Software Security: Importance, Techniques and Limitations
VerifiedAdded on 2023/05/29
|9
|2795
|469
AI Summary
This paper focuses on the importance of software security, techniques to ensure security, and limitations associated with it. It covers topics such as advanced malware detection, software process maturity, code scanning, runtime software controls, and general advantages and disadvantages of software security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Abstract
The foremost determination of the
paper is to focus on the importance of the
software security in the software
development life cycle. The software’s
which deals with sensitive data should be
arranged and managed in every phase of the
cycle so that the reliability and the
consistence of the data are maintained. The
technological enhancement has both
advantages and drawbacks, which is the
main reason that security of the software
should be focused on. The technological
advancements are the chief reason behind
the security threats associated to the
software’s. The extensive development in
the field of software technology is also one
of the reasons behind the software security.
The paper will be focusing on a thorough
examination of the literature works, the
latest developments of the software security
will be stated in this paper. The paper will
be highlighting the issues associated with
software security such as the detection of the
malware, software security control
measures, software process maturity, run
time software controls and the benefits and
limitations of the software safety.
Introduction
The prime determination of this unit
of the paper is to focus on the concept of
software security. Software security is
defined as the type of concept which is
needed to ensure the security of the software
from internal and external threats which
have the capacity to alter the data and harm
the integrity of the software. The attacks
coming from the malicious activities and the
hackers are the main reason behind the need
for the software security controls [1]. There
are three probable aspects of software
security such as the accessibility,
authentication and integrity. Security
software is defined as the type of software
which are needed to ensure that the network
or the particular software is free from the
internal and the external threats. All the
security issues associated to the software
falls under this category. The objective and
the responsibility of the software security
engineer are to focus on the security issues
associated to the software or the probable
threats from which the software might get
negatively affected [1]. The different types
of privacy and security software such as the
anti key loggers, cryptographic, anti-virus
software access control, anti-spyware and
anti-malware. The security risks of a
1
The foremost determination of the
paper is to focus on the importance of the
software security in the software
development life cycle. The software’s
which deals with sensitive data should be
arranged and managed in every phase of the
cycle so that the reliability and the
consistence of the data are maintained. The
technological enhancement has both
advantages and drawbacks, which is the
main reason that security of the software
should be focused on. The technological
advancements are the chief reason behind
the security threats associated to the
software’s. The extensive development in
the field of software technology is also one
of the reasons behind the software security.
The paper will be focusing on a thorough
examination of the literature works, the
latest developments of the software security
will be stated in this paper. The paper will
be highlighting the issues associated with
software security such as the detection of the
malware, software security control
measures, software process maturity, run
time software controls and the benefits and
limitations of the software safety.
Introduction
The prime determination of this unit
of the paper is to focus on the concept of
software security. Software security is
defined as the type of concept which is
needed to ensure the security of the software
from internal and external threats which
have the capacity to alter the data and harm
the integrity of the software. The attacks
coming from the malicious activities and the
hackers are the main reason behind the need
for the software security controls [1]. There
are three probable aspects of software
security such as the accessibility,
authentication and integrity. Security
software is defined as the type of software
which are needed to ensure that the network
or the particular software is free from the
internal and the external threats. All the
security issues associated to the software
falls under this category. The objective and
the responsibility of the software security
engineer are to focus on the security issues
associated to the software or the probable
threats from which the software might get
negatively affected [1]. The different types
of privacy and security software such as the
anti key loggers, cryptographic, anti-virus
software access control, anti-spyware and
anti-malware. The security risks of a
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
computer may arise from the unpatched
operating systems, insecure computer
activities and misconfigured software’s. The
security threats associated to software are
the Trojan horse, privilege escalation, spam,
virus, worms, rootkits and adware [1]. The
safety and security of a computer is very
much needed so that the system can be
saved from the unwanted security threats.
The security of a computer will be ensuring
the protection of the computer as well as the
software installed in it.
