Security Management and Migration Report: Regional Gardens Ltd.
VerifiedAdded on 2021/06/16
|31
|6909
|100
Report
AI Summary
This report presents a strategic proposal for Regional Gardens Ltd., focusing on improving its ICT infrastructure through a cloud-based solution. It evaluates various cloud computing architectures, with a recommendation for a hybrid cloud approach. The report details the chosen architecture, including its benefits and potential issues. It also includes a comprehensive risk assessment, an information security assessment, and proposed changes to the Business Continuity Plan (BCP). Furthermore, the report outlines a SharePoint migration plan, addressing critical points and potential issues. The architecture leverages microservices and considers AWS’s hybrid capabilities. The report discusses various deployment considerations like optimization, augmentation, and migration to the cloud, alongside the strengths and weaknesses of public cloud. The report also addresses security concerns and integration challenges associated with hybrid cloud environments, ensuring a secure and efficient cloud migration. The report recommends the utilization of Deep Security quick start template from AWS Marketplace for data security and managing hybrid cloud performance.

Security Management and Migration
Assignment-4
Name:
Register Number:
Assignment-4
Name:
Register Number:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction............................................................................................................................................................ 1
2. Required Cloud Architecture................................................................................................................................... 1
2.1 Description of Architectures and Reason for Deploying.......................................................................................1
2.2 Benefits and Issues related to Deployment...........................................................................................................7
3. Risk Assessment...................................................................................................................................................... 9
4. Information Security Assessment........................................................................................................................... 15
5. Changes to BCP..................................................................................................................................................... 15
6. Hybrid Cloud Administration and SLA Management............................................................................................17
7. SharePoint Migration Planning.............................................................................................................................19
7.1 Migration Plan.................................................................................................................................................. 19
7.2 Migration Plan’s Critical Points and Issues.......................................................................................................22
8. Conclusion............................................................................................................................................................. 23
References...................................................................................................................................................................... 24
1. Introduction............................................................................................................................................................ 1
2. Required Cloud Architecture................................................................................................................................... 1
2.1 Description of Architectures and Reason for Deploying.......................................................................................1
2.2 Benefits and Issues related to Deployment...........................................................................................................7
3. Risk Assessment...................................................................................................................................................... 9
4. Information Security Assessment........................................................................................................................... 15
5. Changes to BCP..................................................................................................................................................... 15
6. Hybrid Cloud Administration and SLA Management............................................................................................17
7. SharePoint Migration Planning.............................................................................................................................19
7.1 Migration Plan.................................................................................................................................................. 19
7.2 Migration Plan’s Critical Points and Issues.......................................................................................................22
8. Conclusion............................................................................................................................................................. 23
References...................................................................................................................................................................... 24

1. Introduction
The Company named Regional Gardens Ltd., is considered in this report for which a
strategic proposal is required to meet the business requirement. It is a company which runs
various gardening enterprises. It wishes to improve its current ICT infrastructure, with respect to
data storage, monitoring, data flexibility and responsiveness. It looks forward to have a new
manageable cloud based infrastructure.
The objective of this report is to provide a specific cloud computing architecture for
meeting the business needs, where various cloud computing architectures will be compared and
evaluated. The ICT risk management for the cloud computing delivery plan will be represented.
The Information Security assessment will be carried out. Migration plan, its critical points and
issues will be discussed.
2. Required Cloud Architecture
The cloud computing environment helps the grid computing to provide physical and
virtual servers for running the grid applications, which carry out various small tasks (Rouse,
2018). The cloud computing requires management like, changing requests, provisioning,
reimaging, deprovisioning, monitoring and rebalancing of workload. The cloud computing
system is divided into front-end and back-end, which are connected with the help of a network
i.e., internet. There is a central server which administers the system, by managing tasking like,
demands of the clients and traffic monitoring and ensuring everything works smoothly (Sareen,
2013).
For assisting the Regional Gardens for meeting the Board’s strategy, I would employ
Hybrid Cloud Architecture.
2.1 Description of Architectures and Reason for Deploying
For a cloud based solution, the Cloud Computing Architecture is used which contains on
premise and cloud resources. It ensures to facilitate communication between the stakeholders,
and related to high-level design early decisions are documented and can help to reuse the
components of the design ("Cloud Computing Architecture", 2010).
Today, all the organizations are adopting Hybrid cloud architecture for maintaining
control on the privately managed internal cloud, while depending on the public cloud as required
(Waite, 2017).
1
The Company named Regional Gardens Ltd., is considered in this report for which a
strategic proposal is required to meet the business requirement. It is a company which runs
various gardening enterprises. It wishes to improve its current ICT infrastructure, with respect to
data storage, monitoring, data flexibility and responsiveness. It looks forward to have a new
manageable cloud based infrastructure.
The objective of this report is to provide a specific cloud computing architecture for
meeting the business needs, where various cloud computing architectures will be compared and
evaluated. The ICT risk management for the cloud computing delivery plan will be represented.
The Information Security assessment will be carried out. Migration plan, its critical points and
issues will be discussed.
