Comparative Study for Secured Smart Grid Communications and Solutions
VerifiedAdded on 2023/06/05
|12
|4135
|412
Report
AI Summary
This report presents a comparative study of security issues in smart grid communications, focusing on the integration of energy distribution systems with communication networks. It highlights the vulnerabilities introduced by advanced technologies, such as malware attacks and threats to Home Area Networks (HAN) and Neighborhood Area Networks (NAN). The study examines various communication network components like WLAN, ZigBee, and femtocells, assessing their security strengths and limitations. It also addresses challenges related to internetworking, security policies, and trusted computing, emphasizing the need for robust authentication methods and secure services. The report compares different security frameworks, considering device authentication, data packet overhead, and computational costs, ultimately aiming to provide optimum solutions for enhancing cyber security in smart grid systems. Desklib provides access to this and other solved assignments for students.

COMPARATIVE STUDY FOR SECURED SMART GRID COMMUNICATIONS
Abstract:
One of the new forms of electricity network is said to be a smart grid that utilizes maximum
fidelity power-flow control, reliable and secured energy, and self-healing with the help of control
technology and digital communication. Depending on the infrastructure of intelligent and
secured network communication, we could able to upgrade the existing power grid into smart
grid system. For smart grid, it is necessary to have a security framework for the distributed
communication, sensing technologies and pervasive computing in grid networks. But the use of
certain technologies leads to certain vulnerable actions in the cyber security, which causes
untrustworthy system operations, unusual cost expenses and significant tragedy for the utilities
and consumers. In this paper we have discussed certain security issues in smart grid
communication with the comparative optimum solution.
Keywords: Smart grid, Cyber security.
Introduction:
A smart grid is said to be an integration of energy distribution system with the communication
system that forms a bidirectional information as well as power flow infrastructure. These
enhanced technologies not only advance the outdated communication but also transforms the
closed system into public data networks [1]. With the addition of novel services with the
distributed intelligence and state-of-the-art communication capacities, the smart grid
communications could be more efficient, flexible and inexpensive to afford and manage.
Although there are several benefits certain cyber and security threats should be considered by
every industry. The benefits of smart grids could be compensated with the vulnerabilities
produced by it. A significant innovative cyber attack vendor known as malware could
significantly decrease the demand of the smart grid thereby causing problem in the transmission,
generation and distribution progress [2]. A typical smart grid system is shown in the figure given
below.
Abstract:
One of the new forms of electricity network is said to be a smart grid that utilizes maximum
fidelity power-flow control, reliable and secured energy, and self-healing with the help of control
technology and digital communication. Depending on the infrastructure of intelligent and
secured network communication, we could able to upgrade the existing power grid into smart
grid system. For smart grid, it is necessary to have a security framework for the distributed
communication, sensing technologies and pervasive computing in grid networks. But the use of
certain technologies leads to certain vulnerable actions in the cyber security, which causes
untrustworthy system operations, unusual cost expenses and significant tragedy for the utilities
and consumers. In this paper we have discussed certain security issues in smart grid
communication with the comparative optimum solution.
Keywords: Smart grid, Cyber security.
Introduction:
A smart grid is said to be an integration of energy distribution system with the communication
system that forms a bidirectional information as well as power flow infrastructure. These
enhanced technologies not only advance the outdated communication but also transforms the
closed system into public data networks [1]. With the addition of novel services with the
distributed intelligence and state-of-the-art communication capacities, the smart grid
communications could be more efficient, flexible and inexpensive to afford and manage.
Although there are several benefits certain cyber and security threats should be considered by
every industry. The benefits of smart grids could be compensated with the vulnerabilities
produced by it. A significant innovative cyber attack vendor known as malware could
significantly decrease the demand of the smart grid thereby causing problem in the transmission,
generation and distribution progress [2]. A typical smart grid system is shown in the figure given
below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
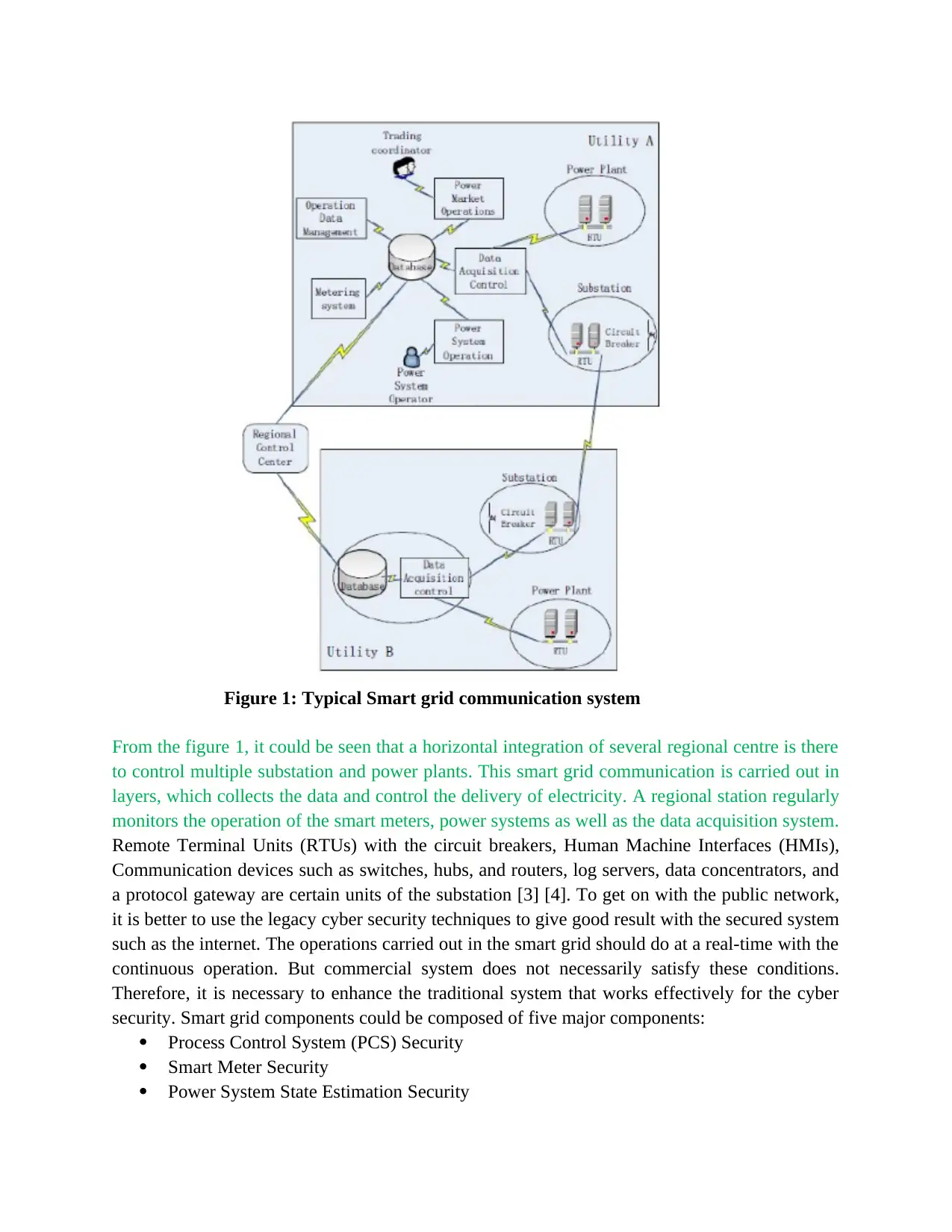
Figure 1: Typical Smart grid communication system
From the figure 1, it could be seen that a horizontal integration of several regional centre is there
to control multiple substation and power plants. This smart grid communication is carried out in
layers, which collects the data and control the delivery of electricity. A regional station regularly
monitors the operation of the smart meters, power systems as well as the data acquisition system.
