Smart Card Based Authentication for Medical Data: Literature Review
VerifiedAdded on 2024/06/28
|89
|11181
|293
Literature Review
AI Summary
This literature review explores the application of smart card-based user authentication in maintaining the data integrity and privacy of medical health records. It analyzes five journal papers, focusing on techniques like certificateless aggregate signature schemes, lightweight streaming authenticated data structures, and verifiable keyword search methods. The review covers solutions such as CL-AS for healthcare wireless sensor networks, PPDIVM-LSADS for cyber-physical systems, and verifiable keyword search schemes for mobile healthcare networks. It discusses the goals, processes, advantages, and limitations of each approach, highlighting their potential to enhance medical data security and access control. The review also evaluates the value of these solutions for a proposed project, emphasizing their role in securing medical health records and improving data management in healthcare settings. Desklib provides access to this and other solved assignments for students.

Literature Review
Student Name & CSU ID
Project Topic Title Smart Card based user authentication in maintaining data integrity and privacy of medical health records
1
Student Name & CSU ID
Project Topic Title Smart Card based user authentication in maintaining data integrity and privacy of medical health records
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Version 1.0 _ Week 1 (5 Journal Papers from CSU Library)
1
Reference in APA format that will be in
'Reference List'
Kumar, P., Kumari, S., Sharma, V., Sangaiah, A. K., Wei, J., & Li, X. (2017). A Certificateless aggregate
signature scheme for healthcare wireless sensor network. Sustainable Computing: Informatics and Systems.
Citation that will be in the content (Kumar, et. al., 2017)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://ac-els-cdn-
com.ezproxy.csu.edu.au/
S2210537917300227/1-s2.0-
S2210537917300227-main.pdf?
_tid=819f5332-39f3-441d-9f11-
97f01ccad1dc&acdnat=1532063198_bb21a
6c24faf79a52ecb120071388933
Level of Journal – Q2 Certificateless aggregate signature scheme, Diffie-Hellman
assumption, Healthcare wireless sensor network, Security
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Techniques/algorithm :
CL-AS (Certificateless aggregate
signature) scheme
Tools:
Internet, wireless standards, wireless sensor
networks.
Applied Area:
Healthcare
Problem:
The authors claim that certificate management,
while the system generates public key for
match up, is very complex and resource
utilizing process.
Goal:
The research aims to increase the security of
patient's online available medical data by
introducing the aggregate signature scheme.
E-health (Electronic Health)
Random Oracle Model
Diffie-Hellman assumption
Sensors
healthcare professionals
personal digital assistant (PDA)
2
1
Reference in APA format that will be in
'Reference List'
Kumar, P., Kumari, S., Sharma, V., Sangaiah, A. K., Wei, J., & Li, X. (2017). A Certificateless aggregate
signature scheme for healthcare wireless sensor network. Sustainable Computing: Informatics and Systems.
Citation that will be in the content (Kumar, et. al., 2017)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://ac-els-cdn-
com.ezproxy.csu.edu.au/
S2210537917300227/1-s2.0-
S2210537917300227-main.pdf?
_tid=819f5332-39f3-441d-9f11-
97f01ccad1dc&acdnat=1532063198_bb21a
6c24faf79a52ecb120071388933
Level of Journal – Q2 Certificateless aggregate signature scheme, Diffie-Hellman
assumption, Healthcare wireless sensor network, Security
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Techniques/algorithm :
CL-AS (Certificateless aggregate
signature) scheme
Tools:
Internet, wireless standards, wireless sensor
networks.
Applied Area:
Healthcare
Problem:
The authors claim that certificate management,
while the system generates public key for
match up, is very complex and resource
utilizing process.
Goal:
The research aims to increase the security of
patient's online available medical data by
introducing the aggregate signature scheme.
E-health (Electronic Health)
Random Oracle Model
Diffie-Hellman assumption
Sensors
healthcare professionals
personal digital assistant (PDA)
2
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Data gathering –
The sensed data is gathered by healthcare
professionals. Further, data is analysed to
provide prescription to the patient.
