Internet of Things: Vision and Architecture
VerifiedAdded on 2020/03/23
|4
|2314
|59
AI Summary
This assignment delves into the realm of the Internet of Things (IoT), examining its fundamental vision and defining architectural components. It explores various perspectives on IoT from leading researchers and organizations, including potential benefits and challenges associated with this transformative technology.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Security Challenges in Emerging Networks
Internet of Things
[Authors Name/s per 1st Affiliation (Author)] [Authors Name/s per 2nd Affiliation (Author)]
Abstract— Internet of Things defines a vision of
expanding the existing connections of the internet to
include a fully autonomous system. This report
highlights this technology and the security challenges
it presents.
Keywords— IoT, Security, RFID
I. INTRODUCTION
Internet of things (IoT) represents a dynamic shift in
the operational structure of the internet where
technological objects and gadget are holistically
embroiled into a worldwide network. In this network,
these devices identify themselves autonomously and
share information based on their needs and those of their
users. Therefore, as a future technology IoT represent the
next evolution of the internet where technology will take
advantage of the advancement in digital systems more so,
virtualization, computing power and system
miniaturization [1]. Furthermore, it is through IoT
technology that smart systems will be developed having
the ability to function without human intervention. In
essence, the implementation of IoT will signal the start of
smart cities, an outcome already seen today. Now, this
report analyses IoT as a technology including the security
challenges and threats that will be experienced as a result
of its implementation.
II. LITERATURE REVIEW
In the current world, the foundational concepts
of IoT are already being seen, things like smart
television systems, smart watches and smart phones are
propelling the digital era into a smart society. These
gadgets rarely need human intervention to operate, an
outcome that is used to define a smart object or device.
Moreover, these devices are designed based on the needs
of the users which make them dynamic and versatile as
compared to conventional systems that were developed
based on the existing conditions [2]. Again, this shift in
the design of technological system outlines the
parameters needed to implement IoT where intelligence
and self-awareness are critical components. However, in
all the research and discussion given on the topic, no
single accepted definition is given on the term (IoT)
other than the ability to add intelligence into the various
working environments [3].
IoT Technologies
To increase the worldwide connection of
devices, extensive networks are needed which outlines
the importance of the internet in the future of IoT. In
fact, its integral role in connectivity outlines why smart
systems and even IoT are named as its next evolution.
However, at the same time, the digital environment has
to consider the demands made by the end users
particularly based on their convenience requirements.
This demand necessitates the need for agile and dynamic
systems, factors that have led to the growth of wireless
technology, a centre mark for IoT [4]. In essence,
wireless technologies will act as the foundation of IoT
connecting different data centres, devices and the
complementary features (sensors and actuators).
Now, the complementary features (sensors and
actuators) will enable the devices to connect with each
other based on various identification technologies. At the
moment, RFID (radio frequency identification) is still
the main technology proposed for IoT as it serves the
connection purpose and has multiple operational benefits
such as simple design structure and minimal cost.
Furthermore, RFID can be integrated with the existing
internet technologies more so IP (Internet Protocol)
addressing which is majorly used to connect and
Internet of Things
[Authors Name/s per 1st Affiliation (Author)] [Authors Name/s per 2nd Affiliation (Author)]
Abstract— Internet of Things defines a vision of
expanding the existing connections of the internet to
include a fully autonomous system. This report
highlights this technology and the security challenges
it presents.
Keywords— IoT, Security, RFID
I. INTRODUCTION
Internet of things (IoT) represents a dynamic shift in
the operational structure of the internet where
technological objects and gadget are holistically
embroiled into a worldwide network. In this network,
these devices identify themselves autonomously and
share information based on their needs and those of their
users. Therefore, as a future technology IoT represent the
next evolution of the internet where technology will take
advantage of the advancement in digital systems more so,
virtualization, computing power and system
miniaturization [1]. Furthermore, it is through IoT
technology that smart systems will be developed having
the ability to function without human intervention. In
essence, the implementation of IoT will signal the start of
smart cities, an outcome already seen today. Now, this
report analyses IoT as a technology including the security
challenges and threats that will be experienced as a result
of its implementation.
II. LITERATURE REVIEW
In the current world, the foundational concepts
of IoT are already being seen, things like smart
television systems, smart watches and smart phones are
propelling the digital era into a smart society. These
gadgets rarely need human intervention to operate, an
outcome that is used to define a smart object or device.
