IT Risk Management Report: VIC Government Security Analysis
VerifiedAdded on 2020/02/19
|17
|3744
|61
Report
AI Summary
This report provides a comprehensive analysis of IT risk management within the Victorian (VIC) government's information security system. It identifies key security risks, including insider threats, cloud storage vulnerabilities, and manual record-keeping issues, using a diagrammatic representation to illustrate these challenges. The report categorizes risk areas into high, medium, and low exposure levels, detailing both deliberate and accidental threats, and ranks them based on severity. It explores internal and external risk management strategies, emphasizing the need for a combined approach to address the specific vulnerabilities of the VIC government's system. Furthermore, the report differentiates between risk and uncertainty and discusses risk control and mitigation techniques, including risk transfer, control, avoidance, and monitoring. The conclusion summarizes the findings and stresses the importance of a robust risk management plan to protect the confidentiality and integrity of sensitive government information.

Running head: IT RISK MANAGEMENT
IT Risk Management
Name of the Student
Name of the University
Author Note
IT Risk Management
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................3
1. Diagram to Illustrate the Security Issues in VIC.............................................................3
2. Risk Areas........................................................................................................................4
2.1 Exposure of Risk........................................................................................................5
2.1.1 High Risk Area...................................................................................................5
2.1.2. Medium Risk Area.............................................................................................5
2.1.3 Low Risk Areas..................................................................................................6
3. Deliberate and Accidental Threats...................................................................................6
3.1. Deliberate Threats.....................................................................................................6
3.2 Accidental Threats.....................................................................................................6
3.3 Risk Ranking.............................................................................................................7
4. Security/ Risk management Issues in the organization...................................................8
4.1 Internal Security/ Risk Management.........................................................................8
4.2. External Security/Risk Management........................................................................9
4.3 The Risk Management Strategy for VIC...................................................................9
5. Risk Vs Uncertainty......................................................................................................10
5.1 Risk..........................................................................................................................10
5.2. Uncertainty.............................................................................................................11
6. Risk Control and Risk Mitigation..................................................................................11
IT RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................3
1. Diagram to Illustrate the Security Issues in VIC.............................................................3
2. Risk Areas........................................................................................................................4
2.1 Exposure of Risk........................................................................................................5
2.1.1 High Risk Area...................................................................................................5
2.1.2. Medium Risk Area.............................................................................................5
2.1.3 Low Risk Areas..................................................................................................6
3. Deliberate and Accidental Threats...................................................................................6
3.1. Deliberate Threats.....................................................................................................6
3.2 Accidental Threats.....................................................................................................6
3.3 Risk Ranking.............................................................................................................7
4. Security/ Risk management Issues in the organization...................................................8
4.1 Internal Security/ Risk Management.........................................................................8
4.2. External Security/Risk Management........................................................................9
4.3 The Risk Management Strategy for VIC...................................................................9
5. Risk Vs Uncertainty......................................................................................................10
5.1 Risk..........................................................................................................................10
5.2. Uncertainty.............................................................................................................11
6. Risk Control and Risk Mitigation..................................................................................11

2
IT RISK MANAGEMENT
6.1. Risk Mitigation: Risk Transfer...............................................................................11
6.2. Risk Mitigation: Risk Control................................................................................12
6.3. Risk Mitigation: Risk Avoidance...........................................................................12
6.4 Risk Mitigation: Risk Monitoring...........................................................................12
Conclusion.........................................................................................................................12
References..........................................................................................................................14
IT RISK MANAGEMENT
6.1. Risk Mitigation: Risk Transfer...............................................................................11
6.2. Risk Mitigation: Risk Control................................................................................12
6.3. Risk Mitigation: Risk Avoidance...........................................................................12
6.4 Risk Mitigation: Risk Monitoring...........................................................................12
Conclusion.........................................................................................................................12
References..........................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
Introduction
The report focuses on the information security system of the VIC government that is
facing certain information security risks. The issue is important because the confidential
information of the Victorian government should be properly protected in order prevent the data
breach and the loss of data and information (Healey, 2016). The report discusses the current
security risks Victorian government is facing and the area of risk exposure. The problems that
Victorian government might face due to its exposure towards the deliberate and the accidental
threats are elaborated in the report. Enforcement of a proper data security standard is essential for
protection and security of the confidential information of a system. The report discusses the area
of high, medium and low risks penetrating in the system. Furthermore, the report contains a
diagrammatic representation of the risks, the government is exposed to and their possible causes.
