SME With Electronic Commercial Transact Research Paper 2022
VerifiedAdded on 2022/09/16
|13
|3019
|21
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: SME WITH ELECTRONIC COMMERCIAL TRANSACTION
SME WITH ELECTRONIC COMMERCIAL TRANSACTION
Name of Student:
Name of University:
Author note:
SME WITH ELECTRONIC COMMERCIAL TRANSACTION
Name of Student:
Name of University:
Author note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
Table of Contents
Executive Summary...................................................................................................................2
Introduction................................................................................................................................3
Body...........................................................................................................................................3
Comodo certificate fraud hack...............................................................................................3
SME: Shopmatic....................................................................................................................3
IT security problem................................................................................................................4
Security problems of Shopmatic............................................................................................4
Proposed solution...................................................................................................................6
Conclusion..................................................................................................................................8
Recommendation........................................................................................................................8
Appendices:..............................................................................................................................12
Table of Contents
Executive Summary...................................................................................................................2
Introduction................................................................................................................................3
Body...........................................................................................................................................3
Comodo certificate fraud hack...............................................................................................3
SME: Shopmatic....................................................................................................................3
IT security problem................................................................................................................4
Security problems of Shopmatic............................................................................................4
Proposed solution...................................................................................................................6
Conclusion..................................................................................................................................8
Recommendation........................................................................................................................8
Appendices:..............................................................................................................................12

2SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
Executive Summary
The aim of the paper is to develop a clear structure relating the Comodo certificate fraud hack
with the SME “Shopmatic” that conduct electronic commercial transactions. In the paper a
brief idea about security problems that are related to IT will be described. The structure of the
organisation will also be defined and the way it uses the electronic transactions. After which
the problems which may affect the organisation will also be discussed. The report will also
give certain solutions relating to the issues. It will be discussed the way the organisation can
overcome the threat while using electronic transactions. Thus the report will help all the other
organisations to understand about the threat and they will be able to guide themselves
according to the paper and will be able to avoid any such vulnerabilities. In the end, the paper
will conclude the advantages that the viewers will be going to avail due to the report. The
report also concludes that the apaer will be helpful for both the companies and the clients.
Executive Summary
The aim of the paper is to develop a clear structure relating the Comodo certificate fraud hack
with the SME “Shopmatic” that conduct electronic commercial transactions. In the paper a
brief idea about security problems that are related to IT will be described. The structure of the
organisation will also be defined and the way it uses the electronic transactions. After which
the problems which may affect the organisation will also be discussed. The report will also
give certain solutions relating to the issues. It will be discussed the way the organisation can
overcome the threat while using electronic transactions. Thus the report will help all the other
organisations to understand about the threat and they will be able to guide themselves
according to the paper and will be able to avoid any such vulnerabilities. In the end, the paper
will conclude the advantages that the viewers will be going to avail due to the report. The
report also concludes that the apaer will be helpful for both the companies and the clients.

3SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
Introduction
The main motive of the investigation is to find all the vulnerabilities that are related to
the attack of Comodo certificate fraud hack. It is also aiming to understand the ways which
may affect the SME’s that are related to electronic commercial transaction. In this report an
organisation is choosen named Shopmatic which does e-commerce transactions. A relation is
drawn in between the fraud attack and the organisation which may cause effect on the
organisation. In this case it is discussed in the report the way the problems can be countered
by the organisation. The report aims that the discussions will help the organisation from
getting affected from the related attacks in future.
Body
Comodo certificate fraud hack
This is the type of hack which cause creating of certificates by Comodo (Kang, Fahd
and Venkatraman 2018). This was popular in case of the email providers such as Gmail,
Hotmail and others. The attack choose targets which are mainly of various email sites (Roosa
and Schultze 2013). It is said that an Iranian hacker is in behind of this hack. It is alleged that
there is full access with him to the InstantSSL.it (Specter 2016). With the help of this the
hacker managed to make nine such certificates of that to within 10 to 15 minutes.
