Comprehensive Solutions: Security of Information in Computing
VerifiedAdded on 2023/06/14
|6
|1864
|196
Homework Assignment
AI Summary
This assignment solution covers key aspects of information security in computing, addressing questions related to confidentiality, integrity, and availability within ATM systems. It explores the vulnerabilities of PIN-based authentication and the potential risks associated with biometric systems, including false positives and false negatives. The solution also delves into encryption techniques, comparing the efficiency of transposition ciphers versus Caesar ciphers, and provides a detailed decryption of a given text using a transposition cipher. The document emphasizes the importance of secure data transmission, the limitations of biometric authentication, and the consequences of system failures, offering a comprehensive overview of essential security concepts and practical applications. Desklib provides this and other solved assignments to help students in their studies.

Running head: SECURITY OF INFORMATION IN COMPUTING
Security of information in computing
Name of the Student
Name of the University
Authors note
Security of information in computing
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY OF INFORMATION IN COMPUTING
Answer to Question 1
Examples of confidentiality, integrity and availability
For the ATM like systems which are used and operated by the users using some kind
of authentication it is important to maintain confidentiality of the user data and the different
transactional data about the operations completed using the system.
The PIN of a customer acts as digital identifier to server and the information system
used by the banks. Hence, it is important to have a secured channel to transmit the user data
along with the PIN in order to protect from data breach or hacking (Singh & Kaur, 2016).
Due to severity of the data breach issues the degree importance is marked as High.
Another issues related to the ATM systems is the integrity of the data. The data
transmitted to and from the ATM should be kept unchanged in the transmission channel so
that the operations does not impact adversely on the users of the ATM or the Customers of
the Bank.
At last the availability of the system is also required so that the users can get the
services from the system. Thus it can be said that, the ATM system should have minimal
downtime for any issues (Hajare et al., 2018). The availability of the services provided by
the ATM is completely dependent on the connectivity of ATM and thus the level of
importance is marked as the Moderate.
Answer to Question 2
Given that the thief has managed to break the five of the total ten keys on the board
that are used by the customers to enter their PIN’s. excluding the five broken keys on the
board, the customer had able to enter their card PIN using those five keys.
Thus the thief has to try and get the 4-digit PIN using multiple combination from the
five keys which will be given by 5P4
The number of attempts available for the thief is 5! =120
Answer to Question 3
The biometrics uniquely identifies the users or persons depending on the data related
to their fingerprints, iris and face. Therefore, any kind of damage and lack of accuracy of the
related data can lead to the failure of the system in the process of recognising the person or
user.
In addition to that, integrity of data that is required for biometric authentication does
not private data. Match of the related data stored in the database mainly depends on efficient
capture of the live samples from the users or behavioural data in order to match with the
predefined data or template.
The bio metric system is also not too secure against hackers. Hackers ca gain access
to the data after implementing brute force attack to the system.
Again, potential misuse of the user’s data is also a concern from the aspect of privacy.
The stolen data of a user can be used to access highly secured area or portal to complete any
kind of criminal activity (Bhagavatula et al., 2015). As an example of lack of security of
Answer to Question 1
Examples of confidentiality, integrity and availability
For the ATM like systems which are used and operated by the users using some kind
of authentication it is important to maintain confidentiality of the user data and the different
transactional data about the operations completed using the system.
The PIN of a customer acts as digital identifier to server and the information system
used by the banks. Hence, it is important to have a secured channel to transmit the user data
along with the PIN in order to protect from data breach or hacking (Singh & Kaur, 2016).
Due to severity of the data breach issues the degree importance is marked as High.
Another issues related to the ATM systems is the integrity of the data. The data
transmitted to and from the ATM should be kept unchanged in the transmission channel so
that the operations does not impact adversely on the users of the ATM or the Customers of
the Bank.
At last the availability of the system is also required so that the users can get the
services from the system. Thus it can be said that, the ATM system should have minimal
downtime for any issues (Hajare et al., 2018). The availability of the services provided by
the ATM is completely dependent on the connectivity of ATM and thus the level of
importance is marked as the Moderate.
