Security Fundamentals: CIA Triad, Biometrics, and Authentication
VerifiedAdded on 2023/06/14
|15
|3822
|398
Homework Assignment
AI Summary
This assignment solution delves into fundamental security concepts, focusing on the CIA triad (Confidentiality, Integrity, Availability) and its application in various scenarios like financial information and government press releases. It also addresses ATM security, calculating the maximum PIN attempts before card blockage. Furthermore, the assignment discusses the advantages and disadvantages of biometric authentication, including concerns about security breaches, false acceptance rates, and system mapping issues. It explores multi-factor authentication as a security enhancement and analyzes the implications of false negatives in biometric systems, highlighting potential risks and operational disruptions. Desklib provides a platform to access this and many other solved assignments.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Answer to Question 1..........................................................................................................2
Answer to Question 2..........................................................................................................4
Answer to Question 3..........................................................................................................4
Answer to Question 4..........................................................................................................7
Answer to Question 5..........................................................................................................8
References..........................................................................................................................11
Table of Contents
Answer to Question 1..........................................................................................................2
Answer to Question 2..........................................................................................................4
Answer to Question 3..........................................................................................................4
Answer to Question 4..........................................................................................................7
Answer to Question 5..........................................................................................................8
References..........................................................................................................................11

2INFORMATION SECURITY
Answer to Question 1
CIA triad is nothing but a model which provides three main goals which are needed for
achieving information security (Bakar et al., 2018). CIA triad goal of confidentiality is
considered to be more important than any other kind of goal in situation when the value of
information is depended on limiting its access. Confidentiality is mainly ensuring that various
kinds of sensitive information are only accessed by an authorized people and it kept away from
those who are not authorized to access it. It is generally implemented by making use of security
mechanism like username, access control list (ACLs) and various kinds of encryption
(Bhagavatula et al., 2015). It is considered to be common for some kinds of information which is
mainly categorized as per the extent of damage which can be done during unintended hands.
Then after that security measures can be easily implemented as per the needs. For example,
confidentiality of information is generally considered to be more important than any other
parameter like priority information of an organization. Also confidentiality is considered to be
most important when information is recorded from various kinds of personal activities. For
providing guarantee of confidentiality under triad of CIA, communication channel should be
monitored and controlled easily for preventing any kind of authorized access.
Integrity mainly ensures that information is provided in a format which is considered to
valid and original to purpose (Choi, Lee & Yoon, 2016). The receiver of this kind of information
must have information regarding which creator must have. Information can be easily edited by
any kind of authorized persons only and it remains in original state when it is considered to be
rest. Integrity can be easily implemented by making use of security mechanism like data
encryption and hashing (Deokar, & Wakode, 2017). In many cases it is seen that changes in data
is seen as a result of non-human caused events like electromagnetic events like electromagnetic
Answer to Question 1
CIA triad is nothing but a model which provides three main goals which are needed for
achieving information security (Bakar et al., 2018). CIA triad goal of confidentiality is
considered to be more important than any other kind of goal in situation when the value of
information is depended on limiting its access. Confidentiality is mainly ensuring that various
kinds of sensitive information are only accessed by an authorized people and it kept away from
those who are not authorized to access it. It is generally implemented by making use of security
mechanism like username, access control list (ACLs) and various kinds of encryption
(Bhagavatula et al., 2015). It is considered to be common for some kinds of information which is
mainly categorized as per the extent of damage which can be done during unintended hands.
Then after that security measures can be easily implemented as per the needs. For example,
confidentiality of information is generally considered to be more important than any other
parameter like priority information of an organization. Also confidentiality is considered to be
most important when information is recorded from various kinds of personal activities. For
providing guarantee of confidentiality under triad of CIA, communication channel should be
monitored and controlled easily for preventing any kind of authorized access.
Integrity mainly ensures that information is provided in a format which is considered to
valid and original to purpose (Choi, Lee & Yoon, 2016). The receiver of this kind of information
must have information regarding which creator must have. Information can be easily edited by
any kind of authorized persons only and it remains in original state when it is considered to be
rest. Integrity can be easily implemented by making use of security mechanism like data
encryption and hashing (Deokar, & Wakode, 2017). In many cases it is seen that changes in data
is seen as a result of non-human caused events like electromagnetic events like electromagnetic
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
pulse (EMP) or even cases of server crash. It is important to note that back up procedure and
redundant system works in place for data integrity (Dere, Gurjar & Sipna, 2016). CIA goal of
integrity is considered to be important than other kind of goal in situation of financial
information. Any kind of changes in financial records may lead to various kinds of issues of
consistency. For example, banks are more concerned about the integrity of financial records
while for them confidentiality is taken on second priority. In some cases, it is seen account
holders or depositors leave various kinds of ATM receipt unchecked (Dere, Gurjar & Sipna,
2016). This mainly ensures that confidentiality is taken on high priority. Instead of that goal of
integrity is considered to be most important in case of information security in the case of banking
system. For providing guarantee of integrity under CIA triad, proper kind of information should
be protected any kind of unauthorized modifications.