SME: Shopmatic
This is an ecommerce company that have international business. The main motto of
this company is to help people that are online intending to sell various products and various
services. They provide any type of services online, thus they goes through various electronic
transactions as well (goshopmatic 2019). In other words they are mainly dependent on
electronic transaction. They also have collaborations with different companies.
Introduction
The main motive of the investigation is to find all the vulnerabilities that are related to
the attack of Comodo certificate fraud hack. It is also aiming to understand the ways which
may affect the SME’s that are related to electronic commercial transaction. In this report an
organisation is choosen named Shopmatic which does e-commerce transactions. A relation is
drawn in between the fraud attack and the organisation which may cause effect on the
organisation. In this case it is discussed in the report the way the problems can be countered
by the organisation. The report aims that the discussions will help the organisation from
getting affected from the related attacks in future.
Body
Comodo certificate fraud hack
This is the type of hack which cause creating of certificates by Comodo (Kang, Fahd
and Venkatraman 2018). This was popular in case of the email providers such as Gmail,
Hotmail and others. The attack choose targets which are mainly of various email sites (Roosa
and Schultze 2013). It is said that an Iranian hacker is in behind of this hack. It is alleged that
there is full access with him to the InstantSSL.it (Specter 2016). With the help of this the
hacker managed to make nine such certificates of that to within 10 to 15 minutes.
SME: Shopmatic
This is an ecommerce company that have international business. The main motto of
this company is to help people that are online intending to sell various products and various
services. They provide any type of services online, thus they goes through various electronic
transactions as well (goshopmatic 2019). In other words they are mainly dependent on
electronic transaction. They also have collaborations with different companies.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
IT security problem
The main issue related to security problems in IT is hacking (Sen 2015). Hacking is
the term that illustrates any type of access which is unauthorised into the database of a
computer system, server network which may cause various type of vulnerabilities in the
system or in the network.
Security problems of Shopmatic
When it is compared in between Shopmatic and Comodo certificate fraud hack it can
be noticed that there are certain ways by which the hackers may attack on Shopmatic. Firstly
the organisation performs all its work online including their electronic transactions
(Stojmenovic and Wen 2014). Besdies there are huge amount of important works done by
Shopmatic which may attract the hackers to hack the organisation.
As the organisation uses E-business, the system of the organisations are always
connected to the internet with other devices. Thus there are high chances for the organisation
to download any type of computer virus, malwares and worms form the internet (Pathan
2016). This may lead to the loss of data of the system and this can lead to loss of money
while performing electronic transactions through the systems.
There are also availability of various software bugs in the internet. This are
themselves malicious programs though they are different from that of viruses. Hacking can
also be done in this way as well. This is a type of computer program which may the systems
behave in a totally different way. This may also cause crash of the sights which may cause
breakage during any electronic transaction. In this time the hackers may have an access to the
transaction and they may steal the money available in the transaction.
IT security problem
The main issue related to security problems in IT is hacking (Sen 2015). Hacking is
the term that illustrates any type of access which is unauthorised into the database of a
computer system, server network which may cause various type of vulnerabilities in the
system or in the network.
Security problems of Shopmatic
When it is compared in between Shopmatic and Comodo certificate fraud hack it can
be noticed that there are certain ways by which the hackers may attack on Shopmatic. Firstly
the organisation performs all its work online including their electronic transactions
(Stojmenovic and Wen 2014). Besdies there are huge amount of important works done by
Shopmatic which may attract the hackers to hack the organisation.
As the organisation uses E-business, the system of the organisations are always
connected to the internet with other devices. Thus there are high chances for the organisation
to download any type of computer virus, malwares and worms form the internet (Pathan
2016). This may lead to the loss of data of the system and this can lead to loss of money
while performing electronic transactions through the systems.
