Information Security Management in Healthcare: Research Report
VerifiedAdded on 2020/03/16
|16
|4641
|349
Report
AI Summary
This group research report comprehensively examines the management of information security within healthcare systems. It begins by highlighting the critical importance of information security and privacy in the context of increasing digitalization and data consolidation in healthcare. The report...

Group Research Report
MANAGEMENT OF INFORMATION SECURITY
Student Name
Student Number
E-mail Address
Student Name
Student Number
E-mail Address
ABSTRACT
Information Security and Network Database privacy is a major issue in today’s world. The
increase in regulation, adoption of digital patient records, provided consolidation and thus the
increase in the requirement for data and information in between patients, providers and
payers. At every point the main target ifs toward the betterment of information security and
management of the system network. There has been many critical survey of research
literature on healthcare privacy, information system and its security. This survey has been
published for both non-informationsecurities, information security disciplines that may
include health datasets, public and private data database, laws, medicine information and
many more. Though this incremental adoption of these electronic and digital media in
healthcare also creates many security risks and violation of privacy in the organization.
Keywords:
Information Security, Healthcare, Privacy Risk, Database, Research Literature.
MANAGEMENT OF INFORMATION SECURITY
Student Name
Student Number
E-mail Address
Student Name
Student Number
E-mail Address
ABSTRACT
Information Security and Network Database privacy is a major issue in today’s world. The
increase in regulation, adoption of digital patient records, provided consolidation and thus the
increase in the requirement for data and information in between patients, providers and
payers. At every point the main target ifs toward the betterment of information security and
management of the system network. There has been many critical survey of research
literature on healthcare privacy, information system and its security. This survey has been
published for both non-informationsecurities, information security disciplines that may
include health datasets, public and private data database, laws, medicine information and
many more. Though this incremental adoption of these electronic and digital media in
healthcare also creates many security risks and violation of privacy in the organization.
Keywords:
Information Security, Healthcare, Privacy Risk, Database, Research Literature.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
ABSTRACT...............................................................................................................................1
INTRODUCTION......................................................................................................................4
1. Data Storage Infrastructure....................................................................................................5
2. Network Infrastructure...........................................................................................................6
3. Privacy and Security Protection Mechanisms........................................................................7
3.1. Health Information Privacy Regulations.........................................................................8
3.2. Threats to Information Privacy........................................................................................8
4. Policies that Ensure Operations Security...............................................................................9
4.1. Providing a Safe Workplace............................................................................................9
5. Potential Risks......................................................................................................................10
6. Disaster Recovery................................................................................................................11
CONCLUSION........................................................................................................................12
REFERENCES.........................................................................................................................13
ABSTRACT...............................................................................................................................1
INTRODUCTION......................................................................................................................4
1. Data Storage Infrastructure....................................................................................................5
2. Network Infrastructure...........................................................................................................6
3. Privacy and Security Protection Mechanisms........................................................................7
3.1. Health Information Privacy Regulations.........................................................................8
3.2. Threats to Information Privacy........................................................................................8
4. Policies that Ensure Operations Security...............................................................................9
4.1. Providing a Safe Workplace............................................................................................9
5. Potential Risks......................................................................................................................10
6. Disaster Recovery................................................................................................................11
CONCLUSION........................................................................................................................12
REFERENCES.........................................................................................................................13

INTRODUCTION
A Cloud storage infrastructure is basically the combination of hardware and software
framework that supports requirement of the public and private storage in cloud services.A
few associations may need the control that private cloud frameworks offer, however would
prefer not to management of lodging, running and keeping up an in-house distributed storage
foundation. There is a chance that they can contract with a distributed storage specialist to
help cloud operations. In this provisioning model, that refers to the Infrastructure-as-a-
Service (IaaS), the specialist organization possesses the equipment like the storage, servers
and systems administration segments. The customer ordinarily is charged on a for each
utilization premise. A disaster recovery plan (DRP) thus depicted as a structured approach
along with instructions in order as a responding to any unplanned incident. This well-
organized process helps in maintaining the prevention of thedisaster,such that the association
can keep track on the operation or the rapidly continue to target the goals. Commonly,
management approval of recuperation arranging includes an examination of business
procedures and coherence needs. Administration endorsement of recuperation procedures is
vital. All techniques ought to line up with the association's objectives. When disaster
recovery systems have been created and endorsed, they can be converted into calamity
recuperation designs.
In this report we are going to discuss about the role of business continuity and disaster
recovery plans to recover the information and operational systems when in the case of
systems and hardware failure. Analysis the vulnerabilities and threats of information security
and thus determining appropriate controls which can be applied for mitigation of the potential
risks. Designing an appropriate medical data storage infrastructure and a network
infrastructure and explaining the ethical and privacy issues that plays vital role in managing
the information security communication in a health organization. Explaining the risks
associated with the infrastructure development and how these disasters can be managed and
recovered by some potential planning in the system.
A Cloud storage infrastructure is basically the combination of hardware and software
framework that supports requirement of the public and private storage in cloud services.A
few associations may need the control that private cloud frameworks offer, however would
prefer not to management of lodging, running and keeping up an in-house distributed storage
foundation. There is a chance that they can contract with a distributed storage specialist to
help cloud operations. In this provisioning model, that refers to the Infrastructure-as-a-
Service (IaaS), the specialist organization possesses the equipment like the storage, servers
and systems administration segments. The customer ordinarily is charged on a for each
utilization premise. A disaster recovery plan (DRP) thus depicted as a structured approach
along with instructions in order as a responding to any unplanned incident. This well-
organized process helps in maintaining the prevention of thedisaster,such that the association
can keep track on the operation or the rapidly continue to target the goals. Commonly,
management approval of recuperation arranging includes an examination of business
procedures and coherence needs. Administration endorsement of recuperation procedures is
vital. All techniques ought to line up with the association's objectives. When disaster
recovery systems have been created and endorsed, they can be converted into calamity
recuperation designs.