Sensors have the capability of calculation. N/A
2 Medical server –
Medical servers are used to transfer the patient’s
information to healthcare professionals.
Strong computing power, Storage space and
has capability to process a large amount of
data received by sensors.
N/A
3 Aggregators –
Collecting the signature from care-district and
generate aggregated signature and transfer to
Medical server.
Limited power of computation and calculation. Limited power of computation and
calculation.
4 Signature transfer through sensors –
Sensors are embedded with the private-public
key pair which belongs to Care-district.
Capable to generate signed message from a
physical word by using private key.
Resource-limited.
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
signature schemes (ID-PKC) public key cryptography
Random Oracle Model security analysis
3
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Data gathering –
The sensed data is gathered by healthcare
professionals. Further, data is analysed to
provide prescription to the patient.
Sensors have the capability of calculation. N/A
2 Medical server –
Medical servers are used to transfer the patient’s
information to healthcare professionals.
Strong computing power, Storage space and
has capability to process a large amount of
data received by sensors.
N/A
3 Aggregators –
Collecting the signature from care-district and
generate aggregated signature and transfer to
Medical server.
Limited power of computation and calculation. Limited power of computation and
calculation.
4 Signature transfer through sensors –
Sensors are embedded with the private-public
key pair which belongs to Care-district.
Capable to generate signed message from a
physical word by using private key.
Resource-limited.
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
signature schemes (ID-PKC) public key cryptography
Random Oracle Model security analysis
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Input and Output Critical Thinking: Feature of this work,
and Why (Justify)
Critical Thinking: Limitations of the
research current solution, and Why
(Justify)
Input (Data) Output (View)
KGC takes a user’s identity
as input.
The input of the research is to
develop a scheme which is
supported signature
authentication for accessing
medical data of patient.
Targeted identity with the
corresponding public key set
The output is to improvise
security of communication in
healthcare wireless sensor
network using aggregate
signature scheme. That could
increase the patient satisfaction
with the medical service.
Certificateless signature (CLS) scheme has
been proposed in the paper. It could
increase the security of communication in
healthcare wireless sensor network.
The proposed include aggregate signature
that increase the security while accessing
the data online.
The proposal is more efficient in terms of
energy consumption and computational
cost.
Calculation and computation by the
sensors are still the limitations in the
research. Although, it is not a big issue
to resolve but the tiny one.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is
valuable for your project
In accordance with Kumar et al. (2017), CL-AS (Certificate less
aggregate signature) scheme can be introduced as an assumption
for the proposed scheme. The aggregate signature-based
authentication mechanism in healthcare wireless sensor network
shall enhance the medical data security of the patients using their
identity (Kumar et al., 2017)
The inducers of the proposed mechanism
are hospitals & patients. The scheme
introduced shall aid in securing the medical
health records via aggregated signature of
patient.
The proposed framework for chronically
ill patients will help to enhance the
process of in-hospital and out-hospital
data to get vaulted and get the access
through third-party applications.
Diagram/Flowchart
4
and Why (Justify)
Critical Thinking: Limitations of the
research current solution, and Why
(Justify)
Input (Data) Output (View)
KGC takes a user’s identity
as input.
The input of the research is to
develop a scheme which is
supported signature
authentication for accessing
medical data of patient.
Targeted identity with the
corresponding public key set
The output is to improvise
security of communication in
healthcare wireless sensor
network using aggregate
signature scheme. That could
increase the patient satisfaction
with the medical service.
Certificateless signature (CLS) scheme has
been proposed in the paper. It could
increase the security of communication in
healthcare wireless sensor network.
The proposed include aggregate signature
that increase the security while accessing
the data online.
The proposal is more efficient in terms of
energy consumption and computational
cost.
