Strategic Information Security in Healthcare: A Comprehensive Report
VerifiedAdded on 2020/07/22
|14
|3454
|25
Report
AI Summary
This report provides a detailed analysis of strategic information security within healthcare organizations, specifically focusing on the National Health Service (NHS). It explores the critical importance of maintaining data confidentiality, integrity, and availability to ensure the success and growth of healthcare enterprises. The report covers key aspects such as health information privacy, security program development, and the proactive identification of security and privacy requirements. It emphasizes the role of information security policies, the phases of policy development, and the implementation of HIPAA compliance. Furthermore, the report discusses layered approaches to privacy and security, including administrative, physical, and technical controls, and highlights the significance of risk management and staff training. The report concludes by underscoring the need for robust security measures, advanced encryption standards, and anti-theft applications to protect sensitive patient data and maintain trust within the healthcare system. The report also focuses on maintaining data integrity and confidentiality for the security of the patient.

STRATEGIC
INFORMATION
SECURITY
INFORMATION
SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
STRATEGIC INFORMATION SECURITY..................................................................................1
INTRODUCTION...........................................................................................................................1
Main body........................................................................................................................................1
Health information and matters related to the privacy and security-..........................................1
Information security programme.................................................................................................1
Proper identification of the security and the privacy requirements............................................2
Information security policy.........................................................................................................3
Phases of the security policy development.................................................................................3
The system checked as per the accordance with the HIPPA compliance- .................................4
Layered approach to privacy and security..................................................................................4
Risk management assessment process........................................................................................6
Increasing of information security with management of roles and responsibility.....................7
CONCLUSION................................................................................................................................9
REFERENCES................................................................................................................................2
STRATEGIC INFORMATION SECURITY..................................................................................1
INTRODUCTION...........................................................................................................................1
Main body........................................................................................................................................1
Health information and matters related to the privacy and security-..........................................1
Information security programme.................................................................................................1
Proper identification of the security and the privacy requirements............................................2
Information security policy.........................................................................................................3
Phases of the security policy development.................................................................................3
The system checked as per the accordance with the HIPPA compliance- .................................4
Layered approach to privacy and security..................................................................................4
Risk management assessment process........................................................................................6
Increasing of information security with management of roles and responsibility.....................7
CONCLUSION................................................................................................................................9
REFERENCES................................................................................................................................2

INTRODUCTION
The term strategic information security defines objectives of an organisation. To maintain
confidentiality of matter relating to business enterprise is essential for its growth and success.
The company should focus on protecting data assets. It is necessary to build and maintain
security programme of an organisation. In hospital, it is very hard to management because in this
there are number of department with the variety of patients. In this file, there is description of the
strategic information security of health organisation of National health service (Ahlholm. f.,
2013). The data system of business enterprise should be well secured so that can be protected
from unauthorized access. various topics have been addressed in this assignment like
improvement, risk management and to maintain integrity and confidentiality of services. Some
kind of important information should be in access of one person only. The National health
services is taking various initiative in regard to maintain essential security of organisation.
Main body
Health information and matters related to the privacy and security-
National health service is a kind of the social service which is taking various steps in
relation to maintain the privacy of the patient record so that relationship exist between the
diligent and with physician in the healthcare can be improvised. In this person should share the
right kind of information to the medical practitioner so he/she can help him to diagnose the
illness properly. To create trust and understanding between both of the hospital administration
should overlook to maintain the confidentiality in the matter relate to their illness. It is the duty
of the hospital information security programme for making improvement on the health care
policies which are essential in the relation towards the maintaining patient privacy (Al-Alawi and
et.al., 2016.). It is very hard to maintain the matter confidential because it passes with the help of
the electronic medium. It is one kind of the challenge with regard to maintain the integrity and
availability of the data. The NHS is a social care department which are working as treating the
number of patients to make security management plan in order to have privacy and security in
the data of the patients.
Information security programme
The information security programme should be taken in the health care organisation. This
thing can be done on the basis of the proactive approach it helps in the way to have protection
with regard to have unauthorised access. The identification of the process can be done on regular
1
The term strategic information security defines objectives of an organisation. To maintain
confidentiality of matter relating to business enterprise is essential for its growth and success.
