Securing Systems: IPTable Firewall Configuration, Security Report
VerifiedAdded on 2022/10/07
|15
|2685
|41
Report
AI Summary
This report details the configuration and security aspects of the IPTable firewall in a Linux environment. The student sets up and configures the firewall to implement specific security measures, including rejecting Telnet packets, allowing Telnet remote connections, denying ping requests, rejecting traffic to the MySQL server, blocking incoming traffic to the virtual machine's IP address, and allowing inbound traffic on port 80 while rejecting outbound traffic. The report includes screenshots of the configurations and the results of the tests. It discusses the advantages and disadvantages of IPTable, explores potential security holes, and suggests methods for improvement. The report covers the installation of necessary packages, such as SSH and a web server, and ensures their proper functioning before configuring the firewall. The student also provides insights into how to overcome IPTable's disadvantages and improve system security.

Running head: SECURING SYSTEM USING IPTABLE FIREWALL
Securing system using IPTable firewall
Name of the Student
Name of the University
Authors note
Securing system using IPTable firewall
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2SECURING SYSTEM USING IPTABLE FIREWALL
Introduction
Along with the increased accessibility to the internet and the administrator of the
system creates filtering rules chains in which the order is significant. Therefore in order to
protect network devices, organizational network in order to protect both the organizational
data as well as individual data it is important to have well configured firewall in place. The
Linux operating system comes with the inbuilt firewall that can be used to protect the
computer systems from unintended intrusions. With the benefits there are some draw backs
of this firewall too. The iptable firewall needs to be configured by the system administrators.
With misconfigured firewalls it is possible to unintentionally create backdoors for the
attackers which can lead to the massive data breach or network attacks carried out by the
attackers.
This means that insertion or removal of different rules in inappropriate order leads to
errors. In addition to that, as the size and number of the data packets or chains determines the
complexity of any kind of rule set, thus it can be stated that iptable firewall consisting too
many large chains of rules becomes very difficult to understand as well as modify them at a
later time. In many of the cases it becomes difficult to know the important requests that are
granted to pass within the firewall filter.
In any network the firewalls have become a foundation for the basic security
implementation against the external attacks to the certain networks along with the many
security policies. The rules and policies used in the firewalls has been grown in complexity in
order to secure the networks from different attacks. Along with the packet filtering process
the typical firewall is now capable of providing state full inspection of the data packets.
Among different other drawbacks of the firewalls one of the most important is the
growing complexity in correctly configuring a specific firewall with the appropriate rule set.
Introduction
Along with the increased accessibility to the internet and the administrator of the
system creates filtering rules chains in which the order is significant. Therefore in order to
protect network devices, organizational network in order to protect both the organizational
data as well as individual data it is important to have well configured firewall in place. The
Linux operating system comes with the inbuilt firewall that can be used to protect the
computer systems from unintended intrusions. With the benefits there are some draw backs
of this firewall too. The iptable firewall needs to be configured by the system administrators.
With misconfigured firewalls it is possible to unintentionally create backdoors for the
attackers which can lead to the massive data breach or network attacks carried out by the
attackers.
This means that insertion or removal of different rules in inappropriate order leads to
errors. In addition to that, as the size and number of the data packets or chains determines the
complexity of any kind of rule set, thus it can be stated that iptable firewall consisting too
many large chains of rules becomes very difficult to understand as well as modify them at a
later time. In many of the cases it becomes difficult to know the important requests that are
granted to pass within the firewall filter.
In any network the firewalls have become a foundation for the basic security
implementation against the external attacks to the certain networks along with the many
security policies. The rules and policies used in the firewalls has been grown in complexity in
order to secure the networks from different attacks. Along with the packet filtering process
the typical firewall is now capable of providing state full inspection of the data packets.
Among different other drawbacks of the firewalls one of the most important is the
growing complexity in correctly configuring a specific firewall with the appropriate rule set.

3SECURING SYSTEM USING IPTABLE FIREWALL
Subtle errors in the configuration of the firewalls may be very challenging to detect among
the lots of rule chains. The subtle error can be responsible for opening a backdoor for the
malicious intruder so that they can carry out denial of service attack or similar other attacks.
The iptables firewall of Linux operating system protects a computer network through
the comparison of the data packets coming through the network traffic against some
implemented rules. These implemented rules are the characteristics that a data packet needs
to match in order to get into the network or dropped out of a certain network or any other
action that needs to be taken for the data packets that are matching with the implemented
rules. These implemented rules are structured in different groups which are known as the
chains. A received packet to a network is checked against the chain or the set of rules
sequentially. Whenever the received data packet matches with one of the implemented rules,
it start executing the associated action declared for the rule and furthermore is not verified
against others rules of the chain.
There are numerous options so that it can be established which packets match a
specific type of rule. The implemented rules of the firewall can match protocol type from
which the packet is coming, source/destination ip/port, interface used for sending the data
packet as well as relation with the previously sent data packets and so on.
Whenever any of the defined pattern/rules matches with the data packets, the
specified actions takes place which is one of drop the packet, allow the packet to the network.
