Database Administrator for Department Store: A Technical Paper
VerifiedAdded on 2023/06/07
|23
|5105
|412
Report
AI Summary
This technical paper discusses the role of a database administrator in managing and designing a database for a department store chain. It covers essential database concepts, including transaction management, concurrency control, and security measures. The paper identifies key entities and attributes within a department store's operations, such as customers, products, and vendors, and establishes business rules for data storage and retrieval. It also explores the use of Crow's Foot notation to illustrate relationships between database entities. Furthermore, the report addresses the integration of Big Data tools for sales and inventory forecasting, highlighting the importance of data analysis in making informed business decisions. The paper also includes discussions on the skills required for database administrators and security vulnerabilities.

Running head: STORE DATABASE MANAGEMENT 1
Database Manager for Store Department
Name
Institution
Course
Date
Introduction
Database Manager for Store Department
Name
Institution
Course
Date
Introduction
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STORE DATABASE MANAGEMENT 2
The database technology has attracted attention to the current businesses. It is commonly
used in large organizations in the storage and transfer of data such as the employee's details;
names, salary, and also the company's product information. The area, however, demands a high
level of knowledge and skills in database designing rather than its operations. A more
professional database designer is more likely to design a database that is easy to maintain. Most
of the organizations have specialization groups of database administrators specialized in
designing and maintaining databases.
The purpose of the research paper is to identify various transactions and probably the
departmental store and the potential sales transaction that can be stored in the database for easy
retrieval when the demand arises or for the update. I will design potential database rules and the
diabase solutions that can be used in the departmental store in performing various tasks such as
the data retrieval and updates. As usual, a database requires relations between the entities for
easy access or transfer of the data, and therefore the database will use the Crow's Foot notation in
showing the relationships. The Crows Foot notation is the most common tools used in showing
many relationships by use of graphical symbols (Clifford, & Bhandari, (2015). The research will
also consider other external sources to identify how the retail stores use the database in
maintaining their customers' information. It will also be essential to determine how such retail
stores retain their customers and increase sales by use of a well-designed database. Moreover,
cloud computing employs the use of a database, and, therefore, the research will also consider
how the data vendors design such a database.
The second part of the research paper will calculate the appropriateness of the use of the
distributed DBMS and identify the best techniques that should be considered in optimizing its
operation in an organization. This may include the use of current technology in designing an
The database technology has attracted attention to the current businesses. It is commonly
used in large organizations in the storage and transfer of data such as the employee's details;
names, salary, and also the company's product information. The area, however, demands a high
level of knowledge and skills in database designing rather than its operations. A more
professional database designer is more likely to design a database that is easy to maintain. Most
of the organizations have specialization groups of database administrators specialized in
designing and maintaining databases.
The purpose of the research paper is to identify various transactions and probably the
departmental store and the potential sales transaction that can be stored in the database for easy
retrieval when the demand arises or for the update. I will design potential database rules and the
diabase solutions that can be used in the departmental store in performing various tasks such as
the data retrieval and updates. As usual, a database requires relations between the entities for
easy access or transfer of the data, and therefore the database will use the Crow's Foot notation in
showing the relationships. The Crows Foot notation is the most common tools used in showing
many relationships by use of graphical symbols (Clifford, & Bhandari, (2015). The research will
also consider other external sources to identify how the retail stores use the database in
maintaining their customers' information. It will also be essential to determine how such retail
stores retain their customers and increase sales by use of a well-designed database. Moreover,
cloud computing employs the use of a database, and, therefore, the research will also consider
how the data vendors design such a database.
The second part of the research paper will calculate the appropriateness of the use of the
distributed DBMS and identify the best techniques that should be considered in optimizing its
operation in an organization. This may include the use of current technology in designing an

STORE DATABASE MANAGEMENT 3
easier database in its maintenance. In this database, fives departments will be generated and two
examples of how uncommitted data and lost updates may occur. The database will also identify
the concurrency control factor vital within the current multiuser environment to ensure any
execution of transactions within such an environment is valid. Due to the security threats on the
database information, the research will also venture into the internet to determine the recovery
and backup solutions and any other security threats to the database that could be applied to the
department (Selinger, 2017).
CIS 515 Week 10 Dis 1
Information professionals with adequate skills are required to maintain the business
continuity of database services in an organization. Identify and assess at least three
professional skills that would be required to be successful database administrators.
According to Sumathi, & Esakkirajan (2017), there are various professional skills
required for a database administrator such as:
Knowledge about the database itself.
