INCS-735: Secure Software Engineering: Core Security Concepts Overview
VerifiedAdded on 2022/11/25
|41
|6066
|423
Homework Assignment
AI Summary
This assignment introduces core concepts in secure software engineering, including discussions on C programming, software configuration, and software reuse. It covers the fundamentals of software development, program environments, and development tools. The document explores the software development lifecycle, emphasizing analysis, design, programming, testing, and deployment phases. Key topics such as software architecture, program development tools, and the importance of reusing code are highlighted. The assignment also touches on configuration management, software attacks, and the role of configuration files, command-line arguments, and shell variables. It emphasizes the importance of secure coding practices, including the use of libraries and the application of software engineering rules. The assignment concludes with a discussion of compilation, programming languages, and the challenges associated with software development, emphasizing the importance of secure coding and system protection.

ARTICLE REWRITE / TYPING
735-I-1
Secure Software Engineering
Introduction
INCS-735 Secure Software Engineering
Core Security Courses
CSCI-620: OS Security (System security)
INCS 615: Net Assets Protection from intrusion (NetSec)
INCS-735: Sec SE (Security of application programs)
INCS- 745: Intrusion Detection (Pato Gatsy) [NetSec after Security Intrusion)
Topics
From Outside Shell or API View
From Inside: Intervals view
Question: Who uses shells? Users of programs via shell commands (command lines)
All digital computers operate on 2-level voltage levies (written on paper as 2-symbols ‘1’ or ‘0’)
where 1 is the first level and 0 id the second level. 1 (2,3) is arithmetic (+) while the 0 is algebra (+,
-).
Graphical symbols
Binding coding symbols are used because it is too long to write, for instance, one million times (too
high > true, too low> false 1;0): This is the shortest most robust mix-up. The binary coding symbols
are used for developing new codes, both low level and high level codes .
1.. Data Codes
2. No lecture on instruction codes (minimal services)
735-I-1
Secure Software Engineering
Introduction
INCS-735 Secure Software Engineering
Core Security Courses
CSCI-620: OS Security (System security)
INCS 615: Net Assets Protection from intrusion (NetSec)
INCS-735: Sec SE (Security of application programs)
INCS- 745: Intrusion Detection (Pato Gatsy) [NetSec after Security Intrusion)
Topics
From Outside Shell or API View
From Inside: Intervals view
Question: Who uses shells? Users of programs via shell commands (command lines)
All digital computers operate on 2-level voltage levies (written on paper as 2-symbols ‘1’ or ‘0’)
where 1 is the first level and 0 id the second level. 1 (2,3) is arithmetic (+) while the 0 is algebra (+,
-).
Graphical symbols
Binding coding symbols are used because it is too long to write, for instance, one million times (too
high > true, too low> false 1;0): This is the shortest most robust mix-up. The binary coding symbols
are used for developing new codes, both low level and high level codes .
1.. Data Codes
2. No lecture on instruction codes (minimal services)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ARTICLE REWRITE / TYPING
735-I-1
Courses in CSCI-691/741 and possibly in ASSEMBLY PROGRAMMING CLASSES)
Example: SANS Institute class on ASSEMBLY hacking
3. Basiscs of program Development (620+)
4. Programming Context / environment (OS of Virtual Machine)
Mac OS (BSD Kernel), Linux (AII -line Kernel)
UNIX line OSS- same shell.
5. Program Development Tools
6. Phase I: C-Programming (FOP)
Phase II: Java Programming (OOP)
Phase III: Wes Programming (Javascript programming) (OB-onject based)
Question: Most used programs in the world
Answer: At Development Time
C Static / Compile Time)
Java (Back End bond enterprises servers IM&+) or Javascript (Front end bond 100K$) -
productivity fast programming at runtime by user. These languages enable fast programming and
are more reliable with fewer bugs inherent in them.
7. Development phases- Analysis: Learning about problem at a project
Software architecture- Design view: Planning programming (not doing the actual programming).
Software engineering- Programming: language development – code view
Testing- user view
Deploy/ roll-out: System is external- Admin view/ command lines
735-I-1
Courses in CSCI-691/741 and possibly in ASSEMBLY PROGRAMMING CLASSES)
Example: SANS Institute class on ASSEMBLY hacking
3. Basiscs of program Development (620+)
4. Programming Context / environment (OS of Virtual Machine)
Mac OS (BSD Kernel), Linux (AII -line Kernel)
UNIX line OSS- same shell.
