SIT202 Computer Networks: Problem Solving Report, Trimester 2, 2019
VerifiedAdded on 2022/11/13
|9
|1519
|182
Report
AI Summary
This report provides solutions to the problem-solving questions from the SIT202 Computer Networks course. The report covers several key concepts including bit rate calculations, multiplexing and demultiplexing techniques, the differences between data rate and capacity, and the principles of circuit-switching and packet-switching. It delves into parity-check codes, including codeword length, number of codewords, and error correction capabilities. Furthermore, the report addresses network encapsulation and frame forwarding, and explores various wireless technologies like Bluetooth and 802.11n. The report concludes with a comparison of different network access methods such as TDMA, Polling, Slotted-ALOHA, and CSMA/CA. The report also includes a bibliography of the sources used.

Running head: SIT202 COMPUTER NETWORKS TRIMESTER 2
SIT202 Computer Networks Trimester 2
Name of the Student
Name of the University
Author’s Note
SIT202 Computer Networks Trimester 2
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SIT202 COMPUTER NETWORKS TRIMESTER 2
Answer to Question 1 (Chapter 3)
1. What is the bit rate?
Bit rate is defined as the number of bits which is passed at a given point in network in a
specific time period in seconds. Bit rate is measured in multiple of bits / second (Batalla et al.,
2016). The bit rate is used for the data transfer rate and used for discussing details of
transmission technology when it is compared with the technology of transmission for the end
users.
2. If the number of signal level is 8 and the bandwidth is 3 MHz, what is the bit rate?
Bit rate is calculated below:
2 * 3 * log2(8) = 3 mbps
3. Suppose that the signal-to-noise ratio (SNR) is 6 dB. What is the capacity (in bits per second)
if the bandwidth is 3 MHz?
The capacity of the channel is calculated using the following formula:
SNRdb = 10log10SNR
SNR = 10SNRdb/10
SNR = 10.6
3.9810
C = B log2 (1+SNR)
= 3*106 * log23.9810
= 3* 106 * 1.993
SIT202 COMPUTER NETWORKS TRIMESTER 2
Answer to Question 1 (Chapter 3)
1. What is the bit rate?
Bit rate is defined as the number of bits which is passed at a given point in network in a
specific time period in seconds. Bit rate is measured in multiple of bits / second (Batalla et al.,
2016). The bit rate is used for the data transfer rate and used for discussing details of
transmission technology when it is compared with the technology of transmission for the end
users.
2. If the number of signal level is 8 and the bandwidth is 3 MHz, what is the bit rate?
Bit rate is calculated below:
2 * 3 * log2(8) = 3 mbps
3. Suppose that the signal-to-noise ratio (SNR) is 6 dB. What is the capacity (in bits per second)
if the bandwidth is 3 MHz?
The capacity of the channel is calculated using the following formula:
SNRdb = 10log10SNR
SNR = 10SNRdb/10
SNR = 10.6
3.9810
C = B log2 (1+SNR)
= 3*106 * log23.9810
= 3* 106 * 1.993

2
SIT202 COMPUTER NETWORKS TRIMESTER 2
= 6 Mbps
4. Discuss the difference between the data rate and the capacity (e.g., answer why they are
different?)
Data rate is defined as the speed of transferring data between the two devices and it is
measured in mbps.
The capacity is defined as the maximum rate in which the data can be transmitted over
the given link of communication or the channel.
Answer to Question 2 (Chapter 6, 7, 8):
1. Explain the purposes of multiplexing and demultiplexing?
Multiplexing – It is the process of transmission of multiple analog or digital input signal over a
single channel. It can also integrate multiple channels of slow speed into a high speed channel
for transmission of the data packets and utilizing it effectively (Bahareva & Tarasov, 2016). The
use of multiplexing avoids the need of maintenance of multiple lines and thus reducing the
operating cost of a network.