Calculation and computation by the
sensors are still the limitations in the
research. Although, it is not a big issue
to resolve but the tiny one.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is
valuable for your project
In accordance with Kumar et al. (2017), CL-AS (Certificate less
aggregate signature) scheme can be introduced as an assumption
for the proposed scheme. The aggregate signature-based
authentication mechanism in healthcare wireless sensor network
shall enhance the medical data security of the patients using their
identity (Kumar et al., 2017)
The inducers of the proposed mechanism
are hospitals & patients. The scheme
introduced shall aid in securing the medical
health records via aggregated signature of
patient.
The proposed framework for chronically
ill patients will help to enhance the
process of in-hospital and out-hospital
data to get vaulted and get the access
through third-party applications.
Diagram/Flowchart
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
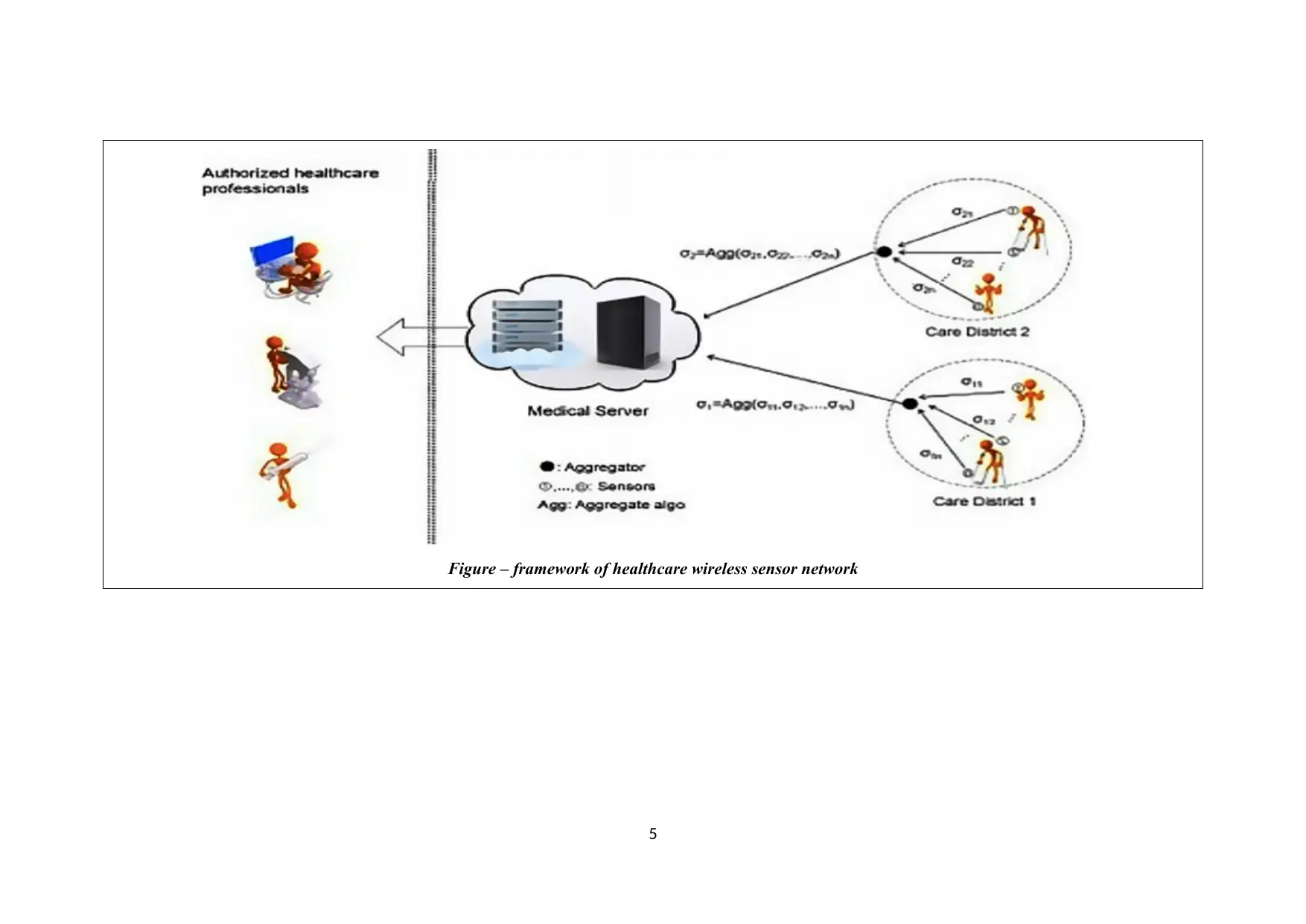
Figure – framework of healthcare wireless sensor network
5
5
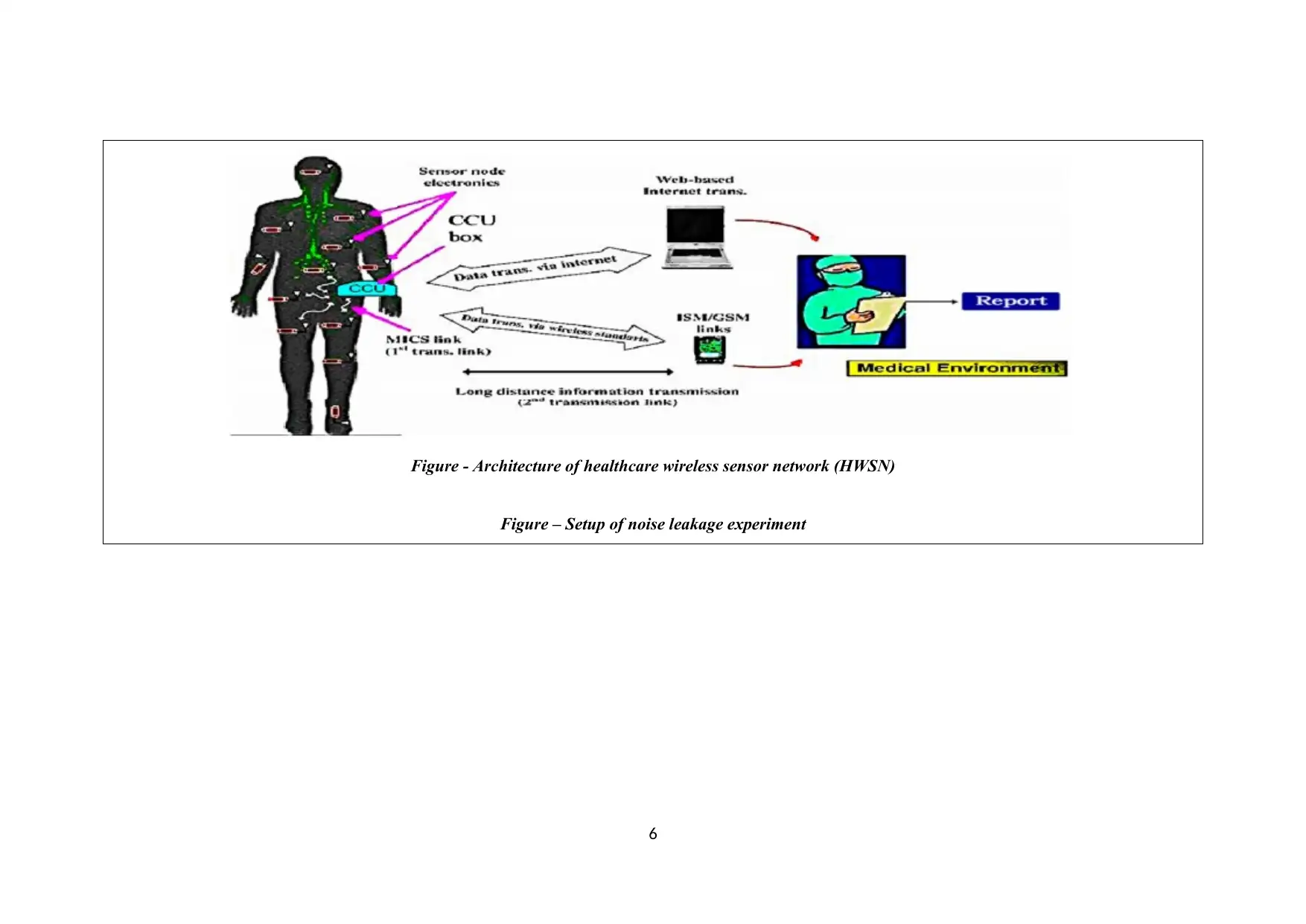
Figure - Architecture of healthcare wireless sensor network (HWSN)
Figure – Setup of noise leakage experiment
6
Figure – Setup of noise leakage experiment
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
2
Reference in APA format that will be in
'Reference List'
Xu, J., Wei, L., Wu, W., Wang, A., Zhang, Y., & Zhou, F. (2018). Privacy-preserving data integrity verification
by using lightweight streaming authenticated data structures for healthcare cyber–physical system. Future
Generation Computer Systems.