Knowledge of database query.
Knowledge of database design.
easier database in its maintenance. In this database, fives departments will be generated and two
examples of how uncommitted data and lost updates may occur. The database will also identify
the concurrency control factor vital within the current multiuser environment to ensure any
execution of transactions within such an environment is valid. Due to the security threats on the
database information, the research will also venture into the internet to determine the recovery
and backup solutions and any other security threats to the database that could be applied to the
department (Selinger, 2017).
CIS 515 Week 10 Dis 1
Information professionals with adequate skills are required to maintain the business
continuity of database services in an organization. Identify and assess at least three
professional skills that would be required to be successful database administrators.
According to Sumathi, & Esakkirajan (2017), there are various professional skills
required for a database administrator such as:
Knowledge about the database itself.
Knowledge of database query.
Knowledge of database design.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STORE DATABASE MANAGEMENT 4
Give your opinion on what the critical nature of a database administrator's role is to IT
industry organizations. Support your answer with specific examples of functions and
responsibilities they perform.
The database administrators help in enhancing data communication. They are tasked with
the responsibility of storing and retrieving data from the database. This data is used to run on the
same or different computer.
They ensure that all the information can be accessed at any time. The administrators are
tasked with the responsibility of running queries on the data stored in the SQL database to extract
information that may be hard to find (McClure, & Kruger 2014, May).
The best database model leads to a more effective function of the industry. The database
designer determines what should be stored in the database and entities to interrelate.
CIS 515 Week 10 Dis 2
Give three security vulnerability and classify each with being technical, managerial,
cultural, or procedural. Provide your rationale.
According to Alhazmi, Malaiya, & Ray (2015), databases are vulnerable to security
threats such:
Stolen database back up. It is a managerial vulnerability of database from both the
external attacker and those within the corporation. The insiders steal the archives including the
database backups.
Deployment Botches. It is a procedural vulnerability that is caused as a result of
ignorance of the installation procedure.
Database feature abuse. It is a technical vulnerability and is associated with a missing
standard feature in the database.
Give your opinion on what the critical nature of a database administrator's role is to IT
industry organizations. Support your answer with specific examples of functions and
responsibilities they perform.
The database administrators help in enhancing data communication. They are tasked with
the responsibility of storing and retrieving data from the database. This data is used to run on the
same or different computer.
They ensure that all the information can be accessed at any time. The administrators are
tasked with the responsibility of running queries on the data stored in the SQL database to extract
information that may be hard to find (McClure, & Kruger 2014, May).
The best database model leads to a more effective function of the industry. The database
designer determines what should be stored in the database and entities to interrelate.
CIS 515 Week 10 Dis 2
Give three security vulnerability and classify each with being technical, managerial,
cultural, or procedural. Provide your rationale.
According to Alhazmi, Malaiya, & Ray (2015), databases are vulnerable to security
threats such:
Stolen database back up. It is a managerial vulnerability of database from both the
external attacker and those within the corporation. The insiders steal the archives including the
database backups.
Deployment Botches. It is a procedural vulnerability that is caused as a result of
ignorance of the installation procedure.
Database feature abuse. It is a technical vulnerability and is associated with a missing
standard feature in the database.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STORE DATABASE MANAGEMENT 5
Suggest specific actions that could be performed to minimize the vulnerabilities. Describe
how often these measures should be performed and the order in which each should be
performed.
The stolen database backups can be mitigated by encrypting the archives frequently to
ensure inaccessibility by both the external and internal attackers within the corporation.
Before the installation, the database should be tested, and the correct procedure of
installation be followed at any time the database is installed. Failure to the test and ignorance in
installation process exposes the database to security attacks (Bireley, 2012).
Any simple errors such as failing to consider certain feature in the database by designers
expose the database to attacks. This can be mitigated by considering all the necessary features
during the time of implementation to keep the database away from any attack.
Suggest specific actions that could be performed to minimize the vulnerabilities. Describe
how often these measures should be performed and the order in which each should be
performed.
The stolen database backups can be mitigated by encrypting the archives frequently to
ensure inaccessibility by both the external and internal attackers within the corporation.
Before the installation, the database should be tested, and the correct procedure of
installation be followed at any time the database is installed. Failure to the test and ignorance in
installation process exposes the database to security attacks (Bireley, 2012).
Any simple errors such as failing to consider certain feature in the database by designers
expose the database to attacks. This can be mitigated by considering all the necessary features
during the time of implementation to keep the database away from any attack.