5. Program Development Tools
6. Phase I: C-Programming (FOP)
Phase II: Java Programming (OOP)
Phase III: Wes Programming (Javascript programming) (OB-onject based)
Question: Most used programs in the world
Answer: At Development Time
C Static / Compile Time)
Java (Back End bond enterprises servers IM&+) or Javascript (Front end bond 100K$) -
productivity fast programming at runtime by user. These languages enable fast programming and
are more reliable with fewer bugs inherent in them.
7. Development phases- Analysis: Learning about problem at a project
Software architecture- Design view: Planning programming (not doing the actual programming).
Software engineering- Programming: language development – code view
Testing- user view
Deploy/ roll-out: System is external- Admin view/ command lines

ARTICLE REWRITE / TYPING
735-I-1
Internal view- Maintain/ administer / options for user software (DB Admin) -User view [Admin
DBMS system].
8. The most used finished program?
How to re-use software (developer) – Libraries
Frameworks (??)
Software object
Fast development – quick to the market/ customer : Reuse, reuse, reuse, whenever possible, reuse is
a fundamental principle of software engineering (SE).
Old workplace
Other people’s work
Old knowledge
Other people’s knowledge [consultants, sub-contractors, friends (Blogs)]
Professor: Dr. Bill Mina Tovic / Michaelson
Cell : 917 693 8173
Questions and Answers: billmic@gmail.com
Homework: dr.bill.unit@gmail.com
802LL – Metro
Testing, Grading
4 x Quiz 4x 30%
1 -midterm 15%
1 Final 10%
735-I-1
Internal view- Maintain/ administer / options for user software (DB Admin) -User view [Admin
DBMS system].
8. The most used finished program?
How to re-use software (developer) – Libraries
Frameworks (??)
Software object
Fast development – quick to the market/ customer : Reuse, reuse, reuse, whenever possible, reuse is
a fundamental principle of software engineering (SE).
Old workplace
Other people’s work
Old knowledge
Other people’s knowledge [consultants, sub-contractors, friends (Blogs)]
Professor: Dr. Bill Mina Tovic / Michaelson
Cell : 917 693 8173
Questions and Answers: billmic@gmail.com
Homework: dr.bill.unit@gmail.com
802LL – Metro
Testing, Grading
4 x Quiz 4x 30%
1 -midterm 15%
1 Final 10%
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ARTICLE REWRITE / TYPING
735-I-1
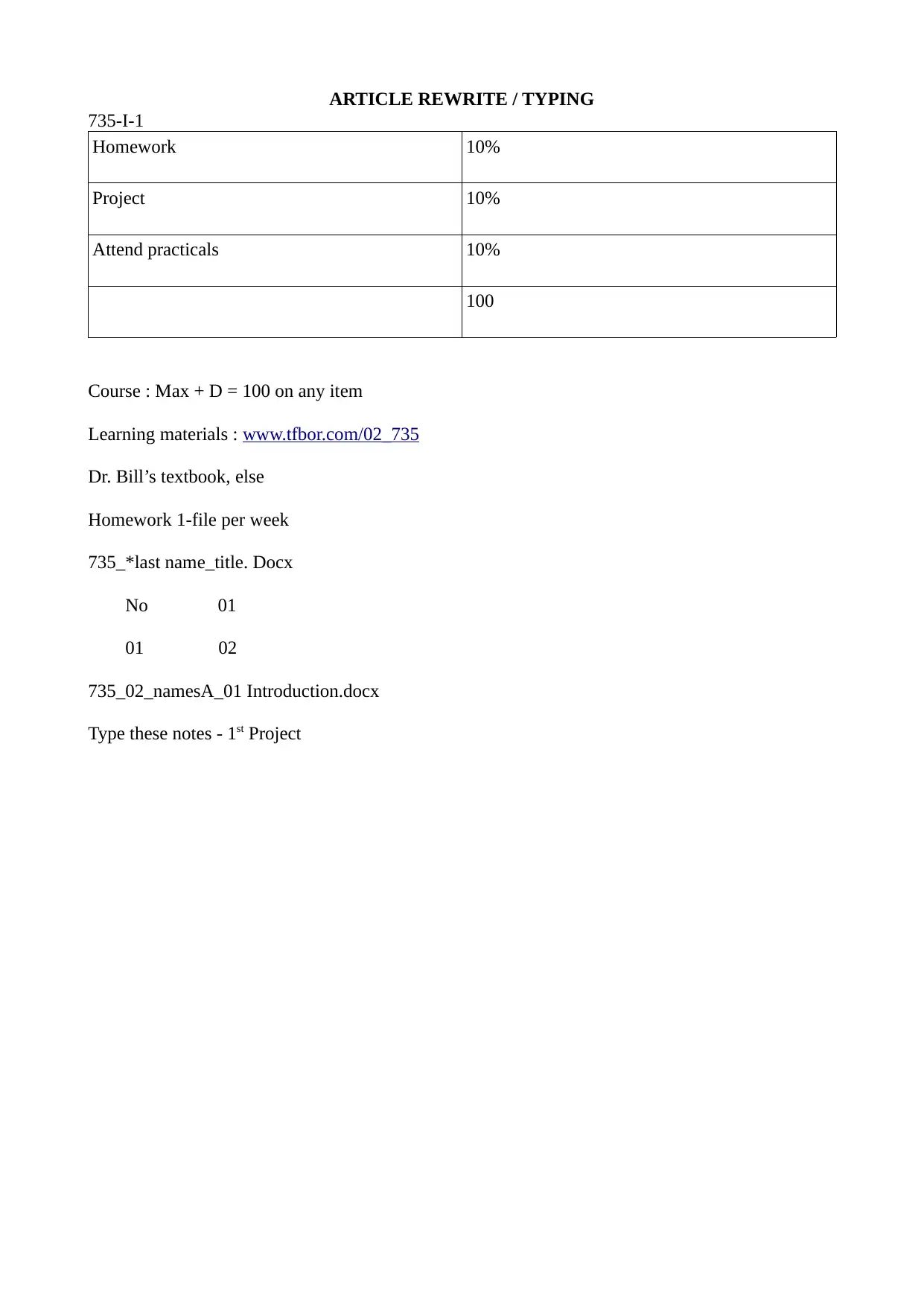
Homework 10%
Project 10%
Attend practicals 10%
100
Course : Max + D = 100 on any item
Learning materials : www.tfbor.com/02_735
Dr. Bill’s textbook, else
Homework 1-file per week
735_*last name_title. Docx
No 01
01 02
735_02_namesA_01 Introduction.docx
Type these notes - 1st Project
735-I-1
Homework 10%
Project 10%
Attend practicals 10%
100
Course : Max + D = 100 on any item
Learning materials : www.tfbor.com/02_735
Dr. Bill’s textbook, else
Homework 1-file per week
735_*last name_title. Docx
No 01
01 02
735_02_namesA_01 Introduction.docx
Type these notes - 1st Project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ARTICLE REWRITE / TYPING
735-I-1
Introduction
There is a popular statement in software development circles that reliable software does what it is
intended to do and nothing else. But how does one get to this point and claim excellence in software