The information security system should be efficient enough to prevent the threats from
penetrating into the system. The Threats, risks and the risk management plan of the Victorian
government is elaborated in the following paragraphs.
1. Diagram to Illustrate the Security Issues in VIC
IT RISK MANAGEMENT
Introduction
The report focuses on the information security system of the VIC government that is
facing certain information security risks. The issue is important because the confidential
information of the Victorian government should be properly protected in order prevent the data
breach and the loss of data and information (Healey, 2016). The report discusses the current
security risks Victorian government is facing and the area of risk exposure. The problems that
Victorian government might face due to its exposure towards the deliberate and the accidental
threats are elaborated in the report. Enforcement of a proper data security standard is essential for
protection and security of the confidential information of a system. The report discusses the area
of high, medium and low risks penetrating in the system. Furthermore, the report contains a
diagrammatic representation of the risks, the government is exposed to and their possible causes.
The information security system should be efficient enough to prevent the threats from
penetrating into the system. The Threats, risks and the risk management plan of the Victorian
government is elaborated in the following paragraphs.
1. Diagram to Illustrate the Security Issues in VIC
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
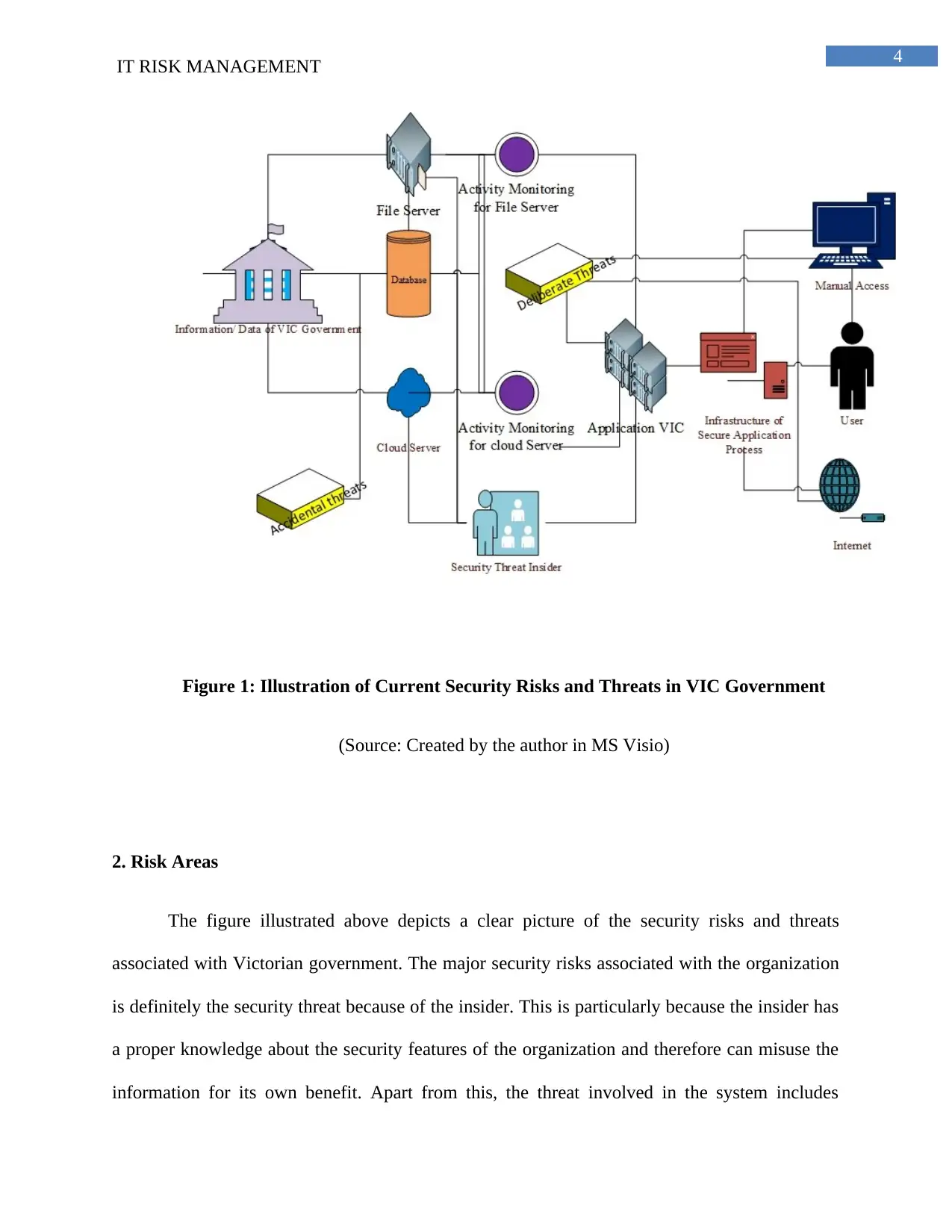
4
IT RISK MANAGEMENT
Figure 1: Illustration of Current Security Risks and Threats in VIC Government
(Source: Created by the author in MS Visio)
2. Risk Areas
The figure illustrated above depicts a clear picture of the security risks and threats
associated with Victorian government. The major security risks associated with the organization
is definitely the security threat because of the insider. This is particularly because the insider has
a proper knowledge about the security features of the organization and therefore can misuse the
information for its own benefit. Apart from this, the threat involved in the system includes
IT RISK MANAGEMENT
Figure 1: Illustration of Current Security Risks and Threats in VIC Government
(Source: Created by the author in MS Visio)
2. Risk Areas
The figure illustrated above depicts a clear picture of the security risks and threats
associated with Victorian government. The major security risks associated with the organization
is definitely the security threat because of the insider. This is particularly because the insider has
a proper knowledge about the security features of the organization and therefore can misuse the
