Security Management and Governance
VerifiedAdded on 2023/01/13
|14
|3130
|34
AI Summary
This report discusses the benefits of security management, developing a security policy and plan, identifying roles and responsibilities, methods for developing a security management program, and implications of legal requirements.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: SECURITY MANAGEMENT AND GOVERNANCE
Security Management and Governance
Name of the Student
Name of the University
Author’s Note:
Security Management and Governance
Name of the Student
Name of the University
Author’s Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
SECURITY MANAGEMENT AND GOVERNANCE
Executive Summary
The main aim of this report is to know about the entire case study of Power AI or PAI. It
develops software for business, home as well as industrial utilizations. The major focus is
given on the subsequent development of several systems of artificial intelligence for
controlling storing, generating and utilization of power within separate environments. It has
developed several unique and significant solutions for the various applications. This report
has provided a detailed description of security awareness and governance program. A proper
risk analysis is also done in this report.
SECURITY MANAGEMENT AND GOVERNANCE
Executive Summary
The main aim of this report is to know about the entire case study of Power AI or PAI. It
develops software for business, home as well as industrial utilizations. The major focus is
given on the subsequent development of several systems of artificial intelligence for
controlling storing, generating and utilization of power within separate environments. It has
developed several unique and significant solutions for the various applications. This report
has provided a detailed description of security awareness and governance program. A proper
risk analysis is also done in this report.

2
SECURITY MANAGEMENT AND GOVERNANCE
Table of Contents
Part A: Report............................................................................................................................3
1. Discussion on Benefits that are derived from the Security Management as the ongoing
procedure as well as Reasons to have a Security Program Policy.........................................3
2. Developing a Proper Security Policy as well as Security Management Plan....................4
3. Identifying the major Functionalities, Tasks, Responsibilities and Roles for Security
Management Program for PIA as well as Roles of the Various Groups or Individuals in
Governance............................................................................................................................5
4. Identifying Major Methods and Models for Developing Security Management Program 6
5. Discussing Implications of Legal and Statutory Requirements and Major Advantages of
the Formal Approach..............................................................................................................7
Part B: Appendix........................................................................................................................8
1. Risk Management Plan......................................................................................................8
2. Threats, Vulnerabilities and Attacks of Formal Plan.........................................................9
3. Risk Management Plan......................................................................................................9
4. Responsibility for User and Vendor.................................................................................10
Summary..................................................................................................................................11
References................................................................................................................................12
SECURITY MANAGEMENT AND GOVERNANCE
Table of Contents
Part A: Report............................................................................................................................3
1. Discussion on Benefits that are derived from the Security Management as the ongoing
procedure as well as Reasons to have a Security Program Policy.........................................3
2. Developing a Proper Security Policy as well as Security Management Plan....................4
3. Identifying the major Functionalities, Tasks, Responsibilities and Roles for Security
Management Program for PIA as well as Roles of the Various Groups or Individuals in
Governance............................................................................................................................5
4. Identifying Major Methods and Models for Developing Security Management Program 6
5. Discussing Implications of Legal and Statutory Requirements and Major Advantages of
the Formal Approach..............................................................................................................7
Part B: Appendix........................................................................................................................8
1. Risk Management Plan......................................................................................................8
2. Threats, Vulnerabilities and Attacks of Formal Plan.........................................................9
3. Risk Management Plan......................................................................................................9
4. Responsibility for User and Vendor.................................................................................10
Summary..................................................................................................................................11
References................................................................................................................................12

3
SECURITY MANAGEMENT AND GOVERNANCE
Part A: Report
1. Discussion on Benefits that are derived from the Security Management as the ongoing
procedure as well as Reasons to have a Security Program Policy
Some of the most important and significant advantages that could be derived from the
security management program as an ongoing procedure are given below:
i) Helps to Protect and Secure Every Form of Information: All the significant forms
of confidential information would be secured and protected for Power AI (Flores, Antonsen
and Ekstedt 2014).
ii) Increments Cyber Attack Resilience: This is the second significant advantage of
security management program. It helps in incrementing the cyber attack resilience.
iii) Provides Framework for Keeping Organizational Information Protected: The
security management program eventually provides a proper and subsequent framework for
effectively keeping all types of organizational information protected.
iv) Reducing Expenses: The ICT security management program would be reducing
the major expenses for information security.
