Security Issues in the Era of Big Data: ITC571 Annotated Bibliography
VerifiedAdded on 2020/03/16
|14
|3982
|303
Annotated Bibliography
AI Summary
This annotated bibliography, prepared for the ITC571 course at Charles Sturt University, explores the critical security issues associated with big data. The assignment begins with an introduction to big data, highlighting its importance and complexity, and then focuses on the domain problem, purpose, and justification of the research. It includes recommendations from the supervisor and a detailed literature review, examining various research articles related to big data security, including technological, organizational, and environmental aspects. The methodology section outlines the conceptual framework, research methodology, system development methodology, data collection methods, and ethical considerations. The project plan encompasses the work breakdown structure, analysis of risks, and a Gantt chart. The bibliography covers a range of sources, addressing topics such as privacy, security in Hadoop architecture, big data in SMEs, data visualization, coastal risk adaptation, MetaCloudDataStorage architecture, cloud-based big data security, and ethical considerations in health sectors. The assignment aims to provide a comprehensive overview of the security challenges and potential solutions in the era of big data.

Annotated Bibliography
Full Name VINITH REDDY KONDAPALLY
Student ID 11645930
Subject ITC571 – Emerging Technology and Innovations
Assignment No Annotated Bibliography
Due Date 08-09-2017
Lecturer’s Name Malka N. Halgamuge
Title:
SECURITY ISSUES IN THE ERA OF BIG DATA
Vinith reddy Kondapally
Vinithreddy.kondapally@gmail.com
School of Computing and Mathematics, Charles Sturt University, Melbourne,
Victoria
Full Name VINITH REDDY KONDAPALLY
Student ID 11645930
Subject ITC571 – Emerging Technology and Innovations
Assignment No Annotated Bibliography
Due Date 08-09-2017
Lecturer’s Name Malka N. Halgamuge
Title:
SECURITY ISSUES IN THE ERA OF BIG DATA
Vinith reddy Kondapally
Vinithreddy.kondapally@gmail.com
School of Computing and Mathematics, Charles Sturt University, Melbourne,
Victoria
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
1. Introduction.........................................................................................................................................3
Domain problem.....................................................................................................................................3
Purpose and justification.........................................................................................................................4
Recommendations of supervisor and sponsors........................................................................................4
Literature Review....................................................................................................................................4
Research questions..................................................................................................................................8
2. MATERIAL & METHODS................................................................................................................9
Conceptual framework............................................................................................................................9
Methodology...........................................................................................................................................9
System development methodology..........................................................................................................9
Data collection or design method..........................................................................................................10
Ethical issues.........................................................................................................................................10
Requirement of compliance...................................................................................................................10
Data analysis.........................................................................................................................................10
Project plan...........................................................................................................................................11
WBS......................................................................................................................................................11
Analysis of risks....................................................................................................................................11
Duration of project plan........................................................................................................................12
Gantt chart.............................................................................................................................................12
3. Results...............................................................................................................................................13
4. Discussion.........................................................................................................................................13
5. Conclusions.......................................................................................................................................13
6. References.........................................................................................................................................14
2
1. Introduction.........................................................................................................................................3
Domain problem.....................................................................................................................................3
Purpose and justification.........................................................................................................................4
Recommendations of supervisor and sponsors........................................................................................4
Literature Review....................................................................................................................................4
Research questions..................................................................................................................................8
2. MATERIAL & METHODS................................................................................................................9
Conceptual framework............................................................................................................................9
Methodology...........................................................................................................................................9
System development methodology..........................................................................................................9
Data collection or design method..........................................................................................................10
Ethical issues.........................................................................................................................................10
Requirement of compliance...................................................................................................................10
Data analysis.........................................................................................................................................10
Project plan...........................................................................................................................................11
WBS......................................................................................................................................................11
Analysis of risks....................................................................................................................................11
Duration of project plan........................................................................................................................12
Gantt chart.............................................................................................................................................12
3. Results...............................................................................................................................................13
4. Discussion.........................................................................................................................................13
5. Conclusions.......................................................................................................................................13
6. References.........................................................................................................................................14
2

1. INTRODUCTION
Section-1
Big data [1] is one of most large and complex structured and unstructured data sets which help to handle
and control the business in more convenient and semantic approach as day to day basis. It is not about the
complexity and volume of data as these are used to analyze the insights of business in systematic
approach to develop more effective strategies and decisions for enhancing the business functional
operations [2]. As, the data are collected from numerous sources so, it is automatically faces some
security and privacy issues regarding those data. Big data analysis [3][4] is one of most fundamental
approach to achieve the competitive advantage in recent time. But, in most of the cases there are many
security issues existed relating to big data, which include, gathered information from distributed, no
relational data storage, real time based data compliance and data from accessing point of end users etc.
This proposal will give proper description about the specific domain of business data and their related
security issues. To understand the research topic in more systematic and semantic approach, a suitable
rationale of problem of domain is given with proper justification and also focused on the recommendation
of supervisor and sponsors of those exact business domains [5]. To focus in the research topic, some
research objectives are given with suitable research questions which help to progress the research in
appropriate way to achieve exact suitable solutions. In the later section of this research, the research
methodology will be given to accomplish this research in semantic way and also focus on the data
collection methods to collect appropriate data for enhancing this research. At the end of the research,
project development plan will deliver with proper work break down structure, deliverables, project
durations and Gantt chart to accomplish this research.
