Server Development and Maintenance Report - University Assignment
VerifiedAdded on 2023/01/20
|23
|4781
|28
Report
AI Summary
This report provides a comprehensive analysis of server development and maintenance, focusing on cloud computing models such as SAAS, PAAS, and IAAS. It defines these models, explores their characteristics, and illustrates their application through case studies like Netflix and iCloud. The report then delves into server usage in businesses, detailing server requirements for small, medium, and large organizations, along with cost-benefit analyses. It examines the evolution of computing, including the internet, and discusses technologies like virtualization, abstraction, data centers, and VPNs. The report also compares Azure and AWS, and defines infrastructure and colocation. The assignment addresses the needs of a newly established manufacturing company, SmartWat, and provides insights into setting up network infrastructure, databases, and other essential services. The report includes detailed server specifications and pricing for different business sizes, offering valuable information for IT professionals and students alike.

Running head: SERVER DEVELOPMENT AND MAINTENANCE
SERVER DEVELOPMENT AND MAINTENANCE
Name of the Student
Name of the University
Author Note
SERVER DEVELOPMENT AND MAINTENANCE
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SERVER DEVELOPMENT AND MAINTENANCE
Introduction Summary
SmartWat is one of the manufacturing company which is situated in UK and has its head office in
Midlands. The manufacturing unit of this new organization is located in China where numerous
smart devices are manufactures. The branches of this organization exists in the New York, London,
Beijing and Birmingham as well. As the company is entirely new it is going through the initial
phase of setting up its network infrastructure, databases, e-mail and file sharing facilities. It is
assumed that the company would be requiring shared application as well along with the folders,
files, printers, e-mail services and the CRM software. It is also assumed that the IoT devices would
be used which would be operating in an environment which is very secure. The entire workforce of
the organization would be using different smart as well as mobile devices for the purpose of
conducting its business as usual (BAU) activities.
SAAS, PAAS AND IAAS
In this context, three cloud models will be discussed that is SAAS, PAAS and IAAS. Along with
that an description is provided which describes in details that How a small business, medium
business (for medium business talk ‘smartwat’ as mentioned in the assignment introduction) and
large business use (SAAS, PAAS, IAAS) differently to each other. This discussion provides a
comprehensive overview of how these cloud models are being applied in industrial context and
what makes these cloud models so popular and which cloud model has market advantages
compared to others in terms of features offered.
SAAS:
-define it
Software as a Service (SaaS), which is also known as on-demand software, basically works on
traditional software distribution model with only difference being it is offered through internet
SERVER DEVELOPMENT AND MAINTENANCE
Introduction Summary
SmartWat is one of the manufacturing company which is situated in UK and has its head office in
Midlands. The manufacturing unit of this new organization is located in China where numerous
smart devices are manufactures. The branches of this organization exists in the New York, London,
Beijing and Birmingham as well. As the company is entirely new it is going through the initial
phase of setting up its network infrastructure, databases, e-mail and file sharing facilities. It is
assumed that the company would be requiring shared application as well along with the folders,
files, printers, e-mail services and the CRM software. It is also assumed that the IoT devices would
be used which would be operating in an environment which is very secure. The entire workforce of
the organization would be using different smart as well as mobile devices for the purpose of
conducting its business as usual (BAU) activities.
SAAS, PAAS AND IAAS
In this context, three cloud models will be discussed that is SAAS, PAAS and IAAS. Along with
that an description is provided which describes in details that How a small business, medium
business (for medium business talk ‘smartwat’ as mentioned in the assignment introduction) and
large business use (SAAS, PAAS, IAAS) differently to each other. This discussion provides a
comprehensive overview of how these cloud models are being applied in industrial context and
what makes these cloud models so popular and which cloud model has market advantages
compared to others in terms of features offered.
SAAS:
-define it
Software as a Service (SaaS), which is also known as on-demand software, basically works on
traditional software distribution model with only difference being it is offered through internet

2
SERVER DEVELOPMENT AND MAINTENANCE
(Abdel-Basset, Mohamed, and Chang, 2018). This model makes it possible to access the required
software purchased in the software package offered by the cloud vendor from anywhere anytime.
-talk about it
Some of the important characteristics of SAAS cloud model are the following:
Clients are charged on rental basis for the software they rent. They are not owner of any of
the software required for business applications.
The software that are used by the client are installed on remote server which is owned by the
cloud vendor. It is not installed on the client machine.
As software is not installed on the client machine, there is no requirement for hardware and
infrastructure required for installing software. Only high speed internet connection is
required for accessing the software rented for the business purpose.
