Security | Cyber Attackers | Essay
VerifiedAdded on 2022/08/21
|6
|1104
|18
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: Security
Security
Name of the Student:
Name of the University:
Author's Note:
Security
Name of the Student:
Name of the University:
Author's Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1Security
Week 4:-
Current news Event:-
The cyber attackers have gathered 1.5 million dollars by stealing information of more
than 230,000 credit and debit card details on the black website. Some data analysts evaluated that
the hackers have taken up to 18 million datasets, which may drop on the black web for an
extensive period (Ilascu 2020). In this circumstance, the cyber attackers adapted a source based
on "Volusion-based" supplies for directing the user input options. This source loaded the
skimmer from an outside track. Trend Micro has specified that the violence initiated on seventh
September and is the effort of FIN6. RiskIQ has been defined as MageCart Group 6, and it has
been evaluated that it energies only after prestigious marks that confirm a considerable
transaction capacity. It is assumed that the cyber-attack was executed by a cyber-attacking team
named FIN6, who are ostensibly connected with another immense cyber break, including the
breaches of Newegg and British Airways.
There was user evidence that was present on the traveler webpage regarding Piraeus and
Alpha , Euro bank, and the Greece Domestic bank were all mandatory to withdraw cards
(Payment Data From Volusion Hack On Dark Web | PYMNTS.com, 2020). The banks approved
the attack in a mutual declaration and stated that a lesser number of customers had been charging
deceptively. The banking sectors are executing a detailed exploration into the problem to
determine how it occurred and is expected to be finished by this month. Previously, the payment
information was flogging from online stocks introduced by e-Commerce tools, presenting, and
helping commercial Volusion. At present, those documents have looked for the transaction on
the black web, which has conferred to information. The cyber attackers penetrated "Volusion"
Week 4:-
Current news Event:-
The cyber attackers have gathered 1.5 million dollars by stealing information of more
than 230,000 credit and debit card details on the black website. Some data analysts evaluated that
the hackers have taken up to 18 million datasets, which may drop on the black web for an
extensive period (Ilascu 2020). In this circumstance, the cyber attackers adapted a source based
on "Volusion-based" supplies for directing the user input options. This source loaded the
skimmer from an outside track. Trend Micro has specified that the violence initiated on seventh
September and is the effort of FIN6. RiskIQ has been defined as MageCart Group 6, and it has
been evaluated that it energies only after prestigious marks that confirm a considerable
transaction capacity. It is assumed that the cyber-attack was executed by a cyber-attacking team
named FIN6, who are ostensibly connected with another immense cyber break, including the
breaches of Newegg and British Airways.
There was user evidence that was present on the traveler webpage regarding Piraeus and
Alpha , Euro bank, and the Greece Domestic bank were all mandatory to withdraw cards
(Payment Data From Volusion Hack On Dark Web | PYMNTS.com, 2020). The banks approved
the attack in a mutual declaration and stated that a lesser number of customers had been charging
deceptively. The banking sectors are executing a detailed exploration into the problem to
determine how it occurred and is expected to be finished by this month. Previously, the payment
information was flogging from online stocks introduced by e-Commerce tools, presenting, and
helping commercial Volusion. At present, those documents have looked for the transaction on
the black web, which has conferred to information. The cyber attackers penetrated "Volusion"

2Security
servers. They hosted mischievous JavaScript language, which completed its method against
client supply websites, where it logged expense card facts when they have arrived into register
methods (For Sale: Card Data from Online Stores Using Volusion, 2020). The attack was
exposed in September-October, but scholars say the authentic break occurred a previous time, in
September. The code was created in many stores (like 6589), but initially, it was expected that it
would be affecting more than 23000 provisions. The whipped payment details were uploaded
about sometime late, on a dark website attacking forum, and it has been for the deal later then.
Investigators stated that the cyber attackers might have contracted access to nearly 20 to
25 million expense card facts, but they have traced about many (239,000) Card. It has been
assessed that the cyber attackers made about $1.46 million in income from the taken payment
information. The hack is assumed to be performed by the FIN6, which ostensibly connecting
with other massive breaches, like Newegg or other reputed organization British Airways
(Goldfeder et al. 2018). The breaches such the Volusion one are charming more and more usual
and do not just mark servers. The banking webpages are similarly in the list of aims. The break
gave hackers access to clients' evidence, counting Social Safety numbers, drivers' licenses, credit
card facts, and birthdays.
servers. They hosted mischievous JavaScript language, which completed its method against
client supply websites, where it logged expense card facts when they have arrived into register
methods (For Sale: Card Data from Online Stores Using Volusion, 2020). The attack was
exposed in September-October, but scholars say the authentic break occurred a previous time, in
September. The code was created in many stores (like 6589), but initially, it was expected that it
would be affecting more than 23000 provisions. The whipped payment details were uploaded
about sometime late, on a dark website attacking forum, and it has been for the deal later then.
