Security Consultation Report and Guideline
VerifiedAdded on 2022/10/19
|13
|2447
|371
AI Summary
Read this Security Consultation Report and Guideline to learn about the components of organization information system, identification of threats brought with the BYOD policy, identification of potential vulnerabilities, assessment of risks to organization information system, working principle of certificate-based authentication, comparison and contrast over authentication techniques, identification of features for certificate-based device and BYOD policy, characteristics of a phishing act, representative examples of phishing, and phishing handling instruction.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: SECURITY CONSULTATION REPORT AND GUIDELINE
Security Consultation Report and Guideline
Name of the Student
Name of the University
Author note
Security Consultation Report and Guideline
Name of the Student
Name of the University
Author note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1SECURITY CONSULTATION REPORT AND GUIDELINE
Table of Contents
Task 1...............................................................................................................................................2
1.1 Components of Organisation Information System................................................................2
1.2 Identification of Threats brought with the BYOD Policy.....................................................2
1.3 Identification of Potential Vulnerabilities.............................................................................4
1.4 Assessment of Risks to Organisation Information System....................................................5
Task 2...............................................................................................................................................6
2.1 Working Principle of Certificate-based Authentication........................................................6
2.2 Comparison and contrast over authentication techniques.....................................................6
2.3 Identification of features for Certificate-based device and BYOD Policy............................7
Task 3...............................................................................................................................................7
3.1 Characteristics of a Phishing Act...........................................................................................7
3.2 Representative examples of phishing....................................................................................8
3.3 Phishing Handling Instruction...............................................................................................8
References......................................................................................................................................10
Table of Contents
Task 1...............................................................................................................................................2
1.1 Components of Organisation Information System................................................................2
1.2 Identification of Threats brought with the BYOD Policy.....................................................2
1.3 Identification of Potential Vulnerabilities.............................................................................4
1.4 Assessment of Risks to Organisation Information System....................................................5
Task 2...............................................................................................................................................6
2.1 Working Principle of Certificate-based Authentication........................................................6
2.2 Comparison and contrast over authentication techniques.....................................................6
2.3 Identification of features for Certificate-based device and BYOD Policy............................7
Task 3...............................................................................................................................................7
3.1 Characteristics of a Phishing Act...........................................................................................7
3.2 Representative examples of phishing....................................................................................8
3.3 Phishing Handling Instruction...............................................................................................8
References......................................................................................................................................10

2SECURITY CONSULTATION REPORT AND GUIDELINE
Task 1
1.1 Components of Organisation Information System
The critical aspects in relation to organisation information system are:
1. Hardware – This can be defined as the physical technology that helps to make the
system work. Keyboards, routers and external hard drives could be defined as some form of
hardware systems.
2. Software – The computer hardware would need an inbuilt software that would help the
functioning of the computer systems (Lee, Park and Lee 2015). Operating system forms the most
important piece within the system that helps in the designing of specific tasks.
3. Telecommunications – This component helps in establishing a connection between
the hardware and software systems. These connections could be established through physical
wires such as fibre optics, Ethernet cables and also through Wi-Fi technology. Based on the
disperse nature of computers, the network strength would be dependent in order to establish a
proper connection.
4. Data warehouses and Databases – A database can be defined as a place in which a
large pool of data could be stored. A data warehouse helps in storing of data that is highly
needed by organization. These form the repositories that help in the storing of large forms of data
that could be analysed and results be produced.
1.2 Identification of Threats brought with the BYOD Policy
The different threats that could be made with the impact of the BYOD policy are:
Task 1
1.1 Components of Organisation Information System
The critical aspects in relation to organisation information system are:
1. Hardware – This can be defined as the physical technology that helps to make the
system work. Keyboards, routers and external hard drives could be defined as some form of
hardware systems.
2. Software – The computer hardware would need an inbuilt software that would help the
functioning of the computer systems (Lee, Park and Lee 2015). Operating system forms the most
important piece within the system that helps in the designing of specific tasks.