information for its own benefit. Apart from this, the threat involved in the system includes

5
IT RISK MANAGEMENT
storage of data in the cloud storage that indicates major security concerns and privacy issues.
Furthermore, the manual record keeping is also an important area of security risks (Cardona et
al., 2012). Apart from this the other minor threats or security risks associated with the system is
the active monitoring of the database and the cloud storage that requires proper attention. The
different areas of risk include, high, medium and low risk exposure are identified and elaborated
in the following paragraph.
2.1 Exposure of Risk
Areas of risk and the risk exposure are essential to determine in order to determine the
impact of the risk (Behl & Behl, 2012). The risks associated with the Victorian government are
classified into the areas of high, medium and low risk exposure.
2.1.1 High Risk Area
The high-risk area of the Victorian government is definitely the security threat due to
insider along with the manual access of the data. This must be taken care of with highest priority
in order to control and manage the risk. Proper data security must be implemented in order to
eliminate these risks (Haimes, 2015).
2.1.2. Medium Risk Area
The area of medium risk exposure includes the storage of data in the cloud. The cloud
storage of data is very simple and easy to use but has certain security concerns associated with
the system. The cloud storage is vulnerable to attacks and therefore proper security measures are
needed to be implemented in order to manage and control the risk. Proper security measures are
to be taken to protect the data confidentiality (Bommer, Crowley & Pinho, 2015).
IT RISK MANAGEMENT
storage of data in the cloud storage that indicates major security concerns and privacy issues.
Furthermore, the manual record keeping is also an important area of security risks (Cardona et
al., 2012). Apart from this the other minor threats or security risks associated with the system is
the active monitoring of the database and the cloud storage that requires proper attention. The
different areas of risk include, high, medium and low risk exposure are identified and elaborated
in the following paragraph.
2.1 Exposure of Risk
Areas of risk and the risk exposure are essential to determine in order to determine the
impact of the risk (Behl & Behl, 2012). The risks associated with the Victorian government are
classified into the areas of high, medium and low risk exposure.
2.1.1 High Risk Area
The high-risk area of the Victorian government is definitely the security threat due to
insider along with the manual access of the data. This must be taken care of with highest priority
in order to control and manage the risk. Proper data security must be implemented in order to
eliminate these risks (Haimes, 2015).