2. Required Cloud Architecture
The cloud computing environment helps the grid computing to provide physical and
virtual servers for running the grid applications, which carry out various small tasks (Rouse,
2018). The cloud computing requires management like, changing requests, provisioning,
reimaging, deprovisioning, monitoring and rebalancing of workload. The cloud computing
system is divided into front-end and back-end, which are connected with the help of a network
i.e., internet. There is a central server which administers the system, by managing tasking like,
demands of the clients and traffic monitoring and ensuring everything works smoothly (Sareen,
2013).
For assisting the Regional Gardens for meeting the Board’s strategy, I would employ
Hybrid Cloud Architecture.
2.1 Description of Architectures and Reason for Deploying
For a cloud based solution, the Cloud Computing Architecture is used which contains on
premise and cloud resources. It ensures to facilitate communication between the stakeholders,
and related to high-level design early decisions are documented and can help to reuse the
components of the design ("Cloud Computing Architecture", 2010).
Today, all the organizations are adopting Hybrid cloud architecture for maintaining
control on the privately managed internal cloud, while depending on the public cloud as required
(Waite, 2017).
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
The microservices ensures that the applications become highly resilient, agile and
scalable (Ajluni, 2016).
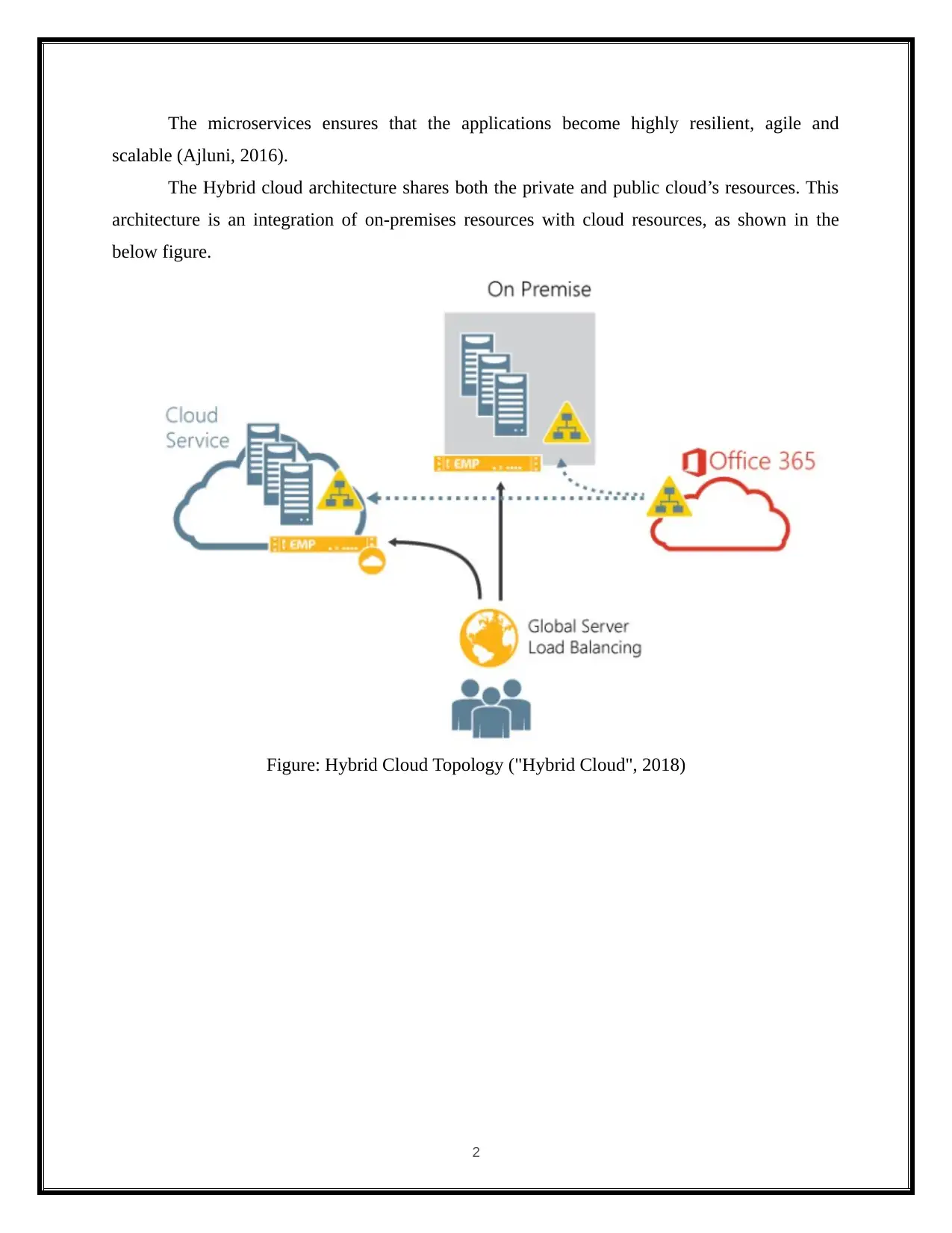
The Hybrid cloud architecture shares both the private and public cloud’s resources. This
architecture is an integration of on-premises resources with cloud resources, as shown in the
below figure.
Figure: Hybrid Cloud Topology ("Hybrid Cloud", 2018)
2
scalable (Ajluni, 2016).