In this report we are going to discuss about the role of business continuity and disaster
recovery plans to recover the information and operational systems when in the case of
systems and hardware failure. Analysis the vulnerabilities and threats of information security
and thus determining appropriate controls which can be applied for mitigation of the potential
risks. Designing an appropriate medical data storage infrastructure and a network
infrastructure and explaining the ethical and privacy issues that plays vital role in managing
the information security communication in a health organization. Explaining the risks
associated with the infrastructure development and how these disasters can be managed and
recovered by some potential planning in the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
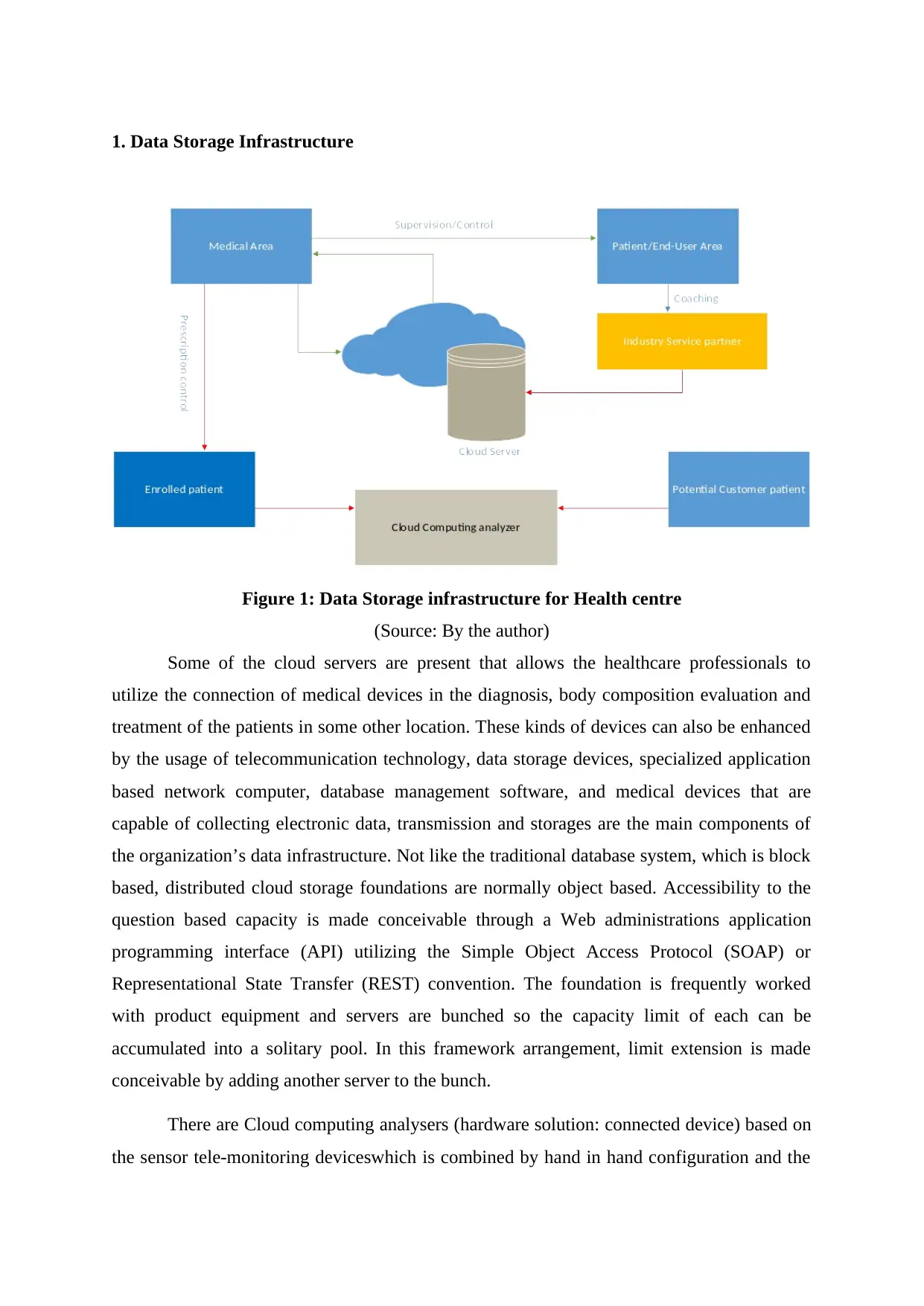
1. Data Storage Infrastructure
Figure 1: Data Storage infrastructure for Health centre
(Source: By the author)
Some of the cloud servers are present that allows the healthcare professionals to
utilize the connection of medical devices in the diagnosis, body composition evaluation and
treatment of the patients in some other location. These kinds of devices can also be enhanced
by the usage of telecommunication technology, data storage devices, specialized application
based network computer, database management software, and medical devices that are
capable of collecting electronic data, transmission and storages are the main components of
the organization’s data infrastructure. Not like the traditional database system, which is block
based, distributed cloud storage foundations are normally object based. Accessibility to the
question based capacity is made conceivable through a Web administrations application
programming interface (API) utilizing the Simple Object Access Protocol (SOAP) or
Representational State Transfer (REST) convention. The foundation is frequently worked
with product equipment and servers are bunched so the capacity limit of each can be
accumulated into a solitary pool. In this framework arrangement, limit extension is made
conceivable by adding another server to the bunch.
There are Cloud computing analysers (hardware solution: connected device) based on
the sensor tele-monitoring deviceswhich is combined by hand in hand configuration and the
Figure 1: Data Storage infrastructure for Health centre
(Source: By the author)
Some of the cloud servers are present that allows the healthcare professionals to
utilize the connection of medical devices in the diagnosis, body composition evaluation and
treatment of the patients in some other location. These kinds of devices can also be enhanced
by the usage of telecommunication technology, data storage devices, specialized application
based network computer, database management software, and medical devices that are
capable of collecting electronic data, transmission and storages are the main components of
the organization’s data infrastructure. Not like the traditional database system, which is block
based, distributed cloud storage foundations are normally object based. Accessibility to the
question based capacity is made conceivable through a Web administrations application
programming interface (API) utilizing the Simple Object Access Protocol (SOAP) or
Representational State Transfer (REST) convention. The foundation is frequently worked
with product equipment and servers are bunched so the capacity limit of each can be
accumulated into a solitary pool. In this framework arrangement, limit extension is made
conceivable by adding another server to the bunch.
There are Cloud computing analysers (hardware solution: connected device) based on
the sensor tele-monitoring deviceswhich is combined by hand in hand configuration and the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
data is linked by the multiband mobile modem links the data to proprietary of cloud server.
There are various software solution levels in the cloud infrastructure where in one level the
web based application offers highly privacy based protection and comfortable interface for
administrative and logistics solutions, in the next level that reports on body composition and
analysis in quality and third is the applications for the tablets and mobile phones such that to
make it easier to connect to people.
