Dark Web and Cybercrime: An Analysis of Theoretical and Cross-Disciplinary Approaches
Added on 2023-02-01
9 Pages2898 Words28 Views
Social engineering
Name
Institution
Professor
Course
Date
Name
Institution
Professor
Course
Date

Introduction
The dark web is known to be the anonymous part of the internet information that cannot
be searched with conventional search engines. To access the dark web content, internet users are
required to anonymize their search engine on the TOR browsers (Hardy & Norgaard, 2016). The
TOR browser works uniquely in such a way that it routes user’s requests through an
interconnection of proxy servers. The servers hosting the dark web content are spread across the
globe but are untraceable as they render specific IP address from TOR users unidentifiable. It is
often difficult to search through the dark web and come up with a reliable source of information
because the information landscape keeps changing. As much as dark web might be regarded as
dangerous and illegal, it cannot be entirely subjected to be unlawful social engineering activities
because it has been used in countries where the internet is not allowed. Experienced users’ uses
dark web, some advanced social engineering techniques such as phishing, eavesdropping and
hacking to retrieve and pass sensitive information. This article focuses on notable differences
between both theoretical and available cross-disciplinary approaches regarding the dark web
(Spalevic & Ilic, 2017). Since there are many cybercriminal activities taking place through the
dark web, an evaluation of dark web forms of cybercriminals, technologies and social
engineering methods facilitating such events would be analyzed. The behavior of both dark web
cybercriminals and victims, the cybercrime assessment and mitigation techniques that can be
used to prevent crimes committed through the dark web. Therefore, this study is critical because
it would help in understanding the obscure web concepts and technologies used to facilitate dark
web cybercrime, making it possible to mitigate some of its impacts.
The dark web is known to be the anonymous part of the internet information that cannot
be searched with conventional search engines. To access the dark web content, internet users are
required to anonymize their search engine on the TOR browsers (Hardy & Norgaard, 2016). The
TOR browser works uniquely in such a way that it routes user’s requests through an
interconnection of proxy servers. The servers hosting the dark web content are spread across the
globe but are untraceable as they render specific IP address from TOR users unidentifiable. It is
often difficult to search through the dark web and come up with a reliable source of information
because the information landscape keeps changing. As much as dark web might be regarded as
dangerous and illegal, it cannot be entirely subjected to be unlawful social engineering activities
because it has been used in countries where the internet is not allowed. Experienced users’ uses
dark web, some advanced social engineering techniques such as phishing, eavesdropping and
hacking to retrieve and pass sensitive information. This article focuses on notable differences
between both theoretical and available cross-disciplinary approaches regarding the dark web
(Spalevic & Ilic, 2017). Since there are many cybercriminal activities taking place through the
dark web, an evaluation of dark web forms of cybercriminals, technologies and social
engineering methods facilitating such events would be analyzed. The behavior of both dark web
cybercriminals and victims, the cybercrime assessment and mitigation techniques that can be
used to prevent crimes committed through the dark web. Therefore, this study is critical because
it would help in understanding the obscure web concepts and technologies used to facilitate dark
web cybercrime, making it possible to mitigate some of its impacts.

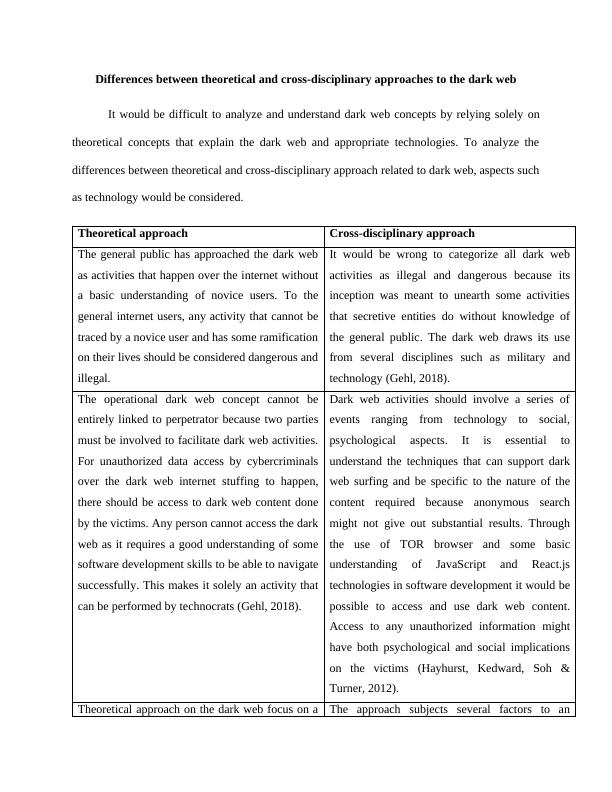
Differences between theoretical and cross-disciplinary approaches to the dark web
It would be difficult to analyze and understand dark web concepts by relying solely on
theoretical concepts that explain the dark web and appropriate technologies. To analyze the
differences between theoretical and cross-disciplinary approach related to dark web, aspects such
as technology would be considered.