Client does not need to care about data backup and software maintenance including software
security as these services are managed by the cloud vendor.
-USE CASE studies as an example
Netflix, a leading online content provider globally, has integrated Amazon Web Services with their
streaming services. According to the company this has made it possible for the company for
managing their extensive traffic from various devices for accessing the contents offered on the
platform. The robust infrastructure support that is required for this service is provided by the
hosting infrastructure that is offered by Amazon hosting services. The company also claims that it
has helped them to improve their productivity and helped them to make their micro service
architecture that is required for their services. According to Netflix, due to the infrastructure support
and software services offered by AWS has made it possible for the company in deploying thousands
SERVER DEVELOPMENT AND MAINTENANCE
(Abdel-Basset, Mohamed, and Chang, 2018). This model makes it possible to access the required
software purchased in the software package offered by the cloud vendor from anywhere anytime.
-talk about it
Some of the important characteristics of SAAS cloud model are the following:
Clients are charged on rental basis for the software they rent. They are not owner of any of
the software required for business applications.
The software that are used by the client are installed on remote server which is owned by the
cloud vendor. It is not installed on the client machine.
As software is not installed on the client machine, there is no requirement for hardware and
infrastructure required for installing software. Only high speed internet connection is
required for accessing the software rented for the business purpose.
Client does not need to care about data backup and software maintenance including software
security as these services are managed by the cloud vendor.
-USE CASE studies as an example
Netflix, a leading online content provider globally, has integrated Amazon Web Services with their
streaming services. According to the company this has made it possible for the company for
managing their extensive traffic from various devices for accessing the contents offered on the
platform. The robust infrastructure support that is required for this service is provided by the
hosting infrastructure that is offered by Amazon hosting services. The company also claims that it
has helped them to improve their productivity and helped them to make their micro service
architecture that is required for their services. According to Netflix, due to the infrastructure support
and software services offered by AWS has made it possible for the company in deploying thousands
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SERVER DEVELOPMENT AND MAINTENANCE
of servers that host terabytes of data, and this has provided users option for streaming Netflix shows
and movies on the web, tablets, or mobile devices and that too from anywhere around the world,
one of the reasons that makes this company a market leader in online entertainment industry
globally.
PAAS:
-define it
It is a cloud model that provides support for required hardware along with software tools that are
required for developing applications (Rittinghouse and Ransome, 2017). These tools are provided
by the third party cloud vendor. -talk about it
Some of the important characteristics of SAAS cloud model are the following:
Once tools are delivered, cloud service provider has no additional service to offer to the
clients. Once the tools are provided, it is now responsibility of the client to properly manage
the tolls and develop application on their own (Botta et al., 2016). Hence, PAAS is not well
suited for most of the client and their business requirements.
Once tools are purchased, client needs to invest for acquiring appropriate resources for their
application development which include support of developers. Along with that no assistance
is provided to the clients for application maintenance. Hence managing application and
maintain it properly depends on the client.
-USE CASE studies as an example
iCloud by apple is one of the biggest company that is developed with PAAS offered by google. It
offers remote access to the files, media and documents saved in the cloud platform. as the company
does not wants to have only developed applications hosted on cloud, the company being the market
leader in smartphone marker, wants have their own dedicated and customized application that is
SERVER DEVELOPMENT AND MAINTENANCE
of servers that host terabytes of data, and this has provided users option for streaming Netflix shows
and movies on the web, tablets, or mobile devices and that too from anywhere around the world,
one of the reasons that makes this company a market leader in online entertainment industry
globally.
PAAS:
-define it
It is a cloud model that provides support for required hardware along with software tools that are
required for developing applications (Rittinghouse and Ransome, 2017). These tools are provided
by the third party cloud vendor. -talk about it
Some of the important characteristics of SAAS cloud model are the following:
Once tools are delivered, cloud service provider has no additional service to offer to the
clients. Once the tools are provided, it is now responsibility of the client to properly manage
the tolls and develop application on their own (Botta et al., 2016). Hence, PAAS is not well
suited for most of the client and their business requirements.
Once tools are purchased, client needs to invest for acquiring appropriate resources for their
application development which include support of developers. Along with that no assistance
is provided to the clients for application maintenance. Hence managing application and
maintain it properly depends on the client.