Section 2
DOMAIN PROBLEM
In recent time, the market is living on era of big data. As increasing of social networks, social media and
Internet of Things are produced lots of diverse types of unstructured data which has directly and
indirectly affect to each and every type of business domains. Thus, every organization is likely to gather
those data and make it suitable to enhance the functional operations of business in more beneficial and
profitable approach by analyzing those gathered data from various sections [2]. To accomplish the
research, big data domain is basically selected to understand the security and privacy issues in more
3
Section-1
Big data [1] is one of most large and complex structured and unstructured data sets which help to handle
and control the business in more convenient and semantic approach as day to day basis. It is not about the
complexity and volume of data as these are used to analyze the insights of business in systematic
approach to develop more effective strategies and decisions for enhancing the business functional
operations [2]. As, the data are collected from numerous sources so, it is automatically faces some
security and privacy issues regarding those data. Big data analysis [3][4] is one of most fundamental
approach to achieve the competitive advantage in recent time. But, in most of the cases there are many
security issues existed relating to big data, which include, gathered information from distributed, no
relational data storage, real time based data compliance and data from accessing point of end users etc.
This proposal will give proper description about the specific domain of business data and their related
security issues. To understand the research topic in more systematic and semantic approach, a suitable
rationale of problem of domain is given with proper justification and also focused on the recommendation
of supervisor and sponsors of those exact business domains [5]. To focus in the research topic, some
research objectives are given with suitable research questions which help to progress the research in
appropriate way to achieve exact suitable solutions. In the later section of this research, the research
methodology will be given to accomplish this research in semantic way and also focus on the data
collection methods to collect appropriate data for enhancing this research. At the end of the research,
project development plan will deliver with proper work break down structure, deliverables, project
durations and Gantt chart to accomplish this research.
Section 2
DOMAIN PROBLEM
In recent time, the market is living on era of big data. As increasing of social networks, social media and
Internet of Things are produced lots of diverse types of unstructured data which has directly and
indirectly affect to each and every type of business domains. Thus, every organization is likely to gather
those data and make it suitable to enhance the functional operations of business in more beneficial and
profitable approach by analyzing those gathered data from various sections [2]. To accomplish the
research, big data domain is basically selected to understand the security and privacy issues in more
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

concentrated way. In recent time, social media, IOTs are most increasing and demanding culture among
organizations and customers as well. As, this big data domain is increasing rapidly, so it is huge problem
according to security issues relating big data. So, it is very important to understand the protection issues
of those big data.
Section 3
PURPOSE AND JUSTIFICATION
The purpose of this research is focus on security issues in era of big data[6]. Social media, social network
and Internet of things is rising a huge amount data in every data in various form. So, it is very important
to concentrate on this domain with more consciously as it has generated huge data flow in the business
sectors. Thus, the organization should provide more data security to these data and also the foundations
have to use those big data in protective approach. So, they have automatically faced lots of security issues
regarding this big data domain which are described in more appropriately in following research.
Section 4
RECOMMENDATIONS OF SUPERVISOR AND SPONSORS
To accomplish this research study, the supervisor requires developing proper budget plans and needs to
generate acute time table. And, the supervisor also needs to assure that all of collect data should be valid
and reliable. The supervisor should to develop appropriate WBS to accomplish this project in semantic
manner.
Section 5
LITERATURE REVIEW
Literature review is done by studying various books, journals and web articles. The following references
specified in annotated reference style are studied in details for the investigation of this research study.
Salleh, K.A. and Janczewski, L., 2016. Technological, organizational and environmental
security and privacy issues of big data: A literature review. Procedia Computer Science,
100, pp.19-28.
This research article is focused on the privacy and security issues related with big data. According to the
research paper, the security issues of big data are categorized into three various sections including,
environmental, organizational and technological. According to the technological context, both internal
4
organizations and customers as well. As, this big data domain is increasing rapidly, so it is huge problem
according to security issues relating big data. So, it is very important to understand the protection issues
of those big data.
Section 3
PURPOSE AND JUSTIFICATION
The purpose of this research is focus on security issues in era of big data[6]. Social media, social network
and Internet of things is rising a huge amount data in every data in various form. So, it is very important
to concentrate on this domain with more consciously as it has generated huge data flow in the business
sectors. Thus, the organization should provide more data security to these data and also the foundations
have to use those big data in protective approach. So, they have automatically faced lots of security issues
regarding this big data domain which are described in more appropriately in following research.
Section 4
RECOMMENDATIONS OF SUPERVISOR AND SPONSORS
To accomplish this research study, the supervisor requires developing proper budget plans and needs to
generate acute time table. And, the supervisor also needs to assure that all of collect data should be valid
and reliable. The supervisor should to develop appropriate WBS to accomplish this project in semantic
manner.
Section 5
LITERATURE REVIEW
Literature review is done by studying various books, journals and web articles. The following references
specified in annotated reference style are studied in details for the investigation of this research study.
Salleh, K.A. and Janczewski, L., 2016. Technological, organizational and environmental
security and privacy issues of big data: A literature review. Procedia Computer Science,
100, pp.19-28.
