Comprehensive Report on Secure Systems: Authentication and Security
VerifiedAdded on 2023/04/21
|14
|3428
|384
Report
AI Summary
This report provides a comprehensive overview of secure systems, emphasizing authentication processes, web security measures such as SSL, and various types of attacks including passive, active, and insider threats. It delves into social engineering tactics and the critical human aspects of information systems security, contrasting logical and physical security measures. The report also covers network enumeration, foot printing, scanning techniques, cryptography, and secure data transfer methods, highlighting attack countermeasures and security considerations for wireless networks. Furthermore, it discusses security policies, relevant legislation, ethical principles, and the importance of privacy and data protection, alongside the use of security tools and patches. The document also addresses securing cloud infrastructure and the handling of personal and sensitive data, concluding with a description of ISO27000/ISO27002 standards. Desklib offers this report as a study resource, providing students with access to past papers and solved assignments.

SECURE SYSTEM
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
Authentication.............................................................................................................................1
Web security (Secure socket layer).............................................................................................1
Types of attacks...........................................................................................................................2
Social Engineering & the human aspects to information systems security................................2
Logical vs physical security........................................................................................................3
Network enumeration, foot printing and scanning......................................................................3
Cryptography and secure data transfer........................................................................................4
Attack countermeasures: ............................................................................................................4
Wireless networks.......................................................................................................................5
Security policies and Legislation, ethical principles, privacy and protection of personal and
sensitive data...............................................................................................................................6
Security tools and patches...........................................................................................................6
Securing Cloud infrastructure.....................................................................................................7
Storing and processing personal and sensitive data....................................................................7
Describing ISO27000/ISO27002...............................................................................................8
Conclusion.......................................................................................................................................8
REFERENCES................................................................................................................................9
INTRODUCTION...........................................................................................................................1
Authentication.............................................................................................................................1
Web security (Secure socket layer).............................................................................................1
Types of attacks...........................................................................................................................2
Social Engineering & the human aspects to information systems security................................2
Logical vs physical security........................................................................................................3
Network enumeration, foot printing and scanning......................................................................3
Cryptography and secure data transfer........................................................................................4
Attack countermeasures: ............................................................................................................4
Wireless networks.......................................................................................................................5
Security policies and Legislation, ethical principles, privacy and protection of personal and
sensitive data...............................................................................................................................6
Security tools and patches...........................................................................................................6
Securing Cloud infrastructure.....................................................................................................7
Storing and processing personal and sensitive data....................................................................7
Describing ISO27000/ISO27002...............................................................................................8
Conclusion.......................................................................................................................................8
REFERENCES................................................................................................................................9

ILLUSTRATION INDEX
Illustration 1: Cryptography.............................................................................................................5
1
Illustration 1: Cryptography.............................................................................................................5
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Secure system helps organization against destruction, data corruption, interception and
unauthorized access. It is necessary for the management of corporation to manage its information
and data systems (Wong and Ledley, 2013). The present report describes Authentication process
of IT system in the organizations. Further, it describes working of web security and logical vs.
physical security for corporations. In addition to this, it explains cryptography as well as data
transfer techniques for securing information. It reveals security policies for the organizations as
per rules and regulations of government. It describes techniques of securing cloud infrastructures
as well as wireless networks in the corporations. It explains about social engineering and the
human aspects to information systems security for the organizations.
Authentication
Generally, Authentication is a process to identify genuine user through systematic
process. There are many types of authentication which are described as follows.
Password authentication: Password authentication is an effective method for
recognizing real user. In this process, person log on web page through user name and password
(Alexander and Finch. 2013). Then after, system checks this user name and password with help
of database which contains all information.
Smart card Authentication: Generally, this type of authentication is used by many
organizations like bank and MNC companies. Further, smart card contain computer chip which
is used to store private, public and other important information. To log into network, user has to
insert Smart card into reader and enter personal identification number to access the data.
Biometric Authentication: Mainly, organizations use biometric authentication for better
safety of data. In this process, biological statistics like finger prints, voice as well as iris pattern
of users are adopted by the system (Conheady, 2014). They are used for authentication of the
person by matching biological pattern.