-USE CASE studies as an example
iCloud by apple is one of the biggest company that is developed with PAAS offered by google. It
offers remote access to the files, media and documents saved in the cloud platform. as the company
does not wants to have only developed applications hosted on cloud, the company being the market
leader in smartphone marker, wants have their own dedicated and customized application that is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SERVER DEVELOPMENT AND MAINTENANCE
developed by their own experts and engineering team. They have only singed google to offer them
required hardware and software too, for their developers.
IAAS:
-define it
The IaaS is the Infrastructure as a Service which is actually an online service which provides some
high level of APIs that is used for dereferencing various types of low level details (Hashem et al.,
2015). This low level infrastructure includes computing resources, data partitioning, security,
scaling and location. It is one of the four types of cloud services that is managed over internet. -talk
about it (Chen et al., 2016). This low level infrastructure includes computing resources, data
partitioning, security, scaling and location. It is one of the four types of cloud services that is
managed over internet
-USE CASE studies as an example
Microsoft Azure is one of the most important organization which uses this IaaS service.
Define and apply how servers are used in businesses and your chosen business
A sever is a type of computer that is capable of delivering information to another computer
provided that the target computer is linked with the host computer through a network (Almorsy,
Grundy and Müller, 2016).
Servers are often used for running high end applications for which complex infrastructure is
required and these applications are known as server applications. In order to have data management
at centralised level, servers are often deployed (Gai et al., 2016). It is also considered for file
sharing. In organizations and business it is often required to manage shared resources like storage
and printers and for this kind of applications servers are deployed. Along with that servers are also
considered for applications like managing user identity and login details of the users.
SERVER DEVELOPMENT AND MAINTENANCE
developed by their own experts and engineering team. They have only singed google to offer them
required hardware and software too, for their developers.
IAAS:
-define it
The IaaS is the Infrastructure as a Service which is actually an online service which provides some
high level of APIs that is used for dereferencing various types of low level details (Hashem et al.,
2015). This low level infrastructure includes computing resources, data partitioning, security,
scaling and location. It is one of the four types of cloud services that is managed over internet. -talk
about it (Chen et al., 2016). This low level infrastructure includes computing resources, data
partitioning, security, scaling and location. It is one of the four types of cloud services that is
managed over internet
-USE CASE studies as an example
Microsoft Azure is one of the most important organization which uses this IaaS service.
Define and apply how servers are used in businesses and your chosen business
A sever is a type of computer that is capable of delivering information to another computer
provided that the target computer is linked with the host computer through a network (Almorsy,
Grundy and Müller, 2016).
Servers are often used for running high end applications for which complex infrastructure is
required and these applications are known as server applications. In order to have data management
at centralised level, servers are often deployed (Gai et al., 2016). It is also considered for file
sharing. In organizations and business it is often required to manage shared resources like storage
and printers and for this kind of applications servers are deployed. Along with that servers are also
considered for applications like managing user identity and login details of the users.

5
SERVER DEVELOPMENT AND MAINTENANCE
Having backup for important business data is a major requirement for any business. This backup not
only include organisational data, but it also considers backup for client data (Marinescu, 2017).
Now for a medium to large business, there are huge amount of client as well as organisational data
and hence it is not possible to manage this service manually and hence automation is required (Ali,
Khan and Vasilakos, 2015). Servers provide option for automatic data backup. Along with, servers
are also deployed for remote access to files and applications require for managing application and
services required for managing business.
Securing network is another major requirement for any business as it ensures data security (Stergiou
et al., 2018). Now in order to ensure that additional security suits are required which include
firewalls, intrusion detection, user access management, and software updates. It is not possible to
integrate these features and services with the network without support for server and hence servers
are considered in business (Li et al., 2015).
Explore the evolution of computing
-when did it start
-how did it start
-Mention the internet-who invented it & when did it come out etc.
-Nomad computing, cloud computing, distributed computing, cluster computing
Differences between VPS-shared VPS & Dedicated VPS
Explore & Justify- Cost Benefit Analysis
-What server is needed for small, medium and large organisation
Server requirements for small business:
1. Windows Small Business Server 2003 Standard Edition:
SERVER DEVELOPMENT AND MAINTENANCE
Having backup for important business data is a major requirement for any business. This backup not
only include organisational data, but it also considers backup for client data (Marinescu, 2017).
Now for a medium to large business, there are huge amount of client as well as organisational data
and hence it is not possible to manage this service manually and hence automation is required (Ali,
Khan and Vasilakos, 2015). Servers provide option for automatic data backup. Along with, servers
are also deployed for remote access to files and applications require for managing application and
services required for managing business.
