Security Management and Governance
VerifiedAdded on 2023/01/23
|15
|3064
|45
AI Summary
This document discusses the benefits of a risk management plan and the steps to build one. It emphasizes the importance of contingency planning to PIA and includes a discussion on risk analysis and cost-benefit analysis. It also lists the threats, vulnerabilities, and attacks that a formal plan would manage. The document focuses on security management and governance.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

SECURITY MANAGEMENT AND GOVERNANCE 1
RISK MANAGEMENT
Name of the student:
Name of the university:
Student’s ID:
RISK MANAGEMENT
Name of the student:
Name of the university:
Student’s ID:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

SECURITY MANAGEMENT AND GOVERNANCE 2
Executive summary:
Risk management is part of every business plan in order to achieve success. In order to
achieve success most of the company have maintained a particular management strategy.
This kind of management strategy is very much effective to prevent any kind of accidental
risk in their company.
Executive summary:
Risk management is part of every business plan in order to achieve success. In order to
achieve success most of the company have maintained a particular management strategy.
This kind of management strategy is very much effective to prevent any kind of accidental
risk in their company.

SECURITY MANAGEMENT AND GOVERNANCE 3
Table of Contents
Briefly explain the benefits a Risk Management Plan can bring to a company and the steps
necessary to build one. Include a discussion on the importance of Contingency Planning to
PIA, as well as the risk analysis and CBA mentioned above.....................................................4
Contingency planning to PIA:................................................................................................5
Risk analysis:..........................................................................................................................5
Cost benefits analysis:............................................................................................................6
For the Patient Information area, list the threats, vulnerabilities, and attacks that your formal
plan would manage. This should not be an exhaustive, detailed list. Keep the focus on PIA’s
context........................................................................................................................................6
Work on this aspect and draw up a Risk Management Plan for it and include a
recommendation based on a Cost-Benefit Analysis...................................................................8
Where does the responsibility for the user and the vendor begin?..........................................10
Reference:................................................................................................................................12
Table of Contents
Briefly explain the benefits a Risk Management Plan can bring to a company and the steps
necessary to build one. Include a discussion on the importance of Contingency Planning to
PIA, as well as the risk analysis and CBA mentioned above.....................................................4
Contingency planning to PIA:................................................................................................5
Risk analysis:..........................................................................................................................5
Cost benefits analysis:............................................................................................................6
For the Patient Information area, list the threats, vulnerabilities, and attacks that your formal
plan would manage. This should not be an exhaustive, detailed list. Keep the focus on PIA’s
context........................................................................................................................................6
Work on this aspect and draw up a Risk Management Plan for it and include a
recommendation based on a Cost-Benefit Analysis...................................................................8
Where does the responsibility for the user and the vendor begin?..........................................10
Reference:................................................................................................................................12

SECURITY MANAGEMENT AND GOVERNANCE 4
Part- B
Briefly explain the benefits a Risk Management Plan can bring to a
company and the steps necessary to build one. Include a discussion on the
importance of Contingency Planning to PIA, as well as the risk analysis
and CBA mentioned above
A company’s risk management team follow and analyze different possible risks to prevent
and solve the upcoming risk of any company. Sometimes they categorize the risk in a
probabilistic approach that is very effective for the company. That means if it has a greater
chance to occur then definitely the risk management team of the company will monitor it
closely, work upon it and find possible solutions to reduce the risk as soon as possible. The
company PAI is one of the most reputed artificial intelligence companies in our country
which offers power service to our country (Marin et al. 2019). This company not only
offering power it generates and stores power for future use. It also offers various security
services to the customers. In the case of the security management system there are some
benefits which this company offers a follows:
As this company deals with high-level technical parameters and artificial intelligence,
with the help of the software they offer, that can protect any sort of confidential data.
Any kind of marketing and business oriented data also can be protected with the help
of this security software.
They have their own framework with the help of this the security services are always
been protected, upgrades and secured as well.
Cyber attack is a very common problem in most of the information and technological
companies. As we discussed above PAI has their own framework thus with the help
of that programs they can prevent this kind of complexities and problematic scenarios.
Part- B
Briefly explain the benefits a Risk Management Plan can bring to a
company and the steps necessary to build one. Include a discussion on the
importance of Contingency Planning to PIA, as well as the risk analysis
and CBA mentioned above
A company’s risk management team follow and analyze different possible risks to prevent
and solve the upcoming risk of any company. Sometimes they categorize the risk in a
probabilistic approach that is very effective for the company. That means if it has a greater
chance to occur then definitely the risk management team of the company will monitor it
closely, work upon it and find possible solutions to reduce the risk as soon as possible. The
company PAI is one of the most reputed artificial intelligence companies in our country
which offers power service to our country (Marin et al. 2019). This company not only
offering power it generates and stores power for future use. It also offers various security
services to the customers. In the case of the security management system there are some
benefits which this company offers a follows:
As this company deals with high-level technical parameters and artificial intelligence,
with the help of the software they offer, that can protect any sort of confidential data.
