Detailed Analysis of Security and VPN Technologies: SSL-TLS Report
VerifiedAdded on 2023/01/11
|7
|1448
|24
Report
AI Summary
This report provides a comprehensive overview of SSL-TLS VPN technologies, addressing key aspects of network security. It begins with an introduction to VPNs and SSL, emphasizing their role in establishing secure connections over less secure networks. The report then analyzes how integrity and confidentiality are maintained in SSL communication through the use of symmetric and asymmetric encryption, as well as hash algorithms. It explores various VPN client software options available for organizations. Furthermore, the report delves into the mitigation of anti-replay attacks within SSL communication and outlines strategies firms can employ to protect themselves against SSL attacks. The conclusion summarizes the key findings, highlighting the importance of robust security measures and encryption protocols in safeguarding data and communications. The report references several sources to support its findings, including academic papers and conference proceedings.

SSL-TLS VPN
Technologies
Table of Contents
Technologies
Table of Contents
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction......................................................................................................................................3
Part C...............................................................................................................................................3
Analyse ways in which integrity and confidentiality is attained in SSL communication......3
Explicate role of hash algorithm and symmetric encryption in SSL communication............3
Illustrate VPN client software options...................................................................................5
Part D...............................................................................................................................................5
How anti-replay attacks can be mitigated within SSL communication.................................5
Ways to protect firm against SSL attacks...............................................................................5
Conclusion.......................................................................................................................................6
References........................................................................................................................................7
Part C...............................................................................................................................................3
Analyse ways in which integrity and confidentiality is attained in SSL communication......3
Explicate role of hash algorithm and symmetric encryption in SSL communication............3
Illustrate VPN client software options...................................................................................5
Part D...............................................................................................................................................5
How anti-replay attacks can be mitigated within SSL communication.................................5
Ways to protect firm against SSL attacks...............................................................................5
Conclusion.......................................................................................................................................6
References........................................................................................................................................7

Introduction
The network which is liable for creating safe, encrypted connection on less secured
network like public internet is referred to as VPN (virtual private network). It makes use of
tunnelling protocols for encryption (Aung and Thein, 2020). Secured socket layer (SSL) implies
standard technology that is utilised for keeping internet connection secured when any kind of
sensitive data is being transmitted among two systems for preventing criminals from having
access it. This report comprises of aspects relate with confidentiality, integrity along with anti
replay.
Part C
Analyse ways in which integrity and confidentiality is attained in SSL communication
Secured socket layer is secured session key foundation as well as symmetric key based
activity privacy. Confidentiality within SSL can be attained via aggregation of both the keys i.e.
symmetric and asymmetric encryption that is liable for making sure that complete privacy of
message is being shared. While the process of SSL is being carried out both server as well as
client agree on algorithm encryption which has to be used and share secret key which has to be
used for one session only (Thaseen, Poorva and Ushasree, 2020). The algorithm along with
agreed key will be liable for managing confidentiality of data that is transmitted among SSL and
clients by ensuring that message is not decrypted even in case if it has been intercepted via a
intruder or third person. This also denotes that integrity of text is maintained as intruder is not
able to decrypt the message that implies they can modify or alter it. The added advantage that is
being offered by SSL is that with data confidentiality is that key distribution issues do not occur
as asymmetric algorithms are being used while transmission of secret key. To identify cipher
suite which can be used, the supported cipher suites are being identified and from them weak
ciphers are eradicated to ensure that adequate cipher is being used.
Explicate role of hash algorithm and symmetric encryption in SSL communication
Symmetric encryption is liable for entailing shared secret key encryption. Within such
kind of encryption, a single key is key is utilised for encrypting as well decrypting the messages
(Owada and et. al, 2019). Here, encryption is quick along with this complexity is low which
facilitates secured socket layer protection.
The network which is liable for creating safe, encrypted connection on less secured
network like public internet is referred to as VPN (virtual private network). It makes use of
tunnelling protocols for encryption (Aung and Thein, 2020). Secured socket layer (SSL) implies
standard technology that is utilised for keeping internet connection secured when any kind of
sensitive data is being transmitted among two systems for preventing criminals from having
access it. This report comprises of aspects relate with confidentiality, integrity along with anti
replay.