3. Telecommunications – This component helps in establishing a connection between
the hardware and software systems. These connections could be established through physical
wires such as fibre optics, Ethernet cables and also through Wi-Fi technology. Based on the
disperse nature of computers, the network strength would be dependent in order to establish a
proper connection.
4. Data warehouses and Databases – A database can be defined as a place in which a
large pool of data could be stored. A data warehouse helps in storing of data that is highly
needed by organization. These form the repositories that help in the storing of large forms of data
that could be analysed and results be produced.
1.2 Identification of Threats brought with the BYOD Policy
The different threats that could be made with the impact of the BYOD policy are:

3SECURITY CONSULTATION REPORT AND GUIDELINE
1. Increasing risks due to data leakage – With the high form of reliance over mobile
devices, there has been major risks of data being leaked without the prior information to
customers and employees. Irregularity in patch updates being supported to the system software
could be one of the primary reason behind the risk of data leakage.
2. Exploitation of vulnerabilities – Any official within an organization has less control
over mobile device usage. Hence, they are highly susceptible to attacks being raised over the
system.
3. Combination of business and personal data – The most obvious challenges made to
BYOD policy is based on the storage of personal and corporate data. The highest threats is that
malware being installed within the mobile devices (Eslahi et al. 2014). This means that a
particular malware application could get installed when the user would make use of the network
supported within the organization.
1. Increasing risks due to data leakage – With the high form of reliance over mobile
devices, there has been major risks of data being leaked without the prior information to
customers and employees. Irregularity in patch updates being supported to the system software
could be one of the primary reason behind the risk of data leakage.
2. Exploitation of vulnerabilities – Any official within an organization has less control
over mobile device usage. Hence, they are highly susceptible to attacks being raised over the
system.
3. Combination of business and personal data – The most obvious challenges made to
BYOD policy is based on the storage of personal and corporate data. The highest threats is that