In addition to that, this policies can also move the data packet to different other rule sets for
further processing or log the occurrence in the concerned log files.
Utility of Iptables
The firewalls are frequently introduced away from the rest of the computer networks
so no approaching data packets or request get legitimately to the secured network resources.
Subtle errors in the configuration of the firewalls may be very challenging to detect among
the lots of rule chains. The subtle error can be responsible for opening a backdoor for the
malicious intruder so that they can carry out denial of service attack or similar other attacks.
The iptables firewall of Linux operating system protects a computer network through
the comparison of the data packets coming through the network traffic against some
implemented rules. These implemented rules are the characteristics that a data packet needs
to match in order to get into the network or dropped out of a certain network or any other
action that needs to be taken for the data packets that are matching with the implemented
rules. These implemented rules are structured in different groups which are known as the
chains. A received packet to a network is checked against the chain or the set of rules
sequentially. Whenever the received data packet matches with one of the implemented rules,
it start executing the associated action declared for the rule and furthermore is not verified
against others rules of the chain.
There are numerous options so that it can be established which packets match a
specific type of rule. The implemented rules of the firewall can match protocol type from
which the packet is coming, source/destination ip/port, interface used for sending the data
packet as well as relation with the previously sent data packets and so on.
Whenever any of the defined pattern/rules matches with the data packets, the
specified actions takes place which is one of drop the packet, allow the packet to the network.
In addition to that, this policies can also move the data packet to different other rule sets for
further processing or log the occurrence in the concerned log files.
Utility of Iptables
The firewalls are frequently introduced away from the rest of the computer networks
so no approaching data packets or request get legitimately to the secured network resources.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4SECURING SYSTEM USING IPTABLE FIREWALL
In the event that it is designed appropriately, the other side framework of the firewall are
guarded from the opposite direction framework. Firewalls for the most part channel traffic
dependent on two procedures:
A firewall can grant any traffic aside from what is designated as limited. It
actually depending on the utilized firewall type, the goal address, the sources
and the ports.
A firewall can reject any traffic which is not meeting the particular criteria
dependent on the system layer. Depending on this system layer the firewall
executes.
These criteria are mainly utilized for determining whether the traffic should be
allowed through changes from one kind to another.
Firewalls can be concerned about the type of traffic or with the goal or source
locations and ports.
A firewall is capable of using complex guidelines dependent on application
information investigation for deciding whether the traffic ought to be allowed
through.
The majority of the iptable packet filters follow the principle of first-hit. Each of the
rule defined in the rule set is consisting different types of parameters which mainly
correspond to the network packet headers. All of the packets, traversing within firewall is
matched against the rules defined in filtering table. In this aspect, the rule of which
parameters are having the similar values with the packet parameters under matching progress
is applied to it. This instance decides whether it better to let the packet go further or it is
better to just drop it. Specific rules which are succeeding the rule which is being matched are
not accounted. In such of the incidents when the rule is not discovered, the global rule from
In the event that it is designed appropriately, the other side framework of the firewall are
guarded from the opposite direction framework. Firewalls for the most part channel traffic
dependent on two procedures:
A firewall can grant any traffic aside from what is designated as limited. It
actually depending on the utilized firewall type, the goal address, the sources
and the ports.
A firewall can reject any traffic which is not meeting the particular criteria
dependent on the system layer. Depending on this system layer the firewall
executes.
These criteria are mainly utilized for determining whether the traffic should be
allowed through changes from one kind to another.
Firewalls can be concerned about the type of traffic or with the goal or source
locations and ports.
A firewall is capable of using complex guidelines dependent on application
information investigation for deciding whether the traffic ought to be allowed
through.
The majority of the iptable packet filters follow the principle of first-hit. Each of the
rule defined in the rule set is consisting different types of parameters which mainly
correspond to the network packet headers. All of the packets, traversing within firewall is
matched against the rules defined in filtering table. In this aspect, the rule of which
parameters are having the similar values with the packet parameters under matching progress
is applied to it. This instance decides whether it better to let the packet go further or it is
better to just drop it. Specific rules which are succeeding the rule which is being matched are
not accounted. In such of the incidents when the rule is not discovered, the global rule from
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5SECURING SYSTEM USING IPTABLE FIREWALL
the set of rule is applied over the packet. Checking of the global rule is done at the last after
matching to all the other rules of the rule set is done.
It is important to ensure that the security policy associated with the firewall, is
successfully implemented to the network it belongs and it is done quite efficiently. Rule set
must be evaluated properly for determination of any type of errors which includes duplicate
entry, conflicting and shadowed type of rules. In the cases of error determination these errors
must be rectified proactively. Rearrangement of the rules can be done for making the process
of filtering efficient in an optimal procedure. There can be difficulty in the rules
rearrangement process due to the property of precedence of the rule set that is coming from
the principle of first-hit of the packet filters.
Sample screenshots of the using IPtables in virtual environment
Following are the list of commands that can be used for the installinig the webserver
and ssh.
Installing Web-server
#sudo apt-get install apache2
Checking the installation and package version :
#apache2 -v
The following are the screenshots of different commands and options that can be
used for the configuring the iptable firewall.