Part C
Analyse ways in which integrity and confidentiality is attained in SSL communication
Secured socket layer is secured session key foundation as well as symmetric key based
activity privacy. Confidentiality within SSL can be attained via aggregation of both the keys i.e.
symmetric and asymmetric encryption that is liable for making sure that complete privacy of
message is being shared. While the process of SSL is being carried out both server as well as
client agree on algorithm encryption which has to be used and share secret key which has to be
used for one session only (Thaseen, Poorva and Ushasree, 2020). The algorithm along with
agreed key will be liable for managing confidentiality of data that is transmitted among SSL and
clients by ensuring that message is not decrypted even in case if it has been intercepted via a
intruder or third person. This also denotes that integrity of text is maintained as intruder is not
able to decrypt the message that implies they can modify or alter it. The added advantage that is
being offered by SSL is that with data confidentiality is that key distribution issues do not occur
as asymmetric algorithms are being used while transmission of secret key. To identify cipher
suite which can be used, the supported cipher suites are being identified and from them weak
ciphers are eradicated to ensure that adequate cipher is being used.
Explicate role of hash algorithm and symmetric encryption in SSL communication
Symmetric encryption is liable for entailing shared secret key encryption. Within such
kind of encryption, a single key is key is utilised for encrypting as well decrypting the messages
(Owada and et. al, 2019). Here, encryption is quick along with this complexity is low which
facilitates secured socket layer protection.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
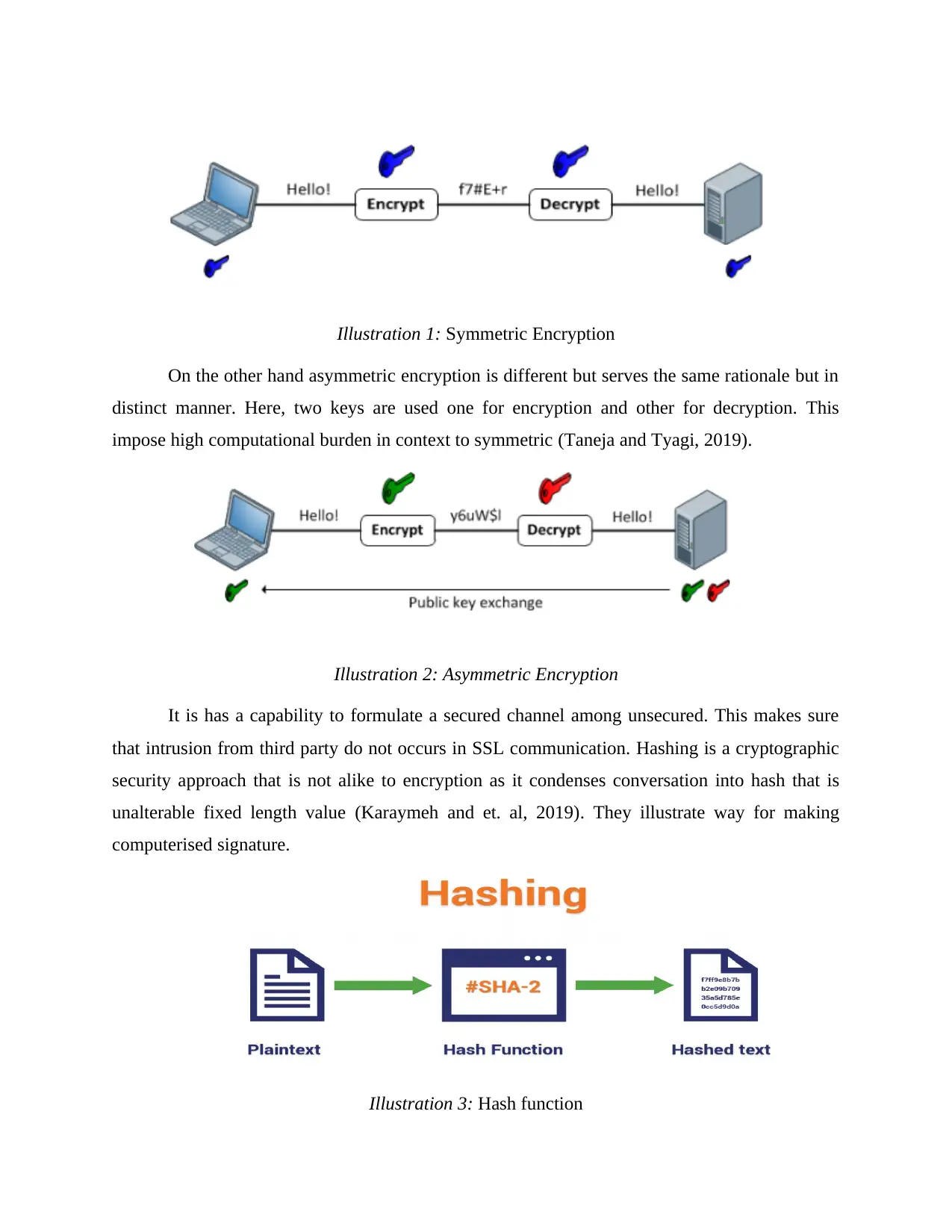
Illustration 1: Symmetric Encryption
On the other hand asymmetric encryption is different but serves the same rationale but in
distinct manner. Here, two keys are used one for encryption and other for decryption. This
impose high computational burden in context to symmetric (Taneja and Tyagi, 2019).