Any kind of marketing and business oriented data also can be protected with the help
of this security software.
They have their own framework with the help of this the security services are always
been protected, upgrades and secured as well.
Cyber attack is a very common problem in most of the information and technological
companies. As we discussed above PAI has their own framework thus with the help
of that programs they can prevent this kind of complexities and problematic scenarios.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

SECURITY MANAGEMENT AND GOVERNANCE 5
Contingency planning to PIA:
According to PIA contingency planning, this company must secure their intellectual
and technical properties as well. A contingency plan is to operate the ability of the
organisation adversely. In case of the business and marketing scenario with the help
of this contingency plan organisation not only can protect the resources also decreases
the inconveniences of the customers, identifies the acute problems and recovers it as
well. There are some key features to develop the contingency plan as follows:
With the help of this planning, the organisation can set its goal to achieve its primitive
operations.
With the help of this contingency planning organisation can develop brief strategic
planning to every department of this organisation.
With the help of this planning, process company can identify what are those key areas
where an organisation need to focus on their further benefits.
Risk analysis:
To analyse the original risk of this artificial intelligence industry it is very important
to do the actual framework in risk management.
Contingency planning to PIA:
According to PIA contingency planning, this company must secure their intellectual
and technical properties as well. A contingency plan is to operate the ability of the
organisation adversely. In case of the business and marketing scenario with the help
of this contingency plan organisation not only can protect the resources also decreases
the inconveniences of the customers, identifies the acute problems and recovers it as
well. There are some key features to develop the contingency plan as follows:
With the help of this planning, the organisation can set its goal to achieve its primitive
operations.
With the help of this contingency planning organisation can develop brief strategic
planning to every department of this organisation.
With the help of this planning, process company can identify what are those key areas
where an organisation need to focus on their further benefits.
Risk analysis:
To analyse the original risk of this artificial intelligence industry it is very important
to do the actual framework in risk management.

SECURITY MANAGEMENT AND GOVERNANCE 6
Cost benefits analysis:
With the help o, this analysis company can understand their financial position and
their capital strength.
Direct capitals or costs will be applied in the new programs, types of
equipment and software etc.
Direct company capitals are also invested in legal services as well.
The indirect capitals or costs will actually be invested in the stock and share
market.
For the Patient Information area, list the threats, vulnerabilities, and
attacks that your formal plan would manage. This should not be an
exhaustive, detailed list. Keep the focus on PIA’s context
In this company PAI the primary asset of this company is the employees, who are greatly
experienced and skilful in case of the IT and software. There are almost more than 45
efficient employees are working who have profound knowledge in cloud computing,
designing, software testing, data modelling (Moser et al. 2018). Those are all about technical
parameters. There are some employees are present as well who are very much skilled in
human resource management and business planning. For preventing the risk factor human
resource employees play a pivotal role. A company must have some financial expertise to
handle their companies’ financial state. So as this company also have some senior finance
managers. This company provide some excellent quality of staffing, planning, directing and
controlling the information.
Cost benefits analysis:
With the help o, this analysis company can understand their financial position and
their capital strength.
Direct capitals or costs will be applied in the new programs, types of
equipment and software etc.
Direct company capitals are also invested in legal services as well.
The indirect capitals or costs will actually be invested in the stock and share
market.
For the Patient Information area, list the threats, vulnerabilities, and
attacks that your formal plan would manage. This should not be an
exhaustive, detailed list. Keep the focus on PIA’s context
In this company PAI the primary asset of this company is the employees, who are greatly
experienced and skilful in case of the IT and software. There are almost more than 45
efficient employees are working who have profound knowledge in cloud computing,
designing, software testing, data modelling (Moser et al. 2018). Those are all about technical
parameters. There are some employees are present as well who are very much skilled in
human resource management and business planning. For preventing the risk factor human
resource employees play a pivotal role. A company must have some financial expertise to
handle their companies’ financial state. So as this company also have some senior finance
managers. This company provide some excellent quality of staffing, planning, directing and
controlling the information.

SECURITY MANAGEMENT AND GOVERNANCE 7
As the company PAI offers artificial intelligence they also some technical boundaries as well
(Pearson-Stuttard et al. 2018). This company now has become a quite reputed e-commerce
portal thus they have confronted some of the threats nowadays which is considered as the risk
of their business as well. Some of those potential risks are as follows:
Nowadays hacking has become a trend among the young generations. In the other
hand most of the scammers now trying to do hacking mostly in e-commerce portal.
With the help of this hacking process, they can steal an immense amount of money.
There are several infamous hacking techniques present which are phishing, scanning,
sniffing etc. In the case of phishing, hackers are hacking the e-commerce portal via
emails. With the help of this scam email, they can access all the personalized data,
account information and passwords as well. In the case of sniffing hackers send a
program file via the internet and with the help of this, they can access all the
personalized data of the portal user.