Citation that will be in the content (Xu, et al., 2017)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://ac-els-cdn-
com.ezproxy.csu.edu.au/
S0167739X17326067/1-s2.0-
S0167739X17326067-main.pdf?
_tid=c0303bc4-0c85-44fa-b68c-
858d5e5060e0&acdnat=1532106809_f458
e06b40b469a6ff6ccbf115b51be5
Level of Journal - Q1 Wireless Body Area Networks (WBANs), Cloud computing,
Authenticated data structures, Cyber-physical system (CPS),
Healthcare
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Privacy preserving data integrity
verification model by using lightweight
streaming authenticated data structures
(PPDIVM-LSADS)
Tools:
Electronic health records (EHRs)
Wireless Body Area Networks (WBANs)
Applied Area:
Problem:
In this journal, the authors identified that the
major issue with existing cyber-physical
system is underdeveloped security in medical
data management. Further, hostile
environments integrity is disturbed.
Goal:
The goal of the research is to develop a
privacy-preserving data integrity verification
by using lightweight streaming authenticated
Cyber-physical system (CPS)
Cloud computing,
Electronic health records (EHRs)
Health-CPS
7
Reference in APA format that will be in
'Reference List'
Xu, J., Wei, L., Wu, W., Wang, A., Zhang, Y., & Zhou, F. (2018). Privacy-preserving data integrity verification
by using lightweight streaming authenticated data structures for healthcare cyber–physical system. Future
Generation Computer Systems.
Citation that will be in the content (Xu, et al., 2017)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://ac-els-cdn-
com.ezproxy.csu.edu.au/
S0167739X17326067/1-s2.0-
S0167739X17326067-main.pdf?
_tid=c0303bc4-0c85-44fa-b68c-
858d5e5060e0&acdnat=1532106809_f458
e06b40b469a6ff6ccbf115b51be5
Level of Journal - Q1 Wireless Body Area Networks (WBANs), Cloud computing,
Authenticated data structures, Cyber-physical system (CPS),
Healthcare
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Privacy preserving data integrity
verification model by using lightweight
streaming authenticated data structures
(PPDIVM-LSADS)
Tools:
Electronic health records (EHRs)
Wireless Body Area Networks (WBANs)
Applied Area:
Problem:
In this journal, the authors identified that the
major issue with existing cyber-physical
system is underdeveloped security in medical
data management. Further, hostile
environments integrity is disturbed.
Goal:
The goal of the research is to develop a
privacy-preserving data integrity verification
by using lightweight streaming authenticated
Cyber-physical system (CPS)
Cloud computing,
Electronic health records (EHRs)
Health-CPS
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Health-CPS data structures for healthcare cyber–physical
system
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Data source –
Gather the real-time data from the source or
body of the patient or client. Information such as
body temperature & blood pressure. If the client
or patient willing to get the detail about data,
this process route the query to the system
through authentication.
Reduce the storage issue Range query
2 Cloud server –
Provide query and storage services. It receives
and collects the data from the source If the client
or patient willing to get the detail about data,
this process route the query to the system
through authentication.