There are some of the most significant reasons to have a proper policy and these
reasons are given below:
i) Protecting CIA of Information: CIA or confidentiality, integrity and availability of
the confidential information could be easily and promptly secured with a collection of
technical as well as physical controls and this is important for the organization (Whitman and
Mattord 2014).
SECURITY MANAGEMENT AND GOVERNANCE
Part A: Report
1. Discussion on Benefits that are derived from the Security Management as the ongoing
procedure as well as Reasons to have a Security Program Policy
Some of the most important and significant advantages that could be derived from the
security management program as an ongoing procedure are given below:
i) Helps to Protect and Secure Every Form of Information: All the significant forms
of confidential information would be secured and protected for Power AI (Flores, Antonsen
and Ekstedt 2014).
ii) Increments Cyber Attack Resilience: This is the second significant advantage of
security management program. It helps in incrementing the cyber attack resilience.
iii) Provides Framework for Keeping Organizational Information Protected: The
security management program eventually provides a proper and subsequent framework for
effectively keeping all types of organizational information protected.
iv) Reducing Expenses: The ICT security management program would be reducing
the major expenses for information security.
There are some of the most significant reasons to have a proper policy and these
reasons are given below:
i) Protecting CIA of Information: CIA or confidentiality, integrity and availability of
the confidential information could be easily and promptly secured with a collection of
technical as well as physical controls and this is important for the organization (Whitman and
Mattord 2014).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
SECURITY MANAGEMENT AND GOVERNANCE
ii) Ensuring Proper Resumption of the Major Business Processes: The second
important and significant reason to keep this ICT security management program is ensuing
that there is a timely resumption of several important business processes for Power AI.
iii) Improvement of Company Culture: This is yet another important reason for
keeping ICT security management program in PAI (Bahl and Wali 2014). The entire
company culture can be improved with this program.
2. Developing a Proper Security Policy as well as Security Management Plan
A security management plan and security policy must be eventually developed by
Power AI so that the integrity of information could be maintained as well as legal and
regulatory requirements are being fulfilled. Major steps for developing a security
management plan and a security policy are provided below:
i) Performing Proper Regulatory Review.
ii) Specifying Oversight, Responsibilities and Governance.
iii) Considering Inventory of Assets.
iv) Evaluating Proper Assessment of Third Party Risk.
v) Properly Creating Incident Response Planning.
vi) Training as well as Testing of Employees.
All the above mentioned steps are quite significant to make the entire security
program efficient for Power AI as they are extremely concerned regarding their intellectual
property. The security program would be extremely effective for them (Carcary et al. 2016).
SECURITY MANAGEMENT AND GOVERNANCE
ii) Ensuring Proper Resumption of the Major Business Processes: The second
important and significant reason to keep this ICT security management program is ensuing
that there is a timely resumption of several important business processes for Power AI.
iii) Improvement of Company Culture: This is yet another important reason for
keeping ICT security management program in PAI (Bahl and Wali 2014). The entire
company culture can be improved with this program.
2. Developing a Proper Security Policy as well as Security Management Plan
A security management plan and security policy must be eventually developed by
Power AI so that the integrity of information could be maintained as well as legal and
regulatory requirements are being fulfilled. Major steps for developing a security
management plan and a security policy are provided below:
i) Performing Proper Regulatory Review.
ii) Specifying Oversight, Responsibilities and Governance.
iii) Considering Inventory of Assets.
iv) Evaluating Proper Assessment of Third Party Risk.
v) Properly Creating Incident Response Planning.
vi) Training as well as Testing of Employees.
All the above mentioned steps are quite significant to make the entire security
program efficient for Power AI as they are extremely concerned regarding their intellectual
property. The security program would be extremely effective for them (Carcary et al. 2016).

