Cloud Computing Security: Data Protection, Risks, and Mitigation
VerifiedAdded on 2023/06/12
|6
|4738
|66
Report
AI Summary
This report delves into the critical aspects of cloud computing security, focusing on data protection strategies, potential risks, and effective mitigation techniques. It highlights the increasing importance of cloud computing and the corresponding need for robust security measures to safeguard sensitive user data. The report examines challenges such as lack of appropriate governance, data interception, insecure data deletion, and retrieval issues, along with pricing concerns. It also explores the Goal-Question-Metric (GQM) methodology and Security Metrics Hierarchy (SMH) model for enhancing cloud security management. Furthermore, the paper reviews various methods for securing data in the cloud, including encryption techniques and security matrix approaches, emphasizing the importance of strong password practices and careful consideration of data sensitivity when utilizing cloud services. Desklib offers a wealth of similar resources to aid students in their studies.

Security of Cloud Computing
First A. Author, Second B. Author, and Third C. Author
Abstract— the primary aim of the paper is to take into
consideration the security which can be applied to the
concept of cloud computing. The security in this aspect
mainly refers to the data, which is stored in the idea of the
cloud. The paper would be directly focusing on the concept of
the security and the threat and the provide recommendation
to mitigate the problem. There are different concepts, which
can be applied to the idea of the clouding computing for the
aspect of giving provision for the security of the data. The
analysis of the element of the protection of the data can be
considered one of the most critical factors, which are related
to the concept of the data of the user.
Index Terms— cloud computing, data security, risks,
privacy and data protection.
I. TINTRODUCTION
The concept of cloud computing can be considered one of
the technologies which are playing a vital role in recent
times. A primary concern in the sector of the cloud
computing is the security which can be applied to the
concept. It is a critical factor for the cloud service
providers to ensure the aspects of privacy and protection.
To achieve this different concept policies are being
incorporated. Sometimes the data of the user is too
sensitive to be saved in the idea of the cloud as the
security, which would be applied to the data, is not entirely
up to the mark. These type of data can be a significant loss
for the organisation if it is exposed to any third party or
intruders. When comparing the concept of the cloud
computing to another aspect such as the traditional system
it can be stated, it has many advantages over the system,
but there is no justification of the security aspects, which
are involved into the concept. The concept of cloud
computing can deliver different types of infrastructure
solutions with the element of dynamic resource allocation
and system approach towards the retrieval of the data
which is stored in the concept of the cloud computing. The
application of the idea of cloud computing is not just
restricted to one area it can be applied to any area which
has data involved in the concept. Most of the data in the
are stored in the idea of the cloud are highly secured and
which can be retrieved when the user wants to do so. In
most of the cases taking into consideration technology,
there can be some flaws involved in the concept.
II. Research methods
In the 1970s, the GQM (Goal – Question –Metric) was
developed with a motive to move to move testing for the
defects of the software from the individual and qualitative
state, which is currently included in an empirical model.
This model helps to identify the errors, which would be
measured according to the defined goals, and objectives
when they can be linked with the result [1].
The GQM methodology states a model of
measurement on three level which is i) conceptual model
ii) operational model and iii) quantitative model. In a
model, the pyramid of the security is directly generated
from the GQM process relating to the definition during
which the security features are mapped to the equivalent
security matrices. The relation between the different
concepts shows the relationship between the security
metrics hierarchy (SHM) and the GQM methodology,
which play a vital in the sector of the security.
For each of the goal statement, which is
identified in the level a group matrices, will be adequately
defined. The operational level, that is, identified which
object or activities must be collected.
III. Result and analysis
Undoubtedly it can be stated that it is not easy to ensure
and secure the safety of the linked computers due to the
factor that a series of equipment and clients which are
involved; this concept can be termed as multi-tenancy. The
services, which are related to the idea of cloud computing
can be facing different types of problem which are
connected to the security issue and the safety of the data
which is stored in the context. Therefore, it can be stated
that it is very much essential to get the hold of the security
aspects and find out ways in which the overall elements
can be reduced. Some of the significant challenges, which
are founded out from the research, are stated below:
Lack of appropriate governance: During the
functionality of the cloud computing the cloud,
providers have the total access to the system. This
concept can have some security aspects involved in
the data due to the factor that the loss of the control
can put the data at a danger stage of being accessed by
any third person
Data interception: Taking into consideration the
traditional system, the data of the cloud computing is
distributed and segmented in transit. This aspect can
1
First A. Author, Second B. Author, and Third C. Author
Abstract— the primary aim of the paper is to take into
consideration the security which can be applied to the
concept of cloud computing. The security in this aspect
mainly refers to the data, which is stored in the idea of the
cloud. The paper would be directly focusing on the concept of
the security and the threat and the provide recommendation
to mitigate the problem. There are different concepts, which
can be applied to the idea of the clouding computing for the
aspect of giving provision for the security of the data. The
analysis of the element of the protection of the data can be
considered one of the most critical factors, which are related
to the concept of the data of the user.
Index Terms— cloud computing, data security, risks,
privacy and data protection.
I. TINTRODUCTION
The concept of cloud computing can be considered one of
the technologies which are playing a vital role in recent
times. A primary concern in the sector of the cloud
computing is the security which can be applied to the
concept. It is a critical factor for the cloud service
providers to ensure the aspects of privacy and protection.
