Small Office Upgrade
VerifiedAdded on 2022/11/29
|14
|3449
|312
AI Summary
This report discusses the small office upgrade assessment for Heaps of Books, including stakeholder questionnaires, current problems, future issues, system requirements, network design, installation plans, and security measures.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Small Office Upgrade
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.


Table of Contents

INTRODUCTION...........................................................................................................................1
Create questionnaires for key stakeholders to find out expectations...............................................2
Create an Upgrade Proposal for the Client......................................................................................2
Current problems that the client is experiencing....................................................................2
Future possible issues the client may have.............................................................................3
Identify new system requirements and specifications for quote............................................3
Create a GAP report...............................................................................................................3
Network design.......................................................................................................................4
Creating quotes for low cost, medium cost and high cost...............................................................4
Hardware................................................................................................................................4
Software..................................................................................................................................5
Procurement timeline..............................................................................................................5
Cabling requirements..............................................................................................................6
Create an expected timeline.............................................................................................................6
Create a staged 3-year plan to address the expected growth of Heaps of Books.............................7
Create installation plans that cover pre – actual – post....................................................................7
Automation of software installation.......................................................................................7
Testing plan to test the installed system.................................................................................8
Security plan that lists types of threats and how you will protect the system........................8
Create a post installation review questionnaire...............................................................................8
Create a grievance process for the client to report any issues.........................................................9
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10
Create questionnaires for key stakeholders to find out expectations...............................................2
Create an Upgrade Proposal for the Client......................................................................................2
Current problems that the client is experiencing....................................................................2
Future possible issues the client may have.............................................................................3
Identify new system requirements and specifications for quote............................................3
Create a GAP report...............................................................................................................3
Network design.......................................................................................................................4
Creating quotes for low cost, medium cost and high cost...............................................................4
Hardware................................................................................................................................4
Software..................................................................................................................................5
Procurement timeline..............................................................................................................5
Cabling requirements..............................................................................................................6
Create an expected timeline.............................................................................................................6
Create a staged 3-year plan to address the expected growth of Heaps of Books.............................7
Create installation plans that cover pre – actual – post....................................................................7
Automation of software installation.......................................................................................7
Testing plan to test the installed system.................................................................................8
Security plan that lists types of threats and how you will protect the system........................8
Create a post installation review questionnaire...............................................................................8
Create a grievance process for the client to report any issues.........................................................9
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTRODUCTION
Information systems can be defined as the organisational system which is designed formally
in order to gather and process the data so that it can be retrieved and used for business
operations. There are mainly five components of an information system such as computer
hardware and computer software along with the telecommunications and data bases and human
resources (Abdullayev, 2020). This report is all about the given scenario which states the small
office upgrade assessment on the company heaps of books. they want to upgrade and install their
information and data system with the security and configuration. Previously they were doing
management manually but now they want advancement in technology so that the less human
efforts can be consumed in an organisation. Therefore the following discussion is based on the
question as for stakeholders to find out expectations, finding about current problems that the
client is experiencing, future possible issues the client may have, identification of the new system
requirements and specifications for quotations, creating the GAP report, network design,
hardware and software requirements, procurement timeline, cabling requirements, creating an
expected timeline, creating 3 year plan to address the expected growth of the company,
automation of software installation, testing plan to test the installed system, security plan that list
types of threats and how will it protect the system, creating a post installation review
questionnaire and creating a grievance process for the clients to report any issues with proper
findings and conclusion.
1
Information systems can be defined as the organisational system which is designed formally
in order to gather and process the data so that it can be retrieved and used for business
operations. There are mainly five components of an information system such as computer
hardware and computer software along with the telecommunications and data bases and human
resources (Abdullayev, 2020). This report is all about the given scenario which states the small
office upgrade assessment on the company heaps of books. they want to upgrade and install their
information and data system with the security and configuration. Previously they were doing
management manually but now they want advancement in technology so that the less human
efforts can be consumed in an organisation. Therefore the following discussion is based on the
question as for stakeholders to find out expectations, finding about current problems that the
client is experiencing, future possible issues the client may have, identification of the new system
requirements and specifications for quotations, creating the GAP report, network design,
hardware and software requirements, procurement timeline, cabling requirements, creating an
expected timeline, creating 3 year plan to address the expected growth of the company,
automation of software installation, testing plan to test the installed system, security plan that list
types of threats and how will it protect the system, creating a post installation review
questionnaire and creating a grievance process for the clients to report any issues with proper
findings and conclusion.
1

Create questionnaires for key stakeholders to find out expectations
Questionnaire
1. What type of inventory system is more preferable for the company?
a. Logistics management
b. Automatically notify them when stock is low
2. What type of ordering system is more preferable for the company?
a. Automate the order of books
b. Transaction system
3. What type of sales system is more preferable for the company?
a. Tracking system
b. Sales dockets
4. What type of financial system is more preferable for the company?
a. Recording of profit loss statement, salaries, tax and GST
b. Financial decision making
5. What type of database system is more preferable for the company?
a. Data analytics
b. Identification of books being specifically ordered or held for customers
Create an Upgrade Proposal for the Client
Current problems that the client is experiencing
Current problems that the client is experiencing is that they are reluctant to upgrade the
manual system which they were working, initially the proprietor was not realising that manual
system is increasing the human efforts and time consuming process along with the expensive one
but now proprietor has started to realise that he is required to do something to stay competitive in
the market place. Moreover, they were facing the problem of database management and financial
management along with the inventory management so all these systems are needed to be
upgraded with an advanced technology of information systems (Johansson, Malmsköld, Fast-
Berglund and Moestam, 2018).
