ITECH 7410 Assignment 1: Software Engineering Methodologies Analysis
VerifiedAdded on 2022/12/23
|11
|1190
|1
Homework Assignment
AI Summary
This assignment analyzes a real-time bank transfer application, a common feature in modern banking systems. The solution begins with an introduction to the application, followed by an Entity Relationship Diagram (ERD) illustrating the database structure, including entities for sender, recipient, account, and transfer data. A Data Flow Diagram (DFD) depicts the flow of data through the system, from user authentication to fund transfer completion. Control specifications, including a state machine diagram, detail the application's states and transitions. A comprehensive data dictionary defines the attributes of each database table. The assignment concludes with a discussion of the application's effectiveness and potential for future improvements.

Running head: SOFTWARE ENGINEERING METHODOLOGIES
Software Engineering Methodologies
Name of the Student
Name of the University
Author’s note:
Software Engineering Methodologies
Name of the Student
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SOFTWARE ENGINEERING METHODOLOGIES
Table of Contents
Introduction: ............................................................................................................................... 2
Entity Relationship Diagram: ...................................................................................................... 3
Data Flow Diagram: .................................................................................................................... 4
Control Specifications: ................................................................................................................ 5
Data Dictionary: .......................................................................................................................... 5
Conclusion: ................................................................................................................................. 9