There are also availability of various software bugs in the internet. This are
themselves malicious programs though they are different from that of viruses. Hacking can
also be done in this way as well. This is a type of computer program which may the systems
behave in a totally different way. This may also cause crash of the sights which may cause
breakage during any electronic transaction. In this time the hackers may have an access to the
transaction and they may steal the money available in the transaction.

5SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
In an e-business the organisation allow their users to interact with a website after
registering in it (Borgohain, Kumar and Sanyal 2015). The users also buy things through the
website and pay online with the help of electronic transactions. The hackers can easily find
out the weakness that are available in the website and after that they can easily hack the
website and get access to it. After this they may steal various important information from the
website and even they can steal money from the website while in a transaction (Ahmed and
Hossain 2014). Thus Shopmatic have huge amount of risks from the hackers as their website
have get hack by this process and many important information’s may get lost and huge
amount of money may also be stolen.
To perform the electronic transactions of Shopmatic the devices and the systems that
are used are mainly wireless devices. The hackers put various security hazards in the network
of the organisation and the outsiders can easily enter the network (Fennelly 2016). When a
security key is provided by setting a password in the network becomes difficult for the
outsiders to interrupt in the network, though a wireless connection can never be as secured as
of a wired network. Though the organisation uses a wireless network thus it becomes easier
for the hackers to interrupt in the network and they can easily steal useful information’s form
the network and even can interrupt in an online transaction done through the network.
By the application of spear phishing the attacks can also hack the network of the
organisation which may cause huge amount of loss for the organisation every year (Wang et
al. 2015). This technique can be a serious challenge for the organisation.
If the mentioned organisation do not have enough knowledge regarding the security of
the network of the organisation there remains various drawbacks in the organisation which
helps the attackers to easily hack the systems and the network of the organisation and get
access to it.
In an e-business the organisation allow their users to interact with a website after
registering in it (Borgohain, Kumar and Sanyal 2015). The users also buy things through the
website and pay online with the help of electronic transactions. The hackers can easily find
out the weakness that are available in the website and after that they can easily hack the
website and get access to it. After this they may steal various important information from the
website and even they can steal money from the website while in a transaction (Ahmed and
Hossain 2014). Thus Shopmatic have huge amount of risks from the hackers as their website
have get hack by this process and many important information’s may get lost and huge
amount of money may also be stolen.
To perform the electronic transactions of Shopmatic the devices and the systems that
are used are mainly wireless devices. The hackers put various security hazards in the network
of the organisation and the outsiders can easily enter the network (Fennelly 2016). When a
security key is provided by setting a password in the network becomes difficult for the
outsiders to interrupt in the network, though a wireless connection can never be as secured as
of a wired network. Though the organisation uses a wireless network thus it becomes easier
for the hackers to interrupt in the network and they can easily steal useful information’s form
the network and even can interrupt in an online transaction done through the network.
By the application of spear phishing the attacks can also hack the network of the
organisation which may cause huge amount of loss for the organisation every year (Wang et
al. 2015). This technique can be a serious challenge for the organisation.
If the mentioned organisation do not have enough knowledge regarding the security of
the network of the organisation there remains various drawbacks in the organisation which
helps the attackers to easily hack the systems and the network of the organisation and get
access to it.

6SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
If the network of the organisation is attacked by DDoS attack it may paralyze the
whole organisation because it leads the network to be inaccessible by the organisation while
on the other hand the attackers can access the network and the system. Thus this is the attack
which is very serious for the organisation.
The attack that was held by the hacker of the Comodo certificate fraud attack was
very malicious. As they hacked the system and the network totally and then they made fake
certificates and then distributed them through the web. As the discussed organisation is also
dependent on the web, their business are held through the websites and the transactions
related to their business occurs electronically there are broad ways for the particular hacker to
hack the website and the network of the organisation. After which they can easily make fake
products like the products that are sold by the organisation. Even they can make fake
payment gateways to that of the original gateways of the organisation which will disrupt the
users and they can even make their payment in the fake gateway. This is the reason this type
of hackers are very critical for the organisation as they are completely depend on the
electronic transaction. The organisation is not even that much secured reading this type of
attacks which even attracts the attackers more.