5
SECURITY MANAGEMENT AND GOVERNANCE
3. Identifying the major Functionalities, Tasks, Responsibilities and Roles for Security
Management Program for PIA as well as Roles of the Various Groups or Individuals in
Governance
Power AI comprises of fifty employees and within them twenty five are directly
involved in the processes of designing, developing, examination and finally deploying the
products. Each of the positions of employees are stable as well as employee turnover are
extremely high to maintain the high demands of information technology staff with subsequent
knowledge regarding system of AI (Mueller, Schmidt and Kuerbis 2013). The respective
organizational senior management consists of three employees that include IT Manager,
finance Manager and Sales Manager. The human resource department of this team is
overseen by the owner.
The various responsibilities, roles, tasks and functionalities for this security
management program majorly involve offering a proper protection to the entire organization,
is helpful to respond to the various evolving security risks, business continuity plan, acting
against information as well as intellectual property and several others (Silic and Back 2014).
The major roles of the information technology manager for the security management
program in Power AI involve planning, organizing, direction as well as controlling all types
of intellectual properties and information. This is needed for saving the major and the most
significant algorithms, which are mainly developed for services and products since these are
the considerable investments (Van Eeten and Mueller 2013). The major roles and
responsibilities of the Power AI based finance manager include proper maintenance of
financial development as well as growth of strategies in the longer term financial objectives
of PAI. Sales manager of this particular organization comprises of some of the major and
most significant responsibilities include meeting of the organizational revenue target by the
SECURITY MANAGEMENT AND GOVERNANCE
3. Identifying the major Functionalities, Tasks, Responsibilities and Roles for Security
Management Program for PIA as well as Roles of the Various Groups or Individuals in
Governance
Power AI comprises of fifty employees and within them twenty five are directly
involved in the processes of designing, developing, examination and finally deploying the
products. Each of the positions of employees are stable as well as employee turnover are
extremely high to maintain the high demands of information technology staff with subsequent
knowledge regarding system of AI (Mueller, Schmidt and Kuerbis 2013). The respective
organizational senior management consists of three employees that include IT Manager,
finance Manager and Sales Manager. The human resource department of this team is
overseen by the owner.
The various responsibilities, roles, tasks and functionalities for this security
management program majorly involve offering a proper protection to the entire organization,
is helpful to respond to the various evolving security risks, business continuity plan, acting
against information as well as intellectual property and several others (Silic and Back 2014).
The major roles of the information technology manager for the security management
program in Power AI involve planning, organizing, direction as well as controlling all types
of intellectual properties and information. This is needed for saving the major and the most
significant algorithms, which are mainly developed for services and products since these are
the considerable investments (Van Eeten and Mueller 2013). The major roles and
responsibilities of the Power AI based finance manager include proper maintenance of
financial development as well as growth of strategies in the longer term financial objectives
of PAI. Sales manager of this particular organization comprises of some of the major and
most significant responsibilities include meeting of the organizational revenue target by the

6
SECURITY MANAGEMENT AND GOVERNANCE
activity of sales representative. It is extremely important and significant to maintain a proper
balance between the organizational security management and governance.
4. Identifying Major Methods and Models for Developing Security Management
Program
Power AI or PAI is a company that is significant responsible for developing software
for the industrial, business and home uses (Yaokumah and Brown 2014). They have decided
to implement an ICT Security Program within their business. The plan of security program
for this organization will be properly discussing the procedure of information privacy is
getting better controlled only after developing the Security Management plan and thus they
would be providing a proper program with several roles and tasks for development of
program. They are mainly concerned about their intellectual properties and the various
algorithms are being developed for the products (Debreceny 2013). Recently, the
development work is being completed on the closed on site network, which is being managed
internally by the IT service employees. The completed products in an executable form are
being ported to the Sales system that is being provided by the cloud application provider or
Cloud Services International (Safa, Von Solms and Furnell 2016). The subsequent planning
will be discussing about the procedure of information privacy that is being well managed
after developing the Security Management Program policy and this would be providing a
program with the major roles and tasks for development of program.
Some of the most subsequent methods and models for an efficient as well as effective
development of security management policy. The several methods as well as models are
extremely important for making the entire security program quite efficient and effective in
terms of other security program (Layton 2016). The proper illegal and loss of the copies of
the source codes and associated documentation would be the most significant need for Power
AI. The complexity as well as velocity of the threat companies were eventually facing
SECURITY MANAGEMENT AND GOVERNANCE
activity of sales representative. It is extremely important and significant to maintain a proper
balance between the organizational security management and governance.