Remote Terminal Units (RTUs) with the circuit breakers, Human Machine Interfaces (HMIs),
Communication devices such as switches, hubs, and routers, log servers, data concentrators, and
a protocol gateway are certain units of the substation [3] [4]. To get on with the public network,
it is better to use the legacy cyber security techniques to give good result with the secured system
such as the internet. The operations carried out in the smart grid should do at a real-time with the
continuous operation. But commercial system does not necessarily satisfy these conditions.
Therefore, it is necessary to enhance the traditional system that works effectively for the cyber
security. Smart grid components could be composed of five major components:
Process Control System (PCS) Security
Smart Meter Security
Power System State Estimation Security
From the figure 1, it could be seen that a horizontal integration of several regional centre is there
to control multiple substation and power plants. This smart grid communication is carried out in
layers, which collects the data and control the delivery of electricity. A regional station regularly
monitors the operation of the smart meters, power systems as well as the data acquisition system.
Remote Terminal Units (RTUs) with the circuit breakers, Human Machine Interfaces (HMIs),
Communication devices such as switches, hubs, and routers, log servers, data concentrators, and
a protocol gateway are certain units of the substation [3] [4]. To get on with the public network,
it is better to use the legacy cyber security techniques to give good result with the secured system
such as the internet. The operations carried out in the smart grid should do at a real-time with the
continuous operation. But commercial system does not necessarily satisfy these conditions.
Therefore, it is necessary to enhance the traditional system that works effectively for the cyber
security. Smart grid components could be composed of five major components:
Process Control System (PCS) Security
Smart Meter Security
Power System State Estimation Security

Smart Grid Communication Protocol Security
Smart Grid Simulation for Security analysis.
Communication Network:
The communication Network is said to be the subpart of the smart grid that is composed of
Home Area Network (HAN) and Neighborhood Area Network (NAN). These networks provide
the data communication between the end user and the utility. AMI is said to be the key element
of HANs. HAN is composed of three main components:
1) WLAN: This is said to be the wireless LAN. This could be operated with the set of 802.11
standards. The smart devices provide the demand side management such as demand response and
energy efficiency management [5]. 802.11 provide the necessary security with the advanced
encryption standard (AEC). The integrity is offered by the AES-CBC-MAC algorithm. However,
802.11 faces certain security issues that could be easily hijacked, since by default they do not
provide any authorization mechanism. When the WLAN is easily hacked then the hacker could
change the entire smart grid data that does the falsified operation in the grid. IEEE 802.11
provides the easy pathway for the hackers to enter the WLAN network. If WLAN is hacked then
the entire connected network with the NAN could be completely targeted. Hence, we could say
that WLAN with its open standards and maximum throughput with the secured data is best suited
for HAN.
2) ZigBee: This works in IEEE 802.15.4 standard. Zigbee communication module handles
multiple devices at a minimum baud rate that explains the physical layer and Media Access
Control (MAC) standard. Here the threat occurs with the 802.15.4 protocol that is vulnerable to
jamming. This could affect the system’s availability to services. Another threat occurs in the
Zigbee while capturing the messages that are difficult to avoid in LR-WPANs [6]. The next case
with be exhaustion. In this case, the coordinator of the compromised node will temp the
maximum number of nodes that offers with the high quality link. At first, it will be forced to
work well followed by the battery depletion within short period of time.
ZigBee Smart Energy has been used by the large stakeholders recently. This technology works
with AMI that significantly goes well with the HAN network [7]. Two communication streams
will be supported by the ZigBee gateway that merges the utility AMI central database to the
smart devices. This gateway will therefore act as a firewall that will protect the network asset
from the grid side. It is necessary to configure and authenticate the ZigBee modules for the in-
house smart devices, in order to complete the network topology. However, security issues occur
when there is an opposition that occurs with the ZigBee coordinator node. This could sufficiently
deplete the battery causing the system failure. As a result it could be said that a low cost with the
minimum power consumption, usage of unlicensed spectrum with the existing smart energy
devices will provide effective communication for HAN.
Smart Grid Simulation for Security analysis.