The company should focus on protecting data assets. It is necessary to build and maintain
security programme of an organisation. In hospital, it is very hard to management because in this
there are number of department with the variety of patients. In this file, there is description of the
strategic information security of health organisation of National health service (Ahlholm. f.,
2013). The data system of business enterprise should be well secured so that can be protected
from unauthorized access. various topics have been addressed in this assignment like
improvement, risk management and to maintain integrity and confidentiality of services. Some
kind of important information should be in access of one person only. The National health
services is taking various initiative in regard to maintain essential security of organisation.
Main body
Health information and matters related to the privacy and security-
National health service is a kind of the social service which is taking various steps in
relation to maintain the privacy of the patient record so that relationship exist between the
diligent and with physician in the healthcare can be improvised. In this person should share the
right kind of information to the medical practitioner so he/she can help him to diagnose the
illness properly. To create trust and understanding between both of the hospital administration
should overlook to maintain the confidentiality in the matter relate to their illness. It is the duty
of the hospital information security programme for making improvement on the health care
policies which are essential in the relation towards the maintaining patient privacy (Al-Alawi and
et.al., 2016.). It is very hard to maintain the matter confidential because it passes with the help of
the electronic medium. It is one kind of the challenge with regard to maintain the integrity and
availability of the data. The NHS is a social care department which are working as treating the
number of patients to make security management plan in order to have privacy and security in
the data of the patients.
Information security programme
The information security programme should be taken in the health care organisation. This
thing can be done on the basis of the proactive approach it helps in the way to have protection
with regard to have unauthorised access. The identification of the process can be done on regular
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

basis. The administration should have their eyes on this matter in the regular basis. It is very
essential to understand the subject matter and taking various steps in relation to make effective
security management plan (Cooper, 2017). There are the various elements in order to make
efficient and well defined secures plan in context of strategic data protection are:
1. Making number of implementation in relation to maintain the information security
management program.
2. Development and proper identification of the security policies and the number of the
procedures.
3. Make proper determination of the role and responsibilities of the various department to
have protection in term to unauthorised assessed of the sensitive data of the patient.
4. The staff of the medical organisation should be effective trained that they maintain the
work of the firm in the strict and discipline manner.
5. The working of the security staff should be well monitored and checked on the regular
basis.
In order to make this process more effective the management programme of the NHS is inclusive
of eh three strategies are as-
1. Proper privacy and security programme.
2. Risk management
3. compliance
The risk management strategy should work in well and effective manner in order to make well
objective in relation to have proper identification and assessing the data from unauthorised
access. The security control management are required to deal with the risk are as risk mitigation
and risk avoidance. The effective benefit of the risk management strategy is to allow the hospital
to make informed decision regarding the allocation of the different security resource and this
kind of activity helps in manner to have improved data protection. The audit logs of the
organisation should be well secured in relation to have protective data.
Proper identification of the security and the privacy requirements
The proactive approach should be opted by the health care organisation in order to deal
with the security and the privacy instead of being reactive. The health organisation needs to do
the activity in such manner which can develop both kind of the approaches as preventive and
proactive at the same time, so, the risk of the data assess can be well secured from unauthorised
2
essential to understand the subject matter and taking various steps in relation to make effective
security management plan (Cooper, 2017). There are the various elements in order to make
efficient and well defined secures plan in context of strategic data protection are:
1. Making number of implementation in relation to maintain the information security
management program.
2. Development and proper identification of the security policies and the number of the
procedures.
3. Make proper determination of the role and responsibilities of the various department to
have protection in term to unauthorised assessed of the sensitive data of the patient.
4. The staff of the medical organisation should be effective trained that they maintain the
work of the firm in the strict and discipline manner.
5. The working of the security staff should be well monitored and checked on the regular
basis.
In order to make this process more effective the management programme of the NHS is inclusive
of eh three strategies are as-
1. Proper privacy and security programme.
2. Risk management
3. compliance
The risk management strategy should work in well and effective manner in order to make well
objective in relation to have proper identification and assessing the data from unauthorised
access. The security control management are required to deal with the risk are as risk mitigation
and risk avoidance. The effective benefit of the risk management strategy is to allow the hospital
to make informed decision regarding the allocation of the different security resource and this
kind of activity helps in manner to have improved data protection. The audit logs of the
organisation should be well secured in relation to have protective data.