Availability ensures that various kinds of information and resources are made available to
large number of business owners who badly need them (Farooq et la., 2015). It mainly focuses
on implementation of large number of methods like maintenance of hardware, patching of
hardware and optimization of network. Various kinds of process like failover, high-availability,
redundancy and clusters are used for mitigation or overcoming of serious kinds of consequences
when various kinds of hardware issues occur (Fernandez & Alexander, 2016). Various kinds of
dedicated devices are generally used for guarding against downtime and unreachable data due to
various kinds of malicious actions. It also focuses on the use of distributed denial of services
(DDoS) attacks. CIA triad goal of availability is considered to be much more important than any
other kind of goal when government generate online press releases are involved in it. Press
release are generally considered to be important for public consumption (Hadid et al., 2015). For
them to them to be properly effective in nature the information contained by them are made
pulse (EMP) or even cases of server crash. It is important to note that back up procedure and
redundant system works in place for data integrity (Dere, Gurjar & Sipna, 2016). CIA goal of
integrity is considered to be important than other kind of goal in situation of financial
information. Any kind of changes in financial records may lead to various kinds of issues of
consistency. For example, banks are more concerned about the integrity of financial records
while for them confidentiality is taken on second priority. In some cases, it is seen account
holders or depositors leave various kinds of ATM receipt unchecked (Dere, Gurjar & Sipna,
2016). This mainly ensures that confidentiality is taken on high priority. Instead of that goal of
integrity is considered to be most important in case of information security in the case of banking
system. For providing guarantee of integrity under CIA triad, proper kind of information should
be protected any kind of unauthorized modifications.
Availability ensures that various kinds of information and resources are made available to
large number of business owners who badly need them (Farooq et la., 2015). It mainly focuses
on implementation of large number of methods like maintenance of hardware, patching of
hardware and optimization of network. Various kinds of process like failover, high-availability,
redundancy and clusters are used for mitigation or overcoming of serious kinds of consequences
when various kinds of hardware issues occur (Fernandez & Alexander, 2016). Various kinds of
dedicated devices are generally used for guarding against downtime and unreachable data due to
various kinds of malicious actions. It also focuses on the use of distributed denial of services
(DDoS) attacks. CIA triad goal of availability is considered to be much more important than any
other kind of goal when government generate online press releases are involved in it. Press
release are generally considered to be important for public consumption (Hadid et al., 2015). For
them to them to be properly effective in nature the information contained by them are made
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
available to public. So in this case confidentiality is not a matter of concern while integrity is
considered on the second priority. In the domain of CIA triad, for providing guarantee
availability of information related to press release government mainly checks that their website
and system have minimum kind of effect on public information.
Answer to Question 2
Maximum number of pins which this thief can enter before proper discovery of actual pin
number can be calculated by the help of permutation technique from mathematics. The total
number of keypad of an ATM machine is ten that is zero to 10. Now the situation provided in the
question is that the thief has broken five keys so more five number of keys will be available to
him for making inputs. The pin number of a ATM machine is generally made of four numbers.
Therefore, after damaging the five keys four-digit pin number can be entered by left five keys
which is available to him. This situation can be calculated by permutation from mathematics.
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
So total number of outcomes from the calculation is 120. On the contrary as per the ATM
security an individual can easily enter pin for a maximum value of three. After providing three
inputs the ATM card gets blocked. So considered the situation of ATM machine the maximum
number of times in which an individual can enter pin is three. On the contrary after three trials
made by the card the card will be blocked automatically.
Answer to Question 3
There are many kinds of advantages which can be obtained by the use of biometric. On
the contrary a large number of issues can be faced during the usage (Haque, Nasrollahi &
available to public. So in this case confidentiality is not a matter of concern while integrity is
considered on the second priority. In the domain of CIA triad, for providing guarantee
availability of information related to press release government mainly checks that their website
and system have minimum kind of effect on public information.