The Hybrid cloud architecture shares both the private and public cloud’s resources. This
architecture is an integration of on-premises resources with cloud resources, as shown in the
below figure.
Figure: Hybrid Cloud Topology ("Hybrid Cloud", 2018)
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
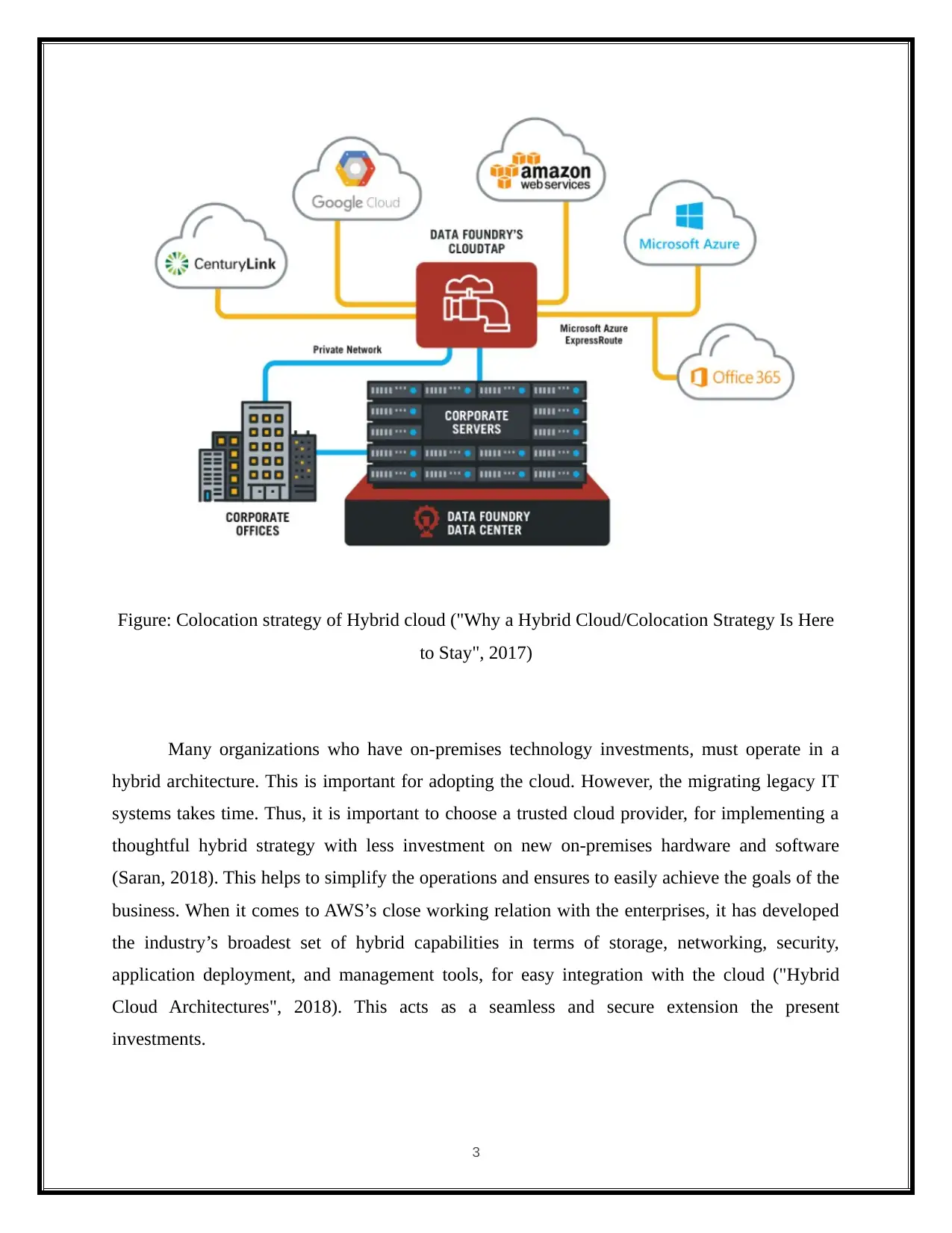
Figure: Colocation strategy of Hybrid cloud ("Why a Hybrid Cloud/Colocation Strategy Is Here
to Stay", 2017)
Many organizations who have on-premises technology investments, must operate in a
hybrid architecture. This is important for adopting the cloud. However, the migrating legacy IT
systems takes time. Thus, it is important to choose a trusted cloud provider, for implementing a
thoughtful hybrid strategy with less investment on new on-premises hardware and software
(Saran, 2018). This helps to simplify the operations and ensures to easily achieve the goals of the
business. When it comes to AWS’s close working relation with the enterprises, it has developed
the industry’s broadest set of hybrid capabilities in terms of storage, networking, security,
application deployment, and management tools, for easy integration with the cloud ("Hybrid
Cloud Architectures", 2018). This acts as a seamless and secure extension the present
investments.