2
Questionnaire
1. What type of inventory system is more preferable for the company?
a. Logistics management
b. Automatically notify them when stock is low
2. What type of ordering system is more preferable for the company?
a. Automate the order of books
b. Transaction system
3. What type of sales system is more preferable for the company?
a. Tracking system
b. Sales dockets
4. What type of financial system is more preferable for the company?
a. Recording of profit loss statement, salaries, tax and GST
b. Financial decision making
5. What type of database system is more preferable for the company?
a. Data analytics
b. Identification of books being specifically ordered or held for customers
Create an Upgrade Proposal for the Client
Current problems that the client is experiencing
Current problems that the client is experiencing is that they are reluctant to upgrade the
manual system which they were working, initially the proprietor was not realising that manual
system is increasing the human efforts and time consuming process along with the expensive one
but now proprietor has started to realise that he is required to do something to stay competitive in
the market place. Moreover, they were facing the problem of database management and financial
management along with the inventory management so all these systems are needed to be
upgraded with an advanced technology of information systems (Johansson, Malmsköld, Fast-
Berglund and Moestam, 2018).
2

Future possible issues the client may have
Suppose the client has upgraded their system of finance and inventory along with the
database management system but the resolving of the problems is not ended here. That can be
the future possible issues with the client has to face while operating the information systems such
as the privacy and security and an expertise in order to handle the technical equipment. All such
requirements can prove expensive but it is need to be resolved so that an effective and efficient
information system can be implemented in the company (Gronwald, 2020).
Identify new system requirements and specifications for quote
New information system which are required to get upgraded in the company have some
requirements and specifications such as the company highly means the financial management
system and inventory management system along with the ordering system and sales system with
the highly requirement of database management system. It consists several hardware and
software requirements along with the internet and networking with the cabling requirements
which has the specific quotations. So therefore as per the needs and requirements of the company
these are the requirements which must be implemented and installed with the information system
(Kang, Lee and Chan, 2019).
Create a GAP report
Current system of the client specifies that they have four personal computers with
Windows XP operating system connected with the help of coaxial network with a modem and
HP desk jet that prints A4 receipts from a spreadsheet. Moreover, they have Microsoft Excel
2003 e workbook which contains the spreadsheet for customers and books along with the
suppliers and books on hold. Climb is highly requiring the system which is updated and have
advanced features to perform same functions but in a both strategic and effective manner and
efficiently as well. all such functions the client is doing manually but with the implementation of
information system it will all automatic for the client and the business operations will be easy.
Technical equipment which can be reused are the personal computers and the spreadsheets along
with the data and filtration. there are a lot of things which are required to get purchased in order
to implement the information system which is discussed for the in task 3 (Granderson, Piette,
Ghatikar and Price, 2020).
3
Suppose the client has upgraded their system of finance and inventory along with the
database management system but the resolving of the problems is not ended here. That can be
the future possible issues with the client has to face while operating the information systems such
as the privacy and security and an expertise in order to handle the technical equipment. All such
requirements can prove expensive but it is need to be resolved so that an effective and efficient
information system can be implemented in the company (Gronwald, 2020).
Identify new system requirements and specifications for quote
New information system which are required to get upgraded in the company have some
requirements and specifications such as the company highly means the financial management
system and inventory management system along with the ordering system and sales system with
the highly requirement of database management system. It consists several hardware and
software requirements along with the internet and networking with the cabling requirements
which has the specific quotations. So therefore as per the needs and requirements of the company
these are the requirements which must be implemented and installed with the information system
(Kang, Lee and Chan, 2019).
Create a GAP report
Current system of the client specifies that they have four personal computers with
Windows XP operating system connected with the help of coaxial network with a modem and
HP desk jet that prints A4 receipts from a spreadsheet. Moreover, they have Microsoft Excel
2003 e workbook which contains the spreadsheet for customers and books along with the
suppliers and books on hold. Climb is highly requiring the system which is updated and have
advanced features to perform same functions but in a both strategic and effective manner and
efficiently as well. all such functions the client is doing manually but with the implementation of
information system it will all automatic for the client and the business operations will be easy.
Technical equipment which can be reused are the personal computers and the spreadsheets along
with the data and filtration. there are a lot of things which are required to get purchased in order
to implement the information system which is discussed for the in task 3 (Granderson, Piette,
Ghatikar and Price, 2020).
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network design
As per the given scenario and the needs and requirements of the company the network
design is develop such as it includes be components of internet, modem, router, firewall, secure
wireless access point, server, switch, four workstations and printer. All these are connected
according to the working and operations of the company and workstation contains the necessary
information systems which are implemented and installed for the company which contains the
essential financial and inventory management around with the database management systems in
order to resolve the issues which the company was facing bi manual working in the heaps of
books (Rajaraman, 2018).
