Cybersecurity and Risk Management Challenges
VerifiedAdded on 2020/02/19
|16
|3803
|51
AI Summary
This assignment delves into the complexities of cybersecurity and risk management. It examines various threats, including insider attacks, and explores effective risk mitigation strategies. The discussion encompasses process mining techniques for identifying vulnerabilities, the role of uncertainty in risk assessment, and the importance of communication in addressing cybersecurity concerns. The assignment also touches upon the legal and regulatory aspects of cybersecurity compliance.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Security Threats and Risks of VIC Government
Name of the Student
Name of the University
Author’s note
Security Threats and Risks of VIC Government
Name of the Student
Name of the University
Author’s note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Executive Summary
The main aim of this report is to discuss the security threats of VIC Government of Australia.
This report also discusses in details, the distinction between deliberate or intentional and
accidental or unintentional threats. It also gives suggestions to control and mitigate all the types
of risks.
Executive Summary
The main aim of this report is to discuss the security threats of VIC Government of Australia.
This report also discusses in details, the distinction between deliberate or intentional and
accidental or unintentional threats. It also gives suggestions to control and mitigate all the types
of risks.

2SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Table of Contents
Introduction..........................................................................................................................3
1. Illustration of Security Risks and Threats in VIC Government......................................3
2. Explanation of the Diagram and Categorization of Risk Factors....................................5
2.1 Description of the components of diagram................................................................5
2.2 Classification of Risk Exposure Areas......................................................................8
3. Comparison and Ranking of Accidental and Deliberate Threats....................................9
4. Security or Risk Management Challenges of VIC Government...................................10
5. Risk Vs Uncertainty.......................................................................................................10
6. Risk Control and Mitigation of VIC Government.........................................................11
Conclusion.........................................................................................................................12
References..........................................................................................................................13
Table of Contents
Introduction..........................................................................................................................3
1. Illustration of Security Risks and Threats in VIC Government......................................3
2. Explanation of the Diagram and Categorization of Risk Factors....................................5
2.1 Description of the components of diagram................................................................5
2.2 Classification of Risk Exposure Areas......................................................................8
3. Comparison and Ranking of Accidental and Deliberate Threats....................................9
4. Security or Risk Management Challenges of VIC Government...................................10
5. Risk Vs Uncertainty.......................................................................................................10
6. Risk Control and Mitigation of VIC Government.........................................................11
Conclusion.........................................................................................................................12
References..........................................................................................................................13

3SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Introduction
The threats that any organization or government face is the chances of any types of
danger that tries to take the advantage of the weaknesses and vulnerabilities of the organization.
These threats can be called as the security threats of the government or business. This threat is
becoming one of the most important concerns in the present generation of IT environment. Every
firm has its individual type of weaknesses. Based on these weaknesses the threats can be
classified into various groups. Every state has an individual government. VIC Government is in
the control of a state in Australia called Victoria.
This report brings out the various categories and sub categories of threats of security that
are faced by the government of VIC. Different positions are awarded to the risks. These positions
are dependent on the severity of the risks and their effects. There are three types of classes of
risks are shown in this report like high level, medium level and low level. The most dangerous
and harmful type of risks are categorized under the type of external and intentional risks. They
are not under the control of the internal people. A proper and substantiated comparison of risk is
carried out in this report. The problems faced by the government while selecting the type of risk
management process in the organization are also discussed in brief. Uncertainty has been
differentiated from risk. Risk assessing and managing procedures have also been discussed here.