Theoretical approach Cross-disciplinary approach
The general public has approached the dark web
as activities that happen over the internet without
a basic understanding of novice users. To the
general internet users, any activity that cannot be
traced by a novice user and has some ramification
on their lives should be considered dangerous and
illegal.
It would be wrong to categorize all dark web
activities as illegal and dangerous because its
inception was meant to unearth some activities
that secretive entities do without knowledge of
the general public. The dark web draws its use
from several disciplines such as military and
technology (Gehl, 2018).
The operational dark web concept cannot be
entirely linked to perpetrator because two parties
must be involved to facilitate dark web activities.
For unauthorized data access by cybercriminals
over the dark web internet stuffing to happen,
there should be access to dark web content done
by the victims. Any person cannot access the dark
web as it requires a good understanding of some
software development skills to be able to navigate
successfully. This makes it solely an activity that
can be performed by technocrats (Gehl, 2018).
Dark web activities should involve a series of
events ranging from technology to social,
psychological aspects. It is essential to
understand the techniques that can support dark
web surfing and be specific to the nature of the
content required because anonymous search
might not give out substantial results. Through
the use of TOR browser and some basic
understanding of JavaScript and React.js
technologies in software development it would be
possible to access and use dark web content.
Access to any unauthorized information might
have both psychological and social implications
on the victims (Hayhurst, Kedward, Soh &
Turner, 2012).
Theoretical approach on the dark web focus on a The approach subjects several factors to an
It would be difficult to analyze and understand dark web concepts by relying solely on
theoretical concepts that explain the dark web and appropriate technologies. To analyze the
differences between theoretical and cross-disciplinary approach related to dark web, aspects such
as technology would be considered.
Theoretical approach Cross-disciplinary approach
The general public has approached the dark web
as activities that happen over the internet without
a basic understanding of novice users. To the
general internet users, any activity that cannot be
traced by a novice user and has some ramification
on their lives should be considered dangerous and
illegal.
It would be wrong to categorize all dark web
activities as illegal and dangerous because its
inception was meant to unearth some activities
that secretive entities do without knowledge of
the general public. The dark web draws its use
from several disciplines such as military and
technology (Gehl, 2018).
The operational dark web concept cannot be
entirely linked to perpetrator because two parties
must be involved to facilitate dark web activities.
For unauthorized data access by cybercriminals
over the dark web internet stuffing to happen,
there should be access to dark web content done
by the victims. Any person cannot access the dark
web as it requires a good understanding of some
software development skills to be able to navigate
successfully. This makes it solely an activity that
can be performed by technocrats (Gehl, 2018).
Dark web activities should involve a series of
events ranging from technology to social,
psychological aspects. It is essential to
understand the techniques that can support dark
web surfing and be specific to the nature of the
content required because anonymous search
might not give out substantial results. Through
the use of TOR browser and some basic
understanding of JavaScript and React.js
technologies in software development it would be
possible to access and use dark web content.
Access to any unauthorized information might
have both psychological and social implications
on the victims (Hayhurst, Kedward, Soh &
Turner, 2012).
Theoretical approach on the dark web focus on a The approach subjects several factors to an
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Cyber Crime - Pros and Cons of Dark Netlg...
|9
|3265
|11
Assessment of Work and Progress Towards Learning Outcomeslg...
|9
|2156
|186
Information Security Assignment (pdf)lg...
|12
|3554
|71
Dark-Net: The Hidden Side of the Internetlg...
|7
|1982
|419
Assignment on IT Secuirty (pdf)lg...
|9
|3078
|209