Answer to Question 2
Maximum number of pins which this thief can enter before proper discovery of actual pin
number can be calculated by the help of permutation technique from mathematics. The total
number of keypad of an ATM machine is ten that is zero to 10. Now the situation provided in the
question is that the thief has broken five keys so more five number of keys will be available to
him for making inputs. The pin number of a ATM machine is generally made of four numbers.
Therefore, after damaging the five keys four-digit pin number can be entered by left five keys
which is available to him. This situation can be calculated by permutation from mathematics.
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
So total number of outcomes from the calculation is 120. On the contrary as per the ATM
security an individual can easily enter pin for a maximum value of three. After providing three
inputs the ATM card gets blocked. So considered the situation of ATM machine the maximum
number of times in which an individual can enter pin is three. On the contrary after three trials
made by the card the card will be blocked automatically.
Answer to Question 3
There are many kinds of advantages which can be obtained by the use of biometric. On
the contrary a large number of issues can be faced during the usage (Haque, Nasrollahi &

5INFORMATION SECURITY
Moeslund, 2015). The main three reason which is taken to be reluctant for the usage of biometric
are
Security is considered to be important reason behind the use of biometric. The
vital information of a person is mainly stored in the database (Havenetidis et al.,
2015). The information generally consists of address, contact number and various
other personal details. Now there is a situation in which a particular system is
hacked then it can affect that particular individual. In many situations it is
observed that various kinds of hackers take into identity of an individual in which
Many kinds of issues are generally encountered in biometric technology. The
important parameter which is considered to be important in this case is false
accepting and entry (He & Wang, 2015). Failure rates are generally considered to
be important in major kinds of biometric devices. There are generally two type of
rates are taken that is false acceptance and false rejection. Failure rates can be
used to verify that how system can verify an individual with specific characteristic
which is registered for them. Fingerprint system is totally based on fingerprint
that is merely used for authentication for large number of user.
An important which is encountered in biometric system is mapping. In some
situation it is observed that proper kind of identification is generally stored but the
particular situation the system may fail to recognize the particular person (Holz &
Knaust, 2015). This will thing will ultimately result in delay of entry a person. In
some of the situation it is encountered that the whole working system is damaged
by this.
Moeslund, 2015). The main three reason which is taken to be reluctant for the usage of biometric
are
Security is considered to be important reason behind the use of biometric. The
vital information of a person is mainly stored in the database (Havenetidis et al.,
2015). The information generally consists of address, contact number and various
other personal details. Now there is a situation in which a particular system is
hacked then it can affect that particular individual. In many situations it is
observed that various kinds of hackers take into identity of an individual in which
Many kinds of issues are generally encountered in biometric technology. The
important parameter which is considered to be important in this case is false
accepting and entry (He & Wang, 2015). Failure rates are generally considered to
be important in major kinds of biometric devices. There are generally two type of
rates are taken that is false acceptance and false rejection. Failure rates can be
used to verify that how system can verify an individual with specific characteristic
which is registered for them. Fingerprint system is totally based on fingerprint
that is merely used for authentication for large number of user.
An important which is encountered in biometric system is mapping. In some
situation it is observed that proper kind of identification is generally stored but the
particular situation the system may fail to recognize the particular person (Holz &
Knaust, 2015). This will thing will ultimately result in delay of entry a person. In
some of the situation it is encountered that the whole working system is damaged
by this.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY
Multifactor authentication is well known term in biometric in which large number of
problems are encountered (Jain, Nandakumar & Ross, 2016). In this method authentication is
mainly done by the help of name, password and lastly fingerprint. Multi-factor authentication
generally adds a layer of security which provides various kinds of organization to provide
protection against data breach like compromised credentials. Users generally provide some kinds
of extra information regarding corporate application, servers and other kinds of network.
Multifactor authentication generally considered to be combination of following factors like
username, password, pin and lastly security questions (Jain, Jain & Kapil, 2016). With large
number of credentials taking into account password based security is considered to be longer
effective. Multiple factor authentication (MFA) generally needs multiple methods for
identification and it is generally considered to be best method for preventing authorized users
from easily accessing the data of corporate.
Team of biometric works in gradient organization for more than ten years and also
achieved a lot of success in this domain (Lippi et al., 2017). According to this particular
organization that is gradient three important aspects must be taken into consideration that is
comfort, safety and lastly availability of an individual. Access to particular kind of database is
mainly provided to user when they require any kind of information. In many situations it is
observed that linkage between access and information generally fails and this does not allow
them to easily patch to have an access to it.