Proper identification of the security and the privacy requirements
The proactive approach should be opted by the health care organisation in order to deal
with the security and the privacy instead of being reactive. The health organisation needs to do
the activity in such manner which can develop both kind of the approaches as preventive and
proactive at the same time, so, the risk of the data assess can be well secured from unauthorised
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

accession of the information. In order To make this process various information security
management programme are undertaken. The security programme is carried by the certain
standards as such ISO 27001 and ISO 27002 for the terms like information management system
and security techniques programme (Santee, 2017). The NHS should adopt the security standard
of the ISO 27001 in order to make privacy regulation of HIPAA which deals with the health
insurance portability and the accountability act. This function helps in manner to make
determination between the security policy and risk management. The approval from the senior
management should be taken to make security and privacy policy it helps in the way to have risk
assessment and treatment. These things are to be handled on the basis of the priority manner.
Risk mitigation and risk avoidance are important measures which help in making the function in
the properly analytical and cleared style. This kind of the data protection services should be
based on the encryption standard. This function helps in the manner to have protection in related
to the information and maintain the confidentiality of the data.
Information security policy
This function defines the various roles, responsibilities and procedures which are required
to safeguard the information system (Yeow, Yuen and Loo, 2013). It is also inclusive of the
policies in relation to the personal health info of the patient and this should be properly coalition
of the information with business strategy of the hospital. The information should be passes in
accordingly in the well and properly analysed manner. The legislature, and regulatory framework
should also take their valuable step with the view to maintain the information privacy and the
security.
Phases of the security policy development
There are various kinds of stages in relation to the security policy development are as-
Acquired executive support- At the time of making implementation and drafting there should
have effective support (Sousa, Costa and Manso, 2013). The involvement of the senior executive
management is very essential in relation to have policy development.
Drafting and engagement- At the time of making draft of the security those people who get
affected by Such policy can open the draft and review the content in relates to this matter so
important information can have in this regard.
3
management programme are undertaken. The security programme is carried by the certain
standards as such ISO 27001 and ISO 27002 for the terms like information management system
and security techniques programme (Santee, 2017). The NHS should adopt the security standard
of the ISO 27001 in order to make privacy regulation of HIPAA which deals with the health
insurance portability and the accountability act. This function helps in manner to make
determination between the security policy and risk management. The approval from the senior
management should be taken to make security and privacy policy it helps in the way to have risk
assessment and treatment. These things are to be handled on the basis of the priority manner.
Risk mitigation and risk avoidance are important measures which help in making the function in
the properly analytical and cleared style. This kind of the data protection services should be
based on the encryption standard. This function helps in the manner to have protection in related
to the information and maintain the confidentiality of the data.
Information security policy
This function defines the various roles, responsibilities and procedures which are required
to safeguard the information system (Yeow, Yuen and Loo, 2013). It is also inclusive of the
policies in relation to the personal health info of the patient and this should be properly coalition
of the information with business strategy of the hospital. The information should be passes in
accordingly in the well and properly analysed manner. The legislature, and regulatory framework
should also take their valuable step with the view to maintain the information privacy and the
security.
Phases of the security policy development
There are various kinds of stages in relation to the security policy development are as-
Acquired executive support- At the time of making implementation and drafting there should
have effective support (Sousa, Costa and Manso, 2013). The involvement of the senior executive
management is very essential in relation to have policy development.
Drafting and engagement- At the time of making draft of the security those people who get
affected by Such policy can open the draft and review the content in relates to this matter so
important information can have in this regard.
3

Review- To have the accurate and corrective information of the senior management should
review the security in order to make policy draft in well-defined and corrective manner (Olijnyk,
2015). The changes can be made at the time initial stage.
Approval and implementation- The approval can be taken with the help of the higher authority
in relation to the making regulation of the policy development. The communication should be in
the proper manner in the organisation (Rhee, Kim and Ryu, 2009). After having the approval, it
is essential to implement the process as per the action plan to reach compliance and it can be
monitored in the well-defined process.
Maintenance and review- After completion of the all above process the policy should be
maintained and review function is to be done on the regular periodical basis as per the changing
environment, technologies, policies and business strategies.
