Dark Web and Cybercrime: An Analysis of Theoretical and Cross-Disciplinary Approaches
VerifiedAdded on 2023/02/01
|9
|2898
|28
AI Summary
This article analyzes the differences between theoretical and cross-disciplinary approaches to the dark web and explores the various forms of cybercrime, technologies, and social engineering methods used on the dark web. It also discusses the behavior of offenders and victims, as well as the impact of cybercrime and mitigating techniques.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Social engineering
Name
Institution
Professor
Course
Date
Name
Institution
Professor
Course
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Introduction
The dark web is known to be the anonymous part of the internet information that cannot
be searched with conventional search engines. To access the dark web content, internet users are
required to anonymize their search engine on the TOR browsers (Hardy & Norgaard, 2016). The
TOR browser works uniquely in such a way that it routes user’s requests through an
interconnection of proxy servers. The servers hosting the dark web content are spread across the
globe but are untraceable as they render specific IP address from TOR users unidentifiable. It is
often difficult to search through the dark web and come up with a reliable source of information
because the information landscape keeps changing. As much as dark web might be regarded as
dangerous and illegal, it cannot be entirely subjected to be unlawful social engineering activities
because it has been used in countries where the internet is not allowed. Experienced users’ uses
dark web, some advanced social engineering techniques such as phishing, eavesdropping and
hacking to retrieve and pass sensitive information. This article focuses on notable differences
between both theoretical and available cross-disciplinary approaches regarding the dark web
(Spalevic & Ilic, 2017). Since there are many cybercriminal activities taking place through the
dark web, an evaluation of dark web forms of cybercriminals, technologies and social
engineering methods facilitating such events would be analyzed. The behavior of both dark web
cybercriminals and victims, the cybercrime assessment and mitigation techniques that can be
used to prevent crimes committed through the dark web. Therefore, this study is critical because
it would help in understanding the obscure web concepts and technologies used to facilitate dark
web cybercrime, making it possible to mitigate some of its impacts.
The dark web is known to be the anonymous part of the internet information that cannot
be searched with conventional search engines. To access the dark web content, internet users are
required to anonymize their search engine on the TOR browsers (Hardy & Norgaard, 2016). The
TOR browser works uniquely in such a way that it routes user’s requests through an
interconnection of proxy servers. The servers hosting the dark web content are spread across the
globe but are untraceable as they render specific IP address from TOR users unidentifiable. It is
often difficult to search through the dark web and come up with a reliable source of information
because the information landscape keeps changing. As much as dark web might be regarded as
dangerous and illegal, it cannot be entirely subjected to be unlawful social engineering activities
because it has been used in countries where the internet is not allowed. Experienced users’ uses
dark web, some advanced social engineering techniques such as phishing, eavesdropping and
hacking to retrieve and pass sensitive information. This article focuses on notable differences
between both theoretical and available cross-disciplinary approaches regarding the dark web
(Spalevic & Ilic, 2017). Since there are many cybercriminal activities taking place through the
dark web, an evaluation of dark web forms of cybercriminals, technologies and social
engineering methods facilitating such events would be analyzed. The behavior of both dark web
cybercriminals and victims, the cybercrime assessment and mitigation techniques that can be
used to prevent crimes committed through the dark web. Therefore, this study is critical because
it would help in understanding the obscure web concepts and technologies used to facilitate dark
web cybercrime, making it possible to mitigate some of its impacts.