Bibliography: ............................................................................................................................ 10
Table of Contents
Introduction: ............................................................................................................................... 2
Entity Relationship Diagram: ...................................................................................................... 3
Data Flow Diagram: .................................................................................................................... 4
Control Specifications: ................................................................................................................ 5
Data Dictionary: .......................................................................................................................... 5
Conclusion: ................................................................................................................................. 9
Bibliography: ............................................................................................................................ 10

2SOFTWARE ENGINEERING METHODOLOGIES
Introduction:
The fund transferring applications are very popular now a days. These application reduces
the amount of effort needed to transfer amount to another bank manually at the bank. Each instance
of the application is installed at the client side or sender. The concept of sender and recipient is
completely dependent on the application instance. The ERD will provide insight to the data
attributes required for database. The DFD shows how the data flows through various processes.
Finally the state machine diagram shows each state of the application what activates the state.
Introduction:
The fund transferring applications are very popular now a days. These application reduces
the amount of effort needed to transfer amount to another bank manually at the bank. Each instance
of the application is installed at the client side or sender. The concept of sender and recipient is
completely dependent on the application instance. The ERD will provide insight to the data
attributes required for database. The DFD shows how the data flows through various processes.
Finally the state machine diagram shows each state of the application what activates the state.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3SOFTWARE ENGINEERING METHODOLOGIES
Entity Relationship Diagram:
Sender
Account
Transfer
Recipient
user_idPK
email
password
name
address
contact
account_numberPK
signature
net_banking_passwor
d
branch
bank
balance
user_idFK
transfer_idPK
sender_idFK
recipient_idFK
amount
recipient_idPK
account_numberFK
name
contact_number
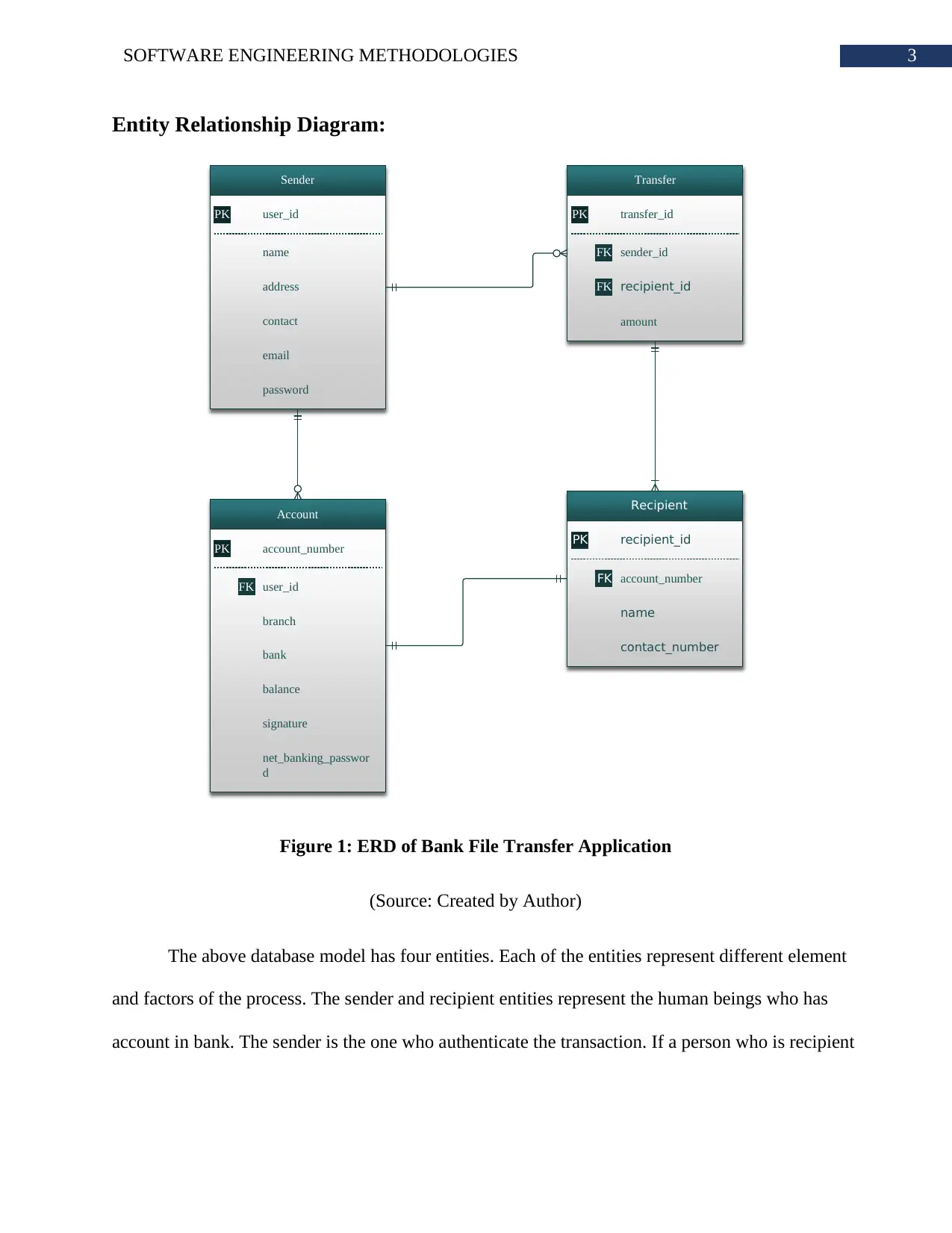
Figure 1: ERD of Bank File Transfer Application
(Source: Created by Author)
The above database model has four entities. Each of the entities represent different element
and factors of the process. The sender and recipient entities represent the human beings who has
account in bank. The sender is the one who authenticate the transaction. If a person who is recipient
Entity Relationship Diagram:
Sender
Account
Transfer
Recipient
user_idPK
password
name
address
contact
account_numberPK
signature
net_banking_passwor
d
branch
bank
balance
user_idFK
transfer_idPK
sender_idFK
recipient_idFK
amount
recipient_idPK
account_numberFK
name
contact_number
Figure 1: ERD of Bank File Transfer Application
(Source: Created by Author)
The above database model has four entities. Each of the entities represent different element
and factors of the process. The sender and recipient entities represent the human beings who has
account in bank. The sender is the one who authenticate the transaction. If a person who is recipient
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SOFTWARE ENGINEERING METHODOLOGIES
in one person’s application is sending money to that person then role of sender and recipient
interchanges.
Data Flow Diagram:
1.0
Authenticate
Sender
User_id and password
2.0
Select Recipient
Recipient
Info
2.1