A large number of problems can be encountered in biometric so it focuses to be secure
and trustworthy in many situations (Lumini & Nanni, 2017). There are some kinds of issues
which are encountered in biometric that are rouge sensors and various kinds of unauthorized kind
Multifactor authentication is well known term in biometric in which large number of
problems are encountered (Jain, Nandakumar & Ross, 2016). In this method authentication is
mainly done by the help of name, password and lastly fingerprint. Multi-factor authentication
generally adds a layer of security which provides various kinds of organization to provide
protection against data breach like compromised credentials. Users generally provide some kinds
of extra information regarding corporate application, servers and other kinds of network.
Multifactor authentication generally considered to be combination of following factors like
username, password, pin and lastly security questions (Jain, Jain & Kapil, 2016). With large
number of credentials taking into account password based security is considered to be longer
effective. Multiple factor authentication (MFA) generally needs multiple methods for
identification and it is generally considered to be best method for preventing authorized users
from easily accessing the data of corporate.
Team of biometric works in gradient organization for more than ten years and also
achieved a lot of success in this domain (Lippi et al., 2017). According to this particular
organization that is gradient three important aspects must be taken into consideration that is
comfort, safety and lastly availability of an individual. Access to particular kind of database is
mainly provided to user when they require any kind of information. In many situations it is
observed that linkage between access and information generally fails and this does not allow
them to easily patch to have an access to it.
A large number of problems can be encountered in biometric so it focuses to be secure
and trustworthy in many situations (Lumini & Nanni, 2017). There are some kinds of issues
which are encountered in biometric that are rouge sensors and various kinds of unauthorized kind
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
of access, establishment of communication between different sensor, speed, cost and lastly issues
related to privacy.
Answer to Question 4
False negative can be defined as a situation in which a user cannot get access to location
of biometric (Mosenia & Jha, 2017). In many situations it is seen that although identity of person
is stored is the database but no kind of access is provided to him due to any kind of technical
fault. In many cases it is observed that false identity person gets identity which may result in
cases of miss identity. In the first case it is observed that identity of an individual in unknown
(Sagar et al., 2015). It may result in creation of issues and it can easily restrict an individual form
performing a large number of activities. In the second case it is observed that concept or identity
of a person is generally taken to be loss of identity of a person. Other person can easily make use
of identity and is mainly involved in some kind of legal activities. On personal level it is
observed that owner of a safe is prevented from using or accessing it (Onuchowska & de Vreede,
2018). On the level of institution, it is observed that entire infrastructure is shut down and the
organization needs to restore the various kinds of services. It may result in losing of thousands of
dollars for an organization along with reputation which is associated with it. In some of the cases
it is observed that a particular staff member of a firm has collapsed due to some disease like
cardiac arrest, at that particular time it is observed biometric system can fail to recognize another
person who reaching to that patient for help.
Biometric system is mainly used for having various kinds of notes regarding login and
logout time biometric are also used for authentication and validation. Biometric system is
considered to be useful for regarding analyzing the precise time of a person (Pagnin &
Mitrokotsa, 2017). In many cases it is seen that CCTV have failed to provide information
of access, establishment of communication between different sensor, speed, cost and lastly issues
related to privacy.
Answer to Question 4
False negative can be defined as a situation in which a user cannot get access to location
of biometric (Mosenia & Jha, 2017). In many situations it is seen that although identity of person
is stored is the database but no kind of access is provided to him due to any kind of technical
fault. In many cases it is observed that false identity person gets identity which may result in
cases of miss identity. In the first case it is observed that identity of an individual in unknown
(Sagar et al., 2015). It may result in creation of issues and it can easily restrict an individual form
performing a large number of activities. In the second case it is observed that concept or identity
of a person is generally taken to be loss of identity of a person. Other person can easily make use
of identity and is mainly involved in some kind of legal activities. On personal level it is
observed that owner of a safe is prevented from using or accessing it (Onuchowska & de Vreede,
2018). On the level of institution, it is observed that entire infrastructure is shut down and the
organization needs to restore the various kinds of services. It may result in losing of thousands of
dollars for an organization along with reputation which is associated with it. In some of the cases
it is observed that a particular staff member of a firm has collapsed due to some disease like
cardiac arrest, at that particular time it is observed biometric system can fail to recognize another
person who reaching to that patient for help.