Demultiplexing – It is the process of reconverting a signal that contains multiple stream of
analog or digital signal into original unrelated and separated signals. The demultiplexer is used
for receiving the output signal from multiplexer and converting them back into the original form
as sent by the receiver (Ruffato et al., 2017).
2. Place one of “circuit-switching” and “packet-switching” into the followings sentences
• “…” can further be divided into two subcategories – virtual-circuit approach and datagram
approach. - Packet switching
SIT202 COMPUTER NETWORKS TRIMESTER 2
= 6 Mbps
4. Discuss the difference between the data rate and the capacity (e.g., answer why they are
different?)
Data rate is defined as the speed of transferring data between the two devices and it is
measured in mbps.
The capacity is defined as the maximum rate in which the data can be transmitted over
the given link of communication or the channel.
Answer to Question 2 (Chapter 6, 7, 8):
1. Explain the purposes of multiplexing and demultiplexing?
Multiplexing – It is the process of transmission of multiple analog or digital input signal over a
single channel. It can also integrate multiple channels of slow speed into a high speed channel
for transmission of the data packets and utilizing it effectively (Bahareva & Tarasov, 2016). The
use of multiplexing avoids the need of maintenance of multiple lines and thus reducing the
operating cost of a network.
Demultiplexing – It is the process of reconverting a signal that contains multiple stream of
analog or digital signal into original unrelated and separated signals. The demultiplexer is used
for receiving the output signal from multiplexer and converting them back into the original form
as sent by the receiver (Ruffato et al., 2017).