Securing network is another major requirement for any business as it ensures data security (Stergiou
et al., 2018). Now in order to ensure that additional security suits are required which include
firewalls, intrusion detection, user access management, and software updates. It is not possible to
integrate these features and services with the network without support for server and hence servers
are considered in business (Li et al., 2015).
Explore the evolution of computing
-when did it start
-how did it start
-Mention the internet-who invented it & when did it come out etc.
-Nomad computing, cloud computing, distributed computing, cluster computing
Differences between VPS-shared VPS & Dedicated VPS
Explore & Justify- Cost Benefit Analysis
-What server is needed for small, medium and large organisation
Server requirements for small business:
1. Windows Small Business Server 2003 Standard Edition:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SERVER DEVELOPMENT AND MAINTENANCE
A Pentium II 300-megahertz (MHz)-or-compatible processor
256 megabytes (MB) of random access memory (RAM)
4 gigabytes (GB) of available hard disk space
A CD-ROM or a DVD-ROM drive
A network adapter from the Microsoft Windows Server 2003 Hardware Compatibility List
(HCL)
A video graphics adapter from the Windows Server 2003 HCL that can support 256 colors
and a resolution of 800 by 600 dots per inch (dpi)
A dedicated Class 1 fax modem for fax service
2. Windows Small Business Server 2003 Premium Edition:
A Pentium II 300-MHz-or-compatible processor
256 MB of RAM
5 GB of available hard disk space
A CD-ROM or a DVD-ROM drive
A network adapter from the Windows Server 2003 HCL
A video graphics adapter that can support 256 colors and a resolution of 800 by 600 dpi
