Applied Science: Managing Data with LIMS and Data Protection Act
VerifiedAdded on 2023/06/03
|12
|1844
|283
Report
AI Summary
This report provides a detailed overview of Laboratory Information Management Systems (LIMS) and their role in managing and protecting scientific data, particularly in the context of applied science. It begins by describing the procedure for storing scientific information in a LIMS, using examples from a crime scene to illustrate the types of data that can be stored, such as fingerprint analysis, blood group information, substance composition, bite mark details, and hair/fiber characteristics. The report then outlines three key strategies for protecting information within a LIMS database: implementing robust password policies, utilizing encryption systems, and regularly monitoring and auditing database access. Furthermore, it explains the significance of the Data Protection Act (DPA) in the UK, emphasizing its principles of fairness, transparency, and accountability in data usage, and provides screenshots demonstrating how data related to samples and patients can be stored in LIMS databases. Finally, the report highlights the advantages of using LIMS, including the elimination of manual errors, real-time monitoring capabilities, time savings, revenue increases, inventory alerts, reduced stress for personnel, enhanced data security through centralized storage and authentication, and the reduction of redundant data. The report concludes by referencing relevant academic literature and patents to support its findings.

Running head: HEALTH AND SAFETY- APPLIED SCIENCE
Health and Safety- Applied Science
Name of the Student
Name of the University
Author Note
Health and Safety- Applied Science
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1HEALTH AND SAFETY- APPLIED SCIENCE
Task 1: Description of the procedure for storing scientific information in a Laboratory
Information Management System
Laboratory Information Management System (LIMS) is software that helps in the
effective management of data related to laboratory samples and results and thus automates
workflows and data flows, integrate instruments as well as manage data (Craig et al. 2017).
For example, in a crime scene where evidence such as fingerprint, blood droplet,
white substance and a yellow fluid, bite mark on victim and a hair and fiber sample has been
collected, the data related to the samples can be stored in the LMS system. The poster below
illustrates what information can be stored in the LIMS pertaining to these samples.
Task 1: Description of the procedure for storing scientific information in a Laboratory
Information Management System
Laboratory Information Management System (LIMS) is software that helps in the
effective management of data related to laboratory samples and results and thus automates
workflows and data flows, integrate instruments as well as manage data (Craig et al. 2017).
For example, in a crime scene where evidence such as fingerprint, blood droplet,
white substance and a yellow fluid, bite mark on victim and a hair and fiber sample has been
collected, the data related to the samples can be stored in the LMS system. The poster below
illustrates what information can be stored in the LIMS pertaining to these samples.

2HEALTH AND SAFETY- APPLIED SCIENCE
Fingerprint:
Data related to fingerprints that can be stored in the LIMS includes: Fingerprint image,
Fingerprint pattern analysis including the arches, and whorls, as well as bifurcations, dots and
ridge endings. Also individual identities corresponding to fingerprints can also be stored.
Blood Droplet:
Data related to blood droplets can include the blood group and Rhesus factor.
White Substance:
Viscosity of the substance, source of the substance and composition of the substance are vital data
related to the white substance that can be stored in the LMS.
Yellow Fluid:
Density of the fluid, composition of the fluid and the chemical properties of the fluid are the
important information of the yellowish fluid that can be stored.
Bite Mark on Victim:
Data related to the size and location of the bite mark, nature of the bite, extent of damage caused
by the bite, signs of infection around the bite mark and the image of the bite mark are important
data that can be stored on the LIMS.
Hair and Fiber Sample:
Data such as the size and thickness of the fiber, DNA profile of the hair, source of the fiber, where
the hair or fiber was found along with an image are important data that can be stored in the LMS.
Fingerprint:
Data related to fingerprints that can be stored in the LIMS includes: Fingerprint image,
Fingerprint pattern analysis including the arches, and whorls, as well as bifurcations, dots and
ridge endings. Also individual identities corresponding to fingerprints can also be stored.
Blood Droplet:
Data related to blood droplets can include the blood group and Rhesus factor.
White Substance:
Viscosity of the substance, source of the substance and composition of the substance are vital data
related to the white substance that can be stored in the LMS.
Yellow Fluid:
Density of the fluid, composition of the fluid and the chemical properties of the fluid are the
important information of the yellowish fluid that can be stored.