Answer to Question 2
Given that the thief has managed to break the five of the total ten keys on the board
that are used by the customers to enter their PIN’s. excluding the five broken keys on the
board, the customer had able to enter their card PIN using those five keys.
Thus the thief has to try and get the 4-digit PIN using multiple combination from the
five keys which will be given by 5P4
The number of attempts available for the thief is 5! =120
Answer to Question 3
The biometrics uniquely identifies the users or persons depending on the data related
to their fingerprints, iris and face. Therefore, any kind of damage and lack of accuracy of the
related data can lead to the failure of the system in the process of recognising the person or
user.
In addition to that, integrity of data that is required for biometric authentication does
not private data. Match of the related data stored in the database mainly depends on efficient
capture of the live samples from the users or behavioural data in order to match with the
predefined data or template.
The bio metric system is also not too secure against hackers. Hackers ca gain access
to the data after implementing brute force attack to the system.
Again, potential misuse of the user’s data is also a concern from the aspect of privacy.
The stolen data of a user can be used to access highly secured area or portal to complete any
kind of criminal activity (Bhagavatula et al., 2015). As an example of lack of security of

2SECURITY OF INFORMATION IN COMPUTING
authentication by the bio metric, the Samsung S8 smartphone which unlocks itself by
scanning the Iris of its owner. The hackers were successful by using a contact lens on the
image of the user’s eye which lead to unlocking the phone.
Answer to Question 4
Both the false negative and false positive are types of failures related to the Biometric.
False negative is referred to the situation when due to some accuracy issues the biometric
system rejects a valid user entry.
On the other hand, the false positive is referred to the situation in which due to
malfunctions in the system the biometric systems allow an unauthorized user to access a
restricted premises or digital account through passing by the Biometric authentication
process. The system providing vendors can tune or adjust the accept or reject rates
(Bhagavatula et al., 2015). This can be done by improving the size of the biometric template,
or increasing the confidence interval between two consecutive access attempts after one fails
to do so.
As the process of finding a match mainly depends on the statistical comparison of the
live captured data and not on some Boolean response (Yes or No) from the system. In order
to avoid the situations of false positive or false negative it is advised to simply increase the
probability of false rejects. On the other hand, setting high confidence level in the biometric
systems also helpful in increasing the probability of false negatives.
Two scenarios where the false negatives lead to the significant consequences are
described below;
Example 1
For a IT organization that provides cloud services, at some instant the servers
infrastructure goes down. In this situation the software or hardware engineers need to access
the restricted premises to restore the service by correcting the issues with the server. At this
situation at every minute the organization will be losing its reputation and the revenue from
the business. At this time if the biometric system issues false negative for the engineers and
does not recognize the engineers it will lead to more loses of the company.
Example 2
Another scenario is in case of medical emergency a surgeon or a medical staff needs
to reach to a patient to provide him/her CPR at the time they are affected with cardiac arrest.
In this scenario if due to a false negative response of the biometric system, the medical staff
are not able to reach the patient then in a worst case scenario the patient may die.
Answer to Question 5
Use of Transposition for encrypting the data is more efficient than the simple Caesar
cipher text. In case of the Caesar cipher the it only changes the text by substitution, on the
other hand the Transposition Cipher it changes the order of the letters.
The main idea behind this technique is, to generate a permutation of the letters of a
given string in plaintext (Poonia & Kantha, 2016). This encryption technique makes the
encrypted or cipher text to be well-encrypted.
authentication by the bio metric, the Samsung S8 smartphone which unlocks itself by
scanning the Iris of its owner. The hackers were successful by using a contact lens on the
image of the user’s eye which lead to unlocking the phone.
Answer to Question 4
Both the false negative and false positive are types of failures related to the Biometric.
False negative is referred to the situation when due to some accuracy issues the biometric
system rejects a valid user entry.