The system checked as per the accordance with the HIPPA compliance-
This system of protecting information security and privacy of confidential method of
medical reports of the patients should be in accordance with the rules and responsibilities under
the department of the HIPAA. This is working towards the activities of making these activities as
per the health insurance practice and managing the health information because firm in moving
slowly to the electronic based manner. This is very helpful with regard to protect the data of
patients and provide them the best quality of care. This activity helps to enhance patients trust
on the social service department of National health service. The matter of the confidentiality
should be maintained in relation to enhance patient care in the good manner. To have the better
risk management and assessment can be done with the help of the department of the HIPAA
(Santee, 2017). They help in defining the accurate advise at the time of the potential risk. The
security measures should be taken in relation to maintain the security and deal with the problem
in relation to the threats and vulnerabilities.
Layered approach to privacy and security
Privacy is the main issue that can build strong relationship between care users and
providers. It is very important that patients share their medical issues with the practitioner
properly do that doctors can give them quality treatment. Information system can support in
managing records of patients effectively but due to security issues nursing staff fails to manage
this data properly. This kind information security and use of advanced technology can be
beneficial in keeping the data secure and increasing trust of users on medical professionals. That
4
review the security in order to make policy draft in well-defined and corrective manner (Olijnyk,
2015). The changes can be made at the time initial stage.
Approval and implementation- The approval can be taken with the help of the higher authority
in relation to the making regulation of the policy development. The communication should be in
the proper manner in the organisation (Rhee, Kim and Ryu, 2009). After having the approval, it
is essential to implement the process as per the action plan to reach compliance and it can be
monitored in the well-defined process.
Maintenance and review- After completion of the all above process the policy should be
maintained and review function is to be done on the regular periodical basis as per the changing
environment, technologies, policies and business strategies.
The system checked as per the accordance with the HIPPA compliance-
This system of protecting information security and privacy of confidential method of
medical reports of the patients should be in accordance with the rules and responsibilities under
the department of the HIPAA. This is working towards the activities of making these activities as
per the health insurance practice and managing the health information because firm in moving
slowly to the electronic based manner. This is very helpful with regard to protect the data of
patients and provide them the best quality of care. This activity helps to enhance patients trust
on the social service department of National health service. The matter of the confidentiality
should be maintained in relation to enhance patient care in the good manner. To have the better
risk management and assessment can be done with the help of the department of the HIPAA
(Santee, 2017). They help in defining the accurate advise at the time of the potential risk. The
security measures should be taken in relation to maintain the security and deal with the problem
in relation to the threats and vulnerabilities.
Layered approach to privacy and security
Privacy is the main issue that can build strong relationship between care users and
providers. It is very important that patients share their medical issues with the practitioner
properly do that doctors can give them quality treatment. Information system can support in
managing records of patients effectively but due to security issues nursing staff fails to manage
this data properly. This kind information security and use of advanced technology can be
beneficial in keeping the data secure and increasing trust of users on medical professionals. That
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

may support in improving their health and minimizing their health issues. But due to data
leakage people do not share their problems with them in the properly manner.(Chapman, 2017).
The main risk that take place in the NHS and health and social care entities are administrative,
physical and technical issues. It is essential for NHS to make effective control over these risks
so that overall working of social services can be improved. Encryption of data cannot be able to
perform well until there is an effective administrative control. It helps in maintaining data
confidentiality. NHS needs to provide proper training to its staff members so that they can know
about data protection and security. Physical control is another most important part of social
services.
Health and social care organisations need to adopt multi layered approach that assists in
providing high performance hardware security. With the help of this tool NHS can handles
complex threats and vulnerabilities easily (Al-Alawi, Al-Kandari and Abdel-Razek, 2016). It is
the way that supports in re-busting of system. That assists in improving performance of hardware
system.
NHS needs to use advanced encryption standards in order to improve their performance
level. With the help of this, cited firm will be able to maintain confidentiality of private
information.
Anti-theft application is another relevant option through which risk of information can
be minimized in the social service companies. This technology supports in mitigating
issues related to loss of sensitive information in the network.
In order to maintain integrity in the system NHS needs to use execution technology. That
can assist in protecting sensitive data and minimizing risk.
Health and social care sector is the industry in which companies like NHS needs to
manage remote desktop. NHS should maintain security measures and compliance as well.