Investigators stated that the cyber attackers might have contracted access to nearly 20 to
25 million expense card facts, but they have traced about many (239,000) Card. It has been
assessed that the cyber attackers made about $1.46 million in income from the taken payment
information. The hack is assumed to be performed by the FIN6, which ostensibly connecting
with other massive breaches, like Newegg or other reputed organization British Airways
(Goldfeder et al. 2018). The breaches such the Volusion one are charming more and more usual
and do not just mark servers. The banking webpages are similarly in the list of aims. The break
gave hackers access to clients' evidence, counting Social Safety numbers, drivers' licenses, credit
card facts, and birthdays.
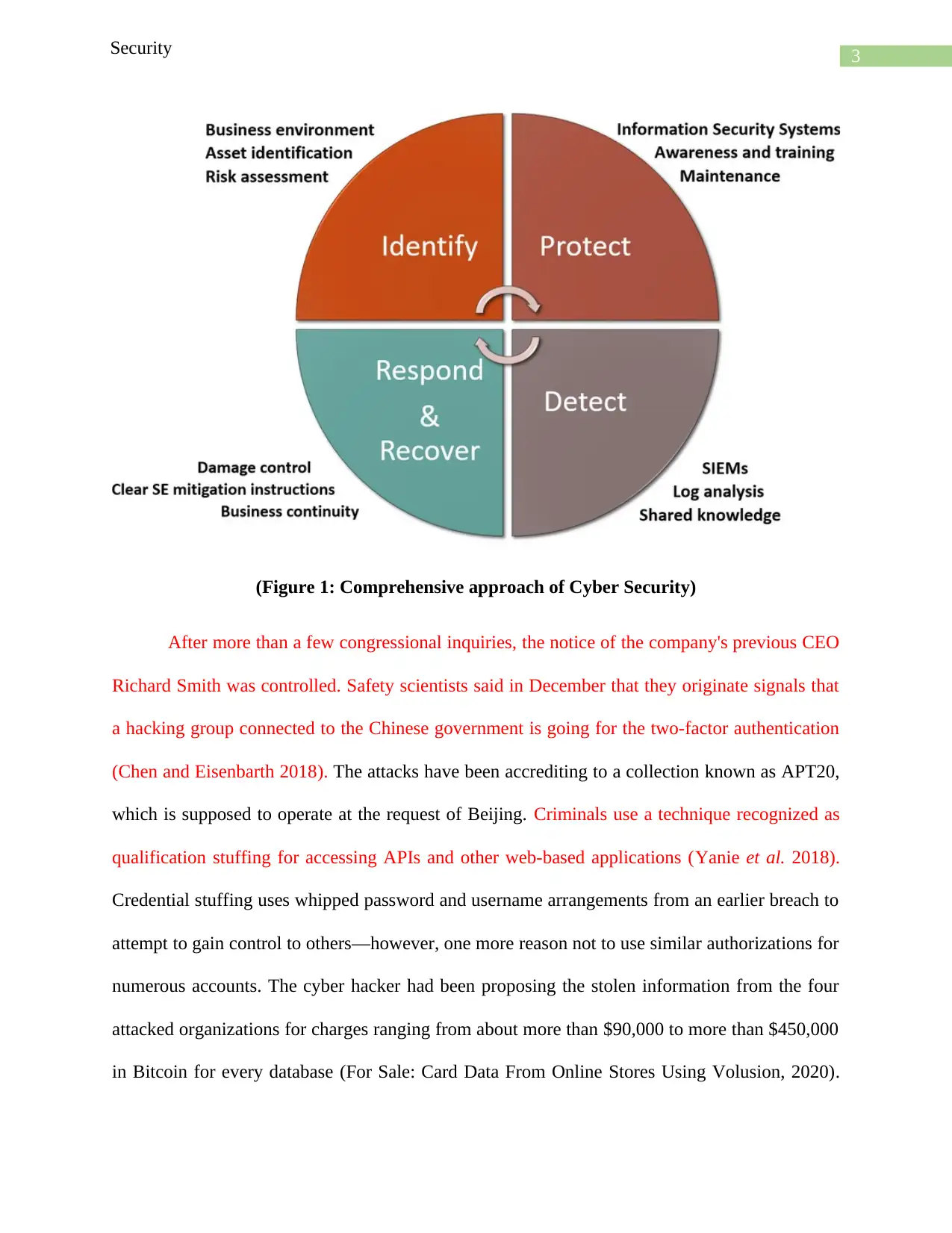
3Security
(Figure 1: Comprehensive approach of Cyber Security)
After more than a few congressional inquiries, the notice of the company's previous CEO
Richard Smith was controlled. Safety scientists said in December that they originate signals that
a hacking group connected to the Chinese government is going for the two-factor authentication
(Chen and Eisenbarth 2018). The attacks have been accrediting to a collection known as APT20,
which is supposed to operate at the request of Beijing. Criminals use a technique recognized as
qualification stuffing for accessing APIs and other web-based applications (Yanie et al. 2018).