3
to Stay", 2017)
Many organizations who have on-premises technology investments, must operate in a
hybrid architecture. This is important for adopting the cloud. However, the migrating legacy IT
systems takes time. Thus, it is important to choose a trusted cloud provider, for implementing a
thoughtful hybrid strategy with less investment on new on-premises hardware and software
(Saran, 2018). This helps to simplify the operations and ensures to easily achieve the goals of the
business. When it comes to AWS’s close working relation with the enterprises, it has developed
the industry’s broadest set of hybrid capabilities in terms of storage, networking, security,
application deployment, and management tools, for easy integration with the cloud ("Hybrid
Cloud Architectures", 2018). This acts as a seamless and secure extension the present
investments.
3
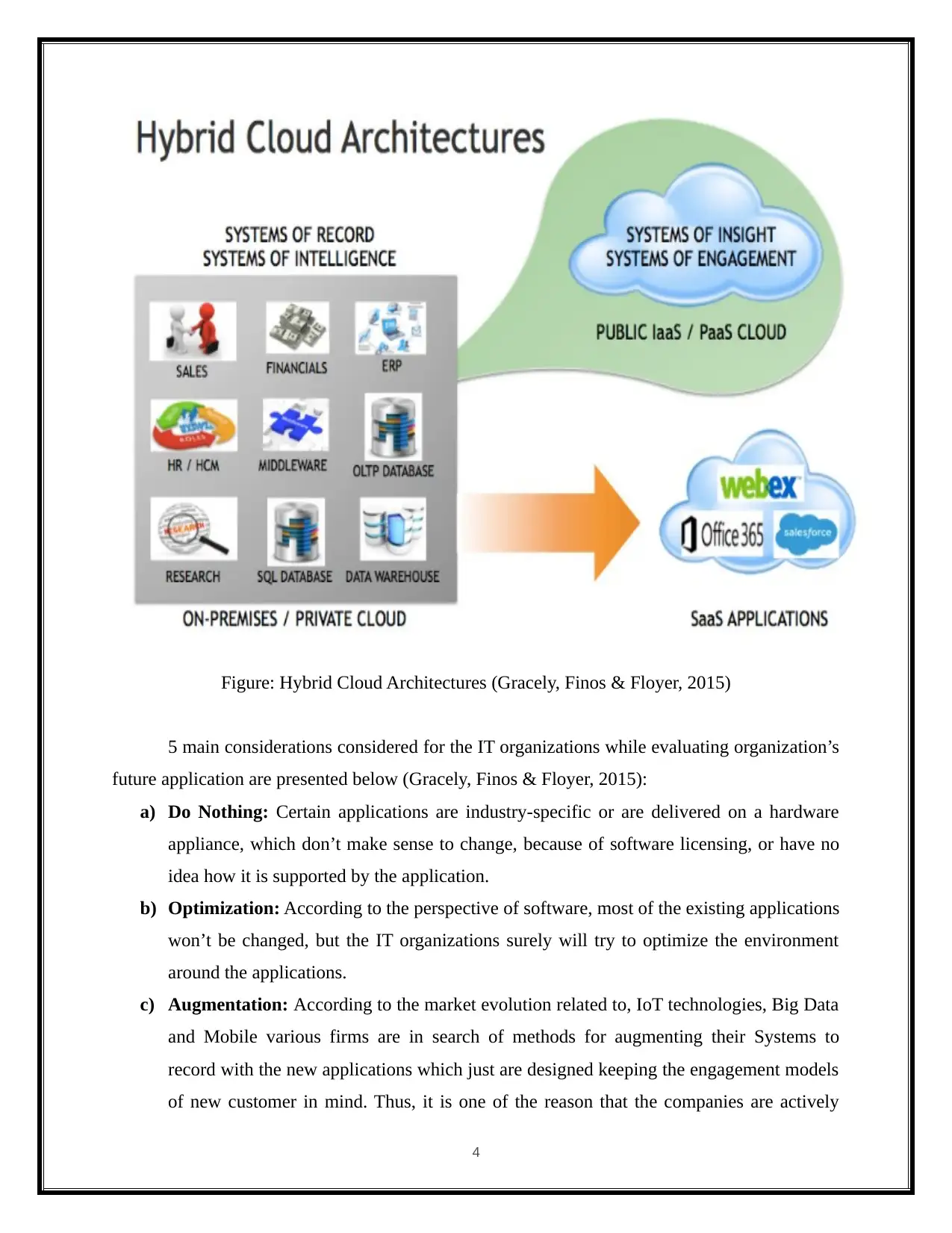
Figure: Hybrid Cloud Architectures (Gracely, Finos & Floyer, 2015)
5 main considerations considered for the IT organizations while evaluating organization’s
future application are presented below (Gracely, Finos & Floyer, 2015):
a) Do Nothing: Certain applications are industry-specific or are delivered on a hardware
appliance, which don’t make sense to change, because of software licensing, or have no
idea how it is supported by the application.
b) Optimization: According to the perspective of software, most of the existing applications
won’t be changed, but the IT organizations surely will try to optimize the environment
around the applications.
c) Augmentation: According to the market evolution related to, IoT technologies, Big Data
and Mobile various firms are in search of methods for augmenting their Systems to
record with the new applications which just are designed keeping the engagement models
of new customer in mind. Thus, it is one of the reason that the companies are actively
4
5 main considerations considered for the IT organizations while evaluating organization’s
future application are presented below (Gracely, Finos & Floyer, 2015):
a) Do Nothing: Certain applications are industry-specific or are delivered on a hardware
appliance, which don’t make sense to change, because of software licensing, or have no
idea how it is supported by the application.