Web security (Secure socket layer)
The SSL protocol is an Internet standard which is used to give secured access to Web
sites with help of public key technology and secret key technology. In addition to this, secret key
encryption provides effective speed for processing data and it is called symmetric encryption. On
the other side, asymmetric public key encryption gives better authentication to websites (Yeluri
and Castro-Leon, 2014). Secure Socket Layer is developed to take benefit of symmetric as well
2
Secure system helps organization against destruction, data corruption, interception and
unauthorized access. It is necessary for the management of corporation to manage its information
and data systems (Wong and Ledley, 2013). The present report describes Authentication process
of IT system in the organizations. Further, it describes working of web security and logical vs.
physical security for corporations. In addition to this, it explains cryptography as well as data
transfer techniques for securing information. It reveals security policies for the organizations as
per rules and regulations of government. It describes techniques of securing cloud infrastructures
as well as wireless networks in the corporations. It explains about social engineering and the
human aspects to information systems security for the organizations.
Authentication
Generally, Authentication is a process to identify genuine user through systematic
process. There are many types of authentication which are described as follows.
Password authentication: Password authentication is an effective method for
recognizing real user. In this process, person log on web page through user name and password
(Alexander and Finch. 2013). Then after, system checks this user name and password with help
of database which contains all information.
Smart card Authentication: Generally, this type of authentication is used by many
organizations like bank and MNC companies. Further, smart card contain computer chip which
is used to store private, public and other important information. To log into network, user has to
insert Smart card into reader and enter personal identification number to access the data.
Biometric Authentication: Mainly, organizations use biometric authentication for better
safety of data. In this process, biological statistics like finger prints, voice as well as iris pattern
of users are adopted by the system (Conheady, 2014). They are used for authentication of the
person by matching biological pattern.
Web security (Secure socket layer)
The SSL protocol is an Internet standard which is used to give secured access to Web
sites with help of public key technology and secret key technology. In addition to this, secret key
encryption provides effective speed for processing data and it is called symmetric encryption. On
the other side, asymmetric public key encryption gives better authentication to websites (Yeluri
and Castro-Leon, 2014). Secure Socket Layer is developed to take benefit of symmetric as well
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

as asymmetric encryption. In addition to this, it supports Netscape, Microsoft as well as other
major browsers. It works on application layer of DOD networking model. Secure socket layer
authentication is based on digital certificates which enable the clients and web servers to verify
each other identities before they set up a connection. Hence, secure socket layer uses client and
server certificates for proper authentication.
Types of attacks
There are many types of attack which affects the organizational performance and
efficiency at the work place. Some of them are described as follows.
Passive attack: Passive attack includes monitoring of unencrypted traffic, clear-text
passwords as well as sensitive information which are used to attack organizational server
(Network Security Types of attacks. 2010). In addition to this, passive attacks covers monitoring
of unprotected communications, traffic analysis, decrypting daily basis or weakly encrypted
traffic as well as capturing authentication information such as passwords
Active attacks: In this type of attack, attacker tries to break or bypass secured systems in
the organization. This process can be performed by stealth, worms’ viruses and Trojan horses to
steal or destroy sensitive information of organization.
Insider attack: An insider attack is done by corrupted employees who create complexities
to other employees to access the information (Schwalbe, 2015). This type of attack can also steal
or damage valuable data of the corporation.
Social Engineering & the human aspects to information systems security
Social engineering: Social engineering is considered as attack vector which depends on
human interaction as well as involves tricking people into breaking normal security procedures
in the organizations. For example, hacker pretends to be associated with the person who has
some kind of important issues which requires access to extra network resources in the enterprise
(Zissis and Lekkas, 2012). In addition to this, social engineering includes several types of attacks
such as baiting, phishing, pretexting and scare-ware.
Human aspects to information systems security: Information systems security is used to
save business' or corporations important information. Along with this, systems security
professionals test, execute, maintain as well as repair software and hardware to protect sensitive
3
major browsers. It works on application layer of DOD networking model. Secure socket layer
authentication is based on digital certificates which enable the clients and web servers to verify
each other identities before they set up a connection. Hence, secure socket layer uses client and
server certificates for proper authentication.
Types of attacks
There are many types of attack which affects the organizational performance and
efficiency at the work place. Some of them are described as follows.
Passive attack: Passive attack includes monitoring of unencrypted traffic, clear-text
passwords as well as sensitive information which are used to attack organizational server
(Network Security Types of attacks. 2010). In addition to this, passive attacks covers monitoring
of unprotected communications, traffic analysis, decrypting daily basis or weakly encrypted
traffic as well as capturing authentication information such as passwords
Active attacks: In this type of attack, attacker tries to break or bypass secured systems in
the organization. This process can be performed by stealth, worms’ viruses and Trojan horses to
steal or destroy sensitive information of organization.