Moreover, these devices are designed based on the needs
of the users which make them dynamic and versatile as
compared to conventional systems that were developed
based on the existing conditions [2]. Again, this shift in
the design of technological system outlines the
parameters needed to implement IoT where intelligence
and self-awareness are critical components. However, in
all the research and discussion given on the topic, no
single accepted definition is given on the term (IoT)
other than the ability to add intelligence into the various
working environments [3].
IoT Technologies
To increase the worldwide connection of
devices, extensive networks are needed which outlines
the importance of the internet in the future of IoT. In
fact, its integral role in connectivity outlines why smart
systems and even IoT are named as its next evolution.
However, at the same time, the digital environment has
to consider the demands made by the end users
particularly based on their convenience requirements.
This demand necessitates the need for agile and dynamic
systems, factors that have led to the growth of wireless
technology, a centre mark for IoT [4]. In essence,
wireless technologies will act as the foundation of IoT
connecting different data centres, devices and the
complementary features (sensors and actuators).
Now, the complementary features (sensors and
actuators) will enable the devices to connect with each
other based on various identification technologies. At the
moment, RFID (radio frequency identification) is still
the main technology proposed for IoT as it serves the
connection purpose and has multiple operational benefits
such as simple design structure and minimal cost.
Furthermore, RFID can be integrated with the existing
internet technologies more so IP (Internet Protocol)
addressing which is majorly used to connect and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
uniquely identify devices online [5]. Now, IP has in the
past few years experienced drastic changes especially in
its addressing scheme where the IPv6 has been
developed to handle the number of devices expected in
the future. In all, IPv6 will offer an unlimited number of
addresses based on a bi-directional and symmetrical
machine to machine (M2M) communication structure.
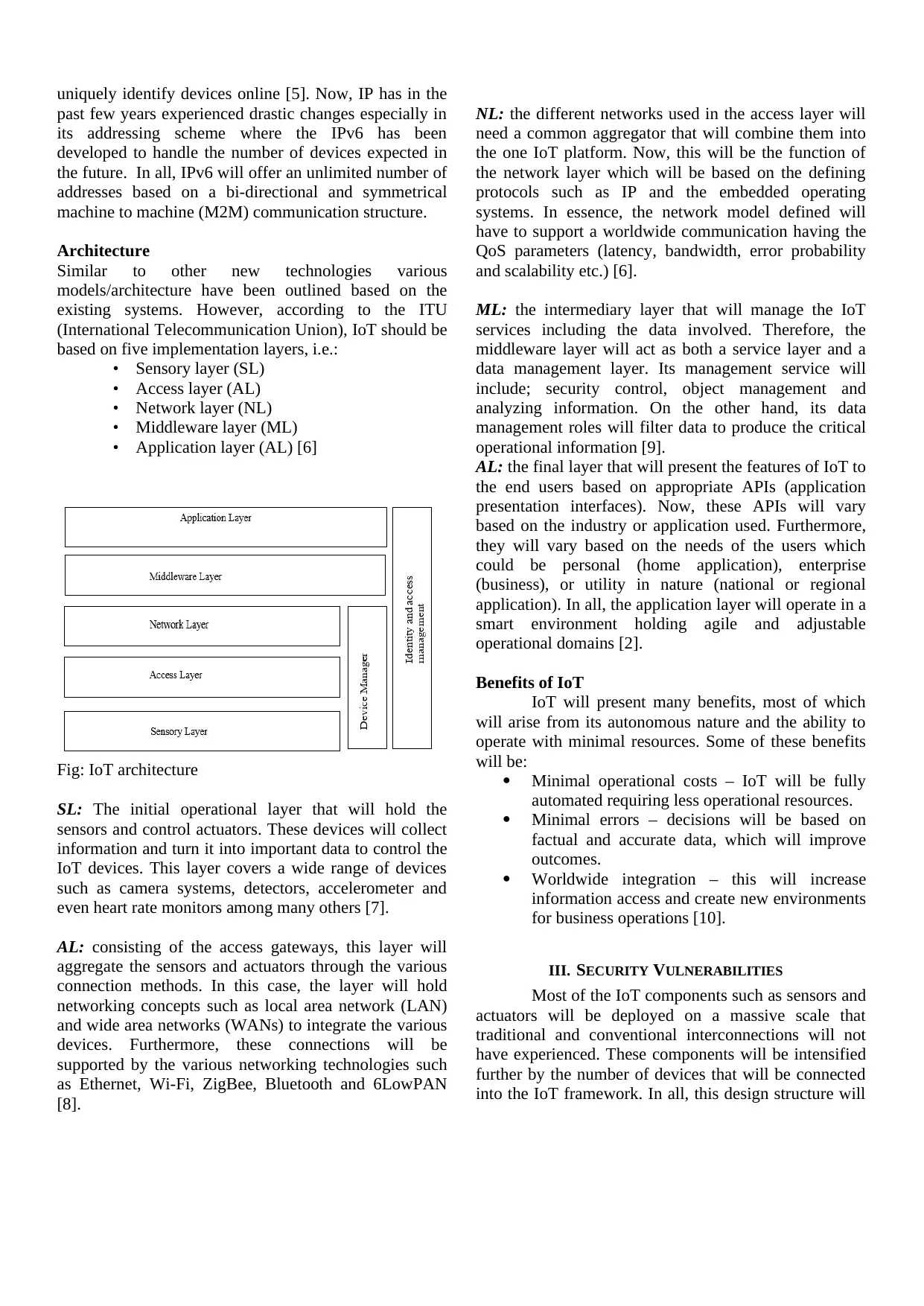
Architecture
Similar to other new technologies various
models/architecture have been outlined based on the
existing systems. However, according to the ITU
(International Telecommunication Union), IoT should be
based on five implementation layers, i.e.:
• Sensory layer (SL)
• Access layer (AL)
• Network layer (NL)
• Middleware layer (ML)
• Application layer (AL) [6]
Fig: IoT architecture
SL: The initial operational layer that will hold the
sensors and control actuators. These devices will collect
information and turn it into important data to control the
IoT devices. This layer covers a wide range of devices
such as camera systems, detectors, accelerometer and
even heart rate monitors among many others [7].
AL: consisting of the access gateways, this layer will
aggregate the sensors and actuators through the various
connection methods. In this case, the layer will hold
networking concepts such as local area network (LAN)
and wide area networks (WANs) to integrate the various
devices. Furthermore, these connections will be