The extensive development in the field of
information technology has resulted in the
growth of the cyber security communities
which works for the security and safety of
the software [2]. The compatibility issues
associated with software can also be
significantly minimized with the help of this
community. The developments in the field
of cyber security has guided us to
understand the advancements of the security
controls as well as provide idea about the
future development in this field [2]. The
current developments in the field of cyber
security have vgiven rise to software such as
DevOps coding. Strategies are adopted by
the cyber security communities to deal with
the security threats of the software with the
help of specific methods and techniques,
each dealing with specific kinds of risks.
The inefficiency of the back e3nd coding is
also a security concern, this also falls under
the category of the cyber security
communities [2]. The paper will be focusing
on the recent developments in this field and
also on the literature works. This will be
beneficial to understand the role of cyber
security considering the cyber security
threats.
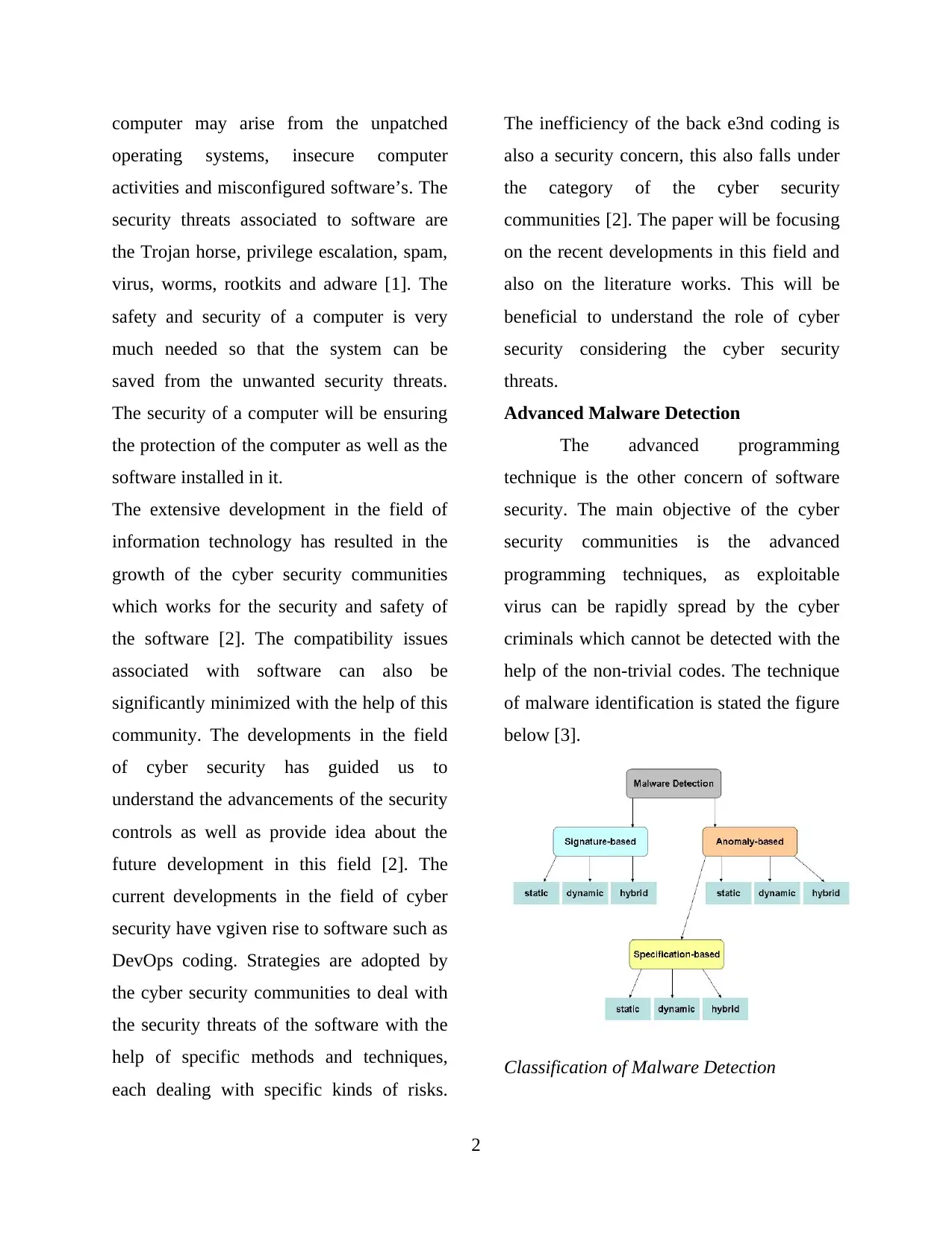
Advanced Malware Detection
The advanced programming
technique is the other concern of software
security. The main objective of the cyber
security communities is the advanced
programming techniques, as exploitable
virus can be rapidly spread by the cyber
criminals which cannot be detected with the
help of the non-trivial codes. The technique
of malware identification is stated the figure
below [3].