STORE DATABASE MANAGEMENT 6
Assignment
Transaction in the department store and potentials sales stored in database
Due to the current market activity which may project the increase in sales, there is the
need to design a comprehensive relational database for several new stores. In the mission to
design a useful database, several factors should be weight depending on the nature of the
database and its intended functions. After keenly analyzing all the transaction or activities to be
performed in every store department, a list of major entities can be developed to help ensure the
success of the transaction from one department to another. According to Starkey (2012), the
transactions that are performed in each department include.
Every core entity in the database will include other attributes whose information is
relevant to that department and this will make it easier to display the data in a hierarchical nature.
The main attributes contained in each entity are as shown below:
Assignment
Transaction in the department store and potentials sales stored in database
Due to the current market activity which may project the increase in sales, there is the
need to design a comprehensive relational database for several new stores. In the mission to
design a useful database, several factors should be weight depending on the nature of the
database and its intended functions. After keenly analyzing all the transaction or activities to be
performed in every store department, a list of major entities can be developed to help ensure the
success of the transaction from one department to another. According to Starkey (2012), the
transactions that are performed in each department include.
Every core entity in the database will include other attributes whose information is
relevant to that department and this will make it easier to display the data in a hierarchical nature.
The main attributes contained in each entity are as shown below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
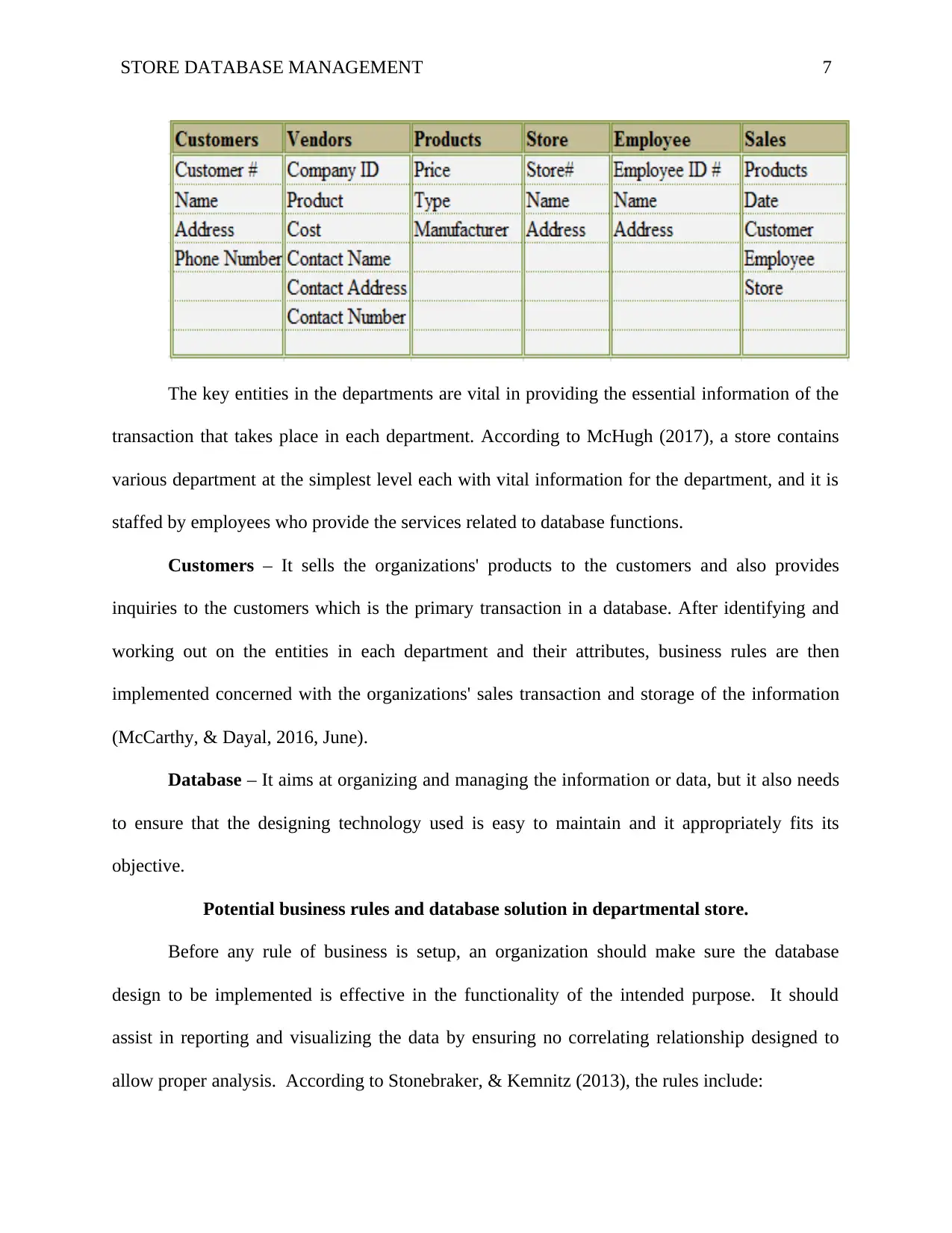
STORE DATABASE MANAGEMENT 7
The key entities in the departments are vital in providing the essential information of the
transaction that takes place in each department. According to McHugh (2017), a store contains
various department at the simplest level each with vital information for the department, and it is
staffed by employees who provide the services related to database functions.