Entities which are engaged in the health and social services, they must deal with
sensitive information. Encryption can be considered as effective counter measure that helps in
maintaining security in the social service companies (Ahlholm, 2013.). With the help of this
technology NHS can protect their data and can manage their sensitive information effectively.
Most of the hospitals are facing issues in which they feel unable to keep secure their confidential
details.
5
leakage people do not share their problems with them in the properly manner.(Chapman, 2017).
The main risk that take place in the NHS and health and social care entities are administrative,
physical and technical issues. It is essential for NHS to make effective control over these risks
so that overall working of social services can be improved. Encryption of data cannot be able to
perform well until there is an effective administrative control. It helps in maintaining data
confidentiality. NHS needs to provide proper training to its staff members so that they can know
about data protection and security. Physical control is another most important part of social
services.
Health and social care organisations need to adopt multi layered approach that assists in
providing high performance hardware security. With the help of this tool NHS can handles
complex threats and vulnerabilities easily (Al-Alawi, Al-Kandari and Abdel-Razek, 2016). It is
the way that supports in re-busting of system. That assists in improving performance of hardware
system.
NHS needs to use advanced encryption standards in order to improve their performance
level. With the help of this, cited firm will be able to maintain confidentiality of private
information.
Anti-theft application is another relevant option through which risk of information can
be minimized in the social service companies. This technology supports in mitigating
issues related to loss of sensitive information in the network.
In order to maintain integrity in the system NHS needs to use execution technology. That
can assist in protecting sensitive data and minimizing risk.
Health and social care sector is the industry in which companies like NHS needs to
manage remote desktop. NHS should maintain security measures and compliance as well.
Entities which are engaged in the health and social services, they must deal with
sensitive information. Encryption can be considered as effective counter measure that helps in
maintaining security in the social service companies (Ahlholm, 2013.). With the help of this
technology NHS can protect their data and can manage their sensitive information effectively.
Most of the hospitals are facing issues in which they feel unable to keep secure their confidential
details.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

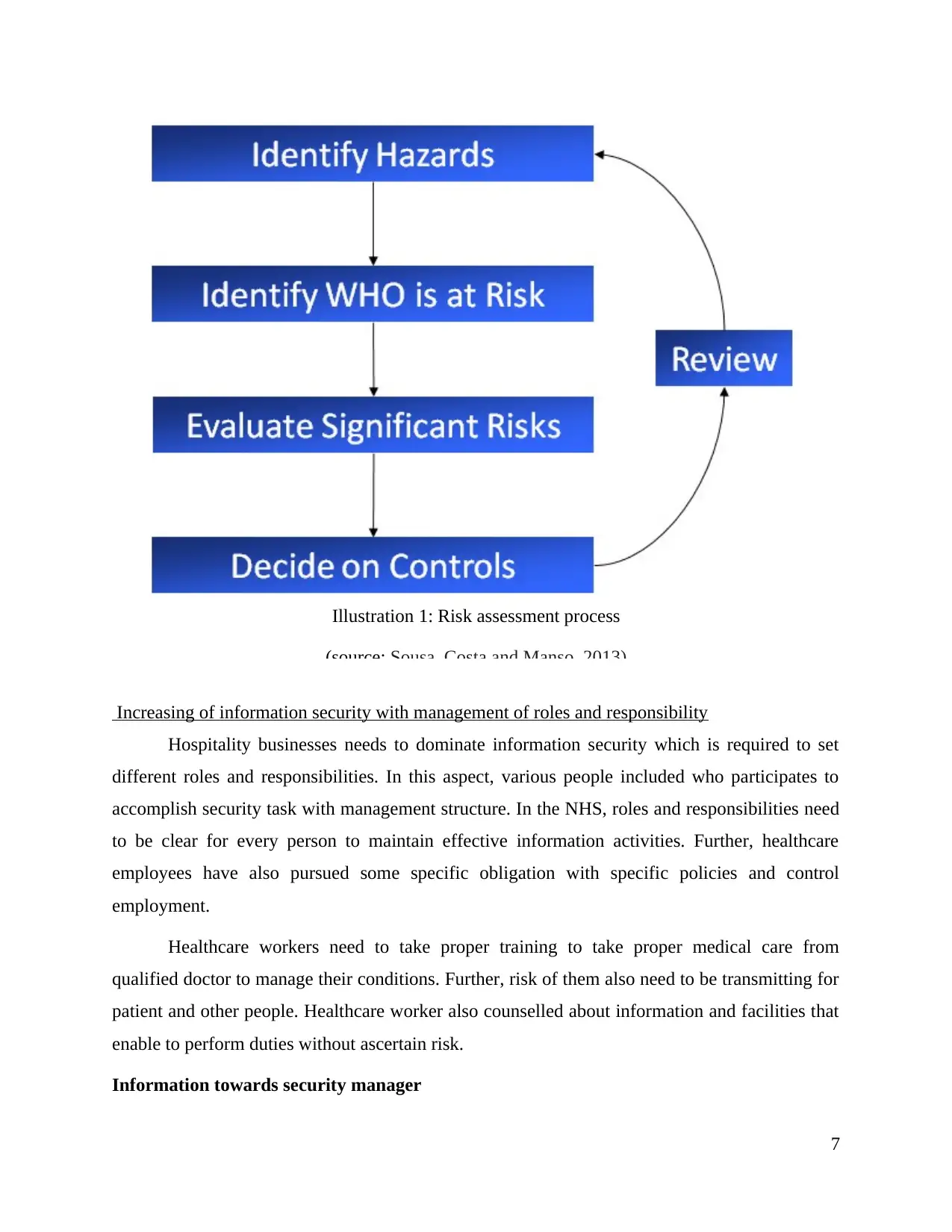
Risk management assessment process
The risk management is the important aspects in relation maintain the control of the
hazardous process which are inclusive of the functions like security purpose, legal issue and the
safety concerns. It should be monitored on the regular basis to have the updates. This process
should be followed in the effective manner in relation to the process of risk management which
are based on the identification of threat and then defining the measure to have effective security
aspects in the organisation (Zafar, 2013). His all function should be appropriate in order to deal