This research article is focused on the privacy and security issues related with big data. According to the
research paper, the security issues of big data are categorized into three various sections including,
environmental, organizational and technological. According to the technological context, both internal
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and external technologies are described related to security issues in era of big data and also gives some
recommendation to integrate the technology capabilities to overcome faced security issues. In the
organization context, the solutions are given to overcome from faced security issues and also policies and
strategies are provided. And, in environmental context, the security issues are described, those are
generated from transferring data among external shareholders or in case of dealing with government etc.
So, basically this article developed with aid of these three deliverables and give suitable information
about security issues with big data and their related solutions.
Saraladevi, B., Pazhaniraja, N., Paul, P.V., Basha, M.S. and Dhavachelvan, P., 2015. Big
Data and Hadoop-A study in security perspective. Procedia computer science, 50, pp.596-
601.
This research article basically gives proper information about big data security issues and it is mainly
focused on the raised security and privacy issues according to Hadoop Architecture. To understand this
Hadoop Distributed File system, some key characteristics are given including Name Node, Algorithm and
Kerberos. In this paper, the storage, management processing issues are described in more effective way
which helps to understand the security issues as basis of HDFS. To secure data in HDFS, Kerberos
mechanism, Bull Eye Algorithm approach and Name node approach are described briefly, those enhance
this research study more informative and semantic approach. So, basically this paper focused on real time
based security issues and their consequences.
Sen, D., Ozturk, M. and Vayvay, O., 2016. An Overview of Big Data for Growth in SMEs.
Procedia-Social and Behavioral Sciences, 235, pp.159-167.
This research article gives suitable description about the security issues related to era of big data
according to business operations of SMEs. The aim of this research study is to provide future scope of
accessibility and usability of big data in SMEs and their faced threats during functional operations.
According to this paper, SMEs are using these unstructured and data to give a profitable direction to
business but, in this case, they faces lots of security issues and they requires to overcome those issues to
develop a sustainable and potential future for organization. In this paper, there are some recommendations
are given to overcome from faced issues and improve the growth of SMEs.
Ruan, Z., Miao, Y., Pan, L., Patterson, N. and Zhang, J., 2017. Visualization for big data
security—A case study on KDD99 cup data set. Digital Communications and Networks.
5
recommendation to integrate the technology capabilities to overcome faced security issues. In the
organization context, the solutions are given to overcome from faced security issues and also policies and
strategies are provided. And, in environmental context, the security issues are described, those are
generated from transferring data among external shareholders or in case of dealing with government etc.
So, basically this article developed with aid of these three deliverables and give suitable information
about security issues with big data and their related solutions.
Saraladevi, B., Pazhaniraja, N., Paul, P.V., Basha, M.S. and Dhavachelvan, P., 2015. Big
Data and Hadoop-A study in security perspective. Procedia computer science, 50, pp.596-
601.
This research article basically gives proper information about big data security issues and it is mainly
focused on the raised security and privacy issues according to Hadoop Architecture. To understand this
Hadoop Distributed File system, some key characteristics are given including Name Node, Algorithm and
Kerberos. In this paper, the storage, management processing issues are described in more effective way
which helps to understand the security issues as basis of HDFS. To secure data in HDFS, Kerberos
mechanism, Bull Eye Algorithm approach and Name node approach are described briefly, those enhance
this research study more informative and semantic approach. So, basically this paper focused on real time
based security issues and their consequences.
Sen, D., Ozturk, M. and Vayvay, O., 2016. An Overview of Big Data for Growth in SMEs.
Procedia-Social and Behavioral Sciences, 235, pp.159-167.
This research article gives suitable description about the security issues related to era of big data
according to business operations of SMEs. The aim of this research study is to provide future scope of
accessibility and usability of big data in SMEs and their faced threats during functional operations.
According to this paper, SMEs are using these unstructured and data to give a profitable direction to
business but, in this case, they faces lots of security issues and they requires to overcome those issues to
develop a sustainable and potential future for organization. In this paper, there are some recommendations
are given to overcome from faced issues and improve the growth of SMEs.
Ruan, Z., Miao, Y., Pan, L., Patterson, N. and Zhang, J., 2017. Visualization for big data
security—A case study on KDD99 cup data set. Digital Communications and Networks.
5

This research article is given a depth review on KDD99 data set and visualized the security issues related
big data of this specific data set. As the research is progressing, some more data are taken such as, HybD,
KDDCUP99 to compare them with each other to gather security issues which help to solve the security
issues. In this paper, also system design is provided including, visualization algorithm to recommend
some potential solutions. Also, analysis are given in this paper which helps to identify the inter class
distinctness and inner class competences. So, as the basis of this visualization process, this research paper
is developed.
Rumson, A.G., Hallett, S.H. and Brewer, T.R., 2017. Coastal risk adaptation: the potential
role of accessible geospatial Big Data. Marine Policy, 83, pp.100-110.
This research is developed with aid of example of increasing population in coastal area. According to
previous collected data, it is noticed that, the population of coastal areas has to faced some environmental
threats such as, erosion, floods etc. so, the organizations of those areas have suffered due to loss of data
and security issues. So, those organization has adopted innovative data center like, cloud based data
storage to protect their data in more effective approach. So, they can collect all unstructured big data
where they require. At end of this research some security issue are also given, those are faced by
organizations and also given some recommendation to overcome from this situation.