Any rule of iptable is consist of the following components;
Table’s component is the name of set of chains.
The Chain is considered as collection of rules.
the set of rule is applied over the packet. Checking of the global rule is done at the last after
matching to all the other rules of the rule set is done.
It is important to ensure that the security policy associated with the firewall, is
successfully implemented to the network it belongs and it is done quite efficiently. Rule set
must be evaluated properly for determination of any type of errors which includes duplicate
entry, conflicting and shadowed type of rules. In the cases of error determination these errors
must be rectified proactively. Rearrangement of the rules can be done for making the process
of filtering efficient in an optimal procedure. There can be difficulty in the rules
rearrangement process due to the property of precedence of the rule set that is coming from
the principle of first-hit of the packet filters.
Sample screenshots of the using IPtables in virtual environment
Following are the list of commands that can be used for the installinig the webserver
and ssh.
Installing Web-server
#sudo apt-get install apache2
Checking the installation and package version :
#apache2 -v
The following are the screenshots of different commands and options that can be
used for the configuring the iptable firewall.
Any rule of iptable is consist of the following components;
Table’s component is the name of set of chains.
The Chain is considered as collection of rules.
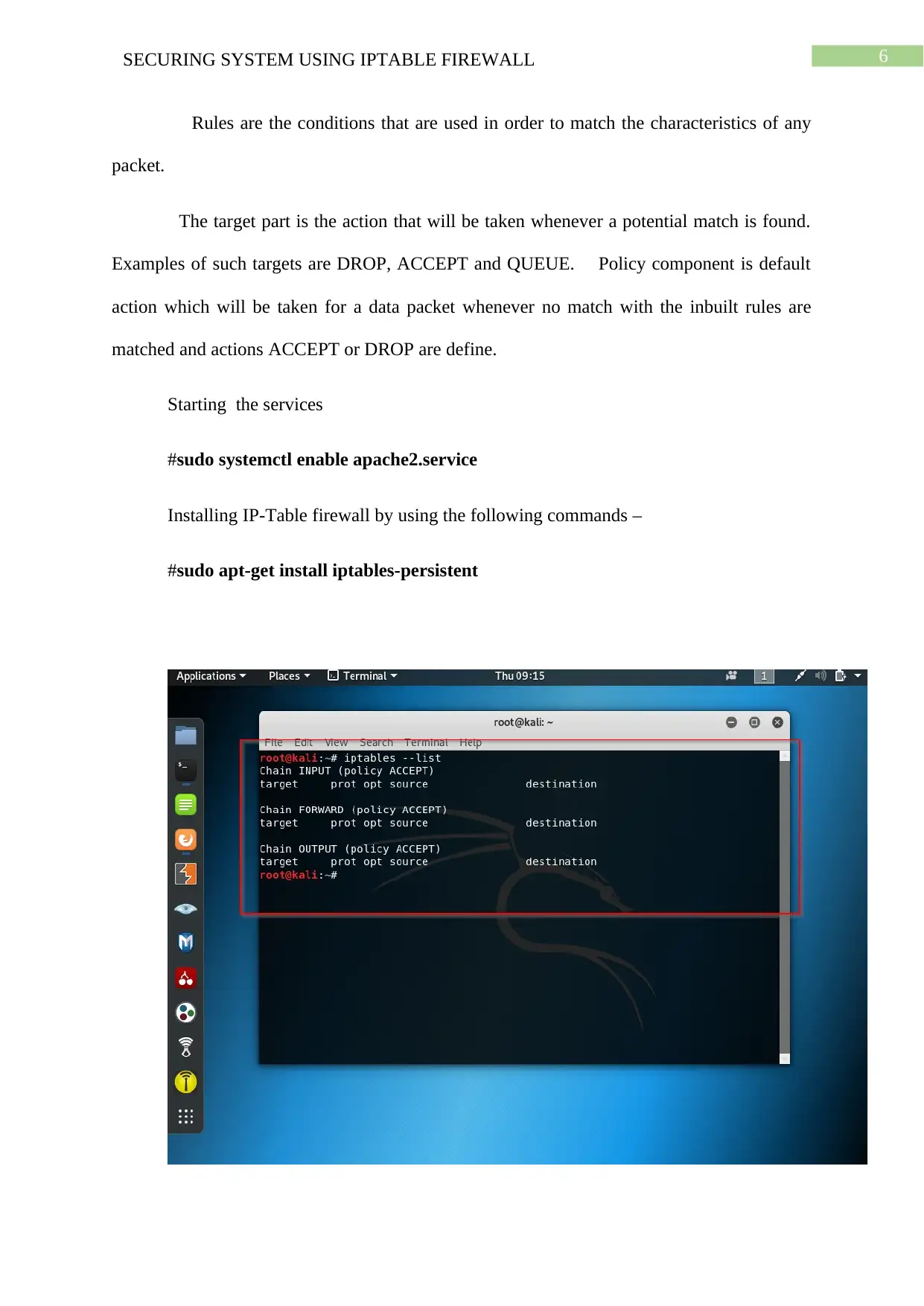
6SECURING SYSTEM USING IPTABLE FIREWALL
Rules are the conditions that are used in order to match the characteristics of any
packet.