Apart from the technical risk, there are some kinds of business risk as well. Some of
those risks are where some employees are present who have the least technical
knowledge. Their less knowledge and experience might cause a huge risk for this
company's future.
The working environment is also a major cause of risk for this company.
Week business strategy and lack of Providence also a cause of the risk of this
company.
The financial state is also a major cause of risk for a company.
In order to PIA contingency plan, the primary risk for this company is the to
maintaining, testing and developing the planning. In such cases, the communication
between the leaders and their employees is not that much deep. This scenario is not
acceptable for an organisation which is planning to expand its area and its profits.
As the company PAI offers artificial intelligence they also some technical boundaries as well
(Pearson-Stuttard et al. 2018). This company now has become a quite reputed e-commerce
portal thus they have confronted some of the threats nowadays which is considered as the risk
of their business as well. Some of those potential risks are as follows:
Nowadays hacking has become a trend among the young generations. In the other
hand most of the scammers now trying to do hacking mostly in e-commerce portal.
With the help of this hacking process, they can steal an immense amount of money.
There are several infamous hacking techniques present which are phishing, scanning,
sniffing etc. In the case of phishing, hackers are hacking the e-commerce portal via
emails. With the help of this scam email, they can access all the personalized data,
account information and passwords as well. In the case of sniffing hackers send a
program file via the internet and with the help of this, they can access all the
personalized data of the portal user.
Apart from the technical risk, there are some kinds of business risk as well. Some of
those risks are where some employees are present who have the least technical
knowledge. Their less knowledge and experience might cause a huge risk for this
company's future.
The working environment is also a major cause of risk for this company.
Week business strategy and lack of Providence also a cause of the risk of this
company.
The financial state is also a major cause of risk for a company.
In order to PIA contingency plan, the primary risk for this company is the to
maintaining, testing and developing the planning. In such cases, the communication
between the leaders and their employees is not that much deep. This scenario is not
acceptable for an organisation which is planning to expand its area and its profits.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
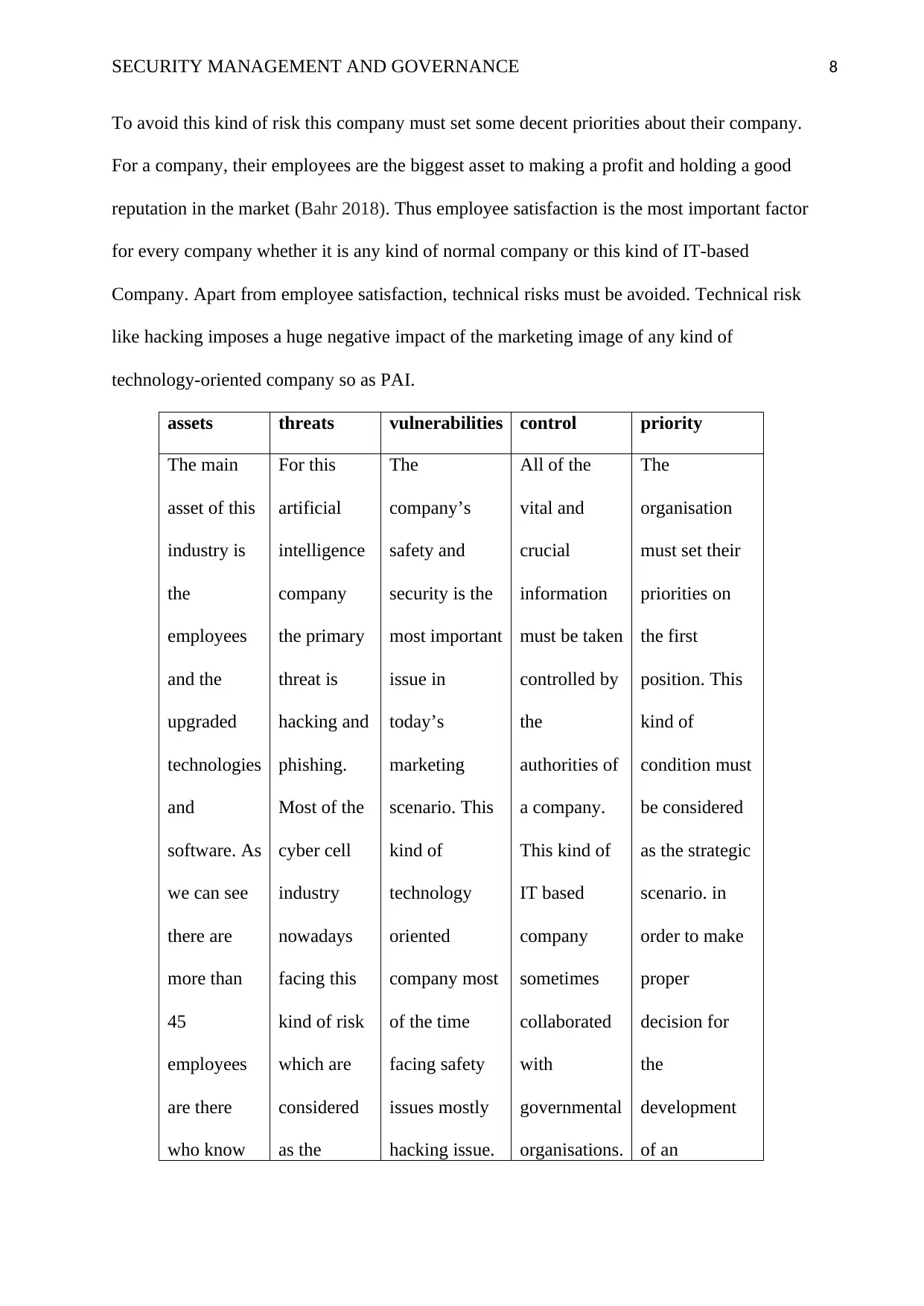
SECURITY MANAGEMENT AND GOVERNANCE 8
To avoid this kind of risk this company must set some decent priorities about their company.