Manogaran, G., Thota, C. and Kumar, M.V., 2016. MetaCloudDataStorage architecture
for Big Data security in cloud computing. Procedia Computer Science, 87, pp.128-133.
As the technology is improving, the cloud based big data security issue is one of biggest concern topic in
recent years. The purpose of this research is to identify the security issues in era of big data. According to
this research paper, the security issues are given related to big data and then, the potential solutions are
also described in cloud based system. This paper also gives a suitable overview of data security and the
solutions according based on some small medium size organizational operations. This research paper is
based MetaDataStorage architecture to give more protection to big data by overcoming faced issues in the
cloud based environment.
Fan, L., Strasser-Weippl, K., Li, J.J., St Louis, J., Finkelstein, D.M., Yu, K.D., Chen, W.Q.,
Shao, Z.M. and Goss, P.E., 2014. Breast cancer in China. The lancet oncology, 15(7),
pp.e279-e289.
This research is basically focus on security issues related big data during the massive data storage and
processing those data. According to this paper, the business operation is changing day by day and SMEs
and also MNCs are looking to use and analyze big data in more effective way to sustain their scope of
future. Most of foundations are doing their business in cloud based architecture. Though, scalability and
flexibility of big data is huge and profitable but, using this process organization has to face lots of security
6
big data of this specific data set. As the research is progressing, some more data are taken such as, HybD,
KDDCUP99 to compare them with each other to gather security issues which help to solve the security
issues. In this paper, also system design is provided including, visualization algorithm to recommend
some potential solutions. Also, analysis are given in this paper which helps to identify the inter class
distinctness and inner class competences. So, as the basis of this visualization process, this research paper
is developed.
Rumson, A.G., Hallett, S.H. and Brewer, T.R., 2017. Coastal risk adaptation: the potential
role of accessible geospatial Big Data. Marine Policy, 83, pp.100-110.
This research is developed with aid of example of increasing population in coastal area. According to
previous collected data, it is noticed that, the population of coastal areas has to faced some environmental
threats such as, erosion, floods etc. so, the organizations of those areas have suffered due to loss of data
and security issues. So, those organization has adopted innovative data center like, cloud based data
storage to protect their data in more effective approach. So, they can collect all unstructured big data
where they require. At end of this research some security issue are also given, those are faced by
organizations and also given some recommendation to overcome from this situation.
Manogaran, G., Thota, C. and Kumar, M.V., 2016. MetaCloudDataStorage architecture
for Big Data security in cloud computing. Procedia Computer Science, 87, pp.128-133.
As the technology is improving, the cloud based big data security issue is one of biggest concern topic in
recent years. The purpose of this research is to identify the security issues in era of big data. According to
this research paper, the security issues are given related to big data and then, the potential solutions are
also described in cloud based system. This paper also gives a suitable overview of data security and the
solutions according based on some small medium size organizational operations. This research paper is
based MetaDataStorage architecture to give more protection to big data by overcoming faced issues in the
cloud based environment.
Fan, L., Strasser-Weippl, K., Li, J.J., St Louis, J., Finkelstein, D.M., Yu, K.D., Chen, W.Q.,
Shao, Z.M. and Goss, P.E., 2014. Breast cancer in China. The lancet oncology, 15(7),
pp.e279-e289.
This research is basically focus on security issues related big data during the massive data storage and
processing those data. According to this paper, the business operation is changing day by day and SMEs
and also MNCs are looking to use and analyze big data in more effective way to sustain their scope of
future. Most of foundations are doing their business in cloud based architecture. Though, scalability and
flexibility of big data is huge and profitable but, using this process organization has to face lots of security
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

and privacy issues. So, in this research study, some recommendations are given, those enhance the
business operational functionality related security issues of big data.
Knoppers, B.M. and Thorogood, A.M., 2017. Ethics and Big Data in Health. Current
Opinion in Systems Biology.
This research paper is developed on topic of security issues related to big data in health sectors.
According this research, the administration of health care center has face lots of security issues during
using the big data. In this domain, big data analyzing is so important to enhance the health care system in
more effective approach. Thus, in this research paper, some ethical rule and regulations are given to use
those big data related with health care to overcome the security issues. In this paper, also some
recommendation are given such as, increasing of HDFS for protecting big data in more systematic and
semantic manner.
Everett, C., 2015. Big data–the future of cyber-security or its latest threat?. Computer
Fraud & Security, 2015(9), pp.14-17.
The fundamental aim of this research is to focus on future scope of big data and their faced security
issues. In the beginning section of this paper, definition of big data is given and then importance and
impact of big data on current business market is described briefly. As, the research is progression, the
researcher focuses one secondary data which makes this paper more informative and relevant as
connecting with this information with research objectives. After that, secondary analysis has done to
gather an appropriate conclusion about security issues related to big data. At the end of the research
article some recommendations and solutions are given, those will be considered as helpful to overcome
security issues related with big data.
Mounia, B. and Habiba, C., 2015. Big Data Privacy in Healthcare Moroccan Context.
Procedia Computer Science, 63, pp.575-580.
This research article is based on security issue related to big data. The market is globalizing as well as
health industry is improving. According to this research, it is noticed that, to enhance the health care
system in more effective approach, big data analysis is one of most emerging and trendy practice. So, it is
important to use the big data in more ethical way to overcome the security issues related with big data.