Creating quotes for low cost, medium cost and high cost
Hardware
Hardware devices Low cost Medium cost High cost
4
As per the given scenario and the needs and requirements of the company the network
design is develop such as it includes be components of internet, modem, router, firewall, secure
wireless access point, server, switch, four workstations and printer. All these are connected
according to the working and operations of the company and workstation contains the necessary
information systems which are implemented and installed for the company which contains the
essential financial and inventory management around with the database management systems in
order to resolve the issues which the company was facing bi manual working in the heaps of
books (Rajaraman, 2018).
Creating quotes for low cost, medium cost and high cost
Hardware
Hardware devices Low cost Medium cost High cost
4
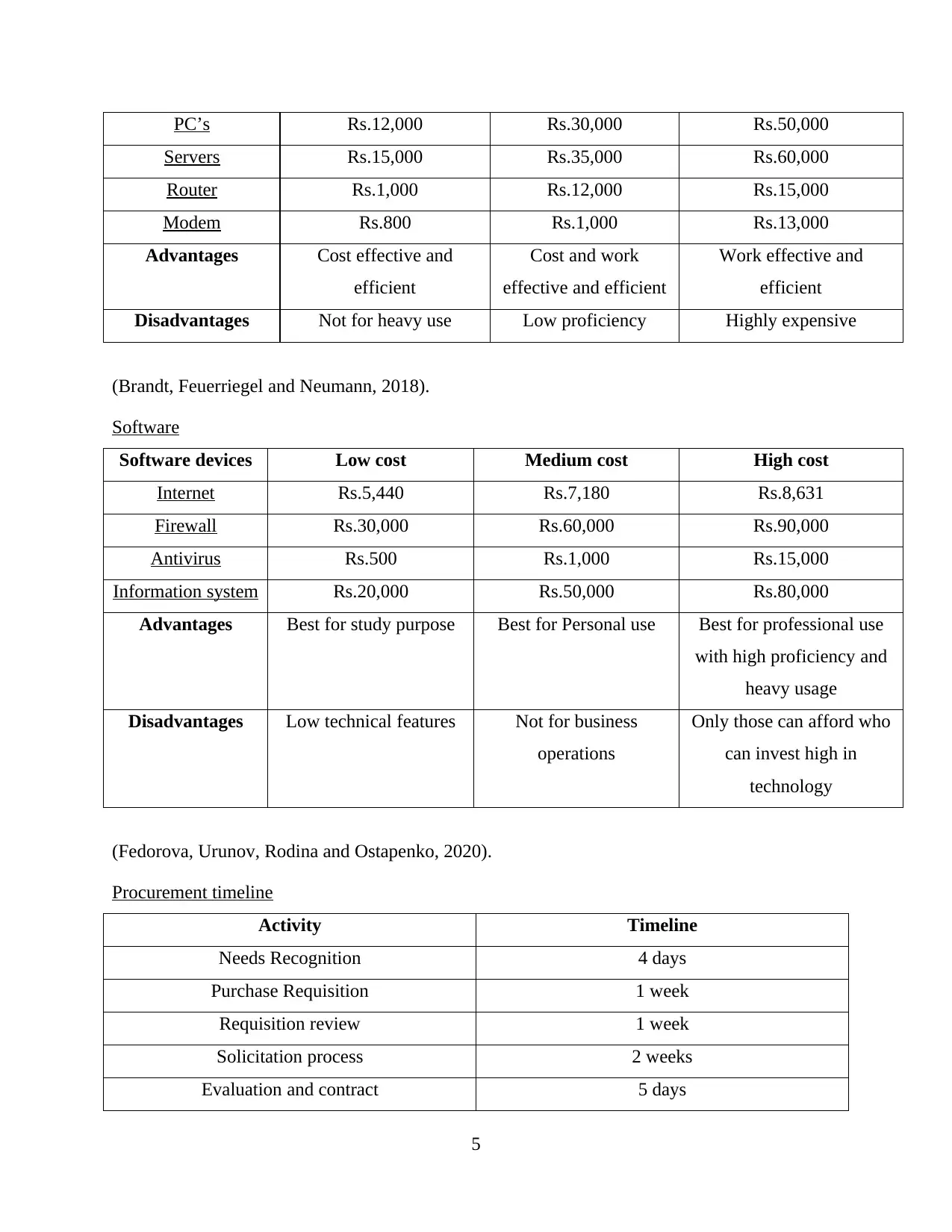
PC’s Rs.12,000 Rs.30,000 Rs.50,000
Servers Rs.15,000 Rs.35,000 Rs.60,000
Router Rs.1,000 Rs.12,000 Rs.15,000
Modem Rs.800 Rs.1,000 Rs.13,000
Advantages Cost effective and
efficient
Cost and work
effective and efficient
Work effective and
efficient
Disadvantages Not for heavy use Low proficiency Highly expensive
(Brandt, Feuerriegel and Neumann, 2018).
Software
Software devices Low cost Medium cost High cost
Internet Rs.5,440 Rs.7,180 Rs.8,631
Firewall Rs.30,000 Rs.60,000 Rs.90,000
Antivirus Rs.500 Rs.1,000 Rs.15,000
Information system Rs.20,000 Rs.50,000 Rs.80,000
Advantages Best for study purpose Best for Personal use Best for professional use
with high proficiency and
heavy usage
Disadvantages Low technical features Not for business
operations
Only those can afford who
can invest high in
technology
(Fedorova, Urunov, Rodina and Ostapenko, 2020).