from the Windows Server 2003 HCL
A dedicated Class 1 fax modem for fax services
SERVER DEVELOPMENT AND MAINTENANCE
A Pentium II 300-megahertz (MHz)-or-compatible processor
256 megabytes (MB) of random access memory (RAM)
4 gigabytes (GB) of available hard disk space
A CD-ROM or a DVD-ROM drive
A network adapter from the Microsoft Windows Server 2003 Hardware Compatibility List
(HCL)
A video graphics adapter from the Windows Server 2003 HCL that can support 256 colors
and a resolution of 800 by 600 dots per inch (dpi)
A dedicated Class 1 fax modem for fax service
2. Windows Small Business Server 2003 Premium Edition:
A Pentium II 300-MHz-or-compatible processor
256 MB of RAM
5 GB of available hard disk space
A CD-ROM or a DVD-ROM drive
A network adapter from the Windows Server 2003 HCL
A video graphics adapter that can support 256 colors and a resolution of 800 by 600 dpi
from the Windows Server 2003 HCL
A dedicated Class 1 fax modem for fax services
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
SERVER DEVELOPMENT AND MAINTENANCE
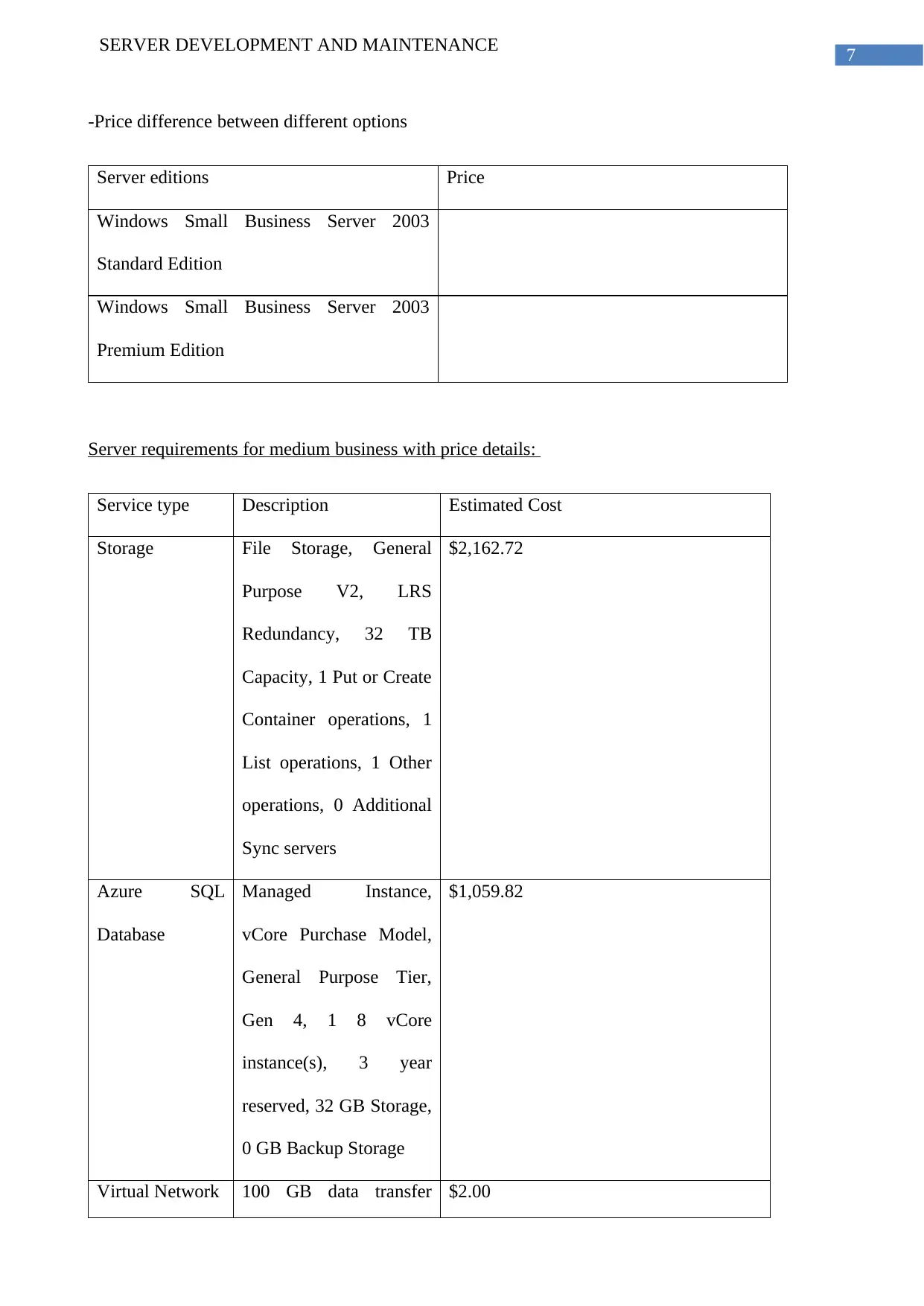
-Price difference between different options
Server editions Price
Windows Small Business Server 2003
Standard Edition
Windows Small Business Server 2003
Premium Edition
Server requirements for medium business with price details:
Service type Description Estimated Cost
Storage File Storage, General
Purpose V2, LRS
Redundancy, 32 TB
Capacity, 1 Put or Create
Container operations, 1
List operations, 1 Other
operations, 0 Additional
Sync servers
$2,162.72
Azure SQL
Database
Managed Instance,
vCore Purchase Model,
General Purpose Tier,
Gen 4, 1 8 vCore
instance(s), 3 year
reserved, 32 GB Storage,