Multitasking at the same time Plaintext weights thus prone to hijacking
3 Data user –
This is the main step as it generates a pair key
for the authentication. Public key forwarding to
server and private key retain itself.
The procedure provides security to the process. N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
8
system
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Data source –
Gather the real-time data from the source or
body of the patient or client. Information such as
body temperature & blood pressure. If the client
or patient willing to get the detail about data,
this process route the query to the system
through authentication.
Reduce the storage issue Range query
2 Cloud server –
Provide query and storage services. It receives
and collects the data from the source If the client
or patient willing to get the detail about data,
this process route the query to the system
through authentication.
Multitasking at the same time Plaintext weights thus prone to hijacking
3 Data user –
This is the main step as it generates a pair key
for the authentication. Public key forwarding to
server and private key retain itself.
The procedure provides security to the process. N/A
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
8
Data weights VerfierTree
Lightweight Streaming Authenticated Data Structure Fully Homomorphic encryption
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
An empty data
structure and
private key
In order is to improve
the security and
authentication system
data access using the
two-way
authentication
scheme.
Public/private key
pair
The out of the
research is to provide
private and public key
of the storage data so
that client or hospital
can access the data
and care the patient
effectively.
The feature of this research is to introduce three
entities data source, data server, data user. These
entities are based on the PPDIVM-LADS system.
This proposed system provides data server
capability to generate public and private key to get
the access to data available in cloud storage.
This research has a few limitations such as storage
capacity and computation. The author had
illuminated these issues to be compelling the
processing of the projected scheme.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In the research proposed PPDIVM-LADS
(Privacy-preserving data integrity verification-
lightweight streaming authenticated data
structures) system for increasing the security of
healthcare data (Xu et al., 2018).
Clients and hospitals are projected to be the major
users of this scheme as illuminated by the author.
The system can be used for securing the un-stored
data that is in need to be restored after storage thus
aiming to eradicate issue in the wearable devices.
Also, enhancing the security of healthcare data.
In the research, author has been proposed a system
Health-CPS based on cloud computing. The two-
way authentication provided security to the
medical data.
Diagram/Flowchart
9
Lightweight Streaming Authenticated Data Structure Fully Homomorphic encryption
Input and Output Critical Thinking: Feature of this work, and
Why (Justify)
Critical Thinking: Limitations of the research
current solution, and Why (Justify)
Input (Data) Output (View)
An empty data
structure and
private key
In order is to improve
the security and
authentication system
data access using the
two-way
authentication
scheme.
Public/private key
pair
The out of the
research is to provide
private and public key
of the storage data so
that client or hospital
can access the data
and care the patient
effectively.
The feature of this research is to introduce three
entities data source, data server, data user. These
entities are based on the PPDIVM-LADS system.
This proposed system provides data server
capability to generate public and private key to get
the access to data available in cloud storage.
This research has a few limitations such as storage
capacity and computation. The author had
illuminated these issues to be compelling the
processing of the projected scheme.
(Describe the research/current solution) Evaluation Criteria How this research/current solution is valuable
for your project
In the research proposed PPDIVM-LADS
(Privacy-preserving data integrity verification-
lightweight streaming authenticated data
structures) system for increasing the security of
healthcare data (Xu et al., 2018).
Clients and hospitals are projected to be the major
users of this scheme as illuminated by the author.
The system can be used for securing the un-stored
data that is in need to be restored after storage thus
aiming to eradicate issue in the wearable devices.
Also, enhancing the security of healthcare data.
In the research, author has been proposed a system
Health-CPS based on cloud computing. The two-
way authentication provided security to the
medical data.