engineering? Each year, there are a plethora of vulnerabilities that are exposed in various software,
form popular operating systems to specialized software such as those used in financial applications
and this suggests that the adage that ‘reliable software only does what it is intended to do and
nothing else’ is far from being achieved. The question then is, does it mean developers do not know
how to develop secure software or they just do not fully implement what is necessary to achieve
secure software? Th SOFtware Engineering institute (SEI) clearly distinguishes between
engineering work and artisanal work in its five stage software maturity model;
Ad hoc heroics and individual effort
Repeatable
Defined
managed, and
Optimized
Artisanal work is dependent entirely on a developers’ unique skills and an organizations personnel
levels while engineering work in the context of software is objective and independent from one’s
perception; it also does not require unique skills. Engineering work is predictable, reproducible, and
systematic. A common error in software design is the creating of lists of ‘bad’ characters and inputs,
or any other undesirable things, creating a black list: this approach usually fails since there is
incomplete enumeration and because removing ‘bad’ characters from a software development
project can easily lead to other bad inputs being produced if they are not detected or identified. The
black lists also fail since they are based upon previous experience and only the ‘known’ bad inputs
are enumerated
735-I-1
Introduction
There is a popular statement in software development circles that reliable software does what it is
intended to do and nothing else. But how does one get to this point and claim excellence in software
engineering? Each year, there are a plethora of vulnerabilities that are exposed in various software,
form popular operating systems to specialized software such as those used in financial applications
and this suggests that the adage that ‘reliable software only does what it is intended to do and
nothing else’ is far from being achieved. The question then is, does it mean developers do not know
how to develop secure software or they just do not fully implement what is necessary to achieve
secure software? Th SOFtware Engineering institute (SEI) clearly distinguishes between
engineering work and artisanal work in its five stage software maturity model;
Ad hoc heroics and individual effort
Repeatable
Defined
managed, and
Optimized
Artisanal work is dependent entirely on a developers’ unique skills and an organizations personnel
levels while engineering work in the context of software is objective and independent from one’s
perception; it also does not require unique skills. Engineering work is predictable, reproducible, and
systematic. A common error in software design is the creating of lists of ‘bad’ characters and inputs,
or any other undesirable things, creating a black list: this approach usually fails since there is
incomplete enumeration and because removing ‘bad’ characters from a software development
project can easily lead to other bad inputs being produced if they are not detected or identified. The
black lists also fail since they are based upon previous experience and only the ‘known’ bad inputs
are enumerated