To achieve this different concept policies are being
incorporated. Sometimes the data of the user is too
sensitive to be saved in the idea of the cloud as the
security, which would be applied to the data, is not entirely
up to the mark. These type of data can be a significant loss
for the organisation if it is exposed to any third party or
intruders. When comparing the concept of the cloud
computing to another aspect such as the traditional system
it can be stated, it has many advantages over the system,
but there is no justification of the security aspects, which
are involved into the concept. The concept of cloud
computing can deliver different types of infrastructure
solutions with the element of dynamic resource allocation
and system approach towards the retrieval of the data
which is stored in the concept of the cloud computing. The
application of the idea of cloud computing is not just
restricted to one area it can be applied to any area which
has data involved in the concept. Most of the data in the
are stored in the idea of the cloud are highly secured and
which can be retrieved when the user wants to do so. In
most of the cases taking into consideration technology,
there can be some flaws involved in the concept.
II. Research methods
In the 1970s, the GQM (Goal – Question –Metric) was
developed with a motive to move to move testing for the
defects of the software from the individual and qualitative
state, which is currently included in an empirical model.
This model helps to identify the errors, which would be
measured according to the defined goals, and objectives
when they can be linked with the result [1].
The GQM methodology states a model of
measurement on three level which is i) conceptual model
ii) operational model and iii) quantitative model. In a
model, the pyramid of the security is directly generated
from the GQM process relating to the definition during
which the security features are mapped to the equivalent
security matrices. The relation between the different
concepts shows the relationship between the security
metrics hierarchy (SHM) and the GQM methodology,
which play a vital in the sector of the security.
For each of the goal statement, which is
identified in the level a group matrices, will be adequately
defined. The operational level, that is, identified which
object or activities must be collected.
III. Result and analysis
Undoubtedly it can be stated that it is not easy to ensure
and secure the safety of the linked computers due to the
factor that a series of equipment and clients which are
involved; this concept can be termed as multi-tenancy. The
services, which are related to the idea of cloud computing
can be facing different types of problem which are
connected to the security issue and the safety of the data
which is stored in the context. Therefore, it can be stated
that it is very much essential to get the hold of the security
aspects and find out ways in which the overall elements
can be reduced. Some of the significant challenges, which
are founded out from the research, are stated below:
Lack of appropriate governance: During the
functionality of the cloud computing the cloud,
providers have the total access to the system. This
concept can have some security aspects involved in
the data due to the factor that the loss of the control
can put the data at a danger stage of being accessed by
any third person
Data interception: Taking into consideration the
traditional system, the data of the cloud computing is
distributed and segmented in transit. This aspect can
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
possess more threats due to the concept of the fragility
and vulnerability of the computing technology and in
notably spoofing and sniffing, third-party attacks and
he replies attacks.
Insecure and incomplete data deletion: in the situation
where the client wants the data either entirely or
partially, this can raise the question whether it would
be possible to delete the desired part of the data
segments with accuracy. [4].
Retrieval of the data: In most of the cases, it is seen
that the users store their crucial data into the concept
of the cloud. On the other hand, when the data of the
user need it is not available. This can be due to many
factors, for example, link failure between the domain
of the cloud and the user. Another aspect, which can
directly lead to the problem, is the aspect of the
server. The data can be stored in one of the servers
which are located at another location which would not
be easily accessed. This can directly lead to different
types of problem for the user.
Pricing: The concept of pricing can also be considered
to be one of the areas where the idea of cloud
computing lacks. It can be stated here that in most of
the situation the cloud providers tend to increase the
price of the service, and on the other hand, it can be
noted that the customers do not have any other option
but to involve in the given amount due to the service
they have to achieve. There are different factors which
play a role in this context due to which the pricing of
the technology varies all the time. On the other hand,
it can be stated that the process is sometimes very
much useful if the pricing is based on the concept of
the usage.
FIGURE 1
MANAGEMENT OF CLOUD COMPUTING
IV. Literature Review
There are different ways by which the data in the
concept of cloud can be secured. The privacy aspect of
the data can be achieved by implementing the following
few factors. The sensitive data of the user should not be
stored in the concept of the cloud. This is due to the
element that the security of the data in the idea of the
cloud so not very much secured. There is no
justification which is in control of the data and how the
different security aspects are applied to the data. The
password should be one of the areas of concern. It
should be taken into consideration that the password,
which is implemented, are severe enough to be cracked
by an unauthorised person.
GCM level SMH Level
Operational level Metric
Conceptual level Group metric
Quantitative level Sub - metric
GQM Model: The fundamental idea which can be
applied to the concept of GQM is that the identification
of the goals have to be made which has to be achieved
and working according to the set goal. The main factor
is to achieve the standard of goal by any means.
SMH Model: SMH can be considered as a model
which is related to the mechanism of the actions which
are directly goal oriented.
TABLE 1
RELATION BETWEEN GQM METHODOLOGY
AND SMG
In the concept of cloud, computing one of the most
significant factors, which play a role, is the encryption
technique of the data. The work, which can be followed
in the concept, is that if someone has to store a file in
the idea of the cloud, the user can add password security
into the aspect, which would be directly securing the
data, and no one would be able to access the file. The
most trending technique, which can be implemented in
this case, is performing a zip operation into the record
and protecting it with a password. This would be
beneficial in the way of not allowing unauthorised
access to the data. Encryption can also be beneficial in
the way of transferring data from one cloud platform to
another. It can be stated here that the data are
transferred in a highly secured manner by which no
third party can have direct access to the data.
The methodology which is proposed in the aspect
of the cloud security can be derived from the concept of
the security management which mainly include i)
security index (IndSec) ii) security matrix hierarchy iii)
allocation index (IndAlloc) iv) management of the cloud
2
and vulnerability of the computing technology and in
notably spoofing and sniffing, third-party attacks and
he replies attacks.