supported by the various networking technologies such
as Ethernet, Wi-Fi, ZigBee, Bluetooth and 6LowPAN
[8].
NL: the different networks used in the access layer will
need a common aggregator that will combine them into
the one IoT platform. Now, this will be the function of
the network layer which will be based on the defining
protocols such as IP and the embedded operating
systems. In essence, the network model defined will
have to support a worldwide communication having the
QoS parameters (latency, bandwidth, error probability
and scalability etc.) [6].
ML: the intermediary layer that will manage the IoT
services including the data involved. Therefore, the
middleware layer will act as both a service layer and a
data management layer. Its management service will
include; security control, object management and
analyzing information. On the other hand, its data
management roles will filter data to produce the critical
operational information [9].
AL: the final layer that will present the features of IoT to
the end users based on appropriate APIs (application
presentation interfaces). Now, these APIs will vary
based on the industry or application used. Furthermore,
they will vary based on the needs of the users which
could be personal (home application), enterprise
(business), or utility in nature (national or regional
application). In all, the application layer will operate in a
smart environment holding agile and adjustable
operational domains [2].
Benefits of IoT
IoT will present many benefits, most of which
will arise from its autonomous nature and the ability to
operate with minimal resources. Some of these benefits
will be:
Minimal operational costs – IoT will be fully
automated requiring less operational resources.
Minimal errors – decisions will be based on
factual and accurate data, which will improve
outcomes.
Worldwide integration – this will increase
information access and create new environments
for business operations [10].
III. SECURITY VULNERABILITIES
Most of the IoT components such as sensors and
actuators will be deployed on a massive scale that
traditional and conventional interconnections will not
have experienced. These components will be intensified
further by the number of devices that will be connected
into the IoT framework. In all, this design structure will
past few years experienced drastic changes especially in
its addressing scheme where the IPv6 has been
developed to handle the number of devices expected in
the future. In all, IPv6 will offer an unlimited number of
addresses based on a bi-directional and symmetrical
machine to machine (M2M) communication structure.
Architecture
Similar to other new technologies various
models/architecture have been outlined based on the
existing systems. However, according to the ITU
(International Telecommunication Union), IoT should be
based on five implementation layers, i.e.:
• Sensory layer (SL)
• Access layer (AL)
• Network layer (NL)
• Middleware layer (ML)
• Application layer (AL) [6]
Fig: IoT architecture
SL: The initial operational layer that will hold the
sensors and control actuators. These devices will collect
information and turn it into important data to control the
IoT devices. This layer covers a wide range of devices
such as camera systems, detectors, accelerometer and
even heart rate monitors among many others [7].