Classification of Malware Detection
2
operating systems, insecure computer
activities and misconfigured software’s. The
security threats associated to software are
the Trojan horse, privilege escalation, spam,
virus, worms, rootkits and adware [1]. The
safety and security of a computer is very
much needed so that the system can be
saved from the unwanted security threats.
The security of a computer will be ensuring
the protection of the computer as well as the
software installed in it.
The extensive development in the field of
information technology has resulted in the
growth of the cyber security communities
which works for the security and safety of
the software [2]. The compatibility issues
associated with software can also be
significantly minimized with the help of this
community. The developments in the field
of cyber security has guided us to
understand the advancements of the security
controls as well as provide idea about the
future development in this field [2]. The
current developments in the field of cyber
security have vgiven rise to software such as
DevOps coding. Strategies are adopted by
the cyber security communities to deal with
the security threats of the software with the
help of specific methods and techniques,
each dealing with specific kinds of risks.
The inefficiency of the back e3nd coding is
also a security concern, this also falls under
the category of the cyber security
communities [2]. The paper will be focusing
on the recent developments in this field and
also on the literature works. This will be
beneficial to understand the role of cyber
security considering the cyber security
threats.
Advanced Malware Detection
The advanced programming
technique is the other concern of software
security. The main objective of the cyber
security communities is the advanced
programming techniques, as exploitable
virus can be rapidly spread by the cyber
criminals which cannot be detected with the
help of the non-trivial codes. The technique
of malware identification is stated the figure
below [3].
Classification of Malware Detection
2

The conventional malware detection
techniques were created on the application
code to the signatures but the latest
techniques considers the run time activities
as the measurement of the software security
[2]. It can be understood that every business
organization which deals with sensitive data
should be anticipating different types of
security issues so that they can achieve the
desired results. Cyber metric equipment’s
are used in the recent times for the
behavioral investigations of the software.
The absence of the cybernetic settings is
very much dangerous for the computer
systems [5].
In the recent times, machine learning
techniques are being applied to deal with the
cyber security issues such as the malware.
Efficiencies of the logarithms is improved to
a great extent. Continuous presences of the
complications associated to the software are
also detected with the help of these
developments. However it is also found the
possibilities of complete removal of the
malware is also very much difficult [5].
Advanced malware protection depends upon
the malware sand box to prevent the
distribution of the malicious documents.
The evasion approach of a malware depends
upon the following approaches:
Stalling delays: Malware generally
infects the computer system for a
maximum of 10 minutes.
User action need: The activity of the
malware starts only after any activity
of the users.
Suspended activities: The malware
helps in suspending any kinds of
malicious actions when it operates
with in a sand box. It has the
capability to modify the codes with
the other applications. Downloading
the additional codes and developing
the tenacity is the other activities of
the malware. Malware relocates
cross wise with in a network and
connect to the C & C servers.