with risk management of the firm. The data security risk management is kind of the coordinated
activity in which identification of the type of the hazard can be identified, analysed and
addressed in the easy manner the privacy legislation should be enhanced to reduce the problem
of the breaches of the information confidentiality and security measure relates to it. The Proper
identification should be made in relation to identification of the assets which are important with
the context of the health care business needs which is to be evaluated in the well manner.
6
The risk management is the important aspects in relation maintain the control of the
hazardous process which are inclusive of the functions like security purpose, legal issue and the
safety concerns. It should be monitored on the regular basis to have the updates. This process
should be followed in the effective manner in relation to the process of risk management which
are based on the identification of threat and then defining the measure to have effective security
aspects in the organisation (Zafar, 2013). His all function should be appropriate in order to deal
with risk management of the firm. The data security risk management is kind of the coordinated
activity in which identification of the type of the hazard can be identified, analysed and
addressed in the easy manner the privacy legislation should be enhanced to reduce the problem
of the breaches of the information confidentiality and security measure relates to it. The Proper
identification should be made in relation to identification of the assets which are important with
the context of the health care business needs which is to be evaluated in the well manner.
6
Increasing of information security with management of roles and responsibility
Hospitality businesses needs to dominate information security which is required to set
different roles and responsibilities. In this aspect, various people included who participates to
accomplish security task with management structure. In the NHS, roles and responsibilities need
to be clear for every person to maintain effective information activities. Further, healthcare
employees have also pursued some specific obligation with specific policies and control
employment.
Healthcare workers need to take proper training to take proper medical care from
qualified doctor to manage their conditions. Further, risk of them also need to be transmitting for
patient and other people. Healthcare worker also counselled about information and facilities that
enable to perform duties without ascertain risk.
Information towards security manager
7
Illustration 1: Risk assessment process
(source: Sousa, Costa and Manso. 2013)
Hospitality businesses needs to dominate information security which is required to set
different roles and responsibilities. In this aspect, various people included who participates to
accomplish security task with management structure. In the NHS, roles and responsibilities need
to be clear for every person to maintain effective information activities. Further, healthcare
employees have also pursued some specific obligation with specific policies and control
employment.
Healthcare workers need to take proper training to take proper medical care from
qualified doctor to manage their conditions. Further, risk of them also need to be transmitting for
patient and other people. Healthcare worker also counselled about information and facilities that
enable to perform duties without ascertain risk.