Illustration 2: Asymmetric Encryption
It is has a capability to formulate a secured channel among unsecured. This makes sure
that intrusion from third party do not occurs in SSL communication. Hashing is a cryptographic
security approach that is not alike to encryption as it condenses conversation into hash that is
unalterable fixed length value (Karaymeh and et. al, 2019). They illustrate way for making
computerised signature.
Illustration 3: Hash function
On the other hand asymmetric encryption is different but serves the same rationale but in
distinct manner. Here, two keys are used one for encryption and other for decryption. This
impose high computational burden in context to symmetric (Taneja and Tyagi, 2019).
Illustration 2: Asymmetric Encryption
It is has a capability to formulate a secured channel among unsecured. This makes sure
that intrusion from third party do not occurs in SSL communication. Hashing is a cryptographic
security approach that is not alike to encryption as it condenses conversation into hash that is
unalterable fixed length value (Karaymeh and et. al, 2019). They illustrate way for making
computerised signature.
Illustration 3: Hash function
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Illustrate VPN client software options
There are four VPN client software’s that can be used by organisation, they are VPNs,
MPLS-based L3 VPNs, network based VPNs and Dynamic Multipoint. Client dependent virtual
private network can be normally established among user and their remote networks. Generally,
they are involved within development of applications. Network based VPNs denotes private
network that are liable for securely linking two networks among untrusted network (Aung and
Thein, 2020). For an instance, IPsec based WAN allows business offices to connect with each
device over internet through usage of IPsec tunnels. VPN client software works in peculiar
constraints of operating system which are installed within host computers instead of fact that OS
is integrated like a secondary OS. Some VPN software need to porting for enhancing their
functionalities. There are number of VPN which can be utilised by organisations they are,
PrivateVPN, CyberGhost, PrivateInternetAccess, NordVPN and IPVanish. VPN software can be
connected with routers, mobile or any other internet connected device.
Part D
How anti-replay attacks can be mitigated within SSL communication
The sub-protocol of IPsec which is liable for avoiding third person to inject or alter
packets that are transmitted from source to destination is referred to as anti-replay. Replay
attacks illustrate distinct groups for infiltration network that have relevant effect both online as
well as offline (Thaseen, Poorva and Ushasree, 2020). They are common and are liable for
compromising SSL communication session via performance of fraudulent transaction by making
use of chip based credit cards. For this, SSL has designed various strategies by this it can be
prevented but as such none of them is able to completely solve this. To ensure that messages are
not compromised or tempered, SSL has included both origin as well as destination verification
along with time based encryption. The time stamp is being used for mitigating anti-reply attacks
and it also marks teh label that message has been shared.
Ways to protect firm against SSL attacks
Firms can protect their communication against SSL attacks by different methods, the
initial and basic is usage of standardisation HTTPS which is ubiquitous protocol that assists
within secured communication via internet (Owada and et. al, 2019). It will lead firm to have
secured interaction. The other measure is formulation of strong security measures which can be
There are four VPN client software’s that can be used by organisation, they are VPNs,
MPLS-based L3 VPNs, network based VPNs and Dynamic Multipoint. Client dependent virtual
private network can be normally established among user and their remote networks. Generally,
they are involved within development of applications. Network based VPNs denotes private
network that are liable for securely linking two networks among untrusted network (Aung and
Thein, 2020). For an instance, IPsec based WAN allows business offices to connect with each
device over internet through usage of IPsec tunnels. VPN client software works in peculiar
constraints of operating system which are installed within host computers instead of fact that OS
is integrated like a secondary OS. Some VPN software need to porting for enhancing their
functionalities. There are number of VPN which can be utilised by organisations they are,
PrivateVPN, CyberGhost, PrivateInternetAccess, NordVPN and IPVanish. VPN software can be
connected with routers, mobile or any other internet connected device.
Part D
How anti-replay attacks can be mitigated within SSL communication
The sub-protocol of IPsec which is liable for avoiding third person to inject or alter
packets that are transmitted from source to destination is referred to as anti-replay. Replay
attacks illustrate distinct groups for infiltration network that have relevant effect both online as
well as offline (Thaseen, Poorva and Ushasree, 2020). They are common and are liable for
compromising SSL communication session via performance of fraudulent transaction by making
use of chip based credit cards. For this, SSL has designed various strategies by this it can be
prevented but as such none of them is able to completely solve this. To ensure that messages are
not compromised or tempered, SSL has included both origin as well as destination verification
along with time based encryption. The time stamp is being used for mitigating anti-reply attacks
and it also marks teh label that message has been shared.