For a company, their employees are the biggest asset to making a profit and holding a good
reputation in the market (Bahr 2018). Thus employee satisfaction is the most important factor
for every company whether it is any kind of normal company or this kind of IT-based
Company. Apart from employee satisfaction, technical risks must be avoided. Technical risk
like hacking imposes a huge negative impact of the marketing image of any kind of
technology-oriented company so as PAI.
assets threats vulnerabilities control priority
The main
asset of this
industry is
the
employees
and the
upgraded
technologies
and
software. As
we can see
there are
more than
45
employees
are there
who know
For this
artificial
intelligence
company
the primary
threat is
hacking and
phishing.
Most of the
cyber cell
industry
nowadays
facing this
kind of risk
which are
considered
as the
The
company’s
safety and
security is the
most important
issue in
today’s
marketing
scenario. This
kind of
technology
oriented
company most
of the time
facing safety
issues mostly
hacking issue.
All of the
vital and
crucial
information
must be taken
controlled by
the
authorities of
a company.
This kind of
IT based
company
sometimes
collaborated
with
governmental
organisations.
The
organisation
must set their
priorities on
the first
position. This
kind of
condition must
be considered
as the strategic
scenario. in
order to make
proper
decision for
the
development
of an
To avoid this kind of risk this company must set some decent priorities about their company.
For a company, their employees are the biggest asset to making a profit and holding a good
reputation in the market (Bahr 2018). Thus employee satisfaction is the most important factor
for every company whether it is any kind of normal company or this kind of IT-based
Company. Apart from employee satisfaction, technical risks must be avoided. Technical risk
like hacking imposes a huge negative impact of the marketing image of any kind of
technology-oriented company so as PAI.
assets threats vulnerabilities control priority
The main
asset of this
industry is
the
employees
and the
upgraded
technologies
and
software. As
we can see
there are
more than
45
employees
are there
who know
For this
artificial
intelligence
company
the primary
threat is
hacking and
phishing.
Most of the
cyber cell
industry
nowadays
facing this
kind of risk
which are
considered
as the
The
company’s
safety and
security is the
most important
issue in
today’s
marketing
scenario. This
kind of
technology
oriented
company most
of the time
facing safety
issues mostly
hacking issue.
All of the
vital and
crucial
information
must be taken
controlled by
the
authorities of
a company.
This kind of
IT based
company
sometimes
collaborated
with
governmental
organisations.