Biometric system is mainly used for having various kinds of notes regarding login and
logout time biometric are also used for authentication and validation. Biometric system is
considered to be useful for regarding analyzing the precise time of a person (Pagnin &
Mitrokotsa, 2017). In many cases it is seen that CCTV have failed to provide information

8INFORMATION SECURITY
regarding the activities of a person like login and log out then biometric can be considered to be
effective for analyzing this particular situation (Russell & Chow, 2017).
Two common terms are encountered in biometric that is false matching or false no match.
FM and FNM are taken to new kind of terms in which match process is established by live
sample and biometric template. A false match is encountered in when the provided sample is
matched incorrectly with template with is provided to him (Qizi, 2015). On the contrary a false
negative occurs when a given sample is matched incorrectly with the template provided in the
database.
Answer to Question 5
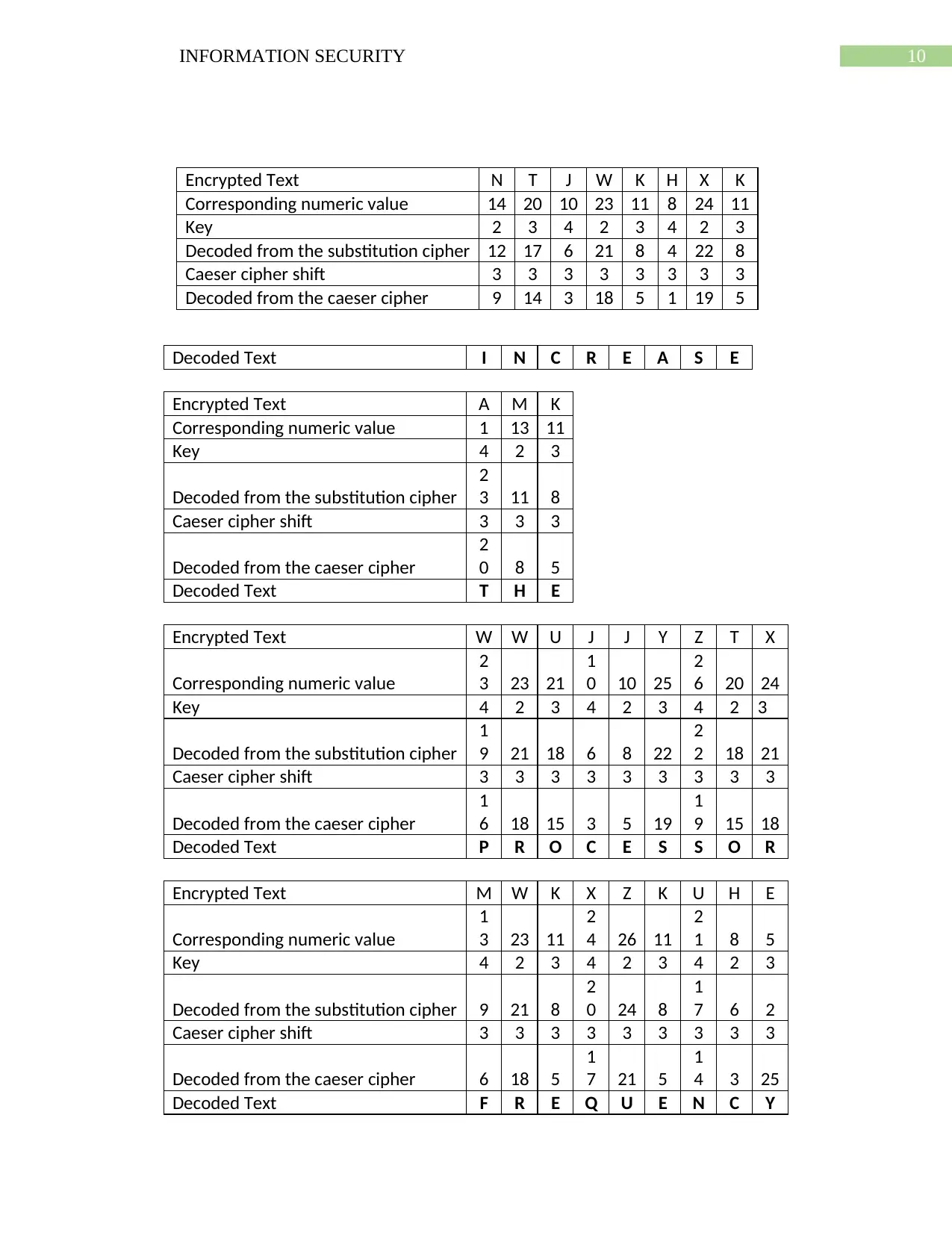
Transposition cipher works by arranging the various kinds of orders of a letter for hiding
the message which is being sent (Shubhangi et al., 2016). But in simple substitution of cipher
that is Caesar Cipher the letter of the message is switched around. In this technique, simple kind
of data encryption is mainly changed plain text character followed by some kind of regular
pattern for forming cipher text.