b) Optimization: According to the perspective of software, most of the existing applications
won’t be changed, but the IT organizations surely will try to optimize the environment
around the applications.
c) Augmentation: According to the market evolution related to, IoT technologies, Big Data
and Mobile various firms are in search of methods for augmenting their Systems to
record with the new applications which just are designed keeping the engagement models
of new customer in mind. Thus, it is one of the reason that the companies are actively
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

researching on the Cloud Native applications. Most of the firms are employing the in-
house developers for building such applications, because these applications can bring
new change for the business. Moreover, augmentation is a section where the companies
create integrations between SaaS applications and their in-house Systems of Record, to
gain the opportunities for effectively aligning the application development team and the
operations team.
d) Migrate to Cloud: Despite the IT leaders understanding on the importance of Cloud
Computing, still evaluation exists on whether it makes sense to migrate the applications
to a Private Cloud or a Public Cloud. On the other hand, with the growth of Public Cloud,
most of the IT organizations are still evolving their Cloud Computing skills. For a Private
Cloud, the migrating applications permits the IT organizations to maintain the present
performance including the characteristics of security, during local access to the
application data. However, it is proved that such migrations are highly cost effective. The
Private Cloud projects concentrate to deliver automated infrastructure and services which
imitates what could be taken from the Public Clouds like, AWS or Azure.
Figure: Public Cloud’s Strengths and Weaknesses
e) Replacing: Since 15 years, the companies utilize technology for increasing their business
and productivity of employees. But, as time passes the technologies loses its effectiveness
for the business. This increases the company’s interest to replace their previous
5
house developers for building such applications, because these applications can bring
new change for the business. Moreover, augmentation is a section where the companies
create integrations between SaaS applications and their in-house Systems of Record, to