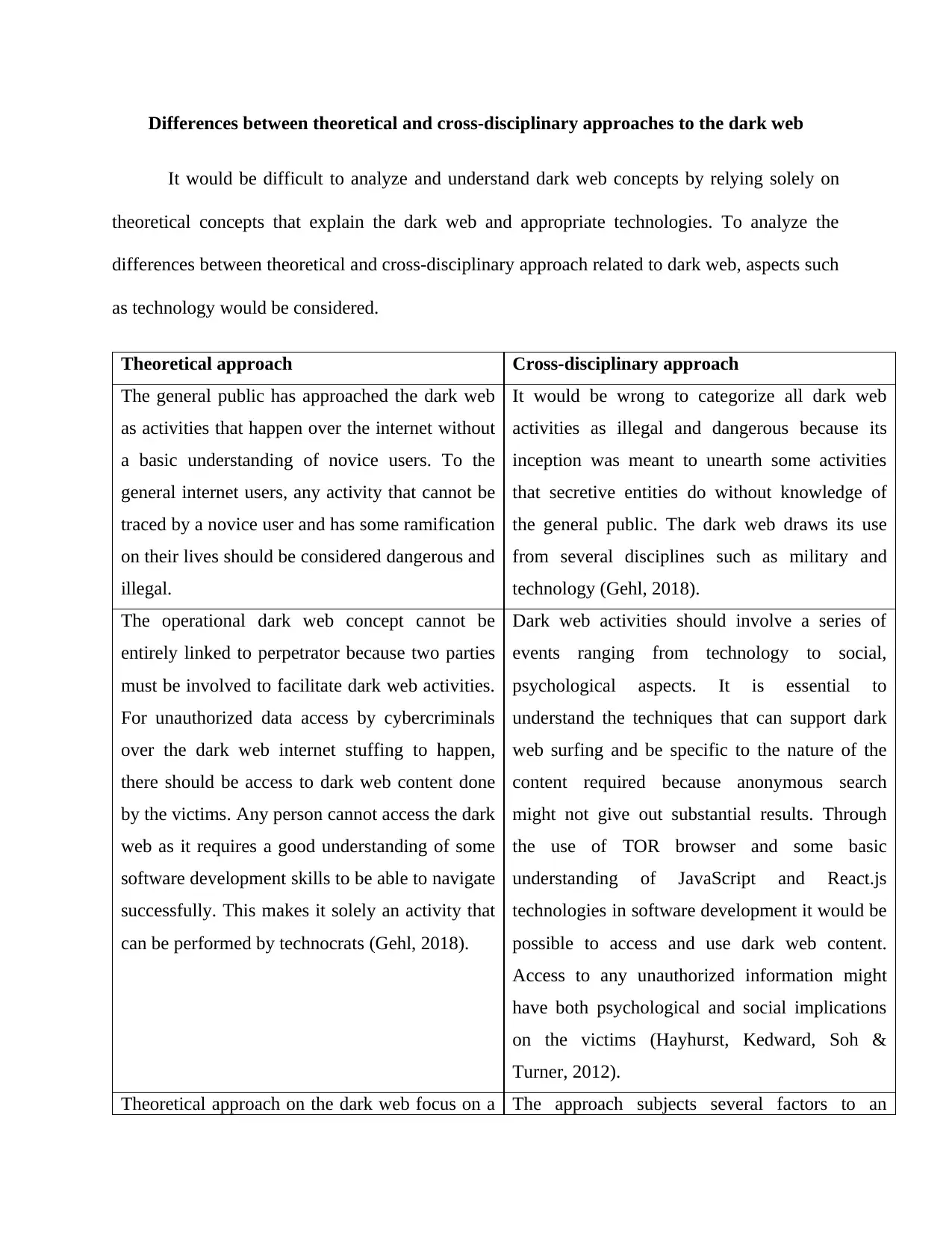
Differences between theoretical and cross-disciplinary approaches to the dark web
It would be difficult to analyze and understand dark web concepts by relying solely on
theoretical concepts that explain the dark web and appropriate technologies. To analyze the
differences between theoretical and cross-disciplinary approach related to dark web, aspects such
as technology would be considered.
Theoretical approach Cross-disciplinary approach
The general public has approached the dark web
as activities that happen over the internet without
a basic understanding of novice users. To the
general internet users, any activity that cannot be
traced by a novice user and has some ramification
on their lives should be considered dangerous and
illegal.
It would be wrong to categorize all dark web
activities as illegal and dangerous because its
inception was meant to unearth some activities
that secretive entities do without knowledge of
the general public. The dark web draws its use
from several disciplines such as military and
technology (Gehl, 2018).
The operational dark web concept cannot be
entirely linked to perpetrator because two parties
must be involved to facilitate dark web activities.
For unauthorized data access by cybercriminals
over the dark web internet stuffing to happen,
there should be access to dark web content done
by the victims. Any person cannot access the dark
web as it requires a good understanding of some
software development skills to be able to navigate
successfully. This makes it solely an activity that
can be performed by technocrats (Gehl, 2018).