Enter Recipient name
and Account Info
Recipient Data
3.0
Complete Transfer
2.2
Enter O.T.P.
SMS Code
Transfer
D1 Sender
User_id and password
D2 Saved Recipient
Name and Account Info
D3 Saved Recipient
Name
and
Account Info
D4 Transfer
Sender, recipient, amount
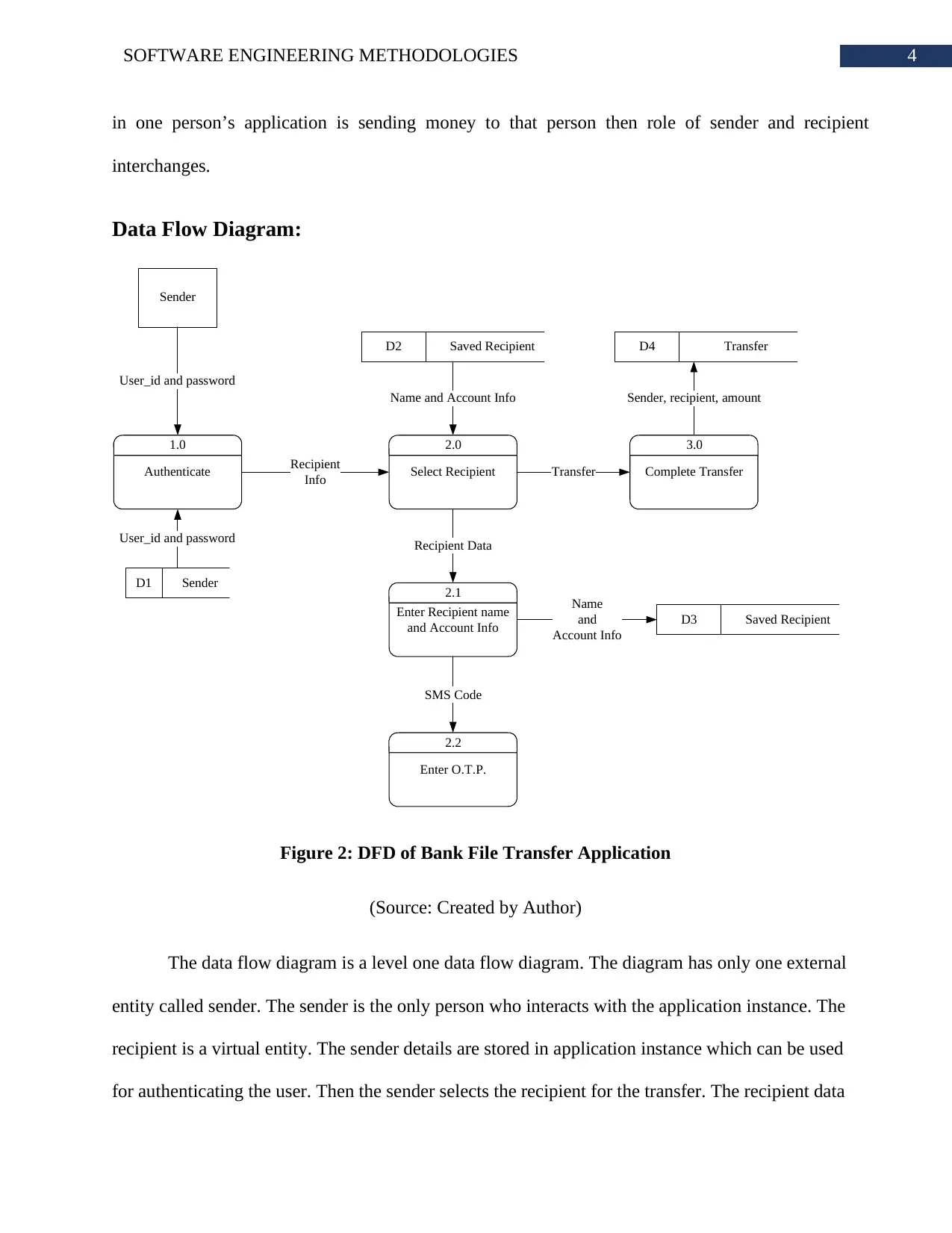
Figure 2: DFD of Bank File Transfer Application
(Source: Created by Author)
The data flow diagram is a level one data flow diagram. The diagram has only one external
entity called sender. The sender is the only person who interacts with the application instance. The
recipient is a virtual entity. The sender details are stored in application instance which can be used
for authenticating the user. Then the sender selects the recipient for the transfer. The recipient data
in one person’s application is sending money to that person then role of sender and recipient
interchanges.
Data Flow Diagram:
1.0
Authenticate
Sender
User_id and password
2.0
Select Recipient
Recipient
Info
2.1
Enter Recipient name
and Account Info
Recipient Data
3.0
Complete Transfer
2.2
Enter O.T.P.
SMS Code
Transfer
D1 Sender
User_id and password
D2 Saved Recipient
Name and Account Info
D3 Saved Recipient
Name
and
Account Info
D4 Transfer
Sender, recipient, amount
Figure 2: DFD of Bank File Transfer Application
(Source: Created by Author)
The data flow diagram is a level one data flow diagram. The diagram has only one external
entity called sender. The sender is the only person who interacts with the application instance. The
recipient is a virtual entity. The sender details are stored in application instance which can be used
for authenticating the user. Then the sender selects the recipient for the transfer. The recipient data
5SOFTWARE ENGINEERING METHODOLOGIES
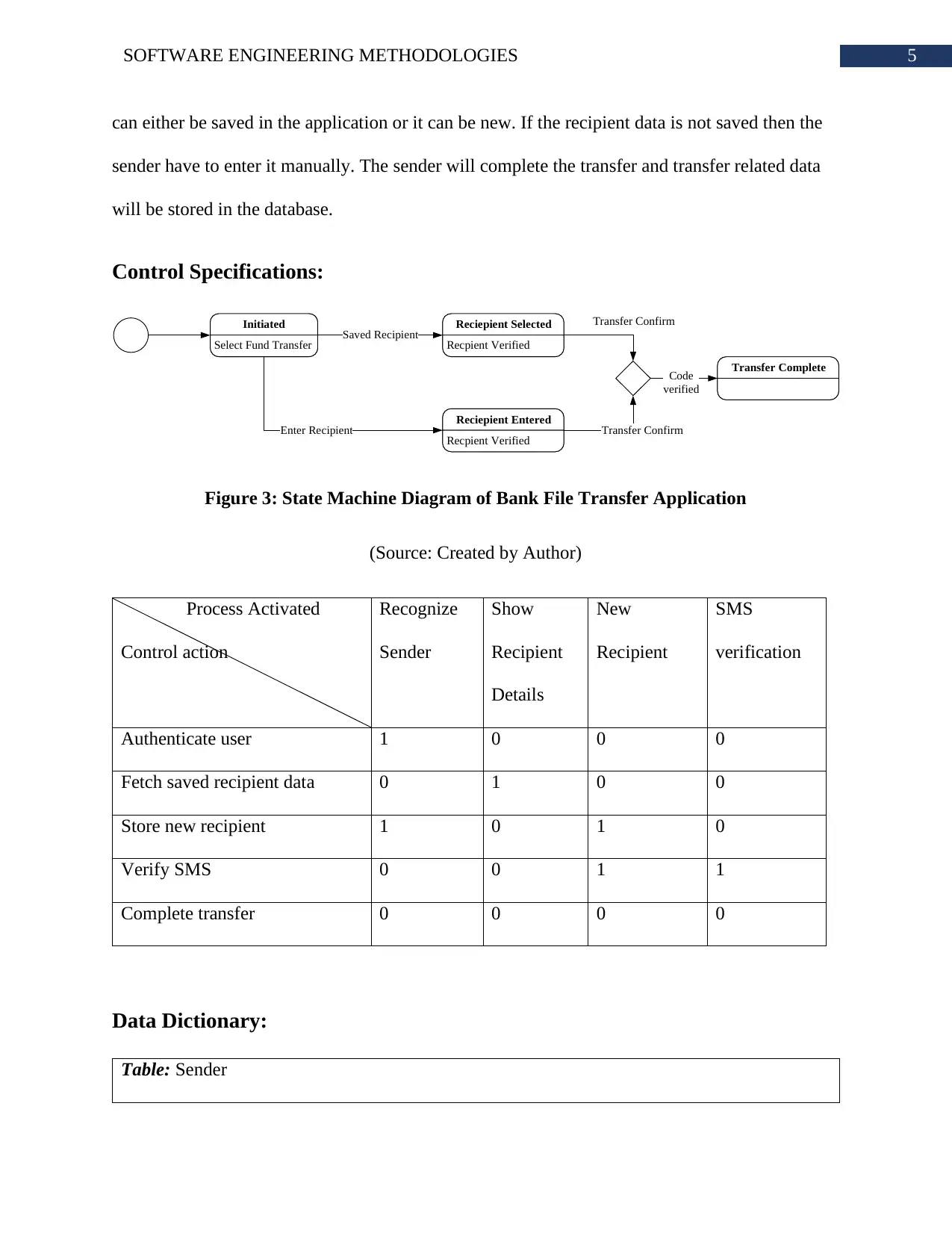
can either be saved in the application or it can be new. If the recipient data is not saved then the
sender have to enter it manually. The sender will complete the transfer and transfer related data
will be stored in the database.
Control Specifications:
Initiated
Select Fund Transfer
Reciepient Selected
Recpient Verified
Saved Recipient
Reciepient Entered
Recpient Verified
Enter Recipient
Transfer Complete
Transfer Confirm
Transfer Confirm
Code
verified
Figure 3: State Machine Diagram of Bank File Transfer Application
(Source: Created by Author)
Process Activated
Control action
Recognize
Sender
Show
Recipient
Details
New
Recipient
SMS
verification
Authenticate user 1 0 0 0
Fetch saved recipient data 0 1 0 0
Store new recipient 1 0 1 0
Verify SMS 0 0 1 1
Complete transfer 0 0 0 0
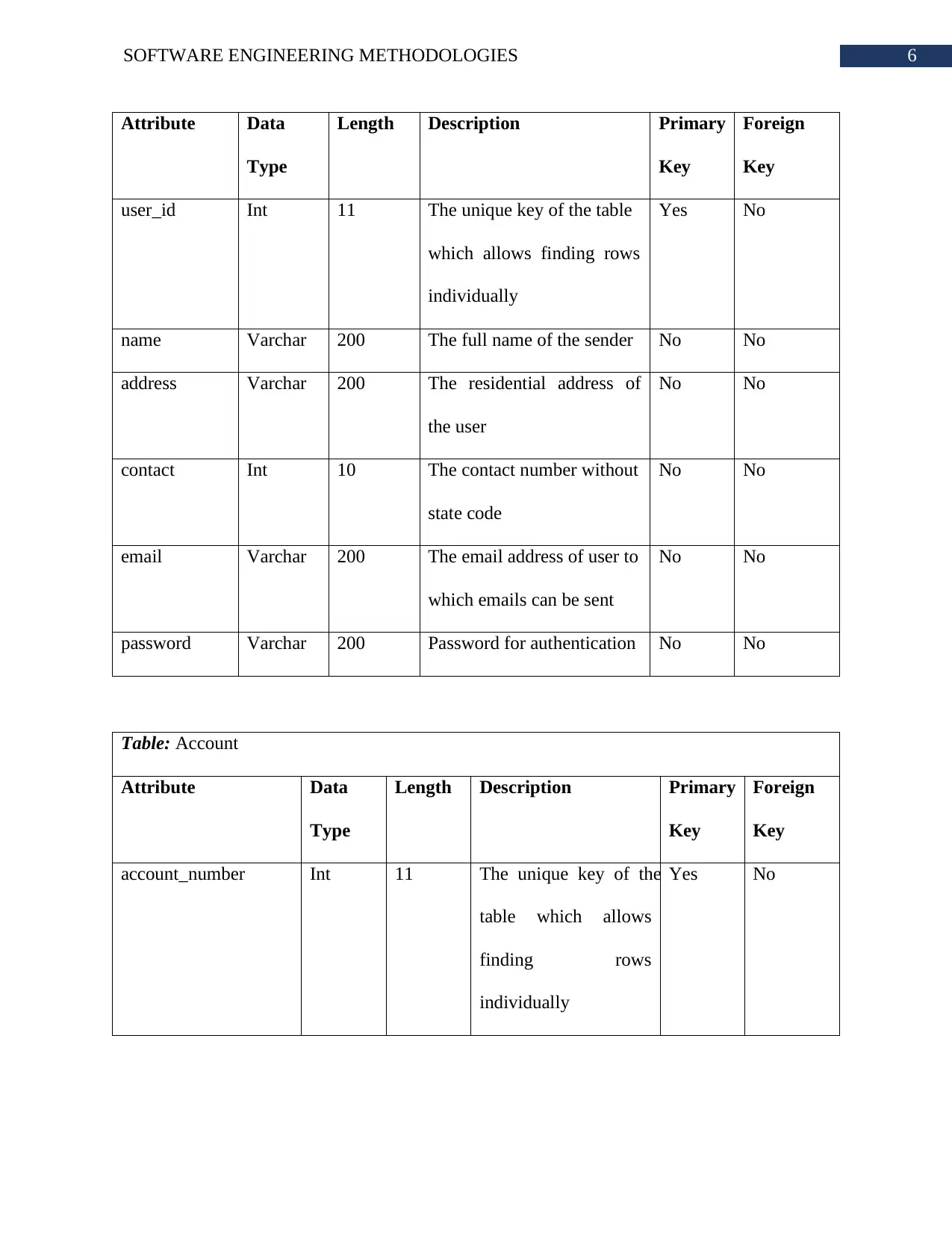
Data Dictionary:
Table: Sender
can either be saved in the application or it can be new. If the recipient data is not saved then the
sender have to enter it manually. The sender will complete the transfer and transfer related data
will be stored in the database.
Control Specifications:
Initiated
Select Fund Transfer
Reciepient Selected
Recpient Verified
Saved Recipient
Reciepient Entered
Recpient Verified
Enter Recipient
Transfer Complete
Transfer Confirm
Transfer Confirm
Code
verified
Figure 3: State Machine Diagram of Bank File Transfer Application
(Source: Created by Author)
Process Activated
Control action
Recognize
Sender
Show
Recipient
Details
New
Recipient
SMS
verification
Authenticate user 1 0 0 0
Fetch saved recipient data 0 1 0 0
Store new recipient 1 0 1 0
Verify SMS 0 0 1 1
Complete transfer 0 0 0 0
Data Dictionary:
Table: Sender
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SOFTWARE ENGINEERING METHODOLOGIES
Attribute Data
Type
Length Description Primary
Key
Foreign
Key
user_id Int 11 The unique key of the table
which allows finding rows
individually
Yes No
name Varchar 200 The full name of the sender No No
address Varchar 200 The residential address of
the user
No No
contact Int 10 The contact number without
state code
No No
email Varchar 200 The email address of user to
which emails can be sent
No No
password Varchar 200 Password for authentication No No
Table: Account
Attribute Data
Type
Length Description Primary