Fragmentation: Malware can divide
itself into numerous fragments and
perform activities accordingly [6].
Return Oriented Programming
(ROP) evasion: The modifications of
the codes have no effect on the
malware. The adjustments of the
stack contents which sets the
memories address which are directed
to be executed afterward.
Rootkits: The lower strata of the
operating system is the home of the
malicious codes as the sand box tools
are unable to reach that spot.
3
techniques were created on the application
code to the signatures but the latest
techniques considers the run time activities
as the measurement of the software security
[2]. It can be understood that every business
organization which deals with sensitive data
should be anticipating different types of
security issues so that they can achieve the
desired results. Cyber metric equipment’s
are used in the recent times for the
behavioral investigations of the software.
The absence of the cybernetic settings is
very much dangerous for the computer
systems [5].
In the recent times, machine learning
techniques are being applied to deal with the
cyber security issues such as the malware.
Efficiencies of the logarithms is improved to
a great extent. Continuous presences of the
complications associated to the software are
also detected with the help of these
developments. However it is also found the
possibilities of complete removal of the
malware is also very much difficult [5].
Advanced malware protection depends upon
the malware sand box to prevent the
distribution of the malicious documents.
The evasion approach of a malware depends
upon the following approaches:
Stalling delays: Malware generally
infects the computer system for a
maximum of 10 minutes.
User action need: The activity of the
malware starts only after any activity
of the users.
Suspended activities: The malware
helps in suspending any kinds of
malicious actions when it operates
with in a sand box. It has the
capability to modify the codes with
the other applications. Downloading
the additional codes and developing
the tenacity is the other activities of
the malware. Malware relocates
cross wise with in a network and
connect to the C & C servers.
Fragmentation: Malware can divide
itself into numerous fragments and
perform activities accordingly [6].
Return Oriented Programming
(ROP) evasion: The modifications of
the codes have no effect on the
malware. The adjustments of the
stack contents which sets the
memories address which are directed
to be executed afterward.
Rootkits: The lower strata of the
operating system is the home of the
malicious codes as the sand box tools
are unable to reach that spot.
3
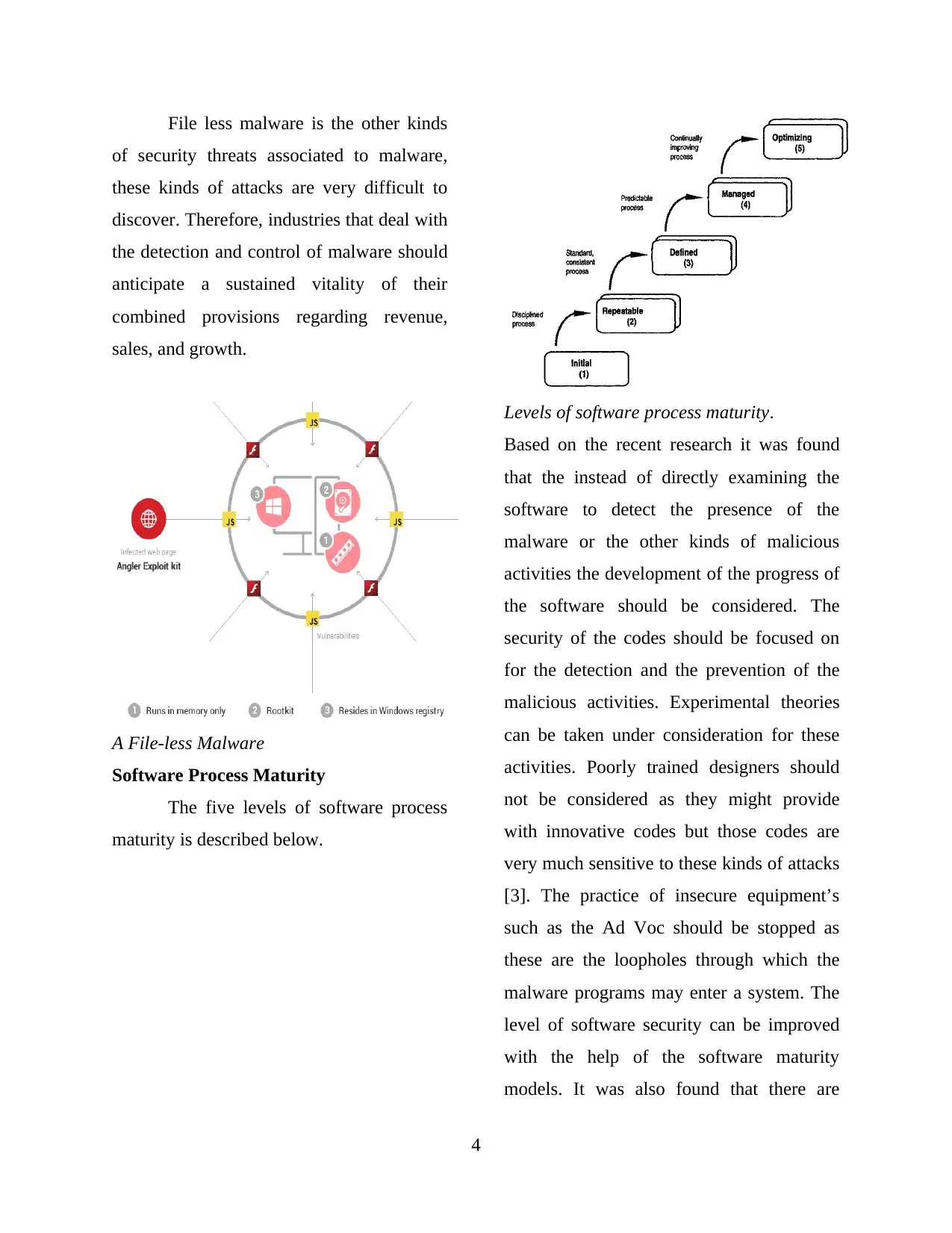
File less malware is the other kinds
of security threats associated to malware,
these kinds of attacks are very difficult to
discover. Therefore, industries that deal with
the detection and control of malware should
anticipate a sustained vitality of their