0 GB Backup Storage
$1,059.82
Virtual Network 100 GB data transfer $2.00
SERVER DEVELOPMENT AND MAINTENANCE
-Price difference between different options
Server editions Price
Windows Small Business Server 2003
Standard Edition
Windows Small Business Server 2003
Premium Edition
Server requirements for medium business with price details:
Service type Description Estimated Cost
Storage File Storage, General
Purpose V2, LRS
Redundancy, 32 TB
Capacity, 1 Put or Create
Container operations, 1
List operations, 1 Other
operations, 0 Additional
Sync servers
$2,162.72
Azure SQL
Database
Managed Instance,
vCore Purchase Model,
General Purpose Tier,
Gen 4, 1 8 vCore
instance(s), 3 year
reserved, 32 GB Storage,
0 GB Backup Storage
$1,059.82
Virtual Network 100 GB data transfer $2.00
8
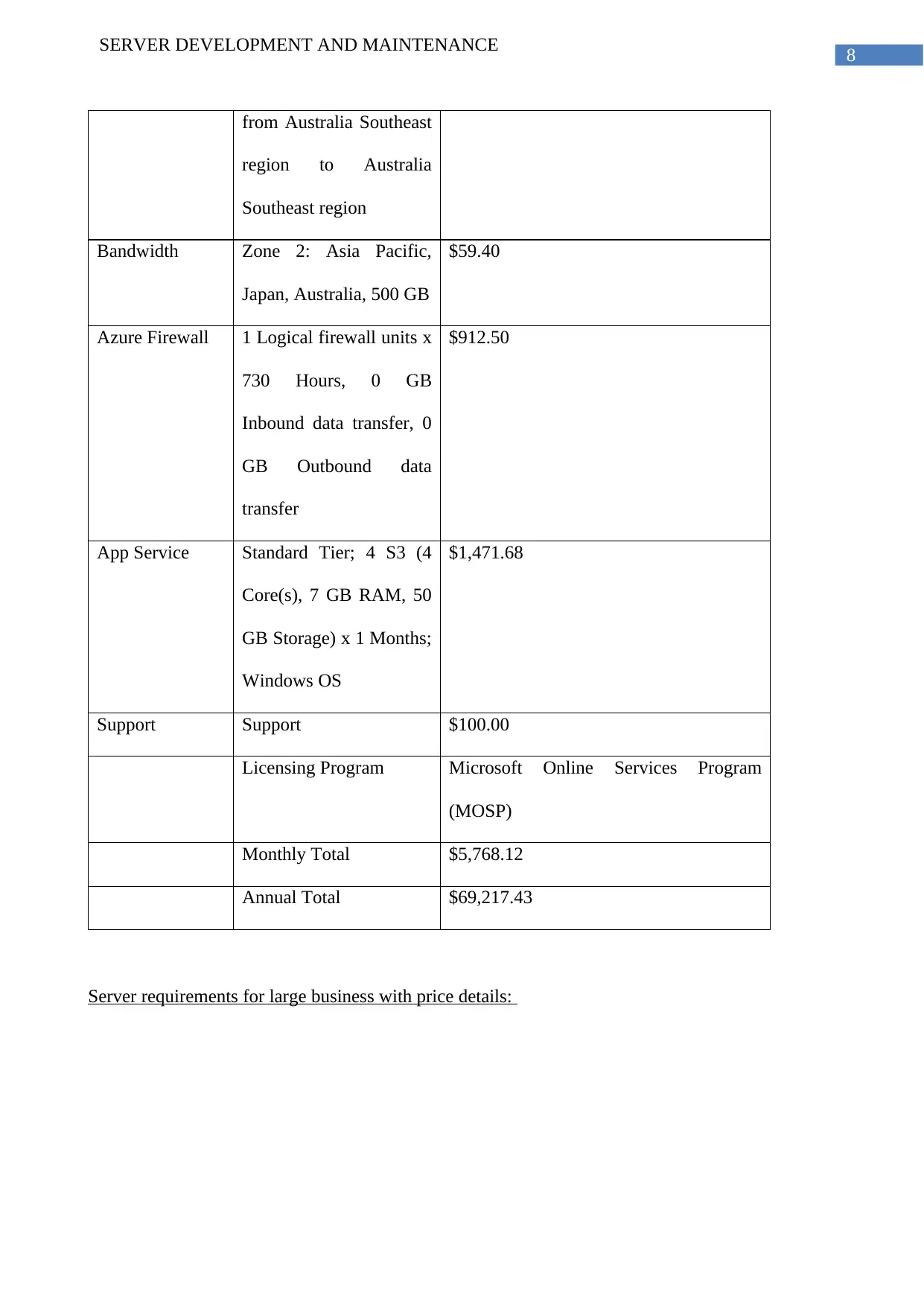
SERVER DEVELOPMENT AND MAINTENANCE
from Australia Southeast
region to Australia
Southeast region
Bandwidth Zone 2: Asia Pacific,
Japan, Australia, 500 GB
$59.40
Azure Firewall 1 Logical firewall units x
730 Hours, 0 GB
Inbound data transfer, 0
GB Outbound data
transfer
$912.50
App Service Standard Tier; 4 S3 (4
Core(s), 7 GB RAM, 50
GB Storage) x 1 Months;
Windows OS
$1,471.68
Support Support $100.00
Licensing Program Microsoft Online Services Program
(MOSP)
Monthly Total $5,768.12
Annual Total $69,217.43
Server requirements for large business with price details:
SERVER DEVELOPMENT AND MAINTENANCE
from Australia Southeast
region to Australia
Southeast region
Bandwidth Zone 2: Asia Pacific,
Japan, Australia, 500 GB
$59.40
Azure Firewall 1 Logical firewall units x
730 Hours, 0 GB
Inbound data transfer, 0
GB Outbound data
transfer
$912.50
App Service Standard Tier; 4 S3 (4