The
organisation
must set their
priorities on
the first
position. This
kind of
condition must
be considered
as the strategic
scenario. in
order to make
proper
decision for
the
development
of an
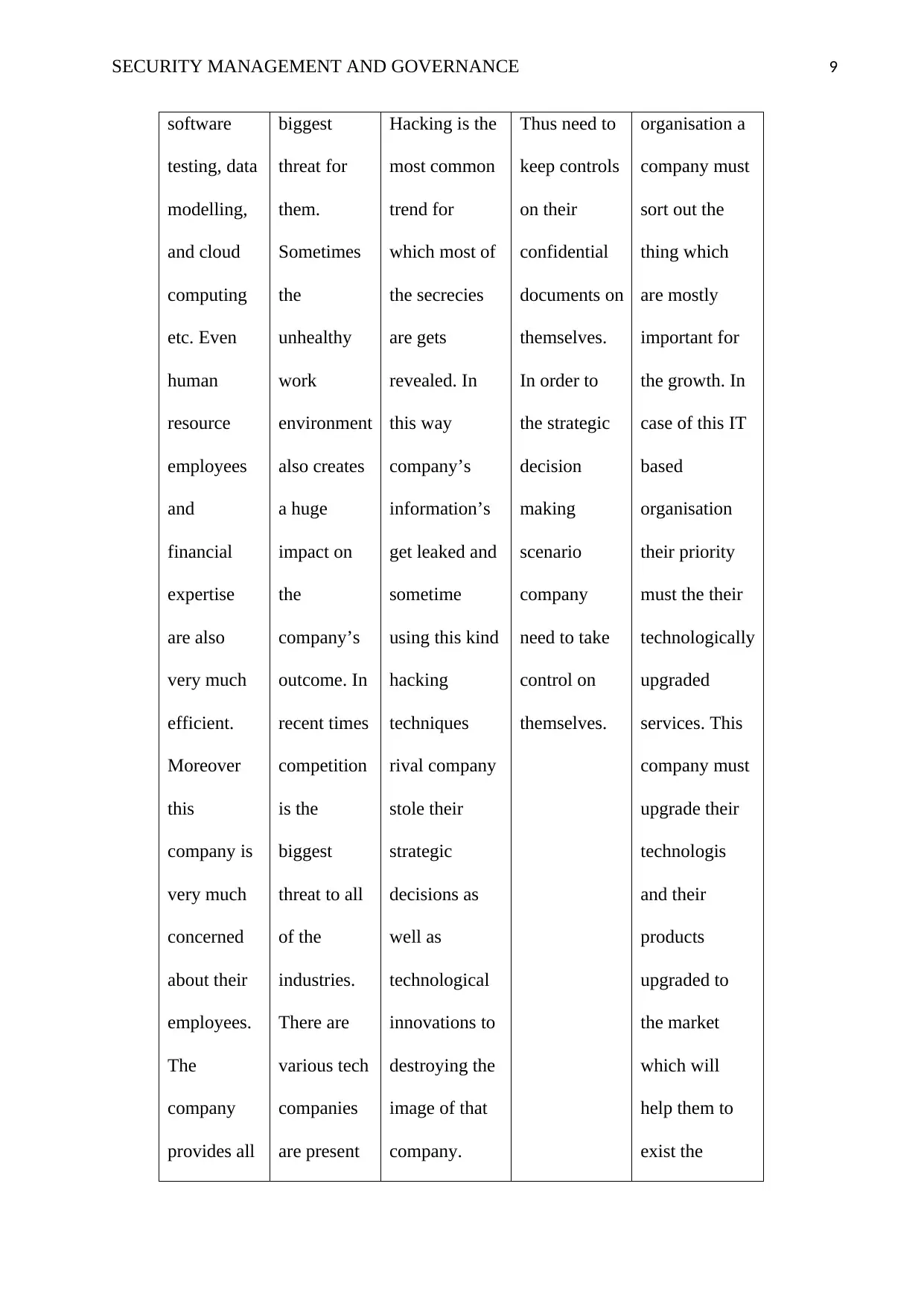
SECURITY MANAGEMENT AND GOVERNANCE 9
software
testing, data
modelling,
and cloud
computing
etc. Even
human
resource
employees
and
financial
expertise
are also
very much
efficient.
Moreover
this
company is
very much
concerned
about their
employees.
The
company
provides all
biggest
threat for
them.
Sometimes
the
unhealthy
work
environment
also creates
a huge
impact on
the
company’s
outcome. In
recent times
competition
is the
biggest
threat to all
of the
industries.
There are
various tech
companies
are present
Hacking is the
most common
trend for
which most of
the secrecies
are gets
revealed. In
this way
company’s
information’s
get leaked and
sometime
using this kind
hacking
techniques
rival company
stole their
strategic
decisions as
well as
technological
innovations to
destroying the
image of that
company.
Thus need to
keep controls
on their
confidential
documents on
themselves.
In order to
the strategic
decision
making
scenario
company
need to take
control on
themselves.
organisation a
company must
sort out the
thing which
are mostly
important for
the growth. In
case of this IT
based
organisation
their priority
must the their
technologically
upgraded
services. This
company must
upgrade their
technologis
and their
products
upgraded to
the market
which will
help them to
exist the
software
testing, data
modelling,
and cloud
computing
etc. Even
human
resource
employees
and
financial
expertise
are also
very much
efficient.
Moreover
this
company is
very much
concerned
about their
employees.
The
company
provides all
biggest
threat for
them.
Sometimes
the
unhealthy
work
environment
also creates
a huge
impact on
the
company’s
outcome. In
recent times
competition
is the
biggest
threat to all
of the
industries.
There are
various tech
companies
are present
Hacking is the
most common
trend for
which most of
the secrecies
are gets
revealed. In
this way
company’s
information’s
get leaked and
sometime
using this kind
hacking
techniques
rival company
stole their
strategic
decisions as
well as
technological
innovations to
destroying the
image of that
company.
Thus need to
keep controls
on their
confidential
documents on
themselves.