gain the opportunities for effectively aligning the application development team and the
operations team.
d) Migrate to Cloud: Despite the IT leaders understanding on the importance of Cloud
Computing, still evaluation exists on whether it makes sense to migrate the applications
to a Private Cloud or a Public Cloud. On the other hand, with the growth of Public Cloud,
most of the IT organizations are still evolving their Cloud Computing skills. For a Private
Cloud, the migrating applications permits the IT organizations to maintain the present
performance including the characteristics of security, during local access to the
application data. However, it is proved that such migrations are highly cost effective. The
Private Cloud projects concentrate to deliver automated infrastructure and services which
imitates what could be taken from the Public Clouds like, AWS or Azure.
Figure: Public Cloud’s Strengths and Weaknesses
e) Replacing: Since 15 years, the companies utilize technology for increasing their business
and productivity of employees. But, as time passes the technologies loses its effectiveness
for the business. This increases the company’s interest to replace their previous
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
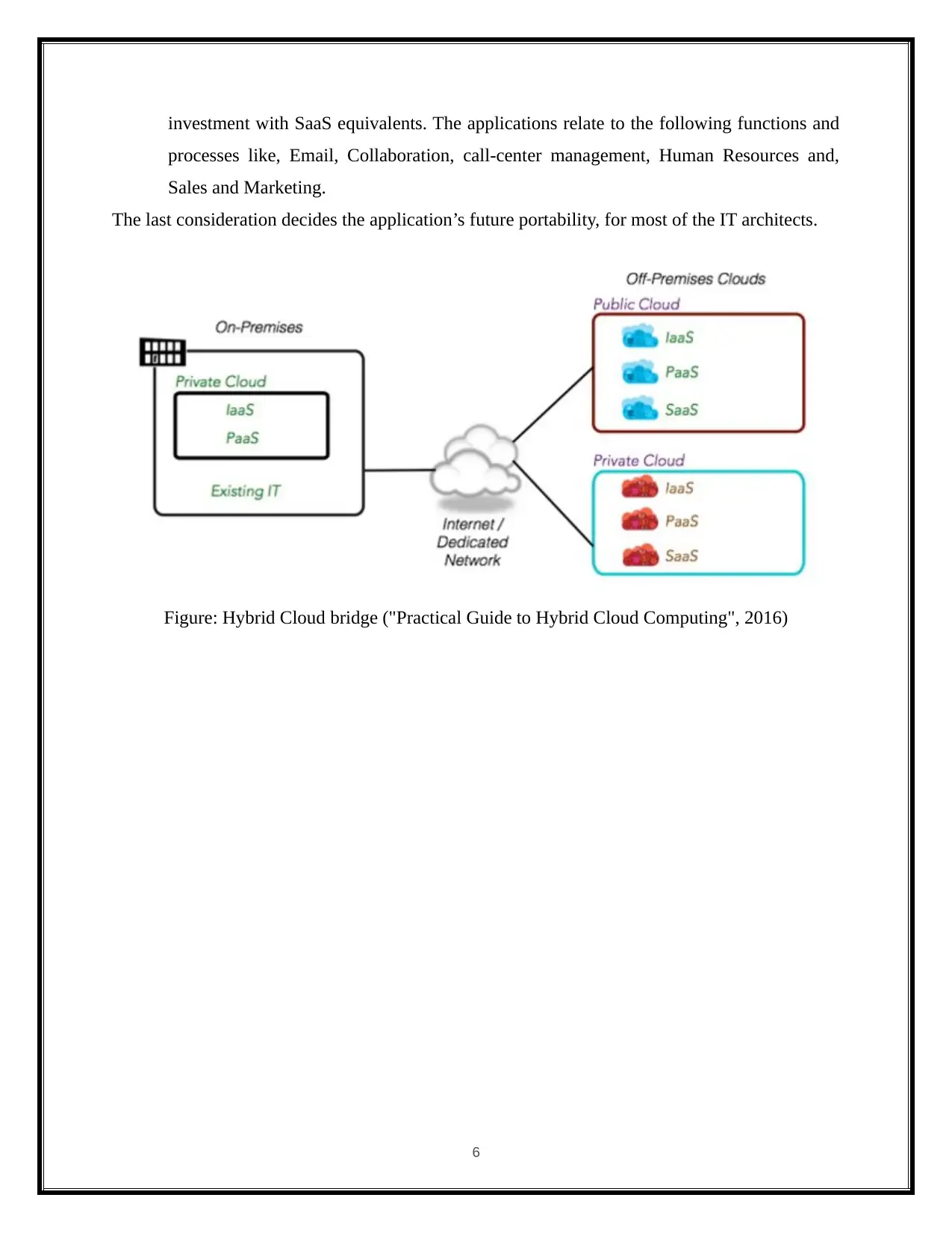
investment with SaaS equivalents. The applications relate to the following functions and
processes like, Email, Collaboration, call-center management, Human Resources and,
Sales and Marketing.
The last consideration decides the application’s future portability, for most of the IT architects.
Figure: Hybrid Cloud bridge ("Practical Guide to Hybrid Cloud Computing", 2016)
6
processes like, Email, Collaboration, call-center management, Human Resources and,
Sales and Marketing.
The last consideration decides the application’s future portability, for most of the IT architects.
Figure: Hybrid Cloud bridge ("Practical Guide to Hybrid Cloud Computing", 2016)
6
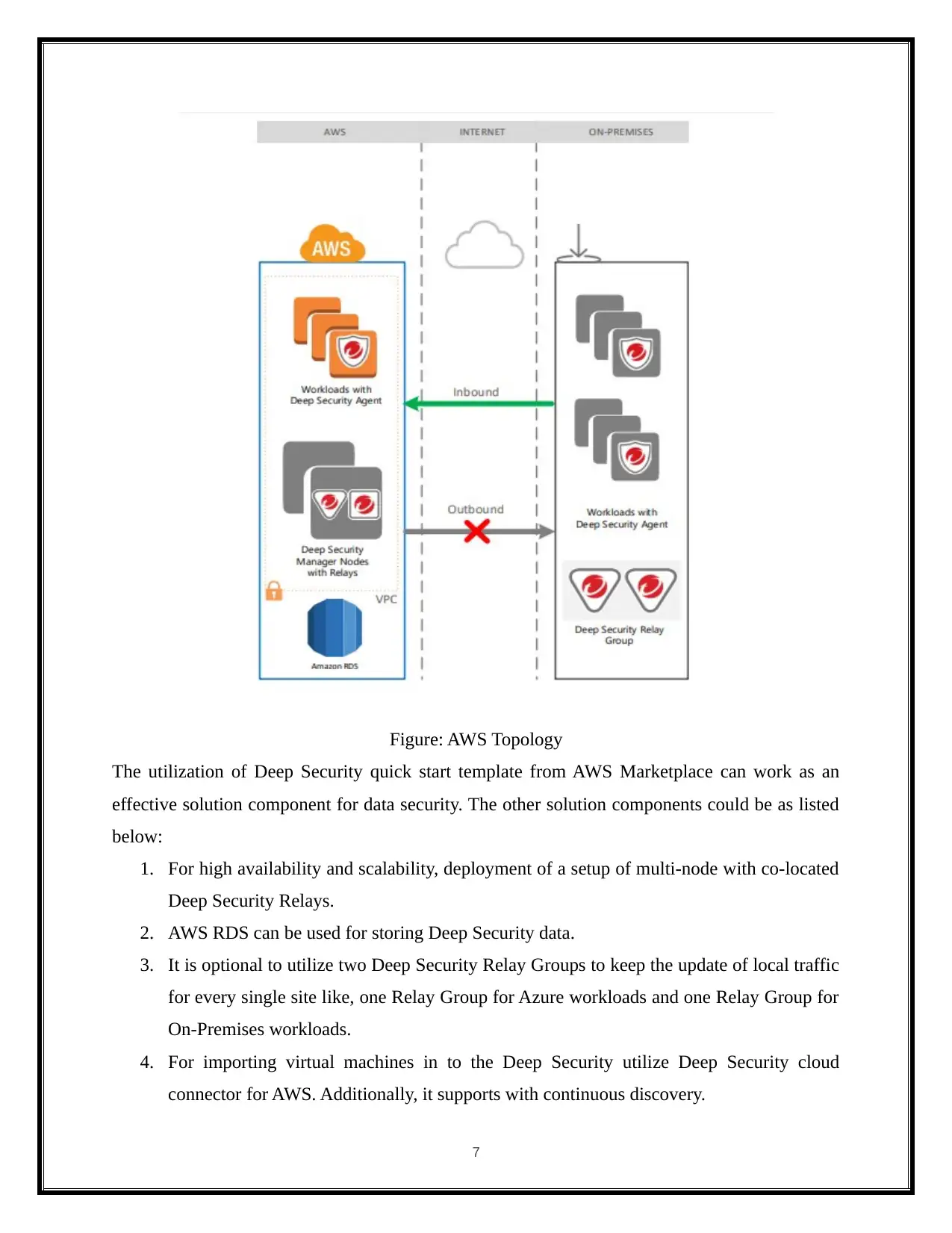
Figure: AWS Topology
The utilization of Deep Security quick start template from AWS Marketplace can work as an
effective solution component for data security. The other solution components could be as listed
below:
1. For high availability and scalability, deployment of a setup of multi-node with co-located
Deep Security Relays.