AL: consisting of the access gateways, this layer will
aggregate the sensors and actuators through the various
connection methods. In this case, the layer will hold
networking concepts such as local area network (LAN)
and wide area networks (WANs) to integrate the various
devices. Furthermore, these connections will be
supported by the various networking technologies such
as Ethernet, Wi-Fi, ZigBee, Bluetooth and 6LowPAN
[8].
NL: the different networks used in the access layer will
need a common aggregator that will combine them into
the one IoT platform. Now, this will be the function of
the network layer which will be based on the defining
protocols such as IP and the embedded operating
systems. In essence, the network model defined will
have to support a worldwide communication having the
QoS parameters (latency, bandwidth, error probability
and scalability etc.) [6].
ML: the intermediary layer that will manage the IoT
services including the data involved. Therefore, the
middleware layer will act as both a service layer and a
data management layer. Its management service will
include; security control, object management and
analyzing information. On the other hand, its data
management roles will filter data to produce the critical
operational information [9].
AL: the final layer that will present the features of IoT to
the end users based on appropriate APIs (application
presentation interfaces). Now, these APIs will vary
based on the industry or application used. Furthermore,
they will vary based on the needs of the users which
could be personal (home application), enterprise
(business), or utility in nature (national or regional
application). In all, the application layer will operate in a
smart environment holding agile and adjustable
operational domains [2].
Benefits of IoT
IoT will present many benefits, most of which
will arise from its autonomous nature and the ability to
operate with minimal resources. Some of these benefits
will be:
Minimal operational costs – IoT will be fully
automated requiring less operational resources.
Minimal errors – decisions will be based on
factual and accurate data, which will improve
outcomes.
Worldwide integration – this will increase
information access and create new environments
for business operations [10].
III. SECURITY VULNERABILITIES
Most of the IoT components such as sensors and
actuators will be deployed on a massive scale that
traditional and conventional interconnections will not
have experienced. These components will be intensified
further by the number of devices that will be connected
into the IoT framework. In all, this design structure will

have resounding pressures on the existing networking
systems more so, the security structures that are
designed to contain and isolate networks. In essence, the
existing security protocols will lose their strengths as
IoT will infringe directly on their operation mechanisms
which will make them vulnerable to intrusions/attacks
[11].
Secondly, consider the diversity of devices,
protocols and network models that will exist within the
general framework of IoT. In the existing structure of the
internet, various systems are used which make it
vulnerable to attacks as different security measures are
used. Similarly, IoT will have different components that
will either be identical or non-identical. This
homogeneity and heterogeneity will magnify the existing
security problems of worldwide connections. In essence,
some devices and networks will have the necessary
security measure to protect the users as compared to
others. A good example is a smart watch that may act a
rogue access point having minimal security measures
while connected to a home network having sensitive data
[11].
Finally, consider the manufacturers and
developers of IoT devices and technologies. Most of
these companies will design systems based on the
immediate needs of the users while having minimal
security considerations. In fact, some companies will
design systems without security features so as to boost
support business. Moreover, other companies will design
systems without upgrade features which will affect the
overall IoT security when new intrusion mechanisms are
developed. In addition to this, some devices will outlive
their manufacturers while they are still connected to the
worldwide structure which will create serious security
vulnerabilities as they will have no technical support
[12].
IV. POSSIBLE SOLUTION
Although the solution outlined in this section
covers the deployment of IoT devices i.e. the first
vulnerability, this mitigation procedure can as well
prevent the other security threats outlined. In essence,
the solution to the security issues of massive system
deployment is proper design practices. How is this so?
While worldwide connection and integration are needed,
there should be critical trade-offs between the
technologies used and the security measures
implemented. The design and development of IoT
devices should be done based on specific industry
standards that would see all manufacturers conform to
certain security regulations. Moreover, the same
standards would outline the design practices or
framework of deploying all IoT systems. Now, this
design practices would include security features such as
cryptography where system authentication, authorization
and encryption would be done. Furthermore, the same
practices would encapsulate the requirements of system
upgrades, particularly in the field setting [11].