On the other hand, the false positive is referred to the situation in which due to
malfunctions in the system the biometric systems allow an unauthorized user to access a
restricted premises or digital account through passing by the Biometric authentication
process. The system providing vendors can tune or adjust the accept or reject rates
(Bhagavatula et al., 2015). This can be done by improving the size of the biometric template,
or increasing the confidence interval between two consecutive access attempts after one fails
to do so.
As the process of finding a match mainly depends on the statistical comparison of the
live captured data and not on some Boolean response (Yes or No) from the system. In order
to avoid the situations of false positive or false negative it is advised to simply increase the
probability of false rejects. On the other hand, setting high confidence level in the biometric
systems also helpful in increasing the probability of false negatives.
Two scenarios where the false negatives lead to the significant consequences are
described below;
Example 1
For a IT organization that provides cloud services, at some instant the servers
infrastructure goes down. In this situation the software or hardware engineers need to access
the restricted premises to restore the service by correcting the issues with the server. At this
situation at every minute the organization will be losing its reputation and the revenue from
the business. At this time if the biometric system issues false negative for the engineers and
does not recognize the engineers it will lead to more loses of the company.
Example 2
Another scenario is in case of medical emergency a surgeon or a medical staff needs
to reach to a patient to provide him/her CPR at the time they are affected with cardiac arrest.
In this scenario if due to a false negative response of the biometric system, the medical staff
are not able to reach the patient then in a worst case scenario the patient may die.
Answer to Question 5
Use of Transposition for encrypting the data is more efficient than the simple Caesar
cipher text. In case of the Caesar cipher the it only changes the text by substitution, on the
other hand the Transposition Cipher it changes the order of the letters.