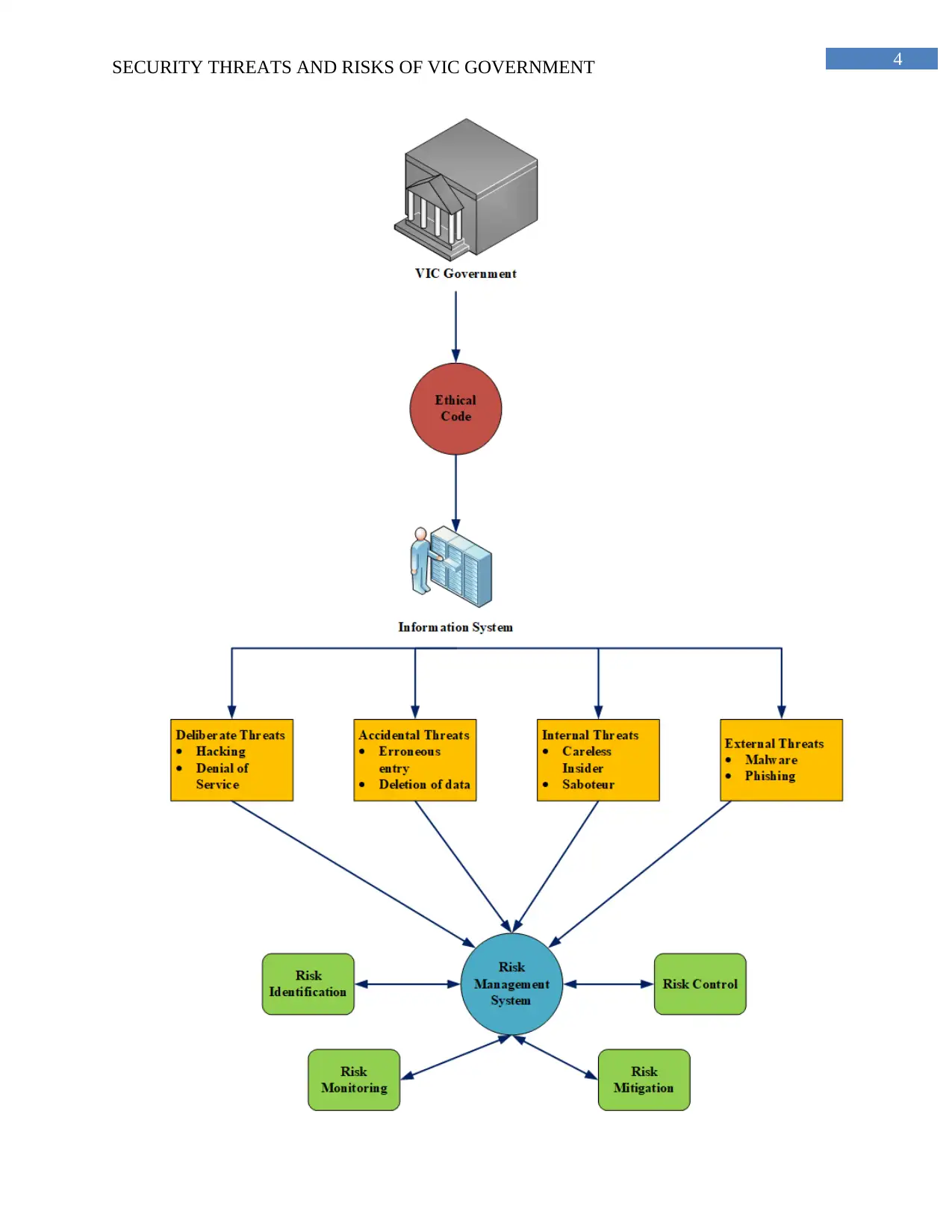
1. Illustration of Security Risks and Threats in VIC Government
This diagram presented here shows the security threats of the VIC government.
Introduction
The threats that any organization or government face is the chances of any types of
danger that tries to take the advantage of the weaknesses and vulnerabilities of the organization.
These threats can be called as the security threats of the government or business. This threat is
becoming one of the most important concerns in the present generation of IT environment. Every
firm has its individual type of weaknesses. Based on these weaknesses the threats can be
classified into various groups. Every state has an individual government. VIC Government is in
the control of a state in Australia called Victoria.
This report brings out the various categories and sub categories of threats of security that
are faced by the government of VIC. Different positions are awarded to the risks. These positions
are dependent on the severity of the risks and their effects. There are three types of classes of
risks are shown in this report like high level, medium level and low level. The most dangerous
and harmful type of risks are categorized under the type of external and intentional risks. They
are not under the control of the internal people. A proper and substantiated comparison of risk is
carried out in this report. The problems faced by the government while selecting the type of risk
management process in the organization are also discussed in brief. Uncertainty has been
differentiated from risk. Risk assessing and managing procedures have also been discussed here.
1. Illustration of Security Risks and Threats in VIC Government
This diagram presented here shows the security threats of the VIC government.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SECURITY THREATS AND RISKS OF VIC GOVERNMENT

5SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Figure 1: Factors of Risk and Threats in information system of VIC Government
(Source: Created by the author in Ms-Visio)
2. Explanation of the Diagram and Categorization of Risk Factors
2.1 Description of the components of diagram
The diagram that is presented in this report gives an overview of the entire government. It
shows the various categories and sub categories of security threats. These threats are harmful to
the operational and informational flow and working mechanism of the system. The diagram
points out that there is an ethical code that exists in the government. There is also a procedure for
identifying, monitoring, mitigating and controlling the risks.