Core(s), 7 GB RAM, 50
GB Storage) x 1 Months;
Windows OS
$1,471.68
Support Support $100.00
Licensing Program Microsoft Online Services Program
(MOSP)
Monthly Total $5,768.12
Annual Total $69,217.43
Server requirements for large business with price details:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
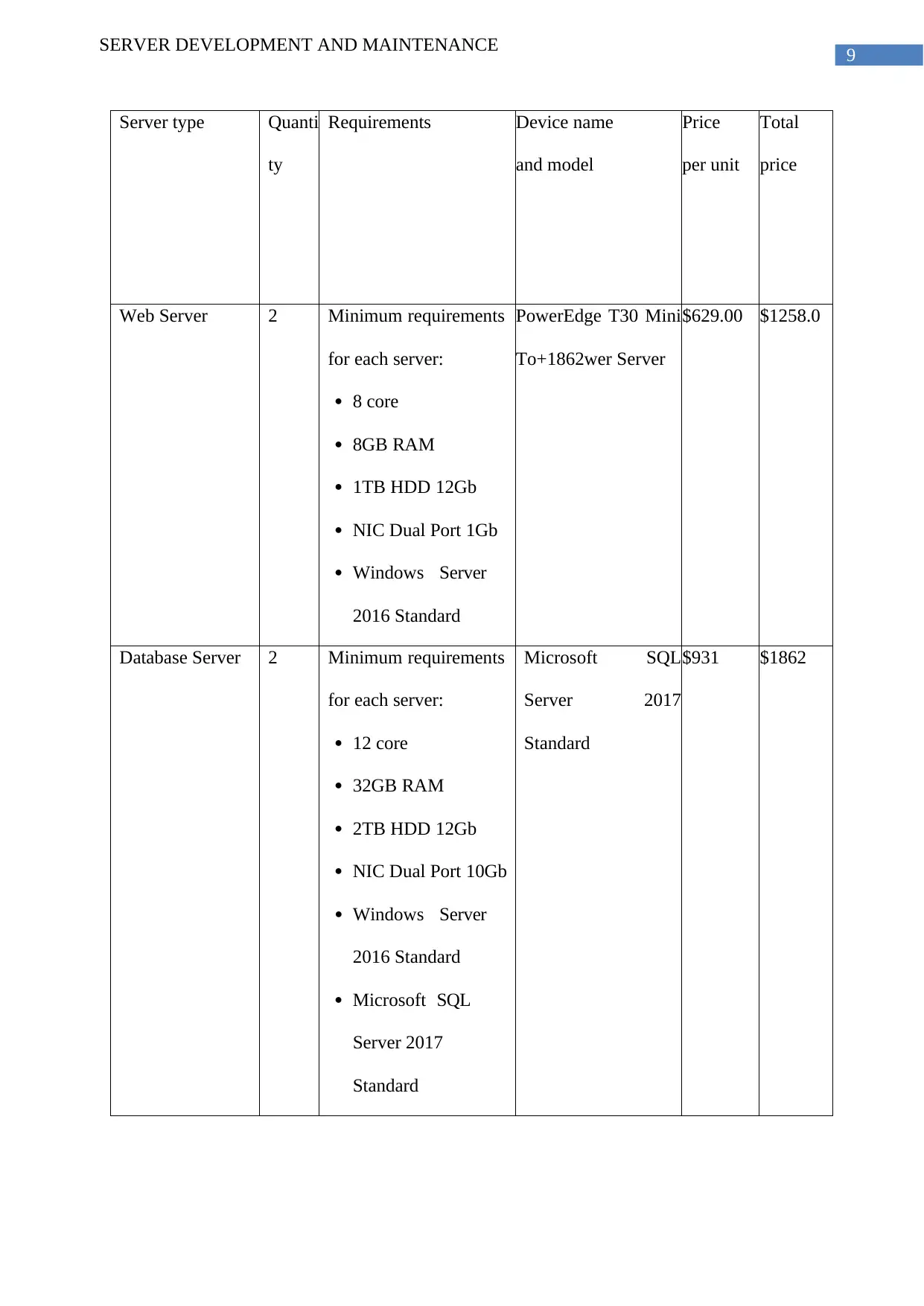
SERVER DEVELOPMENT AND MAINTENANCE
Server type Quanti
ty
Requirements Device name
and model
Price
per unit
Total
price
Web Server 2 Minimum requirements
for each server:
8 core
8GB RAM
1TB HDD 12Gb
NIC Dual Port 1Gb
Windows Server
2016 Standard
PowerEdge T30 Mini
To+1862wer Server
$629.00 $1258.0
Database Server 2 Minimum requirements
for each server:
12 core
32GB RAM
2TB HDD 12Gb
NIC Dual Port 10Gb
Windows Server
2016 Standard
Microsoft SQL
Server 2017
Standard
Microsoft SQL
Server 2017
Standard
$931 $1862
SERVER DEVELOPMENT AND MAINTENANCE
Server type Quanti
ty
Requirements Device name
and model
Price
per unit
Total
price
Web Server 2 Minimum requirements
for each server:
8 core
8GB RAM
1TB HDD 12Gb
NIC Dual Port 1Gb
Windows Server
2016 Standard
PowerEdge T30 Mini
To+1862wer Server
$629.00 $1258.0
Database Server 2 Minimum requirements
for each server:
12 core
32GB RAM
2TB HDD 12Gb
NIC Dual Port 10Gb
Windows Server
2016 Standard
Microsoft SQL
Server 2017
Standard
Microsoft SQL
Server 2017
Standard
$931 $1862
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
SERVER DEVELOPMENT AND MAINTENANCE
Define infrastructure and colocation
A colocation (colo) is a data center facility. It allows business deploy servers with renting through
server space acquired through renting. Along with the server space, business can rent other required
computing hardware if needed.