The main idea behind this technique is, to generate a permutation of the letters of a
given string in plaintext (Poonia & Kantha, 2016). This encryption technique makes the
encrypted or cipher text to be well-encrypted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
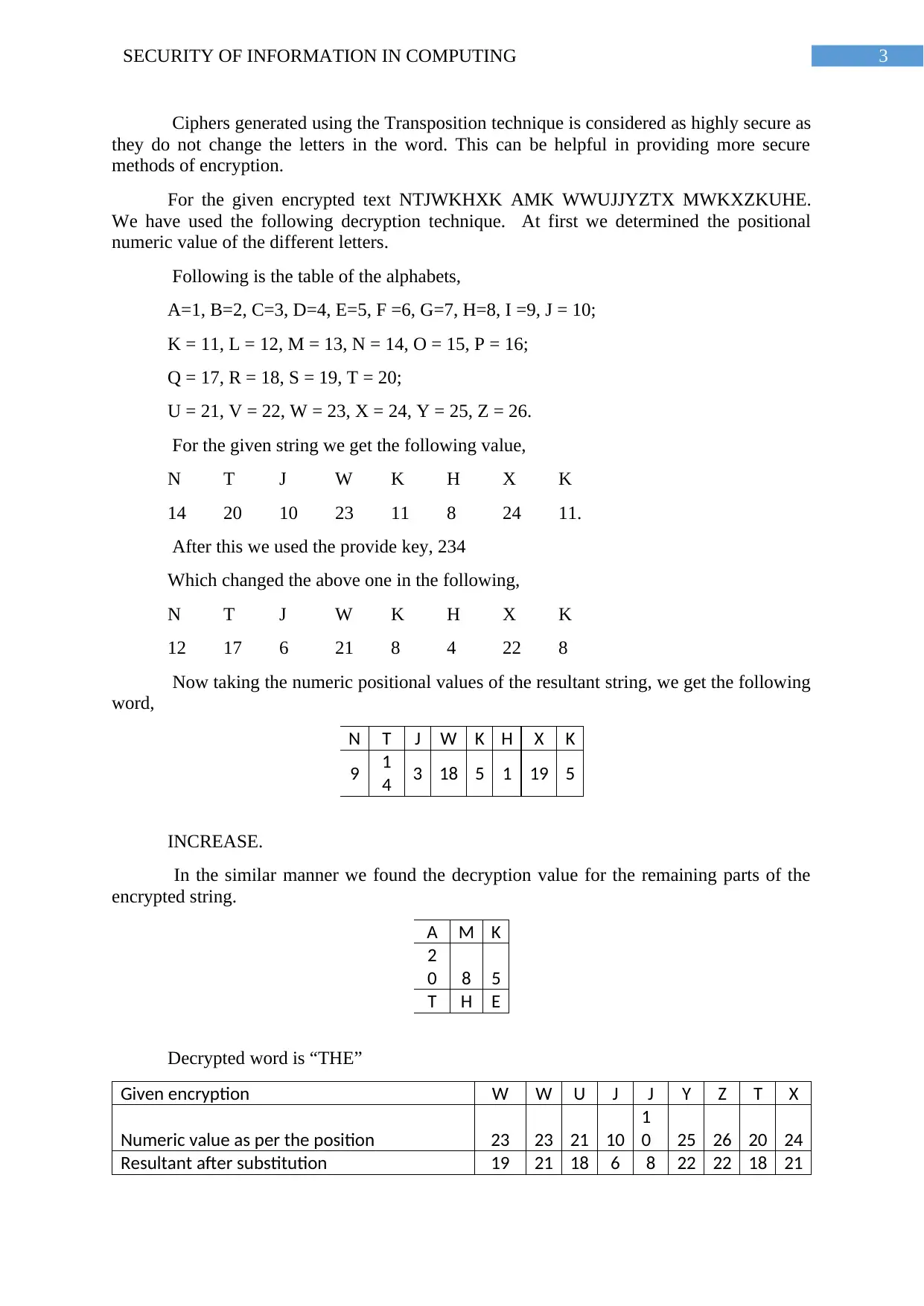
3SECURITY OF INFORMATION IN COMPUTING
Ciphers generated using the Transposition technique is considered as highly secure as
they do not change the letters in the word. This can be helpful in providing more secure
methods of encryption.
For the given encrypted text NTJWKHXK AMK WWUJJYZTX MWKXZKUHE.
We have used the following decryption technique. At first we determined the positional
numeric value of the different letters.
Following is the table of the alphabets,
A=1, B=2, C=3, D=4, E=5, F =6, G=7, H=8, I =9, J = 10;
K = 11, L = 12, M = 13, N = 14, O = 15, P = 16;
Q = 17, R = 18, S = 19, T = 20;
U = 21, V = 22, W = 23, X = 24, Y = 25, Z = 26.
For the given string we get the following value,
N T J W K H X K
14 20 10 23 11 8 24 11.
After this we used the provide key, 234
Which changed the above one in the following,
N T J W K H X K
12 17 6 21 8 4 22 8
Now taking the numeric positional values of the resultant string, we get the following
word,
N T J W K H X K
9 1
4 3 18 5 1 19 5
INCREASE.
In the similar manner we found the decryption value for the remaining parts of the
encrypted string.
A M K
2
0 8 5
T H E
Decrypted word is “THE”
Given encryption W W U J J Y Z T X
Numeric value as per the position 23 23 21 10
1
0 25 26 20 24
Resultant after substitution 19 21 18 6 8 22 22 18 21
Ciphers generated using the Transposition technique is considered as highly secure as
they do not change the letters in the word. This can be helpful in providing more secure
methods of encryption.
For the given encrypted text NTJWKHXK AMK WWUJJYZTX MWKXZKUHE.
We have used the following decryption technique. At first we determined the positional
numeric value of the different letters.
Following is the table of the alphabets,
A=1, B=2, C=3, D=4, E=5, F =6, G=7, H=8, I =9, J = 10;
K = 11, L = 12, M = 13, N = 14, O = 15, P = 16;
Q = 17, R = 18, S = 19, T = 20;
U = 21, V = 22, W = 23, X = 24, Y = 25, Z = 26.
For the given string we get the following value,
N T J W K H X K
14 20 10 23 11 8 24 11.