Information towards security manager
7
Illustration 1: Risk assessment process
(source: Sousa, Costa and Manso. 2013)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information security manager of the chosen health care need to be assigned one senior
manager who is responsible to create staff awareness and training for them as well. He/she
should be responsible to develop security policy, aim and connectivity with objectives. This is
effective business strategy for information safety manager in NHS. Manager also works to make
progress of implementation and drafting security program and address issues. Threats and
incident to the management also cater that required to work in business.
Compliance officer
Officer of the NHS need to make independent information security management
program. With the help of policies and procedures, they have responsible to review and monitor
in accordance with the best security and practices. Compliance also assured with legislation and
guidelines to govern health care security.
Information technology users
Information technology users in NHS also responsible to follow all security policy and
procedures with the physical as well. In addition to this, they are also responsible to report
security incident to information technology manager and need to understand code of conduct
with details information technology and policies standards as well. Information technology users
need to make security also important part for every person in chosen business to adopt security
procedures (Zafar, 2013).
Operational duties
In NHS, administrators also oversee human resource activities that create and manage
ethics program facility to allocate resources. In addition to this, in different department leaders
accountable to defines outcomes to concern different duties.
Promote positive mental, physical and nutritional health
To make effective functions and operations, NHS also create positive results to satisfy
each patient. In this aspect, they play role to ascertain more profits and revenue at workplace.
Personal care also undertakes in this way so that it required to make hygiene and comfort
assistant in business unit. It creates opportunity to develop profits and revenue at workplace
towards appropriate foundation degree (Zafar, 2013).
Aware about maintenance personal records
8
manager who is responsible to create staff awareness and training for them as well. He/she
should be responsible to develop security policy, aim and connectivity with objectives. This is
effective business strategy for information safety manager in NHS. Manager also works to make
progress of implementation and drafting security program and address issues. Threats and
incident to the management also cater that required to work in business.
Compliance officer
Officer of the NHS need to make independent information security management
program. With the help of policies and procedures, they have responsible to review and monitor
in accordance with the best security and practices. Compliance also assured with legislation and
guidelines to govern health care security.
Information technology users
Information technology users in NHS also responsible to follow all security policy and
procedures with the physical as well. In addition to this, they are also responsible to report
security incident to information technology manager and need to understand code of conduct
with details information technology and policies standards as well. Information technology users
need to make security also important part for every person in chosen business to adopt security
procedures (Zafar, 2013).
Operational duties
In NHS, administrators also oversee human resource activities that create and manage
ethics program facility to allocate resources. In addition to this, in different department leaders
accountable to defines outcomes to concern different duties.
Promote positive mental, physical and nutritional health
To make effective functions and operations, NHS also create positive results to satisfy
each patient. In this aspect, they play role to ascertain more profits and revenue at workplace.
Personal care also undertakes in this way so that it required to make hygiene and comfort
assistant in business unit. It creates opportunity to develop profits and revenue at workplace
towards appropriate foundation degree (Zafar, 2013).
Aware about maintenance personal records
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Healthcare workers need to aware about requirement of each patient. Therefore, they can
demonstrate proper treatment against diseases through maintains personal records. In specific
circumstances, health and safety people also need to ensure safe work practices. This role plays a
vital role to keep proper security in NHS.
CONCLUSION
The information security and privacy legislation plays the crucial role in relation to
maintain the patients’ confidentiality and privacy in the health care organisation. This study has
been focused on the aspect of social service of the National health care organisation. This
process is covered the following things like the risk assessment, mitigation, management and
compliance as per rules and responsibilities of the HIPAA department. In addition to this there is
also give the ISO 2700 standard with should be op by the NHS to have the effective and efficient
service in the health organisation and initiative steps should be taken for providing the quality
patient care.
9
demonstrate proper treatment against diseases through maintains personal records. In specific
circumstances, health and safety people also need to ensure safe work practices. This role plays a
vital role to keep proper security in NHS.
CONCLUSION
The information security and privacy legislation plays the crucial role in relation to
maintain the patients’ confidentiality and privacy in the health care organisation. This study has
been focused on the aspect of social service of the National health care organisation. This
process is covered the following things like the risk assessment, mitigation, management and
compliance as per rules and responsibilities of the HIPAA department. In addition to this there is
also give the ISO 2700 standard with should be op by the NHS to have the effective and efficient
service in the health organisation and initiative steps should be taken for providing the quality
patient care.