2.1.2. Medium Risk Area
The area of medium risk exposure includes the storage of data in the cloud. The cloud
storage of data is very simple and easy to use but has certain security concerns associated with
the system. The cloud storage is vulnerable to attacks and therefore proper security measures are
needed to be implemented in order to manage and control the risk. Proper security measures are
to be taken to protect the data confidentiality (Bommer, Crowley & Pinho, 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT RISK MANAGEMENT
2.1.3 Low Risk Areas
The area of low risk exposure includes the VIC government database. The accidental
threats that are incorporated with the manual record keeping and are erroneous data entry are the
primary causes of the risk. This risk can be eliminated by imparting proper training to the users
and the database administrator. Therefore, this risk has the lowest priority.
3. Deliberate and Accidental Threats
Victorian Government is exposed to mainly two different types of threats: deliberate
threat and accidental threat. The details about the deliberate and the accidental threats along with
their order of ranking are elaborated in the following paragraphs.
3.1. Deliberate Threats
The deliberate threats include those threats that are done intentionally. The different areas
of deliberate threats include espionage threats that occur when any unauthorized person try to
access the confidential information, Information extortion, which occurs when an attacker
threatens to commit a theft for his own benefit, software attack, which includes hacking, denial
of service attack or using malicious software to fetch the information (Alcorn, Good & Pain,
2013). The deliberate threats are implied intentionally into a system with an aiming to cause
harm to the victims. Victorian government is exposed to a serious deliberate threat, as many
opportunists will be benefited with the information stored in the security system. Victorian
government should implement proper methods of detecting the deliberate threats and eliminating
it from the system as well.
3.2 Accidental Threats
IT RISK MANAGEMENT
2.1.3 Low Risk Areas
The area of low risk exposure includes the VIC government database. The accidental
threats that are incorporated with the manual record keeping and are erroneous data entry are the
primary causes of the risk. This risk can be eliminated by imparting proper training to the users
and the database administrator. Therefore, this risk has the lowest priority.
3. Deliberate and Accidental Threats
Victorian Government is exposed to mainly two different types of threats: deliberate
threat and accidental threat. The details about the deliberate and the accidental threats along with
their order of ranking are elaborated in the following paragraphs.
3.1. Deliberate Threats
The deliberate threats include those threats that are done intentionally. The different areas
of deliberate threats include espionage threats that occur when any unauthorized person try to
access the confidential information, Information extortion, which occurs when an attacker
threatens to commit a theft for his own benefit, software attack, which includes hacking, denial
of service attack or using malicious software to fetch the information (Alcorn, Good & Pain,
2013). The deliberate threats are implied intentionally into a system with an aiming to cause
harm to the victims. Victorian government is exposed to a serious deliberate threat, as many
opportunists will be benefited with the information stored in the security system. Victorian
government should implement proper methods of detecting the deliberate threats and eliminating
it from the system as well.
3.2 Accidental Threats
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT RISK MANAGEMENT
The threats that a system is exposed to mainly due to human error is termed as accidental
threat. Accidental threats are unintentional and can be eliminated with proper caution. The
number of accidental threats reported in the Victorian Government is huge mainly due to the
involvement of untrained employees. An organization is exposed to accidental threats only due
to its employees. Outsiders can never be a reason of accidental threats. Accidental threats lead to
certain circumstances that causes potential harm to the system in form of disclosure or
modification of data due to human error. The effects of accidental threats are therefore very
minor and can be eliminated from the system with little labor (Man et al., 2013). Victorian
government can eliminate the accidental threats by training their employees regarding the current
issues the government is facing.
3.3 Risk Ranking
The deliberate and the accidental threats are ranked on basic of their severity and the
negative effect an organization might face. Deliberate threat is more dangerous than accidental
threat and therefore it is ranked at number one.
Rank 1: Deliberate Threat: Deliberate threats hold the number one position because the
information system of the Victorian government is probable of causing serious damage and data
loss to the information security system. Deliberate threats include access of information by
hacking into the system or by other malicious acts, which may result in serious data and
information loss (Luiijf, 2012). Therefore, this threat is allocated the number one ranking so that
Victorian government look into the matter with greater priority and importance and implement
necessary actions to eliminate any sort of deliberate risks from the system in order to protect
confidential information of the organization.