Diagram/Flowchart
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
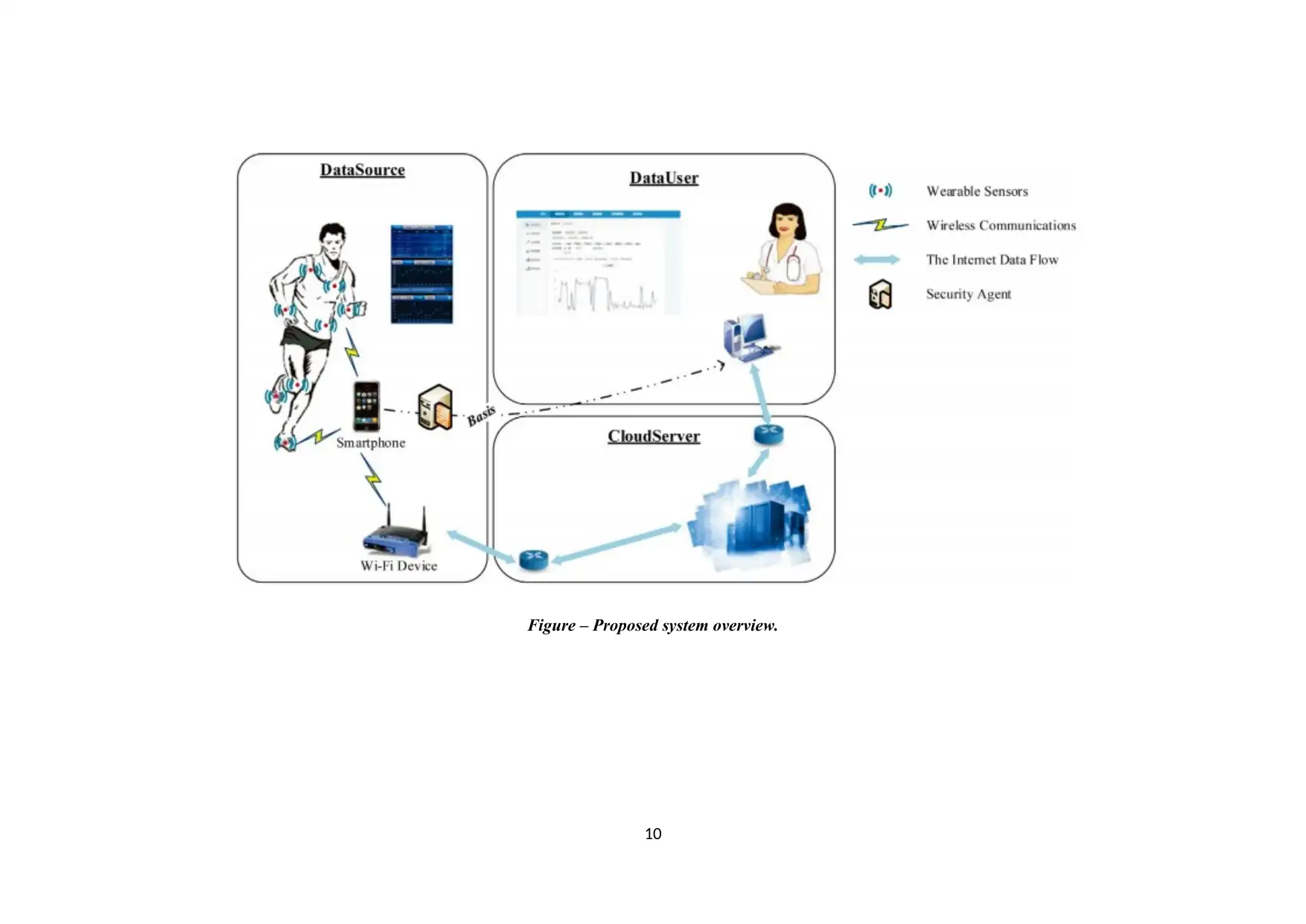
Figure – Proposed system overview.
10
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3
Reference in APA format that will be in
'Reference List'
Chen, Z., Zhang, F., Zhang, P., Liu, J. K., Huang, J., Zhao, H., & Shen, J. (2018). Verifiable keyword search for
secure big data-based mobile healthcare networks with fine-grained authorization control. Future Generation
Computer Systems, 87, 712-724.