The target part is the action that will be taken whenever a potential match is found.
Examples of such targets are DROP, ACCEPT and QUEUE. Policy component is default
action which will be taken for a data packet whenever no match with the inbuilt rules are
matched and actions ACCEPT or DROP are define.
Starting the services
#sudo systemctl enable apache2.service
Installing IP-Table firewall by using the following commands –
#sudo apt-get install iptables-persistent
Rules are the conditions that are used in order to match the characteristics of any
packet.
The target part is the action that will be taken whenever a potential match is found.
Examples of such targets are DROP, ACCEPT and QUEUE. Policy component is default
action which will be taken for a data packet whenever no match with the inbuilt rules are
matched and actions ACCEPT or DROP are define.
Starting the services
#sudo systemctl enable apache2.service
Installing IP-Table firewall by using the following commands –
#sudo apt-get install iptables-persistent
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
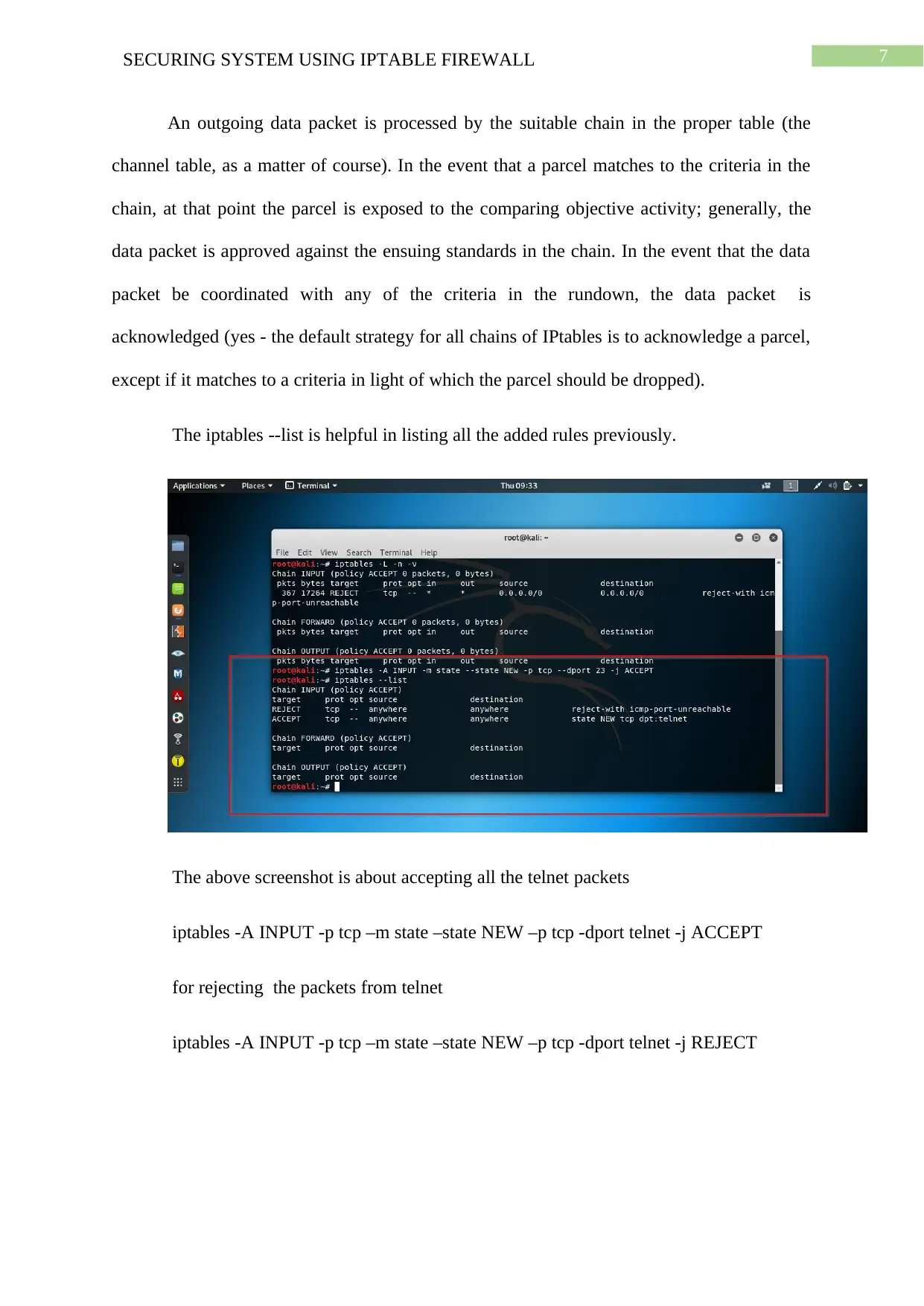
7SECURING SYSTEM USING IPTABLE FIREWALL
An outgoing data packet is processed by the suitable chain in the proper table (the
channel table, as a matter of course). In the event that a parcel matches to the criteria in the
chain, at that point the parcel is exposed to the comparing objective activity; generally, the
data packet is approved against the ensuing standards in the chain. In the event that the data
packet be coordinated with any of the criteria in the rundown, the data packet is
acknowledged (yes - the default strategy for all chains of IPtables is to acknowledge a parcel,
except if it matches to a criteria in light of which the parcel should be dropped).