Communication Network:
The communication Network is said to be the subpart of the smart grid that is composed of
Home Area Network (HAN) and Neighborhood Area Network (NAN). These networks provide
the data communication between the end user and the utility. AMI is said to be the key element
of HANs. HAN is composed of three main components:
1) WLAN: This is said to be the wireless LAN. This could be operated with the set of 802.11
standards. The smart devices provide the demand side management such as demand response and
energy efficiency management [5]. 802.11 provide the necessary security with the advanced
encryption standard (AEC). The integrity is offered by the AES-CBC-MAC algorithm. However,
802.11 faces certain security issues that could be easily hijacked, since by default they do not
provide any authorization mechanism. When the WLAN is easily hacked then the hacker could
change the entire smart grid data that does the falsified operation in the grid. IEEE 802.11
provides the easy pathway for the hackers to enter the WLAN network. If WLAN is hacked then
the entire connected network with the NAN could be completely targeted. Hence, we could say
that WLAN with its open standards and maximum throughput with the secured data is best suited
for HAN.
2) ZigBee: This works in IEEE 802.15.4 standard. Zigbee communication module handles
multiple devices at a minimum baud rate that explains the physical layer and Media Access
Control (MAC) standard. Here the threat occurs with the 802.15.4 protocol that is vulnerable to
jamming. This could affect the system’s availability to services. Another threat occurs in the
Zigbee while capturing the messages that are difficult to avoid in LR-WPANs [6]. The next case
with be exhaustion. In this case, the coordinator of the compromised node will temp the
maximum number of nodes that offers with the high quality link. At first, it will be forced to
work well followed by the battery depletion within short period of time.
ZigBee Smart Energy has been used by the large stakeholders recently. This technology works
with AMI that significantly goes well with the HAN network [7]. Two communication streams
will be supported by the ZigBee gateway that merges the utility AMI central database to the
smart devices. This gateway will therefore act as a firewall that will protect the network asset
from the grid side. It is necessary to configure and authenticate the ZigBee modules for the in-
house smart devices, in order to complete the network topology. However, security issues occur
when there is an opposition that occurs with the ZigBee coordinator node. This could sufficiently
deplete the battery causing the system failure. As a result it could be said that a low cost with the
minimum power consumption, usage of unlicensed spectrum with the existing smart energy
devices will provide effective communication for HAN.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3) Mobile Communication and Femtocells: Femtocells is the way to have a connection
between the household devices and the mobile operators with the help of optical fibers or
broadband connection along with the residential DSL [8] [9]. Femtocells could highly save the
power with the secure connection. It is said that the cellular femtocells with relatively higher
cost, secured implementation and limited device access will be best suited for HAN.
Challenges (LIMITATIONS):
Smart grid is said to be the coordination of various systems with the new and innovative
technologies in the system architecture that purely depends on various standards and regulations,
which is necessarily implemented in the communication protocols in order to support the
challenges faced by the commercial power systems [10]. The major challenge occurs while going
on with the inter-networking, efficiency and security services could occur that while dealing with
the smart communication networks.
Internetworking:
In certain application and devices, there is a lack of security and there is a cause of threats to
occur while going with several networks[11]. These types of networks are not preferred for the
smart grids. The cyber security network for the smart grid layers should be composed in such a
way that it has to deal with the maximum interruption, unnoticeable functionalities and
corruption. A way to deal with the intruders visit towards the network could be making the
transport network layer completely private i.e. the network could be completely owned by the
utility. This could stop the unwanted access of vulnerabilities over the internet. But this is not
possible in all cases. Therefore, there could be certain hostile groups who tend to cause cyber
attacks towards the power supply. A worm infestation is proved to have certain unusual impacts
to the environment. One of these cyber attacks is worm infestations which have proven to
negatively impact critical network infrastructures. For instance, if DoS has been attacked certain
vulnerable issues, then this could stop all the servers connected with the directory, which could
stop the users connecting to the networks. Hence the smart grid connection towards the internet
should be highly secured.
Private network has an advantage of having faster responses since the number of parties involved
is relatively low [12]. However, this is not the case when large amount of parties involved. This
could decrease the response and resolution.
Security Policy and Operations:
A proper connection should be maintained among the components of the smart grid
connection in order to enhance the reliability [13]. A hacker could attempt to gain access
over the component and change the configuration that could interrupt all other system
connected to it. This is extensively done in DoS since hacking the server could interrupt all
other nodes connected to it [14]. During the protocol development it is necessary for the
protocol designers to pay attention to this threat.
between the household devices and the mobile operators with the help of optical fibers or
broadband connection along with the residential DSL [8] [9]. Femtocells could highly save the
power with the secure connection. It is said that the cellular femtocells with relatively higher
cost, secured implementation and limited device access will be best suited for HAN.
Challenges (LIMITATIONS):
Smart grid is said to be the coordination of various systems with the new and innovative
technologies in the system architecture that purely depends on various standards and regulations,
which is necessarily implemented in the communication protocols in order to support the
challenges faced by the commercial power systems [10]. The major challenge occurs while going
on with the inter-networking, efficiency and security services could occur that while dealing with
the smart communication networks.
Internetworking:
In certain application and devices, there is a lack of security and there is a cause of threats to
occur while going with several networks[11]. These types of networks are not preferred for the
smart grids. The cyber security network for the smart grid layers should be composed in such a
way that it has to deal with the maximum interruption, unnoticeable functionalities and
corruption. A way to deal with the intruders visit towards the network could be making the
transport network layer completely private i.e. the network could be completely owned by the
utility. This could stop the unwanted access of vulnerabilities over the internet. But this is not
possible in all cases. Therefore, there could be certain hostile groups who tend to cause cyber
attacks towards the power supply. A worm infestation is proved to have certain unusual impacts
to the environment. One of these cyber attacks is worm infestations which have proven to
negatively impact critical network infrastructures. For instance, if DoS has been attacked certain
vulnerable issues, then this could stop all the servers connected with the directory, which could
stop the users connecting to the networks. Hence the smart grid connection towards the internet
should be highly secured.
Private network has an advantage of having faster responses since the number of parties involved
is relatively low [12]. However, this is not the case when large amount of parties involved. This
could decrease the response and resolution.