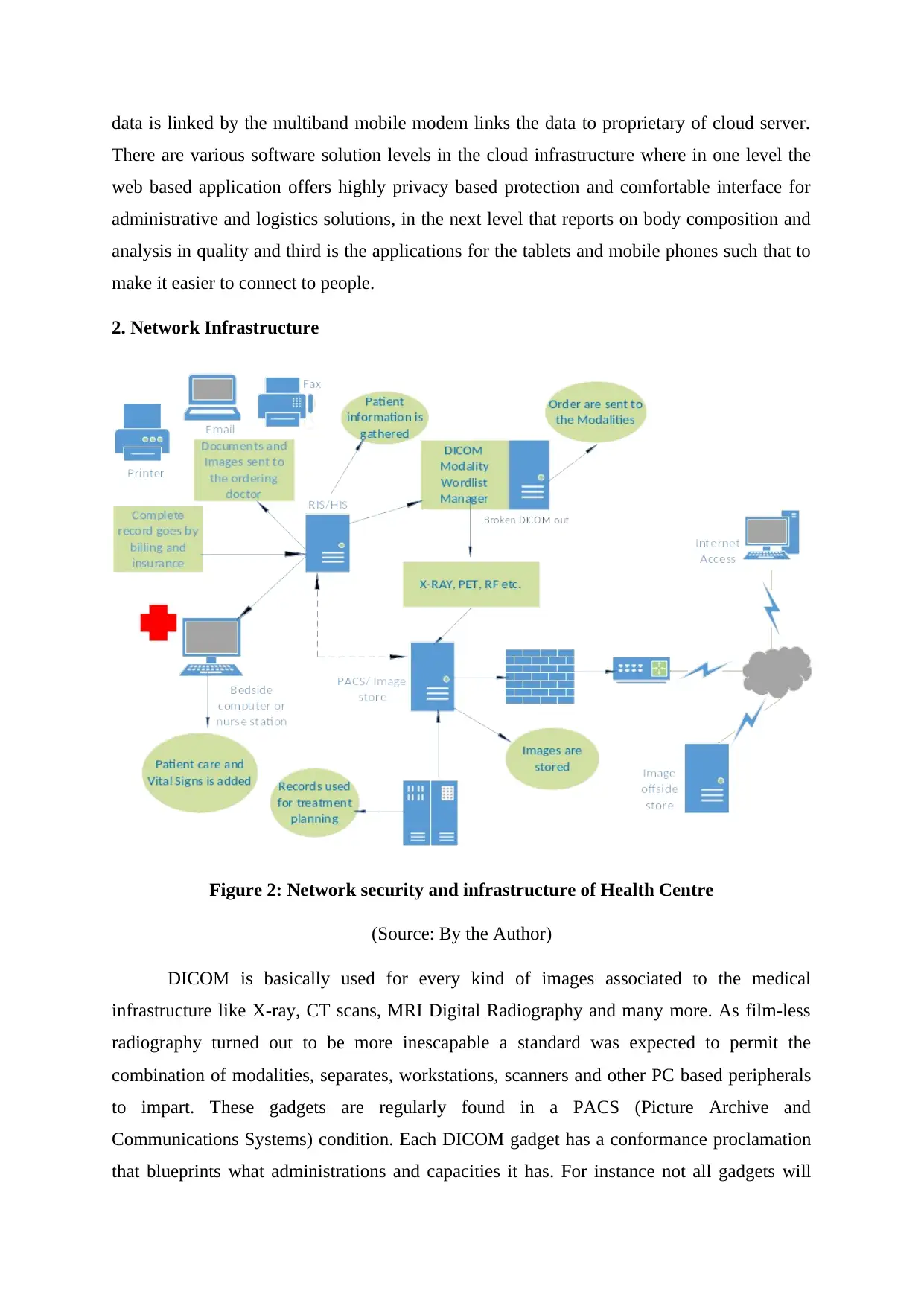
2. Network Infrastructure
Figure 2: Network security and infrastructure of Health Centre
(Source: By the Author)
DICOM is basically used for every kind of images associated to the medical
infrastructure like X-ray, CT scans, MRI Digital Radiography and many more. As film-less
radiography turned out to be more inescapable a standard was expected to permit the
combination of modalities, separates, workstations, scanners and other PC based peripherals
to impart. These gadgets are regularly found in a PACS (Picture Archive and
Communications Systems) condition. Each DICOM gadget has a conformance proclamation
that blueprints what administrations and capacities it has. For instance not all gadgets will
There are various software solution levels in the cloud infrastructure where in one level the
web based application offers highly privacy based protection and comfortable interface for
administrative and logistics solutions, in the next level that reports on body composition and
analysis in quality and third is the applications for the tablets and mobile phones such that to
make it easier to connect to people.
2. Network Infrastructure
Figure 2: Network security and infrastructure of Health Centre
(Source: By the Author)
DICOM is basically used for every kind of images associated to the medical
infrastructure like X-ray, CT scans, MRI Digital Radiography and many more. As film-less
radiography turned out to be more inescapable a standard was expected to permit the
combination of modalities, separates, workstations, scanners and other PC based peripherals
to impart. These gadgets are regularly found in a PACS (Picture Archive and
Communications Systems) condition. Each DICOM gadget has a conformance proclamation
that blueprints what administrations and capacities it has. For instance not all gadgets will

have the capacity to 'STORE' DICOM pictures, so they won't have that in their conformance
proclamation. The combination of workstations, scanners, servers, printers and system
equipment from numerous makers has been empowered by the DIACOM into a Picture
documenting and corresponding framework. The distinctive gadget accompanies DICOM
conformances articulations that unmistakably state which of DICOM classes. DICOM has
been broadly received by hospitals and is influencing advances in smaller applications to like
dental specialists' and specialists' workplaces.
Network infrastructure is defined basically the software and hardware combination of
the systems, which empowers the organizations availability, operation, correspondence and
even administration of an undertaking system. This delivers the correspondences on the path
operation
3. Privacy and Security Protection Mechanisms
Security is a basic representing guideline of the relationship between the doctor and
the patient successful part of medicinal services. Patient requires sharing data to their
respective doctors for encouraging experimental finding and assurance of treatment,
particular to ignore antagonistic medication connections. Like example, data can be utilized
to move forward proficiency inside medicinal services frameworks that drives and open
arrangement for the advancement of organization at state and government levels, moreover in
the way of research to the science of treatment. Though there is a chance of unveiling
essential data for instances of medical issues, like mental state conduction and HIV as their
revelation may result to social disgrace and segregation. Physical and physiological data of
patients has also been utilized for normal people to elected and state government level
medication with respect to the general wellbeing of administration centre accreditation,
therapeutic research, and for overseeing social and welfare frameworks. Additionally,
providers may share prosperity information through a nearby prosperity information
relationship to energize mind organizations. The complete plan of the protection and security
assurance instruments for the databases, programming, equipment and system of the
framework. The medical records of the patients are also imparted to payer relationship, for
instance, insurance, Medicare to legitimize portion of organizations rendered by specialists.
Social protection providers may use records to manage their operations, to study profit
quality, and to recognize quality change openings. This includes controlling physical security
and logical security of the system.
proclamation. The combination of workstations, scanners, servers, printers and system
equipment from numerous makers has been empowered by the DIACOM into a Picture
documenting and corresponding framework. The distinctive gadget accompanies DICOM
conformances articulations that unmistakably state which of DICOM classes. DICOM has
been broadly received by hospitals and is influencing advances in smaller applications to like
dental specialists' and specialists' workplaces.