According to this research article, the health care center has adopted more advanced technology to
overcome security issues by adopting cloud based architecture and HDFS.
Vennila, S. and Priyadarshini, J., 2015. Scalable Privacy Preservation in Big Data a
Survey. Procedia Computer Science, 50, pp.369-373.
7
business operational functionality related security issues of big data.
Knoppers, B.M. and Thorogood, A.M., 2017. Ethics and Big Data in Health. Current
Opinion in Systems Biology.
This research paper is developed on topic of security issues related to big data in health sectors.
According this research, the administration of health care center has face lots of security issues during
using the big data. In this domain, big data analyzing is so important to enhance the health care system in
more effective approach. Thus, in this research paper, some ethical rule and regulations are given to use
those big data related with health care to overcome the security issues. In this paper, also some
recommendation are given such as, increasing of HDFS for protecting big data in more systematic and
semantic manner.
Everett, C., 2015. Big data–the future of cyber-security or its latest threat?. Computer
Fraud & Security, 2015(9), pp.14-17.
The fundamental aim of this research is to focus on future scope of big data and their faced security
issues. In the beginning section of this paper, definition of big data is given and then importance and
impact of big data on current business market is described briefly. As, the research is progression, the
researcher focuses one secondary data which makes this paper more informative and relevant as
connecting with this information with research objectives. After that, secondary analysis has done to
gather an appropriate conclusion about security issues related to big data. At the end of the research
article some recommendations and solutions are given, those will be considered as helpful to overcome
security issues related with big data.
Mounia, B. and Habiba, C., 2015. Big Data Privacy in Healthcare Moroccan Context.
Procedia Computer Science, 63, pp.575-580.
This research article is based on security issue related to big data. The market is globalizing as well as
health industry is improving. According to this research, it is noticed that, to enhance the health care
system in more effective approach, big data analysis is one of most emerging and trendy practice. So, it is
important to use the big data in more ethical way to overcome the security issues related with big data.
According to this research article, the health care center has adopted more advanced technology to
overcome security issues by adopting cloud based architecture and HDFS.
Vennila, S. and Priyadarshini, J., 2015. Scalable Privacy Preservation in Big Data a
Survey. Procedia Computer Science, 50, pp.369-373.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In this research study, the difference between survey and big data analysis is described in descriptive way.
In the first section of article, the concept of survey and big data is given and then, their differences are
elaborated. After that, security issues are given respectively and advantages are also described in more
detailed. As the research is progressing, the researcher focuses on security issues related to big data and
gives some recommendation to overcome from these faced issues. In this comparative research paper,
also some recommendation are given such as, researcher has recommended to analyze the big data on
HDFS architecture to reduce the security issues related to big data domain.
Bao, H. and Chen, L., 2016. A lightweight privacy‐preserving scheme with data integrity
for smart grid communications. Concurrency and Computation: Practice and Experience,
28(4), pp.1094-1110.
In smart grid, huge of big data is analyzed to enhance the business culture. This research study mainly
focuses on security issues related to big data. This paper describes the security issues as the basis of
organizational and technology context. According to this paper, it is cleared that, HDFS is very good
options to use big data in more convenient way although, there are some problems and security issues are
still existed related to big data. At the end of this research paper, some recommendations and solutions are
given, those are considered as helpful approach to enhance this big data analysis process.
Section 6
RESEARCH QUESTIONS
This research question is developed on the basis of research aims and research objectives and those
research question will help to understand the research topic in more convenient approach.
What is the concept of big data?
What are the security issues related to big data?
What are the impact of security issues related to big data?
What are methodologies, techniques are used to solve the security issues related to big data?
8
In the first section of article, the concept of survey and big data is given and then, their differences are
elaborated. After that, security issues are given respectively and advantages are also described in more
detailed. As the research is progressing, the researcher focuses on security issues related to big data and
gives some recommendation to overcome from these faced issues. In this comparative research paper,
also some recommendation are given such as, researcher has recommended to analyze the big data on
HDFS architecture to reduce the security issues related to big data domain.
Bao, H. and Chen, L., 2016. A lightweight privacy‐preserving scheme with data integrity
for smart grid communications. Concurrency and Computation: Practice and Experience,
28(4), pp.1094-1110.
In smart grid, huge of big data is analyzed to enhance the business culture. This research study mainly
focuses on security issues related to big data. This paper describes the security issues as the basis of
organizational and technology context. According to this paper, it is cleared that, HDFS is very good
options to use big data in more convenient way although, there are some problems and security issues are
still existed related to big data. At the end of this research paper, some recommendations and solutions are
given, those are considered as helpful approach to enhance this big data analysis process.
Section 6
RESEARCH QUESTIONS
This research question is developed on the basis of research aims and research objectives and those
research question will help to understand the research topic in more convenient approach.
What is the concept of big data?
What are the security issues related to big data?
What are the impact of security issues related to big data?
What are methodologies, techniques are used to solve the security issues related to big data?