Victorian Government: The state government that exists in Victoria, Australia is under
the threats of various types of risks. The various data storage in the IT system is vulnerable to
many risks. Misuse or deletion of such information can lead the entire state into trouble. The
whole state will be affected if there is any loss of data. The control of the data of the people is in
the hands of the government. Any attack on the IT system would not only affect the whole state
in a bad manner but also the country (Von Solms & Van Niekerk, 2013). Government has many
members and these members are also users of the IT system in the organization.
Information System: Government deals with sensitive information of the members of the
state. Efficient and effective management of information is required in order to keep the
harmony of the state as well as the organization. This information system is used for the purpose
of collecting, storing, processing and communicating the information within the organizational
Figure 1: Factors of Risk and Threats in information system of VIC Government
(Source: Created by the author in Ms-Visio)
2. Explanation of the Diagram and Categorization of Risk Factors
2.1 Description of the components of diagram
The diagram that is presented in this report gives an overview of the entire government. It
shows the various categories and sub categories of security threats. These threats are harmful to
the operational and informational flow and working mechanism of the system. The diagram
points out that there is an ethical code that exists in the government. There is also a procedure for
identifying, monitoring, mitigating and controlling the risks.
Victorian Government: The state government that exists in Victoria, Australia is under
the threats of various types of risks. The various data storage in the IT system is vulnerable to
many risks. Misuse or deletion of such information can lead the entire state into trouble. The
whole state will be affected if there is any loss of data. The control of the data of the people is in
the hands of the government. Any attack on the IT system would not only affect the whole state
in a bad manner but also the country (Von Solms & Van Niekerk, 2013). Government has many
members and these members are also users of the IT system in the organization.
Information System: Government deals with sensitive information of the members of the
state. Efficient and effective management of information is required in order to keep the
harmony of the state as well as the organization. This information system is used for the purpose
of collecting, storing, processing and communicating the information within the organizational

6SECURITY THREATS AND RISKS OF VIC GOVERNMENT
structure of the government. The government itself has the responsibility of maintaining and
handling the sensitive information of the users (Bommer, Crowley & Pinho, 2015). Proper
planning of handling the information system will help the government to work in a better
manner. The information system needs to be well protected by security policies.
Ethical Code: The ethical code shown in the diagram represents different rules and
norms that need to be followed in the government of VIC. This helps the working mechanism of
the government to be in an orderly fashion. The people of the government will be ethical and
there will not be any unethical issues arising by following and practicing such code of conduct.
This code will ensure that the unauthorized people will not get any access to the sensitive data
that is present in the database of the government. The ISO is integrated with the ethical code of
the government.
Security Risks and Security Threats: Any organization is vulnerable to the security
threats and attacks. This case study presents the various security threats that are faced by the
government of Victoria, which is a state in Australia. This VIC government has taken the
responsibility of the information of the entire state (Bommer, Crowley & Pinho, 2015).The
various data storage in the IT system is vulnerable to many risks. Misuse or deletion of such
information can lead the entire state into trouble. The whole state will be affected if there is any
loss of data. The control of the data of the people is in the hands of the government. Any attack
on the IT system would not only affect the whole state in a bad manner but also the country. The
flow of information can be affected by the security threats.
Accidental or Unintentional Threats: Unintentional threats can be defined as a threat
that occurs due to some kind of accidental activities (Alcorn, Good & Pain, 2013). There is no
structure of the government. The government itself has the responsibility of maintaining and
handling the sensitive information of the users (Bommer, Crowley & Pinho, 2015). Proper
planning of handling the information system will help the government to work in a better
manner. The information system needs to be well protected by security policies.
Ethical Code: The ethical code shown in the diagram represents different rules and
norms that need to be followed in the government of VIC. This helps the working mechanism of
the government to be in an orderly fashion. The people of the government will be ethical and
there will not be any unethical issues arising by following and practicing such code of conduct.
This code will ensure that the unauthorized people will not get any access to the sensitive data
that is present in the database of the government. The ISO is integrated with the ethical code of
the government.
Security Risks and Security Threats: Any organization is vulnerable to the security
threats and attacks. This case study presents the various security threats that are faced by the
government of Victoria, which is a state in Australia. This VIC government has taken the
responsibility of the information of the entire state (Bommer, Crowley & Pinho, 2015).The
various data storage in the IT system is vulnerable to many risks. Misuse or deletion of such
information can lead the entire state into trouble. The whole state will be affected if there is any
loss of data. The control of the data of the people is in the hands of the government. Any attack
on the IT system would not only affect the whole state in a bad manner but also the country. The
flow of information can be affected by the security threats.