malware being installed within the mobile devices (Eslahi et al. 2014). This means that a
particular malware application could get installed when the user would make use of the network
supported within the organization.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4SECURITY CONSULTATION REPORT AND GUIDELINE
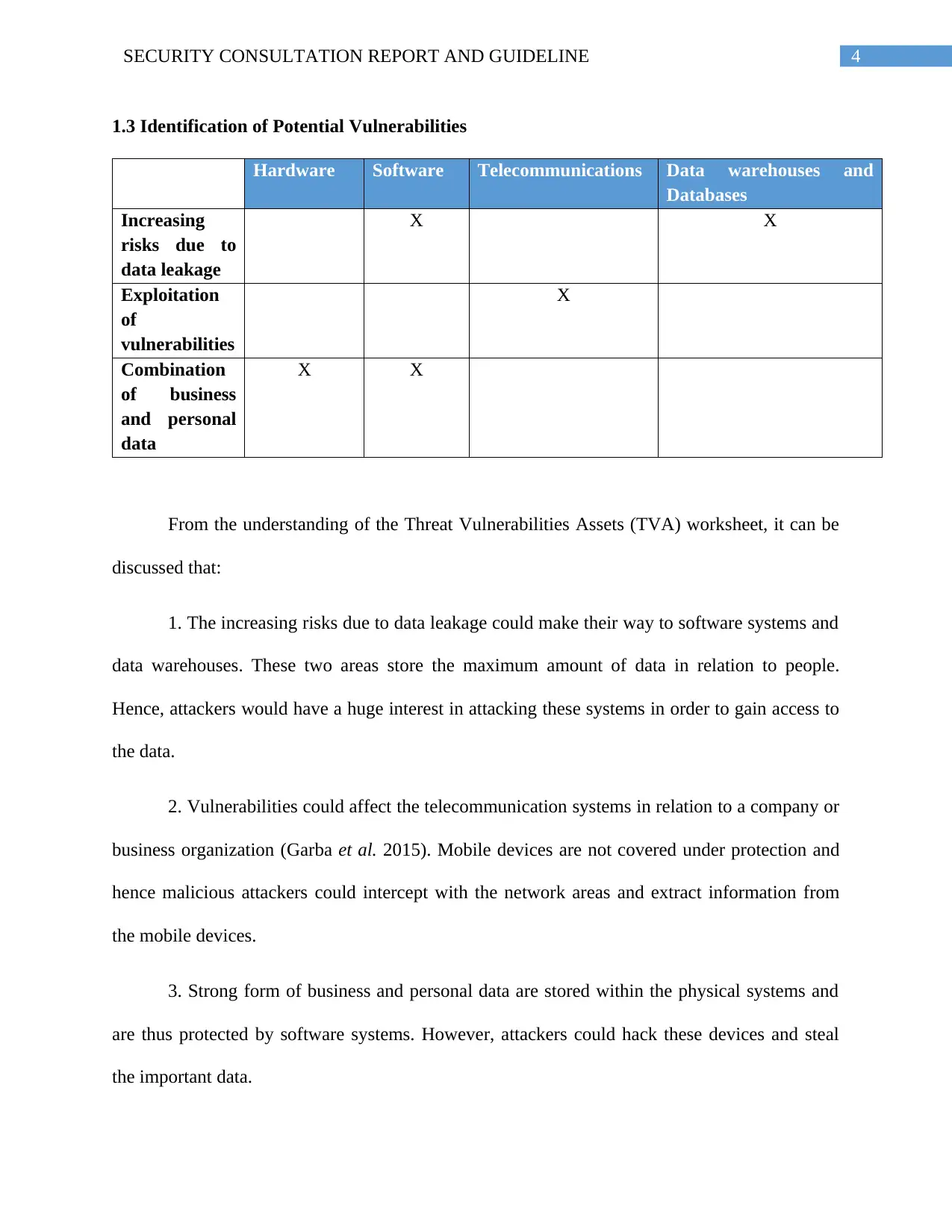
1.3 Identification of Potential Vulnerabilities
Hardware Software Telecommunications Data warehouses and
Databases
Increasing
risks due to
data leakage
X X
Exploitation
of
vulnerabilities
X
Combination
of business
and personal
data
X X
From the understanding of the Threat Vulnerabilities Assets (TVA) worksheet, it can be
discussed that:
1. The increasing risks due to data leakage could make their way to software systems and
data warehouses. These two areas store the maximum amount of data in relation to people.
Hence, attackers would have a huge interest in attacking these systems in order to gain access to
the data.
2. Vulnerabilities could affect the telecommunication systems in relation to a company or
business organization (Garba et al. 2015). Mobile devices are not covered under protection and
hence malicious attackers could intercept with the network areas and extract information from
the mobile devices.
3. Strong form of business and personal data are stored within the physical systems and
are thus protected by software systems. However, attackers could hack these devices and steal
the important data.
1.3 Identification of Potential Vulnerabilities
Hardware Software Telecommunications Data warehouses and
Databases
Increasing
risks due to
data leakage
X X
Exploitation
of
vulnerabilities
X
Combination
of business
and personal
data
X X
From the understanding of the Threat Vulnerabilities Assets (TVA) worksheet, it can be
discussed that:
1. The increasing risks due to data leakage could make their way to software systems and
data warehouses. These two areas store the maximum amount of data in relation to people.
Hence, attackers would have a huge interest in attacking these systems in order to gain access to
the data.
2. Vulnerabilities could affect the telecommunication systems in relation to a company or
business organization (Garba et al. 2015). Mobile devices are not covered under protection and
hence malicious attackers could intercept with the network areas and extract information from
the mobile devices.
3. Strong form of business and personal data are stored within the physical systems and
are thus protected by software systems. However, attackers could hack these devices and steal
the important data.