Key
Foreign
Key
account_number Int 11 The unique key of the
table which allows
finding rows
individually
Yes No
Attribute Data
Type
Length Description Primary
Key
Foreign
Key
user_id Int 11 The unique key of the table
which allows finding rows
individually
Yes No
name Varchar 200 The full name of the sender No No
address Varchar 200 The residential address of
the user
No No
contact Int 10 The contact number without
state code
No No
email Varchar 200 The email address of user to
which emails can be sent
No No
password Varchar 200 Password for authentication No No
Table: Account
Attribute Data
Type
Length Description Primary
Key
Foreign
Key
account_number Int 11 The unique key of the
table which allows
finding rows
individually
Yes No
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
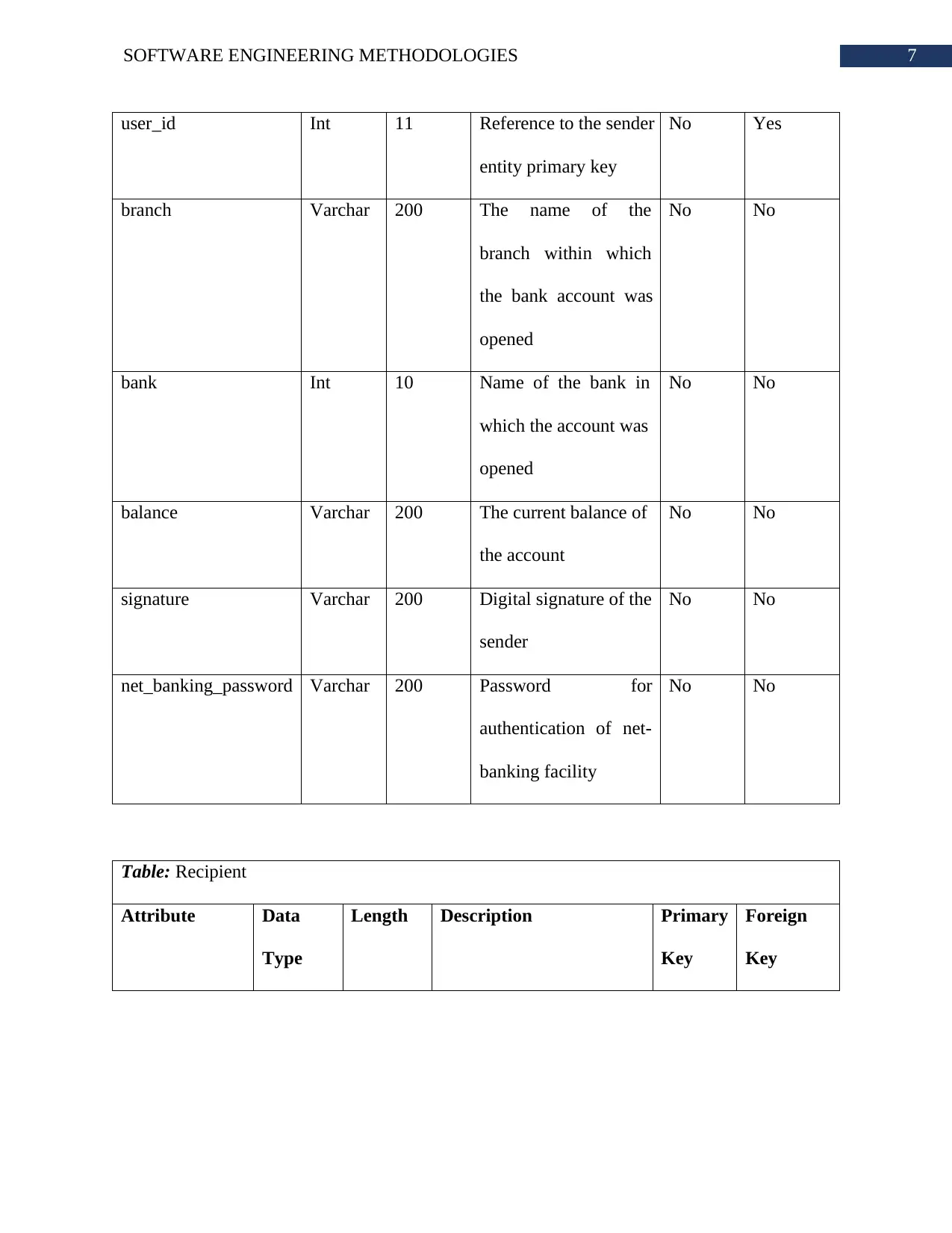
7SOFTWARE ENGINEERING METHODOLOGIES
user_id Int 11 Reference to the sender
entity primary key
No Yes
branch Varchar 200 The name of the
branch within which
the bank account was
opened
No No
bank Int 10 Name of the bank in
which the account was
opened
No No
balance Varchar 200 The current balance of
the account
No No
signature Varchar 200 Digital signature of the
sender
No No
net_banking_password Varchar 200 Password for
authentication of net-
banking facility
No No
Table: Recipient
Attribute Data
Type
Length Description Primary
Key
Foreign
Key
user_id Int 11 Reference to the sender
entity primary key
No Yes
branch Varchar 200 The name of the
branch within which
the bank account was
opened
No No
bank Int 10 Name of the bank in
which the account was
opened
No No
balance Varchar 200 The current balance of
the account
No No
signature Varchar 200 Digital signature of the
sender
No No
net_banking_password Varchar 200 Password for
authentication of net-
banking facility
No No
Table: Recipient
Attribute Data
Type
Length Description Primary
Key
Foreign
Key
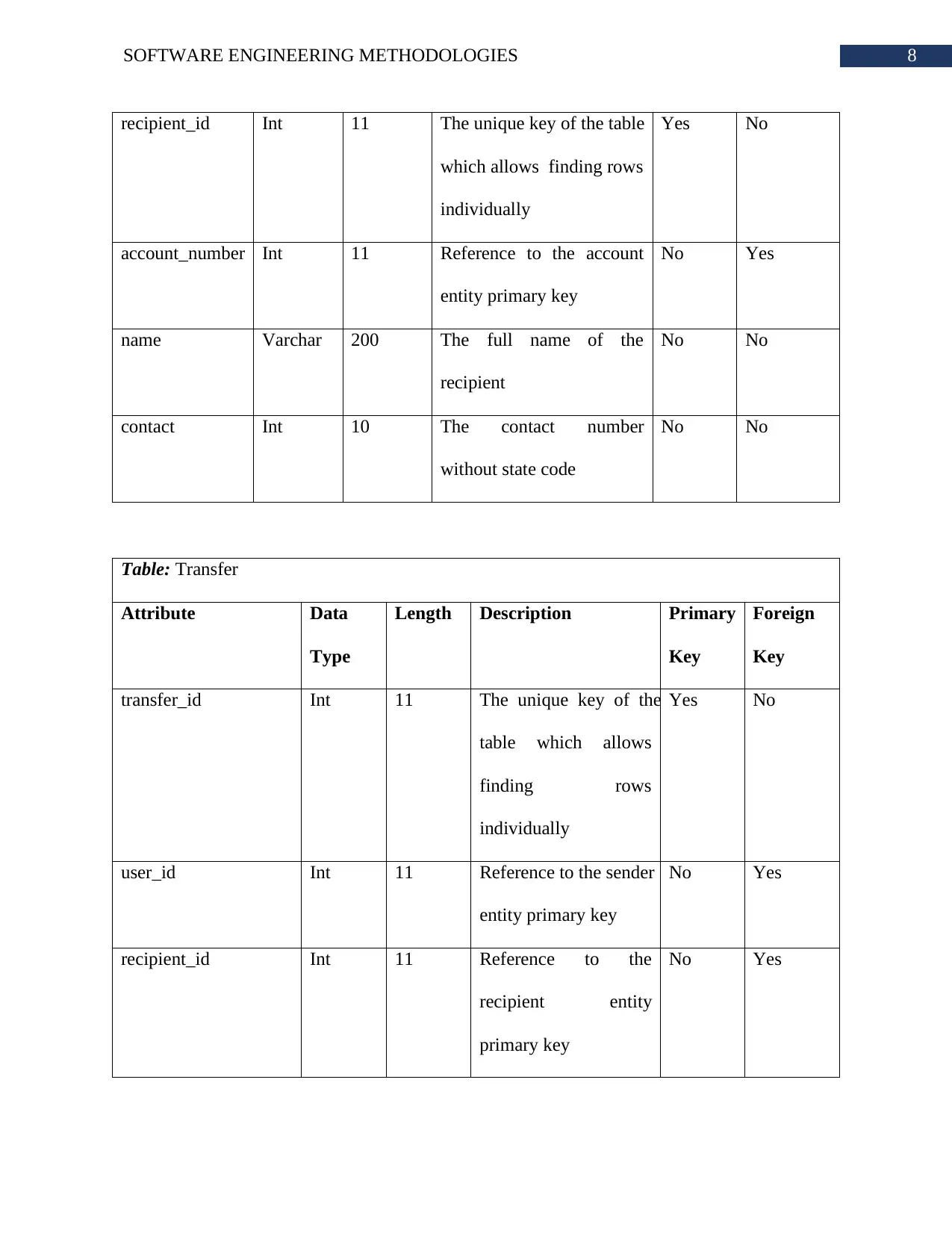
8SOFTWARE ENGINEERING METHODOLOGIES
recipient_id Int 11 The unique key of the table
which allows finding rows