4. Identifying Major Methods and Models for Developing Security Management
Program
Power AI or PAI is a company that is significant responsible for developing software
for the industrial, business and home uses (Yaokumah and Brown 2014). They have decided
to implement an ICT Security Program within their business. The plan of security program
for this organization will be properly discussing the procedure of information privacy is
getting better controlled only after developing the Security Management plan and thus they
would be providing a proper program with several roles and tasks for development of
program. They are mainly concerned about their intellectual properties and the various
algorithms are being developed for the products (Debreceny 2013). Recently, the
development work is being completed on the closed on site network, which is being managed
internally by the IT service employees. The completed products in an executable form are
being ported to the Sales system that is being provided by the cloud application provider or
Cloud Services International (Safa, Von Solms and Furnell 2016). The subsequent planning
will be discussing about the procedure of information privacy that is being well managed
after developing the Security Management Program policy and this would be providing a
program with the major roles and tasks for development of program.
Some of the most subsequent methods and models for an efficient as well as effective
development of security management policy. The several methods as well as models are
extremely important for making the entire security program quite efficient and effective in
terms of other security program (Layton 2016). The proper illegal and loss of the copies of
the source codes and associated documentation would be the most significant need for Power
AI. The complexity as well as velocity of the threat companies were eventually facing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SECURITY MANAGEMENT AND GOVERNANCE
subsequent attack trends to determine the efficient mitigations (Ahmad, Maynard and Park
2014). Several elements and components of the model of security management involve policy
statement, proper compliance with all applicable standards, proper definition, threat
assessment and threat analysis, training of employees, laws and regulations, roles of the
security program managers, management as well as supervisor training, management
commitment as well as responsibilities and program exercise and drills (Da Veiga and
Martins 2015).
5. Discussing Implications of Legal and Statutory Requirements and Major Advantages
of the Formal Approach
Security management as well as governance program will be quite significant for PAI.
This particular program helps to provide various important benefits as well as a proper
security to subsequent organization (Mishra 2015). These systems and information, which are
eventually present in the organization of Power AI are being included in the respective
program of security management and governance. A proper access to authenticated
information is considered as a major indispensable element for conducting the business and
in a growing number of organizations, this information is termed as business (Trautman,
Triche and Wetherbe 2013). The various statutory and legal requirements of program of
security management and governance involve a subsequent set of processes and policies to
achieve the various security objectives that will be securing the several intellectual properties
for Power AI from all types of theft, loss and release.
Such plans also include agreements and arrangements with proper entity companies
such as local law enforcement. This information will be giving competitors with subsequent
cost benefits to gain a better development for every similar product. As, the respective
assessed value of the knowledge is approximately 3 million dollars and the information is
also kept as trade secrets, where source code and end products would be secured by copyright
SECURITY MANAGEMENT AND GOVERNANCE
subsequent attack trends to determine the efficient mitigations (Ahmad, Maynard and Park
2014). Several elements and components of the model of security management involve policy
statement, proper compliance with all applicable standards, proper definition, threat
assessment and threat analysis, training of employees, laws and regulations, roles of the
security program managers, management as well as supervisor training, management
commitment as well as responsibilities and program exercise and drills (Da Veiga and
Martins 2015).
5. Discussing Implications of Legal and Statutory Requirements and Major Advantages
of the Formal Approach
Security management as well as governance program will be quite significant for PAI.
This particular program helps to provide various important benefits as well as a proper
security to subsequent organization (Mishra 2015). These systems and information, which are
eventually present in the organization of Power AI are being included in the respective
program of security management and governance. A proper access to authenticated
information is considered as a major indispensable element for conducting the business and
in a growing number of organizations, this information is termed as business (Trautman,
Triche and Wetherbe 2013). The various statutory and legal requirements of program of
security management and governance involve a subsequent set of processes and policies to
achieve the various security objectives that will be securing the several intellectual properties
for Power AI from all types of theft, loss and release.