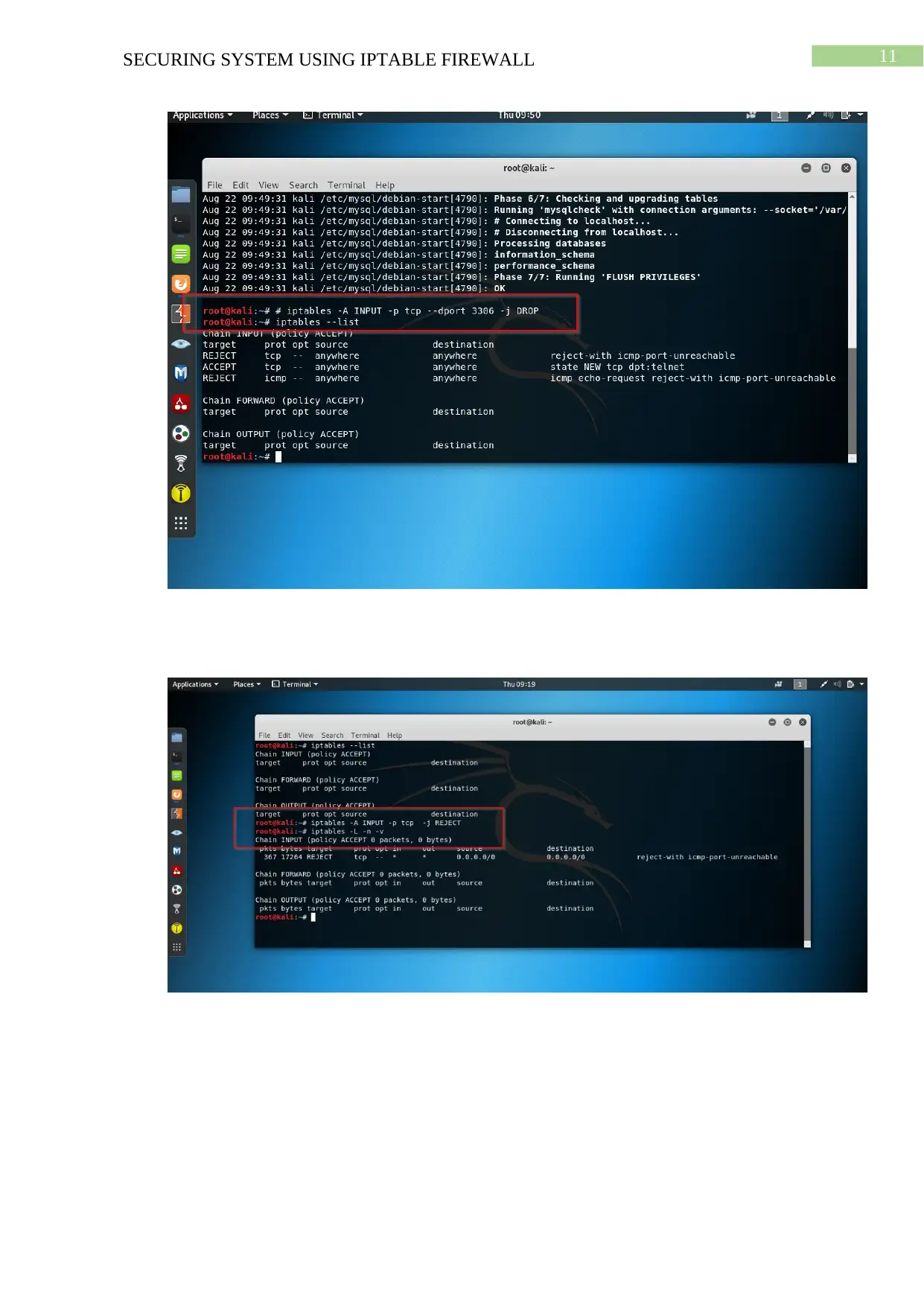
The iptables --list is helpful in listing all the added rules previously.
The above screenshot is about accepting all the telnet packets
iptables -A INPUT -p tcp –m state –state NEW –p tcp -dport telnet -j ACCEPT
for rejecting the packets from telnet
iptables -A INPUT -p tcp –m state –state NEW –p tcp -dport telnet -j REJECT
An outgoing data packet is processed by the suitable chain in the proper table (the
channel table, as a matter of course). In the event that a parcel matches to the criteria in the
chain, at that point the parcel is exposed to the comparing objective activity; generally, the
data packet is approved against the ensuing standards in the chain. In the event that the data
packet be coordinated with any of the criteria in the rundown, the data packet is
acknowledged (yes - the default strategy for all chains of IPtables is to acknowledge a parcel,
except if it matches to a criteria in light of which the parcel should be dropped).