Ways to protect firm against SSL attacks
Firms can protect their communication against SSL attacks by different methods, the
initial and basic is usage of standardisation HTTPS which is ubiquitous protocol that assists
within secured communication via internet (Owada and et. al, 2019). It will lead firm to have
secured interaction. The other measure is formulation of strong security measures which can be

attained through setting up servers that will provide their employees or clients with HTTPS
pages which imply a secured transmission of information among firms server and their clients.
Along with this, they can opt for Bit encryption and making use of cookies will lead them to
prevent third party intervention within communication that takes place among different people.
Conclusion
Form the above it can be concluded that secured socket layer refers to a standard security
technology that ia responsible for establishing encrypted link among client and server normally a
website (web server). It has to be ensured that a secured communication occur between two by
which integrity as well as confidentiality of information can be maintained. Anti-replay is liable
for ensuring security of packets but various attacks have been made on them. Firm needs to make
use of adequate policies, encryption and decryption protocols through which such attacks can be
mitigated.
pages which imply a secured transmission of information among firms server and their clients.
Along with this, they can opt for Bit encryption and making use of cookies will lead them to
prevent third party intervention within communication that takes place among different people.
Conclusion
Form the above it can be concluded that secured socket layer refers to a standard security
technology that ia responsible for establishing encrypted link among client and server normally a
website (web server). It has to be ensured that a secured communication occur between two by
which integrity as well as confidentiality of information can be maintained. Anti-replay is liable
for ensuring security of packets but various attacks have been made on them. Firm needs to make
use of adequate policies, encryption and decryption protocols through which such attacks can be
mitigated.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Books & References
Aung, S.T. and Thein, T., 2020, February. Comparative Analysis of Site-to-Site Layer 2 Virtual
Private Networks. In 2020 IEEE Conference on Computer Applications (ICCA) (pp. 1-5).
IEEE.
Thaseen, I.S., Poorva, B. and Ushasree, P.S., 2020, February. Network Intrusion Detection using
Machine Learning Techniques. In 2020 International Conference on Emerging Trends in
Information Technology and Engineering (ic-ETITE) (pp. 1-7). IEEE.
Owada, Y. and et. al, 2019, November. An Implementation of Layer 2 Overlay Mesh Network
and Edge Computing Platform for IoT. In 2019 Twelfth International Conference on
Mobile Computing and Ubiquitous Network (ICMU) (pp. 1-6). IEEE.
Taneja, D. and Tyagi, S.S., 2019, February. Impact of SSL Enabled Collaboration Tool on
Clinical Research. In 2019 International Conference on Machine Learning, Big Data,
Cloud and Parallel Computing (COMITCon) (pp. 549-552). IEEE.
Karaymeh, A. and et. al, 2019, October. Enhancing Data Protection Provided by VPN
Connections over Open WiFi Networks. In 2019 2nd International Conference on new
Trends in Computing Sciences (ICTCS) (pp. 1-6). IEEE.
Books & References
Aung, S.T. and Thein, T., 2020, February. Comparative Analysis of Site-to-Site Layer 2 Virtual
Private Networks. In 2020 IEEE Conference on Computer Applications (ICCA) (pp. 1-5).
IEEE.
Thaseen, I.S., Poorva, B. and Ushasree, P.S., 2020, February. Network Intrusion Detection using
Machine Learning Techniques. In 2020 International Conference on Emerging Trends in
Information Technology and Engineering (ic-ETITE) (pp. 1-7). IEEE.
Owada, Y. and et. al, 2019, November. An Implementation of Layer 2 Overlay Mesh Network
and Edge Computing Platform for IoT. In 2019 Twelfth International Conference on
Mobile Computing and Ubiquitous Network (ICMU) (pp. 1-6). IEEE.
Taneja, D. and Tyagi, S.S., 2019, February. Impact of SSL Enabled Collaboration Tool on
Clinical Research. In 2019 International Conference on Machine Learning, Big Data,
Cloud and Parallel Computing (COMITCon) (pp. 549-552). IEEE.
Karaymeh, A. and et. al, 2019, October. Enhancing Data Protection Provided by VPN
Connections over Open WiFi Networks. In 2019 2nd International Conference on new
Trends in Computing Sciences (ICTCS) (pp. 1-6). IEEE.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