Insecure and incomplete data deletion: in the situation
where the client wants the data either entirely or
partially, this can raise the question whether it would
be possible to delete the desired part of the data
segments with accuracy. [4].
Retrieval of the data: In most of the cases, it is seen
that the users store their crucial data into the concept
of the cloud. On the other hand, when the data of the
user need it is not available. This can be due to many
factors, for example, link failure between the domain
of the cloud and the user. Another aspect, which can
directly lead to the problem, is the aspect of the
server. The data can be stored in one of the servers
which are located at another location which would not
be easily accessed. This can directly lead to different
types of problem for the user.
Pricing: The concept of pricing can also be considered
to be one of the areas where the idea of cloud
computing lacks. It can be stated here that in most of
the situation the cloud providers tend to increase the
price of the service, and on the other hand, it can be
noted that the customers do not have any other option
but to involve in the given amount due to the service
they have to achieve. There are different factors which
play a role in this context due to which the pricing of
the technology varies all the time. On the other hand,
it can be stated that the process is sometimes very
much useful if the pricing is based on the concept of
the usage.
FIGURE 1
MANAGEMENT OF CLOUD COMPUTING
IV. Literature Review
There are different ways by which the data in the
concept of cloud can be secured. The privacy aspect of
the data can be achieved by implementing the following
few factors. The sensitive data of the user should not be
stored in the concept of the cloud. This is due to the
element that the security of the data in the idea of the
cloud so not very much secured. There is no
justification which is in control of the data and how the
different security aspects are applied to the data. The
password should be one of the areas of concern. It
should be taken into consideration that the password,
which is implemented, are severe enough to be cracked
by an unauthorised person.
GCM level SMH Level
Operational level Metric
Conceptual level Group metric
Quantitative level Sub - metric
GQM Model: The fundamental idea which can be
applied to the concept of GQM is that the identification
of the goals have to be made which has to be achieved
and working according to the set goal. The main factor
is to achieve the standard of goal by any means.
SMH Model: SMH can be considered as a model
which is related to the mechanism of the actions which
are directly goal oriented.
TABLE 1
RELATION BETWEEN GQM METHODOLOGY
AND SMG
In the concept of cloud, computing one of the most
significant factors, which play a role, is the encryption
technique of the data. The work, which can be followed
in the concept, is that if someone has to store a file in
the idea of the cloud, the user can add password security
into the aspect, which would be directly securing the
data, and no one would be able to access the file. The
most trending technique, which can be implemented in
this case, is performing a zip operation into the record
and protecting it with a password. This would be
beneficial in the way of not allowing unauthorised
access to the data. Encryption can also be beneficial in
the way of transferring data from one cloud platform to
another. It can be stated here that the data are
transferred in a highly secured manner by which no
third party can have direct access to the data.
The methodology which is proposed in the aspect
of the cloud security can be derived from the concept of
the security management which mainly include i)
security index (IndSec) ii) security matrix hierarchy iii)
allocation index (IndAlloc) iv) management of the cloud
2
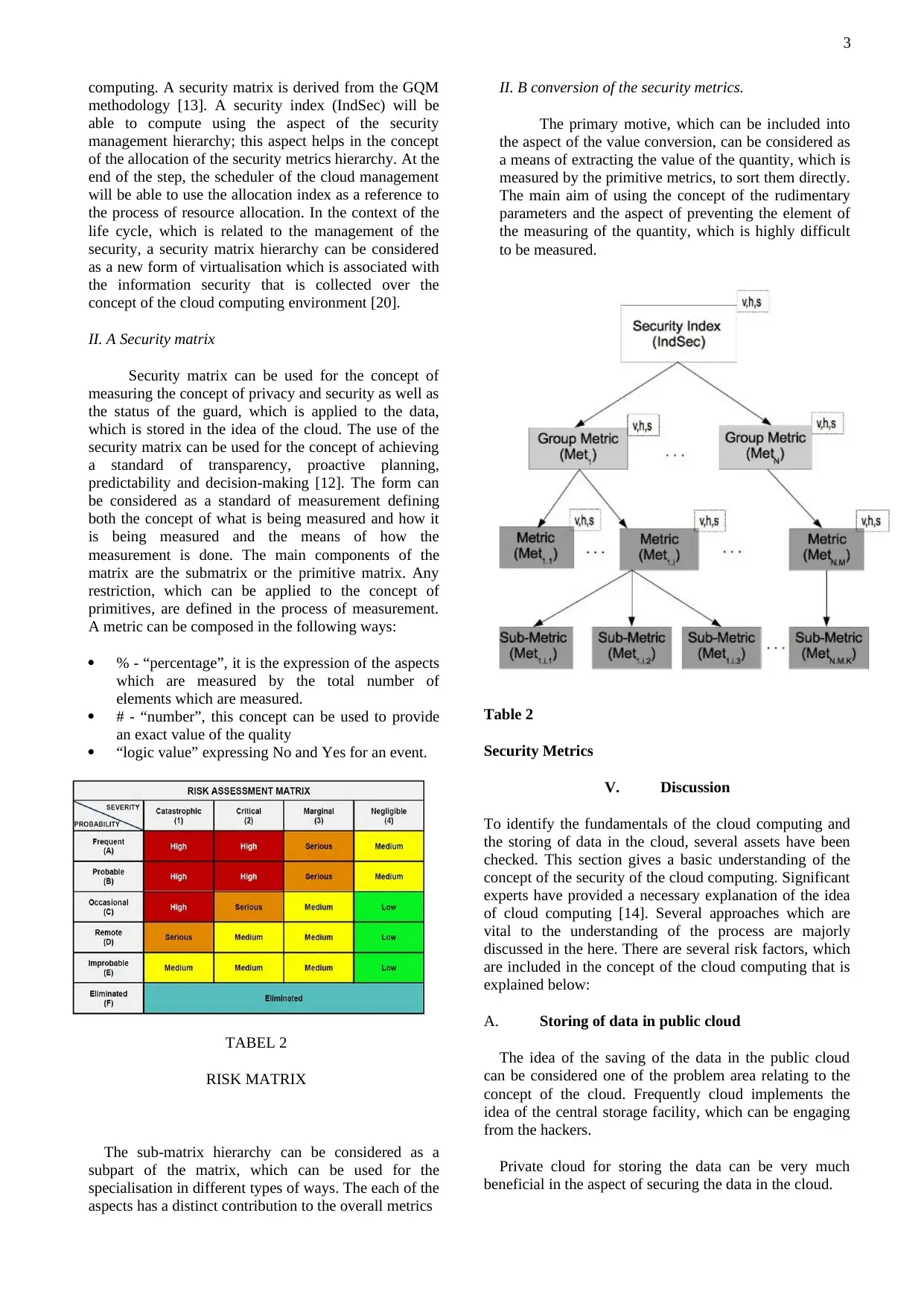
computing. A security matrix is derived from the GQM
methodology [13]. A security index (IndSec) will be
able to compute using the aspect of the security
management hierarchy; this aspect helps in the concept
of the allocation of the security metrics hierarchy. At the
end of the step, the scheduler of the cloud management
will be able to use the allocation index as a reference to
the process of resource allocation. In the context of the
life cycle, which is related to the management of the
security, a security matrix hierarchy can be considered
as a new form of virtualisation which is associated with
the information security that is collected over the
concept of the cloud computing environment [20].
II. A Security matrix
Security matrix can be used for the concept of
measuring the concept of privacy and security as well as