combined provisions regarding revenue,
sales, and growth.
A File-less Malware
Software Process Maturity
The five levels of software process
maturity is described below.
Levels of software process maturity.
Based on the recent research it was found
that the instead of directly examining the
software to detect the presence of the
malware or the other kinds of malicious
activities the development of the progress of
the software should be considered. The
security of the codes should be focused on
for the detection and the prevention of the
malicious activities. Experimental theories
can be taken under consideration for these
activities. Poorly trained designers should
not be considered as they might provide
with innovative codes but those codes are
very much sensitive to these kinds of attacks
[3]. The practice of insecure equipment’s
such as the Ad Voc should be stopped as
these are the loopholes through which the
malware programs may enter a system. The
level of software security can be improved
with the help of the software maturity
models. It was also found that there are
4
of security threats associated to malware,
these kinds of attacks are very difficult to
discover. Therefore, industries that deal with
the detection and control of malware should
anticipate a sustained vitality of their
combined provisions regarding revenue,
sales, and growth.
A File-less Malware
Software Process Maturity
The five levels of software process
maturity is described below.
Levels of software process maturity.
Based on the recent research it was found
that the instead of directly examining the
software to detect the presence of the
malware or the other kinds of malicious
activities the development of the progress of
the software should be considered. The
security of the codes should be focused on
for the detection and the prevention of the
malicious activities. Experimental theories
can be taken under consideration for these
activities. Poorly trained designers should
not be considered as they might provide
with innovative codes but those codes are
very much sensitive to these kinds of attacks
[3]. The practice of insecure equipment’s
such as the Ad Voc should be stopped as
these are the loopholes through which the
malware programs may enter a system. The
level of software security can be improved
with the help of the software maturity
models. It was also found that there are
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

several issues associated to the software
security models as it always opts for
additional safety of all the codes that
develop from software [2]. The techniques
which are need for those systems are
periodic penetration testing’s, maintenance
processes and automation. The advantage
associated with the process models is its
small downside in every model which helps
in enhancing the procedures od developing a
code. Code saving which is a common
criteria among all the recent software’s help
in maintaining high quality enhancements.