Security Policy and Operations:
A proper connection should be maintained among the components of the smart grid
connection in order to enhance the reliability [13]. A hacker could attempt to gain access
over the component and change the configuration that could interrupt all other system
connected to it. This is extensively done in DoS since hacking the server could interrupt all
other nodes connected to it [14]. During the protocol development it is necessary for the
protocol designers to pay attention to this threat.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Multiple organizations are involved in this design for the effective operation of the smart
grid systems [15]. An issue known as federated identity management occurs, which needs
the access from the remote organization for the multiple components involved in the smart
grid since several equipments needs certain authorization ( person or equipments involves
in getting permission from other entities). This issues could be solved by Security Assertion
Markup Language (SAML), Web Services Trust (WS-Trust), and PKI. It is necessary to
have interoperability, since no conflicts should happen among the involved organizations.
Secured Services:
It is necessary to maintain the security of smart grid rather that the development,
deployment and the integration. According to EPRI, each feature of a smart grid must be
secure. The features involved in the cyber security are not enough for maintaining the
smart network since human intervention could consume a lot of time [16]. An illustration
of the typical security service is shown in the figure given below, which is the framework
that sets the cyber security across the process, technology and policy of every organization.
Figure 2: Security services involved in the smart grid.
Trusted Computing:
Trusted computing encompasses the operations of the smart grid virtually. This is modeled
in order to ensure that none of the malware has been introduced in the software processing
devices. The malware protection can be categorized based on the system that has been
considered: 1) General purpose computer system 2) Embedded systems. General purpose
system is specifically designed to run the third party software that has been received by the
client [17] [18]. Rather embedded system is the combination of hardware and software that
has been designed to do a specific task. It is necessary to have separate malware protection
system based on their types. Embedded systems could solve their security issues with the
high degree of assurance. It is necessary to have a secured software development process by
grid systems [15]. An issue known as federated identity management occurs, which needs
the access from the remote organization for the multiple components involved in the smart
grid since several equipments needs certain authorization ( person or equipments involves
in getting permission from other entities). This issues could be solved by Security Assertion
Markup Language (SAML), Web Services Trust (WS-Trust), and PKI. It is necessary to
have interoperability, since no conflicts should happen among the involved organizations.
Secured Services:
It is necessary to maintain the security of smart grid rather that the development,
deployment and the integration. According to EPRI, each feature of a smart grid must be
secure. The features involved in the cyber security are not enough for maintaining the
smart network since human intervention could consume a lot of time [16]. An illustration
of the typical security service is shown in the figure given below, which is the framework
that sets the cyber security across the process, technology and policy of every organization.
Figure 2: Security services involved in the smart grid.
Trusted Computing:
Trusted computing encompasses the operations of the smart grid virtually. This is modeled
in order to ensure that none of the malware has been introduced in the software processing
devices. The malware protection can be categorized based on the system that has been
considered: 1) General purpose computer system 2) Embedded systems. General purpose
system is specifically designed to run the third party software that has been received by the
client [17] [18]. Rather embedded system is the combination of hardware and software that
has been designed to do a specific task. It is necessary to have separate malware protection
system based on their types. Embedded systems could solve their security issues with the
high degree of assurance. It is necessary to have a secured software development process by

the manufactures. Next, if the device is said to be field upgradable, the manufacturer
should offer solution that should be upgraded and secure software. This method is
predominantly carried out to secure the embedded system with the keying element by the
software validation. Such a practical methodology can supply huge level of assurance than
can be obtained with a reactive approach such as a virus checker.
Security Framework comparison:
Authentication methods have certain security issues due to the deficient work in the
security schemes and AMI. There exist certain approaches [12] that could solve the
authentication problems after which the communication technology could be utilized. In
comparison, Data packets do not require any momentous overhead when compared to the
Cryptographic methods. Moreover, the digital certificates (cryptographic methods) require
high computational costs. Smart meters relatively send a meter reading at a period of 500
ms. with the help of commodity computer, PKI based schemes is not an issue [19]. In
controversy, the power grid that is connected to the numerous buildings and their reading
requires verification by the NAN gateway could be higher than the capacity. This
cryptography though uses the digital signature and message verification but it could be
neither affordable nor scalable. Following objectives should be satisfied by the employed
smart grid application:
1) Device authentication: Proper utility services should be provided by the smart meters
and their connected consumers.
2) Confidential data: Privacy should be maintained among the smart meter readings and
the control message send by the management to the consumers.
3) Integration of messages: AMI should have the correct reading messages from the AMI.
The data should not be altered.
4) Prevention of hijacking: Secure communication should be offered by the AMI network
even if there is an occurrence to compromise an individual meter
5) Facilitating communication overhead: Efficiency should be provided between the
communication overhead and processing latency.
A key management protocol for secure broadcast communications in pay-TV broadcasting
systems has been proposed in [10]. This protocol has a slight modification with the existing
protocol in the following criteria:
This protocol finds a way in securing the smart grid communication with the new
requirement. Here, secret keys have been managed with the help of the binary tree for
should offer solution that should be upgraded and secure software. This method is
predominantly carried out to secure the embedded system with the keying element by the
software validation. Such a practical methodology can supply huge level of assurance than
can be obtained with a reactive approach such as a virus checker.
Security Framework comparison:
Authentication methods have certain security issues due to the deficient work in the
security schemes and AMI. There exist certain approaches [12] that could solve the
authentication problems after which the communication technology could be utilized. In
comparison, Data packets do not require any momentous overhead when compared to the
Cryptographic methods. Moreover, the digital certificates (cryptographic methods) require
high computational costs. Smart meters relatively send a meter reading at a period of 500
ms. with the help of commodity computer, PKI based schemes is not an issue [19]. In
controversy, the power grid that is connected to the numerous buildings and their reading
requires verification by the NAN gateway could be higher than the capacity. This
cryptography though uses the digital signature and message verification but it could be
neither affordable nor scalable. Following objectives should be satisfied by the employed
smart grid application:
1) Device authentication: Proper utility services should be provided by the smart meters
and their connected consumers.
2) Confidential data: Privacy should be maintained among the smart meter readings and
the control message send by the management to the consumers.
3) Integration of messages: AMI should have the correct reading messages from the AMI.
The data should not be altered.
4) Prevention of hijacking: Secure communication should be offered by the AMI network
even if there is an occurrence to compromise an individual meter
5) Facilitating communication overhead: Efficiency should be provided between the
communication overhead and processing latency.