the status of the guard, which is applied to the data,
which is stored in the idea of the cloud. The use of the
security matrix can be used for the concept of achieving
a standard of transparency, proactive planning,
predictability and decision-making [12]. The form can
be considered as a standard of measurement defining
both the concept of what is being measured and how it
is being measured and the means of how the
measurement is done. The main components of the
matrix are the submatrix or the primitive matrix. Any
restriction, which can be applied to the concept of
primitives, are defined in the process of measurement.
A metric can be composed in the following ways:
% - “percentage”, it is the expression of the aspects
which are measured by the total number of
elements which are measured.
# - “number”, this concept can be used to provide
an exact value of the quality
“logic value” expressing No and Yes for an event.
TABEL 2
RISK MATRIX
The sub-matrix hierarchy can be considered as a
subpart of the matrix, which can be used for the
specialisation in different types of ways. The each of the
aspects has a distinct contribution to the overall metrics
II. B conversion of the security metrics.
The primary motive, which can be included into
the aspect of the value conversion, can be considered as
a means of extracting the value of the quantity, which is
measured by the primitive metrics, to sort them directly.
The main aim of using the concept of the rudimentary
parameters and the aspect of preventing the element of
the measuring of the quantity, which is highly difficult
to be measured.
Table 2
Security Metrics
V. Discussion
To identify the fundamentals of the cloud computing and
the storing of data in the cloud, several assets have been
checked. This section gives a basic understanding of the
concept of the security of the cloud computing. Significant
experts have provided a necessary explanation of the idea
of cloud computing [14]. Several approaches which are
vital to the understanding of the process are majorly
discussed in the here. There are several risk factors, which
are included in the concept of the cloud computing that is
explained below:
A. Storing of data in public cloud
The idea of the saving of the data in the public cloud
can be considered one of the problem area relating to the
concept of the cloud. Frequently cloud implements the
idea of the central storage facility, which can be engaging
from the hackers.
Private cloud for storing the data can be very much
beneficial in the aspect of securing the data in the cloud.
3
methodology [13]. A security index (IndSec) will be
able to compute using the aspect of the security
management hierarchy; this aspect helps in the concept
of the allocation of the security metrics hierarchy. At the
end of the step, the scheduler of the cloud management
will be able to use the allocation index as a reference to
the process of resource allocation. In the context of the
life cycle, which is related to the management of the
security, a security matrix hierarchy can be considered
as a new form of virtualisation which is associated with
the information security that is collected over the
concept of the cloud computing environment [20].
II. A Security matrix
Security matrix can be used for the concept of
measuring the concept of privacy and security as well as
the status of the guard, which is applied to the data,
which is stored in the idea of the cloud. The use of the
security matrix can be used for the concept of achieving
a standard of transparency, proactive planning,
predictability and decision-making [12]. The form can
be considered as a standard of measurement defining
both the concept of what is being measured and how it
is being measured and the means of how the
measurement is done. The main components of the
matrix are the submatrix or the primitive matrix. Any
restriction, which can be applied to the concept of
primitives, are defined in the process of measurement.
A metric can be composed in the following ways:
% - “percentage”, it is the expression of the aspects
which are measured by the total number of
elements which are measured.
# - “number”, this concept can be used to provide
an exact value of the quality
“logic value” expressing No and Yes for an event.
TABEL 2
RISK MATRIX
The sub-matrix hierarchy can be considered as a
subpart of the matrix, which can be used for the
specialisation in different types of ways. The each of the
aspects has a distinct contribution to the overall metrics
II. B conversion of the security metrics.
The primary motive, which can be included into
the aspect of the value conversion, can be considered as
a means of extracting the value of the quantity, which is
measured by the primitive metrics, to sort them directly.