V. CONCLUSION
IoT defines the next evolution of information technology
where the internet will be extended to support all devices
and objects. Now, through this extension, IoT will
integrate all aspects of life from business to home
activities. Furthermore, through this technology devices
will become autonomous which will improve their
intelligence hence increase their efficiency. However,
the implementation process should also cater for the
security issues outlined as they may derail and interfere
with the objectives of the technology.
VI. REFERENCES
[1] S. Madakam, E. Ramaswamy and S. Tripathi,
"Internet of Things (IoT): A Literature review," Journal
of Computer and Communications, p. Available:
https://file.scirp.org/pdf/JCC_2015052516013923.pdf,
2015.
[2] S. Madakam, "Internet of Things: Smart
Things," International Journal of Future Computer and
Communication, pp. Available:
http://www.ijfcc.org/vol4/395-ICNT2014-2-203.pdf.,
2015.
[3] E. Alsaadi and A. Tubaishat, "Internet of
Things: Features, Challenges, and Vulnerabilities,"
International Journal of Advanced Computer Science
and Information Technology (IJACSIT), p. Available: ,
2015.
[4] F. Mattern and C. Floerkemeier, "Fro m the
Internet of Computers to the Internet of Things,"
Distributed Systems Group, Institute for Pervasive
Computing, ETH Zurich, pp. Available:
http://www.vs.inf.ethz.ch/publ/papers/Internet-of-
things.pdf., 2012.
[5] V. Vatsa and G. Singh, "A Literature Review on
Internet of Things (IoT)," International Journal of
Computer Systems , p. Available:
http://www.academia.edu/19560667/A_Literature_Revie
w_on_Internet_of_Things_IoT_, 2015.
systems more so, the security structures that are
designed to contain and isolate networks. In essence, the
existing security protocols will lose their strengths as
IoT will infringe directly on their operation mechanisms
which will make them vulnerable to intrusions/attacks
[11].
Secondly, consider the diversity of devices,
protocols and network models that will exist within the
general framework of IoT. In the existing structure of the
internet, various systems are used which make it
vulnerable to attacks as different security measures are
used. Similarly, IoT will have different components that
will either be identical or non-identical. This
homogeneity and heterogeneity will magnify the existing
security problems of worldwide connections. In essence,
some devices and networks will have the necessary
security measure to protect the users as compared to
others. A good example is a smart watch that may act a
rogue access point having minimal security measures
while connected to a home network having sensitive data
[11].
Finally, consider the manufacturers and
developers of IoT devices and technologies. Most of
these companies will design systems based on the
immediate needs of the users while having minimal
security considerations. In fact, some companies will
design systems without security features so as to boost
support business. Moreover, other companies will design
systems without upgrade features which will affect the
overall IoT security when new intrusion mechanisms are
developed. In addition to this, some devices will outlive
their manufacturers while they are still connected to the
worldwide structure which will create serious security
vulnerabilities as they will have no technical support
[12].
IV. POSSIBLE SOLUTION
Although the solution outlined in this section
covers the deployment of IoT devices i.e. the first
vulnerability, this mitigation procedure can as well
prevent the other security threats outlined. In essence,
the solution to the security issues of massive system
deployment is proper design practices. How is this so?
While worldwide connection and integration are needed,
there should be critical trade-offs between the
technologies used and the security measures
implemented. The design and development of IoT
devices should be done based on specific industry
standards that would see all manufacturers conform to
certain security regulations. Moreover, the same
standards would outline the design practices or
framework of deploying all IoT systems. Now, this
design practices would include security features such as
cryptography where system authentication, authorization
and encryption would be done. Furthermore, the same
practices would encapsulate the requirements of system
upgrades, particularly in the field setting [11].
V. CONCLUSION
IoT defines the next evolution of information technology
where the internet will be extended to support all devices
and objects. Now, through this extension, IoT will
integrate all aspects of life from business to home
activities. Furthermore, through this technology devices
will become autonomous which will improve their
intelligence hence increase their efficiency. However,
the implementation process should also cater for the
security issues outlined as they may derail and interfere
with the objectives of the technology.
VI. REFERENCES
[1] S. Madakam, E. Ramaswamy and S. Tripathi,
"Internet of Things (IoT): A Literature review," Journal
of Computer and Communications, p. Available:
https://file.scirp.org/pdf/JCC_2015052516013923.pdf,
2015.
[2] S. Madakam, "Internet of Things: Smart
Things," International Journal of Future Computer and
Communication, pp. Available:
http://www.ijfcc.org/vol4/395-ICNT2014-2-203.pdf.,
2015.