Azure
Azure is considered in comparison to AWS because:
Wide ranges of services
Low cost
Superior maintenance
Enhanced consumer support
Virtualisation & Abstraction
Virtualization is a process which helps to abstract hardware, software and infrastructure required for
any computing application.
Data Centres
A data center (or datacenter) is a collection of networked computers along with computing storage
that businesses or other organizations considers for storing, processing and retrieving data.
VPN
A VPN, or virtual private network, is a network tunnel that is established between computing
devices device and the internet
Cloud Computing
SAAS: software as a service and in this model client are provided access to cloud applications
SERVER DEVELOPMENT AND MAINTENANCE
Define infrastructure and colocation
A colocation (colo) is a data center facility. It allows business deploy servers with renting through
server space acquired through renting. Along with the server space, business can rent other required
computing hardware if needed.
Azure
Azure is considered in comparison to AWS because:
Wide ranges of services
Low cost
Superior maintenance
Enhanced consumer support
Virtualisation & Abstraction
Virtualization is a process which helps to abstract hardware, software and infrastructure required for
any computing application.
Data Centres
A data center (or datacenter) is a collection of networked computers along with computing storage
that businesses or other organizations considers for storing, processing and retrieving data.
VPN
A VPN, or virtual private network, is a network tunnel that is established between computing
devices device and the internet
Cloud Computing
SAAS: software as a service and in this model client are provided access to cloud applications

11
SERVER DEVELOPMENT AND MAINTENANCE
PAAS: platform as a service and in this cloud model platform support is provided for application
development
IAAS: infrastructure as a service and in this cloud model infrastructure support is provided for
application development
Explore maintenance such as:
-Backup
In the context of information technology a backup is considered as process of smoothing backing
up. This actually refers to copying of some kind of computer data that is currently in a secondary
storage copied to another kind of secondary storage (Jalali et al., 2016).
-Redundancy
The redundancy is considered as critical component duplication of a system, aiming increasing
reliability of the system. Redundancy mainly occurs in form of a backup for improving actual
performance of the system (Chang, Kuo and Ramachandran, 2016).
-Upgrades
The upgrade is considered as the process of replacing some data or products with some newer
version of same kind of data or product. Upgrade mainly consists hardware replacement or changes
in the software firmware for a better and improved performance (Sen, 2015).
-Repair
In the process of maintenance the repair means restoring something faulty and damaged parts.
Repair can lead to upgrading also if a part becomes non-reparable (Etro, 2015).
And how it is affected by virtualisation
SERVER DEVELOPMENT AND MAINTENANCE
PAAS: platform as a service and in this cloud model platform support is provided for application
development
IAAS: infrastructure as a service and in this cloud model infrastructure support is provided for
application development
Explore maintenance such as:
-Backup
In the context of information technology a backup is considered as process of smoothing backing
up. This actually refers to copying of some kind of computer data that is currently in a secondary
storage copied to another kind of secondary storage (Jalali et al., 2016).
-Redundancy
The redundancy is considered as critical component duplication of a system, aiming increasing
reliability of the system. Redundancy mainly occurs in form of a backup for improving actual
performance of the system (Chang, Kuo and Ramachandran, 2016).
-Upgrades
The upgrade is considered as the process of replacing some data or products with some newer
version of same kind of data or product. Upgrade mainly consists hardware replacement or changes
in the software firmware for a better and improved performance (Sen, 2015).
-Repair
In the process of maintenance the repair means restoring something faulty and damaged parts.
Repair can lead to upgrading also if a part becomes non-reparable (Etro, 2015).
And how it is affected by virtualisation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