8
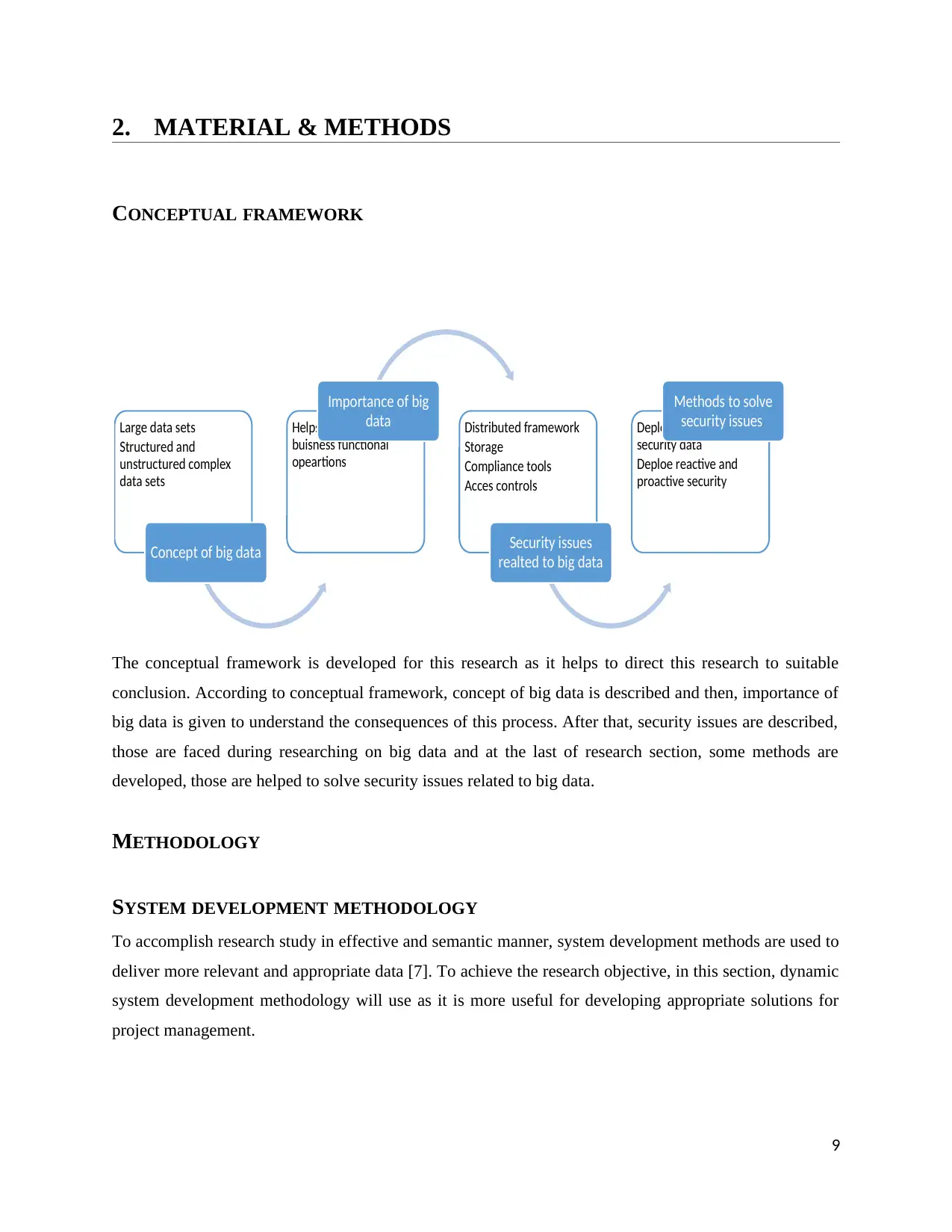
2. MATERIAL & METHODS
CONCEPTUAL FRAMEWORK
The conceptual framework is developed for this research as it helps to direct this research to suitable
conclusion. According to conceptual framework, concept of big data is described and then, importance of
big data is given to understand the consequences of this process. After that, security issues are described,
those are faced during researching on big data and at the last of research section, some methods are
developed, those are helped to solve security issues related to big data.
METHODOLOGY
SYSTEM DEVELOPMENT METHODOLOGY
To accomplish research study in effective and semantic manner, system development methods are used to
deliver more relevant and appropriate data [7]. To achieve the research objective, in this section, dynamic
system development methodology will use as it is more useful for developing appropriate solutions for
project management.
9
Large data sets
Structured and
unstructured complex
data sets
Concept of big data
Helps to improve the
buisness functional
opeartions
Importance of big
data Distributed framework
Storage
Compliance tools
Acces controls
Security issues
realted to big data
Deploy real time based
security data
Deploe reactive and
proactive security
Methods to solve
security issues
CONCEPTUAL FRAMEWORK
The conceptual framework is developed for this research as it helps to direct this research to suitable
conclusion. According to conceptual framework, concept of big data is described and then, importance of
big data is given to understand the consequences of this process. After that, security issues are described,
those are faced during researching on big data and at the last of research section, some methods are
developed, those are helped to solve security issues related to big data.
METHODOLOGY
SYSTEM DEVELOPMENT METHODOLOGY
To accomplish research study in effective and semantic manner, system development methods are used to
deliver more relevant and appropriate data [7]. To achieve the research objective, in this section, dynamic
system development methodology will use as it is more useful for developing appropriate solutions for
project management.
