the off chance that the ports of the assailant realize what ports are open in the switch,
he can enter any kind of malware or deal with the system(Alheeti, Gruebler, & McDonald-Maier,
2015, January).
3. Assailant had picked up the accreditations of the OpenVPN from the worker of the merchant.
number of answer parcels. This makes the objective become out of reach to ordinary
traffic(Mahajan, Adagale, & Sahare, 2016).
Others sorts of ICMP solicitation assaults may include custom instruments or code, for example,
hping and scapy. Assault traffic that exudes from various gadgets is viewed as Distributed-
Denial-of-Service (DDoS) assault. In this sort of assault, both approaching and active channels
of the system are overpowering, expending noteworthy transfer speed and bringing about a
forswearing of administration(Daramas, Pattarakitsophon, Eiumtrakul, Tantidham, &
Tamkittikhun, 2016, May).
Assumptions in the network provided
a) Organization's firewall is not configured properly, not fixed to the most recent firmware and
guidelines are additionally not designed appropriately. The most generally perceived firewall
course of action that leaves systems in peril is neglecting to set up early on firewall rules. Exactly
when firewalls are from the start set up, they are consistently left in an 'any to any' status, which
means traffic can develop out of and go to any objective(Gopal, Clark, Wolrich, & Feghali,
2016).
2. They are utilizing the unmanaged switch which is profoundly helpless against the system
assault. On the off chance that the ports of the assailant realize what ports are open in the switch,
he can enter any kind of malware or deal with the system(Alheeti, Gruebler, & McDonald-Maier,
2015, January).
3. Assailant had picked up the accreditations of the OpenVPN from the worker of the merchant.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
This is because of absence of preparing to the merchant's staff. They are very little natural about
the security of the frameworks(Sforzin, Mármol, Conti, & Bohli, 2016, July).
The accompanying graph shows the vulnerabilities of the organization's system and how the
aggressor picked up the entrance of the webserver because of those vulnerabilities:
Solution to the cyber attack above
Legitimate clients are not ready to get entrance on data assets during DoS assault. Be that as it
may, here is some arrangement with which Dos assault can be counteracted:
Firewall arrangement: Firewall can be designed in a manner with the goal that it can square
This is because of absence of preparing to the merchant's staff. They are very little natural about
the security of the frameworks(Sforzin, Mármol, Conti, & Bohli, 2016, July).
The accompanying graph shows the vulnerabilities of the organization's system and how the
aggressor picked up the entrance of the webserver because of those vulnerabilities:
Solution to the cyber attack above
Legitimate clients are not ready to get entrance on data assets during DoS assault. Be that as it
may, here is some arrangement with which Dos assault can be counteracted:
Firewall arrangement: Firewall can be designed in a manner with the goal that it can square
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
assault. There are a few decides in design that can stop DoS assault(Anwar, Mohamad Zain,
Zolkipli, Inayat, Khan, Anthony, & Chang, 2017).
IDS Configuration: We can tweak the IDS rules which are found in local.rules in/and so
on/grunt/rules/catalog. In this arrangement record we can compose the principles like which is
the kind of the assault, need can be set, interim of the parcels can be set as appeared in the image
underneath
ISP: Internet specialist organization (ISP) can be another way to deal with stop DoS assault as
ISP can square traffic towards unfortunate casualty and direct that traffic to waste. Along these
lines, by diverting traffic ISP can stop DoS assault to happen(Alsubhi, 2016).
Switch Proxy: it is a server that put between web server and customer and aloe simply approved
clients to connect web server and other data assets in the system. By blocking unapproved clients
to get to assets DoS assault can be averted.
WAF: Web Application Firewall (WAF) is a sort of firewall that screen and can prevent
information stream from web server to customer and from customer to web server. WAF is of
three kinds; arrange based, have based, and cloud based. it sits among customer and web server
and shield web server from assault. There are various arrangements as per which WAF works
and channel pernicious traffic. It stops DoS assault by blocking HTTP traffic.
Interruption counteractive action framework (IPS): Similar to IDS it checks and channel
assault. There are a few decides in design that can stop DoS assault(Anwar, Mohamad Zain,
Zolkipli, Inayat, Khan, Anthony, & Chang, 2017).
IDS Configuration: We can tweak the IDS rules which are found in local.rules in/and so
on/grunt/rules/catalog. In this arrangement record we can compose the principles like which is
the kind of the assault, need can be set, interim of the parcels can be set as appeared in the image
underneath
ISP: Internet specialist organization (ISP) can be another way to deal with stop DoS assault as
ISP can square traffic towards unfortunate casualty and direct that traffic to waste. Along these
lines, by diverting traffic ISP can stop DoS assault to happen(Alsubhi, 2016).
Switch Proxy: it is a server that put between web server and customer and aloe simply approved
clients to connect web server and other data assets in the system. By blocking unapproved clients
to get to assets DoS assault can be averted.
WAF: Web Application Firewall (WAF) is a sort of firewall that screen and can prevent
information stream from web server to customer and from customer to web server. WAF is of
three kinds; arrange based, have based, and cloud based. it sits among customer and web server
and shield web server from assault. There are various arrangements as per which WAF works
and channel pernicious traffic. It stops DoS assault by blocking HTTP traffic.