Dark web activities should involve a series of
events ranging from technology to social,
psychological aspects. It is essential to
understand the techniques that can support dark
web surfing and be specific to the nature of the
content required because anonymous search
might not give out substantial results. Through
the use of TOR browser and some basic
understanding of JavaScript and React.js
technologies in software development it would be
possible to access and use dark web content.
Access to any unauthorized information might
have both psychological and social implications
on the victims (Hayhurst, Kedward, Soh &
Turner, 2012).
Theoretical approach on the dark web focus on a The approach subjects several factors to an
It would be difficult to analyze and understand dark web concepts by relying solely on
theoretical concepts that explain the dark web and appropriate technologies. To analyze the
differences between theoretical and cross-disciplinary approach related to dark web, aspects such
as technology would be considered.
Theoretical approach Cross-disciplinary approach
The general public has approached the dark web
as activities that happen over the internet without
a basic understanding of novice users. To the
general internet users, any activity that cannot be
traced by a novice user and has some ramification
on their lives should be considered dangerous and
illegal.
It would be wrong to categorize all dark web
activities as illegal and dangerous because its
inception was meant to unearth some activities
that secretive entities do without knowledge of
the general public. The dark web draws its use
from several disciplines such as military and
technology (Gehl, 2018).
The operational dark web concept cannot be
entirely linked to perpetrator because two parties
must be involved to facilitate dark web activities.
For unauthorized data access by cybercriminals
over the dark web internet stuffing to happen,
there should be access to dark web content done
by the victims. Any person cannot access the dark
web as it requires a good understanding of some
software development skills to be able to navigate
successfully. This makes it solely an activity that
can be performed by technocrats (Gehl, 2018).
Dark web activities should involve a series of
events ranging from technology to social,
psychological aspects. It is essential to
understand the techniques that can support dark
web surfing and be specific to the nature of the
content required because anonymous search
might not give out substantial results. Through
the use of TOR browser and some basic
understanding of JavaScript and React.js
technologies in software development it would be
possible to access and use dark web content.
Access to any unauthorized information might
have both psychological and social implications
on the victims (Hayhurst, Kedward, Soh &
Turner, 2012).
Theoretical approach on the dark web focus on a The approach subjects several factors to an

single aspect and the effects caused by the dark
web. In this case, cybercrime over the dark web
might be viewed as typical hacking to an
information system involving an instance such as
password retrieval through various activities.
occurrence of activity over the dark web. The
cybercriminal should use some simple social
engineering practices to get some necessary
information about the target system or data. Once
social activities are applied, technological
mechanisms should be applied to extract the data
or compromise the target system. Since all events
would be done over the dark web, it would not be
possible to uncover the cybercriminal (Ehney &
Shorter, 2016).
Cybercriminal activities, technological and social engineering methods on the dark web
There are different forms of cybercriminals that have been happening over the dark web
and remain unnoticed because it has not been accessible to everyone. Hacking has a large
percentage of cybercrime that is committed over the dark web. The criminals have preferred it
because it is not possible to detect the criminal neither the location it was done from. According
to Lacson & Jones (2016), hackers have been using social engineering practices such as
password snooping and IP address to get some of the sensitive data. Once they get the data,
hacking activities are turned into a complex chain of internet activities performed over the dark
web. Since the users of the dark web remain anonymous, it has been possible to commit
cybercrime activities and stay unnoticed. Through the use of TOR browser, hackers have been
able to sabotage the system and create a Distributed Reflection Denial of services (Uma &
Padmavathi, 2013). To advance hacking activities, dark web criminals have established some
websites which have some useful download that is infected with some malware. Once the
software has been installed, it creates access to the system which can be accessed by the
web. In this case, cybercrime over the dark web
might be viewed as typical hacking to an
information system involving an instance such as
password retrieval through various activities.
occurrence of activity over the dark web. The
cybercriminal should use some simple social
engineering practices to get some necessary
information about the target system or data. Once
social activities are applied, technological
mechanisms should be applied to extract the data
or compromise the target system. Since all events
would be done over the dark web, it would not be
possible to uncover the cybercriminal (Ehney &
Shorter, 2016).
