Wireless Sensor Network Fundamentals
VerifiedAdded on 2020/04/01
|22
|5654
|99
AI Summary
This assignment explores the core concepts of wireless sensor networks. It examines various network architectures, including single-hop and multi-hop configurations. Key communication protocols used in these networks are discussed, along with their roles in data transmission and network management. The assignment also investigates diverse applications of wireless sensor networks across different domains.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Sensor Network
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
1. Introduction............................................................................................................................2
2. Lab Setup................................................................................................................................2
2.1 Task-1.............................................................................................................................11
Requirements.........................................................................................................................11
Results....................................................................................................................................12
2.2 Task 2 - Single hop communication.............................................................................12
Requirements:........................................................................................................................12
Results....................................................................................................................................13
2.3 Lab Task-3.....................................................................................................................13
Requirements.........................................................................................................................13
Results....................................................................................................................................14
2.4 Task 4- Multihop communication...............................................................................14
Requirements.........................................................................................................................14
Results....................................................................................................................................14
3. Conclusion............................................................................................................................15
1. Introduction............................................................................................................................2
2. Lab Setup................................................................................................................................2
2.1 Task-1.............................................................................................................................11
Requirements.........................................................................................................................11
Results....................................................................................................................................12
2.2 Task 2 - Single hop communication.............................................................................12
Requirements:........................................................................................................................12
Results....................................................................................................................................13
2.3 Lab Task-3.....................................................................................................................13
Requirements.........................................................................................................................13
Results....................................................................................................................................14
2.4 Task 4- Multihop communication...............................................................................14
Requirements.........................................................................................................................14
Results....................................................................................................................................14
3. Conclusion............................................................................................................................15

1. Introduction
The wireless sensor network plays an important role in data communication systems like
commercial application, industrial application and many real time applications. The large
number of sensor node devices are spread in multiple fields. The sensor nodes are low power
devices and it can be in the order of hundred or it may be thousand. Sensor nodes are mainly
used to Comprises a large number of distribution in Wireless sensor network. The sensor nodes
are performing many tasks like smart sensing, target tracking, data aggregation, neighbor node
discovery in single hop and Multihop communication system. Current advances in
semiconductor, materials science and networking technologies are motivating the ubiquitous
distribution of large-scale WSNs (Wireless Sensor Networks).
In single hop communication to use the channel coding in WSNs with a star molded single-hop
structure, which is similar to the current cellular telephony networks. The single hop sensor
network have one common node with appropriate sufficient energy and computational power
resources to achieve the difficult channel decoding for entering packets. The larger networks of
numerous number of nodes will nearly does not have single hop connectivity for multiple
reasons. It may be more energy effective to communicate a message through the multi-hop
communications over small distances in its place of a single hop extensive distance
communication to the Base Station. A protocol for energy efficient both the single-hop and
multi-hop communications in WSNs is presented and it will be discussed. In the existing
approach, SNs form supportive clusters. Within each and every cluster, SNs can easily
communicate with each other with the help of multi-hop links, and these SN at the most recent
hop communicates with the Base Station by communicating the grouped multi-hop data.
The main objective of this project is to provide the solution for tasks like Binary counter, single
hop communication, Single hop communication with acknowledgement and Multihop
communication. The lab setup will be provided in detailed manner. The task’s requirements will
be provided for each and every tasks. The Micaz board and led's will be discussed in all the
requirements. The ActiveMessageC, AMReceiverC and AMSenderC components will be used
The wireless sensor network plays an important role in data communication systems like
commercial application, industrial application and many real time applications. The large
number of sensor node devices are spread in multiple fields. The sensor nodes are low power
devices and it can be in the order of hundred or it may be thousand. Sensor nodes are mainly
used to Comprises a large number of distribution in Wireless sensor network. The sensor nodes
are performing many tasks like smart sensing, target tracking, data aggregation, neighbor node
discovery in single hop and Multihop communication system. Current advances in
semiconductor, materials science and networking technologies are motivating the ubiquitous
distribution of large-scale WSNs (Wireless Sensor Networks).
In single hop communication to use the channel coding in WSNs with a star molded single-hop
structure, which is similar to the current cellular telephony networks. The single hop sensor
network have one common node with appropriate sufficient energy and computational power
resources to achieve the difficult channel decoding for entering packets. The larger networks of
numerous number of nodes will nearly does not have single hop connectivity for multiple
reasons. It may be more energy effective to communicate a message through the multi-hop
communications over small distances in its place of a single hop extensive distance
communication to the Base Station. A protocol for energy efficient both the single-hop and
multi-hop communications in WSNs is presented and it will be discussed. In the existing
approach, SNs form supportive clusters. Within each and every cluster, SNs can easily
communicate with each other with the help of multi-hop links, and these SN at the most recent
hop communicates with the Base Station by communicating the grouped multi-hop data.
The main objective of this project is to provide the solution for tasks like Binary counter, single
hop communication, Single hop communication with acknowledgement and Multihop
communication. The lab setup will be provided in detailed manner. The task’s requirements will
be provided for each and every tasks. The Micaz board and led's will be discussed in all the
requirements. The ActiveMessageC, AMReceiverC and AMSenderC components will be used

for transmission and receive the data. The tasks will be implemented by using Micaz board and
led’s.
2. Lab Setup
VirtualBox is much capable of x86 and AMD64/Intel64 virtualization item for big business and
in addition home utilize. It is not exclusively that a VirtualBox is to a greater degree which
includes rich, superior item for big business clients, it is additionally the main expert
arrangement that is uninhibitedly accessible as Open Source Software under the terms of the
GNU General Public License (GPL) rendition (Bakshi, 2017)
Virtual Machine
VM (Virtual machines) are based on the computer architecture. The virtual machine is a
simulation of a computer system. It provides the functionality of a physical computer
(Bourennane, n.d.). The implementation may contains the specialized software and hardware.
The various types of virtual machines are used and each machine have the numerous functions.
There are given below,
• Process VM
• System VM
The SVM (System Virtual Machine) also called as the full virtualization VM. The system VM
provides an additional substitute for a real or physical machine. It offers the functionality desired
to perform complete operating system. A hypervisor is used for the native execution in virtual
machine. It share and manage hardware, permitting for more number of environments which are
isolated from one another. The modern hypervisor is used for the hardware helped virtualization.
The process VM (Virtual Machine) are intended to perform computer programs in an
independent platform environment (Hać, 2003).
Ubuntu
It is an open source OS (Operating system) software for computers. Ubuntu software is
based on the debain architecture. Ubuntu is distribution systems of Linux and it is usually run on
led’s.
2. Lab Setup
VirtualBox is much capable of x86 and AMD64/Intel64 virtualization item for big business and
in addition home utilize. It is not exclusively that a VirtualBox is to a greater degree which
includes rich, superior item for big business clients, it is additionally the main expert
arrangement that is uninhibitedly accessible as Open Source Software under the terms of the
GNU General Public License (GPL) rendition (Bakshi, 2017)
Virtual Machine
VM (Virtual machines) are based on the computer architecture. The virtual machine is a
simulation of a computer system. It provides the functionality of a physical computer
(Bourennane, n.d.). The implementation may contains the specialized software and hardware.
The various types of virtual machines are used and each machine have the numerous functions.
There are given below,
• Process VM
• System VM
The SVM (System Virtual Machine) also called as the full virtualization VM. The system VM
provides an additional substitute for a real or physical machine. It offers the functionality desired
to perform complete operating system. A hypervisor is used for the native execution in virtual
machine. It share and manage hardware, permitting for more number of environments which are
isolated from one another. The modern hypervisor is used for the hardware helped virtualization.
The process VM (Virtual Machine) are intended to perform computer programs in an
independent platform environment (Hać, 2003).
Ubuntu
It is an open source OS (Operating system) software for computers. Ubuntu software is
based on the debain architecture. Ubuntu is distribution systems of Linux and it is usually run on
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