Proposed solution
From the above discussion it can be seen that there are different security problems in
the organisation which makes easier for the hackers to attack the organisation. It is suggested
that the organisation should maintain certain solutions which can prevent the organisation
form getting attacked by the hackers:
Installation of trusted Anti-virus software is one of the primary step that should be
followed by the organisation. All the systems used by the organisation must have the
If the network of the organisation is attacked by DDoS attack it may paralyze the
whole organisation because it leads the network to be inaccessible by the organisation while
on the other hand the attackers can access the network and the system. Thus this is the attack
which is very serious for the organisation.
The attack that was held by the hacker of the Comodo certificate fraud attack was
very malicious. As they hacked the system and the network totally and then they made fake
certificates and then distributed them through the web. As the discussed organisation is also
dependent on the web, their business are held through the websites and the transactions
related to their business occurs electronically there are broad ways for the particular hacker to
hack the website and the network of the organisation. After which they can easily make fake
products like the products that are sold by the organisation. Even they can make fake
payment gateways to that of the original gateways of the organisation which will disrupt the
users and they can even make their payment in the fake gateway. This is the reason this type
of hackers are very critical for the organisation as they are completely depend on the
electronic transaction. The organisation is not even that much secured reading this type of
attacks which even attracts the attackers more.
Proposed solution
From the above discussion it can be seen that there are different security problems in
the organisation which makes easier for the hackers to attack the organisation. It is suggested
that the organisation should maintain certain solutions which can prevent the organisation
form getting attacked by the hackers:
Installation of trusted Anti-virus software is one of the primary step that should be
followed by the organisation. All the systems used by the organisation must have the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
software installed in it. Biggest concern must be given to the networks tend the systems that
are used remotely.
The organisation must look up to the anti-virus software so that it is always updated,
because if the anti-virus software gets outdated it becomes easier for the attackers to attack on
the network.
The organisation must always employ a reputed firewall in the network of the
organisation, because the firewall helps to block any type of unwanted traffic form getting
entered into the network of the organisation. It also protect the gateway of the electronic
transaction any blocks all the outsiders from entering the network (Scott-Hayward,
O'Callaghan and Sezer 2013). The firewall is more important for the organisation because
they are very useful for wireless connections and this is the organisation which is totally
dependent on wireless network.
All traffic of the email must be filtered because the hacker discussed in the topic
mainly focuses on the emails to attack on their target. Thus all of the incoming emails and the
outgoing emails must be filtered and must be checked if there are any viruses attached in the
emails. Even if the emails are coming from any known sources then also they should be
checked as they may attach any link with the mail and by clicking on this it may lead to a
computer virus attack.
The downloads that are done form the internet network must be scanned because there
can be lot of virus which may enter the system or the network form the internet downloads
(Wang 2014). The hackers intentionally attack virus to different files that are available in the
internet for downloads and they may intentionally attach this viruses to the specific files
which have high chance to be downloaded by the organisation.
software installed in it. Biggest concern must be given to the networks tend the systems that
are used remotely.
The organisation must look up to the anti-virus software so that it is always updated,
because if the anti-virus software gets outdated it becomes easier for the attackers to attack on
the network.
The organisation must always employ a reputed firewall in the network of the
organisation, because the firewall helps to block any type of unwanted traffic form getting
entered into the network of the organisation. It also protect the gateway of the electronic
transaction any blocks all the outsiders from entering the network (Scott-Hayward,
O'Callaghan and Sezer 2013). The firewall is more important for the organisation because
they are very useful for wireless connections and this is the organisation which is totally
dependent on wireless network.