Procurement timeline
Activity Timeline
Needs Recognition 4 days
Purchase Requisition 1 week
Requisition review 1 week
Solicitation process 2 weeks
Evaluation and contract 5 days
5
Servers Rs.15,000 Rs.35,000 Rs.60,000
Router Rs.1,000 Rs.12,000 Rs.15,000
Modem Rs.800 Rs.1,000 Rs.13,000
Advantages Cost effective and
efficient
Cost and work
effective and efficient
Work effective and
efficient
Disadvantages Not for heavy use Low proficiency Highly expensive
(Brandt, Feuerriegel and Neumann, 2018).
Software
Software devices Low cost Medium cost High cost
Internet Rs.5,440 Rs.7,180 Rs.8,631
Firewall Rs.30,000 Rs.60,000 Rs.90,000
Antivirus Rs.500 Rs.1,000 Rs.15,000
Information system Rs.20,000 Rs.50,000 Rs.80,000
Advantages Best for study purpose Best for Personal use Best for professional use
with high proficiency and
heavy usage
Disadvantages Low technical features Not for business
operations
Only those can afford who
can invest high in
technology
(Fedorova, Urunov, Rodina and Ostapenko, 2020).
Procurement timeline
Activity Timeline
Needs Recognition 4 days
Purchase Requisition 1 week
Requisition review 1 week
Solicitation process 2 weeks
Evaluation and contract 5 days
5
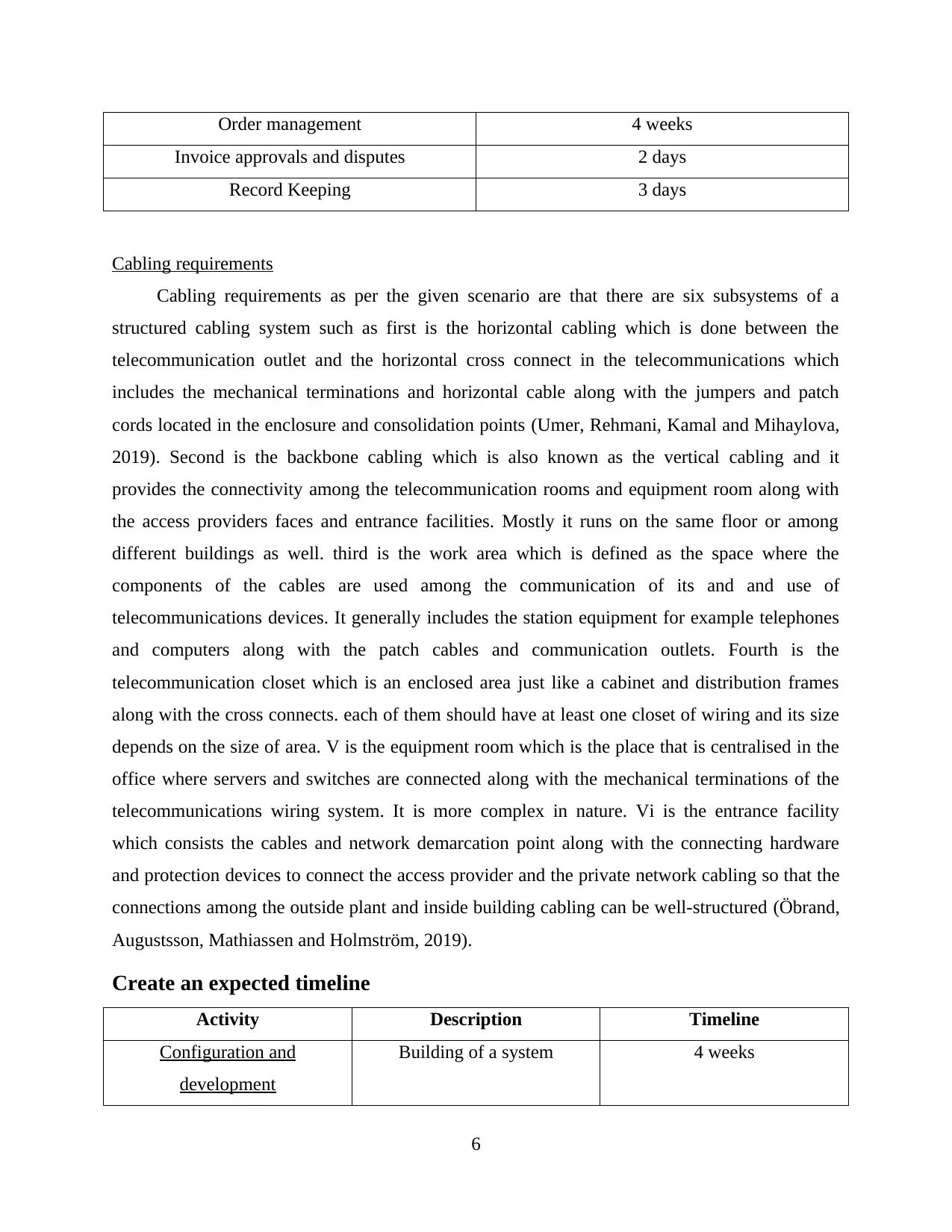
Order management 4 weeks
Invoice approvals and disputes 2 days
Record Keeping 3 days
Cabling requirements
Cabling requirements as per the given scenario are that there are six subsystems of a
structured cabling system such as first is the horizontal cabling which is done between the
telecommunication outlet and the horizontal cross connect in the telecommunications which
includes the mechanical terminations and horizontal cable along with the jumpers and patch
cords located in the enclosure and consolidation points (Umer, Rehmani, Kamal and Mihaylova,
2019). Second is the backbone cabling which is also known as the vertical cabling and it
provides the connectivity among the telecommunication rooms and equipment room along with
the access providers faces and entrance facilities. Mostly it runs on the same floor or among
different buildings as well. third is the work area which is defined as the space where the
components of the cables are used among the communication of its and and use of
telecommunications devices. It generally includes the station equipment for example telephones
and computers along with the patch cables and communication outlets. Fourth is the
telecommunication closet which is an enclosed area just like a cabinet and distribution frames
along with the cross connects. each of them should have at least one closet of wiring and its size
depends on the size of area. V is the equipment room which is the place that is centralised in the
office where servers and switches are connected along with the mechanical terminations of the
telecommunications wiring system. It is more complex in nature. Vi is the entrance facility
which consists the cables and network demarcation point along with the connecting hardware
and protection devices to connect the access provider and the private network cabling so that the
connections among the outside plant and inside building cabling can be well-structured (Öbrand,
Augustsson, Mathiassen and Holmström, 2019).