Such plans also include agreements and arrangements with proper entity companies
such as local law enforcement. This information will be giving competitors with subsequent
cost benefits to gain a better development for every similar product. As, the respective
assessed value of the knowledge is approximately 3 million dollars and the information is
also kept as trade secrets, where source code and end products would be secured by copyright

8
SECURITY MANAGEMENT AND GOVERNANCE
laws (Hagmann 2013). Major advantages that this formal approach will be providing are
protecting intellectual property information, protection of confidentiality, integrity and
availability of the data, giving a centrally controlled frameworks and several others.
Part B: Appendix
1. Risk Management Plan
The risk assessment or management of the major risks of PAI patient information is
required for the organization.
i) The major advantages that a Risk Management Plan can bring to a company are as
follows:
a) Easy to Spot Projects: It helps in spotting the projects easily and promptly.
b) Provides Better Data Quality: The data quality becomes better with this type of
plan.
c) Effective Decision Making: The entire process of decision making is extremely
effective and efficient and thus risk management planning is required.
d) Better Communication: An effective communication is the next important and
significant advantage of risk management plan.
e) Better Eradication of Issues: The risks and issues are eradicated in a better manner
without any kind of complexity.
The main steps to make this type of plan are as follows:
a) Identification of Risks.
b) Analysis of the Identified Risks.
c) Action taken for the Identified Risks.
SECURITY MANAGEMENT AND GOVERNANCE
laws (Hagmann 2013). Major advantages that this formal approach will be providing are
protecting intellectual property information, protection of confidentiality, integrity and
availability of the data, giving a centrally controlled frameworks and several others.
Part B: Appendix
1. Risk Management Plan
The risk assessment or management of the major risks of PAI patient information is
required for the organization.
i) The major advantages that a Risk Management Plan can bring to a company are as
follows:
a) Easy to Spot Projects: It helps in spotting the projects easily and promptly.
b) Provides Better Data Quality: The data quality becomes better with this type of
plan.
c) Effective Decision Making: The entire process of decision making is extremely
effective and efficient and thus risk management planning is required.
d) Better Communication: An effective communication is the next important and
significant advantage of risk management plan.
e) Better Eradication of Issues: The risks and issues are eradicated in a better manner
without any kind of complexity.
The main steps to make this type of plan are as follows:
a) Identification of Risks.
b) Analysis of the Identified Risks.
c) Action taken for the Identified Risks.

9
SECURITY MANAGEMENT AND GOVERNANCE
d) Monitoring the Risks.
e) Removing the Risks.
2. Threats, Vulnerabilities and Attacks of Formal Plan
The major threats, vulnerabilities and attacks of the patient information are as follows:
i) Trojan Horse: This is one of the major and significant threat and attack to the
patient information within Power AI organization. The main purpose of this type of threat is
to conceal themselves within software, which seem legal and when the software is getting
executed, they would be doing the task for either stealing of information and any other
purpose for which these are being designed.
ii) Ransomware: This type of malware mainly encrypts the files and even locks the
system for making is accessible entirely.
iii) Theft of Intellectual Properties: The third risk is the theft of intellectual property
and hence the intellectual property rights such as patents and copyrights are violated.
iv) Information Extortion: This particular risk ensures that the organizational
information and property is being received for exchange of payment.
v) Identity Theft: This kind of risk ensures to act someone else for obtaining the
personal information of an individual for accessing the vital information, which are required
to be accessed.
vi) Sabotage of Data: The sabotage of information refers to destroying of information
for causing loss of confidence.
3. Risk Management Plan
The risk management plan for the patient information within organization of Power
AI is as follows:
SECURITY MANAGEMENT AND GOVERNANCE
d) Monitoring the Risks.
e) Removing the Risks.
2. Threats, Vulnerabilities and Attacks of Formal Plan
The major threats, vulnerabilities and attacks of the patient information are as follows:
i) Trojan Horse: This is one of the major and significant threat and attack to the
patient information within Power AI organization. The main purpose of this type of threat is
to conceal themselves within software, which seem legal and when the software is getting
executed, they would be doing the task for either stealing of information and any other
purpose for which these are being designed.
ii) Ransomware: This type of malware mainly encrypts the files and even locks the
system for making is accessible entirely.
iii) Theft of Intellectual Properties: The third risk is the theft of intellectual property
and hence the intellectual property rights such as patents and copyrights are violated.
iv) Information Extortion: This particular risk ensures that the organizational
information and property is being received for exchange of payment.
v) Identity Theft: This kind of risk ensures to act someone else for obtaining the
personal information of an individual for accessing the vital information, which are required
to be accessed.
vi) Sabotage of Data: The sabotage of information refers to destroying of information
for causing loss of confidence.