5SECURITY CONSULTATION REPORT AND GUIDELINE

6SECURITY CONSULTATION REPORT AND GUIDELINE
1.4 Assessment of Risks to Organisation Information System
Risks Risk Assessment Approach
Increasing risks due to
data leakage
Qualitative risk assessment approach – Consequence/Probability
Matrix
Exploitation of
vulnerabilities
Qualitative risk assessment approach – Decision Tree Analysis
Combination of
business and personal
data
Qualitative risk assessment approach – Delphi Technique
In the first case, the Consequence/Probability Matrix can help in providing a practical
approach based on determining the likelihood of occurrence for the particular risk. Based on the
assessment of probability for occurrence of the risk, the consequence after the risk should be
determined. This could further be presented in the form of a ranking method.
In the second case, it can be determined that there are several kind of vulnerabilities that
might affect the system (Feng, Wang and Li 2014). The use of Decision Tree Analysis could be
helpful in the determination of the best action that could be taken during the course of proposed
event scenarios.
In the third case, with the use of Delphi technique could be used in order to gain opinions
from experts who would gain ideas about the event that has occurred. Each security expert would
provide their own ideas, after which these would be reviewed and assessed properly.
1.4 Assessment of Risks to Organisation Information System
Risks Risk Assessment Approach
Increasing risks due to
data leakage
Qualitative risk assessment approach – Consequence/Probability
Matrix
Exploitation of
vulnerabilities
Qualitative risk assessment approach – Decision Tree Analysis
Combination of
business and personal
data
Qualitative risk assessment approach – Delphi Technique
In the first case, the Consequence/Probability Matrix can help in providing a practical
approach based on determining the likelihood of occurrence for the particular risk. Based on the
assessment of probability for occurrence of the risk, the consequence after the risk should be
determined. This could further be presented in the form of a ranking method.
In the second case, it can be determined that there are several kind of vulnerabilities that
might affect the system (Feng, Wang and Li 2014). The use of Decision Tree Analysis could be
helpful in the determination of the best action that could be taken during the course of proposed
event scenarios.
In the third case, with the use of Delphi technique could be used in order to gain opinions
from experts who would gain ideas about the event that has occurred. Each security expert would
provide their own ideas, after which these would be reviewed and assessed properly.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY CONSULTATION REPORT AND GUIDELINE
Task 2
2.1 Working Principle of Certificate-based Authentication
1. In the primary step, the client side would request requests for a password to the
particular database in order to gain access to a session. After the entering of the password, the
user would need to have to maintain the integrity throughout the session.
2. The client would then be able to unlock the private-key database, retrieve the necessary
private key and make use of the key for signing data (Konstantinov et al. 2015). The digital
signature and data would ensure the validity of private key.
3. The client would then send the randomly generated data and user certificate present
across the network.
4. The server ensures that the user certificate and the data are signed in order to
authenticate the identity of client.
5. The server would perform the other tasks of authentication that includes the factor of
checking whether the presented certificate by the client would be stored within the LDAP
directory. The server would evaluate whether a user have been provided with permission in order
to access the resource (Tan et al. 2016). In case the result derived from the evaluation becomes
positive, the server would be able to provide permission to client for gaining access to the
requested resource.
2.2 Comparison and contrast over authentication techniques
The organisations generally store their data and core programs within the central server
that are stored in a local platform or within the cloud server. In the case of password-based
authentication, the user would need to present their username and their according password
Task 2
2.1 Working Principle of Certificate-based Authentication
1. In the primary step, the client side would request requests for a password to the
particular database in order to gain access to a session. After the entering of the password, the
user would need to have to maintain the integrity throughout the session.
2. The client would then be able to unlock the private-key database, retrieve the necessary
private key and make use of the key for signing data (Konstantinov et al. 2015). The digital
signature and data would ensure the validity of private key.
3. The client would then send the randomly generated data and user certificate present
across the network.
4. The server ensures that the user certificate and the data are signed in order to
authenticate the identity of client.
5. The server would perform the other tasks of authentication that includes the factor of
checking whether the presented certificate by the client would be stored within the LDAP
directory. The server would evaluate whether a user have been provided with permission in order
to access the resource (Tan et al. 2016). In case the result derived from the evaluation becomes
positive, the server would be able to provide permission to client for gaining access to the
requested resource.
