SELinux and Iptables: A Brief Overview
Added on 2023-06-08
14 Pages3617 Words247 Views
University
Essay Title
by
Your Name
Date
Lecturer’s Name and Course Number
Essay Title
by
Your Name
Date
Lecturer’s Name and Course Number

1. SELinux
A brief description of SELinux
SELinux (Security-Enhanced Linux) this is an integrated 2.6 times kernel architecture utilizing
the LSM (Linux security modules). This project was done by the SELinux community and the
(NSA) United States National Security Agency. Integration of Red Hat Enterprise Linux and
SELinux was a combined venture between the Red Hat and NSA
MAC (Mandatory Access Control) is a flexible system developed into Linux kernel which is
provided by SELinux. As per the Linux DAC (Discretionary Access Control), software or a
process operating as a client (SUID or UID) contains the client’s authorization to items like files,
sockets, and other procedures. Executing MACkernel shields the framework away from being
flawed or malicious software’s which could destroy or damage it.
For instance when an application which is a subject tries to view an item such as a file, the policy
implementation administrator in the kernel looks for an AVC (access vector cache); at this point
the subject and the object authorization are cached. I the event a choice cannot be made in the
information in the access vector cache, the inquiry progresses to the server responsible for
security, the searches the security setting of the software and the file arrangement. The
authorization is then denied or allowed with access vector cache: unauthorized message subtle in
/var/log/messages in the event the authorization is denied
A brief description of SELinux
SELinux (Security-Enhanced Linux) this is an integrated 2.6 times kernel architecture utilizing
the LSM (Linux security modules). This project was done by the SELinux community and the
(NSA) United States National Security Agency. Integration of Red Hat Enterprise Linux and
SELinux was a combined venture between the Red Hat and NSA
MAC (Mandatory Access Control) is a flexible system developed into Linux kernel which is
provided by SELinux. As per the Linux DAC (Discretionary Access Control), software or a
process operating as a client (SUID or UID) contains the client’s authorization to items like files,
sockets, and other procedures. Executing MACkernel shields the framework away from being
flawed or malicious software’s which could destroy or damage it.
For instance when an application which is a subject tries to view an item such as a file, the policy
implementation administrator in the kernel looks for an AVC (access vector cache); at this point
the subject and the object authorization are cached. I the event a choice cannot be made in the
information in the access vector cache, the inquiry progresses to the server responsible for
security, the searches the security setting of the software and the file arrangement. The
authorization is then denied or allowed with access vector cache: unauthorized message subtle in
/var/log/messages in the event the authorization is denied
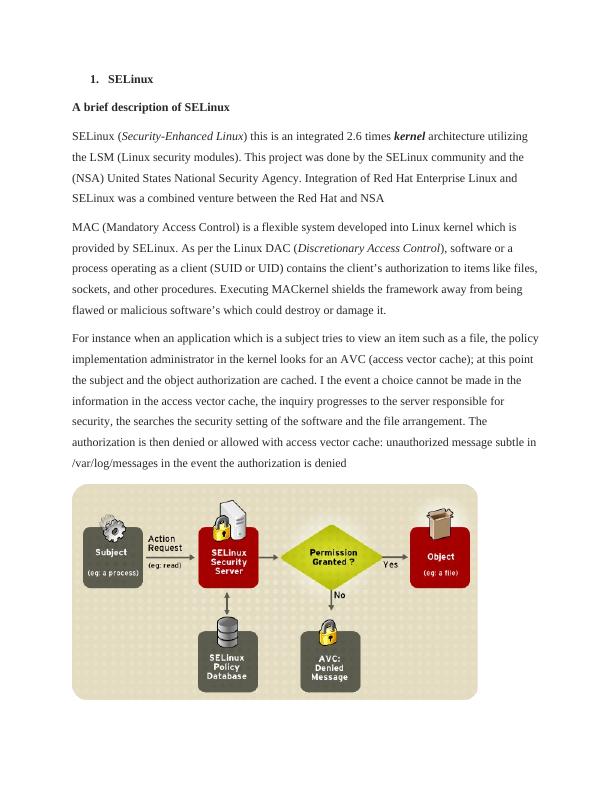
Figure 1: Decision-making process of SELinux
Results obtained
In this section, this paper will demonstrate the SELinux configuration files and the associated file
systems.
The SELinux Pseudo-File System
The SELinux pseudo-file framework comprises commands which are generally and normally
utilized by the kernel’s subsystem. The file type setting is analogous to the /proc/ pseudo-file
framework.