Bite Mark on Victim:
Data related to the size and location of the bite mark, nature of the bite, extent of damage caused
by the bite, signs of infection around the bite mark and the image of the bite mark are important
data that can be stored on the LIMS.
Hair and Fiber Sample:
Data such as the size and thickness of the fiber, DNA profile of the hair, source of the fiber, where
the hair or fiber was found along with an image are important data that can be stored in the LMS.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3HEALTH AND SAFETY- APPLIED SCIENCE
Three Strategies to protect Information on the LIMS Database:
1. Password Policies: It is vital to have effective password policies to secure access to
the LIMS database in order to secure the passwords are of required length and
complexity and are changed after a fixed time period (Wang et al. 2015).
2. Using encryption systems for the database to prevent hacking of information and
ensuring better security (Thakkar 2015; Boneh et al. 2015).
3. Regularly monitoring and auditing database access in order to identify any potential
data breaches (Kirti et al. 2017).
Task 2: Explanation of the process involved in storing information in a scientific
workplace
Data protection Act (DPA) in an act passed in the United Kingdom in 1988 which
outlined how personal information and customer information is used by an organization and
how the data needs to be stored and shared (Townend 2017). It aims to protect people whose
data is being stored, ensuring privacy of the data and preventing its misuse by others as well
as implementing liability of the organizations for effective management of the data. The
significance of the act is that it ensures that the information is used fairly, legally and with
transparency as well as implements accountability of how the data is being used (Carey
2018).
The screenshots below shows how data related to samples can be stored in the LIMS
database:
Screenshot 1:
Three Strategies to protect Information on the LIMS Database:
1. Password Policies: It is vital to have effective password policies to secure access to
the LIMS database in order to secure the passwords are of required length and
complexity and are changed after a fixed time period (Wang et al. 2015).
2. Using encryption systems for the database to prevent hacking of information and
ensuring better security (Thakkar 2015; Boneh et al. 2015).
3. Regularly monitoring and auditing database access in order to identify any potential
data breaches (Kirti et al. 2017).
Task 2: Explanation of the process involved in storing information in a scientific
workplace
Data protection Act (DPA) in an act passed in the United Kingdom in 1988 which
outlined how personal information and customer information is used by an organization and
how the data needs to be stored and shared (Townend 2017). It aims to protect people whose
data is being stored, ensuring privacy of the data and preventing its misuse by others as well
as implementing liability of the organizations for effective management of the data. The
significance of the act is that it ensures that the information is used fairly, legally and with
transparency as well as implements accountability of how the data is being used (Carey
2018).
The screenshots below shows how data related to samples can be stored in the LIMS
database:
Screenshot 1:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4HEALTH AND SAFETY- APPLIED SCIENCE
This screenshot from SmartGene LIMS database shows the fields which can be used
to identify the database entry based upon the cohort, patient label, study type and date stamps.
These fields after being filled up can be saved and then used for searches.
Screenshot 2:
This screenshot from SmartGene LIMS database shows the fields which can be used
to identify the database entry based upon the cohort, patient label, study type and date stamps.
These fields after being filled up can be saved and then used for searches.
Screenshot 2:

5HEALTH AND SAFETY- APPLIED SCIENCE
This screenshot is for an electronic health record database, which shows the fields
related to patient, which needs to be entered and saved.
Screenshot 3:
The screenshot above shows information related to the lab test, with the report on the
samples which can be entered one at a time, related to the lab samples.
Screenshot 4:
This screenshot is for an electronic health record database, which shows the fields
related to patient, which needs to be entered and saved.
Screenshot 3:
The screenshot above shows information related to the lab test, with the report on the
samples which can be entered one at a time, related to the lab samples.