Cybercriminal activities, technological and social engineering methods on the dark web
There are different forms of cybercriminals that have been happening over the dark web
and remain unnoticed because it has not been accessible to everyone. Hacking has a large
percentage of cybercrime that is committed over the dark web. The criminals have preferred it
because it is not possible to detect the criminal neither the location it was done from. According
to Lacson & Jones (2016), hackers have been using social engineering practices such as
password snooping and IP address to get some of the sensitive data. Once they get the data,
hacking activities are turned into a complex chain of internet activities performed over the dark
web. Since the users of the dark web remain anonymous, it has been possible to commit
cybercrime activities and stay unnoticed. Through the use of TOR browser, hackers have been
able to sabotage the system and create a Distributed Reflection Denial of services (Uma &
Padmavathi, 2013). To advance hacking activities, dark web criminals have established some
websites which have some useful download that is infected with some malware. Once the
software has been installed, it creates access to the system which can be accessed by the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

criminals through the dark web and extract either personal or organizational valuable data. Next,
phishing as one of the most used social engineering techniques is used to create duplicate
websites which are advertised with fraudulent URLs to attract internet users (Alyami & Assiri,
2018). Once the user visits the URL, passwords are collected by the hacker’s fraudulent website
and stored on their database. The criminal has all opportunities of using the password to create a
denial of service to authorized users by taking control of the system.
Similarly, with terrorist taking the new shape of using the internet to advance their
mission, the dark web remains a tool that might cause mayhem due to its ability to hide audit
trace. Through the dark web, terrorist can communicate freely without any fear of identification
(Raghavan & Parthiban, 2014). It has been used to bypass information censure where
eavesdropping by state governments’ remains a norm. In this regard, terrorists can make use of
the technology to advance their activities such as radicalization and planning for attacks without
being detected. It is evident that there are some dark websites which terrorist groups such as ISIS
have been using to flourish due to weakness in the technology. Such incidents can be attributed
to the 2015 Paris terrorist attacks was found to be running a series of activities over the dark
web. On the same note, many state governments have banned some contents such as drugs,
pornographic materials and open social media platforms such as Facebook. In such instances,
criminals have found their way through the use of the dark web to facilitate any form of illegal
business in what is known as darknet markets. With the dark web, it has been possible for drug
dealers to trade and propagate the news with any form of fear. Such websites are difficult to
control through censure mechanisms since they are only known to a group of well-orchestrated
individuals. Such sites are only known to specific individuals believed to be operating
phishing as one of the most used social engineering techniques is used to create duplicate
websites which are advertised with fraudulent URLs to attract internet users (Alyami & Assiri,
2018). Once the user visits the URL, passwords are collected by the hacker’s fraudulent website
and stored on their database. The criminal has all opportunities of using the password to create a
denial of service to authorized users by taking control of the system.
Similarly, with terrorist taking the new shape of using the internet to advance their
mission, the dark web remains a tool that might cause mayhem due to its ability to hide audit
trace. Through the dark web, terrorist can communicate freely without any fear of identification
(Raghavan & Parthiban, 2014). It has been used to bypass information censure where
eavesdropping by state governments’ remains a norm. In this regard, terrorists can make use of
the technology to advance their activities such as radicalization and planning for attacks without
being detected. It is evident that there are some dark websites which terrorist groups such as ISIS
have been using to flourish due to weakness in the technology. Such incidents can be attributed
to the 2015 Paris terrorist attacks was found to be running a series of activities over the dark
web. On the same note, many state governments have banned some contents such as drugs,
pornographic materials and open social media platforms such as Facebook. In such instances,
criminals have found their way through the use of the dark web to facilitate any form of illegal
business in what is known as darknet markets. With the dark web, it has been possible for drug
dealers to trade and propagate the news with any form of fear. Such websites are difficult to
control through censure mechanisms since they are only known to a group of well-orchestrated
individuals. Such sites are only known to specific individuals believed to be operating

susceptible businesses which are termed illegal by state governments (Ajayi, 2016). Therefore,
technology is a tool in cybercrime through the use of dark webs.