IT RISK MANAGEMENT
The threats that a system is exposed to mainly due to human error is termed as accidental
threat. Accidental threats are unintentional and can be eliminated with proper caution. The
number of accidental threats reported in the Victorian Government is huge mainly due to the
involvement of untrained employees. An organization is exposed to accidental threats only due
to its employees. Outsiders can never be a reason of accidental threats. Accidental threats lead to
certain circumstances that causes potential harm to the system in form of disclosure or
modification of data due to human error. The effects of accidental threats are therefore very
minor and can be eliminated from the system with little labor (Man et al., 2013). Victorian
government can eliminate the accidental threats by training their employees regarding the current
issues the government is facing.
3.3 Risk Ranking
The deliberate and the accidental threats are ranked on basic of their severity and the
negative effect an organization might face. Deliberate threat is more dangerous than accidental
threat and therefore it is ranked at number one.
Rank 1: Deliberate Threat: Deliberate threats hold the number one position because the
information system of the Victorian government is probable of causing serious damage and data
loss to the information security system. Deliberate threats include access of information by
hacking into the system or by other malicious acts, which may result in serious data and
information loss (Luiijf, 2012). Therefore, this threat is allocated the number one ranking so that
Victorian government look into the matter with greater priority and importance and implement
necessary actions to eliminate any sort of deliberate risks from the system in order to protect
confidential information of the organization.

8
IT RISK MANAGEMENT
Rank 2: Accidental Threats
Accidental threats are allotted the second position because effect of these threats can be
easily controlled or mitigated (Jouini, Rabai & Aissa, 2014). In Victorian government, the
accidental threats are the result of human error and therefore it can be easily controllable.
4. Security/ Risk management Issues in the organization
Risk is unavoidable and therefore, it should be managed with greater priority. A risk is a
probability of damage that may occur due to the result of external and internal vulnerabilities.
Risk implies future uncertainty and deviation from expected or calculated result. Therefore, an
effective risk management plan is essential to eliminate the negative effects of the risk. There are
mainly two different processes of risk management, internal risk management and the external
risk management. The risk management plan suitable for the Victorian government is discussed
in the following paragraphs.
4.1 Internal Security/ Risk Management
Internal security risk management includes the internal employees of an organization and
authorities to come together in resolving a problem and eliminating a risk. This is an effective
risk management strategy where the insider of an organization come together to eliminate the
risk. Internal risk management helps in elimination of the minor risks associated with a system.
Internal risk management does not involve any outsider in the risk management procedure and
therefore it is a cost effective solution. In this method, risk is eliminated by properly training the
user and researching about the effects and the impact of the risk. This process however, needs
involvement of honest employees, as dishonest employees may not suggest an effective solution
to the existing problem. One of the major benefits of internal risk management is that, the
IT RISK MANAGEMENT
Rank 2: Accidental Threats
Accidental threats are allotted the second position because effect of these threats can be
easily controlled or mitigated (Jouini, Rabai & Aissa, 2014). In Victorian government, the
accidental threats are the result of human error and therefore it can be easily controllable.
4. Security/ Risk management Issues in the organization
Risk is unavoidable and therefore, it should be managed with greater priority. A risk is a
probability of damage that may occur due to the result of external and internal vulnerabilities.
Risk implies future uncertainty and deviation from expected or calculated result. Therefore, an
effective risk management plan is essential to eliminate the negative effects of the risk. There are
mainly two different processes of risk management, internal risk management and the external
risk management. The risk management plan suitable for the Victorian government is discussed
in the following paragraphs.
4.1 Internal Security/ Risk Management
Internal security risk management includes the internal employees of an organization and
authorities to come together in resolving a problem and eliminating a risk. This is an effective
risk management strategy where the insider of an organization come together to eliminate the
risk. Internal risk management helps in elimination of the minor risks associated with a system.