In order to
the strategic
decision
making
scenario
company
need to take
control on
themselves.
organisation a
company must
sort out the
thing which
are mostly
important for
the growth. In
case of this IT
based
organisation
their priority
must the their
technologically
upgraded
services. This
company must
upgrade their
technologis
and their
products
upgraded to
the market
which will
help them to
exist the
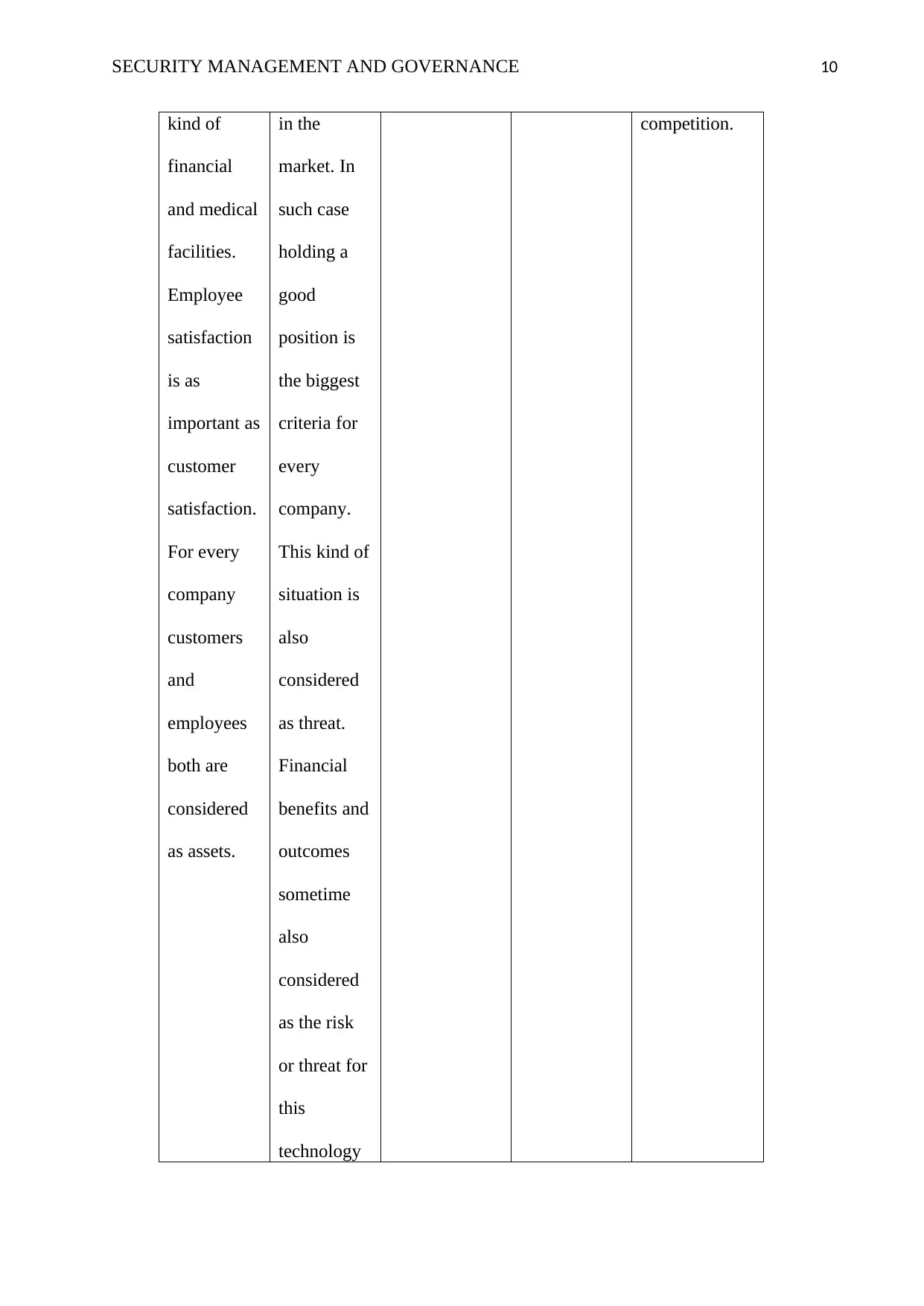
SECURITY MANAGEMENT AND GOVERNANCE 10
kind of
financial
and medical
facilities.
Employee
satisfaction
is as
important as
customer
satisfaction.
For every
company
customers
and
employees
both are
considered
as assets.
in the
market. In
such case
holding a
good
position is
the biggest
criteria for
every
company.
This kind of
situation is
also
considered
as threat.
Financial
benefits and
outcomes
sometime
also
considered
as the risk
or threat for
this
technology
competition.
kind of
financial
and medical
facilities.
Employee
satisfaction
is as
important as
customer
satisfaction.
For every
company
customers
and
employees
both are
considered
as assets.
in the
market. In
such case
holding a
good
position is
the biggest
criteria for
every
company.
This kind of
situation is
also
considered
as threat.