Assumptions about the behavior and role of offenders and victims in the dark web
Considering all activities in the darknet market are done by cybercriminals with the aim
of causing some operational disrupting in cases of hacking, both the offender and the victim
should exhibit some characteristics. First, the offender through the dark web should be a high-
tech surf with an in-depth understanding of the social engineering and hacking process. In most
cases, the victim should be a novice user with no technical skills to protect personal information
while on internet electronic business operations (Buchanan, Dyson & Bell, 2018). This makes
the victim a soft target by the criminals since they cannot understand some of the complex
operations required to secure personal data. In cybercriminal activities, offenders are always
focused on sensitive retrieval of data and holding it in exchange for money. A good example can
be highlighted from the recent GitHub hacking where hackers gained access to some GitHub
accounts, deleted the data and threatened to publish all the codes if the owners do not pay
ransoms in the form of Bitcoins. To avoid such scenarios, victims are required to make sure all
personal information is securely stored online by submitting to only genuine and verified
websites. Once the cybercrime has happened, the victim focus is to gain back access to any data
held hostage by the offender. Depending on the nature of the data, the victim might be tempted
to pay the criminal in exchange for the data held by the criminal (Chitrey, Singh & Singh, 2012).
Once the victim realizes the concept behind the cybercriminal, it is possible would be tempted to
try all reasonable technological measures to gain access to the compromised data. On the same
note, the victim might end up training to be a hacker in revenge of cybercrime activities. In cases
technology is a tool in cybercrime through the use of dark webs.
Assumptions about the behavior and role of offenders and victims in the dark web
Considering all activities in the darknet market are done by cybercriminals with the aim
of causing some operational disrupting in cases of hacking, both the offender and the victim
should exhibit some characteristics. First, the offender through the dark web should be a high-
tech surf with an in-depth understanding of the social engineering and hacking process. In most
cases, the victim should be a novice user with no technical skills to protect personal information
while on internet electronic business operations (Buchanan, Dyson & Bell, 2018). This makes
the victim a soft target by the criminals since they cannot understand some of the complex
operations required to secure personal data. In cybercriminal activities, offenders are always
focused on sensitive retrieval of data and holding it in exchange for money. A good example can
be highlighted from the recent GitHub hacking where hackers gained access to some GitHub
accounts, deleted the data and threatened to publish all the codes if the owners do not pay
ransoms in the form of Bitcoins. To avoid such scenarios, victims are required to make sure all
personal information is securely stored online by submitting to only genuine and verified
websites. Once the cybercrime has happened, the victim focus is to gain back access to any data
held hostage by the offender. Depending on the nature of the data, the victim might be tempted
to pay the criminal in exchange for the data held by the criminal (Chitrey, Singh & Singh, 2012).
Once the victim realizes the concept behind the cybercriminal, it is possible would be tempted to
try all reasonable technological measures to gain access to the compromised data. On the same
note, the victim might end up training to be a hacker in revenge of cybercrime activities. In cases

where the victim is a government entity, it is upon the government to formulate rules and
regulations to protect all other entities from such heinous events.
Impact of cybercrime and mitigating techniques against cybercrime
Cybercrime has a severe impact on various entities that are involved and mainly the
victims. Hacking into an organizational database might result in denial of service, data
corruption, and data leakage. Both denial of service and data corruption disrupts corporate
process if they rely on data for business processes (Bhardwaj, Avasthi, Sastry & Subrahmanyam,
2016). Hacking dominates service industry because it depends on data on service delivery as
well as decision-making. In this case, it would be disastrous to an organization to lose its data or
being unable to access it for sound business decision making. The affected organization might
lose its customers to competitors' believed to have suitable data security mechanism in fear of
falling victim of cybercriminal activities. In such instances, the affected organization may
experience profit margin drop which in turn affect overall economic performance. Besides,
cybercrime on terrorism has been observed to be quite catastrophic as it has been resulting in the
death of innocent people. When attacks coordinated over the dark web happens, they lead in
death and destruction of property worth billions of dollars. Such attacks cause a sharp decline in
the economic growth of the affected country. Important to note is that there are several
techniques which can be used to prevent cybercrime. First, training system users on data security
measures such as data encryption and using only official websites (Broadhurst, Grabosky,
Alazab, Bouhours & Chon, 2014). The next aspect is creating awareness of the most cybercrime
activities that internet users should be wary of. Finally, state government and international
community formulating international rules and regulations to govern cybercrime.
regulations to protect all other entities from such heinous events.
