Security Challenges in Emerging Networks Assignment
Added on 2020-03-23
4 Pages2314 Words59 Views
Security Challenges in Emerging NetworksInternet of Things[Authors Name/s per 1st Affiliation (Author)][Authors Name/s per 2nd Affiliation (Author)]Abstract— Internet of Things defines a vision ofexpanding the existing connections of the internet toinclude a fully autonomous system. This reporthighlights this technology and the security challengesit presents.Keywords— IoT, Security, RFIDI.INTRODUCTIONInternet of things (IoT) represents a dynamic shift inthe operational structure of the internet wheretechnological objects and gadget are holisticallyembroiled into a worldwide network. In this network,these devices identify themselves autonomously andshare information based on their needs and those of theirusers. Therefore, as a future technology IoT represent thenext evolution of the internet where technology will takeadvantage of the advancement in digital systems more so,virtualization, computing power and systemminiaturization [1]. Furthermore, it is through IoTtechnology that smart systems will be developed havingthe ability to function without human intervention. Inessence, the implementation of IoT will signal the start ofsmart cities, an outcome already seen today. Now, thisreport analyses IoT as a technology including the securitychallenges and threats that will be experienced as a resultof its implementation.II.LITERATUREREVIEWIn the current world, the foundational conceptsof IoT are already being seen, things like smarttelevision systems, smart watches and smart phones arepropelling the digital era into a smart society. Thesegadgets rarely need human intervention to operate, anoutcome that is used to define a smart object or device.Moreover, these devices are designed based on the needsof the users which make them dynamic and versatile ascompared to conventional systems that were developedbased on the existing conditions [2]. Again, this shift inthe design of technological system outlines theparameters needed to implement IoT where intelligenceand self-awareness are critical components. However, inall the research and discussion given on the topic, nosingle accepted definition is given on the term (IoT)other than the ability to add intelligence into the variousworking environments [3].IoT TechnologiesTo increase the worldwide connection ofdevices, extensive networks are needed which outlinesthe importance of the internet in the future of IoT. Infact, its integral role in connectivity outlines why smartsystems and even IoT are named as its next evolution.However, at the same time, the digital environment hasto consider the demands made by the end usersparticularly based on their convenience requirements.This demand necessitates the need for agile and dynamicsystems, factors that have led to the growth of wirelesstechnology, a centre mark for IoT [4]. In essence,wireless technologies will act as the foundation of IoTconnecting different data centres, devices and thecomplementary features (sensors and actuators).Now, the complementary features (sensors andactuators) will enable the devices to connect with eachother based on various identification technologies. At themoment, RFID (radio frequency identification) is stillthe main technology proposed for IoT as it serves theconnection purpose and has multiple operational benefitssuch as simple design structure and minimal cost.Furthermore, RFID can be integrated with the existinginternet technologies more so IP (Internet Protocol)addressing which is majorly used to connect and

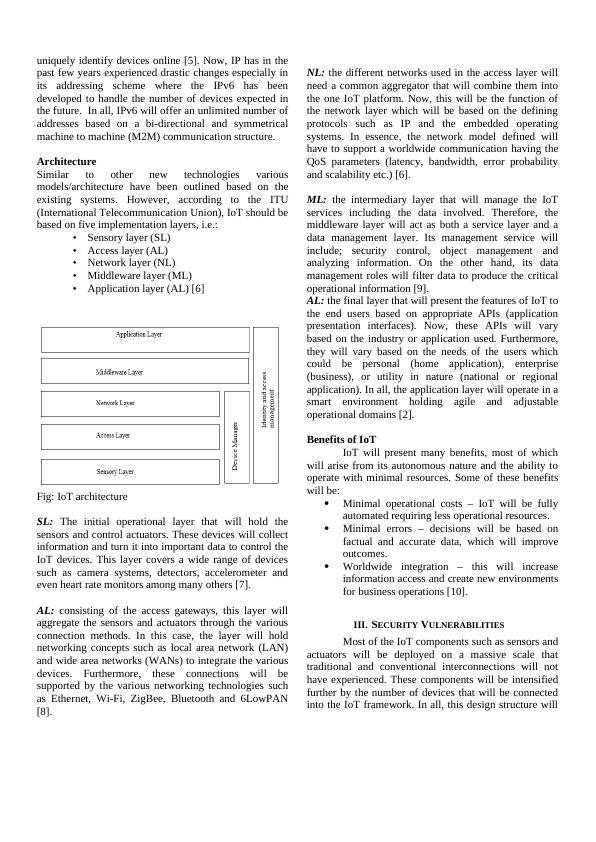