PC (Personal Computers). It is widely used for network server. Ubuntu software also runs on the
popular architecture and it including ARM machine, AMD and Intel.
In Ubuntu, user program run by very low privileges. The advantage of the Ubuntu is
cannot smash the user program files or other files. It cannot corrupt the OS. The sudo command
is used to allocate temporary rights and privileges for executing administrative responsibilities. It
allows the root version account to continue protected and services to check inexperienced
operators from inadvertently building catastrophic changes in system or opening safety holes in
Ubuntu. The system requests and requirements differ among Ubuntu products (López and Zhou,
2008).
VirtualBox keeps successively running on Linux, Windows and Solaris and it has bolsters a
considerable number of visitor working frameworks. However it is not restricted to Windows
Similarly, NT 4.0, 2000
1. XP, Server 2003,
2. Vista,
3. Windows 7,
4. Windows 8,
5. Windows 10.
VirtualBox is large effectively created with visit discharges and has regularly developing
rundown of highlights, upheld visitor working frameworks for the stages it keeps running on.
VirtualBox is a group exertion sponsored by a devoted organization. Everybody is urged to
contribute. But in case of Oracle, it guarantees the item which dependably meets the proficient
quality criteria (Kamila, n.d.).
VirtualBox is a unrestricted, it is open source and is a cross-stage application for creating,
overseeing and running VM virtual machines. PCs equipment parts are imitated by the host PC,
mainly the PC that runs the program. VirtualBox keep running on the OS such as Linux, Solaris
and so on.
It depends on the OS adaptation, however it means that it pays little mind to the host working
framework (Cichoń, Gȩbala and Klonowski, 2013).
popular architecture and it including ARM machine, AMD and Intel.
In Ubuntu, user program run by very low privileges. The advantage of the Ubuntu is
cannot smash the user program files or other files. It cannot corrupt the OS. The sudo command
is used to allocate temporary rights and privileges for executing administrative responsibilities. It
allows the root version account to continue protected and services to check inexperienced
operators from inadvertently building catastrophic changes in system or opening safety holes in
Ubuntu. The system requests and requirements differ among Ubuntu products (López and Zhou,
2008).
VirtualBox keeps successively running on Linux, Windows and Solaris and it has bolsters a
considerable number of visitor working frameworks. However it is not restricted to Windows
Similarly, NT 4.0, 2000
1. XP, Server 2003,
2. Vista,
3. Windows 7,
4. Windows 8,
5. Windows 10.
VirtualBox is large effectively created with visit discharges and has regularly developing
rundown of highlights, upheld visitor working frameworks for the stages it keeps running on.
VirtualBox is a group exertion sponsored by a devoted organization. Everybody is urged to
contribute. But in case of Oracle, it guarantees the item which dependably meets the proficient
quality criteria (Kamila, n.d.).
VirtualBox is a unrestricted, it is open source and is a cross-stage application for creating,
overseeing and running VM virtual machines. PCs equipment parts are imitated by the host PC,
mainly the PC that runs the program. VirtualBox keep running on the OS such as Linux, Solaris
and so on.
It depends on the OS adaptation, however it means that it pays little mind to the host working
framework (Cichoń, Gȩbala and Klonowski, 2013).
The need of VM
Utilization of virtual machines is greatly helpful for various reasons. For instance, user might
need to run a virtual machine to experiment with programming that user think may be perilous,
or user might need to experiment with another working framework without changing the way
user PC is now set up.
User may likewise need to utilize it for security purposes; for instance, user might need to make
a virtual machine only for web based managing account so user can make sure that there are no
spyware or trojans getting at user valuable information (Das and Stephen, 2012).
At long last, user might need to get it since user can. VirtualBox is totally free – there's no reason
not to download
The way to get
The most straightforward approach to get the most recent rendition of VB VirtualBox is
downloaded from the downloading page of VirtualBox site (Hashish, 2011)
There user can download the right form for user stage, or in case user are utilizing Linux user
can navigate to discover a rundown of guidelines for different Linux dispersions.
For every Linux circulation user are given the choice of downloading either the
In case user don't know which rendition of the working framework user are utilizing user are
probably utilizing the 32 bit form, thus user need to download the "i386" variant of VirtualBox.
Introducing VirtualBox is much as same as introducing some additional program on user stage,
so user shouldn't have any issue with establishment. On the off chance that user do stall out
Utilization of virtual machines is greatly helpful for various reasons. For instance, user might
need to run a virtual machine to experiment with programming that user think may be perilous,
or user might need to experiment with another working framework without changing the way
user PC is now set up.
User may likewise need to utilize it for security purposes; for instance, user might need to make
a virtual machine only for web based managing account so user can make sure that there are no
spyware or trojans getting at user valuable information (Das and Stephen, 2012).
At long last, user might need to get it since user can. VirtualBox is totally free – there's no reason
not to download
The way to get
The most straightforward approach to get the most recent rendition of VB VirtualBox is
downloaded from the downloading page of VirtualBox site (Hashish, 2011)
There user can download the right form for user stage, or in case user are utilizing Linux user
can navigate to discover a rundown of guidelines for different Linux dispersions.
For every Linux circulation user are given the choice of downloading either the
In case user don't know which rendition of the working framework user are utilizing user are
probably utilizing the 32 bit form, thus user need to download the "i386" variant of VirtualBox.
Introducing VirtualBox is much as same as introducing some additional program on user stage,
so user shouldn't have any issue with establishment. On the off chance that user do stall out