ARTICLE REWRITE / TYPING
735-I-1
Memory map objects
Q. Software
A. Programs and data
Q. What is software made of?
A. A+ At runtime (in memory) “FUNCTIONS” and “VARIABLES” loaded
A+ Compile time (of files) [programs and data] Install/ roll out time (in storage / HDS)
Software is made of a series of instructions that perform specific tasks; there are two main software
categories- application software and system software. Modules make up the software of which
modules can be code written by programmers or external libraries (Oram and Wilson 65).
Q. Data?
A. Constants / values of some type/ code (encoded)
Some fort of binary code (JP^, ^IF, TiFF, int, Float
Data models are abstract models which organize organizes data elements and standardizes the
relationships between them (Maguire)
Q. Variable?
A. Memory location of of Type / code , and size; they are names used or holding or or more values
such that instead of having to repeat the values in several places within the code, the variables are
used, for example to hold calculation results or other values (Slavin).
..
735-I-1
Memory map objects
Q. Software
A. Programs and data
Q. What is software made of?
A. A+ At runtime (in memory) “FUNCTIONS” and “VARIABLES” loaded
A+ Compile time (of files) [programs and data] Install/ roll out time (in storage / HDS)
Software is made of a series of instructions that perform specific tasks; there are two main software
categories- application software and system software. Modules make up the software of which
modules can be code written by programmers or external libraries (Oram and Wilson 65).
Q. Data?
A. Constants / values of some type/ code (encoded)
Some fort of binary code (JP^, ^IF, TiFF, int, Float
Data models are abstract models which organize organizes data elements and standardizes the
relationships between them (Maguire)
Q. Variable?
A. Memory location of of Type / code , and size; they are names used or holding or or more values
such that instead of having to repeat the values in several places within the code, the variables are
used, for example to hold calculation results or other values (Slavin).
..