2. AWS RDS can be used for storing Deep Security data.
3. It is optional to utilize two Deep Security Relay Groups to keep the update of local traffic
for every single site like, one Relay Group for Azure workloads and one Relay Group for
On-Premises workloads.
4. For importing virtual machines in to the Deep Security utilize Deep Security cloud
connector for AWS. Additionally, it supports with continuous discovery.
7
The utilization of Deep Security quick start template from AWS Marketplace can work as an
effective solution component for data security. The other solution components could be as listed
below:
1. For high availability and scalability, deployment of a setup of multi-node with co-located
Deep Security Relays.
2. AWS RDS can be used for storing Deep Security data.
3. It is optional to utilize two Deep Security Relay Groups to keep the update of local traffic
for every single site like, one Relay Group for Azure workloads and one Relay Group for
On-Premises workloads.
4. For importing virtual machines in to the Deep Security utilize Deep Security cloud
connector for AWS. Additionally, it supports with continuous discovery.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The network connectivity is as follows ("CloudOps: 6 best ways to manage hybrid cloud
performance", 2018):
a) Use Deep Security Manager nodes with Public DNS to make them accessible over the
internet.
b) For Manager and agent communication, utilize Agent Initiated communication mode.
c) Network access is not needed from AWS to On-premises.
d) Allow Deep Security Manager, Deep Security Relays and Deep Security Agents internet
access for software and security updates.
e) For necessary flow of communication between the components, utilize the rules of VPC
Security Group.
For effective flexibility in deployment for Hybrid cloud, the Deep Security 10 supports
with hybrid policy management and auto-scaling. The Deep Security is mainly designed for
supporting traditional IT security model and advanced DevSecOps.
The company will be benefited by the help cloud migration support provider, in making
smooth transition when adopting a hybrid cloud environment (Long, 2018).
2.2 Benefits and Issues related to Deployment
The benefits of the deployment of the Hybrid cloud architecture includes ("7 benefits of a
Hybrid Cloud solution", 2018) (Tracy, 2016):
1) It ensures to have business continuity, in the business operations. Business
continuity not just related to back up of data or a recovery plan instead it a
capacity of the business to continue its business even while a failure ("TDWI
Checklist Report: Data Management Best Practices for Cloud and Hybrid
Architectures", 2018).
2) Increased speed for marketing.
3) Scalability
4) Provides direct accessibility of data.
5) Secure systems (Perez, 2018).
6) More opportunity for innovation
7) It improves the connectivity.
8
performance", 2018):
a) Use Deep Security Manager nodes with Public DNS to make them accessible over the
internet.
b) For Manager and agent communication, utilize Agent Initiated communication mode.
c) Network access is not needed from AWS to On-premises.
d) Allow Deep Security Manager, Deep Security Relays and Deep Security Agents internet
access for software and security updates.
e) For necessary flow of communication between the components, utilize the rules of VPC
Security Group.
For effective flexibility in deployment for Hybrid cloud, the Deep Security 10 supports
with hybrid policy management and auto-scaling. The Deep Security is mainly designed for
supporting traditional IT security model and advanced DevSecOps.
The company will be benefited by the help cloud migration support provider, in making
smooth transition when adopting a hybrid cloud environment (Long, 2018).
2.2 Benefits and Issues related to Deployment
The benefits of the deployment of the Hybrid cloud architecture includes ("7 benefits of a
Hybrid Cloud solution", 2018) (Tracy, 2016):
1) It ensures to have business continuity, in the business operations. Business
continuity not just related to back up of data or a recovery plan instead it a
capacity of the business to continue its business even while a failure ("TDWI
Checklist Report: Data Management Best Practices for Cloud and Hybrid
Architectures", 2018).
2) Increased speed for marketing.
3) Scalability
4) Provides direct accessibility of data.
5) Secure systems (Perez, 2018).
6) More opportunity for innovation
7) It improves the connectivity.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8) It ensures risk management.
9) It provided network optimization.
10) Enables expansion of capacity.
The issues related to the deployment of the Hybrid cloud architecture includes (Tracy,
2016) (Tran, 2018):
1) Cost
Building a private cloud for the enterprise costs more when compared to the public cloud.