Review and Scanning of the Software
The two categories of scanning techniques
are the active and the passive techniques.
The vulnerability assessment is carried out
with the help of the automated testing tools
such as the network security scanners.
Vulnerability scanning is defined as the type
of scanning which are helpful in the
identification of the risks and faults
associated to the cyber security systems [4].
The different categories of the vulnerability
scanners are as port scanner, computer
worm, security scanner, web application
scanner, network vulnerability scanner and
the network enumerator.
Based on a structured and systematic
examination of a document it was found that
the foremost objective of the software
expansion life cycle aims to discover and
eliminate faults [6]. In most of the cases it
was found that the software expansion life
cycle is plays a very important role in
ensuring the security of a computer system
as well as the network. The review of the
security codes is required for auditing the
source of the codes so that any kinds of
application which runs on those codes can
substantiate the available security controls.
Reliability of the software is the other
essential aspect of the security measures in
software [2]. Security of the software’s can
be enhanced with the help of the detailed
examination of the codes and the application
of the code scanning techniques. C
programming codes were first scanned at the
Bell labs in 1970 [2]. They also provided
sufficient recommendations after their
detailed analysis.
5
security models as it always opts for
additional safety of all the codes that
develop from software [2]. The techniques
which are need for those systems are
periodic penetration testing’s, maintenance
processes and automation. The advantage
associated with the process models is its
small downside in every model which helps
in enhancing the procedures od developing a
code. Code saving which is a common
criteria among all the recent software’s help
in maintaining high quality enhancements.
Review and Scanning of the Software
The two categories of scanning techniques
are the active and the passive techniques.
The vulnerability assessment is carried out
with the help of the automated testing tools
such as the network security scanners.
Vulnerability scanning is defined as the type
of scanning which are helpful in the
identification of the risks and faults
associated to the cyber security systems [4].
The different categories of the vulnerability
scanners are as port scanner, computer
worm, security scanner, web application
scanner, network vulnerability scanner and
the network enumerator.
Based on a structured and systematic
examination of a document it was found that
the foremost objective of the software
expansion life cycle aims to discover and
eliminate faults [6]. In most of the cases it
was found that the software expansion life
cycle is plays a very important role in
ensuring the security of a computer system
as well as the network. The review of the
security codes is required for auditing the
source of the codes so that any kinds of
application which runs on those codes can
substantiate the available security controls.
Reliability of the software is the other
essential aspect of the security measures in
software [2]. Security of the software’s can
be enhanced with the help of the detailed
examination of the codes and the application
of the code scanning techniques. C
programming codes were first scanned at the
Bell labs in 1970 [2]. They also provided
sufficient recommendations after their
detailed analysis.
5
Code Scanning
The current application of the manual codes
is very much important in maintain the high
quality and securing items. The primitive
perspective is being challenged with the
rapid cycle times in the DevOps setting
where very less time is available for the
human inspection [2]. Automated scanning
techniques are adopted for these kinds of
scenarios. The cloud based software
development settings and the current
DevOps are the most important control
methods for the security issues associated
with the software security [5].
Runtime Software Controls
The latest runtime software control needs
dynamic updates as it promotes the
makeshift techniques. These systems can be
improved with the help of the principled and
systematic method of run time modification
[6]. This is backup with the help of an
exploitable infrastructure. The benefits of
the run time advancements are not restricted
to security intensive. The modern
commercial software experiences the same
specifications to offer different
customizability and extensibility to the
clients. The latest runtime extension features
have developed to readily access in most of
the operating systems [4].