All traffic of the email must be filtered because the hacker discussed in the topic
mainly focuses on the emails to attack on their target. Thus all of the incoming emails and the
outgoing emails must be filtered and must be checked if there are any viruses attached in the
emails. Even if the emails are coming from any known sources then also they should be
checked as they may attach any link with the mail and by clicking on this it may lead to a
computer virus attack.
The downloads that are done form the internet network must be scanned because there
can be lot of virus which may enter the system or the network form the internet downloads
(Wang 2014). The hackers intentionally attack virus to different files that are available in the
internet for downloads and they may intentionally attach this viruses to the specific files
which have high chance to be downloaded by the organisation.

8SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
The organisation should also implement a policy of security which will help the
organisation to maintain certain terms and rules regarding their security issue of the
organisation (Fung, Molico and Stuber 2014). All the employees of the organisation must be
aware of the policies who are connected with the network server of the organisation, and
whenever they find any vulnerability in the network or in the system they will instantly block
take certain steps to stop the vulnerability and will be able to protect the organisation form
getting attacked by any hacker.
This are the mentioned solutions that will help the organisation from getting an attack
from the hackers (Stone and Dulebohn 2013). As the organisation is totally dependent on
electronic transactions it becomes very riskier for the organisation that they can be attacked
any time by the attackers. The proposed solution beside of saving the organisation from the
attackers will also help the organisation form getting loss of data uncertainly (Alqahtani, Al‐
Badi and Mayhew 2014). This are the ways that can be followed to save the organisation
form the hackers form duplicating their products and also from stealing while in an ongoing
electronic transaction.
Conclusion
The above report describes a clear structure about the Comodo certificate fraud hack
then after it is described about the organisation named Shopmatic. After the discussion it is
also described about all type of IT related security issues which may cause harm to any type
of computer systems and to the network. There are also numerous security issues of the
organisation Shopmatic which makes easier for the hackers to attack on the systems and on
the network of the organisation. There are certain issues regarding the security of the
organisation that includes the attack of various type of virus in the organisation. In the last of
the discussion there are enough solutions that are provided to secure the organisation from
The organisation should also implement a policy of security which will help the
organisation to maintain certain terms and rules regarding their security issue of the
organisation (Fung, Molico and Stuber 2014). All the employees of the organisation must be
aware of the policies who are connected with the network server of the organisation, and
whenever they find any vulnerability in the network or in the system they will instantly block
take certain steps to stop the vulnerability and will be able to protect the organisation form
getting attacked by any hacker.
This are the mentioned solutions that will help the organisation from getting an attack
from the hackers (Stone and Dulebohn 2013). As the organisation is totally dependent on
electronic transactions it becomes very riskier for the organisation that they can be attacked
any time by the attackers. The proposed solution beside of saving the organisation from the
attackers will also help the organisation form getting loss of data uncertainly (Alqahtani, Al‐
Badi and Mayhew 2014). This are the ways that can be followed to save the organisation
form the hackers form duplicating their products and also from stealing while in an ongoing
electronic transaction.
Conclusion
The above report describes a clear structure about the Comodo certificate fraud hack
then after it is described about the organisation named Shopmatic. After the discussion it is
also described about all type of IT related security issues which may cause harm to any type
of computer systems and to the network. There are also numerous security issues of the
organisation Shopmatic which makes easier for the hackers to attack on the systems and on
the network of the organisation. There are certain issues regarding the security of the
organisation that includes the attack of various type of virus in the organisation. In the last of
the discussion there are enough solutions that are provided to secure the organisation from

9SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
any such vulnerable attacks. This may include installation of antitheft software and
installation of firewall to secure the network.
Recommendation
There can be numerous number actions which can be implemented in the organisation to
avoid this type of vulnerable situations caused by the organisation:
Anti-Virus Software installation: The organisation should install reputed anti-virus
software’s in their systems to avoid entering of various viruses.
Incident response plan: The organisation should make certain response plans which
can be implemented during the time of certain incident occurrence.