Create an expected timeline
Activity Description Timeline
Configuration and
development
Building of a system 4 weeks
6
Invoice approvals and disputes 2 days
Record Keeping 3 days
Cabling requirements
Cabling requirements as per the given scenario are that there are six subsystems of a
structured cabling system such as first is the horizontal cabling which is done between the
telecommunication outlet and the horizontal cross connect in the telecommunications which
includes the mechanical terminations and horizontal cable along with the jumpers and patch
cords located in the enclosure and consolidation points (Umer, Rehmani, Kamal and Mihaylova,
2019). Second is the backbone cabling which is also known as the vertical cabling and it
provides the connectivity among the telecommunication rooms and equipment room along with
the access providers faces and entrance facilities. Mostly it runs on the same floor or among
different buildings as well. third is the work area which is defined as the space where the
components of the cables are used among the communication of its and and use of
telecommunications devices. It generally includes the station equipment for example telephones
and computers along with the patch cables and communication outlets. Fourth is the
telecommunication closet which is an enclosed area just like a cabinet and distribution frames
along with the cross connects. each of them should have at least one closet of wiring and its size
depends on the size of area. V is the equipment room which is the place that is centralised in the
office where servers and switches are connected along with the mechanical terminations of the
telecommunications wiring system. It is more complex in nature. Vi is the entrance facility
which consists the cables and network demarcation point along with the connecting hardware
and protection devices to connect the access provider and the private network cabling so that the
connections among the outside plant and inside building cabling can be well-structured (Öbrand,
Augustsson, Mathiassen and Holmström, 2019).
Create an expected timeline
Activity Description Timeline
Configuration and
development
Building of a system 4 weeks
6
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
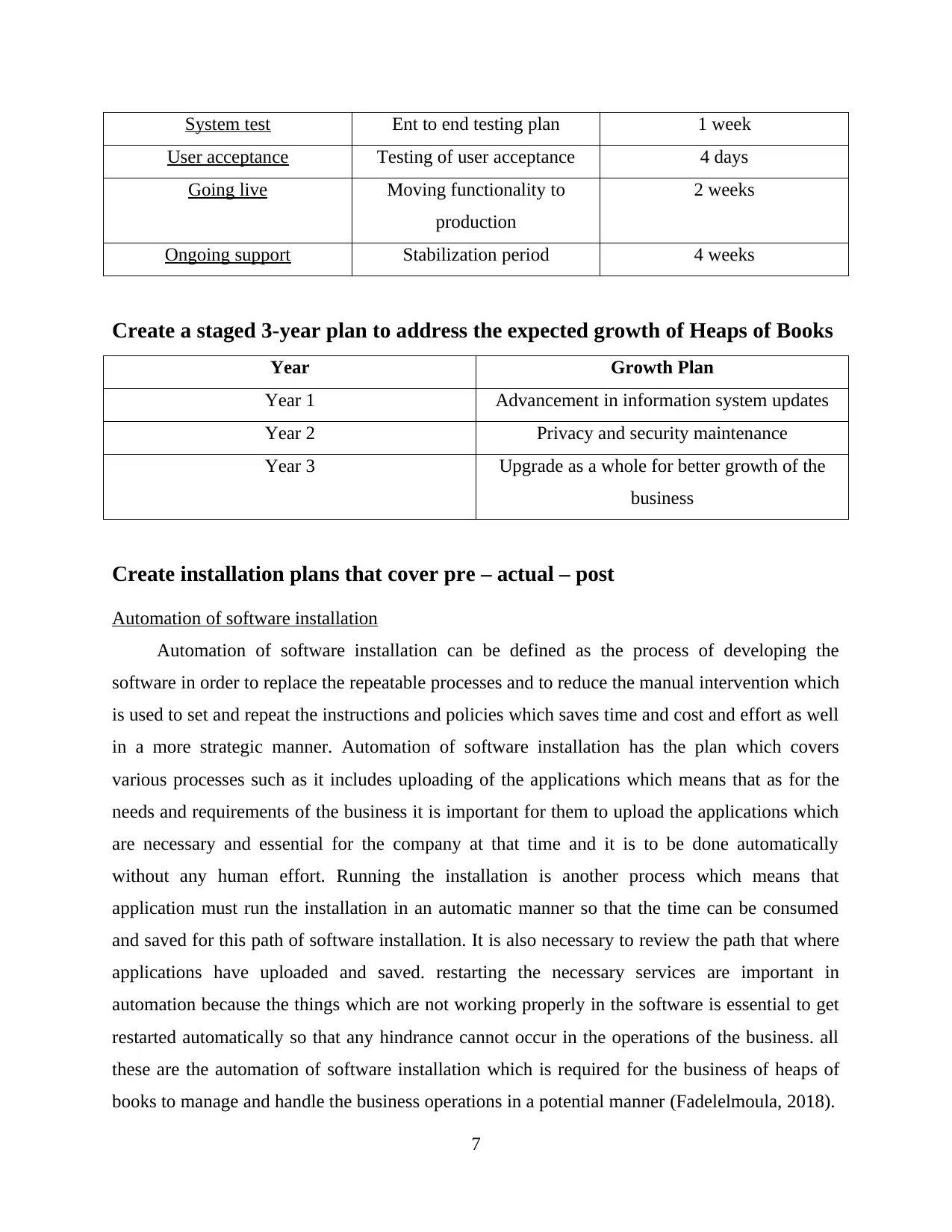
System test Ent to end testing plan 1 week
User acceptance Testing of user acceptance 4 days
Going live Moving functionality to
production
2 weeks
Ongoing support Stabilization period 4 weeks
Create a staged 3-year plan to address the expected growth of Heaps of Books
Year Growth Plan
Year 1 Advancement in information system updates
Year 2 Privacy and security maintenance
Year 3 Upgrade as a whole for better growth of the
business
Create installation plans that cover pre – actual – post
Automation of software installation
Automation of software installation can be defined as the process of developing the
software in order to replace the repeatable processes and to reduce the manual intervention which
is used to set and repeat the instructions and policies which saves time and cost and effort as well
in a more strategic manner. Automation of software installation has the plan which covers
various processes such as it includes uploading of the applications which means that as for the
needs and requirements of the business it is important for them to upload the applications which
are necessary and essential for the company at that time and it is to be done automatically
without any human effort. Running the installation is another process which means that
application must run the installation in an automatic manner so that the time can be consumed
and saved for this path of software installation. It is also necessary to review the path that where