The main aim of using the concept of the rudimentary
parameters and the aspect of preventing the element of
the measuring of the quantity, which is highly difficult
to be measured.
Table 2
Security Metrics
V. Discussion
To identify the fundamentals of the cloud computing and
the storing of data in the cloud, several assets have been
checked. This section gives a basic understanding of the
concept of the security of the cloud computing. Significant
experts have provided a necessary explanation of the idea
of cloud computing [14]. Several approaches which are
vital to the understanding of the process are majorly
discussed in the here. There are several risk factors, which
are included in the concept of the cloud computing that is
explained below:
A. Storing of data in public cloud
The idea of the saving of the data in the public cloud
can be considered one of the problem area relating to the
concept of the cloud. Frequently cloud implements the
idea of the central storage facility, which can be engaging
from the hackers.
Private cloud for storing the data can be very much
beneficial in the aspect of securing the data in the cloud.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

B. Virtualization
The concept of virtualisation can be considered as a
technique in which the operating system image is taken
into consideration into another operating system to make
direct use of the operating system and its benefits. The
concept helps in running directly in the operating system,
which can be used for the proper implementation of the
operating system.
The risk factor, which is associated with the
virtualisation concept, is the allocation and the idea of de-
allocation of the resources [2]. If the virtual machine
operation data is written to the memory and it is not clear
before the reallocation of the mind next to the virtual
machine then there is a potential loss of data exposure to
the next virtual machine, which can be very much
uninvited.
A solution to the problem can be done if proper
planning for the virtualisation of the data is done.
Resources should be very much carefully implemented
and used, and the information appropriately authenticated
before the reallocation of the funds is done.
C. Multitenancy
The connect of multitenancy, or the shared access can
be considered one of the most risk-oriented factors in the
concept of the powerful computing. This is due to the
element that more than one user is accessing the same
shared computing resources like the CPU, memory and
storage [1]. In such type of situation, it can be stated that
there is always a risk, which is associated with the private
data if accidentally being exposed or leaked to any third
person. In this type of scenario, it can be seen that the risk
factor always exists in the working. The concept of multi
can exploit exceptional risk due to the consideration of one
fault in the system can help another person or hacker to
indulge in the idea.
This type of issue can be taken care of user
authentication of the user relating to direct access to the
data. Several authentication processes are available which
can be used for the proper functioning of the approach [1].
FIGURE 2
CONCEPT OF MULTITENANCY
There are a consistent increase and growth in the
application of the cloud usage over the past few years.
This is due to the factor that the organisational leader of
the IT has realised the importance of the concept. The
cloud computing has different types of benefits applied to
the overall working of any organisation [17]. On the other
hand, it can be stated that ones the implementation of the
concept is done for the mangers it becomes a headache.
Just as the idea of the in-house provisioning system, the
account admin should be able to efficiently change
provision and disable the account as well as manage the
overall password and directly ensure the global network is
secured. When any of the organisation implement the
concept of the cloud, computing it becomes a big problem,
which is related to the aspect of who would be in control
of the working and the security of the data. The user can
sometimes have the power of the data, which they should
not be allowed to do so. On the other hand, the security of
the data can also be enhanced using removing the account
of the user ones they leave the organisation.
One of the techniques, which is in recent use, is
the concept of the identity and access management [19].
The idea of the character and access management can be
used for many purposes. The main advantage of this
approach is for the managers; the manager can easily plot
down who would be having access to the data and who
would not be allowed to access the features. Many of the
solution in this aspect helps me the concept of the
management of the workflow. With the idea of the
workflow management and the self-service, the manager
and the employee individually can request the access and
approve the request without the involvement of any IT
interventions. The approval part can be considered the part
of the structured workflow. The concept or the approach
can be very much beneficial not only in the aspect of the
efficiency but also increases the security aspect of the idea
of the cloud computing [21].
To handle the aspect of the different password
and naming conventions, an automated solution would be
very much helpful. The concept of the IAM solution can
enforce a means of naming conventions across the
different platforms. This allows the uniqueness aspect
when more than one user has the same name attached to
the username. Additionally, it can be stated that the single
sign-on the solution can be helpful in the concept of
mitigating the password complexity. This is achieved
using a set of credential, which is unique. This concept can
be used for the idea of logging into the system, and
automatic authentication would be provided. In the
background of such aspect, it can be stated that a SSO
application can be used for the purpose of routinely
resetting the password when the session expires. This is
directly prompted to the user [28].
4
The concept of virtualisation can be considered as a
technique in which the operating system image is taken
into consideration into another operating system to make
direct use of the operating system and its benefits. The
concept helps in running directly in the operating system,
which can be used for the proper implementation of the
operating system.
The risk factor, which is associated with the
virtualisation concept, is the allocation and the idea of de-
allocation of the resources [2]. If the virtual machine
operation data is written to the memory and it is not clear
before the reallocation of the mind next to the virtual
machine then there is a potential loss of data exposure to
the next virtual machine, which can be very much
uninvited.
A solution to the problem can be done if proper
planning for the virtualisation of the data is done.
Resources should be very much carefully implemented
and used, and the information appropriately authenticated
before the reallocation of the funds is done.