3. Risk Management Plan
The risk management plan for the patient information within organization of Power
AI is as follows:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
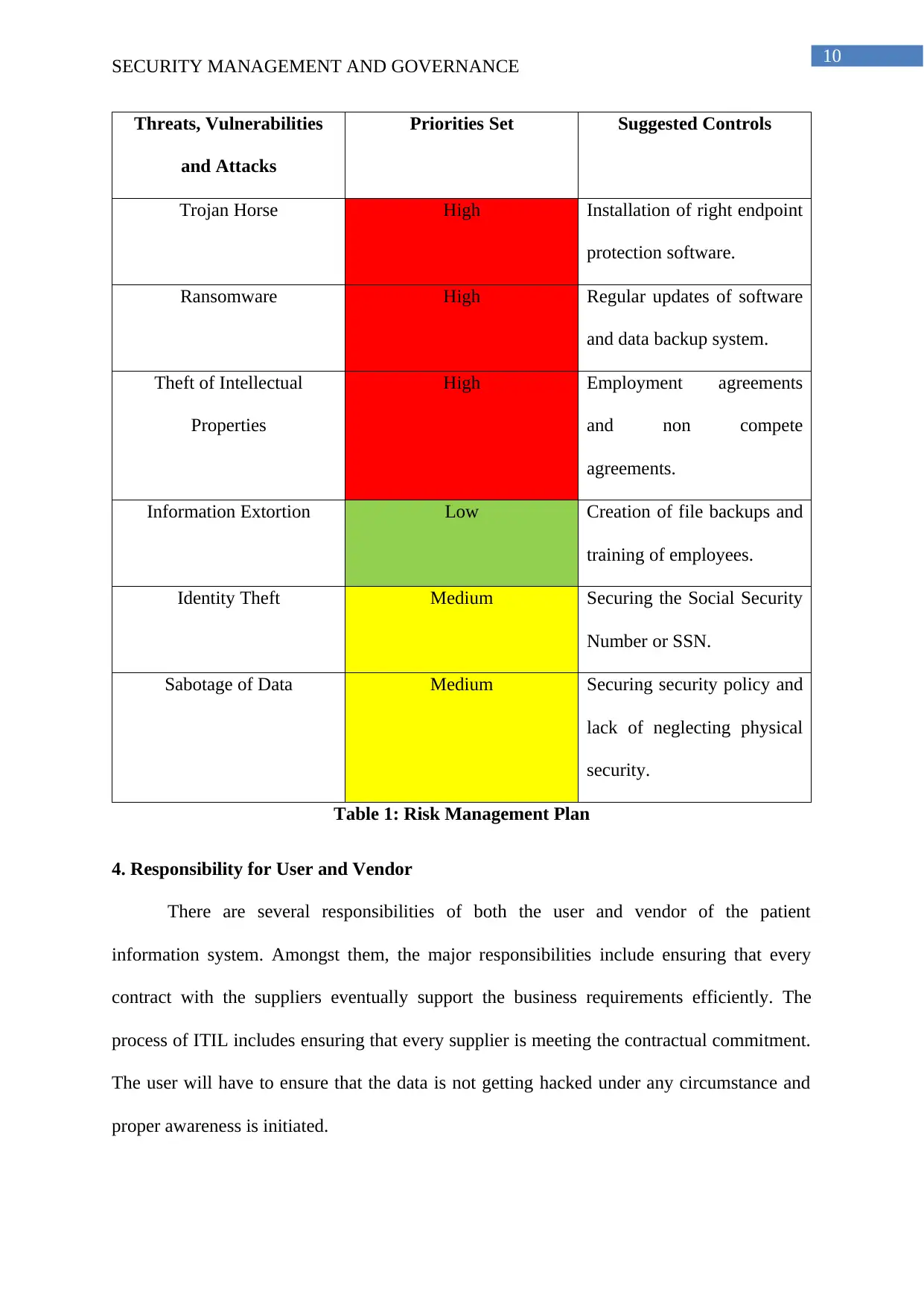
10
SECURITY MANAGEMENT AND GOVERNANCE
Threats, Vulnerabilities
and Attacks
Priorities Set Suggested Controls
Trojan Horse High Installation of right endpoint
protection software.