Network infrastructure is defined basically the software and hardware combination of
the systems, which empowers the organizations availability, operation, correspondence and
even administration of an undertaking system. This delivers the correspondences on the path
operation
3. Privacy and Security Protection Mechanisms
Security is a basic representing guideline of the relationship between the doctor and
the patient successful part of medicinal services. Patient requires sharing data to their
respective doctors for encouraging experimental finding and assurance of treatment,
particular to ignore antagonistic medication connections. Like example, data can be utilized
to move forward proficiency inside medicinal services frameworks that drives and open
arrangement for the advancement of organization at state and government levels, moreover in
the way of research to the science of treatment. Though there is a chance of unveiling
essential data for instances of medical issues, like mental state conduction and HIV as their
revelation may result to social disgrace and segregation. Physical and physiological data of
patients has also been utilized for normal people to elected and state government level
medication with respect to the general wellbeing of administration centre accreditation,
therapeutic research, and for overseeing social and welfare frameworks. Additionally,
providers may share prosperity information through a nearby prosperity information
relationship to energize mind organizations. The complete plan of the protection and security
assurance instruments for the databases, programming, equipment and system of the
framework. The medical records of the patients are also imparted to payer relationship, for
instance, insurance, Medicare to legitimize portion of organizations rendered by specialists.
Social protection providers may use records to manage their operations, to study profit
quality, and to recognize quality change openings. This includes controlling physical security
and logical security of the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3.1. Health Information Privacy Regulations
The experience of US human services industry had some changes in a progressive manner.
Driven by propels in innovation and enactment of the data like, the 1973 Health Maintenance
Organizations Act. The data has been digitalized as an individual wellbeing, transmitted and dug out
for viable care arrangement. A new kind of risk to patient’s protection is to keep getting wrong
information. In perspective of these developing threats and the general objective of representing
practical medicinal service administrations to all residents, a few imperative government directions
have been authorized including the Privacy and Security Rules under HIPAA (1996) and State
Alliance for eHealth (2007).
3.2. Threats to Information Privacy
Threats to privacy of the patient’s and information security are sorted into two expansive
ranges:
(1) Organizational threats which emerges from unauthorized accessibility of the information
of the patients either by inside operators or misusing the advantages or specialist from
outwards abusing the data framework and
(2) Systemic threats that may emerge from the operators in the steam of data chain and
abusing the uncovered past information along with expected utilization (NRC 1997).
Organizational Threats: This may accept diverse structures; let’s take an example of an
employee who receives the information without any authentic check or outside assailant
(programmers) that may invade the organizational framework to take the information. In the
start, the authoritative threats can be portrayed by four categories – thought processes, assets,
openness, and specialized ability (NRC 1997). Depending on these parts, extraordinary
threats may posture diverse standard of hazard to association requiring distinctive alleviation
and anticipation procedures. Thought processes could be both of monetary or noneconomic
nature. For a few, safety net providers, bosses, and writers, tolerant records may have
monetary esteem, while some may have non-economic processes like some of the other may
have a man associated with emotional relationship. The aggressors to complete their
adventures may require diverse sorts of access, for example, accessibility to the site, approval
for the framework and information approval. Likewise, treats may rely on the specialized
capacity of attackers, who may have the qualification of refined developers. A person with
the aim to obtain information also, having sufficient Late examinations recommend that the
wide range of authoritative dangers could be classified into five levels, in the expanding
The experience of US human services industry had some changes in a progressive manner.
Driven by propels in innovation and enactment of the data like, the 1973 Health Maintenance
Organizations Act. The data has been digitalized as an individual wellbeing, transmitted and dug out
for viable care arrangement. A new kind of risk to patient’s protection is to keep getting wrong
information. In perspective of these developing threats and the general objective of representing
practical medicinal service administrations to all residents, a few imperative government directions
have been authorized including the Privacy and Security Rules under HIPAA (1996) and State
Alliance for eHealth (2007).
3.2. Threats to Information Privacy
Threats to privacy of the patient’s and information security are sorted into two expansive
ranges:
(1) Organizational threats which emerges from unauthorized accessibility of the information
of the patients either by inside operators or misusing the advantages or specialist from
outwards abusing the data framework and
(2) Systemic threats that may emerge from the operators in the steam of data chain and
abusing the uncovered past information along with expected utilization (NRC 1997).
Organizational Threats: This may accept diverse structures; let’s take an example of an
employee who receives the information without any authentic check or outside assailant
(programmers) that may invade the organizational framework to take the information. In the
start, the authoritative threats can be portrayed by four categories – thought processes, assets,
openness, and specialized ability (NRC 1997). Depending on these parts, extraordinary
threats may posture diverse standard of hazard to association requiring distinctive alleviation
and anticipation procedures. Thought processes could be both of monetary or noneconomic
nature. For a few, safety net providers, bosses, and writers, tolerant records may have
monetary esteem, while some may have non-economic processes like some of the other may
have a man associated with emotional relationship. The aggressors to complete their
adventures may require diverse sorts of access, for example, accessibility to the site, approval
for the framework and information approval. Likewise, treats may rely on the specialized
capacity of attackers, who may have the qualification of refined developers. A person with
the aim to obtain information also, having sufficient Late examinations recommend that the
wide range of authoritative dangers could be classified into five levels, in the expanding
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

request of modernity: cash related resources may have the ability to buy organizations of
complex software engineers to break human administrations data.
1. Accidental disclosure: human health services work force accidentally reveals tolerant data
to others, like data breaching through distributed sharing of document or message emailed on
wrong address.
2. Insider interest: information provided to an insider get to benefit pries upon the record of
the patient for clearing up something or for their own motivation, e.g. a medical attendant
getting to data about a kindred representative to decide probability in associate of sexually
transmitted sickness; or medicinal work force getting to possibly wellbeing data humiliating
about a big name and transmitting to media.
3. Data breach by insider: insiders who get to quiet data and transmit to outcasts for benefit or
delivering retribution on quiet.
4. Data breach by outsider with physical intrusion: an outcast who enters the physical office
either by intimidation or constrained section and accesses framework.
5. Unauthorized intrusion of network system: an outcast, including previous wrathful
representatives, patients, or programmers who interrupt with the associated system
framework from outside. The access tolerant of the data the framework gets inoperable.