however, user can read the establishment control on the VirtualBox site (Karl, Willig and
Wolisz, 2004).
Using VirtualBox
Instructions to utilize VirtualBox
When started up VirtualBox interestingly VirtualBox Manager welcome the user. This is the
place user can make virtual machines, go on or off and roll out improvements to virtual
equipment accessible.
1. Clearly, VirtualBox making virtual machines for Windows XP
2. Windows 7 and
Ubuntu, as these are the no doubt contender for a VM (Profheath.org, 2017).
these are the main choices that VM(virtual machines )bring to the table. In case user feeling bold,
user might need to attempt one of the other Linux circulations,
1. Puppy Linux,
2. Arch Linux,
3. Linux Mint,
4. CentOS,
In the accompanying segments user will figure out how to make
1. Windows XP,
2. Windows 7 and
3. Ubuntu virtual machines. Each well-ordered area is trailed by numbered screenshots of
the means portrayed. Don't hesitate to counsel both the directions and the photos as user
fabricate user machines (Chandra, 2017).
3. Making a WinXP Virtual Machine
Wolisz, 2004).
Using VirtualBox
Instructions to utilize VirtualBox
When started up VirtualBox interestingly VirtualBox Manager welcome the user. This is the
place user can make virtual machines, go on or off and roll out improvements to virtual
equipment accessible.
1. Clearly, VirtualBox making virtual machines for Windows XP
2. Windows 7 and
Ubuntu, as these are the no doubt contender for a VM (Profheath.org, 2017).
these are the main choices that VM(virtual machines )bring to the table. In case user feeling bold,
user might need to attempt one of the other Linux circulations,
1. Puppy Linux,
2. Arch Linux,
3. Linux Mint,
4. CentOS,
In the accompanying segments user will figure out how to make
1. Windows XP,
2. Windows 7 and
3. Ubuntu virtual machines. Each well-ordered area is trailed by numbered screenshots of
the means portrayed. Don't hesitate to counsel both the directions and the photos as user
fabricate user machines (Chandra, 2017).
3. Making a WinXP Virtual Machine
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Stage 1 – The initial step to making any virtual machine is to tap on the "New" catch in the upper
left hand corner of the VirtualBox Manager window – it's a major blue star that is really difficult
(Meghji and Habibi, 2017).
Step by step instructions to utilize VirtualBox
This begins a New Virtual Machine Wizard which is helpful. The aim is to get another virtual
machine.
Stage 2 – Fill name of VM (Virtual Machine). What user ring it is completely to user – it's truly
so user can locate a particular VM (Virtual Machine) effectively when user have a wide range of
VMs in the administrator (SingleHop, 2017).
VirtualBox manual
VirtualBox will attempt to make sense of what OS user intend to keep running on the VM in
view of what and so on. On the off chance that the name of the VM in it some place it expect that
user will be introducing Windows XP and then it will alter itself as needs be. On the off chance
that user have an enigmatic name for it, however, don't stress. User can physically pick the OS
sort starting from the drop boxes beneath.
Once user have done that, tap on "Proceed" to go to the following stage.
Stage 3 – User will be solicited to choose the sum from RAM that user need to designate to the
virtual machine. The more user give the VM the smoother it'll run, yet be cautioned; memory
apportioned to the VM is memory that the host OS (that is, the PC user have introduced
VirtualBox on) won't have the capacity to utilize.
Things being what they are, the amount RAM would it be advisable for user to assign to the
VM? It relies upon various things. In case user are wanting to utilize just the Virtual Machine
user bear to give RAM since user won't request that the host Operating System is multitasking.
In event that, then again, user will be utilizing the VM in the meantime as doing bunches of
different stuffs on the host OS, user will need to be more moderate with the sums that user give
out. In any case, a great general dependable guideline is to distribute. To the extent hard statistics
Windows XP can run well on 513 MB of Random Access Memory(RAM) or in case user are
left hand corner of the VirtualBox Manager window – it's a major blue star that is really difficult
(Meghji and Habibi, 2017).
Step by step instructions to utilize VirtualBox
This begins a New Virtual Machine Wizard which is helpful. The aim is to get another virtual
machine.
Stage 2 – Fill name of VM (Virtual Machine). What user ring it is completely to user – it's truly
so user can locate a particular VM (Virtual Machine) effectively when user have a wide range of
VMs in the administrator (SingleHop, 2017).
VirtualBox manual
VirtualBox will attempt to make sense of what OS user intend to keep running on the VM in
view of what and so on. On the off chance that the name of the VM in it some place it expect that
user will be introducing Windows XP and then it will alter itself as needs be. On the off chance
that user have an enigmatic name for it, however, don't stress. User can physically pick the OS
sort starting from the drop boxes beneath.
Once user have done that, tap on "Proceed" to go to the following stage.
Stage 3 – User will be solicited to choose the sum from RAM that user need to designate to the
virtual machine. The more user give the VM the smoother it'll run, yet be cautioned; memory
apportioned to the VM is memory that the host OS (that is, the PC user have introduced
VirtualBox on) won't have the capacity to utilize.
Things being what they are, the amount RAM would it be advisable for user to assign to the
VM? It relies upon various things. In case user are wanting to utilize just the Virtual Machine
user bear to give RAM since user won't request that the host Operating System is multitasking.
In event that, then again, user will be utilizing the VM in the meantime as doing bunches of
different stuffs on the host OS, user will need to be more moderate with the sums that user give
out. In any case, a great general dependable guideline is to distribute. To the extent hard statistics
Windows XP can run well on 513 MB of Random Access Memory(RAM) or in case user are

feeling liberal user can drive the watercraft and an entire 1024MB (1GB), so I'd suggest allotting
between numbers.
Stage 4 – The following stage is to make a VHD. This makes a record on user hard drive is
utilized by VB to act similar to its own particular separate hard drive, enabling user to introduce
a working framework without stressing over wiping over user current information.
Ensure that
1. Boot Hard Disk
2. Make new hard plate
are select, at that point click "Proceed". It will begin and create New Virtual Disk Wizard. Snap
"Proceed with" again to continue.
VirtualBox manual
Next user will be inquired as to whether user need to make a "powerfully growing" circle (which
it is active plate starting now and into the foreseeable future) or a "settled size" plate. It has own
particular advantages. The colossal thing about a active plate is just as vast as the information
user can allot it a lot of room without worrying about if user will utilize it or user will come up
short on space. They're likewise a considerable measure speedier to make than a settled plate of
any huge size.
VirtualBox client manual
In any case, user will have to watch out for it, since its adaptability can likewise be its defeat.
Let's assume user make a dynamic plate and allot it 50 GB, at that point put around more than
20GB of information on it. The active circle record will appear as taking just 20GB of space on
the hard drive as indicated by user host OS. Extraordinary. User top off whatever is left over
space on user physical device in hard drive
between numbers.
Stage 4 – The following stage is to make a VHD. This makes a record on user hard drive is
utilized by VB to act similar to its own particular separate hard drive, enabling user to introduce
a working framework without stressing over wiping over user current information.
Ensure that
1. Boot Hard Disk
2. Make new hard plate
are select, at that point click "Proceed". It will begin and create New Virtual Disk Wizard. Snap
"Proceed with" again to continue.
VirtualBox manual
Next user will be inquired as to whether user need to make a "powerfully growing" circle (which
it is active plate starting now and into the foreseeable future) or a "settled size" plate. It has own
particular advantages. The colossal thing about a active plate is just as vast as the information
user can allot it a lot of room without worrying about if user will utilize it or user will come up
short on space. They're likewise a considerable measure speedier to make than a settled plate of
any huge size.
VirtualBox client manual
In any case, user will have to watch out for it, since its adaptability can likewise be its defeat.
Let's assume user make a dynamic plate and allot it 50 GB, at that point put around more than
20GB of information on it. The active circle record will appear as taking just 20GB of space on
the hard drive as indicated by user host OS. Extraordinary. User top off whatever is left over
space on user physical device in hard drive