Customers – It sells the organizations' products to the customers and also provides
inquiries to the customers which is the primary transaction in a database. After identifying and
working out on the entities in each department and their attributes, business rules are then
implemented concerned with the organizations' sales transaction and storage of the information
(McCarthy, & Dayal, 2016, June).
Database – It aims at organizing and managing the information or data, but it also needs
to ensure that the designing technology used is easy to maintain and it appropriately fits its
objective.
Potential business rules and database solution in departmental store.
Before any rule of business is setup, an organization should make sure the database
design to be implemented is effective in the functionality of the intended purpose. It should
assist in reporting and visualizing the data by ensuring no correlating relationship designed to
allow proper analysis. According to Stonebraker, & Kemnitz (2013), the rules include:
The key entities in the departments are vital in providing the essential information of the
transaction that takes place in each department. According to McHugh (2017), a store contains
various department at the simplest level each with vital information for the department, and it is
staffed by employees who provide the services related to database functions.
Customers – It sells the organizations' products to the customers and also provides
inquiries to the customers which is the primary transaction in a database. After identifying and
working out on the entities in each department and their attributes, business rules are then
implemented concerned with the organizations' sales transaction and storage of the information
(McCarthy, & Dayal, 2016, June).
Database – It aims at organizing and managing the information or data, but it also needs
to ensure that the designing technology used is easy to maintain and it appropriately fits its
objective.
Potential business rules and database solution in departmental store.
Before any rule of business is setup, an organization should make sure the database
design to be implemented is effective in the functionality of the intended purpose. It should
assist in reporting and visualizing the data by ensuring no correlating relationship designed to
allow proper analysis. According to Stonebraker, & Kemnitz (2013), the rules include:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STORE DATABASE MANAGEMENT 8
Rule 1: Various codes are programmed to direct specific activities in each department.
Due to a large number of stores that sells products, there are constraints that are associated with
the transactions, and therefore only the assigned codes in each store are permitted as valid.
Rule 2: The relationship constraints within the database will be vital in ensuring that each
of the four vendors has an equal chance of supplying a product and they will only be able to
supply at least one product at a time. The rule will still, hold even if there is legacy or
discontinued vendors or products.
Entity relationship using the Crow's Foot notation.
After identifying the rules that should be applied in the database implementation, the next
step is to design the relationship among the database entities (Lohman et al., 2012). This
relationship should also consider the type of the transaction that will be shared by the two or
more entities. The relationship between the entities will be the key determinant for the effective
functioning of the database such as the data transfer from one entity to another, and, therefore, it
requires accuracy and keenness. We can state that the products and services are sold to
customers, and the customers buy the products and services. However, this does not show each
cardinality's relationship.
For an instant, how many sales transaction are carried out in a single store? By following
this procedure, it will, therefore, be easy to identify all the relationships in the six entities. Since
in the database we have six entities, they will all relate to one another giving a total of 30
relationships. According to Hanson (2015, June), the relationships are shown in the table below:
Rule 1: Various codes are programmed to direct specific activities in each department.
Due to a large number of stores that sells products, there are constraints that are associated with
the transactions, and therefore only the assigned codes in each store are permitted as valid.
Rule 2: The relationship constraints within the database will be vital in ensuring that each
of the four vendors has an equal chance of supplying a product and they will only be able to
supply at least one product at a time. The rule will still, hold even if there is legacy or
discontinued vendors or products.
Entity relationship using the Crow's Foot notation.