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ARTICLE REWRITE / TYPING
735-I-1
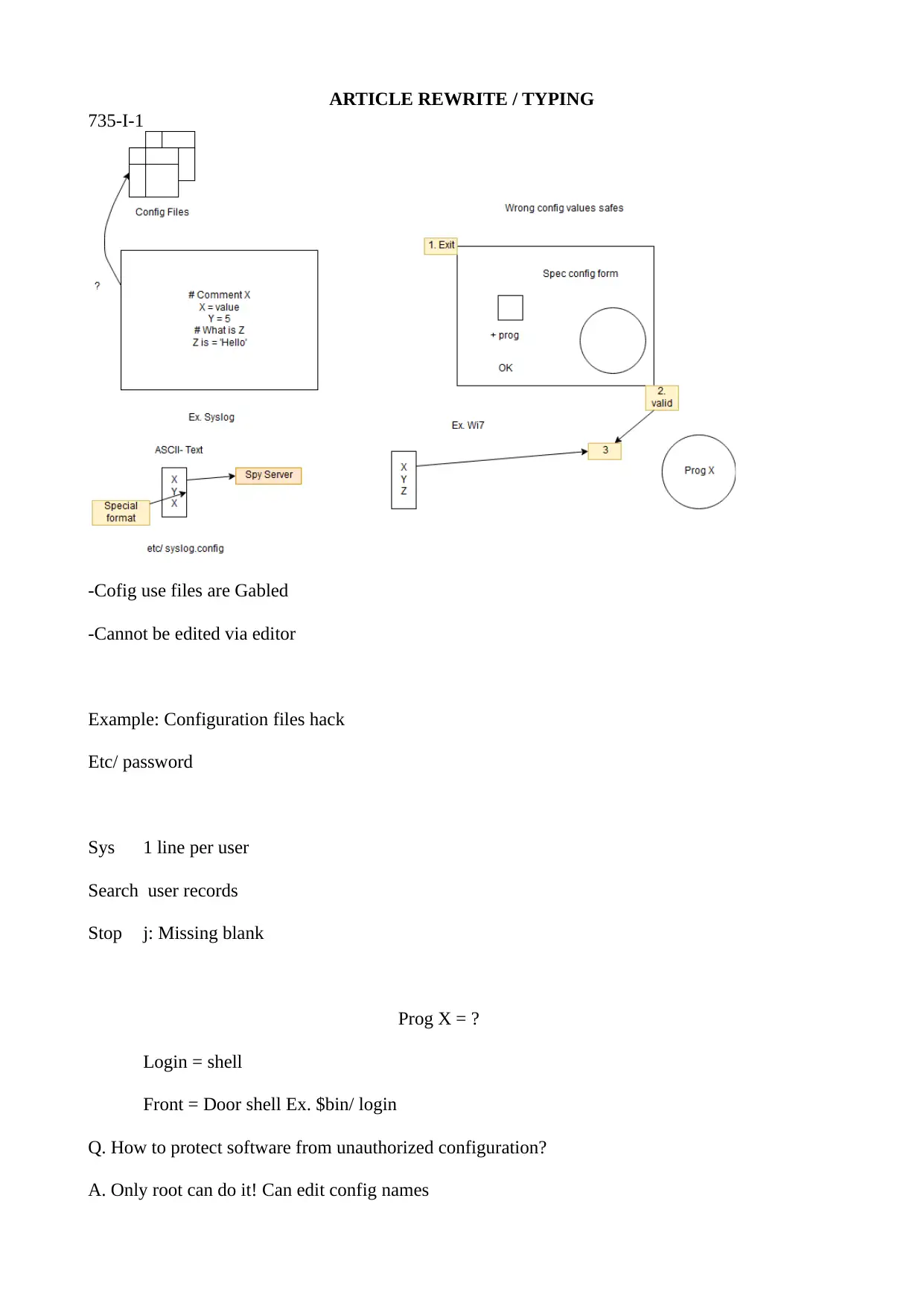
-Cofig use files are Gabled
-Cannot be edited via editor
Example: Configuration files hack
Etc/ password
Sys 1 line per user
Search user records
Stop j: Missing blank
Prog X = ?
Login = shell
Front = Door shell Ex. $bin/ login
Q. How to protect software from unauthorized configuration?
A. Only root can do it! Can edit config names
735-I-1
-Cofig use files are Gabled
-Cannot be edited via editor
Example: Configuration files hack
Etc/ password
Sys 1 line per user
Search user records
Stop j: Missing blank
Prog X = ?
Login = shell
Front = Door shell Ex. $bin/ login
Q. How to protect software from unauthorized configuration?
A. Only root can do it! Can edit config names
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ARTICLE REWRITE / TYPING
735-I-1
-Protect root and never run programs from the root as this can be exploited and allow attackers to
gain root privileges and exploit the software (Jones).
-Not have root but have special admin user that can;
Install and
Configure (change installed config programs)
Example: RBAC (role based access control) or similar; RBAC is a way of restricting network
access based on individual user roles with the enterprise. It lets users enjoy access rights only to the
resources they are authorized to access while preventing access to privileged information (Rouse)
Every software needs – configuration (external)
“Application sys” data (Not Operating system)
Meta data, (not job data) – side data
-Resource data : data needed for program to operate regardless of configuration.
Example: Sound files in game programs (zys, boom…)
Side files
?? [Places program function] Input/ Output (I/O) exiles –speakers – discover
Q. How cab programs get configuration data and when?
A. At load time!
[X = 10] 1. Reading configuration file
[x = 11] 2. Reading its mother-shell (program that starts application as a child) VARIABLES (#echo
$ X)
735-I-1
-Protect root and never run programs from the root as this can be exploited and allow attackers to
gain root privileges and exploit the software (Jones).