2. Place one of “circuit-switching” and “packet-switching” into the followings sentences
• “…” can further be divided into two subcategories – virtual-circuit approach and datagram
approach. - Packet switching
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
SIT202 COMPUTER NETWORKS TRIMESTER 2
• “…” takes places at the physical layer. – Circuit-switching
• In “…,” the resources need to be reserved during the setup phases. - Circuit-switching
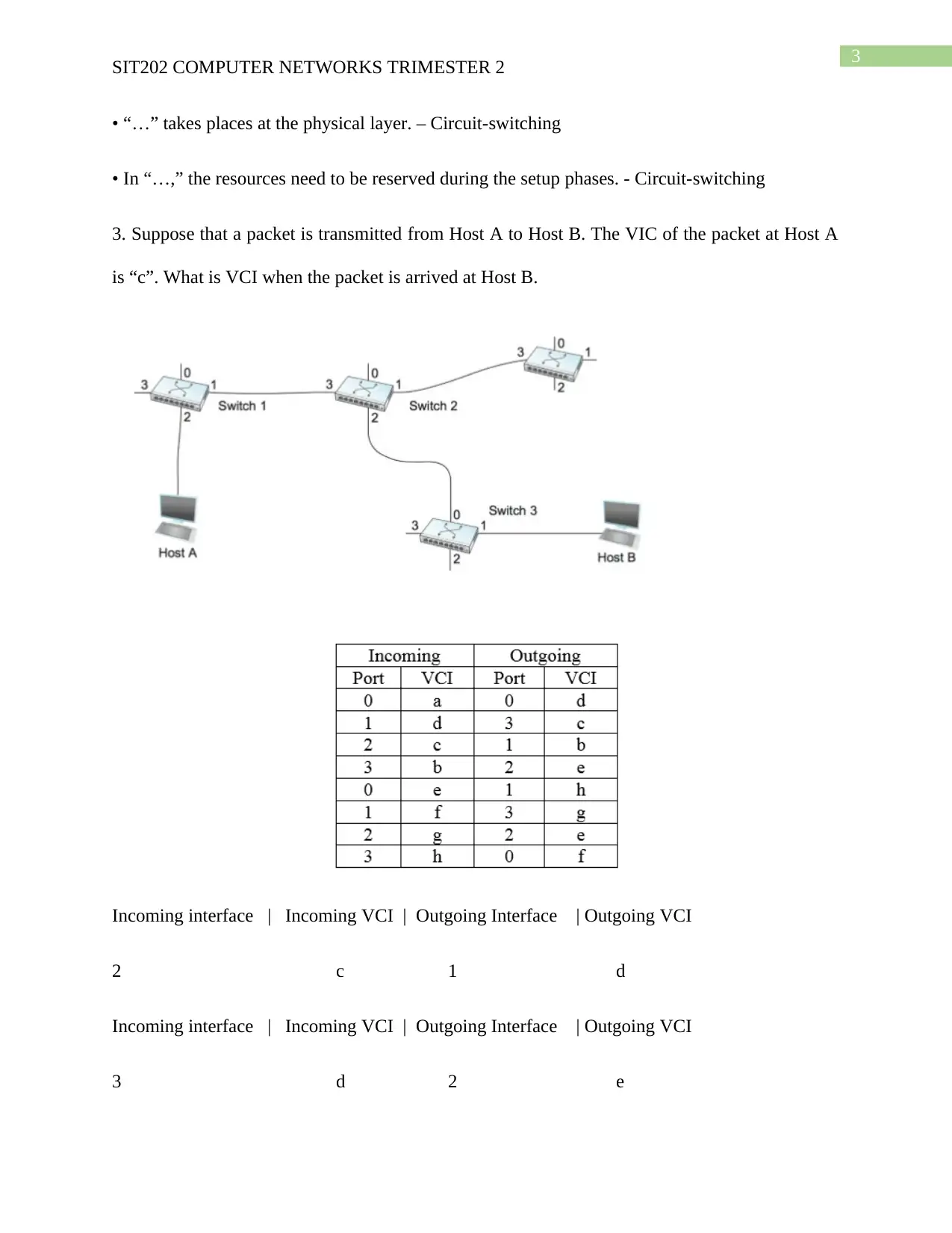
3. Suppose that a packet is transmitted from Host A to Host B. The VIC of the packet at Host A
is “c”. What is VCI when the packet is arrived at Host B.
Incoming interface | Incoming VCI | Outgoing Interface | Outgoing VCI
2 c 1 d
Incoming interface | Incoming VCI | Outgoing Interface | Outgoing VCI
3 d 2 e
SIT202 COMPUTER NETWORKS TRIMESTER 2
• “…” takes places at the physical layer. – Circuit-switching
• In “…,” the resources need to be reserved during the setup phases. - Circuit-switching
3. Suppose that a packet is transmitted from Host A to Host B. The VIC of the packet at Host A
is “c”. What is VCI when the packet is arrived at Host B.
Incoming interface | Incoming VCI | Outgoing Interface | Outgoing VCI
2 c 1 d
Incoming interface | Incoming VCI | Outgoing Interface | Outgoing VCI
3 d 2 e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SIT202 COMPUTER NETWORKS TRIMESTER 2
Incoming interface | Incoming VCI | Outgoing Interface | Outgoing VCI
0 f 1 g
Answer to Question 3 (Chapter 9, 10, 11):
1. Consider the parity-check code with 4-bit dataword
• What is the length of the codeword?
Length of the codeword for the 4 bit data word is 5
• How many codewords the code has?
The code has 2 codewords.
• What is the minimum Hamming distance?
The minimum hamming distance d = 3
• How many errors can be corrected?