Insider attack: An insider attack is done by corrupted employees who create complexities
to other employees to access the information (Schwalbe, 2015). This type of attack can also steal
or damage valuable data of the corporation.
Social Engineering & the human aspects to information systems security
Social engineering: Social engineering is considered as attack vector which depends on
human interaction as well as involves tricking people into breaking normal security procedures
in the organizations. For example, hacker pretends to be associated with the person who has
some kind of important issues which requires access to extra network resources in the enterprise
(Zissis and Lekkas, 2012). In addition to this, social engineering includes several types of attacks
such as baiting, phishing, pretexting and scare-ware.
Human aspects to information systems security: Information systems security is used to
save business' or corporations important information. Along with this, systems security
professionals test, execute, maintain as well as repair software and hardware to protect sensitive
3
data. This method contribute effective role for the organization to increase organizational
security to prevent from higher level attacks.
Logical vs. physical security
Generally, logical and physical security helps the organization to save data from
unauthorized users. Some of differences are described below in the table.
Logical vs physical security
Physical security Logical security
Physical security prevents attackers installing,
alarms, fences, cameras, security guards,
electronic access control, intrusion detection as
well as administration access controls in the
organizations. Along with this, physical
security is also used to protect hardware and
networks at sites of companies (Ng, Lo and
Schober, 2014).
Logical security secure computer software
through implementing user identifications,
passwords, authentication, bio metrics as well
as smart cards in the corporation. This process
helps the firms to secure data assets. In
addition to this, logical Security is also utilized
to electronic data safety like operating system
or data through the firewall, routers as well as
switches in the corporations.
Network enumeration, foot printing and scanning
Network enumeration: It is a procedure which helps to collect information about a
network such as the hosts, connected devices, user names, group information as well as related
data of corporation. By implementing protocols such as ICMP and SNMP, network enumeration
provides better view of the network for protecting data from unauthorized attack in the
organization (Rong, Nguyen and Jaatun, 2013). Network enumeration tools can help to scan
ports from retrieving information of firms. Further, they can play important role for network set
up and management of data traffic. According to some IT specialists, network enumeration is
also used as ethical hackling tool to secure data of the organization.
Foot printing: It is also data retrieval techniques which are used to together information of
organizational sensitive information through finding out of data about the system as possible.
Further, it is also considered as hacking tool to other computer systems (Von Solms and Van
Niekerk, 2013).
4
security to prevent from higher level attacks.
Logical vs. physical security
Generally, logical and physical security helps the organization to save data from
unauthorized users. Some of differences are described below in the table.
Logical vs physical security
Physical security Logical security
Physical security prevents attackers installing,
alarms, fences, cameras, security guards,
electronic access control, intrusion detection as
well as administration access controls in the
organizations. Along with this, physical
security is also used to protect hardware and
networks at sites of companies (Ng, Lo and
Schober, 2014).
Logical security secure computer software
through implementing user identifications,
passwords, authentication, bio metrics as well
as smart cards in the corporation. This process
helps the firms to secure data assets. In
addition to this, logical Security is also utilized
to electronic data safety like operating system
or data through the firewall, routers as well as
switches in the corporations.
Network enumeration, foot printing and scanning
Network enumeration: It is a procedure which helps to collect information about a
network such as the hosts, connected devices, user names, group information as well as related
data of corporation. By implementing protocols such as ICMP and SNMP, network enumeration
provides better view of the network for protecting data from unauthorized attack in the
organization (Rong, Nguyen and Jaatun, 2013). Network enumeration tools can help to scan
ports from retrieving information of firms. Further, they can play important role for network set
up and management of data traffic. According to some IT specialists, network enumeration is
also used as ethical hackling tool to secure data of the organization.
Foot printing: It is also data retrieval techniques which are used to together information of
organizational sensitive information through finding out of data about the system as possible.
Further, it is also considered as hacking tool to other computer systems (Von Solms and Van
Niekerk, 2013).
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Scanning: It is application which is designed to check host and servers in the organization.
Scanning is often utilized by administrators to verify security policies of their networks. In
addition to this, it is also used by hackers to identify the current services running on the host and
weakness.