Impact of cybercrime and mitigating techniques against cybercrime
Cybercrime has a severe impact on various entities that are involved and mainly the
victims. Hacking into an organizational database might result in denial of service, data
corruption, and data leakage. Both denial of service and data corruption disrupts corporate
process if they rely on data for business processes (Bhardwaj, Avasthi, Sastry & Subrahmanyam,
2016). Hacking dominates service industry because it depends on data on service delivery as
well as decision-making. In this case, it would be disastrous to an organization to lose its data or
being unable to access it for sound business decision making. The affected organization might
lose its customers to competitors' believed to have suitable data security mechanism in fear of
falling victim of cybercriminal activities. In such instances, the affected organization may
experience profit margin drop which in turn affect overall economic performance. Besides,
cybercrime on terrorism has been observed to be quite catastrophic as it has been resulting in the
death of innocent people. When attacks coordinated over the dark web happens, they lead in
death and destruction of property worth billions of dollars. Such attacks cause a sharp decline in
the economic growth of the affected country. Important to note is that there are several
techniques which can be used to prevent cybercrime. First, training system users on data security
measures such as data encryption and using only official websites (Broadhurst, Grabosky,
Alazab, Bouhours & Chon, 2014). The next aspect is creating awareness of the most cybercrime
activities that internet users should be wary of. Finally, state government and international
community formulating international rules and regulations to govern cybercrime.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
Cybercrime has been associated with many technological mechanisms that make it
challenging to eliminate cybercrime activities. As technology makes its advancement,
cybercrime activities would also continue to advance. With the innovation of dark web for only
sensitive state government activities, it has been turned to be a weapon in the technology market.
Dark market has been used several cybercrime activities such as drug trafficking, terrorist
activities and hacking among others. With different approaches in the dark web, it would be
essential to consider it from a broad multi-disciplinary point of view. Cybercriminal should be
regarded as a global issue which should be resolved by the international community. Some of the
cybercrimes such as terrorism, hacking and malware infection need internationally set
regulations to be able to control massive crimes. It is also essential for individuals to be aware of
some of the methodologies and techniques being used to gain access to their systems without
their knowledge. Therefore, dark web activities should be taken seriously because they are
hidden from normal monitoring aspects and can be used a tool to commit heinous crimes.
Cybercrime has been associated with many technological mechanisms that make it
challenging to eliminate cybercrime activities. As technology makes its advancement,
cybercrime activities would also continue to advance. With the innovation of dark web for only
sensitive state government activities, it has been turned to be a weapon in the technology market.
Dark market has been used several cybercrime activities such as drug trafficking, terrorist
activities and hacking among others. With different approaches in the dark web, it would be
essential to consider it from a broad multi-disciplinary point of view. Cybercriminal should be
regarded as a global issue which should be resolved by the international community. Some of the
cybercrimes such as terrorism, hacking and malware infection need internationally set
regulations to be able to control massive crimes. It is also essential for individuals to be aware of
some of the methodologies and techniques being used to gain access to their systems without
their knowledge. Therefore, dark web activities should be taken seriously because they are
hidden from normal monitoring aspects and can be used a tool to commit heinous crimes.

References
Ajayi, E. F. G. (2016). Challenges to the enforcement of cyber-crimes laws and policy. Journal
of Internet and Information Systems, 6(1), 1-12.
Alyami, H. Y., & Assiri, E. A. (2018). Invisible Web and Academic Research: A Partnership for
Quality. International Education Studies, 11(4), 84-91.
Bhardwaj, A., Avasthi, V., Sastry, H., & Subrahmanyam, G. V. B. (2016). Ransomware digital
extortion: a rising new age threat. Indian Journal of Science and Technology, 9(14), 1- 5.
Broadhurst, R., Grabosky, P., Alazab, M., Bouhours, B., & Chon, S. (2014). An analysis of the
nature of groups engaged in cybercrime. An Analysis of the Nature of Groups
engaged in Cyber Crime, International Journal of Cyber Criminology, 8(1), 1-20.
Buchanan, W., Dyson, S., & Bell, L. (2018). The Challenges of Investigating Cryptocurrencies
and Blockchain Related Crime. The JBBA, 1(2), pp. 1-5.