Thing is, whether user start up the VM and attempt to add more information to the dynamic
circle, user will keep running into inconvenience – the virtual plate says that it's still got 30GB
free, however there's no place to really put that 30GB of information. The VM goes crazy,
suspecting that the hard drive is flopping, yet that is not valid. It simply needs some all the more
living room on bodily drive to store the information exposed to it's ready to spare.
This is the upside of the settled extent circle. Without a doubt, it's badly designed when users are
attempting to make sense space to give it, however it made user won't need to stress over it until
the end of time.
In this case we'll be utilizing dynamic circles, yet settled plates will work similarly too. Ensure
that "Progressively extending capacity" is chosen, at that point tap on "Proceed" once more.
Next users are made a request to pick name, For most of the user won't have to alterate the name
or the area, yet by tapping on the envelope symbol by the content box (ElProCus - Electronic
Projects for Engineering Students, 2017.
VirtualBox client manual
The size user should make the VHD relies upon and should say how much stuff user intend to
put in it, yet in the event that users are utilizing a dynamic plate it doesn't generally make a
difference on the off chance that user dispense it heaps of room. In case users are simply utilizing
it to run a couple of projects, the proposed size of 10GB ought to be bounty. It ensures the
settings are correct at that point click Proceed with, at that point Done (Mouser.in, 2017).
VirtualBox client manual
Stage 5 – At this point user should simply check over everything and ensure every one of the
settings are as user anticipate that them will be. At that point user simply need to click "Done"
and the VM will be made, prepared for user to introduce Windows.
A. Setup 1:
Direct to direct Communication Setup is clearly illustrated in the following
circle, user will keep running into inconvenience – the virtual plate says that it's still got 30GB
free, however there's no place to really put that 30GB of information. The VM goes crazy,
suspecting that the hard drive is flopping, yet that is not valid. It simply needs some all the more
living room on bodily drive to store the information exposed to it's ready to spare.
This is the upside of the settled extent circle. Without a doubt, it's badly designed when users are
attempting to make sense space to give it, however it made user won't need to stress over it until
the end of time.
In this case we'll be utilizing dynamic circles, yet settled plates will work similarly too. Ensure
that "Progressively extending capacity" is chosen, at that point tap on "Proceed" once more.
Next users are made a request to pick name, For most of the user won't have to alterate the name
or the area, yet by tapping on the envelope symbol by the content box (ElProCus - Electronic
Projects for Engineering Students, 2017.
VirtualBox client manual
The size user should make the VHD relies upon and should say how much stuff user intend to
put in it, yet in the event that users are utilizing a dynamic plate it doesn't generally make a
difference on the off chance that user dispense it heaps of room. In case users are simply utilizing
it to run a couple of projects, the proposed size of 10GB ought to be bounty. It ensures the
settings are correct at that point click Proceed with, at that point Done (Mouser.in, 2017).
VirtualBox client manual
Stage 5 – At this point user should simply check over everything and ensure every one of the
settings are as user anticipate that them will be. At that point user simply need to click "Done"
and the VM will be made, prepared for user to introduce Windows.
A. Setup 1:
Direct to direct Communication Setup is clearly illustrated in the following
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

In this system arrangement, NCA is relaxed through the RSSI worth of finally received
packet, it helps in approximating radial distance which is between the nodes (Ahlawat and
Mittal, 2015). To start the whole process, one of the devices needs the NCA to allow a single
link to the other device which is present in same cell. The NCA is morally founded on
localization substance of point to point system communication within the cell in which it
resolves whether it is going to be a normal cellular message. In this, statistics being relayed over
NCA or a D2D communication (Bhattacharyya, Kim and Pal, 2017).
Once D2D communication message has been accepted, getting device is trained by the NCA
to be in reception mode and transmitting device is trained to start the transmission. At end, both
directs a data transfer accomplishment notification to NCA. The connection is now closed and
the allocated resources are unrestricted.
B. Setup 2: Single Hop D2D Communication can be illustrated through the flow graph
packet, it helps in approximating radial distance which is between the nodes (Ahlawat and
Mittal, 2015). To start the whole process, one of the devices needs the NCA to allow a single
link to the other device which is present in same cell. The NCA is morally founded on
localization substance of point to point system communication within the cell in which it
resolves whether it is going to be a normal cellular message. In this, statistics being relayed over
NCA or a D2D communication (Bhattacharyya, Kim and Pal, 2017).
Once D2D communication message has been accepted, getting device is trained by the NCA
to be in reception mode and transmitting device is trained to start the transmission. At end, both
directs a data transfer accomplishment notification to NCA. The connection is now closed and
the allocated resources are unrestricted.
B. Setup 2: Single Hop D2D Communication can be illustrated through the flow graph

In this lab setup, deployed a NCA, 2 duplex and 1 relay device. Also, all devices have relay.
The NCA is processed via RSSI values of packets. It is then acknowledged from all other
devices, it can estimate the location which is present inside the cell. To start the process, one of
the devices asks NCA to permit a linking to additional device which is present within the cell.
The NCA is purely based on the RSSI info and it infers the challenging devices are not in the
variety of direct D2D communication. The NCA also differentiates that there is added device in
the proximity, accomplished of acting as a relay to both devices which want to connect. The data
packets are then received at the relay and it is directly forwarded directly to the endpoint
(SearchEnterpriseWAN, 2017).
TinyOS
It is an operating system. It is a development of open source. It is mainly designed or
created for wireless embedded sensor network. It has a feature of component rooted architecture.
It supports platform which involves windows 2000 XP associated with Cygwin and
Linux(Khemapech, 2017).
The NCA is processed via RSSI values of packets. It is then acknowledged from all other
devices, it can estimate the location which is present inside the cell. To start the process, one of
the devices asks NCA to permit a linking to additional device which is present within the cell.
The NCA is purely based on the RSSI info and it infers the challenging devices are not in the
variety of direct D2D communication. The NCA also differentiates that there is added device in
the proximity, accomplished of acting as a relay to both devices which want to connect. The data
packets are then received at the relay and it is directly forwarded directly to the endpoint
(SearchEnterpriseWAN, 2017).
TinyOS
It is an operating system. It is a development of open source. It is mainly designed or
created for wireless embedded sensor network. It has a feature of component rooted architecture.
It supports platform which involves windows 2000 XP associated with Cygwin and
Linux(Khemapech, 2017).