uniquely identify devices online [5]. Now, IP has in thepast few years experienced drastic changes especially inits addressing scheme where the IPv6 has beendeveloped to handle the number of devices expected inthe future. In all, IPv6 will offer an unlimited number ofaddresses based on a bi-directional and symmetricalmachine to machine (M2M) communication structure. ArchitectureSimilar to other new technologies variousmodels/architecture have been outlined based on theexisting systems. However, according to the ITU(International Telecommunication Union), IoT should bebased on five implementation layers, i.e.:• Sensory layer (SL)• Access layer (AL)• Network layer (NL)• Middleware layer (ML)• Application layer (AL) [6]Fig: IoT architectureSL: The initial operational layer that will hold thesensors and control actuators. These devices will collectinformation and turn it into important data to control theIoT devices. This layer covers a wide range of devicessuch as camera systems, detectors, accelerometer andeven heart rate monitors among many others [7].AL: consisting of the access gateways, this layer willaggregate the sensors and actuators through the variousconnection methods. In this case, the layer will holdnetworking concepts such as local area network (LAN)and wide area networks (WANs) to integrate the variousdevices. Furthermore, these connections will besupported by the various networking technologies suchas Ethernet, Wi-Fi, ZigBee, Bluetooth and 6LowPAN[8].NL: the different networks used in the access layer willneed a common aggregator that will combine them intothe one IoT platform. Now, this will be the function ofthe network layer which will be based on the definingprotocols such as IP and the embedded operatingsystems. In essence, the network model defined willhave to support a worldwide communication having theQoS parameters (latency, bandwidth, error probabilityand scalability etc.) [6].ML: the intermediary layer that will manage the IoTservices including the data involved. Therefore, themiddleware layer will act as both a service layer and adata management layer. Its management service willinclude; security control, object management andanalyzing information. On the other hand, its datamanagement roles will filter data to produce the criticaloperational information [9].AL: the final layer that will present the features of IoT tothe end users based on appropriate APIs (applicationpresentation interfaces). Now, these APIs will varybased on the industry or application used. Furthermore,they will vary based on the needs of the users whichcould be personal (home application), enterprise(business), or utility in nature (national or regionalapplication). In all, the application layer will operate in asmart environment holding agile and adjustableoperational domains [2].Benefits of IoTIoT will present many benefits, most of whichwill arise from its autonomous nature and the ability tooperate with minimal resources. Some of these benefitswill be:Minimal operational costs – IoT will be fullyautomated requiring less operational resources.Minimal errors – decisions will be based onfactual and accurate data, which will improveoutcomes.Worldwide integration – this will increaseinformation access and create new environmentsfor business operations [10].III.SECURITY VULNERABILITIESMost of the IoT components such as sensors andactuators will be deployed on a massive scale thattraditional and conventional interconnections will nothave experienced. These components will be intensifiedfurther by the number of devices that will be connectedinto the IoT framework. In all, this design structure will
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Security Issues and Solutions Doclg...
|11
|2796
|100
Security Challenges in Emerging Networks | Assignmentlg...
|4
|2579
|48
IFN643 Ransomware Removal Reportlg...
|11
|1954
|42
Overview of Network Security in Internet of Thingslg...
|4
|2832
|54
Internet of Things Technologylg...
|11
|2627
|81
IOT - Security Issues and Solutions - Reportlg...
|9
|2197
|75