Screenshot 4:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
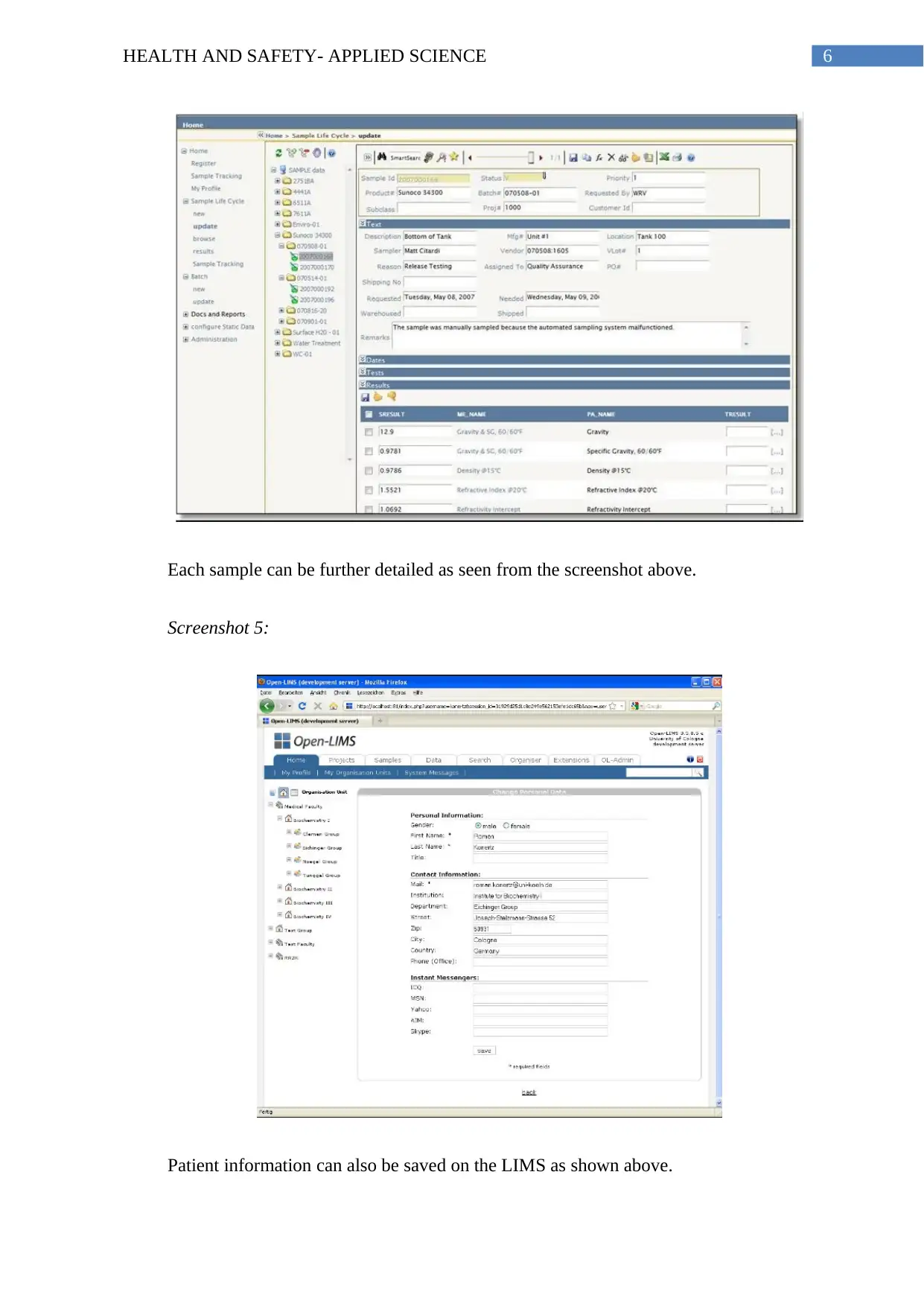
6HEALTH AND SAFETY- APPLIED SCIENCE
Each sample can be further detailed as seen from the screenshot above.
Screenshot 5:
Patient information can also be saved on the LIMS as shown above.
Each sample can be further detailed as seen from the screenshot above.
Screenshot 5:
Patient information can also be saved on the LIMS as shown above.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7HEALTH AND SAFETY- APPLIED SCIENCE
Examples of LMS Databases:
1. Smart GENE
2. Open LIMS
3. Elab
4. LabWare LIMS
5. Clinsis
6. Darwin
Task 3: Advantages gained by keeping data and records on a laboratory management
information systems
Laboratory Information Management Systems us a form of database system that helps
in the effective storage and sharing of laboratory information such as information on samples,
patient data and clinical research findings in an effective, structured and secured manner that
complies to the regulations of the Data Protection Act. The main advantages of LIMS
include:
It eliminates manual errors:
Due to a structured data entry in which only specific data types can be entered in
specific fields and giving error alerts if an incorrect data is being entered can greatly reduce
manual errors while filling up the database. Thus this helps to overcome manual errors of
data entry and optimize the management of the database (Showalter et al. 2014).