Minimum hamming distance d can be used for detecting d-1 errors = d-1
= 2 errors
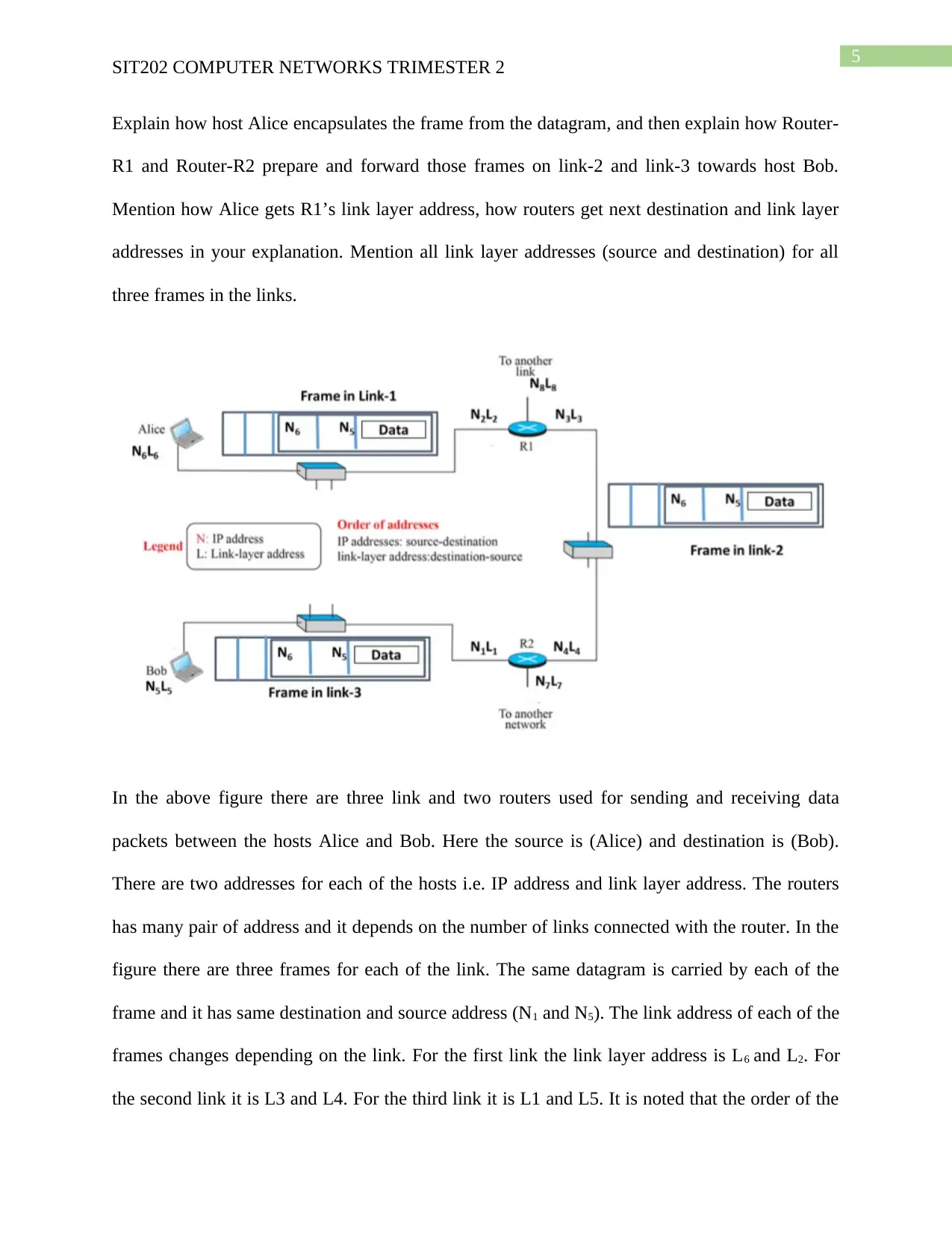
2. In the following network, two hosts Alice and Bob are connected by three links and two
routers. There are two addresses (N: IP address and L: Link layer address) for each interface of
hosts and routers. Host Alice sends a datagram to host Bob. The datagram passes through the
routers and links to host Bob. Before sending, Alice makes a frame from the datagram, then
sends to the router-R1.
SIT202 COMPUTER NETWORKS TRIMESTER 2
Incoming interface | Incoming VCI | Outgoing Interface | Outgoing VCI
0 f 1 g
Answer to Question 3 (Chapter 9, 10, 11):
1. Consider the parity-check code with 4-bit dataword
• What is the length of the codeword?