Accidental or Unintentional Threats: Unintentional threats can be defined as a threat
that occurs due to some kind of accidental activities (Alcorn, Good & Pain, 2013). There is no
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

7SECURITY THREATS AND RISKS OF VIC GOVERNMENT
specific intention or harmful intention behind this type of threat. The flow of information is
affected and there is inefficiency in the operations of the organization. The employees can enter
wrong data or delete any data by mistake. This can be considered as one of the unintentional
threats of the government. Errors can take place also during the transmission of data. These types
of threats cannot be much harmful to the government because there are no harmful intentions
behind this threat.
Deliberate or Intentional Threats: These types of threats are extremely harmful in
nature. There are deliberate intentions behind this category of threats. The malicious attackers
and hackers are the main reasons behind this threat (Von Solms & Van Niekerk, 2013). The
motives behind this type of attacks are dangerous. The flow of information as well as the
operations in the government is affected in a severe manner due to these types of threats. The
diagram points out two deliberate threats like DOS (Denial of Service) and hacking.
External or Extrinsic Threats: Extrinsic threats are the threats that come from the
outside of the government. The agents of the threats are external to the organization (Lam, 2014).
They cannot be controlled by the internal mechanisms of the government. It is out of the control
of the government. External forces are responsible for playing a major role in the government.
The diagram illustrated above shows the presence of phishing attack and malware attacks
(Arachchilage & Love, 2014). The effect of this threat is very high and harmful.
Internal or Intrinsic Threats: There are various kinds of agents that are present inside
the organization that can lead to the loss and modification of sensitive information. Internal lacks
like lack in human resources, financial lack and mismanagement of the database leads to certain
types of threats that affect the operations in the government. The government has full control
specific intention or harmful intention behind this type of threat. The flow of information is
affected and there is inefficiency in the operations of the organization. The employees can enter
wrong data or delete any data by mistake. This can be considered as one of the unintentional
threats of the government. Errors can take place also during the transmission of data. These types
of threats cannot be much harmful to the government because there are no harmful intentions
behind this threat.
Deliberate or Intentional Threats: These types of threats are extremely harmful in
nature. There are deliberate intentions behind this category of threats. The malicious attackers
and hackers are the main reasons behind this threat (Von Solms & Van Niekerk, 2013). The
motives behind this type of attacks are dangerous. The flow of information as well as the
operations in the government is affected in a severe manner due to these types of threats. The
diagram points out two deliberate threats like DOS (Denial of Service) and hacking.
External or Extrinsic Threats: Extrinsic threats are the threats that come from the
outside of the government. The agents of the threats are external to the organization (Lam, 2014).
They cannot be controlled by the internal mechanisms of the government. It is out of the control
of the government. External forces are responsible for playing a major role in the government.
The diagram illustrated above shows the presence of phishing attack and malware attacks
(Arachchilage & Love, 2014). The effect of this threat is very high and harmful.
Internal or Intrinsic Threats: There are various kinds of agents that are present inside
the organization that can lead to the loss and modification of sensitive information. Internal lacks
like lack in human resources, financial lack and mismanagement of the database leads to certain
types of threats that affect the operations in the government. The government has full control

8SECURITY THREATS AND RISKS OF VIC GOVERNMENT
over these types of threats (Man et al., 2013). The degree of harmfulness of this category threats
is much less than the extrinsic threats. Rectification is possible in case of internal errors and
threats (Alcorn, Good & Pain, 2013). Communication failure can also lead to certain issues.
Insiders of the government are responsible for this type of threats (Stavrou et al., 2014). This
diagram shows the presence of careless insiders and saboteurs.
2.2 Classification of Risk Exposure Areas
There are several types of risks. Each risk has its own level of harmfulness. This level of
harmfulness is called the exposures. Every risk has its own impact and the degree varies with its
impact. In this report, the risks or threats of the VIC government are placed under any one of the
categories of medium, low, medium low and high area of risk (Lam, 2014).
High Risk Exposure: As the name suggests, the risks that fall under this category has a
severe impact on the flow of information in the VIC government. The risks that fall under this
category are extremely harmful in nature. The extrinsic threat is under this category of threats.
The agents of the threats are external to the organization (Lam, 2014). They cannot be controlled
by the internal mechanisms of the government. It is out of the control of the government.
External forces are responsible for playing a major role in the government. The intentional
threats are also under this category. Any threats that are not under the control of the government
are highly harmful. These types of threats are extremely harmful in nature. There are deliberate
intentions behind this category of threats. The malicious attackers and hackers are the main
reasons behind this threat (Von Solms & Van Niekerk, 2013). The motives behind this type of
attacks are dangerous. DOS and hacking are not under the control of the organization or
government and are termed as deliberate threats (Zargar, Joshi & Tipper, 2013). Rectification
process is very difficult and in most cases it cannot be rectified.
over these types of threats (Man et al., 2013). The degree of harmfulness of this category threats
is much less than the extrinsic threats. Rectification is possible in case of internal errors and
threats (Alcorn, Good & Pain, 2013). Communication failure can also lead to certain issues.