2.2 Comparison and contrast over authentication techniques
The organisations generally store their data and core programs within the central server
that are stored in a local platform or within the cloud server. In the case of password-based
authentication, the user would need to present their username and their according password

8SECURITY CONSULTATION REPORT AND GUIDELINE
(Chen et al. 2015). Based on the matching of both these data, the client would be granted access
to the system.
In the case of certificate-based authentication technique, transfer of digital bits of
information are transferred over the network. A private key is shared with the client user thus
confirming over the public key allocated to the server. The user would perform a log in within
the server with the help of a public certificate, which would verify the identity. Based on gaining
a confirmation, a level of trust would get established and thus resources could be shared. This
process would in turn ensure the authenticity of user.
2.3 Identification of features for Certificate-based device and BYOD Policy
The primary discussed features based on user authentication and certificate-based device
based on BYOD policy are:
1. Security during access of mails by users within the computers and mobile devices used
at offices.
2. Performing of user authentication and encryption of email contents.
3. Ensuring the security within the established Wi-Fi network (Elatroush 2015).
4. Replacement of vulnerable username and passwords with the help of multi-factor
authentication based on VPN connections.
Task 3
3.1 Characteristics of a Phishing Act
Some of the main characteristics of a phishing act are:
(Chen et al. 2015). Based on the matching of both these data, the client would be granted access
to the system.
In the case of certificate-based authentication technique, transfer of digital bits of
information are transferred over the network. A private key is shared with the client user thus
confirming over the public key allocated to the server. The user would perform a log in within
the server with the help of a public certificate, which would verify the identity. Based on gaining
a confirmation, a level of trust would get established and thus resources could be shared. This
process would in turn ensure the authenticity of user.
2.3 Identification of features for Certificate-based device and BYOD Policy
The primary discussed features based on user authentication and certificate-based device
based on BYOD policy are:
1. Security during access of mails by users within the computers and mobile devices used
at offices.
2. Performing of user authentication and encryption of email contents.
3. Ensuring the security within the established Wi-Fi network (Elatroush 2015).
4. Replacement of vulnerable username and passwords with the help of multi-factor
authentication based on VPN connections.
Task 3
3.1 Characteristics of a Phishing Act
Some of the main characteristics of a phishing act are:

9SECURITY CONSULTATION REPORT AND GUIDELINE
1. Any phishing email that would have been presented could produce unrealistic threats
and make unnecessary demands that could be highly suspicious in nature.
2. Users who would be attacked with a phishing act might send text messages that might
have wrong spelling or mistakes in grammar.
3. An unusual URL might be supported that could not be incoming from a trustworthy
source (Alseadoon, Othman and Chan 2015).
4. Any phishing based message or email content might ask for sensitive information from
the user, which would clearly state that it would be an act of phishing.
3.2 Representative examples of phishing
The representative examples based on phishing based acts are:
1. The phishing emails or messages might be sent in groups. Generic names could be
used in such emails and hence a common name could be used for addressing a large number of
audience.
2. An email that would request the personal information of an individual could be an
example of a forged or phishing based act (Ferreira, Coventry and Lenzini 2015). Any email that
would request the personal information of a user could be determined as an act of phishing.
3. The criminals of the internet would create a sensation before the audience that they
would require the personal information in an urgent manner. Thus, the user might get confused
and would have less time to think about the authenticity of the source.
3.3 Phishing Handling Instruction
Some instructions based on handling acts of phishing are:
1. Any phishing email that would have been presented could produce unrealistic threats
and make unnecessary demands that could be highly suspicious in nature.
2. Users who would be attacked with a phishing act might send text messages that might
have wrong spelling or mistakes in grammar.
3. An unusual URL might be supported that could not be incoming from a trustworthy
source (Alseadoon, Othman and Chan 2015).