9
Large data sets
Structured and
unstructured complex
data sets
Concept of big data
Helps to improve the
buisness functional
opeartions
Importance of big
data Distributed framework
Storage
Compliance tools
Acces controls
Security issues
realted to big data
Deploy real time based
security data
Deploe reactive and
proactive security
Methods to solve
security issues
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

DATA COLLECTION OR DESIGN METHOD
To accomplish this research study [8], secondary will be collected as it is most appropriate to give
suitable information regarding security issues related era of big data. For this research, exploratory
research design is chosen as, it will help to explore the secondary information in more systematic
approach which helps to connect this research study with defined research objectives. The secondary data
are generally collected from books, journals and articles respectively.
ETHICAL ISSUES
According to Data Protection Act 1998, the data collecting process should be done in authentic approach
and it should be kept it mind that all data should be selected from valid, authenticate and reliable sources
to accomplish this research study [8]. It is very important that, the data should be valid and reliable.
REQUIREMENT OF COMPLIANCE
To solve the security issues, the higher authority should accept some innovative technologies which helps
to improve this system in more effective way. And, the higher authority needs to take some specific rules
and regulations such as, The Privacy Act,1983 and Federal Data Protection Act,2001.
DATA ANALYSIS
To accomplish this project, secondary data analysis process is used. With this secondary data analysis
process, it is helpful to connect the research study with research objectives in more effective manners. So,
secondary data analysis process is very important for this research study.
10
To accomplish this research study [8], secondary will be collected as it is most appropriate to give
suitable information regarding security issues related era of big data. For this research, exploratory