individually
Yes No
account_number Int 11 Reference to the account
entity primary key
No Yes
name Varchar 200 The full name of the
recipient
No No
contact Int 10 The contact number
without state code
No No
Table: Transfer
Attribute Data
Type
Length Description Primary
Key
Foreign
Key
transfer_id Int 11 The unique key of the
table which allows
finding rows
individually
Yes No
user_id Int 11 Reference to the sender
entity primary key
No Yes
recipient_id Int 11 Reference to the
recipient entity
primary key
No Yes
recipient_id Int 11 The unique key of the table
which allows finding rows
individually
Yes No
account_number Int 11 Reference to the account
entity primary key
No Yes
name Varchar 200 The full name of the
recipient
No No
contact Int 10 The contact number
without state code
No No
Table: Transfer
Attribute Data
Type
Length Description Primary
Key
Foreign
Key
transfer_id Int 11 The unique key of the
table which allows
finding rows
individually
Yes No
user_id Int 11 Reference to the sender
entity primary key
No Yes
recipient_id Int 11 Reference to the
recipient entity
primary key
No Yes
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
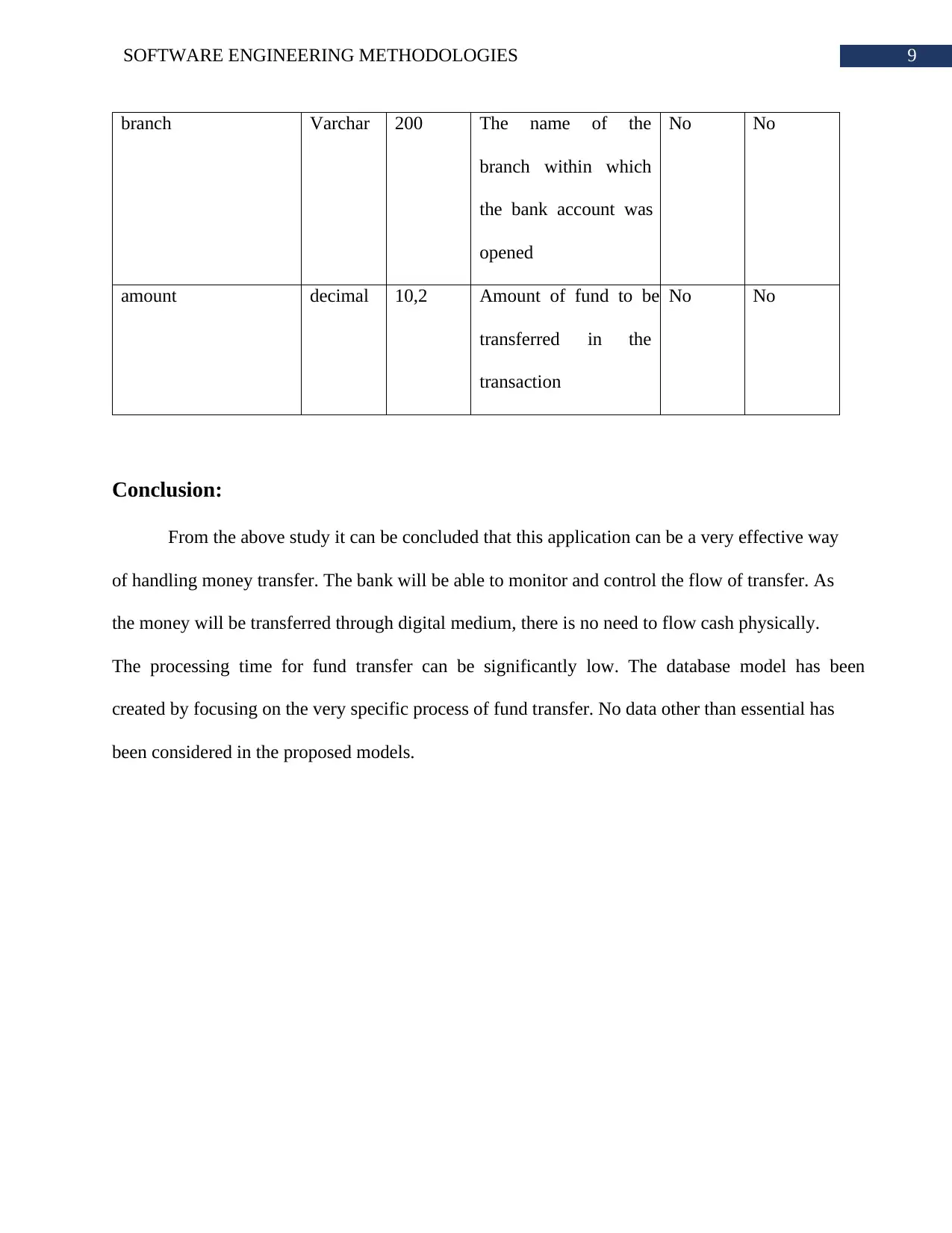
9SOFTWARE ENGINEERING METHODOLOGIES
branch Varchar 200 The name of the
branch within which
the bank account was
opened
No No
amount decimal 10,2 Amount of fund to be
transferred in the
transaction
No No
Conclusion:
From the above study it can be concluded that this application can be a very effective way
of handling money transfer. The bank will be able to monitor and control the flow of transfer. As
the money will be transferred through digital medium, there is no need to flow cash physically.
The processing time for fund transfer can be significantly low. The database model has been
created by focusing on the very specific process of fund transfer. No data other than essential has
been considered in the proposed models.
branch Varchar 200 The name of the
branch within which
the bank account was
opened
No No