Installing TinyOS
First install the Ubuntu 12.04 or 13.04 or 14.04 or any other greater version. Then
enables the root user. Next to install the TinyOS, switch to the root user. And then open terminal
i.e. ctrl plus Alt plus T.
Procedure for the installation
First go to TinyProd and obey the following instructions
First step is to tell apt which is about the signing key for TinyProd.
The second step is to add the following lines to
Then installation of new packages.
Obtain the code from release repository of TinyOs
It will release real code for TinyOs in a folder which is named by tinyOS-release-tinyOS-2_1_2
that is inside the directory command.
Then we will require to add variables to the shell. The required one is on the following file.
First install the Ubuntu 12.04 or 13.04 or 14.04 or any other greater version. Then
enables the root user. Next to install the TinyOS, switch to the root user. And then open terminal
i.e. ctrl plus Alt plus T.
Procedure for the installation
First go to TinyProd and obey the following instructions
First step is to tell apt which is about the signing key for TinyProd.
The second step is to add the following lines to
Then installation of new packages.
Obtain the code from release repository of TinyOs
It will release real code for TinyOs in a folder which is named by tinyOS-release-tinyOS-2_1_2
that is inside the directory command.
Then we will require to add variables to the shell. The required one is on the following file.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
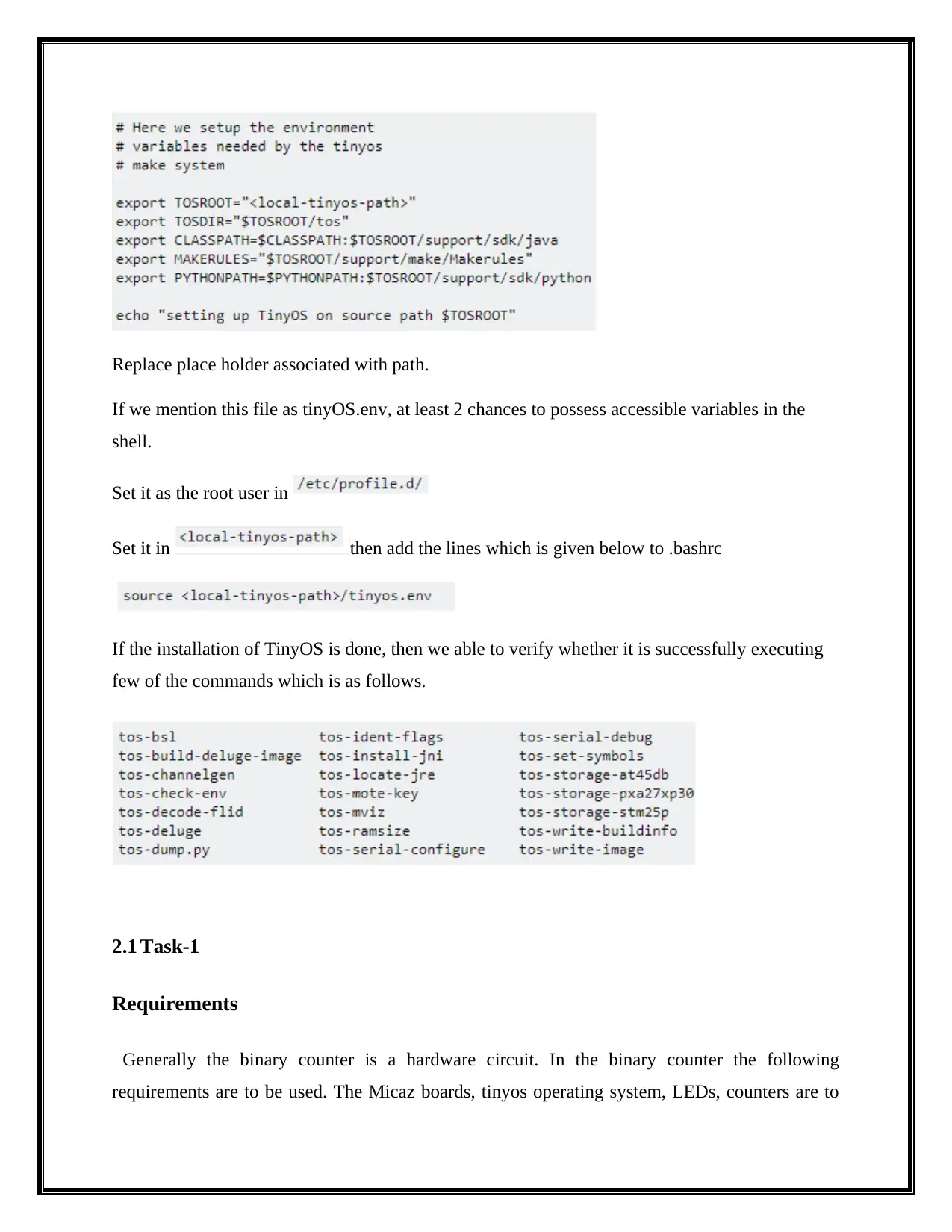
Replace place holder associated with path.
If we mention this file as tinyOS.env, at least 2 chances to possess accessible variables in the
shell.
Set it as the root user in
Set it in then add the lines which is given below to .bashrc
If the installation of TinyOS is done, then we able to verify whether it is successfully executing
few of the commands which is as follows.
2.1 Task-1
Requirements
Generally the binary counter is a hardware circuit. In the binary counter the following
requirements are to be used. The Micaz boards, tinyos operating system, LEDs, counters are to
If we mention this file as tinyOS.env, at least 2 chances to possess accessible variables in the
shell.
Set it as the root user in
Set it in then add the lines which is given below to .bashrc
If the installation of TinyOS is done, then we able to verify whether it is successfully executing
few of the commands which is as follows.
2.1 Task-1
Requirements
Generally the binary counter is a hardware circuit. In the binary counter the following
requirements are to be used. The Micaz boards, tinyos operating system, LEDs, counters are to

