Strategic Information System for Business and Enterprise
VerifiedAdded on 2023/03/17
|20
|3707
|97
AI Summary
This paper discusses the strategic information system for business and enterprise, including transactional cycles, weaknesses, and associated risks. It explores the purchase, sales, payroll, financing, and expenditure cycles, as well as the weaknesses in the Bell studio system. The risks discussed include hardware and software failure, computer viruses and malware, human error, and hacking and fraud.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 1
Strategic information system for business and enterprise:
Name:
Institution:
Course:
Date:
Strategic information system for business and enterprise:
Name:
Institution:
Course:
Date:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 2
Strategic information system for business and enterprise
Executive summary
In this paper, we shall discuss the strategic information system for the enterprise and for
the business by introducing the strategic information and information. We shall also
extend our discussion by discussing the data flow diagram for purchases, payroll, and
cash disbursements and well shall greatly be focused on the discussion the system flow
diagram for purchase system, payroll system, and disbursement systems. Lastly, we
shall discuss various risks associated with the weaknesses of the bell studio system in
the organization. The risks which we will discuss are a failure of software and hardware,
computer virus and malware, human error and frauds and lastly fraud, hacking and
denial to services. Also, we shall discuss various weaknesses associated bell studio
system. In this case, we shall discuss weaknesses for purchase system, payroll system,
and cash disbursements systems.
Strategic information system for business and enterprise
Executive summary
In this paper, we shall discuss the strategic information system for the enterprise and for
the business by introducing the strategic information and information. We shall also
extend our discussion by discussing the data flow diagram for purchases, payroll, and
cash disbursements and well shall greatly be focused on the discussion the system flow
diagram for purchase system, payroll system, and disbursement systems. Lastly, we
shall discuss various risks associated with the weaknesses of the bell studio system in
the organization. The risks which we will discuss are a failure of software and hardware,
computer virus and malware, human error and frauds and lastly fraud, hacking and
denial to services. Also, we shall discuss various weaknesses associated bell studio
system. In this case, we shall discuss weaknesses for purchase system, payroll system,
and cash disbursements systems.

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 3
Table of Contents
Introduction........................................................................................................................3
Transactional cycle............................................................................................................4
Purchase cycle...............................................................................................................5
Sales cycle.....................................................................................................................6
Payroll cycle...................................................................................................................6
Financing cycle...............................................................................................................7
Expenditure cycle...........................................................................................................8
Weaknesses in the Bell studio system..............................................................................9
Purchase system............................................................................................................9
Cash Disbursement system.........................................................................................10
Payroll system..............................................................................................................10
Risks associated with the weaknesses in the Bell Studio system..................................11
Hardware and software failure.....................................................................................11
Computer Viruses and Malware...................................................................................11
Human error.................................................................................................................12
Hacking, fraud, denial-of-service..................................................................................12
Conclusion.......................................................................................................................13
References.......................................................................................................................14
Table of Contents
Introduction........................................................................................................................3
Transactional cycle............................................................................................................4
Purchase cycle...............................................................................................................5
Sales cycle.....................................................................................................................6
Payroll cycle...................................................................................................................6
Financing cycle...............................................................................................................7
Expenditure cycle...........................................................................................................8
Weaknesses in the Bell studio system..............................................................................9
Purchase system............................................................................................................9
Cash Disbursement system.........................................................................................10
Payroll system..............................................................................................................10
Risks associated with the weaknesses in the Bell Studio system..................................11
Hardware and software failure.....................................................................................11
Computer Viruses and Malware...................................................................................11
Human error.................................................................................................................12
Hacking, fraud, denial-of-service..................................................................................12
Conclusion.......................................................................................................................13
References.......................................................................................................................14