Financial
benefits and
outcomes
sometime
also
considered
as the risk
or threat for
this
technology
competition.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

SECURITY MANAGEMENT AND GOVERNANCE 11
based
company.
Work on this aspect and draw up a Risk Management Plan for it and
include a recommendation based on a Cost-Benefit Analysis.
Nowadays business is very unpredictable and also in order to sustain in the competitive
market people love to try different ways and different marketing strategies for which they
have to take some risks as well. So to take the risks it might happen that they will face any
sort of problems in future so for that people are making this risk management system in their
companies that at least they can identify the problems which may take place in future and
take precaution accordingly to prevent this. The risk management team of the company PAI
must follow some procedures and analyze different possible risks associated with the
business to know the problems (Bahr 2018). Therefore, they identify the risks of the company
and for doing this procedure, they need to full fill all kind of monitoring procedure to know
the exact risk and after that, they evaluate the risks and how much problematic it can be for
the company. If it is normal then they try to solve it by themselves with the help of other
members but if the risk is large, it may cause a big problem and discussion continues
regarding risk management among the high authority of the company to resolve this. Higher
management authorities of PAI discuss with their employees who are genius in technical
parameter (Gerba 2019). Only then will be able to guide the employees to work at the grass
root level as they are the backbone of this company. Software and technical expertise are the
ones most aware of different risks in this kind of company and they always have a possible
solution to manage. So Risk assessment and management is the part and parcel of any
successful company especially PAI, to improve productivity and to gain profit.
based
company.
Work on this aspect and draw up a Risk Management Plan for it and
include a recommendation based on a Cost-Benefit Analysis.
Nowadays business is very unpredictable and also in order to sustain in the competitive
market people love to try different ways and different marketing strategies for which they
have to take some risks as well. So to take the risks it might happen that they will face any
sort of problems in future so for that people are making this risk management system in their
companies that at least they can identify the problems which may take place in future and
take precaution accordingly to prevent this. The risk management team of the company PAI
must follow some procedures and analyze different possible risks associated with the
business to know the problems (Bahr 2018). Therefore, they identify the risks of the company
and for doing this procedure, they need to full fill all kind of monitoring procedure to know
the exact risk and after that, they evaluate the risks and how much problematic it can be for
the company. If it is normal then they try to solve it by themselves with the help of other
members but if the risk is large, it may cause a big problem and discussion continues
regarding risk management among the high authority of the company to resolve this. Higher
management authorities of PAI discuss with their employees who are genius in technical
parameter (Gerba 2019). Only then will be able to guide the employees to work at the grass
root level as they are the backbone of this company. Software and technical expertise are the
ones most aware of different risks in this kind of company and they always have a possible
solution to manage. So Risk assessment and management is the part and parcel of any
successful company especially PAI, to improve productivity and to gain profit.

SECURITY MANAGEMENT AND GOVERNANCE 12
To avoid this kind of risk scenarios a company must take care of its efficient employees.
They should offer them increment after every 6 months. The work environment must be very
peaceful, positive and very cooperative or the employees. The positive environment helps
them to expand their ideas and their inventions. To avoid the mentioned technical risk the
company must need to follow some security policies with the help of which they can control
the third party involvement (Wong, Ho and Chan 2018). They can secure personalized data
with the help of their professionally developed security system. The cost-benefit analysis is
also a major feature to control any kind of risk factors of the company. This kind of analysis
or audit must be analysed by the accounts or the efficient finance manager of the company.
This analysis should be brief and clear to understand by the company. With the help of this
analysis, the company can invest their capitals into some new projects, machines and types of
equipment as well. Nowadays PAI is thinking to expand their reach and planning to build a
new office. With the help of the cost-benefit analysis, a company can create a brief budget
work. With the help of this cost analysis, this company can provide good quality training to
their employees. Only these factors or these recommendations will beneficial for the
company growth, reputation and revenue as well.
To avoid this kind of risk scenarios a company must take care of its efficient employees.
They should offer them increment after every 6 months. The work environment must be very
peaceful, positive and very cooperative or the employees. The positive environment helps
them to expand their ideas and their inventions. To avoid the mentioned technical risk the
company must need to follow some security policies with the help of which they can control
the third party involvement (Wong, Ho and Chan 2018). They can secure personalized data
with the help of their professionally developed security system. The cost-benefit analysis is
also a major feature to control any kind of risk factors of the company. This kind of analysis
or audit must be analysed by the accounts or the efficient finance manager of the company.
This analysis should be brief and clear to understand by the company. With the help of this
analysis, the company can invest their capitals into some new projects, machines and types of
equipment as well. Nowadays PAI is thinking to expand their reach and planning to build a
new office. With the help of the cost-benefit analysis, a company can create a brief budget
work. With the help of this cost analysis, this company can provide good quality training to
their employees. Only these factors or these recommendations will beneficial for the
company growth, reputation and revenue as well.