applications have uploaded and saved. restarting the necessary services are important in
automation because the things which are not working properly in the software is essential to get
restarted automatically so that any hindrance cannot occur in the operations of the business. all
these are the automation of software installation which is required for the business of heaps of
books to manage and handle the business operations in a potential manner (Fadelelmoula, 2018).
7
User acceptance Testing of user acceptance 4 days
Going live Moving functionality to
production
2 weeks
Ongoing support Stabilization period 4 weeks
Create a staged 3-year plan to address the expected growth of Heaps of Books
Year Growth Plan
Year 1 Advancement in information system updates
Year 2 Privacy and security maintenance
Year 3 Upgrade as a whole for better growth of the
business
Create installation plans that cover pre – actual – post
Automation of software installation
Automation of software installation can be defined as the process of developing the
software in order to replace the repeatable processes and to reduce the manual intervention which
is used to set and repeat the instructions and policies which saves time and cost and effort as well
in a more strategic manner. Automation of software installation has the plan which covers
various processes such as it includes uploading of the applications which means that as for the
needs and requirements of the business it is important for them to upload the applications which
are necessary and essential for the company at that time and it is to be done automatically
without any human effort. Running the installation is another process which means that
application must run the installation in an automatic manner so that the time can be consumed
and saved for this path of software installation. It is also necessary to review the path that where
applications have uploaded and saved. restarting the necessary services are important in
automation because the things which are not working properly in the software is essential to get
restarted automatically so that any hindrance cannot occur in the operations of the business. all
these are the automation of software installation which is required for the business of heaps of
books to manage and handle the business operations in a potential manner (Fadelelmoula, 2018).
7

Testing plan to test the installed system
The testing plan of the information system which is installed for the business is that the
first step is to create the test plan which means that planning of the testing is done that which part
and which feature is the essential one which are necessary to get tested first and then the other
ones. Second is to create the system test cases and test scripts which means that cases are
developed in order to generate the scripts so that the testing could be done in a systematic
manner. Third is to prepare the test data as per the requirements of the testing because any data
cannot be used to test, it is important for the tester to plan the data which can be accurate for the
testing plan and can help in in identifying and detection of the bugs and errors. Fourth is to
execution of the system test cases and script. V is to report the bugs and we test the bugs once
fixed which means that after the detection of the bugs and errors it is important to rectify the
bugs for the next level of testing. it is important to perform the regression testing in order to
verify the impact of the change in the cold. This testing cycle must be repeated until the system
is ready to be deployed and then the last is the sign off from the testing team (Nwokeji, Stachel,
Holmes and Orji, 2019).