4. Policies that Ensure Operations Security
Security is a centre an incentive at Stanford and the University is focused on proceeded with
headway of an institutional wellbeing society with solid projects of individual wellbeing,
mischance and damage counteractive action, wellbeing advancement, and consistence with
material ecological and wellbeing and wellbeing laws and controls. Stanford University
endeavours every single sensible push to:
Advance word related and individual security, wellbeing and health;
Ensure the wellbeing and security of Stanford University personnel, staff and
understudies;
Give data to personnel, staff, and understudies about wellbeing and security risks;
Distinguish and right wellbeing and security risks and energize workforce, staff, and
understudies to report potential dangers;
Direct exercises in a way defensive of the earth, and illuminate the Stanford people
group regarding natural effects related with institutional operations; and
complex software engineers to break human administrations data.
1. Accidental disclosure: human health services work force accidentally reveals tolerant data
to others, like data breaching through distributed sharing of document or message emailed on
wrong address.
2. Insider interest: information provided to an insider get to benefit pries upon the record of
the patient for clearing up something or for their own motivation, e.g. a medical attendant
getting to data about a kindred representative to decide probability in associate of sexually
transmitted sickness; or medicinal work force getting to possibly wellbeing data humiliating
about a big name and transmitting to media.
3. Data breach by insider: insiders who get to quiet data and transmit to outcasts for benefit or
delivering retribution on quiet.
4. Data breach by outsider with physical intrusion: an outcast who enters the physical office
either by intimidation or constrained section and accesses framework.
5. Unauthorized intrusion of network system: an outcast, including previous wrathful
representatives, patients, or programmers who interrupt with the associated system
framework from outside. The access tolerant of the data the framework gets inoperable.
4. Policies that Ensure Operations Security
Security is a centre an incentive at Stanford and the University is focused on proceeded with
headway of an institutional wellbeing society with solid projects of individual wellbeing,
mischance and damage counteractive action, wellbeing advancement, and consistence with
material ecological and wellbeing and wellbeing laws and controls. Stanford University
endeavours every single sensible push to:
Advance word related and individual security, wellbeing and health;
Ensure the wellbeing and security of Stanford University personnel, staff and
understudies;
Give data to personnel, staff, and understudies about wellbeing and security risks;
Distinguish and right wellbeing and security risks and energize workforce, staff, and
understudies to report potential dangers;
Direct exercises in a way defensive of the earth, and illuminate the Stanford people
group regarding natural effects related with institutional operations; and

Keep up a hazard based crisis administration program to decrease the effect of crisis
occasions to the Stanford people group.
4.1. Providing a Safe Workplace
Stanford's program for giving a protected work environment to personnel, staff and
understudies incorporates: office configuration; peril recognizable proof, work environment
investigation and restorative activity; shutdown of risky exercises; medicinal reconnaissance:
and crisis readiness.
Facility Design: Offices will be composed in a way reliable with wellbeing and security
controls and guidelines of good outline. Those University offices accused of essential
obligation regarding the outline, development, and additionally remodel of offices, together
with EH&S might guarantee that there is proper wellbeing and security audit of office ideas,
plans, and plans.
Hazard Identification and Correction: Administrators, might educate understudies and
representatives of this approach and energize revealing of working workplace hazards.
Administrators, both workforce and staff, should guarantee that general, occasional
examinations of work environments are directed to recognize and assess work environment
risks and risky work rehearses.
The recurrence of examinations ought to be corresponding to the size of hazard
postured in the specific work environment.
Methods for revising found dangers as well as shielding people from the perils should
be resolved and executed suitably.
Risky conditions which can't be revised by the boss or supervisor must be accounted
for to the following larger amount of administration. Any individual, boss or director
who ends up noticeably mindful of a genuine hid risk to the wellbeing or security of
people should report this threat speedily to the Department of EH&S and to the
workforce, staff and understudies who might be influenced.
5. Potential Risks
Potential threats fall into five broadly portrayed classes. Researchers are depended upon
to figure out how to constrain potential threats. The CPHS/IRB and Research Compliance
Services quantifies the potential threats of research against the focal points as a noteworthy
part of the review strategy.
occasions to the Stanford people group.
4.1. Providing a Safe Workplace
Stanford's program for giving a protected work environment to personnel, staff and
understudies incorporates: office configuration; peril recognizable proof, work environment
investigation and restorative activity; shutdown of risky exercises; medicinal reconnaissance:
and crisis readiness.
Facility Design: Offices will be composed in a way reliable with wellbeing and security
controls and guidelines of good outline. Those University offices accused of essential
obligation regarding the outline, development, and additionally remodel of offices, together
with EH&S might guarantee that there is proper wellbeing and security audit of office ideas,
plans, and plans.
Hazard Identification and Correction: Administrators, might educate understudies and
representatives of this approach and energize revealing of working workplace hazards.
Administrators, both workforce and staff, should guarantee that general, occasional
examinations of work environments are directed to recognize and assess work environment
risks and risky work rehearses.
The recurrence of examinations ought to be corresponding to the size of hazard
postured in the specific work environment.
Methods for revising found dangers as well as shielding people from the perils should
be resolved and executed suitably.
Risky conditions which can't be revised by the boss or supervisor must be accounted
for to the following larger amount of administration. Any individual, boss or director
who ends up noticeably mindful of a genuine hid risk to the wellbeing or security of
people should report this threat speedily to the Department of EH&S and to the
workforce, staff and understudies who might be influenced.
5. Potential Risks
Potential threats fall into five broadly portrayed classes. Researchers are depended upon
to figure out how to constrain potential threats. The CPHS/IRB and Research Compliance
Services quantifies the potential threats of research against the focal points as a noteworthy
part of the review strategy.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Mental risks: Lack in resting or sleeping, tangible hardship, utilizations of the
spellbinding, tricker, mental burdens is cases of mental dangers. This kind of risks
incorporates due to the creation of some negative state of mind, for example,
uneasiness, wretchedness, blaming, loss of confidence and conduction change.
Loss of Confidentiality: In all examination including subjects of human emotion,
privacy assumption of identifiable data and should always be kept by the examiner
acquiring the expression authorized of the subject to do something else. Subjects have
the rights to be secured against damage or illicit intrusions of protection and to
conservation depending on their poise. The touchier the examination material, the
more noteworthy the care that should be practiced, to acquired. With a specific end
goal to limit the hazard for loss of classification, specialists should gather some
individual data that re significant to the exploration action. There was an off chance
that the individual data to be gathered that ought to be coded to be right on time of
action and possibly safer thus put away with the goals which only the approved staffs
may get. Without the expression assents of the subject characteristics of individual
subjects may never be discharged. In addition, if a specialist wish to utilize the data
for the reason that other initially collected and the information is yet to be identified,
there must be a requirement of the specialist to acquire assents from the subject for
new version of the information.
Social/Economic risks: Social/Economic risks includes changes that involves with
others, these are said to be burden of the subjects, and including humiliation, loss of
regard of others, marking a way that may have adverse outcomes, or some way
reducing those open doors and forces a man has by temperance of associations.