Interruption counteractive action framework (IPS): Similar to IDS it checks and channel
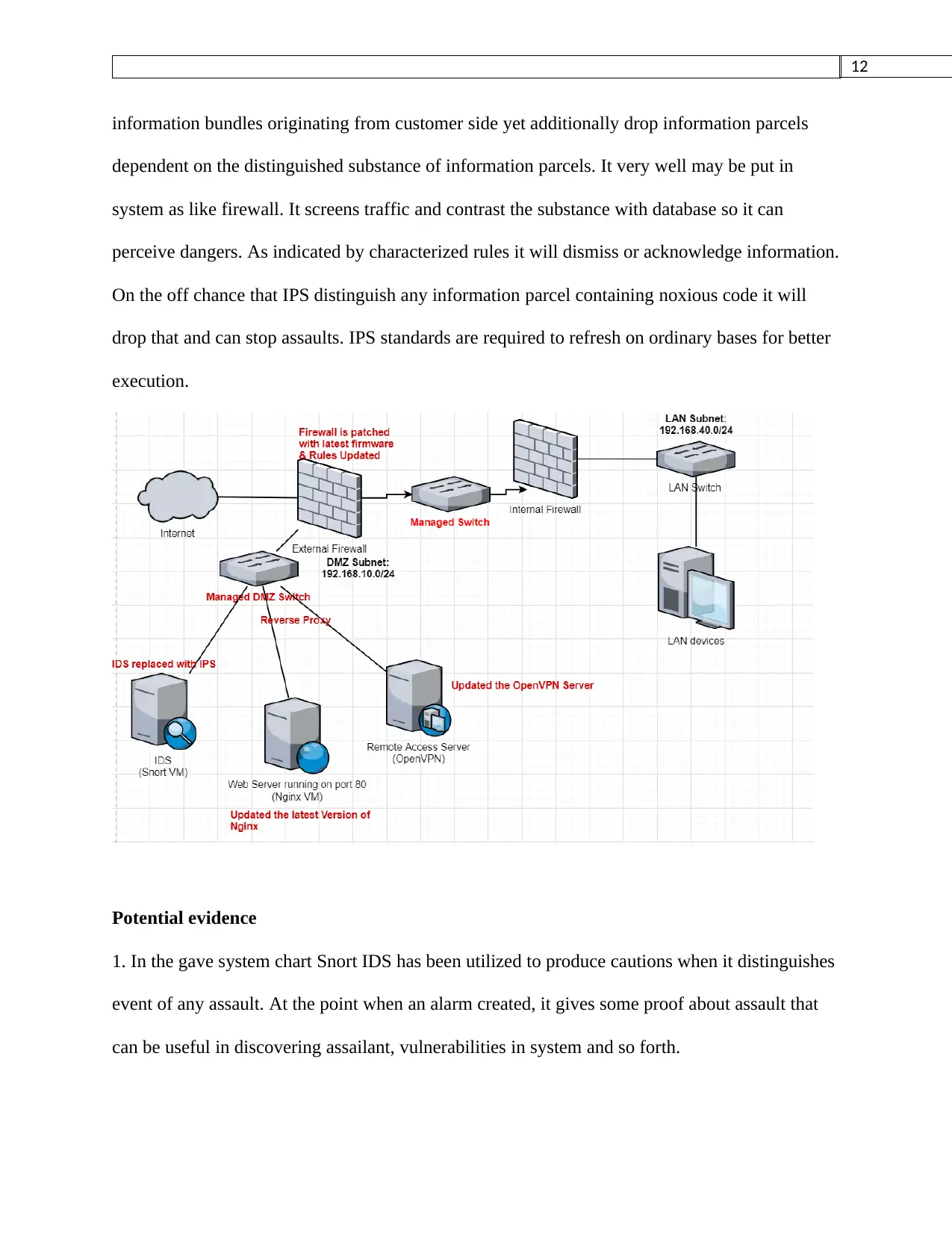
12
information bundles originating from customer side yet additionally drop information parcels
dependent on the distinguished substance of information parcels. It very well may be put in
system as like firewall. It screens traffic and contrast the substance with database so it can
perceive dangers. As indicated by characterized rules it will dismiss or acknowledge information.
On the off chance that IPS distinguish any information parcel containing noxious code it will
drop that and can stop assaults. IPS standards are required to refresh on ordinary bases for better
execution.
Potential evidence
1. In the gave system chart Snort IDS has been utilized to produce cautions when it distinguishes
event of any assault. At the point when an alarm created, it gives some proof about assault that
can be useful in discovering assailant, vulnerabilities in system and so forth.
information bundles originating from customer side yet additionally drop information parcels
dependent on the distinguished substance of information parcels. It very well may be put in
system as like firewall. It screens traffic and contrast the substance with database so it can
perceive dangers. As indicated by characterized rules it will dismiss or acknowledge information.
On the off chance that IPS distinguish any information parcel containing noxious code it will
drop that and can stop assaults. IPS standards are required to refresh on ordinary bases for better
execution.
Potential evidence
1. In the gave system chart Snort IDS has been utilized to produce cautions when it distinguishes
event of any assault. At the point when an alarm created, it gives some proof about assault that
can be useful in discovering assailant, vulnerabilities in system and so forth.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 29
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