Helps in real-time monitoring:
Due to the real time entry and update of data, the database also allows real time data
monitoring, as the database administrators can check the information being entered and
Examples of LMS Databases:
1. Smart GENE
2. Open LIMS
3. Elab
4. LabWare LIMS
5. Clinsis
6. Darwin
Task 3: Advantages gained by keeping data and records on a laboratory management
information systems
Laboratory Information Management Systems us a form of database system that helps
in the effective storage and sharing of laboratory information such as information on samples,
patient data and clinical research findings in an effective, structured and secured manner that
complies to the regulations of the Data Protection Act. The main advantages of LIMS
include:
It eliminates manual errors:
Due to a structured data entry in which only specific data types can be entered in
specific fields and giving error alerts if an incorrect data is being entered can greatly reduce
manual errors while filling up the database. Thus this helps to overcome manual errors of
data entry and optimize the management of the database (Showalter et al. 2014).
Helps in real-time monitoring:
Due to the real time entry and update of data, the database also allows real time data
monitoring, as the database administrators can check the information being entered and

8HEALTH AND SAFETY- APPLIED SCIENCE
identify any possible mistakes in the data, thereby further improving data accuracy (Zhang et
al. 2015).
Saves time:
Due to the structured process of data entry, time is also saved as the data entry
operators can optimize the process of adding new information and avoiding any errors in data
entry. Also, due to the automated updating of the data, time is also saved by avoiding
unnecessary duplication of data and faster searching and indexing of information.
Increases Revenues:
Because of the better output, reduced errors and better accuracy of the data, the
productivity of the organization managing the data can also be enhanced thereby helping to
manage a larger data in a more efficient manner thus increasing their revenues (McGrowder
and Bishop 2015).
Implementing Inventory Alerts:
Automated alerts can also be set on the data, which can be triggered every time a new
data is being added, thus helping the database managers to keep a track of all the changes
made to the data and maintain a database history (Zhang et al. 2015).
Reduced stress:
The improved efficiency can also reduce the stress among the workforce, helping
them to retrieve and store information in a more effective manner (Showalter et al. 2014).
Better Security of data:
The centralized data storage helps to implement centralized security of the data, and
also manage the security in an easier manner. Through centralized authentication of users, the
identify any possible mistakes in the data, thereby further improving data accuracy (Zhang et
al. 2015).
Saves time:
Due to the structured process of data entry, time is also saved as the data entry
operators can optimize the process of adding new information and avoiding any errors in data
entry. Also, due to the automated updating of the data, time is also saved by avoiding
unnecessary duplication of data and faster searching and indexing of information.
Increases Revenues:
Because of the better output, reduced errors and better accuracy of the data, the
productivity of the organization managing the data can also be enhanced thereby helping to
manage a larger data in a more efficient manner thus increasing their revenues (McGrowder
and Bishop 2015).
Implementing Inventory Alerts:
Automated alerts can also be set on the data, which can be triggered every time a new
data is being added, thus helping the database managers to keep a track of all the changes
made to the data and maintain a database history (Zhang et al. 2015).
Reduced stress:
The improved efficiency can also reduce the stress among the workforce, helping
them to retrieve and store information in a more effective manner (Showalter et al. 2014).
Better Security of data:
The centralized data storage helps to implement centralized security of the data, and
also manage the security in an easier manner. Through centralized authentication of users, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9HEALTH AND SAFETY- APPLIED SCIENCE
database administrators can ensure access to only authorized personnel thereby improving
data security (Zhang et al. 2015).
Reduces redundant data:
Centralized data storage also prevents redundancy of data as only one cope of the data
needs to be maintained that can be shared with or accessed by multiple users thereby
optimizing storage space and retrieval time (McGrowder and Bishop 2015).
database administrators can ensure access to only authorized personnel thereby improving
data security (Zhang et al. 2015).
Reduces redundant data:
Centralized data storage also prevents redundancy of data as only one cope of the data
needs to be maintained that can be shared with or accessed by multiple users thereby
optimizing storage space and retrieval time (McGrowder and Bishop 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10HEALTH AND SAFETY- APPLIED SCIENCE
References:
Boneh, D., Lewi, K., Raykova, M., Sahai, A., Zhandry, M. and Zimmerman, J., 2015, April.
Semantically secure order-revealing encryption: Multi-input functional encryption without
obfuscation. In Annual International Conference on the Theory and Applications of
Cryptographic Techniques (pp. 563-594). Springer, Berlin, Heidelberg.