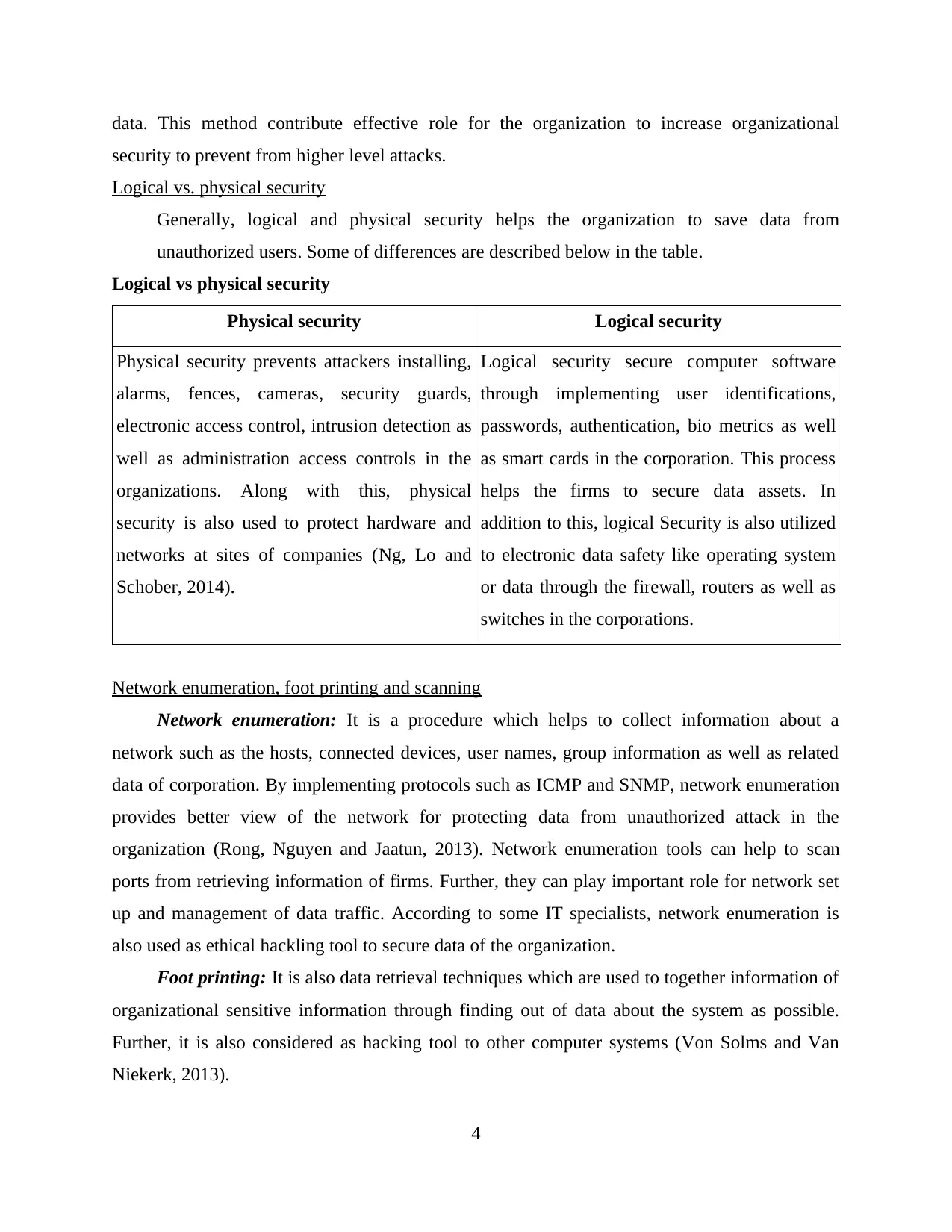
Cryptography and secure data transfer
In this process, management of organization can use cryptography techniques to transfer
the data from one place to another. This process can help the organization for securing
transmission which can reduce the chances of interception. Cryptography techniques convert
plain text into cypher data with the help of encryption techniques. Then after, system transfer
data into communication medium which provides effective security to organizations. In the next
process, users get encrypted data from its computer (Feng, Zhang and Qin, 2015). They decrypt
data with the help of password authentication which are sent by original user. So this process can
provide effective data safety for organizations during data transfer between one place to another.
Cryptography techniques are used by many organizations to prevent hacking of data which
provide reliability to reduce the threat.