research design is chosen as, it will help to explore the secondary information in more systematic
approach which helps to connect this research study with defined research objectives. The secondary data
are generally collected from books, journals and articles respectively.
ETHICAL ISSUES
According to Data Protection Act 1998, the data collecting process should be done in authentic approach
and it should be kept it mind that all data should be selected from valid, authenticate and reliable sources
to accomplish this research study [8]. It is very important that, the data should be valid and reliable.
REQUIREMENT OF COMPLIANCE
To solve the security issues, the higher authority should accept some innovative technologies which helps
to improve this system in more effective way. And, the higher authority needs to take some specific rules
and regulations such as, The Privacy Act,1983 and Federal Data Protection Act,2001.
DATA ANALYSIS
To accomplish this project, secondary data analysis process is used. With this secondary data analysis
process, it is helpful to connect the research study with research objectives in more effective manners. So,
secondary data analysis process is very important for this research study.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
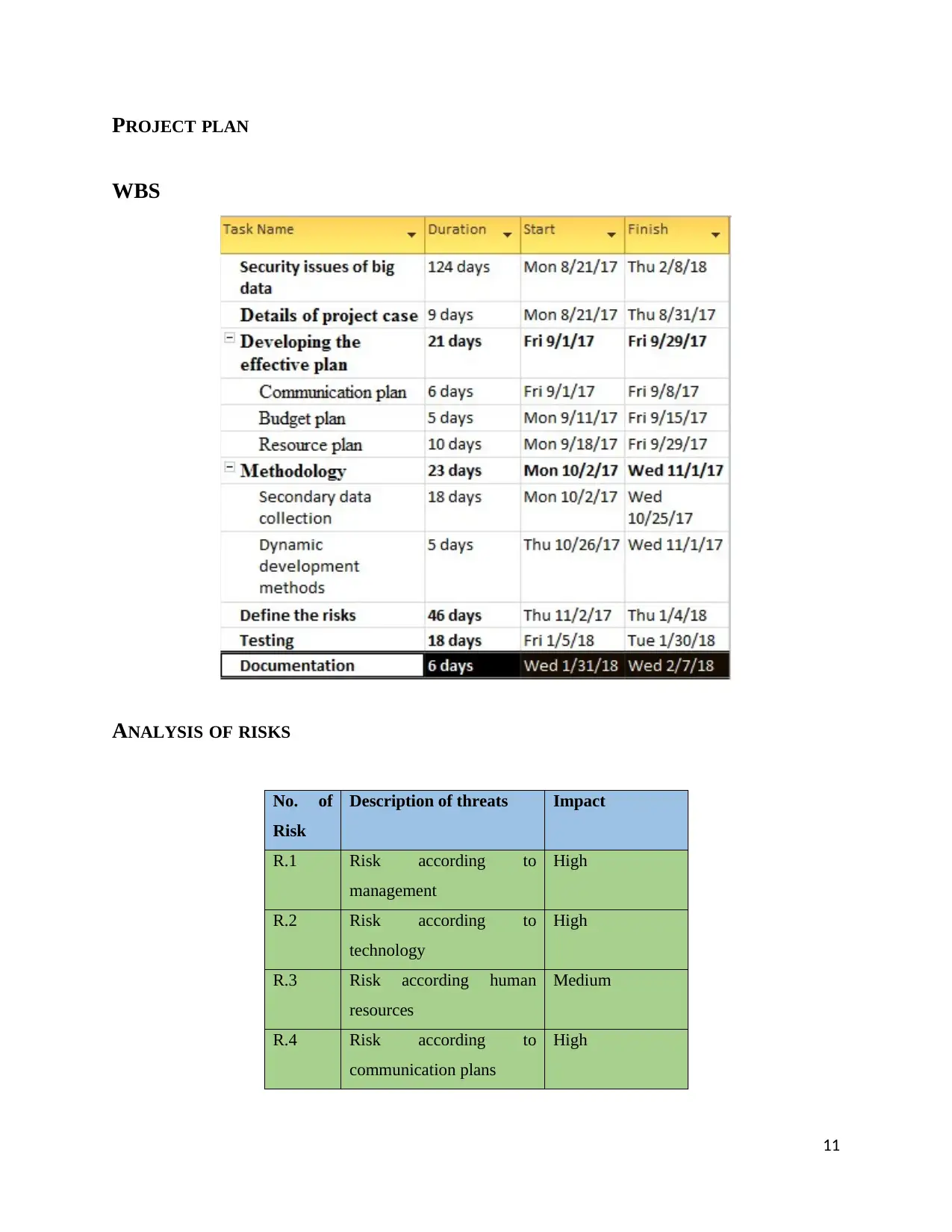
PROJECT PLAN
WBS
ANALYSIS OF RISKS
No. of
Risk
Description of threats Impact
R.1 Risk according to
management
High
R.2 Risk according to
technology
High
R.3 Risk according human
resources
Medium
R.4 Risk according to
communication plans
High
11
WBS
ANALYSIS OF RISKS
No. of
Risk
Description of threats Impact
R.1 Risk according to
management
High
R.2 Risk according to
technology
High
R.3 Risk according human
resources
Medium
R.4 Risk according to
communication plans
High
11
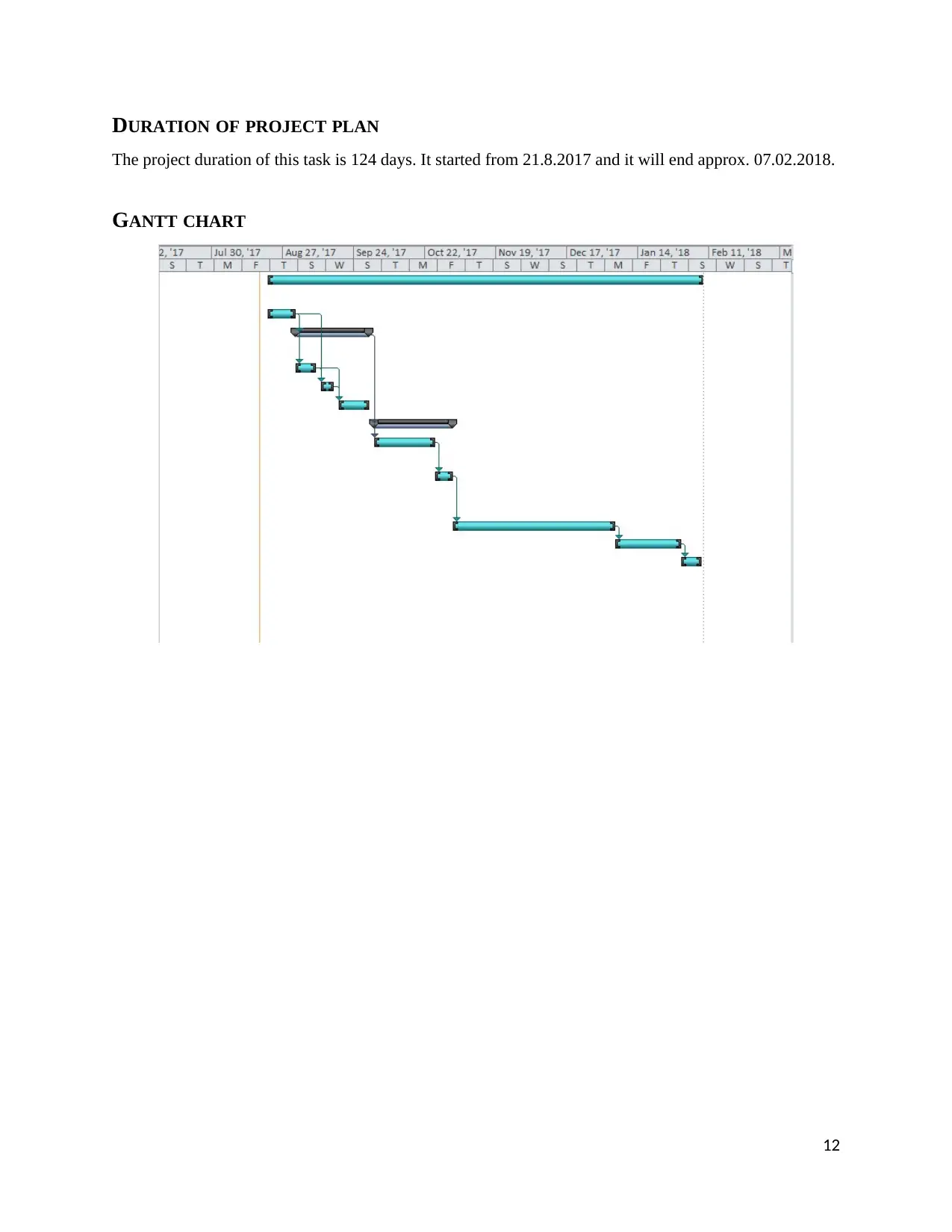
DURATION OF PROJECT PLAN
The project duration of this task is 124 days. It started from 21.8.2017 and it will end approx. 07.02.2018.
GANTT CHART
12
The project duration of this task is 124 days. It started from 21.8.2017 and it will end approx. 07.02.2018.
GANTT CHART
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