C. Multitenancy
The connect of multitenancy, or the shared access can
be considered one of the most risk-oriented factors in the
concept of the powerful computing. This is due to the
element that more than one user is accessing the same
shared computing resources like the CPU, memory and
storage [1]. In such type of situation, it can be stated that
there is always a risk, which is associated with the private
data if accidentally being exposed or leaked to any third
person. In this type of scenario, it can be seen that the risk
factor always exists in the working. The concept of multi
can exploit exceptional risk due to the consideration of one
fault in the system can help another person or hacker to
indulge in the idea.
This type of issue can be taken care of user
authentication of the user relating to direct access to the
data. Several authentication processes are available which
can be used for the proper functioning of the approach [1].
FIGURE 2
CONCEPT OF MULTITENANCY
There are a consistent increase and growth in the
application of the cloud usage over the past few years.
This is due to the factor that the organisational leader of
the IT has realised the importance of the concept. The
cloud computing has different types of benefits applied to
the overall working of any organisation [17]. On the other
hand, it can be stated that ones the implementation of the
concept is done for the mangers it becomes a headache.
Just as the idea of the in-house provisioning system, the
account admin should be able to efficiently change
provision and disable the account as well as manage the
overall password and directly ensure the global network is
secured. When any of the organisation implement the
concept of the cloud, computing it becomes a big problem,
which is related to the aspect of who would be in control
of the working and the security of the data. The user can
sometimes have the power of the data, which they should
not be allowed to do so. On the other hand, the security of
the data can also be enhanced using removing the account
of the user ones they leave the organisation.
One of the techniques, which is in recent use, is
the concept of the identity and access management [19].
The idea of the character and access management can be
used for many purposes. The main advantage of this
approach is for the managers; the manager can easily plot
down who would be having access to the data and who
would not be allowed to access the features. Many of the
solution in this aspect helps me the concept of the
management of the workflow. With the idea of the
workflow management and the self-service, the manager
and the employee individually can request the access and
approve the request without the involvement of any IT
interventions. The approval part can be considered the part
of the structured workflow. The concept or the approach
can be very much beneficial not only in the aspect of the
efficiency but also increases the security aspect of the idea
of the cloud computing [21].
To handle the aspect of the different password
and naming conventions, an automated solution would be
very much helpful. The concept of the IAM solution can
enforce a means of naming conventions across the
different platforms. This allows the uniqueness aspect
when more than one user has the same name attached to
the username. Additionally, it can be stated that the single
sign-on the solution can be helpful in the concept of
mitigating the password complexity. This is achieved
using a set of credential, which is unique. This concept can
be used for the idea of logging into the system, and
automatic authentication would be provided. In the
background of such aspect, it can be stated that a SSO
application can be used for the purpose of routinely
resetting the password when the session expires. This is
directly prompted to the user [28].
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VI. Conclusion
This paper illustrates the concept of the cloud and
demonstrates the cloud capabilities such as elasticity,
scalability, platform, low cost and the aspect of reliability.
The security problem which is faced with the concept of
cloud computing are majorly discussed. The concept of
cloud computing is related to the areas of services and
information management. The issue, which are linked with
the security of the data, is seen more in the concept of the
cloud computing when comparing it with other traditional
systems. This is due to the factor that the data in the cloud-
computing environment are highly dependent on the
concept of the network and the servers. There are many
users who are not aware of the privacy and security of the
cloud and they do not want to move towards the concept.
These type of problem have hindered the development of
the concept of cloud computing and the aspect of the
security. The solution which is related to the IAM has
evolved in the recent times which would be helping to
secure the data of the user as well provide a basic
framework of the concept of the data security. Security in
any type of technology can one of the main aspects, which
can lead to failure of the technology and the trust of the
people in using the technology. The consideration into
how to promote the security of the technology should be
prime factor of investigation which would be directly
include how to upsurge the security of the data which is
stored into the concept of the cloud and how to benefit
from the concept.
REFERENCES
[1] Lombardi, Flavio, and Roberto Di Pietro. Security for
cloud computing. Artech House, 2015.
[2] Singh, Shweta. "Security in Cloud Computing."
International Journal of Computer Applications
Technology and Research 3.8 (2014): 488-493.
[3] Ali, Mazhar, Samee U. Khan, and Athanasios V.
Vasilakos. "Security in cloud computing: Opportunities
and challenges." Information sciences 305 (2015): 357-
383.
[4] Almorsy, Mohamed, John Grundy, and Ingo Müller.
"An analysis of the cloud computing security problem."
arXiv preprint arXiv:1609.01107 (2016).
[5] Rittinghouse, John W., and James F. Ransome. Cloud
computing: implementation, management, and security.
CRC press, 2016.
Hashem, Ibrahim Abaker Targio, et al. "The rise of “big
data” on cloud computing: Review and open research
issues." Information Systems 47 (2015): 98-115
Almorsy, Mohamed, John Grundy, and Ingo Müller. "An
analysis of the cloud computing security problem." arXiv
preprint arXiv:1609.01107 (2016).
[6]Rao, R. Velumadhava, and K. Selvamani. "Data
security challenges and its solutions in cloud computing."
Procedia Computer Science 48 (2015): 204-209.
[7]Puthal, Deepak, et al. "Cloud computing features,
issues, and challenges: a big picture." Computational
Intelligence and Networks (CINE), 2015 International
Conference on. IEEE, 2015.
[8]Krishnan, Y. Navaneeth, Chandan N. Bhagwat, and
Aparajit P. Utpat. "Fog computing—Network based cloud
computing." Electronics and Communication Systems
(ICECS), 2015 2nd International Conference on. IEEE,
2015.