4. Any phishing based message or email content might ask for sensitive information from
the user, which would clearly state that it would be an act of phishing.
3.2 Representative examples of phishing
The representative examples based on phishing based acts are:
1. The phishing emails or messages might be sent in groups. Generic names could be
used in such emails and hence a common name could be used for addressing a large number of
audience.
2. An email that would request the personal information of an individual could be an
example of a forged or phishing based act (Ferreira, Coventry and Lenzini 2015). Any email that
would request the personal information of a user could be determined as an act of phishing.
3. The criminals of the internet would create a sensation before the audience that they
would require the personal information in an urgent manner. Thus, the user might get confused
and would have less time to think about the authenticity of the source.
3.3 Phishing Handling Instruction
Some instructions based on handling acts of phishing are:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10SECURITY CONSULTATION REPORT AND GUIDELINE
1. Users should critically think before clicking on any link. Clicking on random emails or
links could lead to leakage of sensitive information. Hence, users should need to go to the source
of the link before progressing over such stages.
2. Installation of anti-phishing toolbars within the popular internet browsers could be
helpful in protecting the user device from getting attacked by phishing emails and messages
(Abdelhamid, Ayesh and Thabtah 2014). Downloading of content from suspicious websites or
emails could lead to dangerous impacts over users.
3. Users should keep a constant check over their financial account statements in order to
ensure that there is no form of fraudulent transactions. Users should also update their present
passwords regularly in order to ensure that the strength is being maintained continuously.
1. Users should critically think before clicking on any link. Clicking on random emails or
links could lead to leakage of sensitive information. Hence, users should need to go to the source
of the link before progressing over such stages.
2. Installation of anti-phishing toolbars within the popular internet browsers could be
helpful in protecting the user device from getting attacked by phishing emails and messages
(Abdelhamid, Ayesh and Thabtah 2014). Downloading of content from suspicious websites or
emails could lead to dangerous impacts over users.
3. Users should keep a constant check over their financial account statements in order to
ensure that there is no form of fraudulent transactions. Users should also update their present
passwords regularly in order to ensure that the strength is being maintained continuously.

11SECURITY CONSULTATION REPORT AND GUIDELINE
References
Abdelhamid, N., Ayesh, A. and Thabtah, F., 2014. Phishing detection based associative
classification data mining. Expert Systems with Applications, 41(13), pp.5948-5959.
Alseadoon, I., Othman, M.F.I. and Chan, T., 2015. What Is the Influence of Users’
Characteristics on Their Ability to Detect Phishing Emails?. In Advanced Computer and
Communication Engineering Technology (pp. 949-962). Springer, Cham.
Chen, Y., Sun, J., Zhang, R. and Zhang, Y., 2015, April. Your song your way: Rhythm-based
two-factor authentication for multi-touch mobile devices. In 2015 IEEE Conference on
Computer Communications (INFOCOM) (pp. 2686-2694). IEEE.
de las Cuevas, P., Mora, A.M., Merelo, J.J., Castillo, P.A., Garcia-Sanchez, P. and Fernandez-
Ares, A., 2015. Corporate security solutions for BYOD: A novel user-centric and self-adaptive
system. Computer Communications, 68, pp.83-95.
Elatroush, M.M., 2015. A CLOUD BASED INTRUSION DETECTION THAT PROTECT
CORPORATE WIRELESSES NETWORK FROM ANDROID SMARTPHONES
ATTACKS. NETWORK, 28, p.03.
Eslahi, M., Naseri, M.V., Hashim, H., Tahir, N.M. and Saad, E.H.M., 2014, April. BYOD:
Current state and security challenges. In 2014 IEEE Symposium on Computer Applications and
Industrial Electronics (ISCAIE) (pp. 189-192). IEEE.
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information
sciences, 256, pp.57-73.
References
Abdelhamid, N., Ayesh, A. and Thabtah, F., 2014. Phishing detection based associative
classification data mining. Expert Systems with Applications, 41(13), pp.5948-5959.