Ransomware High Regular updates of software
and data backup system.
Theft of Intellectual
Properties
High Employment agreements
and non compete
agreements.
Information Extortion Low Creation of file backups and
training of employees.
Identity Theft Medium Securing the Social Security
Number or SSN.
Sabotage of Data Medium Securing security policy and
lack of neglecting physical
security.
Table 1: Risk Management Plan
4. Responsibility for User and Vendor
There are several responsibilities of both the user and vendor of the patient
information system. Amongst them, the major responsibilities include ensuring that every
contract with the suppliers eventually support the business requirements efficiently. The
process of ITIL includes ensuring that every supplier is meeting the contractual commitment.
The user will have to ensure that the data is not getting hacked under any circumstance and
proper awareness is initiated.
SECURITY MANAGEMENT AND GOVERNANCE
Threats, Vulnerabilities
and Attacks
Priorities Set Suggested Controls
Trojan Horse High Installation of right endpoint
protection software.
Ransomware High Regular updates of software
and data backup system.
Theft of Intellectual
Properties
High Employment agreements
and non compete
agreements.
Information Extortion Low Creation of file backups and
training of employees.
Identity Theft Medium Securing the Social Security
Number or SSN.
Sabotage of Data Medium Securing security policy and
lack of neglecting physical
security.
Table 1: Risk Management Plan
4. Responsibility for User and Vendor
There are several responsibilities of both the user and vendor of the patient
information system. Amongst them, the major responsibilities include ensuring that every
contract with the suppliers eventually support the business requirements efficiently. The
process of ITIL includes ensuring that every supplier is meeting the contractual commitment.
The user will have to ensure that the data is not getting hacked under any circumstance and
proper awareness is initiated.

11
SECURITY MANAGEMENT AND GOVERNANCE
Summary
Therefore, from the above discussion, it can be concluded that security management
and governance program is extremely important and significant for managing the patient
information within Power AI. This type of program is required for knowing about the
importance of patient information and how to deal with them. The second part of the report
has provided a detailed analysis of risk management planning for the Power AI organization.
The risks are being prioritized as per priorities. The most significant risks in this particular
report are identity theft, ransomware, loss of intellectual properties, and sabotage of data,
Trojan horse and information extortion. Proper and relevant mitigation strategies or controls
are also provided in this report.
SECURITY MANAGEMENT AND GOVERNANCE
Summary
Therefore, from the above discussion, it can be concluded that security management
and governance program is extremely important and significant for managing the patient
information within Power AI. This type of program is required for knowing about the
importance of patient information and how to deal with them. The second part of the report
has provided a detailed analysis of risk management planning for the Power AI organization.
The risks are being prioritized as per priorities. The most significant risks in this particular
report are identity theft, ransomware, loss of intellectual properties, and sabotage of data,
Trojan horse and information extortion. Proper and relevant mitigation strategies or controls
are also provided in this report.

12
SECURITY MANAGEMENT AND GOVERNANCE
References
Ahmad, A., Maynard, S.B. and Park, S., 2014. Information security strategies: towards an
organizational multi-strategy perspective. Journal of Intelligent Manufacturing, 25(2),
pp.357-370.
Bahl, S. and Wali, O.P., 2014. Perceived significance of information security governance to
predict the information security service quality in software service industry: An empirical
analysis. Information Management & Computer Security, 22(1), pp.2-23.
Carcary, M., Renaud, K., McLaughlin, S. and O'Brien, C., 2016. A framework for
information security governance and management. IT Professional, 18(2), pp.22-30.
Da Veiga, A. and Martins, N., 2015. Improving the information security culture through
monitoring and implementation actions illustrated through a case study. Computers &
Security, 49, pp.162-176.
Debreceny, R.S., 2013. Research on IT governance, risk, and value: Challenges and
opportunities. Journal of Information Systems, 27(1), pp.129-135.