The runtime features of most of the latest
operating systems have different sorts of
drawbacks associated to them.
Dependability of the software’s are the most
significant limitation of those run time
facilities. Constancy and accuracy are the
most important drawbacks of the runtime
variations. The change management is
directly related to the run time environment,
it helps in identifying things which should
have been modified. The runtime variations
has other aspects such as the stipulation and
executing the changes. The absence of the
change management results in more
complicated issues such as the shutting
down of the computers or getting restarted.
The application of the run time controls are
placed in the implementation settings which
is a great step in improving the security of a
computer system. This process can be also
termed as the Run Time Application Self
6
The current application of the manual codes
is very much important in maintain the high
quality and securing items. The primitive
perspective is being challenged with the
rapid cycle times in the DevOps setting
where very less time is available for the
human inspection [2]. Automated scanning
techniques are adopted for these kinds of
scenarios. The cloud based software
development settings and the current
DevOps are the most important control
methods for the security issues associated
with the software security [5].
Runtime Software Controls
The latest runtime software control needs
dynamic updates as it promotes the
makeshift techniques. These systems can be
improved with the help of the principled and
systematic method of run time modification
[6]. This is backup with the help of an
exploitable infrastructure. The benefits of
the run time advancements are not restricted
to security intensive. The modern
commercial software experiences the same
specifications to offer different
customizability and extensibility to the
clients. The latest runtime extension features
have developed to readily access in most of
the operating systems [4].
The runtime features of most of the latest
operating systems have different sorts of
drawbacks associated to them.
Dependability of the software’s are the most
significant limitation of those run time
facilities. Constancy and accuracy are the
most important drawbacks of the runtime
variations. The change management is
directly related to the run time environment,
it helps in identifying things which should
have been modified. The runtime variations
has other aspects such as the stipulation and
executing the changes. The absence of the
change management results in more
complicated issues such as the shutting
down of the computers or getting restarted.
The application of the run time controls are
placed in the implementation settings which
is a great step in improving the security of a
computer system. This process can be also
termed as the Run Time Application Self
6

Protection (RASP). The vulnerabilities
associated with the codes are covered up
with the help of this process. The integration
of the behavioral and the machine learning
techniques within the process are the other
aspects of this process [2]. Minimization of
the security threats is the primary objective
of RASP. The SMOTION run time software
is an user defined software which can be
entirely customized according to the needs
and requirement is helpful to perform the
desired task.
The SMOTION Runtime Software
The variations of the software achievements
are possible with the help of the machine
learning methods which are developed with
the help of the experimental behavior. The
deep learning advancements are also one of
the most intriguing features of the software
security [4]. The improved effectiveness and
the enhanced monumental parallelism are
the main reason behind the development of
the software security. Considering the huge
amount of complexities associated to a
computer network, this approach is very
much reliable and can be implemented
accordingly [5].
General Advantages and Disadvantages
of Software Security in the Contemporary
world
This unit of the paper will be focusing on
the advantages and the disadvantages of the
software security [1]. There are different
types of benefits and limitations associated
with the software security, The prime
advantages of the software security it that it
saves the computer systems from the
external threats such as the viruses and
worms, spyware or any other kinds of
malware program [6]. The data pilferages
can be restricted with the help of the security
measures [1]. The presence of the security
measures makes it difficult for the hackers
to attack the systems. The crashing problems
and the freezing problems can also be solved
significantly with the help of the control
measure [1]. The disadvantages associated
with the control measures are that it restricts
certain online activities. The other limitation
associated with the control measures is the
periodical updation of the software’s. The
cost of original software’s is the other
7
associated with the codes are covered up
with the help of this process. The integration
of the behavioral and the machine learning
techniques within the process are the other
aspects of this process [2]. Minimization of
the security threats is the primary objective
of RASP. The SMOTION run time software
is an user defined software which can be
entirely customized according to the needs
and requirement is helpful to perform the
desired task.