Insiders of the government are responsible for this type of threats (Stavrou et al., 2014). This
diagram shows the presence of careless insiders and saboteurs.
2.2 Classification of Risk Exposure Areas
There are several types of risks. Each risk has its own level of harmfulness. This level of
harmfulness is called the exposures. Every risk has its own impact and the degree varies with its
impact. In this report, the risks or threats of the VIC government are placed under any one of the
categories of medium, low, medium low and high area of risk (Lam, 2014).
High Risk Exposure: As the name suggests, the risks that fall under this category has a
severe impact on the flow of information in the VIC government. The risks that fall under this
category are extremely harmful in nature. The extrinsic threat is under this category of threats.
The agents of the threats are external to the organization (Lam, 2014). They cannot be controlled
by the internal mechanisms of the government. It is out of the control of the government.
External forces are responsible for playing a major role in the government. The intentional
threats are also under this category. Any threats that are not under the control of the government
are highly harmful. These types of threats are extremely harmful in nature. There are deliberate
intentions behind this category of threats. The malicious attackers and hackers are the main
reasons behind this threat (Von Solms & Van Niekerk, 2013). The motives behind this type of
attacks are dangerous. DOS and hacking are not under the control of the organization or
government and are termed as deliberate threats (Zargar, Joshi & Tipper, 2013). Rectification
process is very difficult and in most cases it cannot be rectified.

9SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Medium Risk Exposure: The threats under this category have a moderate impact on the
flow of operations of the government. The intrinsic risks will fall under this category. Errors that
are of technical nature can be rectified (Bommer, Crowley & Pinho, 2015). The VIC
governments can control such risks.
Medium Low Risk Exposure: The impact of such security threat varies from medium to
the very low level. Any type of spam falls under this category.
Low Risk Exposure: The accidental or unintentional threats can fall under this category.
The effect is low. It is not much harmful as it is possible to rectify this type of threat.
3. Comparison and Ranking of Accidental and Deliberate Threats
Deliberate Threat: This type of threat is ranked one. The reason behind such ranking is
that these threats are extremely harmful in nature. There are no such possible solutions to rectify
these threats. These threats occur because there are deliberate wrong intentions behind the
attacker. Hacking and malware fall under this category (Von Solms & Van Niekerk, 2013).
Examples: Malicious software (Green, Payne & Wood, 2013), phishing and hacking fall
under this category of threats. Other examples are virus and Trojan horse.
Accidental Threat: This type of threat is ranked two. The reason behind such ranks is its
low harmfulness. The unintentional threats fall under this category. Unintentional threats can be
defined as a threat that occurs due to some kind of accidental activities (Alcorn, Good & Pain,
2013). The flow of information is affected and there is inefficiency in the operations of the
organization. The employees can enter wrong data or delete any data by mistake. This can be
considered as one of the unintentional threats of the government. Errors can take place also
Medium Risk Exposure: The threats under this category have a moderate impact on the
flow of operations of the government. The intrinsic risks will fall under this category. Errors that
are of technical nature can be rectified (Bommer, Crowley & Pinho, 2015). The VIC
governments can control such risks.
Medium Low Risk Exposure: The impact of such security threat varies from medium to
the very low level. Any type of spam falls under this category.
Low Risk Exposure: The accidental or unintentional threats can fall under this category.
The effect is low. It is not much harmful as it is possible to rectify this type of threat.
3. Comparison and Ranking of Accidental and Deliberate Threats
Deliberate Threat: This type of threat is ranked one. The reason behind such ranking is
that these threats are extremely harmful in nature. There are no such possible solutions to rectify
these threats. These threats occur because there are deliberate wrong intentions behind the
attacker. Hacking and malware fall under this category (Von Solms & Van Niekerk, 2013).
Examples: Malicious software (Green, Payne & Wood, 2013), phishing and hacking fall
under this category of threats. Other examples are virus and Trojan horse.
Accidental Threat: This type of threat is ranked two. The reason behind such ranks is its
low harmfulness. The unintentional threats fall under this category. Unintentional threats can be
defined as a threat that occurs due to some kind of accidental activities (Alcorn, Good & Pain,
2013). The flow of information is affected and there is inefficiency in the operations of the
organization. The employees can enter wrong data or delete any data by mistake. This can be
considered as one of the unintentional threats of the government. Errors can take place also
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SECURITY THREATS AND RISKS OF VIC GOVERNMENT
during the transmission of data. There is no specific intention or harmful intention behind this
type of threat.