The iptables --list is helpful in listing all the added rules previously.
The above screenshot is about accepting all the telnet packets
iptables -A INPUT -p tcp –m state –state NEW –p tcp -dport telnet -j ACCEPT
for rejecting the packets from telnet
iptables -A INPUT -p tcp –m state –state NEW –p tcp -dport telnet -j REJECT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
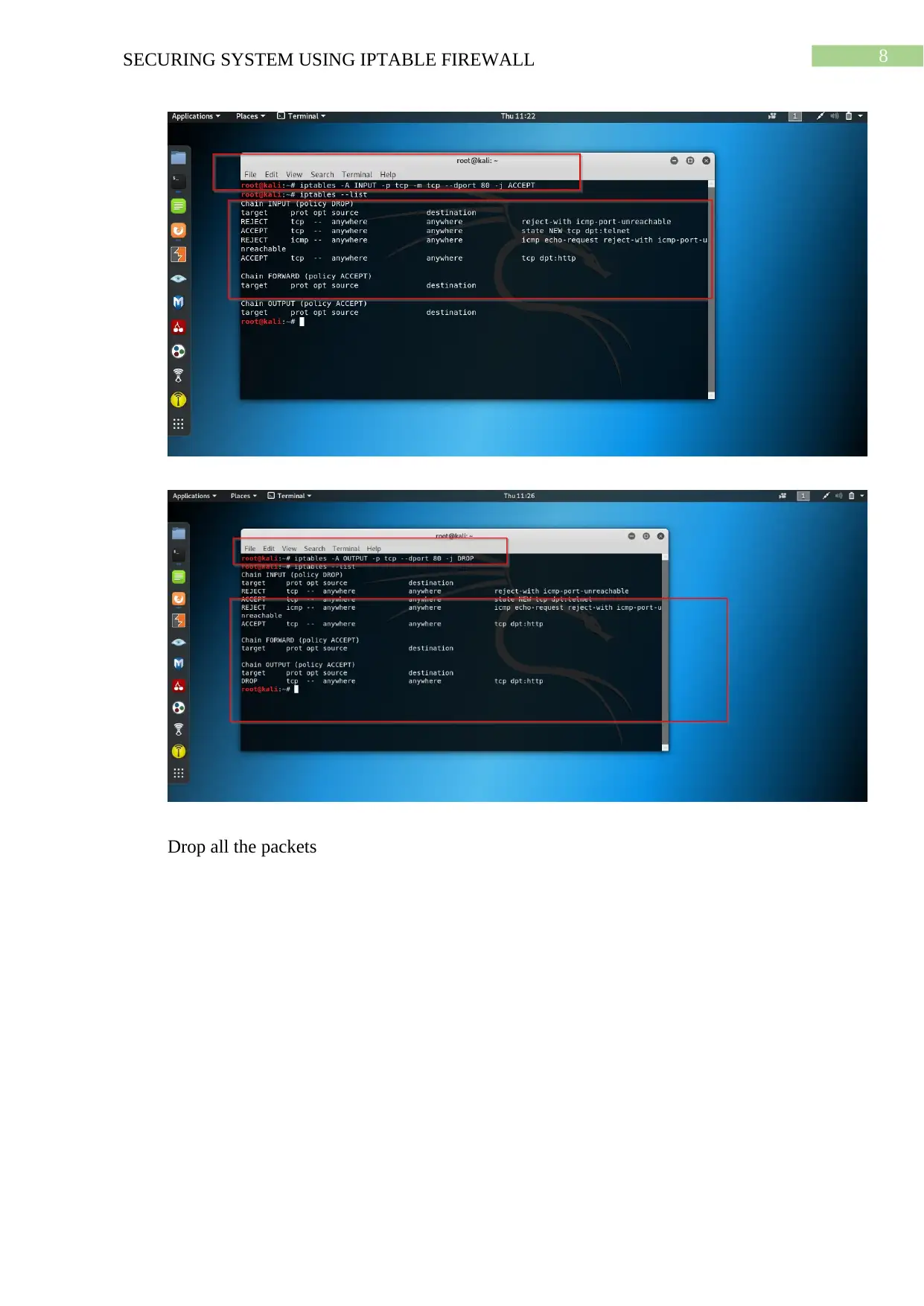
8SECURING SYSTEM USING IPTABLE FIREWALL
Drop all the packets
Drop all the packets
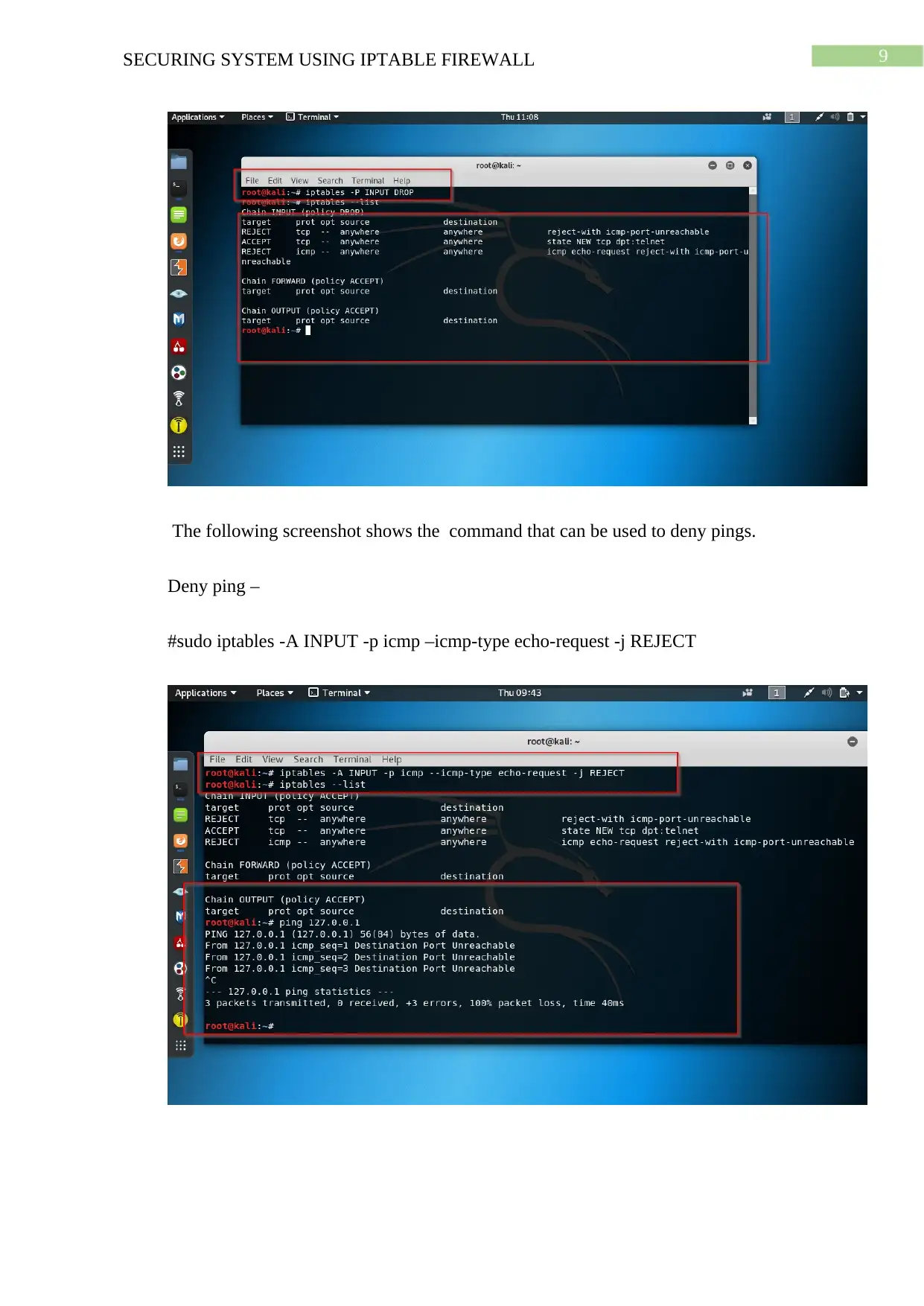
9SECURING SYSTEM USING IPTABLE FIREWALL
The following screenshot shows the command that can be used to deny pings.
Deny ping –
#sudo iptables -A INPUT -p icmp –icmp-type echo-request -j REJECT
The following screenshot shows the command that can be used to deny pings.
Deny ping –
#sudo iptables -A INPUT -p icmp –icmp-type echo-request -j REJECT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
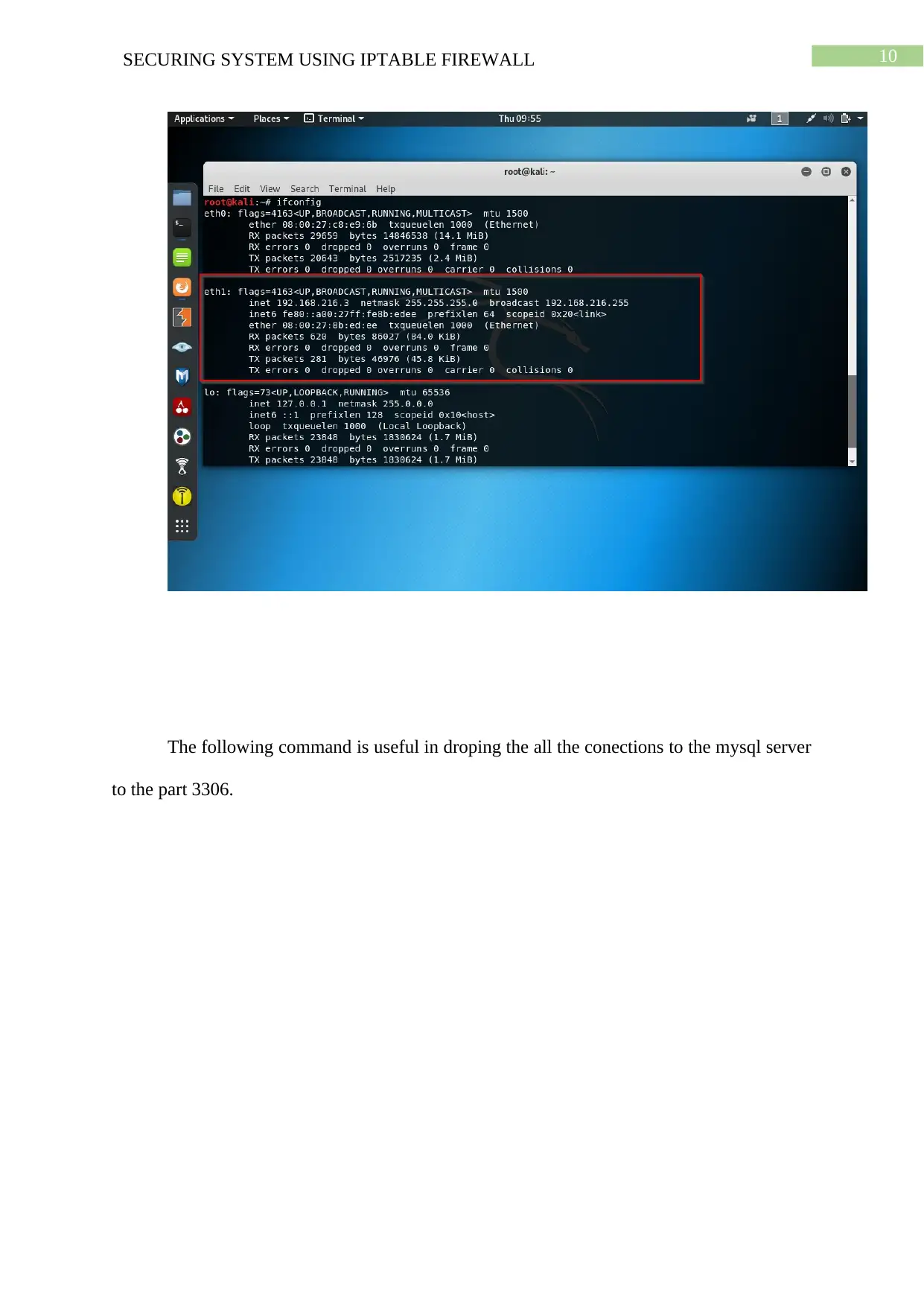
10SECURING SYSTEM USING IPTABLE FIREWALL
The following command is useful in droping the all the conections to the mysql server
to the part 3306.
The following command is useful in droping the all the conections to the mysql server
to the part 3306.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11SECURING SYSTEM USING IPTABLE FIREWALL

12SECURING SYSTEM USING IPTABLE FIREWALL
Advantages of IPtables
The inbuilt firewall iptables is helpful in allow and disallow the data packets