be used to make the binary counter(Han, 2013). The micas boards are the wireless measurement
system and it can be used for to make a binary counter system .This binary counter should be
done based on the tinyos operating system. In the binary counter using the leds on the micaz
board, current state of the system must be diplayed.There are three LEDs are to be used on the
micaz board. The binary counter must be changed for every states of 0.5s.In the system that can
be represented by the limited amount of states. The amount of state reached maximum means,
then the counter must be reset (LI, 2008). In LED the yellow led must be represented by the least
significant bit (LSB) and the red led must be represented by the most significant bit. The timer
module should to be used to make the lights flash at 0.5seconds intervals. The LED modules to
be used for to control the leds. The led0 is to be represented in red colour.Led1 is to be
represented by green colour.and led2 is to be represented by yellow colour (Www3.nd.edu,
2017).
Results
Results for single hop communication
With fresh batteries, entire sensors were produced. I tis significant to indicate that the power of
battery decides the information receptions and transmissions strength (Dalton et al., 2009).
Query vs. Auto send plot for the collection of data (Wu et al., 2017)
The above graph illustrates that, for query and auto send plot of information collection, readings
lost percentage because of an operation of enhancing amount of motes for every 3 mote spatial
arrangements (Levis and Culler, n.d.). Generally, in entire network spatial arrangements,
readings lost percentage enhances because of enhance in motes. .At the starting, reading lost
percentage enhances gradually, but spikes enhances extremely because of enhancing number of
motes. It is due to transmission number enhances constantly associated with motes number. The
reading lost percentage in query plot is at least ten percentage greater than the percentage of
reading lost in auto send plot (Levis and Gay, 2009).
system and it can be used for to make a binary counter system .This binary counter should be
done based on the tinyos operating system. In the binary counter using the leds on the micaz
board, current state of the system must be diplayed.There are three LEDs are to be used on the
micaz board. The binary counter must be changed for every states of 0.5s.In the system that can
be represented by the limited amount of states. The amount of state reached maximum means,
then the counter must be reset (LI, 2008). In LED the yellow led must be represented by the least
significant bit (LSB) and the red led must be represented by the most significant bit. The timer
module should to be used to make the lights flash at 0.5seconds intervals. The LED modules to
be used for to control the leds. The led0 is to be represented in red colour.Led1 is to be
represented by green colour.and led2 is to be represented by yellow colour (Www3.nd.edu,
2017).
Results
Results for single hop communication
With fresh batteries, entire sensors were produced. I tis significant to indicate that the power of
battery decides the information receptions and transmissions strength (Dalton et al., 2009).
Query vs. Auto send plot for the collection of data (Wu et al., 2017)
The above graph illustrates that, for query and auto send plot of information collection, readings
lost percentage because of an operation of enhancing amount of motes for every 3 mote spatial
arrangements (Levis and Culler, n.d.). Generally, in entire network spatial arrangements,
readings lost percentage enhances because of enhance in motes. .At the starting, reading lost
percentage enhances gradually, but spikes enhances extremely because of enhancing number of
motes. It is due to transmission number enhances constantly associated with motes number. The
reading lost percentage in query plot is at least ten percentage greater than the percentage of
reading lost in auto send plot (Levis and Gay, 2009).

2.2 Task 2 - Single hop communication
Requirements:
Single hop communication is a major part of communication in the computer networks
(Bourennane, n.d.).
Single hop is communication between one nodes to another node. It is used to pass the
information from one to another. The main requirement of the single hop communication is
Micaz boards and leds. The main purpose of the Micaz board is develop a program and that is
used to perform wireless communication. The ActiveMessageC, AMReceiverC and AMSenderC
components are used to transmit the data and receive data (Home.hib.no, 2017). The MICAZ
board is a 2.4GHz and it is mainly used for enabling less-power and wireless sensor networks.
The Micaz provides maximum data rate with 250kbps. And it utilize direct sequence that
resistant to radio frequency (RF) and offers security with inherent data. The main purpose of the
Micaz board is can perform a basic wireless communication in the sensor network. Normally
single hop communication is transmit a data from node 1 to node 2. Node 1 is transmit a number
within 0.5S. For every transition, transmission number is increased. Then node 2 is receive a
number from node1 and the transmitted data is displayed on its led’s. The purpose of led is
displaying a data from the nodes. The transmitted data is must able to display on two boards that
is Micaz board and led. By using three bits maximum number can be transmitted from one node
to another. If the maximum number is transmitted, then counter needs to be rest (Iyengar, 2011).
Results
Will be added
Requirements:
Single hop communication is a major part of communication in the computer networks
(Bourennane, n.d.).
Single hop is communication between one nodes to another node. It is used to pass the
information from one to another. The main requirement of the single hop communication is
Micaz boards and leds. The main purpose of the Micaz board is develop a program and that is
used to perform wireless communication. The ActiveMessageC, AMReceiverC and AMSenderC
components are used to transmit the data and receive data (Home.hib.no, 2017). The MICAZ
board is a 2.4GHz and it is mainly used for enabling less-power and wireless sensor networks.
The Micaz provides maximum data rate with 250kbps. And it utilize direct sequence that
resistant to radio frequency (RF) and offers security with inherent data. The main purpose of the
Micaz board is can perform a basic wireless communication in the sensor network. Normally
single hop communication is transmit a data from node 1 to node 2. Node 1 is transmit a number
within 0.5S. For every transition, transmission number is increased. Then node 2 is receive a
number from node1 and the transmitted data is displayed on its led’s. The purpose of led is
displaying a data from the nodes. The transmitted data is must able to display on two boards that
is Micaz board and led. By using three bits maximum number can be transmitted from one node
to another. If the maximum number is transmitted, then counter needs to be rest (Iyengar, 2011).
Results
Will be added
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2.3 Lab Task-3
Requirements
Single hop communication is more efficient than the muti hop communication. In the task
of single hop communication with acknowledgement the following requirements are to be
needed. In this type of communication system the micaz boards must be used. The micaz boards
can perform the basic wireless communication system. The program should be developed on the
micaz boards. In the single hop communication system two nodes are to be used. Node 1 is to be
required to transmit the number and that can be displayed on the leds (López and Zhou, 2008).
Node 2 is to be used to receive a number and that can be displayed on the leds.Node 2 is send an
acknowledgement once, if it is received the number. Node 1 must be used for to increment the
number once and it should receive the acknowledgement message from node 2.The number
transmitted in node 1, must be displayed on the micaz boards. If the maximum number is
transmitted means, then the maximum number can be sent by using 3 bits. The counter must to
be resetted for the maximum number transmission. The ActiveMessageC, AMSenderC,
AMReceiverC components must be used for to transmit and receives the data (Bharathidasan,
2017).
Results
Will be added
Requirements
Single hop communication is more efficient than the muti hop communication. In the task
of single hop communication with acknowledgement the following requirements are to be
needed. In this type of communication system the micaz boards must be used. The micaz boards
can perform the basic wireless communication system. The program should be developed on the
micaz boards. In the single hop communication system two nodes are to be used. Node 1 is to be
required to transmit the number and that can be displayed on the leds (López and Zhou, 2008).
Node 2 is to be used to receive a number and that can be displayed on the leds.Node 2 is send an
acknowledgement once, if it is received the number. Node 1 must be used for to increment the
number once and it should receive the acknowledgement message from node 2.The number
transmitted in node 1, must be displayed on the micaz boards. If the maximum number is
transmitted means, then the maximum number can be sent by using 3 bits. The counter must to
be resetted for the maximum number transmission. The ActiveMessageC, AMSenderC,
AMReceiverC components must be used for to transmit and receives the data (Bharathidasan,
2017).
Results
Will be added