[3] E. Alsaadi and A. Tubaishat, "Internet of
Things: Features, Challenges, and Vulnerabilities,"
International Journal of Advanced Computer Science
and Information Technology (IJACSIT), p. Available: ,
2015.
[4] F. Mattern and C. Floerkemeier, "Fro m the
Internet of Computers to the Internet of Things,"
Distributed Systems Group, Institute for Pervasive
Computing, ETH Zurich, pp. Available:
http://www.vs.inf.ethz.ch/publ/papers/Internet-of-
things.pdf., 2012.
[5] V. Vatsa and G. Singh, "A Literature Review on
Internet of Things (IoT)," International Journal of
Computer Systems , p. Available:
http://www.academia.edu/19560667/A_Literature_Revie
w_on_Internet_of_Things_IoT_, 2015.

[6] J. Gubbi, R. Buyya, S. Marusic and M.
Palaniswami, "Internet of Things (IoT): A Vision,
Architectural Elements, and Future Directions," pp.
Available: http://www.cloudbus.org/papers/Internet-of-
Things-Vision-Future2012.pdf., 2012.
[7] K. Rose, S. Eldridge and L. Eldridge, "The
Internet of Things: An Overview," Understanding the
Issues and Challenges of a More Connected World, pp.
Available:
https://www.internetsociety.org/sites/default/files/ISOC-
IoT-Overview-20151014_0.pdf., 2015.
[8] P. FREMANTLE, "A REFERENCE
ARCHITECTURE FOR THE INTERNET OF
THINGS," WSO2, pp. Available:
http://wso2.com/wso2_resources/wso2_whitepaper_a-
reference-architecture-for-the-internet-of-things.pdf.,
2015.
[9] A. Castellani, N. Bui, P. Casari, M. Rossi, Z.
Shelby and M. Zorzi, "Architecture and Protocols for the
Internet of Things: A Case Study," p. Available:
https://webofthings.org/wot/2010/pdfs/144.pdf., 2010.
[10] C. Reports, "Reaping the Benefits of the Internet
of Things," Cognizant Reports, pp. Available:
https://www.cognizant.com/InsightsWhitepapers/Reapin
g-the-Benefits-of-the-Internet-of-Things.pdf., 2014.
[11] I. society, "The internet of things: overview,"
Understanding the issues and challenges of a more
connected world, pp. Available:
https://www.internetsociety.org/doc/iot-overview, 2015.
[12] Ericsson, "IoT SECURITY," ericsson White
paper, pp. Available:
https://www.ericsson.com/assets/local/publications/whit
e-papers/wp-iot-security-february-2017.pdf., 2017.
Palaniswami, "Internet of Things (IoT): A Vision,
Architectural Elements, and Future Directions," pp.
Available: http://www.cloudbus.org/papers/Internet-of-
Things-Vision-Future2012.pdf., 2012.
[7] K. Rose, S. Eldridge and L. Eldridge, "The
Internet of Things: An Overview," Understanding the
Issues and Challenges of a More Connected World, pp.
Available:
https://www.internetsociety.org/sites/default/files/ISOC-
IoT-Overview-20151014_0.pdf., 2015.
[8] P. FREMANTLE, "A REFERENCE
ARCHITECTURE FOR THE INTERNET OF
THINGS," WSO2, pp. Available:
http://wso2.com/wso2_resources/wso2_whitepaper_a-
reference-architecture-for-the-internet-of-things.pdf.,
2015.
[9] A. Castellani, N. Bui, P. Casari, M. Rossi, Z.
Shelby and M. Zorzi, "Architecture and Protocols for the
Internet of Things: A Case Study," p. Available:
https://webofthings.org/wot/2010/pdfs/144.pdf., 2010.
[10] C. Reports, "Reaping the Benefits of the Internet
of Things," Cognizant Reports, pp. Available:
https://www.cognizant.com/InsightsWhitepapers/Reapin
g-the-Benefits-of-the-Internet-of-Things.pdf., 2014.
[11] I. society, "The internet of things: overview,"
Understanding the issues and challenges of a more
connected world, pp. Available:
https://www.internetsociety.org/doc/iot-overview, 2015.
[12] Ericsson, "IoT SECURITY," ericsson White
paper, pp. Available:
https://www.ericsson.com/assets/local/publications/whit
e-papers/wp-iot-security-february-2017.pdf., 2017.
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