9

REFERENCES
Journal & Book
Ahlholm, T., 2013. Tietoturvallisuusnäkökohtien vaikutus muutostiedostojen hyväksymiseen
avoimen lähdekoodin ohjelmistoprojekteissa.
Al-Alawi, A.I., Al-Kandari, S.M. and Abdel-Razek, R.H., 2016. Evaluation of Information
Systems Security Awareness in Higher Education: An Empirical Study of Kuwait
University.
Al-Alawi, A.I., Al-Kandari, S.M. and Abdel-Razek, R.H., 2016. Evaluation of Information
Systems Security Awareness in Higher Education: An Empirical Study of Kuwait
University.
Chapman, C.L., 2017. The influence of leadership on business continuity planning: A qualitative
phenomenological study (Doctoral dissertation, University of Phoenix).
Cooper, P.K., 2017. Organisational Security Threats Related to Portable Data Storage Devices:
Qualitative Exploratory Inquiry (Doctoral dissertation, University of Phoenix).
Olijnyk, N.V., 2015. A quantitative examination of the intellectual profile and evolution of
information security from 1965 to 2015. Scientometrics. 105(2). pp.883-904.
Rhee, H.S., Kim, C. and Ryu, Y.U., 2009. Self-efficacy in information security: Its influence on
end users' information security practice behavior. Computers & Security. 28(8). pp.816-
826.
Santee, C.D., 2017. An Exploratory Study of the Approach to Bring Your Own Device (BYOD) in
Assuring Information Security (Doctoral dissertation, Nova Southeastern University).
Sousa, P., Costa, J. and Manso, V., 2013. Practical Approach for Data Breach Cases in ERP
Systems. Organisational, Legal, and Technological Dimensions of Information System
Administration.
Yeow, P.H., Yuen, Y.Y. and Loo, W.H., 2013. Ergonomics issues in national identity card for
homeland security. Applied ergonomics. 44(5). pp.719-729.
Zafar, H., 2013. Human resource information systems: Information security concerns for
organisations. Human Resource Management Review. 23(1). pp.105-113.
Journal & Book
Ahlholm, T., 2013. Tietoturvallisuusnäkökohtien vaikutus muutostiedostojen hyväksymiseen
avoimen lähdekoodin ohjelmistoprojekteissa.
Al-Alawi, A.I., Al-Kandari, S.M. and Abdel-Razek, R.H., 2016. Evaluation of Information
Systems Security Awareness in Higher Education: An Empirical Study of Kuwait
University.
Al-Alawi, A.I., Al-Kandari, S.M. and Abdel-Razek, R.H., 2016. Evaluation of Information
Systems Security Awareness in Higher Education: An Empirical Study of Kuwait
University.
Chapman, C.L., 2017. The influence of leadership on business continuity planning: A qualitative
phenomenological study (Doctoral dissertation, University of Phoenix).
Cooper, P.K., 2017. Organisational Security Threats Related to Portable Data Storage Devices:
Qualitative Exploratory Inquiry (Doctoral dissertation, University of Phoenix).
Olijnyk, N.V., 2015. A quantitative examination of the intellectual profile and evolution of
information security from 1965 to 2015. Scientometrics. 105(2). pp.883-904.
Rhee, H.S., Kim, C. and Ryu, Y.U., 2009. Self-efficacy in information security: Its influence on
end users' information security practice behavior. Computers & Security. 28(8). pp.816-
826.
Santee, C.D., 2017. An Exploratory Study of the Approach to Bring Your Own Device (BYOD) in
Assuring Information Security (Doctoral dissertation, Nova Southeastern University).
Sousa, P., Costa, J. and Manso, V., 2013. Practical Approach for Data Breach Cases in ERP
Systems. Organisational, Legal, and Technological Dimensions of Information System
Administration.
Yeow, P.H., Yuen, Y.Y. and Loo, W.H., 2013. Ergonomics issues in national identity card for
homeland security. Applied ergonomics. 44(5). pp.719-729.
Zafar, H., 2013. Human resource information systems: Information security concerns for
organisations. Human Resource Management Review. 23(1). pp.105-113.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