After this we used the provide key, 234
Which changed the above one in the following,
N T J W K H X K
12 17 6 21 8 4 22 8
Now taking the numeric positional values of the resultant string, we get the following
word,
N T J W K H X K
9 1
4 3 18 5 1 19 5
INCREASE.
In the similar manner we found the decryption value for the remaining parts of the
encrypted string.
A M K
2
0 8 5
T H E
Decrypted word is “THE”
Given encryption W W U J J Y Z T X
Numeric value as per the position 23 23 21 10
1
0 25 26 20 24
Resultant after substitution 19 21 18 6 8 22 22 18 21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
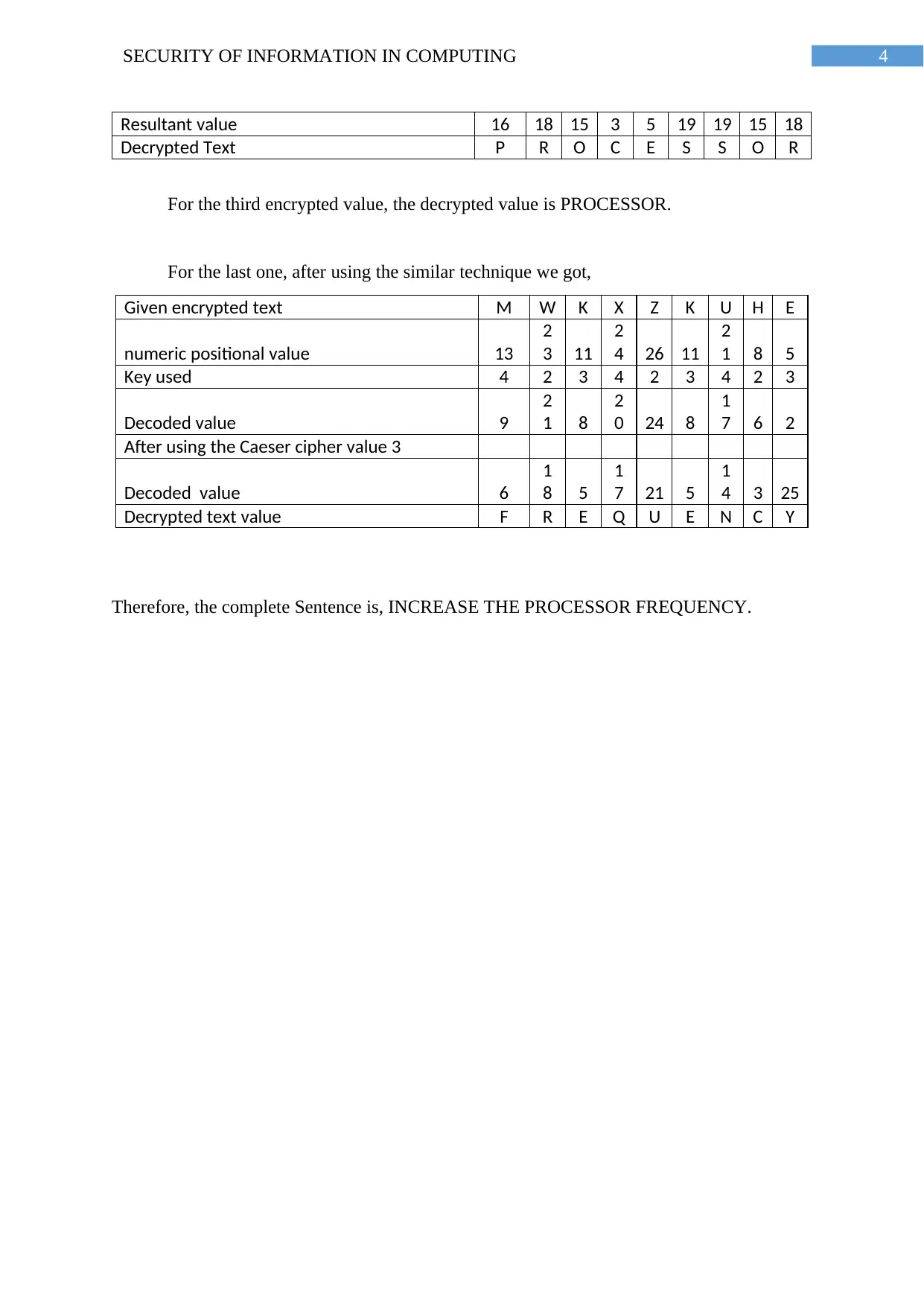
4SECURITY OF INFORMATION IN COMPUTING
Resultant value 16 18 15 3 5 19 19 15 18
Decrypted Text P R O C E S S O R
For the third encrypted value, the decrypted value is PROCESSOR.