After identifying the rules that should be applied in the database implementation, the next
step is to design the relationship among the database entities (Lohman et al., 2012). This
relationship should also consider the type of the transaction that will be shared by the two or
more entities. The relationship between the entities will be the key determinant for the effective
functioning of the database such as the data transfer from one entity to another, and, therefore, it
requires accuracy and keenness. We can state that the products and services are sold to
customers, and the customers buy the products and services. However, this does not show each
cardinality's relationship.
For an instant, how many sales transaction are carried out in a single store? By following
this procedure, it will, therefore, be easy to identify all the relationships in the six entities. Since
in the database we have six entities, they will all relate to one another giving a total of 30
relationships. According to Hanson (2015, June), the relationships are shown in the table below:

STORE DATABASE MANAGEMENT 9
Based on the six entities by five relationships, then the relationship has been captured
successfully. Next is to determine the cardinality of the relationship among the entities and
represent it graphically to define the relationship clearly. According to Stonebraker, Rowe, &
Hirohama (2011), each relationship is expressed as;
Based on the six entities by five relationships, then the relationship has been captured
successfully. Next is to determine the cardinality of the relationship among the entities and
represent it graphically to define the relationship clearly. According to Stonebraker, Rowe, &
Hirohama (2011), each relationship is expressed as;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STORE DATABASE MANAGEMENT 10
One to One (1:1)
1 to Many (1: N)
Many to 1 (N:1)
Many to Many (N: N).
One to One (1:1)
1 to Many (1: N)
Many to 1 (N:1)
Many to Many (N: N).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
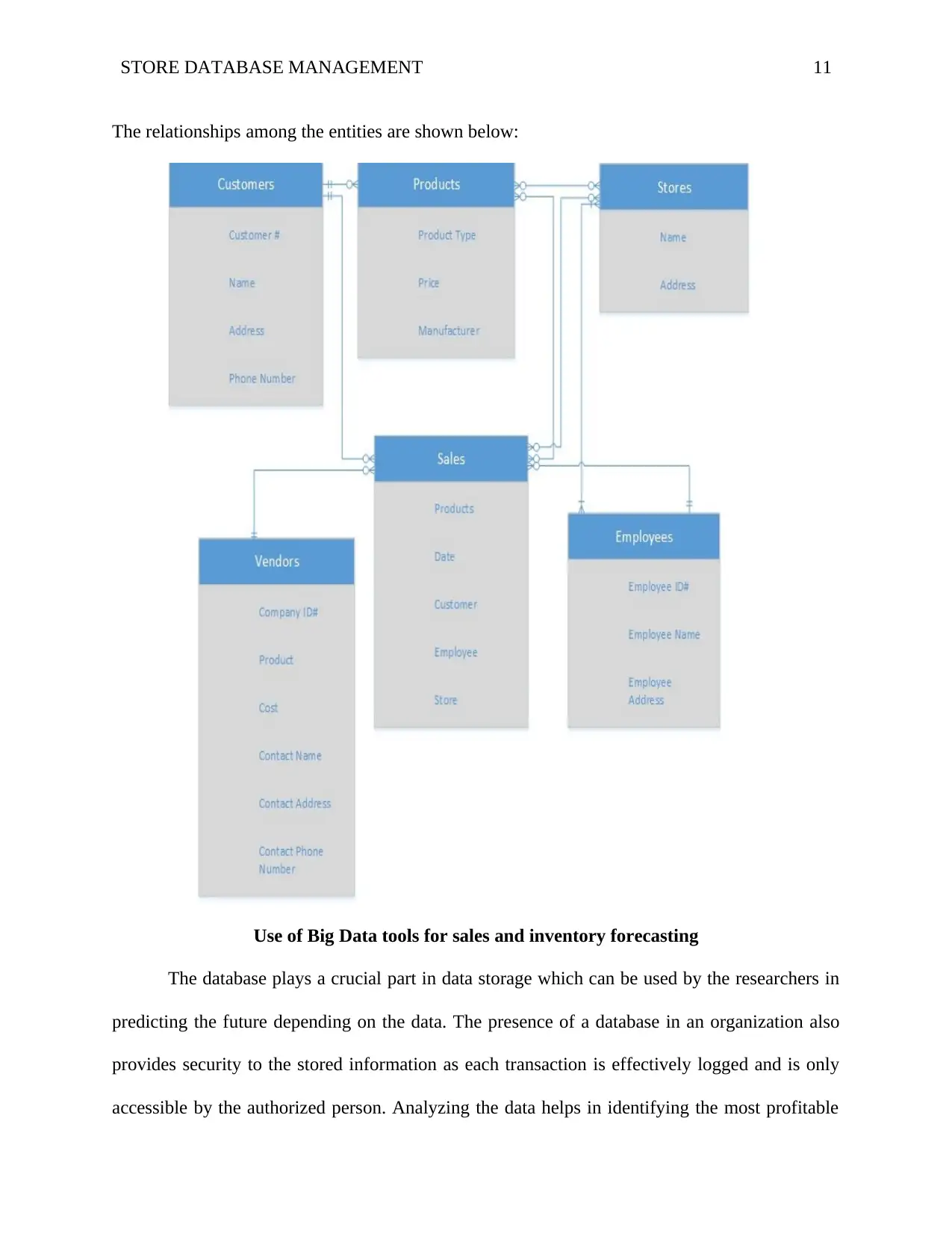
STORE DATABASE MANAGEMENT 11
The relationships among the entities are shown below:
Use of Big Data tools for sales and inventory forecasting
The database plays a crucial part in data storage which can be used by the researchers in
predicting the future depending on the data. The presence of a database in an organization also
provides security to the stored information as each transaction is effectively logged and is only
accessible by the authorized person. Analyzing the data helps in identifying the most profitable
The relationships among the entities are shown below:
Use of Big Data tools for sales and inventory forecasting
The database plays a crucial part in data storage which can be used by the researchers in
predicting the future depending on the data. The presence of a database in an organization also
provides security to the stored information as each transaction is effectively logged and is only
accessible by the authorized person. Analyzing the data helps in identifying the most profitable

STORE DATABASE MANAGEMENT 12
customers and the frequencies at which the customers buy from the department (Gehani, &
Jagadish, 2015, September). This will also be an opportunity for identifying the weaker area and
therefore applying the best strategy to increase the sales volume. There is also access for the
information concerning the customers who have only purchased the products ones, and this will
help in identifying the reason behind the customers not revisiting the store so as to solve the