Internal risk management does not involve any outsider in the risk management procedure and
therefore it is a cost effective solution. In this method, risk is eliminated by properly training the
user and researching about the effects and the impact of the risk. This process however, needs
involvement of honest employees, as dishonest employees may not suggest an effective solution
to the existing problem. One of the major benefits of internal risk management is that, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT RISK MANAGEMENT
employees or the insider of the organization gets a clear idea of the risk associated with a system
or process and takes necessary measures to eliminate the risk (Poolsappasit, Dewri & Ray,
2012). The minor issues or the risks associated with the Victorian government, which includes
the out of date security system, untrained users problem can be resolved effectively using the
internal risk management method. .
4.2. External Security/Risk Management
The risk management strategy, which includes the suggestion of suitable solution from an
outsourced staff, is known External risk management. The major issues of an organization that
cannot be resolved by internal risk management includes hiring of an experienced external agent
who would look into the matter, evaluate and analyzes the risks associated with a system and
recommend proper risk management strategy to eliminate those risks. An organization therefore,
uses external risk management strategy when the insider cannot identify the risk perpetrating in
the organization and the effects of the threat cannot be evaluated (Ali et al., 2014). External risk
management however, is subjected to a large amount of capital investment, as the organization
will have to pay a considerable amount to the external agent. The major benefit of the external
risk management is that, it yields guaranteed result. This is subjected to a proper decision based
on the choosing the external agent. An experienced agent is preferred as he will have a more
detailed knowledge of the risks and uncertainties, an organization is exposed to. The consultant
or the agent will however have the authority to access the important and confidential information
associated with the organization in order to evaluate and analyze the risks associated with a
system (Rakow, Heard & Newell, 2015).
4.3 The Risk Management Strategy for VIC
IT RISK MANAGEMENT
employees or the insider of the organization gets a clear idea of the risk associated with a system
or process and takes necessary measures to eliminate the risk (Poolsappasit, Dewri & Ray,
2012). The minor issues or the risks associated with the Victorian government, which includes
the out of date security system, untrained users problem can be resolved effectively using the
internal risk management method. .
4.2. External Security/Risk Management
The risk management strategy, which includes the suggestion of suitable solution from an
outsourced staff, is known External risk management. The major issues of an organization that
cannot be resolved by internal risk management includes hiring of an experienced external agent
who would look into the matter, evaluate and analyzes the risks associated with a system and
recommend proper risk management strategy to eliminate those risks. An organization therefore,
uses external risk management strategy when the insider cannot identify the risk perpetrating in
the organization and the effects of the threat cannot be evaluated (Ali et al., 2014). External risk
management however, is subjected to a large amount of capital investment, as the organization
will have to pay a considerable amount to the external agent. The major benefit of the external
risk management is that, it yields guaranteed result. This is subjected to a proper decision based
on the choosing the external agent. An experienced agent is preferred as he will have a more
detailed knowledge of the risks and uncertainties, an organization is exposed to. The consultant
or the agent will however have the authority to access the important and confidential information
associated with the organization in order to evaluate and analyze the risks associated with a
system (Rakow, Heard & Newell, 2015).
4.3 The Risk Management Strategy for VIC
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT RISK MANAGEMENT
The information security system of the VIC government is exposed to a number of threats
and security risks. The minor security risks associated with the system, which includes the old
and out of date security systems can be effectively managed using the internal risk management
strategy. However, the deliberate threats and the uncertainties that Victorian government is
exposed to might need the involvement of the external risk management. The external consultant
can help in evaluating the risks associated with VIC and therefore external risk management can
be an effective solution. The risk management strategies suggested by the external consultant
might provide a valid solution to the security risks the government is facing at this moment. This
is a very important decision and should be taken wisely. Therefore it is suggested that the
Victorian government undertake both internal and external security risk management in order to
eliminate the security issue and risks associated with the current system.