Alseadoon, I., Othman, M.F.I. and Chan, T., 2015. What Is the Influence of Users’
Characteristics on Their Ability to Detect Phishing Emails?. In Advanced Computer and
Communication Engineering Technology (pp. 949-962). Springer, Cham.
Chen, Y., Sun, J., Zhang, R. and Zhang, Y., 2015, April. Your song your way: Rhythm-based
two-factor authentication for multi-touch mobile devices. In 2015 IEEE Conference on
Computer Communications (INFOCOM) (pp. 2686-2694). IEEE.
de las Cuevas, P., Mora, A.M., Merelo, J.J., Castillo, P.A., Garcia-Sanchez, P. and Fernandez-
Ares, A., 2015. Corporate security solutions for BYOD: A novel user-centric and self-adaptive
system. Computer Communications, 68, pp.83-95.
Elatroush, M.M., 2015. A CLOUD BASED INTRUSION DETECTION THAT PROTECT
CORPORATE WIRELESSES NETWORK FROM ANDROID SMARTPHONES
ATTACKS. NETWORK, 28, p.03.
Eslahi, M., Naseri, M.V., Hashim, H., Tahir, N.M. and Saad, E.H.M., 2014, April. BYOD:
Current state and security challenges. In 2014 IEEE Symposium on Computer Applications and
Industrial Electronics (ISCAIE) (pp. 189-192). IEEE.
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information
sciences, 256, pp.57-73.

12SECURITY CONSULTATION REPORT AND GUIDELINE
Ferreira, A., Coventry, L. and Lenzini, G., 2015, August. Principles of persuasion in social
engineering and their use in phishing. In International Conference on Human Aspects of
Information Security, Privacy, and Trust (pp. 36-47). Springer, Cham.
Garba, A.B., Armarego, J., Murray, D. and Kenworthy, W., 2015. Review of the information
security and privacy challenges in Bring Your Own Device (BYOD) environments. Journal of
Information privacy and security, 11(1), pp.38-54.
Konstantinov, I.S., Lazarev, S.A., Mihalev, O.V., Demidov, A.V. and Shateev, R.V., 2015. The
development of infrastructure security for distributed information computer environment based
on secured portal network. International Journal of Applied Engineering Research, 10(17),
pp.38116-38120.
Lee, J., Park, J.G. and Lee, S., 2015. Raising team social capital with knowledge and
communication in information systems development projects. International Journal of Project
Management, 33(4), pp.797-807.
Tan, H., Ma, M., Labiod, H., Boudguiga, A., Zhang, J. and Chong, P.H.J., 2016. A secure and
authenticated key management protocol (SA-KMP) for vehicular networks. IEEE Transactions
on Vehicular Technology, 65(12), pp.9570-9584.
Ferreira, A., Coventry, L. and Lenzini, G., 2015, August. Principles of persuasion in social
engineering and their use in phishing. In International Conference on Human Aspects of
Information Security, Privacy, and Trust (pp. 36-47). Springer, Cham.
Garba, A.B., Armarego, J., Murray, D. and Kenworthy, W., 2015. Review of the information
security and privacy challenges in Bring Your Own Device (BYOD) environments. Journal of
Information privacy and security, 11(1), pp.38-54.
Konstantinov, I.S., Lazarev, S.A., Mihalev, O.V., Demidov, A.V. and Shateev, R.V., 2015. The
development of infrastructure security for distributed information computer environment based
on secured portal network. International Journal of Applied Engineering Research, 10(17),
pp.38116-38120.
Lee, J., Park, J.G. and Lee, S., 2015. Raising team social capital with knowledge and
communication in information systems development projects. International Journal of Project
Management, 33(4), pp.797-807.
Tan, H., Ma, M., Labiod, H., Boudguiga, A., Zhang, J. and Chong, P.H.J., 2016. A secure and
authenticated key management protocol (SA-KMP) for vehicular networks. IEEE Transactions
on Vehicular Technology, 65(12), pp.9570-9584.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