2.4 Task 4- Multihop communication
Requirements
The Multihop communication is used for communicating from two or more nodes in the path.
The information is passed from one or more nodes. The Micaz board is a main requirement to
develop a program of wireless Multihop communication. Micaz board is used for indoor building
and security purpose. In MHC the data is transmitted in loop form that one or more nodes. The
main requirement of the MHC is led displaying components (Kanatas, Kalis and Efthymoglou,
2011). The number is transmitted and received from node1, node2, node3, node4. And once a
node received a new number, the number is must added by 1.then only message is passing to
another node. Hence, the received number of each node must display the current number on the
Micaz board and led's. The maximum number that can transmitted by using # bits. The counter is
reset when the maximum number has been transmitted (Khemapech, 2017)
Results
Will be added
3. Conclusion
Combining technologies, the new generations of wireless sensor networks which may varied
from wireless networks are developed. The wireless networks of smooth sensor that includes the
potential to modernize the collection of data and investigation for a host of applications are
investigated. Generally this wireless network consists of multiple shared devices with the help of
sensors to organize the environmental conditions. The mainstream of the already existing
applications for “wireless” sensors based on a single-hop wireless network in order to achieve
the Base Station for additional processing of the dignified occurrences.
The solution is provided for tasks such as Binary counter, single hop communication, Single
hop communication with acknowledgement and Multihop communication. The task’s
requirements are provided for each and every tasks. The lab setup is provided in detailed manner.
Requirements
The Multihop communication is used for communicating from two or more nodes in the path.
The information is passed from one or more nodes. The Micaz board is a main requirement to
develop a program of wireless Multihop communication. Micaz board is used for indoor building
and security purpose. In MHC the data is transmitted in loop form that one or more nodes. The
main requirement of the MHC is led displaying components (Kanatas, Kalis and Efthymoglou,
2011). The number is transmitted and received from node1, node2, node3, node4. And once a
node received a new number, the number is must added by 1.then only message is passing to
another node. Hence, the received number of each node must display the current number on the
Micaz board and led's. The maximum number that can transmitted by using # bits. The counter is
reset when the maximum number has been transmitted (Khemapech, 2017)
Results
Will be added
3. Conclusion
Combining technologies, the new generations of wireless sensor networks which may varied
from wireless networks are developed. The wireless networks of smooth sensor that includes the
potential to modernize the collection of data and investigation for a host of applications are
investigated. Generally this wireless network consists of multiple shared devices with the help of
sensors to organize the environmental conditions. The mainstream of the already existing
applications for “wireless” sensors based on a single-hop wireless network in order to achieve
the Base Station for additional processing of the dignified occurrences.
The solution is provided for tasks such as Binary counter, single hop communication, Single
hop communication with acknowledgement and Multihop communication. The task’s
requirements are provided for each and every tasks. The lab setup is provided in detailed manner.

The Micaz board and led's are discussed in all the requirements. The ActiveMessageC,
AMReceiverC and AMSenderC components are used for transmission and receive the data. The
tasks are implemented by using Micaz board and led’s.
References
Ahlawat, M. and Mittal, A. (2015). Different Communication Protocols for Wireless Sensor
Networks: A Review. IJARCCE, pp.213-216.
Bakshi, A. (2017). [online] Available at:
http://halcyon.usc.edu/~pk/prasannawebsite/papers/ewsn.pdf [Accessed 27 Sep. 2017].
Bharathidasan, A. (2017). [online] Available at: http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.84.5089&rep=rep1&type=pdf [Accessed 27 Sep. 2017].
Bhattacharyya, D., Kim, T. and Pal, S. (2017). A Comparative Study of Wireless Sensor
Networks and Their Routing Protocols.
Bourennane, S. (n.d.). Wireless communication and sensor network.
Bourennane, S. (n.d.). Wireless communication and sensor network.
Chandra, P. (2017). Securing wireless ad hoc networks: Part 1 - single and multi-hop ad hoc
networks. [online] Embedded. Available at:
https://www.embedded.com/design/connectivity/4007202/Securing-wireless-ad-hoc-
networks-Part-1--single-and-multi-hop-ad-hoc-networks [Accessed 27 Sep. 2017].
Cichoń, J., Gȩbala, M. and Klonowski, M. (2013). Ad-hoc, Mobile, and Wireless Network.
Berlin, Heidelberg: Springer Berlin Heidelberg.
Cichoń, J., Kubiak, P. and Kutyłowski, M. (2008). Algorithmic aspects of wireless sensor
networks. Berlin [u.a.]: Springer.
AMReceiverC and AMSenderC components are used for transmission and receive the data. The
tasks are implemented by using Micaz board and led’s.
References
Ahlawat, M. and Mittal, A. (2015). Different Communication Protocols for Wireless Sensor
Networks: A Review. IJARCCE, pp.213-216.
Bakshi, A. (2017). [online] Available at:
http://halcyon.usc.edu/~pk/prasannawebsite/papers/ewsn.pdf [Accessed 27 Sep. 2017].
Bharathidasan, A. (2017). [online] Available at: http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.84.5089&rep=rep1&type=pdf [Accessed 27 Sep. 2017].
Bhattacharyya, D., Kim, T. and Pal, S. (2017). A Comparative Study of Wireless Sensor
Networks and Their Routing Protocols.
Bourennane, S. (n.d.). Wireless communication and sensor network.
Bourennane, S. (n.d.). Wireless communication and sensor network.
Chandra, P. (2017). Securing wireless ad hoc networks: Part 1 - single and multi-hop ad hoc
networks. [online] Embedded. Available at:
https://www.embedded.com/design/connectivity/4007202/Securing-wireless-ad-hoc-
networks-Part-1--single-and-multi-hop-ad-hoc-networks [Accessed 27 Sep. 2017].
Cichoń, J., Gȩbala, M. and Klonowski, M. (2013). Ad-hoc, Mobile, and Wireless Network.
Berlin, Heidelberg: Springer Berlin Heidelberg.
Cichoń, J., Kubiak, P. and Kutyłowski, M. (2008). Algorithmic aspects of wireless sensor
networks. Berlin [u.a.]: Springer.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Dalton, A., Wahba, S., Dandamudi, S. and Hallstrom, J. (2009). Visualizing the runtime behavior
of embedded network systems: A toolkit for TinyOS. Science of Computer Programming,
74(7), pp.446-469.
Das, V. and Stephen, J. (2012). Advances in communication, network, and computing.
Heidelberg: Springer.
ElProCus - Electronic Projects for Engineering Students. (2017). Wireless Sensor Network
(WSN) Architecture And Applications. [online] Available at:
https://www.elprocus.com/architecture-of-wireless-sensor-network-and-applications/
[Accessed 27 Sep. 2017].
Hać, A. (2003). Wireless sensor network designs. Chichester: J. Wiley.
Hać, A. (2003). Wireless sensor network designs. Chichester: J. Wiley.
Hać, A. (2003). Wireless sensor network designs. Chichester: J. Wiley.
Han, Y. (2013). Multiple TinyOS Design for Managing Sensor Networks based the Virtual
Machine. Korea Institute of Information Technology Review, 11(9).
Hashish, S. (2011). Efficient communication protocols for sensor network architecture with
multiple mobile sinks. Ottawa: Library and Archives Canada = Bibliothèque et Archives
Canada.
Home.hib.no. (2017). TinyOS. [online] Available at:
http://home.hib.no/ansatte/aaks/tinyosInstallation.html [Accessed 27 Sep. 2017].
Ieeexplore.ieee.org. (2017). On Direct Diffusion Routing for Wireless Sensor Networks - IEEE
Conference Publication. [online] Available at: http://ieeexplore.ieee.org/document/7821862/
[Accessed 27 Sep. 2017].
Iyengar, S. (2011). Fundamentals of sensor network programming. Hoboken N.J.: Wiley-IEEE.
Kamila, N. (n.d.). Handbook of research on wireless sensor network trends, technologies, and
applications.
of embedded network systems: A toolkit for TinyOS. Science of Computer Programming,
74(7), pp.446-469.
Das, V. and Stephen, J. (2012). Advances in communication, network, and computing.
Heidelberg: Springer.
ElProCus - Electronic Projects for Engineering Students. (2017). Wireless Sensor Network
(WSN) Architecture And Applications. [online] Available at:
https://www.elprocus.com/architecture-of-wireless-sensor-network-and-applications/
[Accessed 27 Sep. 2017].
Hać, A. (2003). Wireless sensor network designs. Chichester: J. Wiley.
Hać, A. (2003). Wireless sensor network designs. Chichester: J. Wiley.
Hać, A. (2003). Wireless sensor network designs. Chichester: J. Wiley.
Han, Y. (2013). Multiple TinyOS Design for Managing Sensor Networks based the Virtual
Machine. Korea Institute of Information Technology Review, 11(9).
Hashish, S. (2011). Efficient communication protocols for sensor network architecture with
multiple mobile sinks. Ottawa: Library and Archives Canada = Bibliothèque et Archives
Canada.
Home.hib.no. (2017). TinyOS. [online] Available at:
http://home.hib.no/ansatte/aaks/tinyosInstallation.html [Accessed 27 Sep. 2017].
Ieeexplore.ieee.org. (2017). On Direct Diffusion Routing for Wireless Sensor Networks - IEEE
Conference Publication. [online] Available at: http://ieeexplore.ieee.org/document/7821862/
[Accessed 27 Sep. 2017].
Iyengar, S. (2011). Fundamentals of sensor network programming. Hoboken N.J.: Wiley-IEEE.
Kamila, N. (n.d.). Handbook of research on wireless sensor network trends, technologies, and
applications.