Security plan that lists types of threats and how you will protect the system
There are different types of threats which can affect the information system in a negative
manner such as malware, phishing, man in the middle attack, denial of service attack, SQL
injection, zero-day exploitation, DNS tunnelling and many more. There different types of cyber
security which are necessary to be installed in the system so that the system can be protected
against these threats such as the critical infrastructure cybersecurity, network security, cloud
security, internet of things security and application security. Along with all such securities it is
important to train and educate the staff so that they can use the technology in a wise manner
without being the victim of cybercrime and moreover the password management and
authentication system must also be implemented for the security.
Create a post installation review questionnaire
1. Are you satisfied with the established inventory, ordering, sales, financial and database
systems?
a. Yes
b. No
8
The testing plan of the information system which is installed for the business is that the
first step is to create the test plan which means that planning of the testing is done that which part
and which feature is the essential one which are necessary to get tested first and then the other
ones. Second is to create the system test cases and test scripts which means that cases are
developed in order to generate the scripts so that the testing could be done in a systematic
manner. Third is to prepare the test data as per the requirements of the testing because any data
cannot be used to test, it is important for the tester to plan the data which can be accurate for the
testing plan and can help in in identifying and detection of the bugs and errors. Fourth is to
execution of the system test cases and script. V is to report the bugs and we test the bugs once
fixed which means that after the detection of the bugs and errors it is important to rectify the
bugs for the next level of testing. it is important to perform the regression testing in order to
verify the impact of the change in the cold. This testing cycle must be repeated until the system
is ready to be deployed and then the last is the sign off from the testing team (Nwokeji, Stachel,
Holmes and Orji, 2019).
Security plan that lists types of threats and how you will protect the system
There are different types of threats which can affect the information system in a negative
manner such as malware, phishing, man in the middle attack, denial of service attack, SQL
injection, zero-day exploitation, DNS tunnelling and many more. There different types of cyber
security which are necessary to be installed in the system so that the system can be protected
against these threats such as the critical infrastructure cybersecurity, network security, cloud
security, internet of things security and application security. Along with all such securities it is
important to train and educate the staff so that they can use the technology in a wise manner
without being the victim of cybercrime and moreover the password management and
authentication system must also be implemented for the security.
Create a post installation review questionnaire
1. Are you satisfied with the established inventory, ordering, sales, financial and database
systems?
a. Yes
b. No
8

Create a grievance process for the client to report any issues
Grievance process includes that first the client is required to generate the report about the
issues they are facing with the information system with the evidence. Secondly they must under
the guarantee and warranty period of the information system as stated in the documents
otherwise client could get charged for servicing and maintenance. If the errors and bugs are
because of the client’s mistake, then they have to pay for the rectification otherwise not. After
clearing all these things, client has to mail the grievance with the document and evidences so that
it can be reviewed deeply and can be rectified soon (Lebedev, Orlov, Kurako and Trapeznikov,
2018).
CONCLUSION
It is concluded that information systems are an important concept to study so that the
implementation in the real world organisations can be effective in a practical manner efficiently.
As per the given scenario, information system is identified and installed with security and post
installation services. Therefore in order to apply such learning, it is important to analyse the
questionnaire creation for stakeholders in order to find out expectations, it is essential to examine
the current problems that the client is experiencing, it is necessary to determine the future
possible issues the client may have, it is significant to gain the knowledge about new system
requirements and specifications for quotations, it is crucial to create the GAP report, it is
imperative to create the proposal, it is required to investigate about the network designing, it is
needed to find out the hardware and software requirements, it is important to assess the
procurement timeline and cabling requirements, it is essential to present the expected timeline, it
is necessary to prepare the 3 year plan to address the expected growth of the company, it is
significant to investigate about the automation of software installation, it is crucial to study about
the testing plan to test the installed system and security plan as well to protect the system, it is
imperative to develop the questionnaire for post installation review and it is vital to generate the
grievance process for the client to report any issues. hence this report covers all such areas in
order to better understand the conception of information systems and small office upgrade
assessment.
9
Grievance process includes that first the client is required to generate the report about the
issues they are facing with the information system with the evidence. Secondly they must under
the guarantee and warranty period of the information system as stated in the documents
otherwise client could get charged for servicing and maintenance. If the errors and bugs are
because of the client’s mistake, then they have to pay for the rectification otherwise not. After
clearing all these things, client has to mail the grievance with the document and evidences so that
it can be reviewed deeply and can be rectified soon (Lebedev, Orlov, Kurako and Trapeznikov,
2018).
CONCLUSION
It is concluded that information systems are an important concept to study so that the
implementation in the real world organisations can be effective in a practical manner efficiently.
As per the given scenario, information system is identified and installed with security and post
installation services. Therefore in order to apply such learning, it is important to analyse the
questionnaire creation for stakeholders in order to find out expectations, it is essential to examine
the current problems that the client is experiencing, it is necessary to determine the future
possible issues the client may have, it is significant to gain the knowledge about new system
requirements and specifications for quotations, it is crucial to create the GAP report, it is
imperative to create the proposal, it is required to investigate about the network designing, it is
needed to find out the hardware and software requirements, it is important to assess the
procurement timeline and cabling requirements, it is essential to present the expected timeline, it
is necessary to prepare the 3 year plan to address the expected growth of the company, it is
significant to investigate about the automation of software installation, it is crucial to study about
the testing plan to test the installed system and security plan as well to protect the system, it is
imperative to develop the questionnaire for post installation review and it is vital to generate the
grievance process for the client to report any issues. hence this report covers all such areas in
order to better understand the conception of information systems and small office upgrade
assessment.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journal
Abdullayev, M., 2020. Analysis of application of information systems at industrial
enterprises. Архив научных исследований, (20).