End user access restrictions: The end users must not be allowed to have access to the
systems of the organisations.
Monitoring logs and monitoring systems: A regular monitoring must be done in the
systems and on the logs to detect if there are any unhealthy situations or not.
Security policy of information’s: A security policy must be created which will help to
secure the information’s related to the organisation.
Scanning of the internet downloads: The downloaded files from the internet must
always be scanned as internet is an open source and any type of malwares can be
present in the internet.
any such vulnerable attacks. This may include installation of antitheft software and
installation of firewall to secure the network.
Recommendation
There can be numerous number actions which can be implemented in the organisation to
avoid this type of vulnerable situations caused by the organisation:
Anti-Virus Software installation: The organisation should install reputed anti-virus
software’s in their systems to avoid entering of various viruses.
Incident response plan: The organisation should make certain response plans which
can be implemented during the time of certain incident occurrence.
End user access restrictions: The end users must not be allowed to have access to the
systems of the organisations.
Monitoring logs and monitoring systems: A regular monitoring must be done in the
systems and on the logs to detect if there are any unhealthy situations or not.
Security policy of information’s: A security policy must be created which will help to
secure the information’s related to the organisation.
Scanning of the internet downloads: The downloaded files from the internet must
always be scanned as internet is an open source and any type of malwares can be
present in the internet.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
Reference:
Ahmed, M. and Hossain, M.A., 2014. Cloud computing and security issues in the cloud.
International Journal of Network Security & Its Applications, 6(1), p.25.
Alqahtani, M.A., Al Badi, A.H. and Mayhew, P.J., 2014. Exploratory Study of M‐ ‐
Transaction: User's Perspectives. The Electronic Journal of Information Systems in
Developing Countries, 60(1), pp.1-22.
Borgohain, T., Kumar, U. and Sanyal, S., 2015. Survey of security and privacy issues of
internet of things. arXiv preprint arXiv:1501.02211.
Fennelly, L., 2016. Effective physical security. Butterworth-Heinemann.
Fung, B., Molico, M. and Stuber, G., 2014. Electronic money and payments: Recent
developments and issues (No. 2014-2). Bank of Canada Discussion Paper.
goshopmatic (2019). Create an Online Store | eCommerce Website Builder - Shopmatic.
[online] goshopmatic.com.
Kang, J.J., Fahd, K. and Venkatraman, S., 2018. Trusted Time-Based Verification Model for
Automatic Man-in-the-Middle Attack Detection in Cybersecurity. Cryptography, 2(4), p.38.
Pathan, A.S.K. ed., 2016. Security of self-organizing networks: MANET, WSN, WMN,
VANET. CRC press.
Roosa, S.B. and Schultze, S., 2013. Trust darknet: Control and compromise in the internet's
certificate authority model. IEEE Internet Computing, 17(3), pp.18-25.
Scott-Hayward, S., O'Callaghan, G. and Sezer, S., 2013, November. SDN security: A survey.
In 2013 IEEE SDN For Future Networks and Services (SDN4FNS) (pp. 1-7). IEEE.
Reference:
Ahmed, M. and Hossain, M.A., 2014. Cloud computing and security issues in the cloud.
International Journal of Network Security & Its Applications, 6(1), p.25.
Alqahtani, M.A., Al Badi, A.H. and Mayhew, P.J., 2014. Exploratory Study of M‐ ‐
Transaction: User's Perspectives. The Electronic Journal of Information Systems in
Developing Countries, 60(1), pp.1-22.
Borgohain, T., Kumar, U. and Sanyal, S., 2015. Survey of security and privacy issues of
internet of things. arXiv preprint arXiv:1501.02211.
Fennelly, L., 2016. Effective physical security. Butterworth-Heinemann.
Fung, B., Molico, M. and Stuber, G., 2014. Electronic money and payments: Recent
developments and issues (No. 2014-2). Bank of Canada Discussion Paper.
goshopmatic (2019). Create an Online Store | eCommerce Website Builder - Shopmatic.