amount decimal 10,2 Amount of fund to be
transferred in the
transaction
No No
Conclusion:
From the above study it can be concluded that this application can be a very effective way
of handling money transfer. The bank will be able to monitor and control the flow of transfer. As
the money will be transferred through digital medium, there is no need to flow cash physically.
The processing time for fund transfer can be significantly low. The database model has been
created by focusing on the very specific process of fund transfer. No data other than essential has
been considered in the proposed models.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SOFTWARE ENGINEERING METHODOLOGIES
Bibliography:
[1] Al-Masree, H.K, ‘Extracting Entity Relationship Diagram (ERD) from relational database
schema’, International Journal of Database Theory and Application, 8(3), pp.15-26, 2015.
[2] Dennis, A., Wixom, B.H. and Roth, R.M, ‘Systems analysis and design’. John wiley & sons,
2018.
[3] Yanushkevich, S.N., Miller, D.M., Shmerko, V.P. and Stankovic, R.S, ‘Decision diagram
techniques for micro-and nanoelectronic design handbook’, CRC Press, 2018.
[4] Damjan, P. and Vatanawood, W, ‘Translating UML state machine diagram into Promela’,
In Proceedings of the International MultiConference of Engineers and Computer Scientists, Vol.
1, 2017.
Bibliography:
[1] Al-Masree, H.K, ‘Extracting Entity Relationship Diagram (ERD) from relational database
schema’, International Journal of Database Theory and Application, 8(3), pp.15-26, 2015.
[2] Dennis, A., Wixom, B.H. and Roth, R.M, ‘Systems analysis and design’. John wiley & sons,
2018.
[3] Yanushkevich, S.N., Miller, D.M., Shmerko, V.P. and Stankovic, R.S, ‘Decision diagram
techniques for micro-and nanoelectronic design handbook’, CRC Press, 2018.
[4] Damjan, P. and Vatanawood, W, ‘Translating UML state machine diagram into Promela’,
In Proceedings of the International MultiConference of Engineers and Computer Scientists, Vol.
1, 2017.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