Carey, P., 2018. Data protection: a practical guide to UK and EU law. Oxford University
Press, Inc..
Craig, T., Holland, R., D’Amore, R., Johnson, J.R., McCue, H.V., West, A., Zulkower, V.,
Tekotte, H., Cai, Y., Swan, D. and Davey, R.P., 2017. Leaf LIMS: A Flexible Laboratory
Information Management System with a Synthetic Biology Focus. ACS synthetic biology,
6(12), pp.2273-2280.
Kirti, G., Gupta, R., Biswas, K. and Turlapati, R.R.S., Oracle International Corp, 2017.
Techniques for cloud security monitoring and threat intelligence. U.S. Patent Application
15/632,174.
McGrowder, D. and Bishop, R., 2015. An evaluation of laboratory information systems in
medical laboratories in Jamaica. In Laboratory Management Information Systems: Current
Requirements and Future Perspectives (pp. 280-296). IGI Global.
Showalter, W. and Larson, A.L., Ventana Medical Systems Inc, 2014. Laboratory
instrumentation information management and control network. U.S. Patent 8,812,329.
Thakkar, J., 2015. KEYWORDS: Database, Security, Encryption, Access Control. Database
Security & Encryption: A Survey Study, (56).
References:
Boneh, D., Lewi, K., Raykova, M., Sahai, A., Zhandry, M. and Zimmerman, J., 2015, April.
Semantically secure order-revealing encryption: Multi-input functional encryption without
obfuscation. In Annual International Conference on the Theory and Applications of
Cryptographic Techniques (pp. 563-594). Springer, Berlin, Heidelberg.
Carey, P., 2018. Data protection: a practical guide to UK and EU law. Oxford University
Press, Inc..
Craig, T., Holland, R., D’Amore, R., Johnson, J.R., McCue, H.V., West, A., Zulkower, V.,
Tekotte, H., Cai, Y., Swan, D. and Davey, R.P., 2017. Leaf LIMS: A Flexible Laboratory
Information Management System with a Synthetic Biology Focus. ACS synthetic biology,
6(12), pp.2273-2280.
Kirti, G., Gupta, R., Biswas, K. and Turlapati, R.R.S., Oracle International Corp, 2017.
Techniques for cloud security monitoring and threat intelligence. U.S. Patent Application
15/632,174.
McGrowder, D. and Bishop, R., 2015. An evaluation of laboratory information systems in
medical laboratories in Jamaica. In Laboratory Management Information Systems: Current
Requirements and Future Perspectives (pp. 280-296). IGI Global.
Showalter, W. and Larson, A.L., Ventana Medical Systems Inc, 2014. Laboratory
instrumentation information management and control network. U.S. Patent 8,812,329.
Thakkar, J., 2015. KEYWORDS: Database, Security, Encryption, Access Control. Database
Security & Encryption: A Survey Study, (56).

11HEALTH AND SAFETY- APPLIED SCIENCE
Townend, J., 2017. Data protection and the ‘right to be forgotten’in practice: A UK
perspective. International Journal of Legal Information, 45(1), pp.28-33.
Wang, P., Ali, A. and Kelly, W., 2015, August. Data security and threat modeling for smart
city infrastructure. In Cyber Security of Smart Cities, Industrial Control System and
Communications (SSIC), 2015 International Conference on (pp. 1-6). IEEE.
Zhang, Y., Zhang, G., Wang, J., Sun, S., Si, S. and Yang, T., 2015. Real-time information
capturing and integration framework of the internet of manufacturing things. International
Journal of Computer Integrated Manufacturing, 28(8), pp.811-822.
Townend, J., 2017. Data protection and the ‘right to be forgotten’in practice: A UK
perspective. International Journal of Legal Information, 45(1), pp.28-33.
Wang, P., Ali, A. and Kelly, W., 2015, August. Data security and threat modeling for smart
city infrastructure. In Cyber Security of Smart Cities, Industrial Control System and
Communications (SSIC), 2015 International Conference on (pp. 1-6). IEEE.
Zhang, Y., Zhang, G., Wang, J., Sun, S., Si, S. and Yang, T., 2015. Real-time information
capturing and integration framework of the internet of manufacturing things. International
Journal of Computer Integrated Manufacturing, 28(8), pp.811-822.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.