A key management protocol for secure broadcast communications in pay-TV broadcasting
systems has been proposed in [10]. This protocol has a slight modification with the existing
protocol in the following criteria:
This protocol finds a way in securing the smart grid communication with the new
requirement. Here, secret keys have been managed with the help of the binary tree for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

securing the unicast, multicast and the broadcast communications. This binary tree is
shown in the figure given below
Figure 3: Binary tree for securing the secret key
Here, SETENTITY3 = SECRETNODE2, SECRETNODE3, SECRETNODE10
The above figure leaves the KEYBROADCAST that has been updated as KEYBROADCAST` that is as
follows:
In the case of rejoining the node, it is necessary to join the entity to the node where it has
been previously allocated. Since the secret key is known to all entity, it could not be used
for the secure unicast and multicast communication. Hence it is necessary to have a secret
key in the communication session where the entities participate. This secret key will be
shared only to the entity of that communication session. This proposed scheme [10] could
eliminate the weakness when compared with [4]. It is necessary to guarantee the backward
secrecy. It is necessary to secure the forward secrecy in order to prevent the attackers from
eavesdropping of the prior communications. If this is not done then the attackers could
easily hack the encrypted communication and they could decrypt them after obtaining the
access to the network. Attackers could misuse these decrypted information.
In [11], the proposed scheme satisfies the external attackers from consuming the encrypted
data. Moreover, it also avoids the internal attackers from hacking the data using their
methods. The author had used an administrative approach not the cryptographic method.
Several proofs of Unforgeability and batch verification security have also been stated. The
time cost of their operation algorithm has also been stated in the table given below.
shown in the figure given below
Figure 3: Binary tree for securing the secret key
Here, SETENTITY3 = SECRETNODE2, SECRETNODE3, SECRETNODE10
The above figure leaves the KEYBROADCAST that has been updated as KEYBROADCAST` that is as
follows:
In the case of rejoining the node, it is necessary to join the entity to the node where it has
been previously allocated. Since the secret key is known to all entity, it could not be used
for the secure unicast and multicast communication. Hence it is necessary to have a secret
key in the communication session where the entities participate. This secret key will be
shared only to the entity of that communication session. This proposed scheme [10] could
eliminate the weakness when compared with [4]. It is necessary to guarantee the backward
secrecy. It is necessary to secure the forward secrecy in order to prevent the attackers from
eavesdropping of the prior communications. If this is not done then the attackers could
easily hack the encrypted communication and they could decrypt them after obtaining the
access to the network. Attackers could misuse these decrypted information.
In [11], the proposed scheme satisfies the external attackers from consuming the encrypted
data. Moreover, it also avoids the internal attackers from hacking the data using their
methods. The author had used an administrative approach not the cryptographic method.
Several proofs of Unforgeability and batch verification security have also been stated. The
time cost of their operation algorithm has also been stated in the table given below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table 1: Time-cost operation of [11]
EPPA (Efficient and Privacy Preserving Aggregate) scheme has been proposed in [12], with
their computational complexity and residential user local GW and OA, and the
communication overhead of user-to-GW and GW-to-OA communications has been
explained. In this scheme, the encryption time could be reduced, since this compress the
multiple residential user data into compressed data. TRAD scheme uses one dimensional
data of a single ciphertext generated by the user. When m dimensional data was produced
then m ciphertext has to be generated. The computational cost of each user and the OA is
found to be low with the proposed EPPA when compared with the TRAD. Moreover,
communication overhead of the GW-to-OA is significantly reduced in the EPPA method.
EPPDR (Efficient Private Preserving Demand Response) Scheme has been proposed in
[14], which offers the secure session key that gives a secured communication between the
HAN and BG. In here, the previous session key (KUij-BGi) will be deleted by the new session
key (K` Uij-BGi). Hence it is not possible to obtain the previous key that will be deleted [20].
Therefore, the forward secrecy (FS) of users’ session keys is accomplished in the
anticipated EPPDR scheme. The information leakage between the forward secrecy and not
a forward secrecy (NFS) has been compared, which is shown in the figure given below.
From this it is inferred that the information leakage could happen only between the
encryption and the decryption by unauthorized adversary. Here the time is compared with
the discrete time intervals with the probably of the events to appear (Poisson distribution).
Moreover, it is also obtained that the information leakage in FS is comparatively low (than
NFS).
EPPA (Efficient and Privacy Preserving Aggregate) scheme has been proposed in [12], with
their computational complexity and residential user local GW and OA, and the
communication overhead of user-to-GW and GW-to-OA communications has been
explained. In this scheme, the encryption time could be reduced, since this compress the
multiple residential user data into compressed data. TRAD scheme uses one dimensional
data of a single ciphertext generated by the user. When m dimensional data was produced
then m ciphertext has to be generated. The computational cost of each user and the OA is
found to be low with the proposed EPPA when compared with the TRAD. Moreover,
communication overhead of the GW-to-OA is significantly reduced in the EPPA method.
EPPDR (Efficient Private Preserving Demand Response) Scheme has been proposed in
[14], which offers the secure session key that gives a secured communication between the
HAN and BG. In here, the previous session key (KUij-BGi) will be deleted by the new session
key (K` Uij-BGi). Hence it is not possible to obtain the previous key that will be deleted [20].
Therefore, the forward secrecy (FS) of users’ session keys is accomplished in the
anticipated EPPDR scheme. The information leakage between the forward secrecy and not
a forward secrecy (NFS) has been compared, which is shown in the figure given below.
From this it is inferred that the information leakage could happen only between the
encryption and the decryption by unauthorized adversary. Here the time is compared with
the discrete time intervals with the probably of the events to appear (Poisson distribution).
Moreover, it is also obtained that the information leakage in FS is comparatively low (than
NFS).