-Not have root but have special admin user that can;
Install and
Configure (change installed config programs)
Example: RBAC (role based access control) or similar; RBAC is a way of restricting network
access based on individual user roles with the enterprise. It lets users enjoy access rights only to the
resources they are authorized to access while preventing access to privileged information (Rouse)
Every software needs – configuration (external)
“Application sys” data (Not Operating system)
Meta data, (not job data) – side data
-Resource data : data needed for program to operate regardless of configuration.
Example: Sound files in game programs (zys, boom…)
Side files
?? [Places program function] Input/ Output (I/O) exiles –speakers – discover
Q. How cab programs get configuration data and when?
A. At load time!
[X = 10] 1. Reading configuration file
[x = 11] 2. Reading its mother-shell (program that starts application as a child) VARIABLES (#echo
$ X)
ARTICLE REWRITE / TYPING
735-I-1
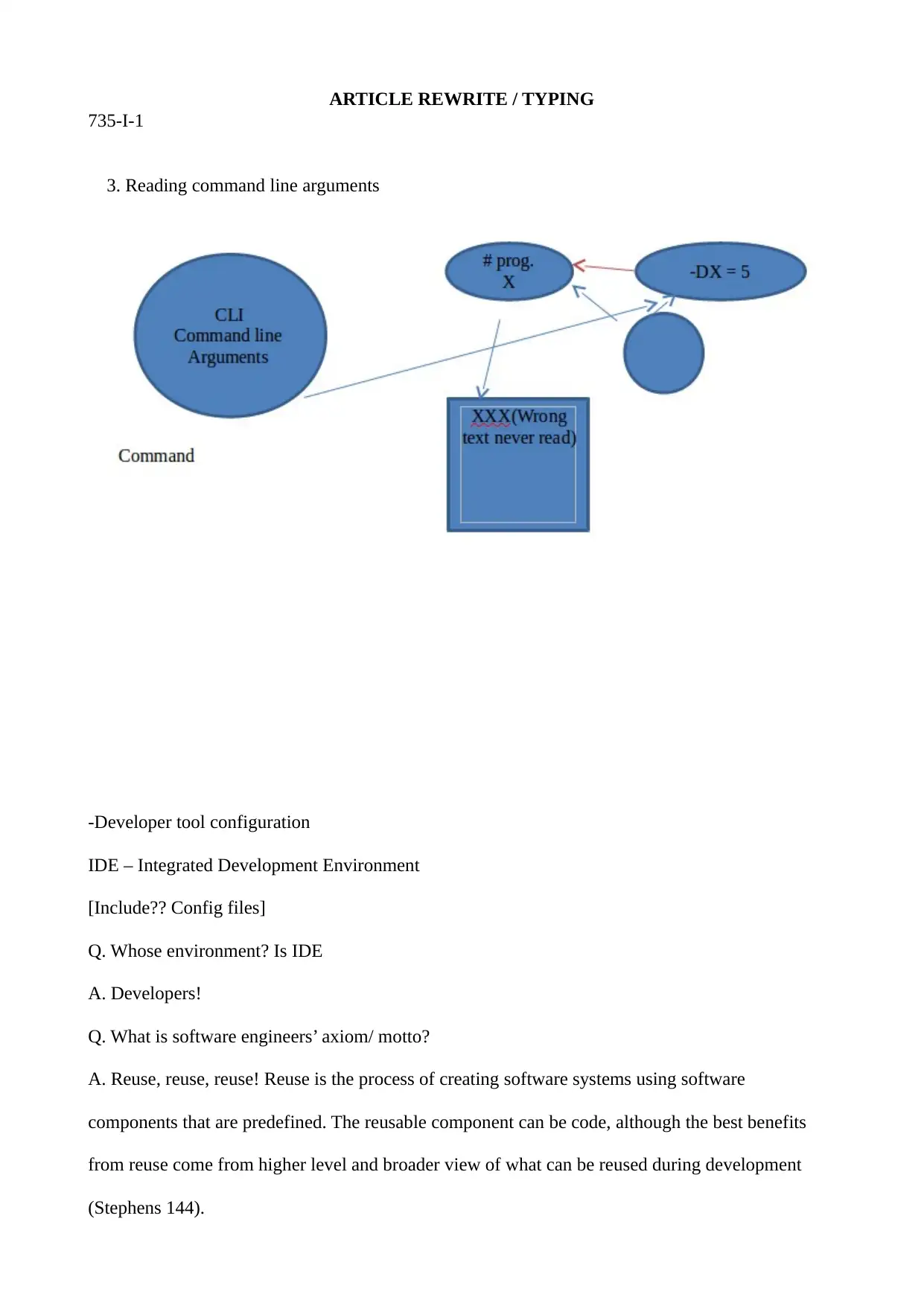
3. Reading command line arguments
-Developer tool configuration
IDE – Integrated Development Environment
[Include?? Config files]