Length of the codeword for the 4 bit data word is 5
• How many codewords the code has?
The code has 2 codewords.
• What is the minimum Hamming distance?
The minimum hamming distance d = 3
• How many errors can be corrected?
Minimum hamming distance d can be used for detecting d-1 errors = d-1
= 2 errors
2. In the following network, two hosts Alice and Bob are connected by three links and two
routers. There are two addresses (N: IP address and L: Link layer address) for each interface of
hosts and routers. Host Alice sends a datagram to host Bob. The datagram passes through the
routers and links to host Bob. Before sending, Alice makes a frame from the datagram, then
sends to the router-R1.
5
SIT202 COMPUTER NETWORKS TRIMESTER 2
Explain how host Alice encapsulates the frame from the datagram, and then explain how Router-
R1 and Router-R2 prepare and forward those frames on link-2 and link-3 towards host Bob.
Mention how Alice gets R1’s link layer address, how routers get next destination and link layer
addresses in your explanation. Mention all link layer addresses (source and destination) for all
three frames in the links.
In the above figure there are three link and two routers used for sending and receiving data
packets between the hosts Alice and Bob. Here the source is (Alice) and destination is (Bob).
There are two addresses for each of the hosts i.e. IP address and link layer address. The routers
has many pair of address and it depends on the number of links connected with the router. In the
figure there are three frames for each of the link. The same datagram is carried by each of the
frame and it has same destination and source address (N1 and N5). The link address of each of the
frames changes depending on the link. For the first link the link layer address is L6 and L2. For
the second link it is L3 and L4. For the third link it is L1 and L5. It is noted that the order of the
SIT202 COMPUTER NETWORKS TRIMESTER 2
Explain how host Alice encapsulates the frame from the datagram, and then explain how Router-
R1 and Router-R2 prepare and forward those frames on link-2 and link-3 towards host Bob.
Mention how Alice gets R1’s link layer address, how routers get next destination and link layer
addresses in your explanation. Mention all link layer addresses (source and destination) for all
three frames in the links.
In the above figure there are three link and two routers used for sending and receiving data
packets between the hosts Alice and Bob. Here the source is (Alice) and destination is (Bob).
There are two addresses for each of the hosts i.e. IP address and link layer address. The routers
has many pair of address and it depends on the number of links connected with the router. In the
figure there are three frames for each of the link. The same datagram is carried by each of the
frame and it has same destination and source address (N1 and N5). The link address of each of the
frames changes depending on the link. For the first link the link layer address is L6 and L2. For
the second link it is L3 and L4. For the third link it is L1 and L5. It is noted that the order of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
SIT202 COMPUTER NETWORKS TRIMESTER 2
link address and the IP address is different from each other. The source address comes before
destination address in case of the IP address and in case of the link address the destination
address comes before the source address.