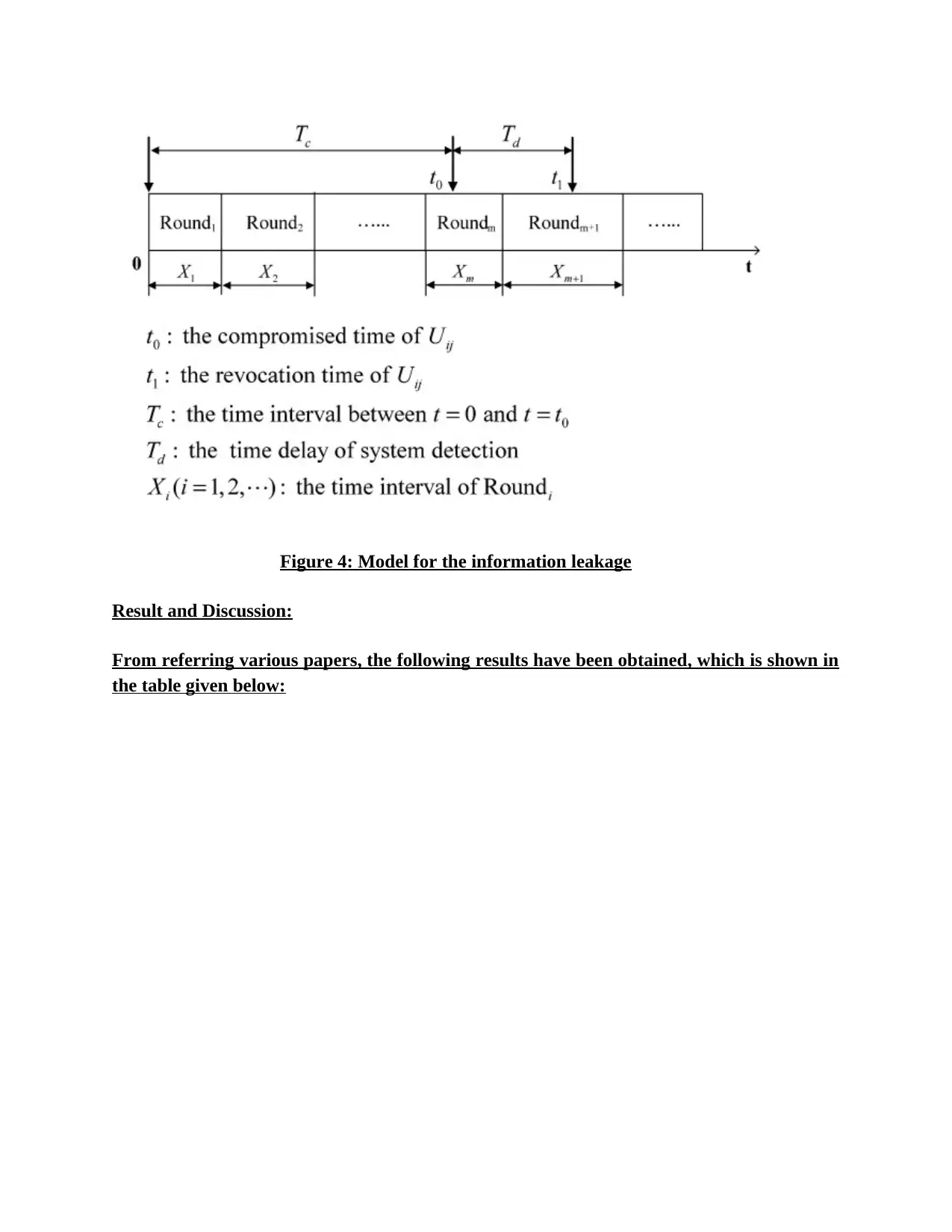
Figure 4: Model for the information leakage
Result and Discussion:
From referring various papers, the following results have been obtained, which is shown in
the table given below:
Result and Discussion:
From referring various papers, the following results have been obtained, which is shown in
the table given below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
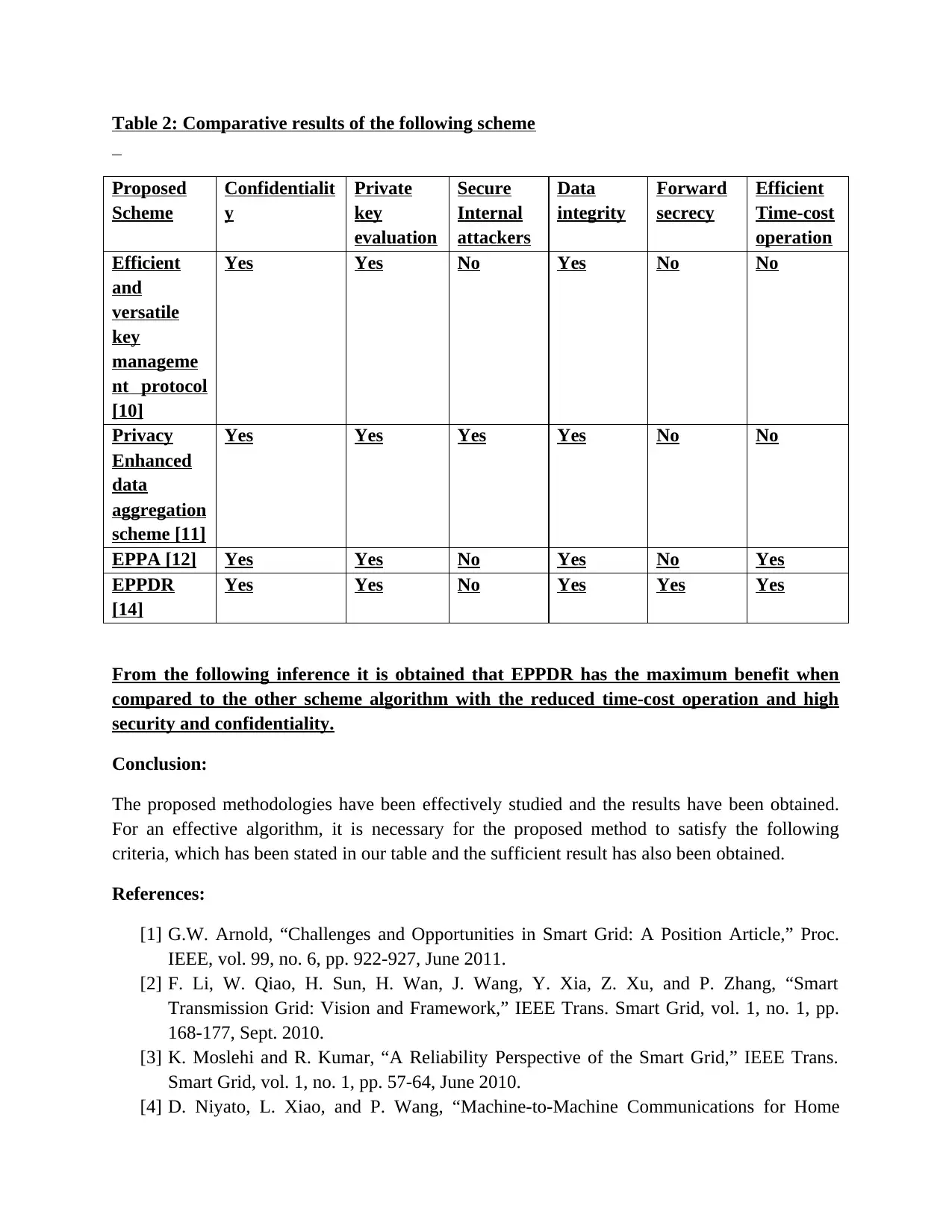
Table 2: Comparative results of the following scheme
Proposed
Scheme
Confidentialit
y
Private
key
evaluation
Secure
Internal
attackers
Data
integrity
Forward
secrecy
Efficient
Time-cost
operation
Efficient
and
versatile
key
manageme
nt protocol
[10]
Yes Yes No Yes No No
Privacy
Enhanced
data
aggregation
scheme [11]
Yes Yes Yes Yes No No
EPPA [12] Yes Yes No Yes No Yes
EPPDR
[14]
Yes Yes No Yes Yes Yes
From the following inference it is obtained that EPPDR has the maximum benefit when
compared to the other scheme algorithm with the reduced time-cost operation and high
security and confidentiality.