Social/Economic incorporate instalment by subjects for techniques not generally
required, loss of wages or other salary and some other money related costs, like harm
to some subject employability, as an outcome of support in the exploration.
Physical risks: A physical risk incorporates physical distress, torments, damages,
sickness or illness realized by the techniques and the system of the examination. In a
Social circumstance connecting with a subject that could include viciousness may
similarly makes a physical hazard. This kind of risk may occur due to the inclusion of
physical boosts, for example, commotion, warm, frosty, electric attractive or
gravitational fields, and so forth.
Legal risks: Existence of Legal risks can be examined in techniques with having the
end goals that the order and subjects can be at risk for the infringement of the
spellbinding, tricker, mental burdens is cases of mental dangers. This kind of risks
incorporates due to the creation of some negative state of mind, for example,
uneasiness, wretchedness, blaming, loss of confidence and conduction change.
Loss of Confidentiality: In all examination including subjects of human emotion,
privacy assumption of identifiable data and should always be kept by the examiner
acquiring the expression authorized of the subject to do something else. Subjects have
the rights to be secured against damage or illicit intrusions of protection and to
conservation depending on their poise. The touchier the examination material, the
more noteworthy the care that should be practiced, to acquired. With a specific end
goal to limit the hazard for loss of classification, specialists should gather some
individual data that re significant to the exploration action. There was an off chance
that the individual data to be gathered that ought to be coded to be right on time of
action and possibly safer thus put away with the goals which only the approved staffs
may get. Without the expression assents of the subject characteristics of individual
subjects may never be discharged. In addition, if a specialist wish to utilize the data
for the reason that other initially collected and the information is yet to be identified,
there must be a requirement of the specialist to acquire assents from the subject for
new version of the information.
Social/Economic risks: Social/Economic risks includes changes that involves with
others, these are said to be burden of the subjects, and including humiliation, loss of
regard of others, marking a way that may have adverse outcomes, or some way
reducing those open doors and forces a man has by temperance of associations.
Social/Economic incorporate instalment by subjects for techniques not generally
required, loss of wages or other salary and some other money related costs, like harm
to some subject employability, as an outcome of support in the exploration.
Physical risks: A physical risk incorporates physical distress, torments, damages,
sickness or illness realized by the techniques and the system of the examination. In a
Social circumstance connecting with a subject that could include viciousness may
similarly makes a physical hazard. This kind of risk may occur due to the inclusion of
physical boosts, for example, commotion, warm, frosty, electric attractive or
gravitational fields, and so forth.
Legal risks: Existence of Legal risks can be examined in techniques with having the
end goals that the order and subjects can be at risk for the infringement of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

techniques and laws. This is either by uncovering the subject matter or by let other
take part in the leads for which the subject or other might be criminally at some risk.
6. Disaster Recovery
A Disaster Recovery procedure should begin at the business level and figure out
which applications are most imperative to running the association. The RTO portrays the
objective measure of time some application of business may be down, normally measured in
hours, minutes or seconds. The RPO portrays the earlier points when the application should
be recouped. Recuperation systems characterize an association's gets ready for reacting to an
occurrence, while debacle recuperation designs depict how the association ought to react.
In deciding a recuperation methodology, associations should consider such issues as:
Financial plan
Assets - individuals and physical offices
Administration's position on dangers
Innovation
Information
Providers
Administration endorsement of recuperation techniques is vital. All techniques ought to line
up with the association's objectives. The develop and approved strategies of disaster recovery
can be translated to disaster recovery plan later.
CONCLUSION
This report depicts the various risks associated to the data framework and features that can
signify the execution in an expansive technique. Understanding this huge range of risks to the
health care organization in the initial phase may guarantee the management of this risks and
prevent it. A disaster recovery plan (DRP) thus depicted as a structured approach along with
instructions in order as a responding to any unplanned incident. This well-organized process
helps in maintaining the prevention of the disaster, such that the association can keep track on
the operation or the rapidly continue to target the goals. cloud servers are present that allows
the healthcare professionals to utilize the connection of medical devices in the diagnosis,
body composition evaluation and treatment of the patients in some other location. DICOM is
used for every kind of images associated to the medical infrastructure like X-ray, CT scans,
MRI Digital Radiography and many more. Commonly, management approval of recuperation
take part in the leads for which the subject or other might be criminally at some risk.
6. Disaster Recovery
A Disaster Recovery procedure should begin at the business level and figure out
which applications are most imperative to running the association. The RTO portrays the
objective measure of time some application of business may be down, normally measured in
hours, minutes or seconds. The RPO portrays the earlier points when the application should
be recouped. Recuperation systems characterize an association's gets ready for reacting to an
occurrence, while debacle recuperation designs depict how the association ought to react.
In deciding a recuperation methodology, associations should consider such issues as:
Financial plan
Assets - individuals and physical offices
Administration's position on dangers
Innovation
Information
Providers
Administration endorsement of recuperation techniques is vital. All techniques ought to line
up with the association's objectives. The develop and approved strategies of disaster recovery
can be translated to disaster recovery plan later.
CONCLUSION
This report depicts the various risks associated to the data framework and features that can
signify the execution in an expansive technique. Understanding this huge range of risks to the
health care organization in the initial phase may guarantee the management of this risks and
prevent it. A disaster recovery plan (DRP) thus depicted as a structured approach along with
instructions in order as a responding to any unplanned incident. This well-organized process
helps in maintaining the prevention of the disaster, such that the association can keep track on
the operation or the rapidly continue to target the goals. cloud servers are present that allows
the healthcare professionals to utilize the connection of medical devices in the diagnosis,
body composition evaluation and treatment of the patients in some other location. DICOM is
used for every kind of images associated to the medical infrastructure like X-ray, CT scans,
MRI Digital Radiography and many more. Commonly, management approval of recuperation

arranging includes an examination of business procedures and coherence needs. All, the
systems gets powerless in front of cyber security dangers like data breaching and attacking
hence it is essential to prevent it in the initial stage. The information security program is the
basic form for the moderation od these dangers and thus keep a break to information. The
historic approach to the security of the data begins with the understanding of the network that
has been used in the organization, along with its architecture, user population and the mission
requirement for the prevention of the system.
systems gets powerless in front of cyber security dangers like data breaching and attacking
hence it is essential to prevent it in the initial stage. The information security program is the
basic form for the moderation od these dangers and thus keep a break to information. The
historic approach to the security of the data begins with the understanding of the network that
has been used in the organization, along with its architecture, user population and the mission
requirement for the prevention of the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Bodie, Z., 2013. Investments. McGraw-Hill.