Flores, W.R., Antonsen, E. and Ekstedt, M., 2014. Information security knowledge sharing in
organizations: Investigating the effect of behavioral information security governance and
national culture. Computers & Security, 43, pp.90-110.
Hagmann, J., 2013. Information governance–beyond the buzz. Records Management
Journal, 23(3), pp.228-240.
Layton, T.P., 2016. Information Security: Design, implementation, measurement, and
compliance. Auerbach Publications.
Mishra, S., 2015. Organizational objectives for information security governance: a value
focused assessment. Information & Computer Security, 23(2), pp.122-144.
SECURITY MANAGEMENT AND GOVERNANCE
References
Ahmad, A., Maynard, S.B. and Park, S., 2014. Information security strategies: towards an
organizational multi-strategy perspective. Journal of Intelligent Manufacturing, 25(2),
pp.357-370.
Bahl, S. and Wali, O.P., 2014. Perceived significance of information security governance to
predict the information security service quality in software service industry: An empirical
analysis. Information Management & Computer Security, 22(1), pp.2-23.
Carcary, M., Renaud, K., McLaughlin, S. and O'Brien, C., 2016. A framework for
information security governance and management. IT Professional, 18(2), pp.22-30.
Da Veiga, A. and Martins, N., 2015. Improving the information security culture through
monitoring and implementation actions illustrated through a case study. Computers &
Security, 49, pp.162-176.
Debreceny, R.S., 2013. Research on IT governance, risk, and value: Challenges and
opportunities. Journal of Information Systems, 27(1), pp.129-135.
Flores, W.R., Antonsen, E. and Ekstedt, M., 2014. Information security knowledge sharing in
organizations: Investigating the effect of behavioral information security governance and
national culture. Computers & Security, 43, pp.90-110.
Hagmann, J., 2013. Information governance–beyond the buzz. Records Management
Journal, 23(3), pp.228-240.
Layton, T.P., 2016. Information Security: Design, implementation, measurement, and
compliance. Auerbach Publications.
Mishra, S., 2015. Organizational objectives for information security governance: a value
focused assessment. Information & Computer Security, 23(2), pp.122-144.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
SECURITY MANAGEMENT AND GOVERNANCE
Mueller, M., Schmidt, A. and Kuerbis, B., 2013. Internet security and networked governance
in international relations. International Studies Review, 15(1), pp.86-104.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. Computers & Security, 56, pp.70-82.
Silic, M. and Back, A., 2014. Information security: Critical review and future directions for
research. Information Management & Computer Security, 22(3), pp.279-308.
Trautman, L.J., Triche, J. and Wetherbe, J., 2013. Corporate information technology
governance under fire. Journal of Strategic and International Studies, 8(3).
Van Eeten, M.J. and Mueller, M., 2013. Where is the governance in Internet
governance?. New Media & Society, 15(5), pp.720-736.
Whitman, M. and Mattord, H.J., 2014. Information security governance for the non-security
business executive.
Yaokumah, W. and Brown, S., 2014. An empirical examination of the relationship between
information security/business strategic alignment and information security governance
domain areas. Journal of Business Systems, Governance & Ethics, 9(2), pp.50-65.
SECURITY MANAGEMENT AND GOVERNANCE
Mueller, M., Schmidt, A. and Kuerbis, B., 2013. Internet security and networked governance
in international relations. International Studies Review, 15(1), pp.86-104.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. Computers & Security, 56, pp.70-82.
Silic, M. and Back, A., 2014. Information security: Critical review and future directions for
research. Information Management & Computer Security, 22(3), pp.279-308.
Trautman, L.J., Triche, J. and Wetherbe, J., 2013. Corporate information technology
governance under fire. Journal of Strategic and International Studies, 8(3).
Van Eeten, M.J. and Mueller, M., 2013. Where is the governance in Internet
governance?. New Media & Society, 15(5), pp.720-736.
Whitman, M. and Mattord, H.J., 2014. Information security governance for the non-security
business executive.
Yaokumah, W. and Brown, S., 2014. An empirical examination of the relationship between
information security/business strategic alignment and information security governance
domain areas. Journal of Business Systems, Governance & Ethics, 9(2), pp.50-65.
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