Chitrey, A., Singh, D., & Singh, V. (2012). A comprehensive study of social engineering based
attacks in India to develop a conceptual model. International Journal of Information
and Network Security, 1(2), 45-52.
Ehney, R., & Shorter, J. D. (2016). Deep web, dark web, invisible web, and the post isis
world. Issues in Information Systems, 17(4), 3-47.
Gehl, R. W. (2018). Archives for the Dark Web: A Field Guide for Study. In Research Methods
for the Digital Humanities (pp. 31-51).
Hardy, R. A., & Norgaard, J. R. (2016). Reputation in the Internet black market: an empirical
and theoretical analysis of the Deep Web. Journal of Institutional Economics, 12(3), 515-539.
Hayhurst, D. R., Kedward, K. T., Soh, H. T., & Turner, K. L. (2012). Innovation-led
multidisciplinary undergraduate design teaching. Journal of Engineering Design, 23(3),
159- 184.
Lacson, W., & Jones, B. (2016). The 21st Century Darknet Market: Lessons from the fall of Silk
Road. International Journal of Cyber Criminology, 10(1), pp. 40-60.
Raghavan, A. R., & Parthiban, L. (2014). The effect of cybercrime on a Bank's
finances. International Journal of Current Research & Academic Review, 2(2),
173- 178.
Spalevic, Z., & Ilic, M. (2017). The use of the dark web for the purpose of illegal activity
spreading. Ekonomika, 63(1), 73-79.
Uma, M., & Padmavathi, G. (2013). A Survey on Various Cyber Attacks and their
Classification. IJ Network Security, 15(5), 390-396.
Ajayi, E. F. G. (2016). Challenges to the enforcement of cyber-crimes laws and policy. Journal
of Internet and Information Systems, 6(1), 1-12.
Alyami, H. Y., & Assiri, E. A. (2018). Invisible Web and Academic Research: A Partnership for
Quality. International Education Studies, 11(4), 84-91.
Bhardwaj, A., Avasthi, V., Sastry, H., & Subrahmanyam, G. V. B. (2016). Ransomware digital
extortion: a rising new age threat. Indian Journal of Science and Technology, 9(14), 1- 5.
Broadhurst, R., Grabosky, P., Alazab, M., Bouhours, B., & Chon, S. (2014). An analysis of the
nature of groups engaged in cybercrime. An Analysis of the Nature of Groups
engaged in Cyber Crime, International Journal of Cyber Criminology, 8(1), 1-20.
Buchanan, W., Dyson, S., & Bell, L. (2018). The Challenges of Investigating Cryptocurrencies
and Blockchain Related Crime. The JBBA, 1(2), pp. 1-5.
Chitrey, A., Singh, D., & Singh, V. (2012). A comprehensive study of social engineering based
attacks in India to develop a conceptual model. International Journal of Information
and Network Security, 1(2), 45-52.
Ehney, R., & Shorter, J. D. (2016). Deep web, dark web, invisible web, and the post isis
world. Issues in Information Systems, 17(4), 3-47.
Gehl, R. W. (2018). Archives for the Dark Web: A Field Guide for Study. In Research Methods
for the Digital Humanities (pp. 31-51).
Hardy, R. A., & Norgaard, J. R. (2016). Reputation in the Internet black market: an empirical
and theoretical analysis of the Deep Web. Journal of Institutional Economics, 12(3), 515-539.
Hayhurst, D. R., Kedward, K. T., Soh, H. T., & Turner, K. L. (2012). Innovation-led
multidisciplinary undergraduate design teaching. Journal of Engineering Design, 23(3),
159- 184.
Lacson, W., & Jones, B. (2016). The 21st Century Darknet Market: Lessons from the fall of Silk
Road. International Journal of Cyber Criminology, 10(1), pp. 40-60.
Raghavan, A. R., & Parthiban, L. (2014). The effect of cybercrime on a Bank's
finances. International Journal of Current Research & Academic Review, 2(2),
173- 178.
Spalevic, Z., & Ilic, M. (2017). The use of the dark web for the purpose of illegal activity
spreading. Ekonomika, 63(1), 73-79.
Uma, M., & Padmavathi, G. (2013). A Survey on Various Cyber Attacks and their
Classification. IJ Network Security, 15(5), 390-396.
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