Example: Erroneous data entry, modification and deletion of information because of
some carelessness.
4. Security or Risk Management Challenges of VIC Government
The VIC government has to manage the risks in one of the following ways. Either they
can hire an external agency that will look after the process of risk management or they can
appoint their own employees for the purpose of managing the potential risks of the government.
Internal Management of Security: The government can appoint their own employees to
manage the process of risks in the organization. This option has certain advantages like there will
not be any time waste because the employees or member will be aware of the operations of the
government. There will not be much expense also behind this method. But this can lead to rivalry
among the members because of attainment of power. Conflicting roles will also lead to chaos.
External Management of Security: Agencies can be hired for the purpose of managing
risk. The benefit of this method is that the expertise knowledge of the hired agents will help the
government to manage risk in an orderly manner (Ali et al., 2014). The limitation of this method
is that the agent takes over the control of the entire operations of the government. There are high
chances of misunderstandings (Rakow, Heard & Newell, 2015). This can be misleading also.
5. Risk Vs Uncertainty
Risk and uncertainty go side by side. There is a thin line of difference between the two.
The probability of a win or loss of something that has a great worth can be called as risk. The
during the transmission of data. There is no specific intention or harmful intention behind this
type of threat.
Example: Erroneous data entry, modification and deletion of information because of
some carelessness.
4. Security or Risk Management Challenges of VIC Government
The VIC government has to manage the risks in one of the following ways. Either they
can hire an external agency that will look after the process of risk management or they can
appoint their own employees for the purpose of managing the potential risks of the government.
Internal Management of Security: The government can appoint their own employees to
manage the process of risks in the organization. This option has certain advantages like there will
not be any time waste because the employees or member will be aware of the operations of the
government. There will not be much expense also behind this method. But this can lead to rivalry
among the members because of attainment of power. Conflicting roles will also lead to chaos.
External Management of Security: Agencies can be hired for the purpose of managing
risk. The benefit of this method is that the expertise knowledge of the hired agents will help the
government to manage risk in an orderly manner (Ali et al., 2014). The limitation of this method
is that the agent takes over the control of the entire operations of the government. There are high
chances of misunderstandings (Rakow, Heard & Newell, 2015). This can be misleading also.
5. Risk Vs Uncertainty
Risk and uncertainty go side by side. There is a thin line of difference between the two.
The probability of a win or loss of something that has a great worth can be called as risk. The

11SECURITY THREATS AND RISKS OF VIC GOVERNMENT
nature of risk is very uncertain (Rasmussen, 2013). The risk in this context is the security threats
and vulnerabilities. Proper management and procedures can be taken to control and mitigate risk
(Silbey, 2013). Minimization of risk is possible but elimination of risk is not possible.
Uncertainty is something that cannot be avoided or eliminated. When the future of any
event is not known then the situation can be considered to be uncertain. Basis of risk is
uncertainty (Covello et al., 2013). Without uncertainty there is no risk. Operational inefficiencies
can occur due to this.
6. Risk Control and Mitigation of VIC Government
The process of risk management involves certain algorithmic steps that are to be followed
in a sequential manner. Right job and right people need to be aligned in a proper way (Perera &
Nand, 2015). In the initial stage, risk need to be identified correctly. Then proper monitoring
needs to be done that finds out the impact of the different types of threats in the government.
After the exposure of the risks, mitigation approaches must be used in order to mitigate the risk.
Control procedure of the risk needs to be implemented in a proper way to minimize the risks.
Analysis approach chooses the best alternative among the options available. Several strategies
are used in the strategy approach. Investigation approach is another method where severe
investigation is carried out to find out the defects in the present management and mitigate the
risk (Nowak, 2013). Risk evaluation and mitigation can take place in a proper way (Cheng, Liu
& Yao, 2017). VIC government can select any of the following approaches to mitigate the risk.
nature of risk is very uncertain (Rasmussen, 2013). The risk in this context is the security threats
and vulnerabilities. Proper management and procedures can be taken to control and mitigate risk
(Silbey, 2013). Minimization of risk is possible but elimination of risk is not possible.
Uncertainty is something that cannot be avoided or eliminated. When the future of any
event is not known then the situation can be considered to be uncertain. Basis of risk is
uncertainty (Covello et al., 2013). Without uncertainty there is no risk. Operational inefficiencies
can occur due to this.
6. Risk Control and Mitigation of VIC Government
The process of risk management involves certain algorithmic steps that are to be followed
in a sequential manner. Right job and right people need to be aligned in a proper way (Perera &
Nand, 2015). In the initial stage, risk need to be identified correctly. Then proper monitoring
needs to be done that finds out the impact of the different types of threats in the government.