Credential stuffing uses whipped password and username arrangements from an earlier breach to
attempt to gain control to others—however, one more reason not to use similar authorizations for
numerous accounts. The cyber hacker had been proposing the stolen information from the four
attacked organizations for charges ranging from about more than $90,000 to more than $450,000
in Bitcoin for every database (For Sale: Card Data From Online Stores Using Volusion, 2020).
(Figure 1: Comprehensive approach of Cyber Security)
After more than a few congressional inquiries, the notice of the company's previous CEO
Richard Smith was controlled. Safety scientists said in December that they originate signals that
a hacking group connected to the Chinese government is going for the two-factor authentication
(Chen and Eisenbarth 2018). The attacks have been accrediting to a collection known as APT20,
which is supposed to operate at the request of Beijing. Criminals use a technique recognized as
qualification stuffing for accessing APIs and other web-based applications (Yanie et al. 2018).
Credential stuffing uses whipped password and username arrangements from an earlier breach to
attempt to gain control to others—however, one more reason not to use similar authorizations for
numerous accounts. The cyber hacker had been proposing the stolen information from the four
attacked organizations for charges ranging from about more than $90,000 to more than $450,000
in Bitcoin for every database (For Sale: Card Data From Online Stores Using Volusion, 2020).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4Security
Though, the attacker also left a message on the dark web that seems to designate that the attacker
tried to extract payments from the objects before putting the documents up for transaction on the
black web.
Though, the attacker also left a message on the dark web that seems to designate that the attacker
tried to extract payments from the objects before putting the documents up for transaction on the
black web.

5Security
References:-
Bankinfosecurity.com. 2020. For Sale: Card Data From Online Stores Using Volusion. [online]
Available at: <https://www.bankinfosecurity.com/payment-card-data-from-online-stores-for-
sale-on-dark-web-a-13937> [Accessed 17 March 2020].
Chen, J.S. and Eisenbarth, S.C., 2018. Two-Factor Authentication for Type 2
Immunity. Immunity, 49(3), pp.381-383.
Goldfeder, S., Kalodner, H., Reisman, D. and Narayanan, A., 2018. When the cookie meets the
blockchain: Privacy risks of web payments via cryptocurrencies. Proceedings on Privacy
Enhancing Technologies, 2018(4), pp.179-199.
Ilascu, I., 2020. Hackers Get $1.6 Million For Card Data From Breached Online Shops. [online]
BleepingComputer. Available at: <https://www.bleepingcomputer.com/news/security/hackers-
get-16-million-for-card-data-from-breached-online-shops/?&web_view=true> [Accessed 16
March 2020].
PYMNTS.com. 2020. Payment Data From Volusion Hack On Dark Web | PYMNTS.Com.
[online] Available at: <https://www.pymnts.com/news/security-and-risk/2020/payment-data-
from-2019-volusion-hack-appears-on-dark-web/> [Accessed 16 March 2020].
Yanie, A., Hasibuan, A., Ishak, I., Marsono, M., Lubis, S., Nurmalini, N., Mesran, M., Nasution,
S.D., Rahim, R., Nurdiyanto, H. and Ahmar, A.S., 2018, June. Web Based Application for
Decision Support System with ELECTRE Method. In Journal of Physics: Conference
Series (Vol. 1028, No. 1, p. 012054). IOP Publishing.
References:-
Bankinfosecurity.com. 2020. For Sale: Card Data From Online Stores Using Volusion. [online]
Available at: <https://www.bankinfosecurity.com/payment-card-data-from-online-stores-for-
sale-on-dark-web-a-13937> [Accessed 17 March 2020].
Chen, J.S. and Eisenbarth, S.C., 2018. Two-Factor Authentication for Type 2
Immunity. Immunity, 49(3), pp.381-383.
Goldfeder, S., Kalodner, H., Reisman, D. and Narayanan, A., 2018. When the cookie meets the
blockchain: Privacy risks of web payments via cryptocurrencies. Proceedings on Privacy
Enhancing Technologies, 2018(4), pp.179-199.
Ilascu, I., 2020. Hackers Get $1.6 Million For Card Data From Breached Online Shops. [online]
BleepingComputer. Available at: <https://www.bleepingcomputer.com/news/security/hackers-
get-16-million-for-card-data-from-breached-online-shops/?&web_view=true> [Accessed 16
March 2020].
PYMNTS.com. 2020. Payment Data From Volusion Hack On Dark Web | PYMNTS.Com.
[online] Available at: <https://www.pymnts.com/news/security-and-risk/2020/payment-data-
from-2019-volusion-hack-appears-on-dark-web/> [Accessed 16 March 2020].
Yanie, A., Hasibuan, A., Ishak, I., Marsono, M., Lubis, S., Nurmalini, N., Mesran, M., Nasution,
S.D., Rahim, R., Nurdiyanto, H. and Ahmar, A.S., 2018, June. Web Based Application for
Decision Support System with ELECTRE Method. In Journal of Physics: Conference
Series (Vol. 1028, No. 1, p. 012054). IOP Publishing.
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