Dehling, T., Gao, F., Schneider, S. and Sunyaev, A., 2015. Exploring the far side of mobile
health: information security and privacy of mobile health apps on iOS and Android. JMIR
mHealth and uHealth, 3(1).
Fernández-Alemán, J.L., Señor, I.C., Lozoya, P.Á.O. and Toval, A., 2013. Security and
privacy in electronic health records: A systematic literature review. Journal of biomedical
informatics, 46(3), pp.541-562.
George, J., Kumar, V. and Kumar, S., 2015. Data Warehouse Design Considerations for a
Healthcare Business Intelligence System. In World Congress on Engineering.
Hofmann, M. and Klinkenberg, R. eds., 2013. RapidMiner: Data mining use cases and
business analytics applications. CRC Press.
Ifinedo, P., 2014. Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), pp.69-
79.
Imtiyaj, S., 2015. Privacy Preserving Data Mining. transactions, 2(2).
Jain, D. and Sharma, M.Y., 2017. Adoption of next generation robotics: A case study on
Amazon.
Kasemsap, K., 2015. The role of data mining for business intelligence in knowledge
management. Integration of data mining in business intelligence systems, pp.12-33.
Kedar, S., Dhawale, S., Vaibhav, W., Kadam, P., Wani, S., and Ingale, P., 2013. Privacy
Preserving Data Mining. International Journal of Advanced Research in Computer and
Communication Engineering, 2(4).
Larose, D.T., 2014. Discovering knowledge in data: an introduction to data mining. John
Wiley & Sons.
Mishra, S., Caputo, D.J., Leone, G.J., Kohun, F.G. and Draus, P.J., 2014. The role of
awareness and communications in information security management: A health care
information systems perspective. International Journal of Management & Information
Systems (Online), 18(2), p.139.
Bodie, Z., 2013. Investments. McGraw-Hill.
Dehling, T., Gao, F., Schneider, S. and Sunyaev, A., 2015. Exploring the far side of mobile
health: information security and privacy of mobile health apps on iOS and Android. JMIR
mHealth and uHealth, 3(1).
Fernández-Alemán, J.L., Señor, I.C., Lozoya, P.Á.O. and Toval, A., 2013. Security and
privacy in electronic health records: A systematic literature review. Journal of biomedical
informatics, 46(3), pp.541-562.
George, J., Kumar, V. and Kumar, S., 2015. Data Warehouse Design Considerations for a
Healthcare Business Intelligence System. In World Congress on Engineering.
Hofmann, M. and Klinkenberg, R. eds., 2013. RapidMiner: Data mining use cases and
business analytics applications. CRC Press.
Ifinedo, P., 2014. Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), pp.69-
79.
Imtiyaj, S., 2015. Privacy Preserving Data Mining. transactions, 2(2).
Jain, D. and Sharma, M.Y., 2017. Adoption of next generation robotics: A case study on
Amazon.
Kasemsap, K., 2015. The role of data mining for business intelligence in knowledge
management. Integration of data mining in business intelligence systems, pp.12-33.
Kedar, S., Dhawale, S., Vaibhav, W., Kadam, P., Wani, S., and Ingale, P., 2013. Privacy
Preserving Data Mining. International Journal of Advanced Research in Computer and
Communication Engineering, 2(4).
Larose, D.T., 2014. Discovering knowledge in data: an introduction to data mining. John
Wiley & Sons.
Mishra, S., Caputo, D.J., Leone, G.J., Kohun, F.G. and Draus, P.J., 2014. The role of
awareness and communications in information security management: A health care
information systems perspective. International Journal of Management & Information
Systems (Online), 18(2), p.139.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Mxoli, A., Gerber, M. and Mostert-Phipps, N., 2014, November. Information security risk
measures for Cloud-based Personal Health Records. In Information Society (i-Society), 2014
International Conference on (pp. 187-193). IEEE.
Peltier, T.R., 2013. Information security fundamentals. CRC Press.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Provost, F. and Fawcett, T., 2013. Data Science for Business: What you need to know about
data mining and data-analytic thinking. " O'Reilly Media, Inc.".
Rusu, D., Triantafyllidis, N.P. and Kremers, J., 2015. Security Intelligence Data Mining.
Ryoo, J., 2017. Big data security problems threaten consumers' privacy. The Conversation.
Retrieved 6 August 2017, from http://theconversation.com/big-data-security-problems-
threaten-consumers-privacy-54798
Sekaran, U. and Bougie, R., 2016. Research methods for business: A skill building approach.
John Wiley & Sons.
Shmueli, G. and Lichtendahl Jr, K.C., 2017. Data Mining for Business Analytics: Concepts,
Techniques, and Applications in R. John Wiley & Sons.
Shmueli, G., Patel, N.R. and Bruce, P.C., 2016. Data Mining for Business Analytics:
Concepts, Techniques, and Applications with XLMiner. John Wiley & Sons.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Swan, M., 2013. The quantified self: Fundamental disruption in big data science and
biological discovery. Big Data, 1(2), pp.85-99.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber security.
computers & security, 38, pp.97-102.
Wager, K.A., Lee, F.W. and Glaser, J.P., 2017. Health care information systems: a practical
approach for health care management. John Wiley & Sons.
measures for Cloud-based Personal Health Records. In Information Society (i-Society), 2014
International Conference on (pp. 187-193). IEEE.
Peltier, T.R., 2013. Information security fundamentals. CRC Press.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Provost, F. and Fawcett, T., 2013. Data Science for Business: What you need to know about
data mining and data-analytic thinking. " O'Reilly Media, Inc.".
Rusu, D., Triantafyllidis, N.P. and Kremers, J., 2015. Security Intelligence Data Mining.
Ryoo, J., 2017. Big data security problems threaten consumers' privacy. The Conversation.
Retrieved 6 August 2017, from http://theconversation.com/big-data-security-problems-
threaten-consumers-privacy-54798
Sekaran, U. and Bougie, R., 2016. Research methods for business: A skill building approach.
John Wiley & Sons.
Shmueli, G. and Lichtendahl Jr, K.C., 2017. Data Mining for Business Analytics: Concepts,
Techniques, and Applications in R. John Wiley & Sons.
Shmueli, G., Patel, N.R. and Bruce, P.C., 2016. Data Mining for Business Analytics:
Concepts, Techniques, and Applications with XLMiner. John Wiley & Sons.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Swan, M., 2013. The quantified self: Fundamental disruption in big data science and
biological discovery. Big Data, 1(2), pp.85-99.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber security.
computers & security, 38, pp.97-102.
Wager, K.A., Lee, F.W. and Glaser, J.P., 2017. Health care information systems: a practical
approach for health care management. John Wiley & Sons.

Willis III, J.E., 2013. Ethics, Big Data, and Analytics: A Model for Application. Educause
Review Online.