Citation that will be in the content (Chen, et. al., 2018)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S0167739X17300730
Level of Journal - Q1 Mobile healthcare networks, Big data, Verifiable keyword
search, Authorization control, Invertible Bloom lookup table
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Bloom lookup table and Merkle hash tree
Tools:
Big data
Wearable devices
Applied Area:
Healthcare data security
Problem:
The problem on which the research is, while
wider adoptions are made in MHNs- Mobile
healthcare networks, untrusted servers are
engaged for data encryption. However, in this
process the data flexibility is affected.
Goal:
The authors of this research have aimed to
introduce a scheme that is based on keyword
searching. It is projected to be increasing the
cloud data security while anyone attempts to
attain access.
Mobile healthcare networks (MHNs)
Internet of Things (IoT)
Cloud service provider (CSP)
Invertible Bloom lookup table (IBLT)
11
Reference in APA format that will be in
'Reference List'
Chen, Z., Zhang, F., Zhang, P., Liu, J. K., Huang, J., Zhao, H., & Shen, J. (2018). Verifiable keyword search for
secure big data-based mobile healthcare networks with fine-grained authorization control. Future Generation
Computer Systems, 87, 712-724.
Citation that will be in the content (Chen, et. al., 2018)
URL of the Reference Level of Journal (Q1, Q2, …Qn) Keywords in this Reference
https://www-sciencedirect-
com.ezproxy.csu.edu.au/science/article/
pii/S0167739X17300730
Level of Journal - Q1 Mobile healthcare networks, Big data, Verifiable keyword
search, Authorization control, Invertible Bloom lookup table
The Name of the Current Solution
(Technique/ Method/ Scheme/
Algorithm/ Model/ Tool/ Framework/ ...
etc )
The Goal (Objective) of this Solution &
What is the Problem that need to be solved
What are the components of it?
Technique/Algorithm name:
Bloom lookup table and Merkle hash tree
Tools:
Big data
Wearable devices
Applied Area:
Healthcare data security
Problem:
The problem on which the research is, while
wider adoptions are made in MHNs- Mobile
healthcare networks, untrusted servers are
engaged for data encryption. However, in this
process the data flexibility is affected.
Goal:
The authors of this research have aimed to
introduce a scheme that is based on keyword
searching. It is projected to be increasing the
cloud data security while anyone attempts to
attain access.
Mobile healthcare networks (MHNs)
Internet of Things (IoT)
Cloud service provider (CSP)
Invertible Bloom lookup table (IBLT)
11
The Process (Mechanism) of this Work; The process steps of the Technique/system
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Initialisation of the system-
Generate two keys public and private. Public
key publishes and private key retains itself.
Security parameters used for key generation. N/A
2 Secret key generation –
By using public key and private key, secret key
generated.
Algorithm used is advance in the key
generation
Computational difficulty
3 Encryption –
When client or user willing to upload data and
need access to that. Collaboration of two
algorithms does the encryption process.
Secure process Time-consuming
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Wearable device Access networks
MHNs big data scheme
Cryptography library cpabe toolkit and the Java Pairing
Input and Output Critical Thinking: Feature of this work, Critical Thinking: Limitations of the
12
Process Steps Advantage (Purpose of this step) Disadvantage (Limitation/Challenge)
1 Initialisation of the system-
Generate two keys public and private. Public
key publishes and private key retains itself.
Security parameters used for key generation. N/A
2 Secret key generation –
By using public key and private key, secret key
generated.
Algorithm used is advance in the key
generation
Computational difficulty
3 Encryption –
When client or user willing to upload data and
need access to that. Collaboration of two
algorithms does the encryption process.
Secure process Time-consuming
Validation Criteria (Measurement Criteria)
Dependent Variable Independent Variable
Wearable device Access networks
MHNs big data scheme
Cryptography library cpabe toolkit and the Java Pairing
Input and Output Critical Thinking: Feature of this work, Critical Thinking: Limitations of the
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 89
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