After the exposure of the risks, mitigation approaches must be used in order to mitigate the risk.
Control procedure of the risk needs to be implemented in a proper way to minimize the risks.
Analysis approach chooses the best alternative among the options available. Several strategies
are used in the strategy approach. Investigation approach is another method where severe
investigation is carried out to find out the defects in the present management and mitigate the
risk (Nowak, 2013). Risk evaluation and mitigation can take place in a proper way (Cheng, Liu
& Yao, 2017). VIC government can select any of the following approaches to mitigate the risk.

12SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Conclusion
It can be concluded from this report that there are various types of security threats that are
involved in the system of the government of VIC. These threats and risks can be mitigated by
following sequential procedures. Risk management process can be used in order to control the
threats. Different positions were awarded to the risks. There are three types of classes of risks
shown in this report like high level, medium level and low level. The most dangerous and
harmful type of risks have been categorized under the type of external and intentional risks. A
proper and substantiated comparison of risk is carried out in this report. The problems faced by
the government while selecting the type of risk management process in the organization are also
discussed in brief. Comparison between risk and uncertainty is done in this report. Risk assessing
and managing procedures are briefly discussed.
Conclusion
It can be concluded from this report that there are various types of security threats that are
involved in the system of the government of VIC. These threats and risks can be mitigated by
following sequential procedures. Risk management process can be used in order to control the
threats. Different positions were awarded to the risks. There are three types of classes of risks
shown in this report like high level, medium level and low level. The most dangerous and
harmful type of risks have been categorized under the type of external and intentional risks. A
proper and substantiated comparison of risk is carried out in this report. The problems faced by
the government while selecting the type of risk management process in the organization are also
discussed in brief. Comparison between risk and uncertainty is done in this report. Risk assessing
and managing procedures are briefly discussed.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

13SECURITY THREATS AND RISKS OF VIC GOVERNMENT
References
Alcorn, A.M., Good, J. and Pain, H., (2013, July). Deliberate system-side errors as a potential
pedagogic strategy for exploratory virtual learning environments. In International
Conference on Artificial Intelligence in Education (pp. 483-492). Springer Berlin
Heidelberg
Ali, E., Denis, A. F., Kujur, F. E., & Chaudhary, M. (2014). Risk Management Strategies for
Accidental Risk Occurrence on Construction Sites–A Case Study of Allahabad. Journal
of Academia and Industrial Research (JAIR),3(2), 89.
Arachchilage, N. A. G., & Love, S. (2014). Security awareness of computer users: A phishing
threat avoidance perspective. Computers in Human Behavior, 38, 304-312.
Bommer, J. J., Crowley, H., & Pinho, R. (2015). A risk-mitigation approach to the management
of induced seismicity. Journal of Seismology, 19(2), 623-646.
Cheng, L., Liu, F., & Yao, D. D. (2017). Enterprise data breach: causes, challenges, prevention,
and future directions. Wiley Interdisciplinary Reviews: Data Mining and Knowledge
Discovery, 7(5).
Covello, V. T., Lave, L. B., Moghissi, A. A., & Uppuluri, V. R. R. (Eds.). (2013). Uncertainty in
risk assessment, risk management, and decision making (Vol. 4). Springer Science &
Business Media.
Green, D. E., Payne, R., & Wood, T. (2013). U.S. Patent No. 8,402,529. Washington, DC: U.S.
Patent and Trademark Office.
References
Alcorn, A.M., Good, J. and Pain, H., (2013, July). Deliberate system-side errors as a potential
pedagogic strategy for exploratory virtual learning environments. In International
Conference on Artificial Intelligence in Education (pp. 483-492). Springer Berlin
Heidelberg
Ali, E., Denis, A. F., Kujur, F. E., & Chaudhary, M. (2014). Risk Management Strategies for
Accidental Risk Occurrence on Construction Sites–A Case Study of Allahabad. Journal
of Academia and Industrial Research (JAIR),3(2), 89.
Arachchilage, N. A. G., & Love, S. (2014). Security awareness of computer users: A phishing
threat avoidance perspective. Computers in Human Behavior, 38, 304-312.
Bommer, J. J., Crowley, H., & Pinho, R. (2015). A risk-mitigation approach to the management
of induced seismicity. Journal of Seismology, 19(2), 623-646.
Cheng, L., Liu, F., & Yao, D. D. (2017). Enterprise data breach: causes, challenges, prevention,
and future directions. Wiley Interdisciplinary Reviews: Data Mining and Knowledge
Discovery, 7(5).