Witten, I.H., Frank, E., Hall, M.A. and Pal, C.J., 2016. Data Mining: Practical machine
learning tools and techniques. Morgan Kaufmann.
Wixom, B., Ariyachandra, T., Douglas, D.E., Goul, M., Gupta, B., Iyer, L.S., Kulkarni, U.R.,
Mooney, J.G., Phillips-Wren, G.E. and Turetken, O., 2014. The current state of business
intelligence in academia: The arrival of big data. CAIS, 34, p.1.
Wu, X., Zhu, X., Wu, G.Q. and Ding, W., 2014. Data mining with big data. IEEE
transactions on knowledge and data engineering, 26(1), pp.97-107.
Review Online.
Witten, I.H., Frank, E., Hall, M.A. and Pal, C.J., 2016. Data Mining: Practical machine
learning tools and techniques. Morgan Kaufmann.
Wixom, B., Ariyachandra, T., Douglas, D.E., Goul, M., Gupta, B., Iyer, L.S., Kulkarni, U.R.,
Mooney, J.G., Phillips-Wren, G.E. and Turetken, O., 2014. The current state of business
intelligence in academia: The arrival of big data. CAIS, 34, p.1.
Wu, X., Zhu, X., Wu, G.Q. and Ding, W., 2014. Data mining with big data. IEEE
transactions on knowledge and data engineering, 26(1), pp.97-107.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
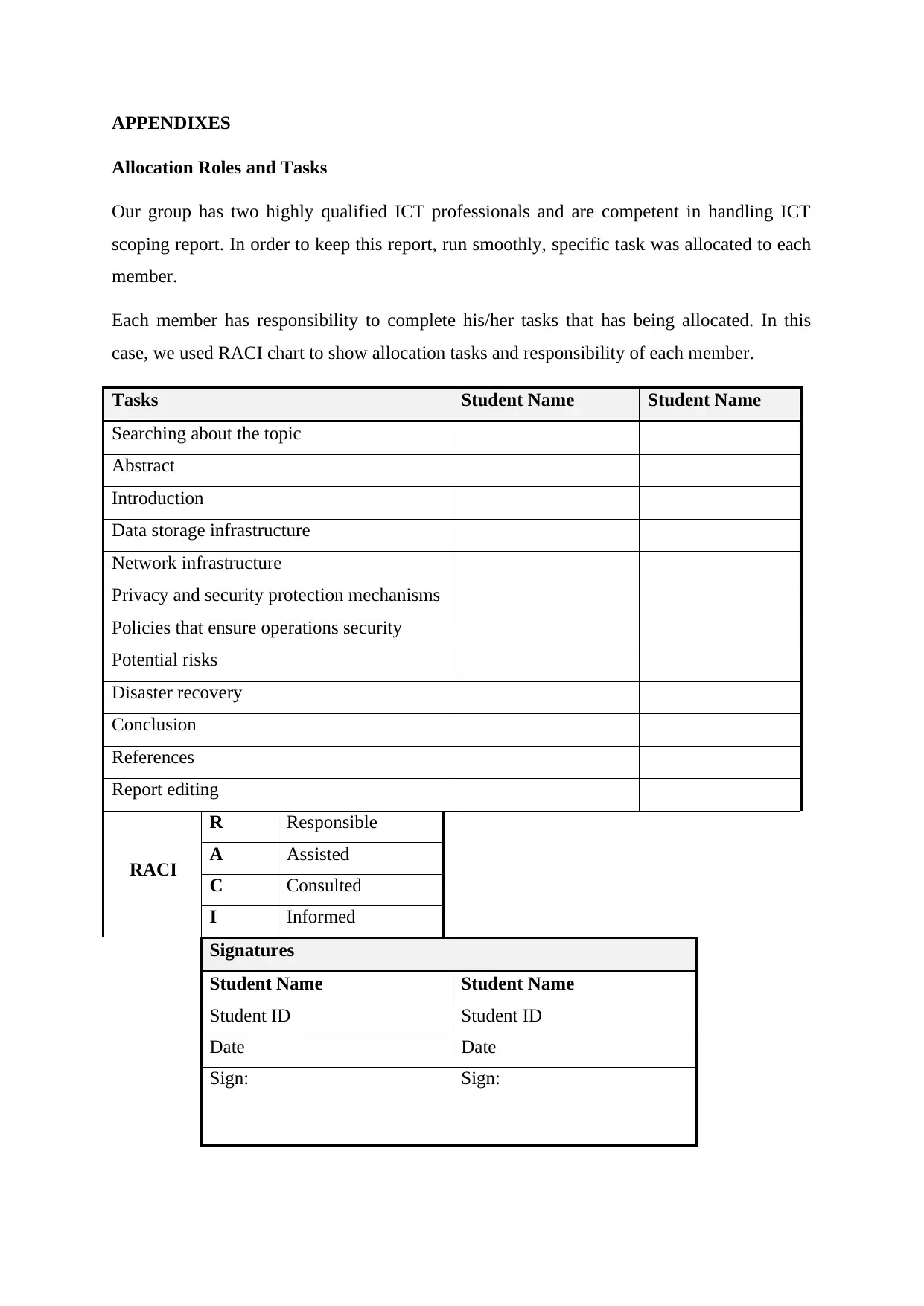
APPENDIXES
Allocation Roles and Tasks
Our group has two highly qualified ICT professionals and are competent in handling ICT
scoping report. In order to keep this report, run smoothly, specific task was allocated to each
member.
Each member has responsibility to complete his/her tasks that has being allocated. In this
case, we used RACI chart to show allocation tasks and responsibility of each member.
Tasks Student Name Student Name
Searching about the topic
Abstract
Introduction
Data storage infrastructure
Network infrastructure
Privacy and security protection mechanisms
Policies that ensure operations security
Potential risks
Disaster recovery
Conclusion
References
Report editing
RACI
R Responsible
A Assisted
C Consulted
I Informed
Signatures
Student Name Student Name
Student ID Student ID
Date Date
Sign: Sign:
Allocation Roles and Tasks
Our group has two highly qualified ICT professionals and are competent in handling ICT
scoping report. In order to keep this report, run smoothly, specific task was allocated to each
member.
Each member has responsibility to complete his/her tasks that has being allocated. In this
case, we used RACI chart to show allocation tasks and responsibility of each member.
Tasks Student Name Student Name
Searching about the topic
Abstract
Introduction
Data storage infrastructure
Network infrastructure
Privacy and security protection mechanisms
Policies that ensure operations security
Potential risks
Disaster recovery
Conclusion
References
Report editing
RACI
R Responsible
A Assisted
C Consulted
I Informed
Signatures
Student Name Student Name
Student ID Student ID
Date Date
Sign: Sign:
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