[online] goshopmatic.com.
Kang, J.J., Fahd, K. and Venkatraman, S., 2018. Trusted Time-Based Verification Model for
Automatic Man-in-the-Middle Attack Detection in Cybersecurity. Cryptography, 2(4), p.38.
Pathan, A.S.K. ed., 2016. Security of self-organizing networks: MANET, WSN, WMN,
VANET. CRC press.
Roosa, S.B. and Schultze, S., 2013. Trust darknet: Control and compromise in the internet's
certificate authority model. IEEE Internet Computing, 17(3), pp.18-25.
Scott-Hayward, S., O'Callaghan, G. and Sezer, S., 2013, November. SDN security: A survey.
In 2013 IEEE SDN For Future Networks and Services (SDN4FNS) (pp. 1-7). IEEE.

11SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
Sen, J., 2015. Security and privacy issues in cloud computing. In Cloud Technology:
Concepts, Methodologies, Tools, and Applications (pp. 1585-1630). IGI Global.
Specter, M.A., 2016. The economics of cryptographic trust: understanding certificate
authorities (Doctoral dissertation, Massachusetts Institute of Technology).
Stojmenovic, I. and Wen, S., 2014, September. The fog computing paradigm: Scenarios and
security issues. In 2014 Federated Conference on Computer Science and Information Systems
(pp. 1-8). IEEE.
Stone, D.L. and Dulebohn, J.H., 2013. Emerging issues in theory and research on electronic
human resource management (eHRM).
Wang, B., Zheng, Y., Lou, W. and Hou, Y.T., 2015. DDoS attack protection in the era of
cloud computing and software-defined networking. Computer Networks, 81, pp.308-319.
Wang, F.F., 2014. Law of electronic commercial transactions: Contemporary issues in the
EU, US and China. Routledge.
Sen, J., 2015. Security and privacy issues in cloud computing. In Cloud Technology:
Concepts, Methodologies, Tools, and Applications (pp. 1585-1630). IGI Global.
Specter, M.A., 2016. The economics of cryptographic trust: understanding certificate
authorities (Doctoral dissertation, Massachusetts Institute of Technology).
Stojmenovic, I. and Wen, S., 2014, September. The fog computing paradigm: Scenarios and
security issues. In 2014 Federated Conference on Computer Science and Information Systems
(pp. 1-8). IEEE.
Stone, D.L. and Dulebohn, J.H., 2013. Emerging issues in theory and research on electronic
human resource management (eHRM).
Wang, B., Zheng, Y., Lou, W. and Hou, Y.T., 2015. DDoS attack protection in the era of
cloud computing and software-defined networking. Computer Networks, 81, pp.308-319.
Wang, F.F., 2014. Law of electronic commercial transactions: Contemporary issues in the
EU, US and China. Routledge.