Covello, V. T., Lave, L. B., Moghissi, A. A., & Uppuluri, V. R. R. (Eds.). (2013). Uncertainty in
risk assessment, risk management, and decision making (Vol. 4). Springer Science &
Business Media.
Green, D. E., Payne, R., & Wood, T. (2013). U.S. Patent No. 8,402,529. Washington, DC: U.S.
Patent and Trademark Office.

14SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Healey, A. N. (2016). The insider threat to nuclear safety and security. Security Journal, 29(1),
23-38.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
Mans, R. S., van der Aalst, W. M., Vanwersch, R. J., & Moleman, A. J. (2013). Process mining
in healthcare: Data challenges when answering frequently posed questions. In Process
Support and Knowledge Representation in Health Care (pp. 140-153). Springer Berlin
Heidelberg.
Nowak, B. (2013). A 5-step strategy for harnessing global information growth.Information
Management, 47(4), 42.
Perera, R., & Nand, P. (2015, April). A multi-strategy approach for lexicalizing linked open data.
In International Conference on Intelligent Text Processing and Computational
Linguistics (pp. 348-363). Springer International Publishing.
Rakow, T., Heard, C. L., & Newell, B. R. (2015). Meeting Three Challenges in Risk
Communication Phenomena, Numbers, and Emotions. Policy Insights from the
Behavioral and Brain Sciences, 2(1), 147-156.
Rasmussen, S. (2013). Risk and uncertainty. In Production Economics (pp. 163-180). Springer
Berlin Heidelberg.
Silbey, S. S. (2013). Organizational Challenges to Regulatory Enforcement and Compliance A
New Common Sense about Regulation. The Annals of the American Academy of Political
and Social Science, 649(1), 6-20.
Healey, A. N. (2016). The insider threat to nuclear safety and security. Security Journal, 29(1),
23-38.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
Mans, R. S., van der Aalst, W. M., Vanwersch, R. J., & Moleman, A. J. (2013). Process mining
in healthcare: Data challenges when answering frequently posed questions. In Process
Support and Knowledge Representation in Health Care (pp. 140-153). Springer Berlin
Heidelberg.
Nowak, B. (2013). A 5-step strategy for harnessing global information growth.Information
Management, 47(4), 42.
Perera, R., & Nand, P. (2015, April). A multi-strategy approach for lexicalizing linked open data.
In International Conference on Intelligent Text Processing and Computational
Linguistics (pp. 348-363). Springer International Publishing.
Rakow, T., Heard, C. L., & Newell, B. R. (2015). Meeting Three Challenges in Risk
Communication Phenomena, Numbers, and Emotions. Policy Insights from the
Behavioral and Brain Sciences, 2(1), 147-156.
Rasmussen, S. (2013). Risk and uncertainty. In Production Economics (pp. 163-180). Springer
Berlin Heidelberg.
Silbey, S. S. (2013). Organizational Challenges to Regulatory Enforcement and Compliance A
New Common Sense about Regulation. The Annals of the American Academy of Political
and Social Science, 649(1), 6-20.

15SECURITY THREATS AND RISKS OF VIC GOVERNMENT
Spring, J. (2014). Fall 2014 SEI Research Review: Malware Analysis. CARNEGIE-MELLON
UNIV PITTSBURGH PA SOFTWARE ENGINEERING INST.
Stavrou, V., Kandias, M., Karoulas, G., & Gritzalis, D. (2014, September). Business Process
Modeling for Insider threat monitoring and handling. In International Conference on
Trust, Privacy and Security in Digital Business(pp. 119-131). Springer, Cham.
Steinberg, A. N. (2016). A model for threat assessment. In Fusion Methodologies in Crisis
Management (pp. 313-340). Springer International Publishing.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Zargar, S. T., Joshi, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed
denial of service (DDoS) flooding attacks. IEEE communications surveys &
tutorials, 15(4), 2046-2069.
Spring, J. (2014). Fall 2014 SEI Research Review: Malware Analysis. CARNEGIE-MELLON
UNIV PITTSBURGH PA SOFTWARE ENGINEERING INST.
Stavrou, V., Kandias, M., Karoulas, G., & Gritzalis, D. (2014, September). Business Process
Modeling for Insider threat monitoring and handling. In International Conference on
Trust, Privacy and Security in Digital Business(pp. 119-131). Springer, Cham.
Steinberg, A. N. (2016). A model for threat assessment. In Fusion Methodologies in Crisis
Management (pp. 313-340). Springer International Publishing.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Zargar, S. T., Joshi, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed
denial of service (DDoS) flooding attacks. IEEE communications surveys &
tutorials, 15(4), 2046-2069.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