Conclusion:
The proposed methodologies have been effectively studied and the results have been obtained.
For an effective algorithm, it is necessary for the proposed method to satisfy the following
criteria, which has been stated in our table and the sufficient result has also been obtained.
References:
[1] G.W. Arnold, “Challenges and Opportunities in Smart Grid: A Position Article,” Proc.
IEEE, vol. 99, no. 6, pp. 922-927, June 2011.
[2] F. Li, W. Qiao, H. Sun, H. Wan, J. Wang, Y. Xia, Z. Xu, and P. Zhang, “Smart
Transmission Grid: Vision and Framework,” IEEE Trans. Smart Grid, vol. 1, no. 1, pp.
168-177, Sept. 2010.
[3] K. Moslehi and R. Kumar, “A Reliability Perspective of the Smart Grid,” IEEE Trans.
Smart Grid, vol. 1, no. 1, pp. 57-64, June 2010.
[4] D. Niyato, L. Xiao, and P. Wang, “Machine-to-Machine Communications for Home
Proposed
Scheme
Confidentialit
y
Private
key
evaluation
Secure
Internal
attackers
Data
integrity
Forward
secrecy
Efficient
Time-cost
operation
Efficient
and
versatile
key
manageme
nt protocol
[10]
Yes Yes No Yes No No
Privacy
Enhanced
data
aggregation
scheme [11]
Yes Yes Yes Yes No No
EPPA [12] Yes Yes No Yes No Yes
EPPDR
[14]
Yes Yes No Yes Yes Yes
From the following inference it is obtained that EPPDR has the maximum benefit when
compared to the other scheme algorithm with the reduced time-cost operation and high
security and confidentiality.
Conclusion:
The proposed methodologies have been effectively studied and the results have been obtained.
For an effective algorithm, it is necessary for the proposed method to satisfy the following
criteria, which has been stated in our table and the sufficient result has also been obtained.
References:
[1] G.W. Arnold, “Challenges and Opportunities in Smart Grid: A Position Article,” Proc.
IEEE, vol. 99, no. 6, pp. 922-927, June 2011.
[2] F. Li, W. Qiao, H. Sun, H. Wan, J. Wang, Y. Xia, Z. Xu, and P. Zhang, “Smart
Transmission Grid: Vision and Framework,” IEEE Trans. Smart Grid, vol. 1, no. 1, pp.
168-177, Sept. 2010.
[3] K. Moslehi and R. Kumar, “A Reliability Perspective of the Smart Grid,” IEEE Trans.
Smart Grid, vol. 1, no. 1, pp. 57-64, June 2010.
[4] D. Niyato, L. Xiao, and P. Wang, “Machine-to-Machine Communications for Home
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Energy Management System in Smart Grid,” IEEE Comm. Magazine, vol. 49, no. 4, pp.
53-59, Apr. 2011.
[5] Z.M. Fadlullah, M.M. Fouda, N. Kato, A. Takeuchi, N. Iwasaki, and Y. Nozaki, “Toward
Intelligent Machine-to-Machine Communications in Smart Grid,” IEEE Comm.
Magazine, vol. 49, no. 4, pp. 60-65, Apr. 2011.
[6] H. Liang, B. Choi, W. Zhuang, and X. Shen, “Towards Optimal Energy Store-Carry-and-
Deliver for Phevs Via v2g System,” Proc. IEEE INFOCOM ’12, pp. 25-30, Mar. 2012.
[7] P. McDaniel and S. McLaughlin, “Security and Privacy Challenges in the Smart Grid,”
IEEE Security & Privacy, vol. 7, no. 3, pp. 75-77, May/June 2009.
[8] Z.M. Fadlullah, M.M. Fouda, X. Shen, Y. Nozaki, and N. Kato, “An Early Warning
System Against Malicious Activities for Smart Grid Communications,” IEEE Network
Magazine, vol. 25, no. 5, pp. 50- 55, Sept./Oct. 2011.
[9] M.M. Fouda, Z.M. Fadlullah, N. Kato, R. Lu, and X. Shen, “A Light-Weight Message
Authentication Scheme for Smart Grid Communications,” IEEE Trans. Smart Grid, vol.
2, no. 4, pp. 675- 685, Dec. 2011.
[10] Y. Yuan, Z. Li, and K. Ren, “Modeling Load Redistribution Attacks in Power
Systems,” IEEE Trans. Smart Grid, vol. 2, no. 2, pp. 382-390, June 2011.