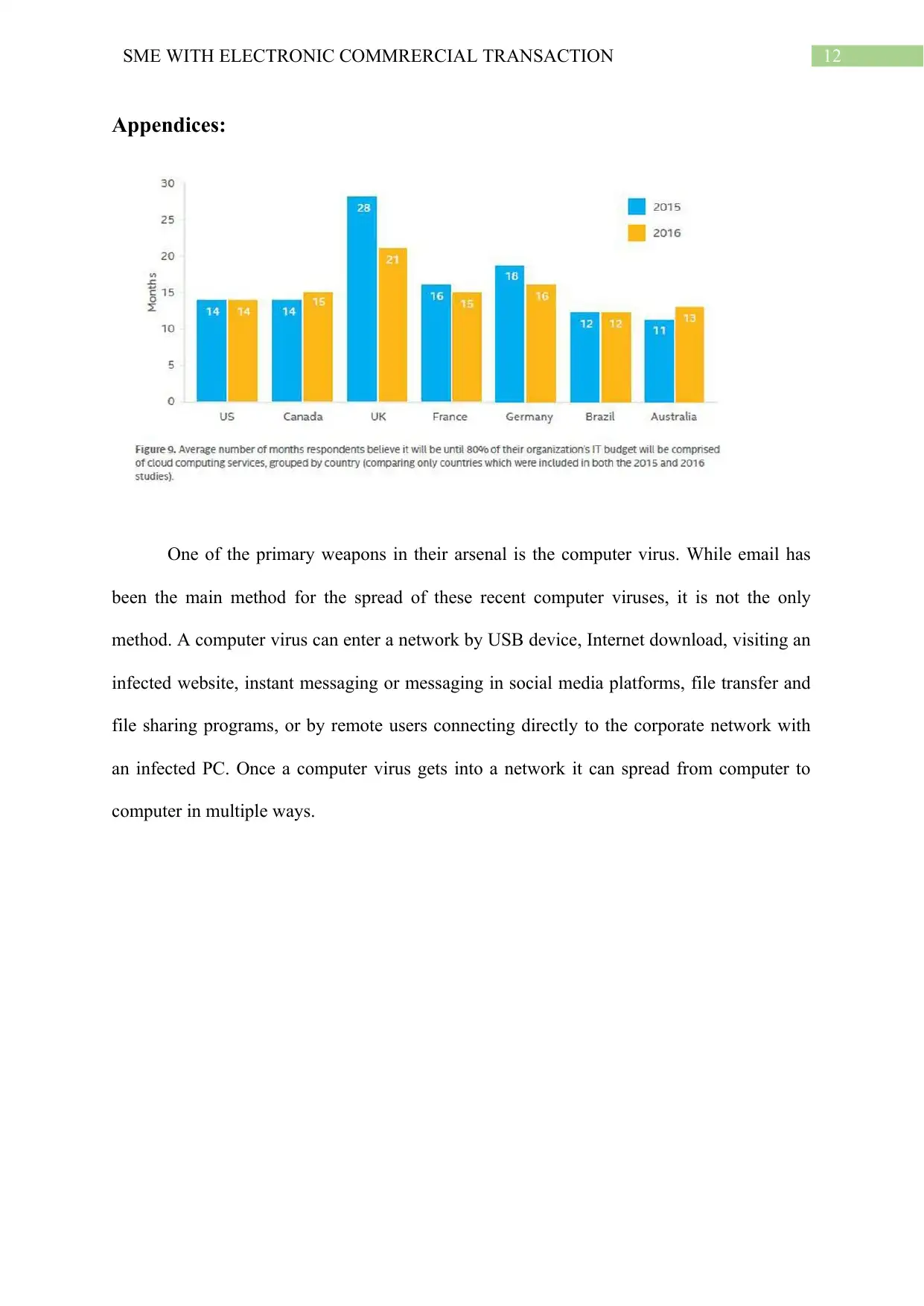
12SME WITH ELECTRONIC COMMRERCIAL TRANSACTION
Appendices:
One of the primary weapons in their arsenal is the computer virus. While email has
been the main method for the spread of these recent computer viruses, it is not the only
method. A computer virus can enter a network by USB device, Internet download, visiting an
infected website, instant messaging or messaging in social media platforms, file transfer and
file sharing programs, or by remote users connecting directly to the corporate network with
an infected PC. Once a computer virus gets into a network it can spread from computer to
computer in multiple ways.
Appendices:
One of the primary weapons in their arsenal is the computer virus. While email has
been the main method for the spread of these recent computer viruses, it is not the only
method. A computer virus can enter a network by USB device, Internet download, visiting an
infected website, instant messaging or messaging in social media platforms, file transfer and
file sharing programs, or by remote users connecting directly to the corporate network with
an infected PC. Once a computer virus gets into a network it can spread from computer to
computer in multiple ways.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