Q. Whose environment? Is IDE
A. Developers!
Q. What is software engineers’ axiom/ motto?
A. Reuse, reuse, reuse! Reuse is the process of creating software systems using software
components that are predefined. The reusable component can be code, although the best benefits
from reuse come from higher level and broader view of what can be reused during development
(Stephens 144).
735-I-1
3. Reading command line arguments
-Developer tool configuration
IDE – Integrated Development Environment
[Include?? Config files]
Q. Whose environment? Is IDE
A. Developers!
Q. What is software engineers’ axiom/ motto?
A. Reuse, reuse, reuse! Reuse is the process of creating software systems using software
components that are predefined. The reusable component can be code, although the best benefits
from reuse come from higher level and broader view of what can be reused during development
(Stephens 144).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ARTICLE REWRITE / TYPING
735-I-1
Q. Initially, what C can developer (C/ C++) reuse?
A. Object code in a form of libraries using LINKER as a tool!
X. lib
OGL
Trust!!!
A. Source code (C-Text) in a form of ASCII-files using PRE-PROCESSOR as a tool! 3GL
“linker”
Reuse source ASCII code file
3GL
2 GL
-Library [x. obj] and header files
OGL – Standard - for all/ everybody needs it
- Nonstandard – Some only/ exotic applications
Q. True or false?
0 – OK, 1 – BAD shell (+25)
735-I-1
Q. Initially, what C can developer (C/ C++) reuse?
A. Object code in a form of libraries using LINKER as a tool!
X. lib
OGL
Trust!!!
A. Source code (C-Text) in a form of ASCII-files using PRE-PROCESSOR as a tool! 3GL
“linker”
Reuse source ASCII code file
3GL
2 GL
-Library [x. obj] and header files
OGL – Standard - for all/ everybody needs it
- Nonstandard – Some only/ exotic applications
Q. True or false?
0 – OK, 1 – BAD shell (+25)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ARTICLE REWRITE / TYPING
735-I-1
735-I-1

ARTICLE REWRITE / TYPING
735-I-1
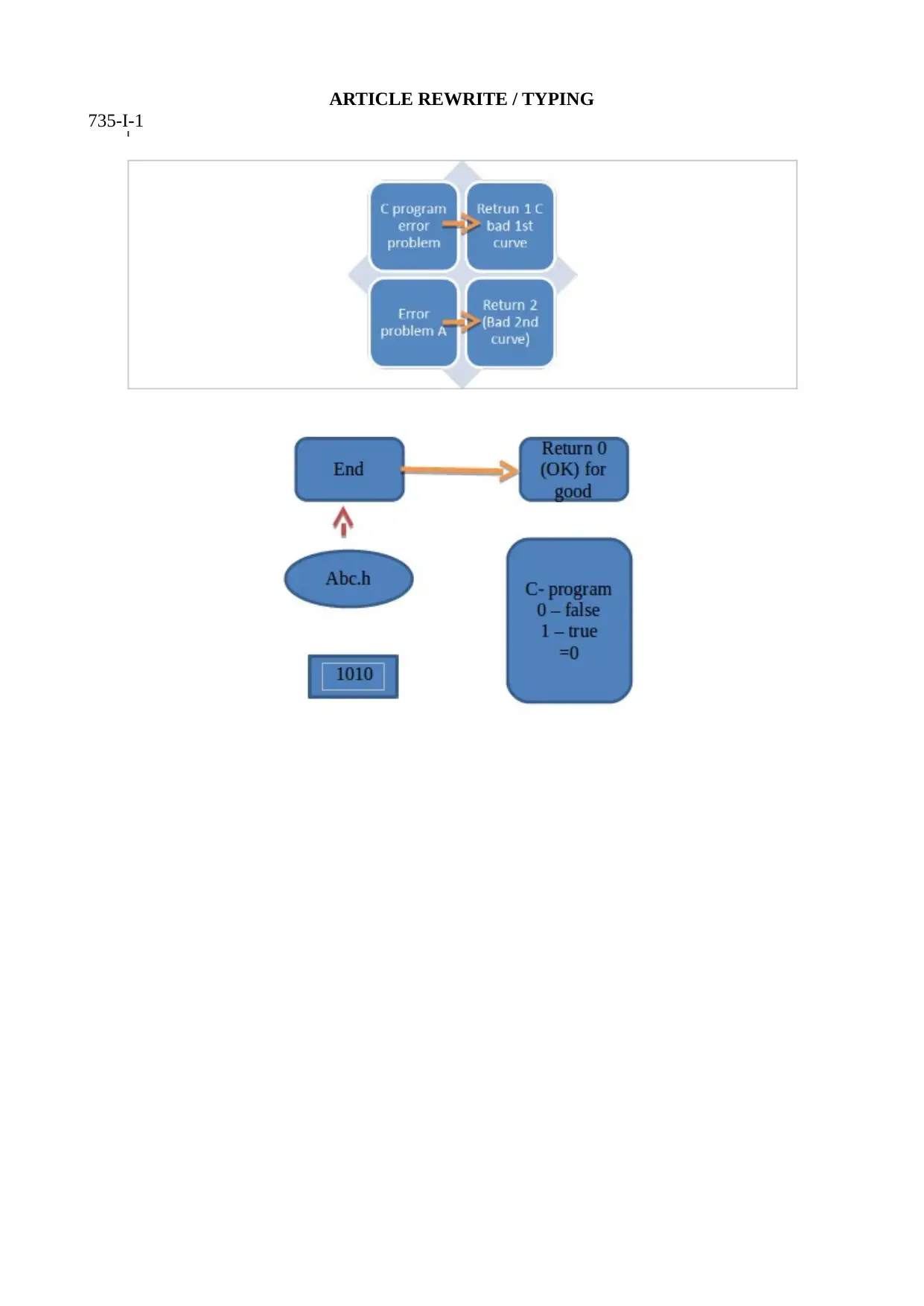
Configuration
Alternative general way program performs planned job !
Appears as re-programming
Q. Why is configuration not re-programming?
A. It is not done at development time (static time)