[9]Inukollu, Venkata Narasimha, Sailaja Arsi, and
Srinivasa Rao Ravuri. "Security issues associated with big
data in cloud computing." International Journal of
Network Security & Its Applications 6.3 (2014): 45.
[10]Wang, Bing, et al. "DDoS attack protection in the era
of cloud computing and software-defined networking."
Computer Networks 81 (2015): 308-319.
[11] Fu, Zhangjie, et al. "Achieving efficient cloud search
services: multi-keyword ranked search over encrypted
cloud data supporting parallel computing." IEICE
Transactions on Communications 98.1 (2015): 190-200.
[12]Botta, Alessio, et al. "On the integration of cloud
computing and internet of things." Future internet of
things and cloud (FiCloud), 2014 international conference
on. IEEE, 2014.
[13]Aazam, Mohammad, et al. "Cloud of Things:
Integrating Internet of Things and cloud computing and
the issues involved." Applied Sciences and Technology
(IBCAST), 2014 11th International Bhurban Conference
on. IEEE, 2014.
[14] Cao, Ning, et al. "Privacy-preserving multi-keyword
ranked search over encrypted cloud data." IEEE
Transactions on parallel and distributed systems 25.1
(2014): 222-233.
[15]Baek, Joonsang, et al. "A secure cloud computing
based framework for big data information management of
smart grid." IEEE transactions on cloud computing 3.2
(2015): 233-244.
[16]Zhang, Yinghui, et al. "Ensuring attribute privacy
protection and fast decryption for outsourced data security
in mobile cloud computing." Information Sciences 379
(2017): 42-61.
[17]Lian, Jiunn-Woei, David C. Yen, and Yen-Ting Wang.
"An exploratory study to understand the critical factors
affecting the decision to adopt cloud computing in Taiwan
hospital." International Journal of Information
Management 34.1 (2014): 28-36.
[18]Pancholi, Vishal R., and Bhadresh P. Patel.
"Enhancement of cloud computing security with secure
5
This paper illustrates the concept of the cloud and
demonstrates the cloud capabilities such as elasticity,
scalability, platform, low cost and the aspect of reliability.
The security problem which is faced with the concept of
cloud computing are majorly discussed. The concept of
cloud computing is related to the areas of services and
information management. The issue, which are linked with
the security of the data, is seen more in the concept of the
cloud computing when comparing it with other traditional
systems. This is due to the factor that the data in the cloud-
computing environment are highly dependent on the
concept of the network and the servers. There are many
users who are not aware of the privacy and security of the
cloud and they do not want to move towards the concept.
These type of problem have hindered the development of
the concept of cloud computing and the aspect of the
security. The solution which is related to the IAM has
evolved in the recent times which would be helping to
secure the data of the user as well provide a basic
framework of the concept of the data security. Security in
any type of technology can one of the main aspects, which
can lead to failure of the technology and the trust of the
people in using the technology. The consideration into
how to promote the security of the technology should be
prime factor of investigation which would be directly
include how to upsurge the security of the data which is
stored into the concept of the cloud and how to benefit
from the concept.
REFERENCES
[1] Lombardi, Flavio, and Roberto Di Pietro. Security for
cloud computing. Artech House, 2015.
[2] Singh, Shweta. "Security in Cloud Computing."
International Journal of Computer Applications
Technology and Research 3.8 (2014): 488-493.
[3] Ali, Mazhar, Samee U. Khan, and Athanasios V.
Vasilakos. "Security in cloud computing: Opportunities
and challenges." Information sciences 305 (2015): 357-
383.
[4] Almorsy, Mohamed, John Grundy, and Ingo Müller.
"An analysis of the cloud computing security problem."
arXiv preprint arXiv:1609.01107 (2016).
[5] Rittinghouse, John W., and James F. Ransome. Cloud
computing: implementation, management, and security.
CRC press, 2016.
Hashem, Ibrahim Abaker Targio, et al. "The rise of “big
data” on cloud computing: Review and open research
issues." Information Systems 47 (2015): 98-115
Almorsy, Mohamed, John Grundy, and Ingo Müller. "An
analysis of the cloud computing security problem." arXiv
preprint arXiv:1609.01107 (2016).
[6]Rao, R. Velumadhava, and K. Selvamani. "Data
security challenges and its solutions in cloud computing."
Procedia Computer Science 48 (2015): 204-209.
[7]Puthal, Deepak, et al. "Cloud computing features,
issues, and challenges: a big picture." Computational
Intelligence and Networks (CINE), 2015 International
Conference on. IEEE, 2015.
[8]Krishnan, Y. Navaneeth, Chandan N. Bhagwat, and
Aparajit P. Utpat. "Fog computing—Network based cloud
computing." Electronics and Communication Systems
(ICECS), 2015 2nd International Conference on. IEEE,
2015.
[9]Inukollu, Venkata Narasimha, Sailaja Arsi, and
Srinivasa Rao Ravuri. "Security issues associated with big
data in cloud computing." International Journal of
Network Security & Its Applications 6.3 (2014): 45.
[10]Wang, Bing, et al. "DDoS attack protection in the era
of cloud computing and software-defined networking."
Computer Networks 81 (2015): 308-319.
[11] Fu, Zhangjie, et al. "Achieving efficient cloud search
services: multi-keyword ranked search over encrypted
cloud data supporting parallel computing." IEICE
Transactions on Communications 98.1 (2015): 190-200.
[12]Botta, Alessio, et al. "On the integration of cloud
computing and internet of things." Future internet of
things and cloud (FiCloud), 2014 international conference
on. IEEE, 2014.