to lowest and closest level of access inside the network implemented by the
linux kernel firewall. This is considered as the most robust as well as
reliable software firewall.
This firewall is a very flexible in order to control the access of the data packets
through command line.
With every tweak by the administrators it is possible to make the firewall
adaptable to protect a single computer as well as a complete network.
The ipchain implementation is supported by the backward compatibility.
Disadvantages of IPtables
A misconfigured iptable firewall can lead to the network security breach and
consequently intrusion to the system. One of the example of this issues is placing new
firewall rules that consist of parameters which are proper subset of an existing firewall rule.
In this scenario, newly created firewall rule would not be used as well as behaviour of the
firewall might differ from the standard one which is anticipated by administrators.
Once the table is misconfigured by the administrators then it is quite cumbersome task to
restore the system or the network traffic on track again. The situation becomes worse if the
firewall is remotely tampered.
Compared to other tools available in Linux, the iptable does not provide a good GUI wrapper
for the new users as the numerous features of this tool can be intimidating for users and same
goes for the for the documentation of this tool.
Advantages of IPtables
The inbuilt firewall iptables is helpful in allow and disallow the data packets
to lowest and closest level of access inside the network implemented by the
linux kernel firewall. This is considered as the most robust as well as
reliable software firewall.
This firewall is a very flexible in order to control the access of the data packets
through command line.
With every tweak by the administrators it is possible to make the firewall
adaptable to protect a single computer as well as a complete network.
The ipchain implementation is supported by the backward compatibility.
Disadvantages of IPtables
A misconfigured iptable firewall can lead to the network security breach and
consequently intrusion to the system. One of the example of this issues is placing new
firewall rules that consist of parameters which are proper subset of an existing firewall rule.
In this scenario, newly created firewall rule would not be used as well as behaviour of the
firewall might differ from the standard one which is anticipated by administrators.
Once the table is misconfigured by the administrators then it is quite cumbersome task to
restore the system or the network traffic on track again. The situation becomes worse if the
firewall is remotely tampered.
Compared to other tools available in Linux, the iptable does not provide a good GUI wrapper
for the new users as the numerous features of this tool can be intimidating for users and same
goes for the for the documentation of this tool.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