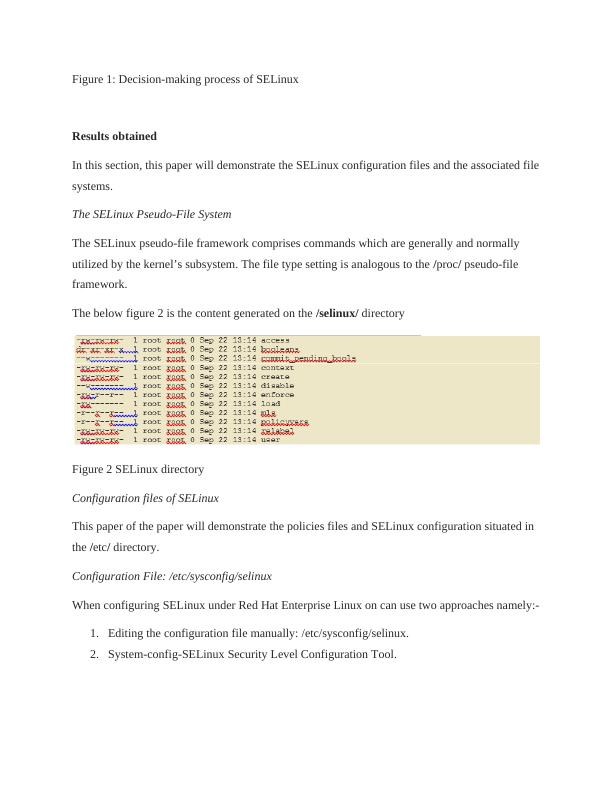
The below figure 2 is the content generated on the /selinux/ directory
Figure 2 SELinux directory
Configuration files of SELinux
This paper of the paper will demonstrate the policies files and SELinux configuration situated in
the /etc/ directory.
Configuration File: /etc/sysconfig/selinux
When configuring SELinux under Red Hat Enterprise Linux on can use two approaches namely:-
1. Editing the configuration file manually: /etc/sysconfig/selinux.
2. System-config-SELinux Security Level Configuration Tool.
Results obtained
In this section, this paper will demonstrate the SELinux configuration files and the associated file
systems.
The SELinux Pseudo-File System
The SELinux pseudo-file framework comprises commands which are generally and normally
utilized by the kernel’s subsystem. The file type setting is analogous to the /proc/ pseudo-file
framework.
The below figure 2 is the content generated on the /selinux/ directory
Figure 2 SELinux directory
Configuration files of SELinux
This paper of the paper will demonstrate the policies files and SELinux configuration situated in
the /etc/ directory.
Configuration File: /etc/sysconfig/selinux
When configuring SELinux under Red Hat Enterprise Linux on can use two approaches namely:-
1. Editing the configuration file manually: /etc/sysconfig/selinux.
2. System-config-SELinux Security Level Configuration Tool.
The primary configuration file for disabling or enabling SELinux is the
/etc/sysconfig/selinux and also for a configuration that the approach to implementing on the
system and the procedure on how to ensure that it is well implemented.
In the actual configuration file, /etc/selinux/config a meaningful configuration is contained in
the etc/sysconfig/selinux.
The below are full subsets of choices that are available for configuration
1. Defining the highest level state of SELinux on the system hence one utilize:
SELINUX=enforcing|permissive|disabled
Permissive – A policy is not enforced but a warning is printed by SELinux
system. This is a great tool for troubleshooting or debugging purposes. In this
permissive mode since more subjects can continue in actions thus more
denials are logged that can either be denied from taking place.
Enforcing- the enforcing of SELinux security policy.
Disabled- the enabling of SELinux is complete. the hooks of the SELinux are
detached from the kernel and the pseudo-file framework is unregistered.
Activities performed when SELinux is deactivated might bring about the system of the file never
again containing the right security setting, That is, the security setting characterized by the
approach. The most ideal approach to label the file framework again is by making the auto
relabel or the flag file and restart the computer. This leads to the relabel happening from the first
stages of the boot procedure before any other procedures start operating on the framework.
Utilizing this method implies that processes cannot incidentally make documents in the incorrect
setting or boot in the wrong setting.
It is conceivable to utilize the fix-files relabel command before empowering SELinux to relabel
the framework of the file. This technique isn't suggested due to the fact that after completing, it is
as yet conceivable to have other processes possibly operating on the framework in the incorrect
setting. These procedures would make documents that would likewise be in the incorrect setting.
/etc/sysconfig/selinux and also for a configuration that the approach to implementing on the
system and the procedure on how to ensure that it is well implemented.
In the actual configuration file, /etc/selinux/config a meaningful configuration is contained in
the etc/sysconfig/selinux.
The below are full subsets of choices that are available for configuration
1. Defining the highest level state of SELinux on the system hence one utilize:
SELINUX=enforcing|permissive|disabled
Permissive – A policy is not enforced but a warning is printed by SELinux
system. This is a great tool for troubleshooting or debugging purposes. In this
permissive mode since more subjects can continue in actions thus more
denials are logged that can either be denied from taking place.
Enforcing- the enforcing of SELinux security policy.
Disabled- the enabling of SELinux is complete. the hooks of the SELinux are
detached from the kernel and the pseudo-file framework is unregistered.
Activities performed when SELinux is deactivated might bring about the system of the file never
again containing the right security setting, That is, the security setting characterized by the
approach. The most ideal approach to label the file framework again is by making the auto
relabel or the flag file and restart the computer. This leads to the relabel happening from the first
stages of the boot procedure before any other procedures start operating on the framework.
Utilizing this method implies that processes cannot incidentally make documents in the incorrect
setting or boot in the wrong setting.
It is conceivable to utilize the fix-files relabel command before empowering SELinux to relabel
the framework of the file. This technique isn't suggested due to the fact that after completing, it is
as yet conceivable to have other processes possibly operating on the framework in the incorrect
setting. These procedures would make documents that would likewise be in the incorrect setting.

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Assignment about Hard Disk Encryptionlg...
|4
|1401
|20
Advanced Network Security: Installation and Configuration Guide for CentOS, Apache, PHP, MySQL, and Morelg...
|28
|1536
|248