For the last one, after using the similar technique we got,
Given encrypted text M W K X Z K U H E
numeric positional value 13
2
3 11
2
4 26 11
2
1 8 5
Key used 4 2 3 4 2 3 4 2 3
Decoded value 9
2
1 8
2
0 24 8
1
7 6 2
After using the Caeser cipher value 3
Decoded value 6
1
8 5
1
7 21 5
1
4 3 25
Decrypted text value F R E Q U E N C Y
Therefore, the complete Sentence is, INCREASE THE PROCESSOR FREQUENCY.
Resultant value 16 18 15 3 5 19 19 15 18
Decrypted Text P R O C E S S O R
For the third encrypted value, the decrypted value is PROCESSOR.
For the last one, after using the similar technique we got,
Given encrypted text M W K X Z K U H E
numeric positional value 13
2
3 11
2
4 26 11
2
1 8 5
Key used 4 2 3 4 2 3 4 2 3
Decoded value 9
2
1 8
2
0 24 8
1
7 6 2
After using the Caeser cipher value 3
Decoded value 6
1
8 5
1
7 21 5
1
4 3 25
Decrypted text value F R E Q U E N C Y
Therefore, the complete Sentence is, INCREASE THE PROCESSOR FREQUENCY.

5SECURITY OF INFORMATION IN COMPUTING
References
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and
influences on adoption. Proc. USEC, 1-2.
Hajare, U., Mahajan, R., Jadhav, S., Pingale, N., & Salunke, S. (2018). Efficient Cash
Withdrawal from ATM machine using Mobile Banking.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45,
390-396.
Khan, R., Hasan, R., & Xu, J. (2015, March). SEPIA: Secure-PIN-authentication-as-a-service
for ATM using mobile and wearable devices. In Mobile Cloud Computing, Services,
and Engineering (MobileCloud), 2015 3rd IEEE International Conference on (pp. 41-
50). IEEE.
Poonia, P., & Kantha, P. (2016). Comparative Study of Various Substitution and
Transposition Encryption Techniques. International Journal of Computer
Applications, 145(10).
Singh, S., & Kaur, S. (2016). Enhancing ATM Security Using Fusion of Biometric
Techniques. IITM Journal of Management and IT, 7(1), 79-82.
References
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and
influences on adoption. Proc. USEC, 1-2.
Hajare, U., Mahajan, R., Jadhav, S., Pingale, N., & Salunke, S. (2018). Efficient Cash
Withdrawal from ATM machine using Mobile Banking.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45,
390-396.
Khan, R., Hasan, R., & Xu, J. (2015, March). SEPIA: Secure-PIN-authentication-as-a-service
for ATM using mobile and wearable devices. In Mobile Cloud Computing, Services,
and Engineering (MobileCloud), 2015 3rd IEEE International Conference on (pp. 41-
50). IEEE.
Poonia, P., & Kantha, P. (2016). Comparative Study of Various Substitution and
Transposition Encryption Techniques. International Journal of Computer
Applications, 145(10).
Singh, S., & Kaur, S. (2016). Enhancing ATM Security Using Fusion of Biometric
Techniques. IITM Journal of Management and IT, 7(1), 79-82.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