Answer to Question 4 (Chapter 12 - 17)
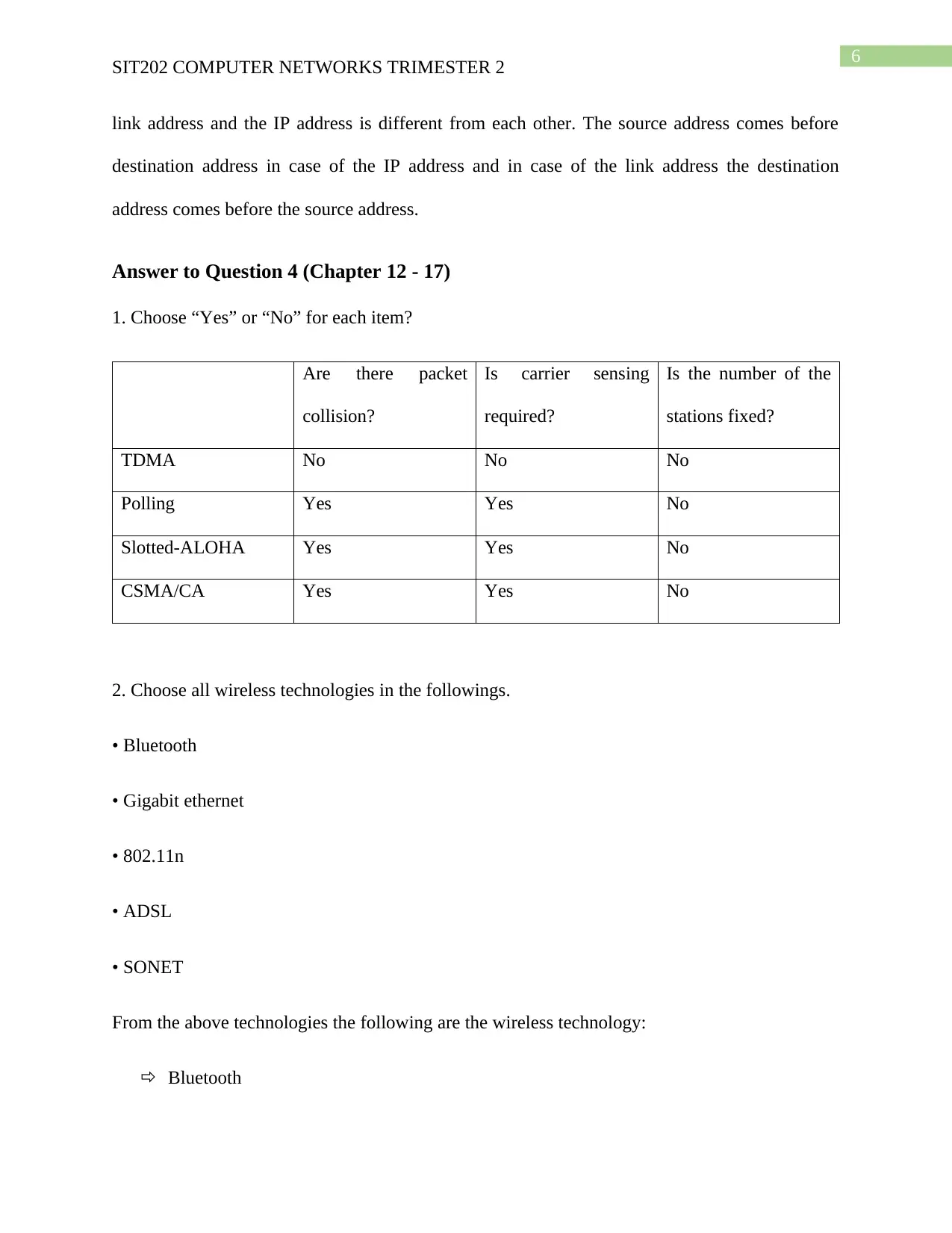
1. Choose “Yes” or “No” for each item?
Are there packet
collision?
Is carrier sensing
required?
Is the number of the
stations fixed?
TDMA No No No
Polling Yes Yes No
Slotted-ALOHA Yes Yes No
CSMA/CA Yes Yes No
2. Choose all wireless technologies in the followings.
• Bluetooth
• Gigabit ethernet
• 802.11n
• ADSL
• SONET
From the above technologies the following are the wireless technology:
Bluetooth
SIT202 COMPUTER NETWORKS TRIMESTER 2
link address and the IP address is different from each other. The source address comes before
destination address in case of the IP address and in case of the link address the destination
address comes before the source address.
Answer to Question 4 (Chapter 12 - 17)
1. Choose “Yes” or “No” for each item?
Are there packet
collision?
Is carrier sensing
required?
Is the number of the
stations fixed?