Brandt, T., Feuerriegel, S. and Neumann, D., 2018. Modeling interferences in information
systems design for cyberphysical systems: Insights from a smart grid
application. European Journal of Information Systems, 27(2), pp.207-220.
Fadelelmoula, A.A., 2018. The effects of the critical success factors for ERP implementation on
the comprehensive achievement of the crucial roles of information systems in the higher
education sector. Interdisciplinary Journal of Information, Knowledge, and
Management, 13(9), pp.21-44.
Fedorova, I., Urunov, A., Rodina, I. and Ostapenko, V., 2020. Financing and quality of housing
construction: introduction of information systems as a regulatory tool. Revista
Inclusiones, pp.328-339.
Granderson, J., Piette, M.A., Ghatikar, G. and Price, P., 2020. Building energy information
systems: State of the technology and user case studies (pp. 133-182). River Publishers.
Gronwald, K.D., 2020. Integrated Business Information Systems. Springer Berlin Heidelberg.
Johansson, P.E., Malmsköld, L., Fast-Berglund, Å. and Moestam, L., 2018. Enhancing future
assembly information systems–putting theory into practice. Procedia Manufacturing, 17,
pp.491-498.
Kang, H.Y., Lee, A.H. and Chan, Y.C., 2019. An integrated fuzzy multi-criteria decision-making
approach for evaluating business process information systems. Mathematics, 7(10),
p.982.
Lebedev, V.N., Orlov, V.L., Kurako, E.A. and Trapeznikov, V.A.A., 2018, October. Tasks of
Small Business and Technologies of Large-scale Information Systems. In 2018 Eleventh
International Conference" Management of large-scale system development"(MLSD (pp.
1-4). IEEE.
Nwokeji, J.C., Stachel, R., Holmes, T. and Orji, R.O., 2019, October. Competencies Required for
Developing Computer and Information Systems Curriculum. In 2019 IEEE Frontiers in
Education Conference (FIE) (pp. 1-9). IEEE.
Öbrand, L., Augustsson, N.P., Mathiassen, L. and Holmström, J., 2019. The interstitiality of IT
risk: An inquiry into information systems development practices. Information Systems
Journal, 29(1), pp.97-118.
Rajaraman, V., 2018. Analysis and design of information systems. PHI Learning Pvt. Ltd..
Umer, T., Rehmani, M.H., Kamal, A.E. and Mihaylova, L., 2019. Information and resource
management systems for Internet of Things: Energy management, communication
protocols and future applications.
10
Books and journal
Abdullayev, M., 2020. Analysis of application of information systems at industrial
enterprises. Архив научных исследований, (20).
Brandt, T., Feuerriegel, S. and Neumann, D., 2018. Modeling interferences in information
systems design for cyberphysical systems: Insights from a smart grid
application. European Journal of Information Systems, 27(2), pp.207-220.
Fadelelmoula, A.A., 2018. The effects of the critical success factors for ERP implementation on
the comprehensive achievement of the crucial roles of information systems in the higher
education sector. Interdisciplinary Journal of Information, Knowledge, and
Management, 13(9), pp.21-44.
Fedorova, I., Urunov, A., Rodina, I. and Ostapenko, V., 2020. Financing and quality of housing
construction: introduction of information systems as a regulatory tool. Revista
Inclusiones, pp.328-339.
Granderson, J., Piette, M.A., Ghatikar, G. and Price, P., 2020. Building energy information
systems: State of the technology and user case studies (pp. 133-182). River Publishers.
Gronwald, K.D., 2020. Integrated Business Information Systems. Springer Berlin Heidelberg.
Johansson, P.E., Malmsköld, L., Fast-Berglund, Å. and Moestam, L., 2018. Enhancing future
assembly information systems–putting theory into practice. Procedia Manufacturing, 17,
pp.491-498.
Kang, H.Y., Lee, A.H. and Chan, Y.C., 2019. An integrated fuzzy multi-criteria decision-making
approach for evaluating business process information systems. Mathematics, 7(10),
p.982.
Lebedev, V.N., Orlov, V.L., Kurako, E.A. and Trapeznikov, V.A.A., 2018, October. Tasks of
Small Business and Technologies of Large-scale Information Systems. In 2018 Eleventh
International Conference" Management of large-scale system development"(MLSD (pp.
1-4). IEEE.
Nwokeji, J.C., Stachel, R., Holmes, T. and Orji, R.O., 2019, October. Competencies Required for
Developing Computer and Information Systems Curriculum. In 2019 IEEE Frontiers in
Education Conference (FIE) (pp. 1-9). IEEE.
Öbrand, L., Augustsson, N.P., Mathiassen, L. and Holmström, J., 2019. The interstitiality of IT
risk: An inquiry into information systems development practices. Information Systems
Journal, 29(1), pp.97-118.
Rajaraman, V., 2018. Analysis and design of information systems. PHI Learning Pvt. Ltd..
Umer, T., Rehmani, M.H., Kamal, A.E. and Mihaylova, L., 2019. Information and resource
management systems for Internet of Things: Energy management, communication
protocols and future applications.
10
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