problem. Perhaps there may be either compelling competing officer or a bad customer
experience.
With the implementation of the database, the customers or sales related issues are
represented to the sales and marketing teams. This team in turn makes the decision concerning
the current customer stand in the business which is vital for the organization. The extraction of
the data for the analysis also requires the database administrators. The growth of an organization
means that the database will have to grow in size, therefore, presenting the information in many
proportions. Due to the extensive database data, it, therefore, becomes difficult in analyzing a
large amount of data using the conventional database management tools and thus the Big Data
tools are considered more effective (Stonebraker, 2012). Given the constant updating stream of
the information in each table and the live nature of the database, the Big Data tool is more
considered due to its ability in manipulating and extrapolating a large amount of data (Widom, &
Finkelstein, 2011, May). The Big Data tool such as the Jaspersoft's BI Suit helps in retrieving a
large amount of data from any SQL table, and, therefore, the tool will be used to retrieve and
collect the data in accordance to the organizations' requirements. The information retrieved using
the tool allows the presentation of the data in the form of graphs and PDF which accelerates the
analysis and presentation of the analyzed report compared to the conventional reporting methods
(Lamb, 2016).
customers and the frequencies at which the customers buy from the department (Gehani, &
Jagadish, 2015, September). This will also be an opportunity for identifying the weaker area and
therefore applying the best strategy to increase the sales volume. There is also access for the
information concerning the customers who have only purchased the products ones, and this will
help in identifying the reason behind the customers not revisiting the store so as to solve the
problem. Perhaps there may be either compelling competing officer or a bad customer
experience.
With the implementation of the database, the customers or sales related issues are
represented to the sales and marketing teams. This team in turn makes the decision concerning
the current customer stand in the business which is vital for the organization. The extraction of
the data for the analysis also requires the database administrators. The growth of an organization
means that the database will have to grow in size, therefore, presenting the information in many
proportions. Due to the extensive database data, it, therefore, becomes difficult in analyzing a
large amount of data using the conventional database management tools and thus the Big Data
tools are considered more effective (Stonebraker, 2012). Given the constant updating stream of
the information in each table and the live nature of the database, the Big Data tool is more
considered due to its ability in manipulating and extrapolating a large amount of data (Widom, &
Finkelstein, 2011, May). The Big Data tool such as the Jaspersoft's BI Suit helps in retrieving a
large amount of data from any SQL table, and, therefore, the tool will be used to retrieve and
collect the data in accordance to the organizations' requirements. The information retrieved using
the tool allows the presentation of the data in the form of graphs and PDF which accelerates the
analysis and presentation of the analyzed report compared to the conventional reporting methods
(Lamb, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