TDMA No No No
Polling Yes Yes No
Slotted-ALOHA Yes Yes No
CSMA/CA Yes Yes No
2. Choose all wireless technologies in the followings.
• Bluetooth
• Gigabit ethernet
• 802.11n
• ADSL
• SONET
From the above technologies the following are the wireless technology:
Bluetooth
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
SIT202 COMPUTER NETWORKS TRIMESTER 2
802.11n
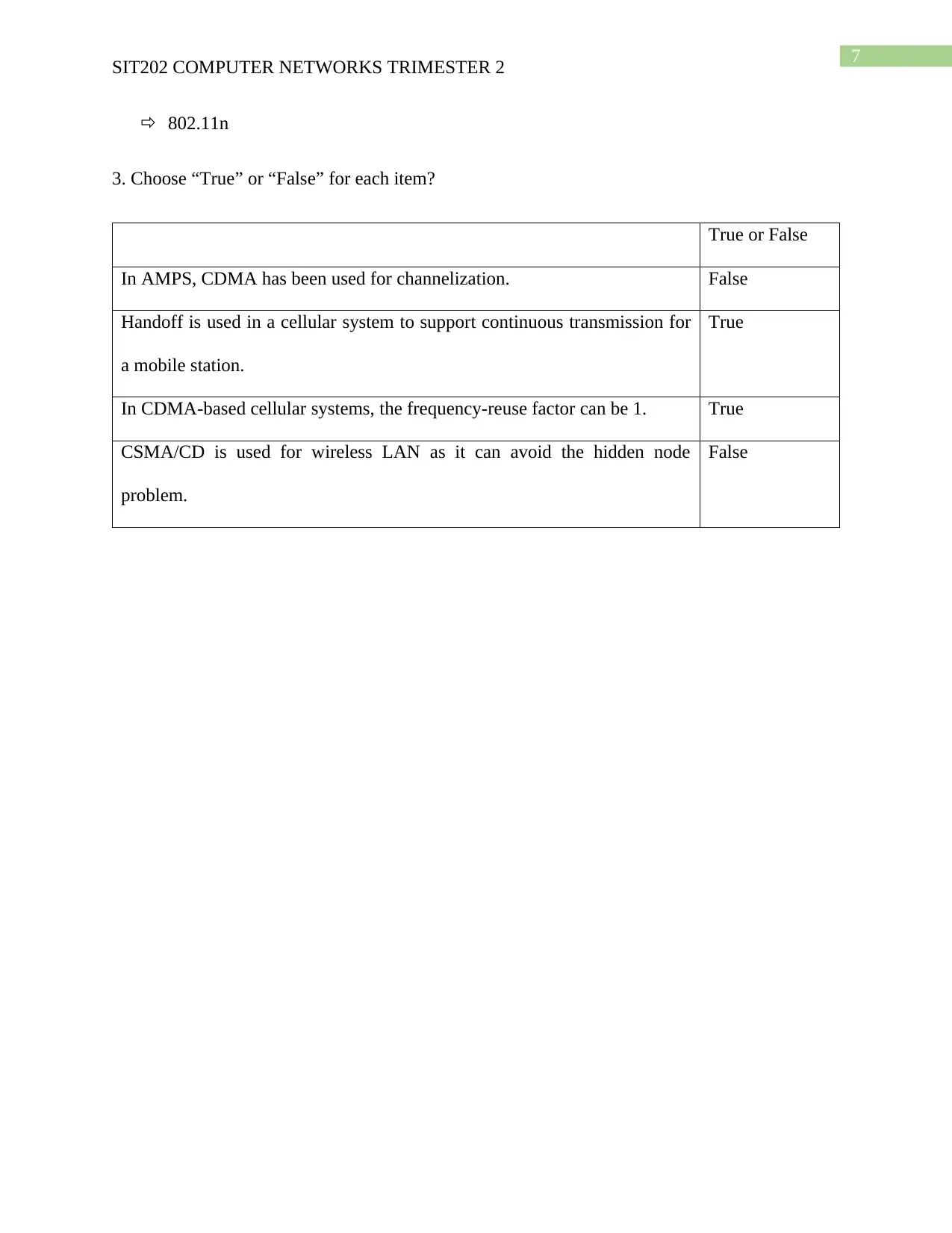
3. Choose “True” or “False” for each item?
True or False
In AMPS, CDMA has been used for channelization. False
Handoff is used in a cellular system to support continuous transmission for
a mobile station.