[11] J. Naruchitparames, M.H. Gunes, and C.Y. Evrenosoglu, “Secure
Communications in the Smart Grid,” in Proc. IEEE CCNC '11, Las Vegas, Nevada, USA,
Jan. 2011, pp. 1171-1175.
[12] G.M. Coates, K.M. Hopkinson, S.R. Graham, and S.H. Kurkowski, “A Trust
System Architecture for SCADA Network Security,” IEEE Trans. Power Delivery, vol.
25, no. 1, pp. 158-169, Jan. 2010.
[13] D. Wu and C. Zhou, “Fault-Tolerant and Scalable Key Management for Smart
Grid,” IEEE Trans. Smart Grid, vol. 2, no. 2, pp. 375-381, 2011.
[14] J. Shi, R. Zhang, Y. Liu, and Y. Zhang, ‘‘Prisense: PrivacyPreserving Data
Aggregation in People-Centric Urban Sensing Systems,’’ in Proc. IEEE INFOCOM,
2010, pp. 1-9.
[15] X. Lin, R. Lu, and X. Shen, ‘‘MDPA: Multidimensional PrivacyPreserving
Aggregation Scheme for Wireless Sensor Networks,’’ Wireless Commun. Mobile
Comput., vol. 10, no. 6, pp. 843-856, June 2010.
[16] D. Seo, H. Lee, and A. Perrig, ‘‘Secure and Efficient CapabilityBased Power
Management in the Smart Grid,’’ in Proc. IEEE ISPAW, 2011, pp. 119-126.
[17] J. Xia and Y. Wang, ‘‘Secure Key Distribution for the Smart Grid,’’ IEEE Trans.
Smart Grid, vol. 3, no. 3, pp. 1437-1443, Sept. 2012.
[18] X. Wang and P. Yi, “Security framework for wireless communications in smart
distribution grid,” IEEE Trans. Smart Grid, vol. 2, no. 4, pp. 809–818, Dec. 2011.
[19] H. Nicanfar and V. C. M. Leung, “Password-authenticated clusterbased group key
agreement for smart grid communication,” Security Commun. Networks 2013, DOI:
11.1002/sec.726.
[20] P. Failla, “Privacy-preserving processing of biometric templates by homomorphic
53-59, Apr. 2011.
[5] Z.M. Fadlullah, M.M. Fouda, N. Kato, A. Takeuchi, N. Iwasaki, and Y. Nozaki, “Toward
Intelligent Machine-to-Machine Communications in Smart Grid,” IEEE Comm.
Magazine, vol. 49, no. 4, pp. 60-65, Apr. 2011.
[6] H. Liang, B. Choi, W. Zhuang, and X. Shen, “Towards Optimal Energy Store-Carry-and-
Deliver for Phevs Via v2g System,” Proc. IEEE INFOCOM ’12, pp. 25-30, Mar. 2012.
[7] P. McDaniel and S. McLaughlin, “Security and Privacy Challenges in the Smart Grid,”
IEEE Security & Privacy, vol. 7, no. 3, pp. 75-77, May/June 2009.
[8] Z.M. Fadlullah, M.M. Fouda, X. Shen, Y. Nozaki, and N. Kato, “An Early Warning
System Against Malicious Activities for Smart Grid Communications,” IEEE Network
Magazine, vol. 25, no. 5, pp. 50- 55, Sept./Oct. 2011.
[9] M.M. Fouda, Z.M. Fadlullah, N. Kato, R. Lu, and X. Shen, “A Light-Weight Message
Authentication Scheme for Smart Grid Communications,” IEEE Trans. Smart Grid, vol.
2, no. 4, pp. 675- 685, Dec. 2011.
[10] Y. Yuan, Z. Li, and K. Ren, “Modeling Load Redistribution Attacks in Power
Systems,” IEEE Trans. Smart Grid, vol. 2, no. 2, pp. 382-390, June 2011.
[11] J. Naruchitparames, M.H. Gunes, and C.Y. Evrenosoglu, “Secure
Communications in the Smart Grid,” in Proc. IEEE CCNC '11, Las Vegas, Nevada, USA,
Jan. 2011, pp. 1171-1175.
[12] G.M. Coates, K.M. Hopkinson, S.R. Graham, and S.H. Kurkowski, “A Trust
System Architecture for SCADA Network Security,” IEEE Trans. Power Delivery, vol.
25, no. 1, pp. 158-169, Jan. 2010.
[13] D. Wu and C. Zhou, “Fault-Tolerant and Scalable Key Management for Smart
Grid,” IEEE Trans. Smart Grid, vol. 2, no. 2, pp. 375-381, 2011.
[14] J. Shi, R. Zhang, Y. Liu, and Y. Zhang, ‘‘Prisense: PrivacyPreserving Data
Aggregation in People-Centric Urban Sensing Systems,’’ in Proc. IEEE INFOCOM,
2010, pp. 1-9.
[15] X. Lin, R. Lu, and X. Shen, ‘‘MDPA: Multidimensional PrivacyPreserving
Aggregation Scheme for Wireless Sensor Networks,’’ Wireless Commun. Mobile
Comput., vol. 10, no. 6, pp. 843-856, June 2010.
[16] D. Seo, H. Lee, and A. Perrig, ‘‘Secure and Efficient CapabilityBased Power
Management in the Smart Grid,’’ in Proc. IEEE ISPAW, 2011, pp. 119-126.
[17] J. Xia and Y. Wang, ‘‘Secure Key Distribution for the Smart Grid,’’ IEEE Trans.
Smart Grid, vol. 3, no. 3, pp. 1437-1443, Sept. 2012.
[18] X. Wang and P. Yi, “Security framework for wireless communications in smart
distribution grid,” IEEE Trans. Smart Grid, vol. 2, no. 4, pp. 809–818, Dec. 2011.
[19] H. Nicanfar and V. C. M. Leung, “Password-authenticated clusterbased group key
agreement for smart grid communication,” Security Commun. Networks 2013, DOI:
11.1002/sec.726.
[20] P. Failla, “Privacy-preserving processing of biometric templates by homomorphic

encryption,” Ph.D. dissertation, Dept. Inf. Eng., Univ. Siena, Siena, Italy, 2010.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