It is really done at LOAD TIME
At lead time, before starting, program reads / inputs config. variable values and restructures code to
be used at functional last minute re-programming.
Reconfigurable computing refers to a software architecture approach in which software flexibility is
combined with high hardware performance processing with high speed computing systems
(Vasconcelos, Vasconcelos and Endler).
There are three ways reconfigure software;
The weakest- config-files x = 0
Midpower- Shell var x =20
Strongest- Command line requests x = 100
Reprogramming by SA or application admin (ex VBA)
Configuration variables mis-configured can represent an attack vector FROM OUTSIDE (SYS-
side)
Q. Does configuration require data input into a program?
A. Yes
From a command line (input)
From the shell (echo $x, echo xyx)
Shell var defending operators ad UNIX/ LINUX
From file yxy – win
Attacks on software (open to attacks) comes from outside along data input points
735-I-1
Configuration
Alternative general way program performs planned job !
Appears as re-programming
Q. Why is configuration not re-programming?
A. It is not done at development time (static time)
It is really done at LOAD TIME
At lead time, before starting, program reads / inputs config. variable values and restructures code to
be used at functional last minute re-programming.
Reconfigurable computing refers to a software architecture approach in which software flexibility is
combined with high hardware performance processing with high speed computing systems
(Vasconcelos, Vasconcelos and Endler).
There are three ways reconfigure software;
The weakest- config-files x = 0
Midpower- Shell var x =20
Strongest- Command line requests x = 100
Reprogramming by SA or application admin (ex VBA)
Configuration variables mis-configured can represent an attack vector FROM OUTSIDE (SYS-
side)
Q. Does configuration require data input into a program?
A. Yes
From a command line (input)
From the shell (echo $x, echo xyx)
Shell var defending operators ad UNIX/ LINUX
From file yxy – win
Attacks on software (open to attacks) comes from outside along data input points
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 41
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.