High usage of the public cloud resources could increase unexpectedly bills of high
charges which might not be part of the plan. Thus, it is necessary to outline a specific
budget for the hybrid cloud project.
2) Security
Cloud computing can surely face some attacks. It requires proper precautions to secure
the data correctly and must ensure that it is controlled and maintained by an appropriate
person (De Laine, 2017).
3) Data and application integration
There is symbolic relationship when it comes to applications and data, where without
each other they are of no use. Most of the times both application and data are chained
together. While its storage topic is discussed, it is required to enquire about its
infrastructure. For instance, if the application is in the private cloud whereas its data is in
the on-premise data center, then can the data be accessed remotely in this application?
Copy data virtualization technologies could decouple the data from the infrastructure and
can make this issue, least problematic.
4) Compatibility has bigger issues while developing a hybrid cloud. One of the challenge in
building the Hybrid cloud is compatibility across the infrastructure. When there are
infrastructures of dual levels, like the private cloud which is controlled by the company
and the public cloud which is not controlled by the company, then there are possibilities
to run different stacks.
5) Networking issues, such as will the cloud have highly active application present in it?
The usage of the bandwidth is important to be considered on a network and similarly it is
necessary to check whether there might be any issues in bottlenecking the rest of the
9
9) It provided network optimization.
10) Enables expansion of capacity.
The issues related to the deployment of the Hybrid cloud architecture includes (Tracy,
2016) (Tran, 2018):
1) Cost
Building a private cloud for the enterprise costs more when compared to the public cloud.
High usage of the public cloud resources could increase unexpectedly bills of high
charges which might not be part of the plan. Thus, it is necessary to outline a specific
budget for the hybrid cloud project.
2) Security
Cloud computing can surely face some attacks. It requires proper precautions to secure
the data correctly and must ensure that it is controlled and maintained by an appropriate
person (De Laine, 2017).
3) Data and application integration
There is symbolic relationship when it comes to applications and data, where without
each other they are of no use. Most of the times both application and data are chained
together. While its storage topic is discussed, it is required to enquire about its
infrastructure. For instance, if the application is in the private cloud whereas its data is in
the on-premise data center, then can the data be accessed remotely in this application?
Copy data virtualization technologies could decouple the data from the infrastructure and
can make this issue, least problematic.
4) Compatibility has bigger issues while developing a hybrid cloud. One of the challenge in
building the Hybrid cloud is compatibility across the infrastructure. When there are
infrastructures of dual levels, like the private cloud which is controlled by the company
and the public cloud which is not controlled by the company, then there are possibilities
to run different stacks.
5) Networking issues, such as will the cloud have highly active application present in it?
The usage of the bandwidth is important to be considered on a network and similarly it is
necessary to check whether there might be any issues in bottlenecking the rest of the
9
applications. This is one of the question which should be asked about hybrid integration
during network designing.
Similar to all the IT projects, developing hybrid cloud for an enterprise could bring both
advantages and also challenges. If proper planning is done, then the organizations can surely
decrease the issues and increase the benefits for the organization.
3. Risk Assessment
The possible risks associated with the Hybrid cloud and microservices strategies are
listed below (Tech, 2016) (Shacklett, 2016) ("17 Hybrid Cloud Security Threats and How To Fix
Them", 2018) (Hatter, 2014):
Sl.
No.
Possible Risks for
Hybrid cloud and
microservices
Description Possible Control
For the Risk
1. IT architecture
design
The architecture can be of cloud, private,
on-premises must be managed well, for
smoothly running the end-to-end
infrastructure.
2. Coordination of
cloud procurement
with end business
users
The Haphazard method is a worst method
for entering into a hybrid cloud strategy.
Because, the haphazard circumstance is
created if the end-user departments and
independently contract IT for cloud
services. It is necessary to have a mix of
public cloud, private cloud, and on-
premises IT and no one who is
accountable for overall coordination and
performance of these investments. This
type of practice brings more number of
risks along with increased inefficiency.
3. Management of In the data centers of many organizations, Rely on a trusted
10
during network designing.
Similar to all the IT projects, developing hybrid cloud for an enterprise could bring both
advantages and also challenges. If proper planning is done, then the organizations can surely
decrease the issues and increase the benefits for the organization.
3. Risk Assessment
The possible risks associated with the Hybrid cloud and microservices strategies are
listed below (Tech, 2016) (Shacklett, 2016) ("17 Hybrid Cloud Security Threats and How To Fix
Them", 2018) (Hatter, 2014):
Sl.
No.
Possible Risks for
Hybrid cloud and
microservices
Description Possible Control
For the Risk
1. IT architecture
design
The architecture can be of cloud, private,
on-premises must be managed well, for
smoothly running the end-to-end
infrastructure.
2. Coordination of
cloud procurement
with end business
users
The Haphazard method is a worst method
for entering into a hybrid cloud strategy.
Because, the haphazard circumstance is
created if the end-user departments and
independently contract IT for cloud
services. It is necessary to have a mix of
public cloud, private cloud, and on-
premises IT and no one who is
accountable for overall coordination and
performance of these investments. This
type of practice brings more number of
risks along with increased inefficiency.
3. Management of In the data centers of many organizations, Rely on a trusted
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 31
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