The SMOTION Runtime Software
The variations of the software achievements
are possible with the help of the machine
learning methods which are developed with
the help of the experimental behavior. The
deep learning advancements are also one of
the most intriguing features of the software
security [4]. The improved effectiveness and
the enhanced monumental parallelism are
the main reason behind the development of
the software security. Considering the huge
amount of complexities associated to a
computer network, this approach is very
much reliable and can be implemented
accordingly [5].
General Advantages and Disadvantages
of Software Security in the Contemporary
world
This unit of the paper will be focusing on
the advantages and the disadvantages of the
software security [1]. There are different
types of benefits and limitations associated
with the software security, The prime
advantages of the software security it that it
saves the computer systems from the
external threats such as the viruses and
worms, spyware or any other kinds of
malware program [6]. The data pilferages
can be restricted with the help of the security
measures [1]. The presence of the security
measures makes it difficult for the hackers
to attack the systems. The crashing problems
and the freezing problems can also be solved
significantly with the help of the control
measure [1]. The disadvantages associated
with the control measures are that it restricts
certain online activities. The other limitation
associated with the control measures is the
periodical updation of the software’s. The
cost of original software’s is the other
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

drawback associated to the security
protocols [6].
Conclusion
From the above paper it can be concluded
that the cyber security community plays
huge role in preventing the cyber security
issues which have the capability to destroy
the online assets of the organization. It can
be also concluded that the efforts of the
software security personnel’s should be a bit
more realistic in minimizing the threats. The
conventional codes are very much sensitive
to vulnerabilities so those codes have to be
replaced by secured optimized codes.
Continuous improvement planning should
be encouraged as the cyber criminals are
always using innovative methods in their
attacks. The benefits and the drawbacks
considering the software security is stated
the paper. The paper also helps in
understanding the problems associated with
the security of the software such as Trojan
horse and malware.
References
8
protocols [6].
Conclusion
From the above paper it can be concluded
that the cyber security community plays
huge role in preventing the cyber security
issues which have the capability to destroy
the online assets of the organization. It can
be also concluded that the efforts of the
software security personnel’s should be a bit
more realistic in minimizing the threats. The
conventional codes are very much sensitive
to vulnerabilities so those codes have to be
replaced by secured optimized codes.
Continuous improvement planning should
be encouraged as the cyber criminals are
always using innovative methods in their
attacks. The benefits and the drawbacks
considering the software security is stated
the paper. The paper also helps in
understanding the problems associated with
the security of the software such as Trojan
horse and malware.
References
8

[1] H. Fujita, New trends in software methodologies, tools, and techniques., Amsterdam: IOS
Press, 2010.
[2] D. Ashbaugh, Security software development, Boca Raton: CRC Press, 2009.
[3] J. Vacca, Managing information security, Amsterdam: Syngress, 2014.
[4] E. Amoroso, "Recent Progress in Software Security," IEEE Software, vol. 35, no. 2, pp.
11-13, 2018.
[5] Chou and C. Fan, "Regulatory-based development processes for software security in
nuclear safety systems," Progress in Nuclear Energy, vol. 52, no. 4, pp. 395-402, 2010.
[6] B. Potter, "Software & network security," Network Security, vol. 2004, no. 10, pp. 4-5,
2004.
9
Press, 2010.
[2] D. Ashbaugh, Security software development, Boca Raton: CRC Press, 2009.
[3] J. Vacca, Managing information security, Amsterdam: Syngress, 2014.
[4] E. Amoroso, "Recent Progress in Software Security," IEEE Software, vol. 35, no. 2, pp.
11-13, 2018.
[5] Chou and C. Fan, "Regulatory-based development processes for software security in
nuclear safety systems," Progress in Nuclear Energy, vol. 52, no. 4, pp. 395-402, 2010.
[6] B. Potter, "Software & network security," Network Security, vol. 2004, no. 10, pp. 4-5,
2004.
9
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