Substitution cipher are considered to be most common type of cipher. It mainly works by
replacing each letter of the plaintext with another kind of letter. A monoalphabetic substitution
cipher is known to be simple substitution cipher which totally depends on the structure. In this
method substitution is fixed for each and every letter of the alphabet (Wayman et al., 2015). For
example, if “a” is encrypted as “R” then every time we come across “a” in the plaintext we
replace it with letter “R” in the cipher text.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
regarding the activities of a person like login and log out then biometric can be considered to be
effective for analyzing this particular situation (Russell & Chow, 2017).
Two common terms are encountered in biometric that is false matching or false no match.
FM and FNM are taken to new kind of terms in which match process is established by live
sample and biometric template. A false match is encountered in when the provided sample is
matched incorrectly with template with is provided to him (Qizi, 2015). On the contrary a false
negative occurs when a given sample is matched incorrectly with the template provided in the
database.
Answer to Question 5
Transposition cipher works by arranging the various kinds of orders of a letter for hiding
the message which is being sent (Shubhangi et al., 2016). But in simple substitution of cipher
that is Caesar Cipher the letter of the message is switched around. In this technique, simple kind
of data encryption is mainly changed plain text character followed by some kind of regular
pattern for forming cipher text.
Substitution cipher are considered to be most common type of cipher. It mainly works by
replacing each letter of the plaintext with another kind of letter. A monoalphabetic substitution
cipher is known to be simple substitution cipher which totally depends on the structure. In this
method substitution is fixed for each and every letter of the alphabet (Wayman et al., 2015). For
example, if “a” is encrypted as “R” then every time we come across “a” in the plaintext we
replace it with letter “R” in the cipher text.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10INFORMATION SECURITY
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y

11INFORMATION SECURITY
So, the decoded text for the cypher text will be
“INCREASE THE PROCESSOR FREQUENCY”
References
Bakar, N. A., Aminallah, A., Ab Rahim, S. S., Zam, N. M., Rahman, S. A., & Veerayangkur, V.
(2018). EXAMINING THE RELATIONSHIP OF WEBSITE SECURITY, ONLINE
PERCEIVED VALUE AND ONLINE PURCHASE INTENTION: EVIDENCES FROM
MALAYSIA AND THAILAND ONLINE SHOPPING CONTEXT. Journal of
Fundamental and Applied Sciences, 10(6S), 1176-1191.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
Choi, H. S., Lee, B., & Yoon, S. (2016). Biometric authentication using noisy
electrocardiograms acquired by mobile sensors. IEEE Access, 4, 1266-1273.
Deokar, S. R., & Wakode, J. S. (2017). Coal Mine Safety Monitoring and Alerting System.
Dere, S. N., Gurjar, A. A., & Sipna, C. O. E. T. (2016). Human Identification Using Palm-Vein
Images: A New Trend in Biometrics. International Journal of Engineering Science, 2298.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the security
concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
So, the decoded text for the cypher text will be
“INCREASE THE PROCESSOR FREQUENCY”
References
Bakar, N. A., Aminallah, A., Ab Rahim, S. S., Zam, N. M., Rahman, S. A., & Veerayangkur, V.
(2018). EXAMINING THE RELATIONSHIP OF WEBSITE SECURITY, ONLINE
PERCEIVED VALUE AND ONLINE PURCHASE INTENTION: EVIDENCES FROM
MALAYSIA AND THAILAND ONLINE SHOPPING CONTEXT. Journal of
Fundamental and Applied Sciences, 10(6S), 1176-1191.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
Choi, H. S., Lee, B., & Yoon, S. (2016). Biometric authentication using noisy
electrocardiograms acquired by mobile sensors. IEEE Access, 4, 1266-1273.
Deokar, S. R., & Wakode, J. S. (2017). Coal Mine Safety Monitoring and Alerting System.
Dere, S. N., Gurjar, A. A., & Sipna, C. O. E. T. (2016). Human Identification Using Palm-Vein
Images: A New Trend in Biometrics. International Journal of Engineering Science, 2298.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the security
concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