5. Risk Vs Uncertainty
Risk and uncertainty although appears similar, has varied differences. The contrasting
characters of risk and uncertainty is elaborated in the following paragraphs-
5.1 Risk
Risk associated with and organization implements the vulnerabilities associated with a
system or organization. The information system of the Victorian government is exposed to
certain risks, which includes the data security threats from an outsider, the loss of data due to
security breach and so on. This risk must be handled with highest priority in order to eliminate its
negative impacts (Silbey, 2013). The security system of VIC should be sturdy enough to
eliminate the information security risks and proper measures should be taken in order to
eliminate the risks associated. Different risk management procedures and strategies can be
IT RISK MANAGEMENT
The information security system of the VIC government is exposed to a number of threats
and security risks. The minor security risks associated with the system, which includes the old
and out of date security systems can be effectively managed using the internal risk management
strategy. However, the deliberate threats and the uncertainties that Victorian government is
exposed to might need the involvement of the external risk management. The external consultant
can help in evaluating the risks associated with VIC and therefore external risk management can
be an effective solution. The risk management strategies suggested by the external consultant
might provide a valid solution to the security risks the government is facing at this moment. This
is a very important decision and should be taken wisely. Therefore it is suggested that the
Victorian government undertake both internal and external security risk management in order to
eliminate the security issue and risks associated with the current system.
5. Risk Vs Uncertainty
Risk and uncertainty although appears similar, has varied differences. The contrasting
characters of risk and uncertainty is elaborated in the following paragraphs-
5.1 Risk
Risk associated with and organization implements the vulnerabilities associated with a
system or organization. The information system of the Victorian government is exposed to
certain risks, which includes the data security threats from an outsider, the loss of data due to
security breach and so on. This risk must be handled with highest priority in order to eliminate its
negative impacts (Silbey, 2013). The security system of VIC should be sturdy enough to
eliminate the information security risks and proper measures should be taken in order to
eliminate the risks associated. Different risk management procedures and strategies can be

11
IT RISK MANAGEMENT
implemented in order to eliminate the information security risks associated with the Victorian
government. Risk is controllable and managed and therefore it is less severe than uncertainties
that a system is exposed to (Rasmussen, 2013).
5.2. Uncertainty
Anything whose impact or effects cannot be determined or guessed is termed as
uncertainty. Uncertainty is furthermore dangerous than risk, as the effect of uncertainty can
never be predicted. Similar is the case with information security of Victorian government. There
are certain uncertainties associated with the Victorian government the major one being the
unidentified security issues and threats the organization is exposed to. Uncertainties may lead to
certain risks, which therefore is needed to be eliminated (Covello et al., 2013).
6. Risk Control and Risk Mitigation
Risk controlling is necessary to eliminate the negative effects of the threats, and
organization is exposed to. Risk mitigation works for reducing the effect of the threat or risk
present in an organization. There are certain risk management and mitigation processes that can
be considered for eliminating the associated risks. Risk mitigation is important mainly when the
risk avoidance is not possible. Identification and analyzing of the risk is very essential in order to
manage, control and mitigate the risk. Risk identification and ranking according to their adverse
effects is necessary for an effective risk management and mitigation. The external as well as the
risk management procedure can help the government in successful risk control and risk
mitigation. The different strategies that Victorian government can consider in risk controlling
and mitigation are elaborated in the following paragraphs-
6.1. Risk Mitigation: Risk Transfer
IT RISK MANAGEMENT
implemented in order to eliminate the information security risks associated with the Victorian
government. Risk is controllable and managed and therefore it is less severe than uncertainties
that a system is exposed to (Rasmussen, 2013).
5.2. Uncertainty
Anything whose impact or effects cannot be determined or guessed is termed as
uncertainty. Uncertainty is furthermore dangerous than risk, as the effect of uncertainty can
never be predicted. Similar is the case with information security of Victorian government. There
are certain uncertainties associated with the Victorian government the major one being the
unidentified security issues and threats the organization is exposed to. Uncertainties may lead to
certain risks, which therefore is needed to be eliminated (Covello et al., 2013).
6. Risk Control and Risk Mitigation
Risk controlling is necessary to eliminate the negative effects of the threats, and
organization is exposed to. Risk mitigation works for reducing the effect of the threat or risk
present in an organization. There are certain risk management and mitigation processes that can
be considered for eliminating the associated risks. Risk mitigation is important mainly when the
risk avoidance is not possible. Identification and analyzing of the risk is very essential in order to
manage, control and mitigate the risk. Risk identification and ranking according to their adverse
effects is necessary for an effective risk management and mitigation. The external as well as the
risk management procedure can help the government in successful risk control and risk
mitigation. The different strategies that Victorian government can consider in risk controlling
and mitigation are elaborated in the following paragraphs-
6.1. Risk Mitigation: Risk Transfer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