Kanatas, A., Kalis, A. and Efthymoglou, G. (2011). A single hop architecture exploiting
cooperative beamforming for wireless sensor networks. Physical Communication, 4(3),
pp.237-243.
Karl, H., Willig, A. and Wolisz, A. (2004). Wireless sensor networks. New York: Springer-
Verlag.
Khemapech, I. (2017). Feasibility Study of Direct Communication in Wireless Sensor Networks.
Khemapech, I. (2017). Feasibility Study of Direct Communication in Wireless Sensor Networks.
Levis, P. and Culler, D. (n.d.). A Tiny Virtual Machine for Sensor Networks. [online] Available
at: https://sing.stanford.edu/site/publications/asplos02levis.pdf.
Levis, P. and Gay, D. (2009). TinyOS Programming. [online] Available at:
http://csl.stanford.edu/~pal/pubs/tos-programming-web.pdf.
LI, X. (2008). A Node Scheduling Scheme Based on Virtual Coordinate in Sensor
Networks. Journal of Software, 19(8), pp.2089-2101.
López, J. and Zhou, J. (2008). Wireless sensor network security. Amsterdam: IOS Press.
López, J. and Zhou, J. (2008). Wireless sensor network security. Amsterdam: IOS Press.
Meghji, M. and Habibi, D. (2017). Transmission Power Control in Single-Hop and Multi-hop
Wireless Sensor Networks.
Mouser.in. (2017). Industrial Wireless Sensor Networks | Mouser. [online] Available at:
http://www.mouser.in/applications/rf-sensor-networks/ [Accessed 27 Sep. 2017].
Profheath.org. (2017). Multi-Hop Networking – Professor Robert W. Heath Jr.. [online]
Available at: http://www.profheath.org/research/multi-hop-networking/ [Accessed 27 Sep.
2017].
SearchEnterpriseWAN. (2017). What is a sensor network?. [online] Available at:
http://searchenterprisewan.techtarget.com/What-is-a-sensor-network [Accessed 27 Sep.
2017].
cooperative beamforming for wireless sensor networks. Physical Communication, 4(3),
pp.237-243.
Karl, H., Willig, A. and Wolisz, A. (2004). Wireless sensor networks. New York: Springer-
Verlag.
Khemapech, I. (2017). Feasibility Study of Direct Communication in Wireless Sensor Networks.
Khemapech, I. (2017). Feasibility Study of Direct Communication in Wireless Sensor Networks.
Levis, P. and Culler, D. (n.d.). A Tiny Virtual Machine for Sensor Networks. [online] Available
at: https://sing.stanford.edu/site/publications/asplos02levis.pdf.
Levis, P. and Gay, D. (2009). TinyOS Programming. [online] Available at:
http://csl.stanford.edu/~pal/pubs/tos-programming-web.pdf.
LI, X. (2008). A Node Scheduling Scheme Based on Virtual Coordinate in Sensor
Networks. Journal of Software, 19(8), pp.2089-2101.
López, J. and Zhou, J. (2008). Wireless sensor network security. Amsterdam: IOS Press.
López, J. and Zhou, J. (2008). Wireless sensor network security. Amsterdam: IOS Press.
Meghji, M. and Habibi, D. (2017). Transmission Power Control in Single-Hop and Multi-hop
Wireless Sensor Networks.
Mouser.in. (2017). Industrial Wireless Sensor Networks | Mouser. [online] Available at:
http://www.mouser.in/applications/rf-sensor-networks/ [Accessed 27 Sep. 2017].
Profheath.org. (2017). Multi-Hop Networking – Professor Robert W. Heath Jr.. [online]
Available at: http://www.profheath.org/research/multi-hop-networking/ [Accessed 27 Sep.
2017].
SearchEnterpriseWAN. (2017). What is a sensor network?. [online] Available at:
http://searchenterprisewan.techtarget.com/What-is-a-sensor-network [Accessed 27 Sep.
2017].

SingleHop. (2017). Network Design 101 - SingleHop. [online] Available at:
https://www.singlehop.com/blog/network-design-101/ [Accessed 27 Sep. 2017].
Wu, D., Zhang, B., Li, H. and Cheng, X. (2017). Target Counting in Wireless Sensor Networks.
Www3.nd.edu. (2017). Wireless Sensor Networks. [online] Available at:
https://www3.nd.edu/~cpoellab/teaching/cse40815/project1.html [Accessed 27 Sep. 2017].
https://www.singlehop.com/blog/network-design-101/ [Accessed 27 Sep. 2017].
Wu, D., Zhang, B., Li, H. and Cheng, X. (2017). Target Counting in Wireless Sensor Networks.
Www3.nd.edu. (2017). Wireless Sensor Networks. [online] Available at:
https://www3.nd.edu/~cpoellab/teaching/cse40815/project1.html [Accessed 27 Sep. 2017].
1 out of 22
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.