[13]Aazam, Mohammad, et al. "Cloud of Things:
Integrating Internet of Things and cloud computing and
the issues involved." Applied Sciences and Technology
(IBCAST), 2014 11th International Bhurban Conference
on. IEEE, 2014.
[14] Cao, Ning, et al. "Privacy-preserving multi-keyword
ranked search over encrypted cloud data." IEEE
Transactions on parallel and distributed systems 25.1
(2014): 222-233.
[15]Baek, Joonsang, et al. "A secure cloud computing
based framework for big data information management of
smart grid." IEEE transactions on cloud computing 3.2
(2015): 233-244.
[16]Zhang, Yinghui, et al. "Ensuring attribute privacy
protection and fast decryption for outsourced data security
in mobile cloud computing." Information Sciences 379
(2017): 42-61.
[17]Lian, Jiunn-Woei, David C. Yen, and Yen-Ting Wang.
"An exploratory study to understand the critical factors
affecting the decision to adopt cloud computing in Taiwan
hospital." International Journal of Information
Management 34.1 (2014): 28-36.
[18]Pancholi, Vishal R., and Bhadresh P. Patel.
"Enhancement of cloud computing security with secure
5

data storage using AES." International Journal for
Innovative Research in Science and Technology 2.9
(2016): 18-21.
[19]Whaiduzzaman, Md, et al. "A survey on vehicular
cloud computing." Journal of Network and Computer
Applications 40 (2014): 325-344.
[20]Shaikh, Rizwana, and M. Sasikumar. "Data
Classification for achieving Security in cloud computing."
Procedia computer science 45 (2015): 493-498.
[21]Zhao, Feng, Chao Li, and Chun Feng Liu. "A cloud
computing security solution based on fully homomorphic
encryption." Advanced Communication Technology
(ICACT), 2014 16th International Conference on. IEEE,
2014.
[22]Pasupuleti, Syam Kumar, Subramanian Ramalingam,
and Rajkumar Buyya. "An efficient and secure privacy-
preserving approach for outsourced data of resource
constrained mobile devices in cloud computing." Journal
of Network and Computer Applications 64 (2016): 12-22.
[23]Shi, Weisong, and Schahram Dustdar. "The promise
of edge computing." Computer 49.5 (2016): 78-81.
[24]Oliveira, Tiago, Manoj Thomas, and Mariana
Espadanal. "Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and
services sectors." Information & Management 51.5 (2014):
497-510.
[25]Oliveira, Tiago, Manoj Thomas, and Mariana
Espadanal. "Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and
services sectors." Information & Management 51.5 (2014):
497-510.
[26]Terzi, Duygu Sinanc, Ramazan Terzi, and Seref
Sagiroglu. "A survey on security and privacy issues in big
data." Internet Technology and Secured Transactions
(ICITST), 2015 10th International Conference for. IEEE,
2015.
[27]Ahmed, Monjur, and Mohammad Ashraf Hossain.
"Cloud computing and security issues in the cloud."
International Journal of Network Security & Its
Applications 6.1 (2014): 25.
[28]Sanaei, Zohreh, et al. "Heterogeneity in mobile cloud
computing: taxonomy and open challenges." IEEE
Communications Surveys & Tutorials 16.1 (2014): 369-
392.
[29]Shahzad, Farrukh. "State-of-the-art survey on cloud
computing security Challenges, approaches and solutions."
Procedia Computer Science 37 (2014): 357-362.
6
Innovative Research in Science and Technology 2.9
(2016): 18-21.
[19]Whaiduzzaman, Md, et al. "A survey on vehicular
cloud computing." Journal of Network and Computer
Applications 40 (2014): 325-344.
[20]Shaikh, Rizwana, and M. Sasikumar. "Data
Classification for achieving Security in cloud computing."
Procedia computer science 45 (2015): 493-498.
[21]Zhao, Feng, Chao Li, and Chun Feng Liu. "A cloud
computing security solution based on fully homomorphic
encryption." Advanced Communication Technology
(ICACT), 2014 16th International Conference on. IEEE,
2014.
[22]Pasupuleti, Syam Kumar, Subramanian Ramalingam,
and Rajkumar Buyya. "An efficient and secure privacy-
preserving approach for outsourced data of resource
constrained mobile devices in cloud computing." Journal
of Network and Computer Applications 64 (2016): 12-22.
[23]Shi, Weisong, and Schahram Dustdar. "The promise
of edge computing." Computer 49.5 (2016): 78-81.
[24]Oliveira, Tiago, Manoj Thomas, and Mariana
Espadanal. "Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and
services sectors." Information & Management 51.5 (2014):
497-510.
[25]Oliveira, Tiago, Manoj Thomas, and Mariana
Espadanal. "Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and
services sectors." Information & Management 51.5 (2014):
497-510.
[26]Terzi, Duygu Sinanc, Ramazan Terzi, and Seref
Sagiroglu. "A survey on security and privacy issues in big
data." Internet Technology and Secured Transactions
(ICITST), 2015 10th International Conference for. IEEE,
2015.
[27]Ahmed, Monjur, and Mohammad Ashraf Hossain.
"Cloud computing and security issues in the cloud."
International Journal of Network Security & Its
Applications 6.1 (2014): 25.
[28]Sanaei, Zohreh, et al. "Heterogeneity in mobile cloud
computing: taxonomy and open challenges." IEEE
Communications Surveys & Tutorials 16.1 (2014): 369-
392.
[29]Shahzad, Farrukh. "State-of-the-art survey on cloud
computing security Challenges, approaches and solutions."
Procedia Computer Science 37 (2014): 357-362.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