(Sources: Feng, Zhang and Qin, 2015)
Attack countermeasures:
Countermeasure is technique which contribute effective role for an organization to reduce
threats of attack by removing them. In addition to this, it also helps the corporation to take
corrective actions to decrease hacking attacks. There are many procedures like understanding
5
Illustration 1: Cryptography
Scanning is often utilized by administrators to verify security policies of their networks. In
addition to this, it is also used by hackers to identify the current services running on the host and
weakness.
Cryptography and secure data transfer
In this process, management of organization can use cryptography techniques to transfer
the data from one place to another. This process can help the organization for securing
transmission which can reduce the chances of interception. Cryptography techniques convert
plain text into cypher data with the help of encryption techniques. Then after, system transfer
data into communication medium which provides effective security to organizations. In the next
process, users get encrypted data from its computer (Feng, Zhang and Qin, 2015). They decrypt
data with the help of password authentication which are sent by original user. So this process can
provide effective data safety for organizations during data transfer between one place to another.
Cryptography techniques are used by many organizations to prevent hacking of data which
provide reliability to reduce the threat.
(Sources: Feng, Zhang and Qin, 2015)
Attack countermeasures:
Countermeasure is technique which contribute effective role for an organization to reduce
threats of attack by removing them. In addition to this, it also helps the corporation to take
corrective actions to decrease hacking attacks. There are many procedures like understanding
5
Illustration 1: Cryptography
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
threat categories and using security procedures to prevent these types of attacks in the
organization. Generally, this table shows various types of threats and its counter measure to stop
these attacks in the organization (Stair and Reynolds, 2013).
Threat Countermeasure
Spoofing user
identification
Organization or individual can use strong authentication.
Companies do not save passwords in plain text for data safety.
Tampering with data Corporation can use hashing and signing to reduce data
tempering
Firm can use digital signatures for proper safety.
Repudiation Organization can design secure audit trails (Schumacher and
et.al., 2013).
Data disclosure Corporation can adopt strong authentication and encryption
techniques.
Organization can use secure communication links with
protocols .
Denial of services The firm can consider resources and bandwidth throttling
techniques.
Firm can utilize validate as well as filter input.
Elevation of privilege Enterprise can use principles of least privilege and follow
privileged service accounts to access its resources (Larsson and
et.al., 2014).
Wireless networks
Wireless network enable the users to access data and applications without any medium.
Further, it provides effective facilities to use internet and email services at any place. There are
many types of wireless network which are used for different purposes.
Wireless local area network (WLAN): WLANS enable people to access internet in
university campus or specific building. Generally, it is used for small number of users without
6
organization. Generally, this table shows various types of threats and its counter measure to stop
these attacks in the organization (Stair and Reynolds, 2013).
Threat Countermeasure
Spoofing user
identification
Organization or individual can use strong authentication.
Companies do not save passwords in plain text for data safety.
Tampering with data Corporation can use hashing and signing to reduce data
tempering
Firm can use digital signatures for proper safety.
Repudiation Organization can design secure audit trails (Schumacher and
et.al., 2013).
Data disclosure Corporation can adopt strong authentication and encryption
techniques.
Organization can use secure communication links with
protocols .
Denial of services The firm can consider resources and bandwidth throttling
techniques.
Firm can utilize validate as well as filter input.
Elevation of privilege Enterprise can use principles of least privilege and follow
privileged service accounts to access its resources (Larsson and
et.al., 2014).
Wireless networks
Wireless network enable the users to access data and applications without any medium.
Further, it provides effective facilities to use internet and email services at any place. There are
many types of wireless network which are used for different purposes.
Wireless local area network (WLAN): WLANS enable people to access internet in
university campus or specific building. Generally, it is used for small number of users without
6

any requirement of access point (Types of Wireless Networks. 2010). In addition to this, it gives
effective performance to access internet in the particular areas.
Wireless metropolitan networks (WMAN): With help of WMAN, it allows the people to
use internet in the city. Further, it offers effective performance to use network in an appropriate
manner in the metropolitan areas.
Wireless wide area networks (WWAN): These types of networks can be used for big
areas like cities or countries with the help of multiple satellite systems or antenna sites (Zhang,
and et.al., 2013). On the other side, performance of this network is low due to lot of data traffic.
Security policies and Legislation, ethical principles, privacy and protection of personal and
sensitive data
Government of many countries designed cyber laws and security policies for data safety
of organization to reduce hacking activities.