SECURITY MANAGEMENT AND GOVERNANCE 13
Where does the responsibility for the user and the vendor begin?
The involvement of the third party is strictly avoided. The services and products which are
offered by them must be available only from their organisation. Vendors are offering their
products in the regular market at high price (Gerba 2019). This kind of scenario is not good
for the reputation of this organisation. This kind of scenario can be avoided by using some
kind of vendor management techniques. Those techniques are as follows.
It is the real fact that a company can hold a large market only with the help of some
reliable and efficient vendors. Thus building a good relationship with them is a very
important factor.
An organisation must clear their priorities and their goals towards their vendors. This
thing will become helpful for them to understand the marketing and business
strategies of that organisation.
Where does the responsibility for the user and the vendor begin?
The involvement of the third party is strictly avoided. The services and products which are
offered by them must be available only from their organisation. Vendors are offering their
products in the regular market at high price (Gerba 2019). This kind of scenario is not good
for the reputation of this organisation. This kind of scenario can be avoided by using some
kind of vendor management techniques. Those techniques are as follows.
It is the real fact that a company can hold a large market only with the help of some
reliable and efficient vendors. Thus building a good relationship with them is a very
important factor.
An organisation must clear their priorities and their goals towards their vendors. This
thing will become helpful for them to understand the marketing and business
strategies of that organisation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY MANAGEMENT AND GOVERNANCE 14
Sometimes that organisation must be liberal and lenient towards their vendors. As
every person have some different ideas, thinking even different inventions as well.
Sometime the organisation must trust them to take some kind of marketing strategies
and inventory ideas on their own.
With the help of this detailed analysis, we can understand that in the case of the
company PAI vendors are needed to expand their market, business and revenues.
Those vendors must be reliable, efficient and experienced as well. Those vendors
must have a license for selling their products at a reasonable price.
Sometimes that organisation must be liberal and lenient towards their vendors. As
every person have some different ideas, thinking even different inventions as well.
Sometime the organisation must trust them to take some kind of marketing strategies
and inventory ideas on their own.
With the help of this detailed analysis, we can understand that in the case of the
company PAI vendors are needed to expand their market, business and revenues.
Those vendors must be reliable, efficient and experienced as well. Those vendors
must have a license for selling their products at a reasonable price.

SECURITY MANAGEMENT AND GOVERNANCE 15
Reference:
Bahr, N.J., 2018. System safety engineering and risk assessment: a practical approach. CRC
press.
Gerba, C.P., 2019. Risk assessment. In Environmental and Pollution Science (pp. 541-563).
Academic Press.
Marin, G., Modica, M., Paleari, S. and Zoboli, R., 2019. Disaster Risk Management: Building
the ‘Disaster Risk Assessment Tool’for Italy (No. 0319). SEEDS, Sustainability
Environmental Economics and Dynamics Studies.
Moser, G., Drewlo, S., Huppertz, B. and Armant, D.R., 2018. Trophoblast retrieval and
isolation from the cervix: origins of cervical trophoblasts and their potential value for risk
assessment of ongoing pregnancies. Human reproduction update, 24(4), pp.484-496.
Pearson-Stuttard, J., Zhou, B., Kontis, V., Bentham, J., Gunter, M.J. and Ezzati, M., 2018.
Worldwide burden of cancer attributable to diabetes and high body-mass index: a
comparative risk assessment. The Lancet Diabetes & Endocrinology, 6(6), pp.e6-e15.
Wong, H.N., Ho, K.K.S. and Chan, Y.C., 2018. Assessment of consequence of landslides.
In Landslide risk assessment (pp. 111-149). Routledge.
Reference:
Bahr, N.J., 2018. System safety engineering and risk assessment: a practical approach. CRC
press.
Gerba, C.P., 2019. Risk assessment. In Environmental and Pollution Science (pp. 541-563).
Academic Press.
Marin, G., Modica, M., Paleari, S. and Zoboli, R., 2019. Disaster Risk Management: Building
the ‘Disaster Risk Assessment Tool’for Italy (No. 0319). SEEDS, Sustainability
Environmental Economics and Dynamics Studies.
Moser, G., Drewlo, S., Huppertz, B. and Armant, D.R., 2018. Trophoblast retrieval and
isolation from the cervix: origins of cervical trophoblasts and their potential value for risk
assessment of ongoing pregnancies. Human reproduction update, 24(4), pp.484-496.
Pearson-Stuttard, J., Zhou, B., Kontis, V., Bentham, J., Gunter, M.J. and Ezzati, M., 2018.
Worldwide burden of cancer attributable to diabetes and high body-mass index: a
comparative risk assessment. The Lancet Diabetes & Endocrinology, 6(6), pp.e6-e15.
Wong, H.N., Ho, K.K.S. and Chan, Y.C., 2018. Assessment of consequence of landslides.
In Landslide risk assessment (pp. 111-149). Routledge.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