True
In CDMA-based cellular systems, the frequency-reuse factor can be 1. True
CSMA/CD is used for wireless LAN as it can avoid the hidden node
problem.
False
SIT202 COMPUTER NETWORKS TRIMESTER 2
802.11n
3. Choose “True” or “False” for each item?
True or False
In AMPS, CDMA has been used for channelization. False
Handoff is used in a cellular system to support continuous transmission for
a mobile station.
True
In CDMA-based cellular systems, the frequency-reuse factor can be 1. True
CSMA/CD is used for wireless LAN as it can avoid the hidden node
problem.
False

8
SIT202 COMPUTER NETWORKS TRIMESTER 2
Bibliography
Alabady, S. A., & Al-Turjman, F. (2018). Low complexity parity check code for futuristic
wireless networks applications. IEEE Access, 6, 18398-18407.
Bahareva, N. F., & Tarasov, V. N. (2016, March). Mathematical multiplexing and
demultiplexing of flows in optical links. In Optical Technologies for
Telecommunications 2015 (Vol. 9807, p. 980703). International Society for Optics and
Photonics.
Batalla, J. M., Krawiec, P., Beben, A., Wisniewski, P., & Chydzinski, A. (2016). Adaptive video
streaming: Rate and buffer on the track of minimum rebuffering. IEEE Journal on
Selected Areas in Communications, 34(8), 2154-2167.
Bi, R., & Liu, P. (2016). Sample size calculation while controlling false discovery rate for
differential expression analysis with RNA-sequencing experiments. BMC
bioinformatics, 17(1), 146.
Ruffato, G., Massari, M., Parisi, G., & Romanato, F. (2017). Test of mode-division multiplexing
and demultiplexing in free-space with diffractive transformation optics. Optics
express, 25(7), 7859-7868.
Saridis, G. M., Peng, S., Yan, Y., Aguado, A., Guo, B., Arslan, M., ... & Spadaro, S. (2016).
Lightness: A function-virtualizable software defined data center network with all-optical
circuit/packet switching. Journal of Lightwave Technology, 34(7), 1618-1627.
SIT202 COMPUTER NETWORKS TRIMESTER 2
Bibliography
Alabady, S. A., & Al-Turjman, F. (2018). Low complexity parity check code for futuristic
wireless networks applications. IEEE Access, 6, 18398-18407.
Bahareva, N. F., & Tarasov, V. N. (2016, March). Mathematical multiplexing and
demultiplexing of flows in optical links. In Optical Technologies for
Telecommunications 2015 (Vol. 9807, p. 980703). International Society for Optics and
Photonics.
Batalla, J. M., Krawiec, P., Beben, A., Wisniewski, P., & Chydzinski, A. (2016). Adaptive video
streaming: Rate and buffer on the track of minimum rebuffering. IEEE Journal on
Selected Areas in Communications, 34(8), 2154-2167.
Bi, R., & Liu, P. (2016). Sample size calculation while controlling false discovery rate for
differential expression analysis with RNA-sequencing experiments. BMC
bioinformatics, 17(1), 146.
Ruffato, G., Massari, M., Parisi, G., & Romanato, F. (2017). Test of mode-division multiplexing
and demultiplexing in free-space with diffractive transformation optics. Optics
express, 25(7), 7859-7868.
Saridis, G. M., Peng, S., Yan, Y., Aguado, A., Guo, B., Arslan, M., ... & Spadaro, S. (2016).
Lightness: A function-virtualizable software defined data center network with all-optical
circuit/packet switching. Journal of Lightwave Technology, 34(7), 1618-1627.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