Security
policies
Description
Data protection
act
Organization has to follow data protection act to secure its personal and
sensitive data safety. To implement this act, corporation has to use IPV6
protocol, firewalls and antivirus to avoid hacking and unauthorized access in
the computer systems (Davison, Ou and Martinsons, 2013).
Electronic fund
transfer act
In addition to this, government of United Kingdom compel the organizations
to use electronic fund transfer act. This rule helps the corporations to reduce
stealing banking details by using latest security measures.
Licensing of
software
Governance also obliges the organisations to use licensing software for data
as well as information safety which support them to reduce unethical
activities.
Assets
management
policies
Legal authorities obligate the organisation to manage IT assets which help to
contribute effectively to secure its system.
Network
connection
In addition to this, government suggest the organisation to check connection
of network security. This rules and regulations plays important role for
7
effective performance to access internet in the particular areas.
Wireless metropolitan networks (WMAN): With help of WMAN, it allows the people to
use internet in the city. Further, it offers effective performance to use network in an appropriate
manner in the metropolitan areas.
Wireless wide area networks (WWAN): These types of networks can be used for big
areas like cities or countries with the help of multiple satellite systems or antenna sites (Zhang,
and et.al., 2013). On the other side, performance of this network is low due to lot of data traffic.
Security policies and Legislation, ethical principles, privacy and protection of personal and
sensitive data
Government of many countries designed cyber laws and security policies for data safety
of organization to reduce hacking activities.
Security
policies
Description
Data protection
act
Organization has to follow data protection act to secure its personal and
sensitive data safety. To implement this act, corporation has to use IPV6
protocol, firewalls and antivirus to avoid hacking and unauthorized access in
the computer systems (Davison, Ou and Martinsons, 2013).
Electronic fund
transfer act
In addition to this, government of United Kingdom compel the organizations
to use electronic fund transfer act. This rule helps the corporations to reduce
stealing banking details by using latest security measures.
Licensing of
software
Governance also obliges the organisations to use licensing software for data
as well as information safety which support them to reduce unethical
activities.
Assets
management
policies
Legal authorities obligate the organisation to manage IT assets which help to
contribute effectively to secure its system.
Network
connection
In addition to this, government suggest the organisation to check connection
of network security. This rules and regulations plays important role for
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

policy company to secure sensitive data. (Wong and Ledley, 2013).
Security tools and patches
Security tools: There are many security tools which helps the organisations or individuals
to manage various activities like password recovery, management, penetration testing,
stenography, vulnerability scanning as well as secure data wiping. For example, organisation can
use intrusion detection system to monitor network activities. In additions to this, this tool can
also inform management station about type of security attack which plays important role for the
organisations to consider correctives steps (Alexander and Finch. 2013). Along with this, it is
also helpful to avoid networking attacks in the corporations.
Patches: It is the application which is designed to update a computer program, its
supporting data as well as operating system updates. In addition to this, it also helps the
individual or organisation to improve and fix defects in the software. It also assists the company
to increase the performance of its software in an appropriate manner.
Securing Cloud infrastructure
Securing cloud infrastructure is part of network or computer security of
organizations. Further, it secures organizational remote data through implementing
various policies, technologies as well as proper in the corporation (Conheady, 2014).
Organization can secure its cloud infrastructure with the help of security controls which
are described below in the table.
Cloud security controls Description
Deterrent controls It can aid the organisation to save cloud infrastructure by giving
warning signals. Further, it provides helps to enterprise to take
appropriate steps regarding network security.
Preventive controls It can aid the corporation to secure cloud infrastructure through
providing appropriate strengths like effective authentication
systems.
Corrective controls Corrective controls can assist the organisations to save cloud
computing security by taking proper data backup as well as
8
Security tools and patches
Security tools: There are many security tools which helps the organisations or individuals
to manage various activities like password recovery, management, penetration testing,
stenography, vulnerability scanning as well as secure data wiping. For example, organisation can
use intrusion detection system to monitor network activities. In additions to this, this tool can
also inform management station about type of security attack which plays important role for the
organisations to consider correctives steps (Alexander and Finch. 2013). Along with this, it is
also helpful to avoid networking attacks in the corporations.
Patches: It is the application which is designed to update a computer program, its
supporting data as well as operating system updates. In addition to this, it also helps the
individual or organisation to improve and fix defects in the software. It also assists the company
to increase the performance of its software in an appropriate manner.
