Analyzing the Sony PlayStation Network Security Breach of 2011
VerifiedAdded on 2023/05/31
|22
|1620
|280
Case Study
AI Summary
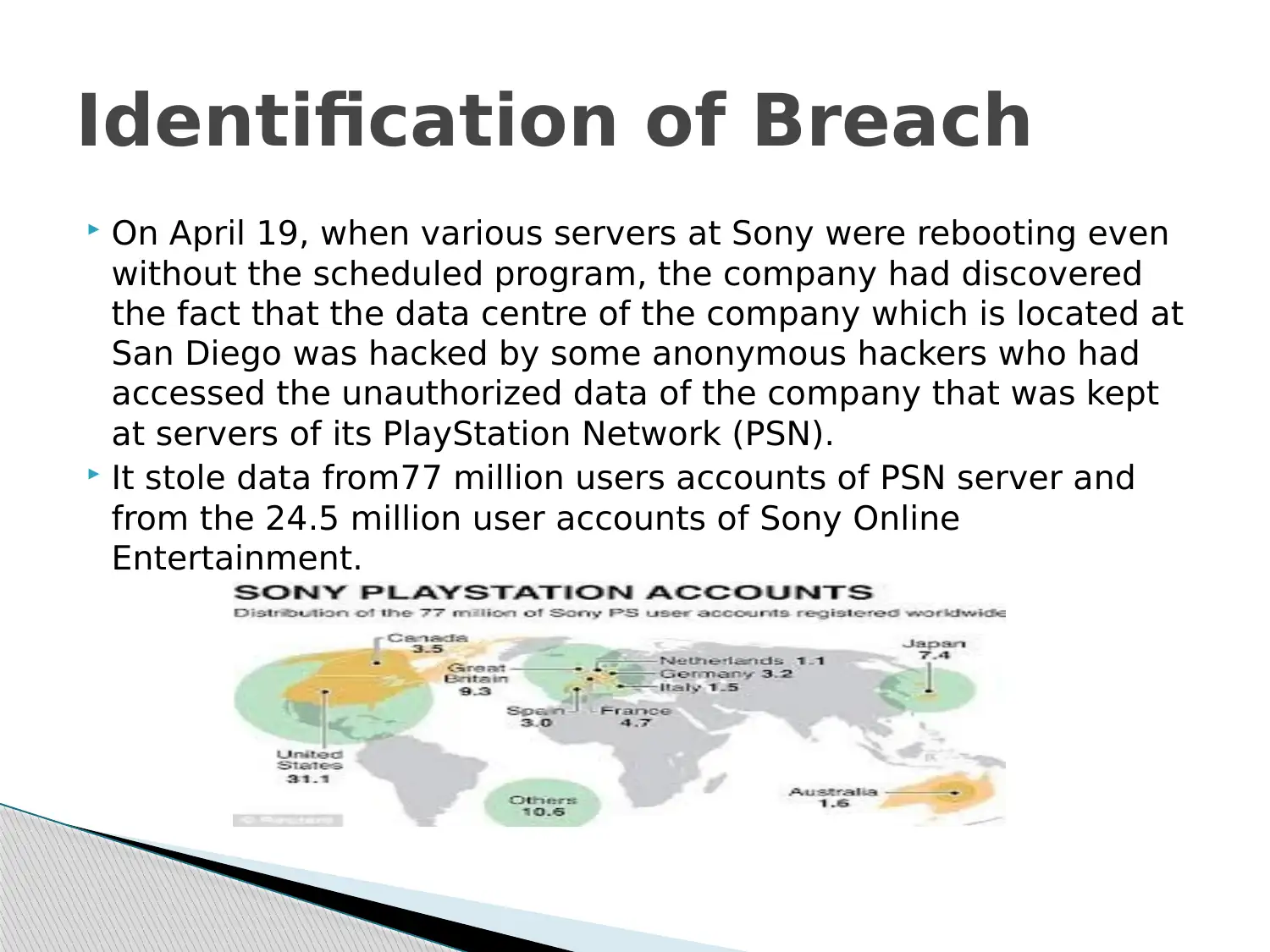
This case study examines the Sony PlayStation Network (PSN) data breach that occurred in April 2011, resulting from an external intrusion aimed at stealing customer data. The breach exploited vulnerabilities in Sony's software, allowing attackers to access the network and steal data from approximately 77 million PSN user accounts and 24.5 million Sony Online Entertainment accounts. The attack involved sophisticated techniques to conceal the intrusion, including deleting log files. The consequences included significant financial losses estimated at $171 million, service shutdowns, and reputational damage. The case study also discusses the customer response to the delayed announcement of the breach and explores potential preventative measures that Sony could have implemented, such as a comprehensive IT security framework, regular security software updates, and advanced intrusion detection systems. It concludes by emphasizing the importance of proactive contingency planning and timely communication in mitigating the impact of such incidents. This document is available on Desklib, a platform offering a range of study tools and solved assignments for students.
1 out of 22

















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)