Securing Cloud infrastructure
Securing cloud infrastructure is part of network or computer security of
organizations. Further, it secures organizational remote data through implementing
various policies, technologies as well as proper in the corporation (Conheady, 2014).
Organization can secure its cloud infrastructure with the help of security controls which
are described below in the table.
Cloud security controls Description
Deterrent controls It can aid the organisation to save cloud infrastructure by giving
warning signals. Further, it provides helps to enterprise to take
appropriate steps regarding network security.
Preventive controls It can aid the corporation to secure cloud infrastructure through
providing appropriate strengths like effective authentication
systems.
Corrective controls Corrective controls can assist the organisations to save cloud
computing security by taking proper data backup as well as
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

reducing effect of the attack (Yeluri and Castro-Leon, 2014).
Storing and processing personal and sensitive data
Organisation or individuals can use to store their sensitive data in the hard drives. In
addition to this, firm can give appropriate passwords to access data drive which can help to store
personal and valuable information. Further, IT specialists of corporation can use encryption
techniques to secure data from unauthorized users during processing. This process can help the
organisation to process data in a better way. Cryptography techniques create complexities for
hackers to decrypt the sensitive information (Zissis and Lekkas, 2012). Along with this, IT
experts of organisation can also consider data protection laws which can guide them to process
or transfer data from one source to other without any interruption. This process can help the
corporation to function its IT operations in an appropriate manner.
Describing ISO27000/ISO27002
These are ISO standardized protocols which are used for data safety in the organizations.
ISO 27000: It is developed by international standardization organization for the data
security. This standard introduces reason of Information Security Management System which is
used to manage information related security risks as well as control in the organization (Ng, Lo
and Schober, 2014). Further, it aids the corporation to prevent various types of complexities
which provide reliability to manage organizational IT operations.
ISO27002: It is also designed by international standardization organization for the same
purpose. This standard gives best recommendations on information security management by
initiating as well as executing or maintaining information security management systems. Along
with this, It can play important role for the company to reduce hacking and unethical activities
(Schumacher and et.al., 2013).
CONCLUSION
From the report, it is found that knowledge of authentication also provide effective
information to use and prevent the data from unauthorized users. Cryptography as well as data
transfer offers better security of information during the transmission. Further, attack
countermeasure contribute effective role for the corporations or individual to reduce hacking
activities by implementing appropriate solutions. In addition to this, security tools as well as
patches help the company to manage secure activities and update software in a better way. It can
9
Storing and processing personal and sensitive data
Organisation or individuals can use to store their sensitive data in the hard drives. In
addition to this, firm can give appropriate passwords to access data drive which can help to store
personal and valuable information. Further, IT specialists of corporation can use encryption
techniques to secure data from unauthorized users during processing. This process can help the
organisation to process data in a better way. Cryptography techniques create complexities for
hackers to decrypt the sensitive information (Zissis and Lekkas, 2012). Along with this, IT
experts of organisation can also consider data protection laws which can guide them to process
or transfer data from one source to other without any interruption. This process can help the
corporation to function its IT operations in an appropriate manner.
Describing ISO27000/ISO27002
These are ISO standardized protocols which are used for data safety in the organizations.
ISO 27000: It is developed by international standardization organization for the data
security. This standard introduces reason of Information Security Management System which is
used to manage information related security risks as well as control in the organization (Ng, Lo
and Schober, 2014). Further, it aids the corporation to prevent various types of complexities
which provide reliability to manage organizational IT operations.
ISO27002: It is also designed by international standardization organization for the same
purpose. This standard gives best recommendations on information security management by
initiating as well as executing or maintaining information security management systems. Along
with this, It can play important role for the company to reduce hacking and unethical activities
(Schumacher and et.al., 2013).
CONCLUSION
From the report, it is found that knowledge of authentication also provide effective
information to use and prevent the data from unauthorized users. Cryptography as well as data
transfer offers better security of information during the transmission. Further, attack
countermeasure contribute effective role for the corporations or individual to reduce hacking
activities by implementing appropriate solutions. In addition to this, security tools as well as
patches help the company to manage secure activities and update software in a better way. It can
9

be concluded that data protection act and electronic fund transfer act aid the IT experts of
organizations to avoid the unethical activities.
10
organizations to avoid the unethical activities.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