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 4
Introduction
Strategic information system (SIS) is usually referred to information systems that are
advanced in reaction to organization business initiative. This system will help in
providing competitive advantages to all organization. The strategic information system
can also be defined as the process of categorizing various applications that can be
utilized to give a channel for configuration with various business strategies. Companies
all over the world have come to realize it is very crucial to evolve in technological
advancement so that their companies run smoothly. As technology is advancing then
there is the need for any business to adopt these new ways so that they can reach their
customers. The technology that is applied in various businesses should be
interoperable with existing systems and in this case, it should never impact the flow of
operation in the company.
Information is term as a crucial part of any company because most of the operations in
any organization greatly rely on the information. And as a result, most of the
organizations should come with the strategy of making sure that they fully utilize the use
of information. Distinct systems need to be joined together so that enough information
for decision making can be obtained. The information exists in the past days was not
meaningful since the information was not used in maximizing the profits in the company.
And currently, the information is well utilized in order for the company to maximize its
profits.
Strategic systems are very crucial for any organization that is intending to gain
competitive advantages, this is because technology can be utilized in developing the
Introduction
Strategic information system (SIS) is usually referred to information systems that are
advanced in reaction to organization business initiative. This system will help in
providing competitive advantages to all organization. The strategic information system
can also be defined as the process of categorizing various applications that can be
utilized to give a channel for configuration with various business strategies. Companies
all over the world have come to realize it is very crucial to evolve in technological
advancement so that their companies run smoothly. As technology is advancing then
there is the need for any business to adopt these new ways so that they can reach their
customers. The technology that is applied in various businesses should be
interoperable with existing systems and in this case, it should never impact the flow of
operation in the company.
Information is term as a crucial part of any company because most of the operations in
any organization greatly rely on the information. And as a result, most of the
organizations should come with the strategy of making sure that they fully utilize the use
of information. Distinct systems need to be joined together so that enough information
for decision making can be obtained. The information exists in the past days was not
meaningful since the information was not used in maximizing the profits in the company.
And currently, the information is well utilized in order for the company to maximize its
profits.
Strategic systems are very crucial for any organization that is intending to gain
competitive advantages, this is because technology can be utilized in developing the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 5
products and services of the company and also it can be advertising the products of the
company. In addition, it gives a step by step procedure of how the product in the
organization is being purchased. It mainly contributes to the database system which its
main aim is to utilize the company information in advertising and marketing of the
products. The strategic information system will make sure that what is carried out in the
business is going hand in hand with various strategies in the organization.
In Bell's studio, the strategic information system is always acquired from analyzing the
transactional cycle in the organization. Below is an elaborate discussion on
transactional cycle and ways in which it impacts the organization processes.
Transactional cycle
A transactional cycle is an interconnecting cycle that clearly discusses the step by step
procedures that are carried out in the business, this activity includes the financial
transactions of a company. In addition, these cycles are related to payments of
employees, sales of goods and payments of suppliers. Below are various transactional
cycles in any business
Purchase cycle
The purchasing system entails the process of identifying the need for inventory, order
placement, Inventory acquisition and identifying liability and any products which do not
suit the demand of the organization. The inventory control works by giving the buyer an
authority to purchase a given product. For instance, if the product which was to be
bought does not meet the needed standard then the product will be supplied back to the
suppliers before the real purchase occurs. This process occurs when the product is not
meeting the needed standard but if the quality of the product is standard then the
products and services of the company and also it can be advertising the products of the
company. In addition, it gives a step by step procedure of how the product in the
organization is being purchased. It mainly contributes to the database system which its
main aim is to utilize the company information in advertising and marketing of the
products. The strategic information system will make sure that what is carried out in the
business is going hand in hand with various strategies in the organization.
In Bell's studio, the strategic information system is always acquired from analyzing the
transactional cycle in the organization. Below is an elaborate discussion on
transactional cycle and ways in which it impacts the organization processes.
Transactional cycle
A transactional cycle is an interconnecting cycle that clearly discusses the step by step
procedures that are carried out in the business, this activity includes the financial
transactions of a company. In addition, these cycles are related to payments of
employees, sales of goods and payments of suppliers. Below are various transactional
cycles in any business
Purchase cycle
The purchasing system entails the process of identifying the need for inventory, order
placement, Inventory acquisition and identifying liability and any products which do not
suit the demand of the organization. The inventory control works by giving the buyer an
authority to purchase a given product. For instance, if the product which was to be
bought does not meet the needed standard then the product will be supplied back to the
suppliers before the real purchase occurs. This process occurs when the product is not
meeting the needed standard but if the quality of the product is standard then the

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 6
purchasing order is prepared by using the computer. This purchase process will be
forwarded from one department to other until the last process is achieved.
A purchasing order is usually given by an organization to a supplier of goods. After the
goods have been received, the company records a given inventory of goods needed to
be paid and pays for the goods. For most organization goods can be verified after it has
been confirmed it meets the required standard. Below is the data flow diagram for
purchases cash flows system.
Data flow diagram
purchasing order is prepared by using the computer. This purchase process will be
forwarded from one department to other until the last process is achieved.
A purchasing order is usually given by an organization to a supplier of goods. After the
goods have been received, the company records a given inventory of goods needed to
be paid and pays for the goods. For most organization goods can be verified after it has
been confirmed it meets the required standard. Below is the data flow diagram for
purchases cash flows system.
Data flow diagram
STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 7
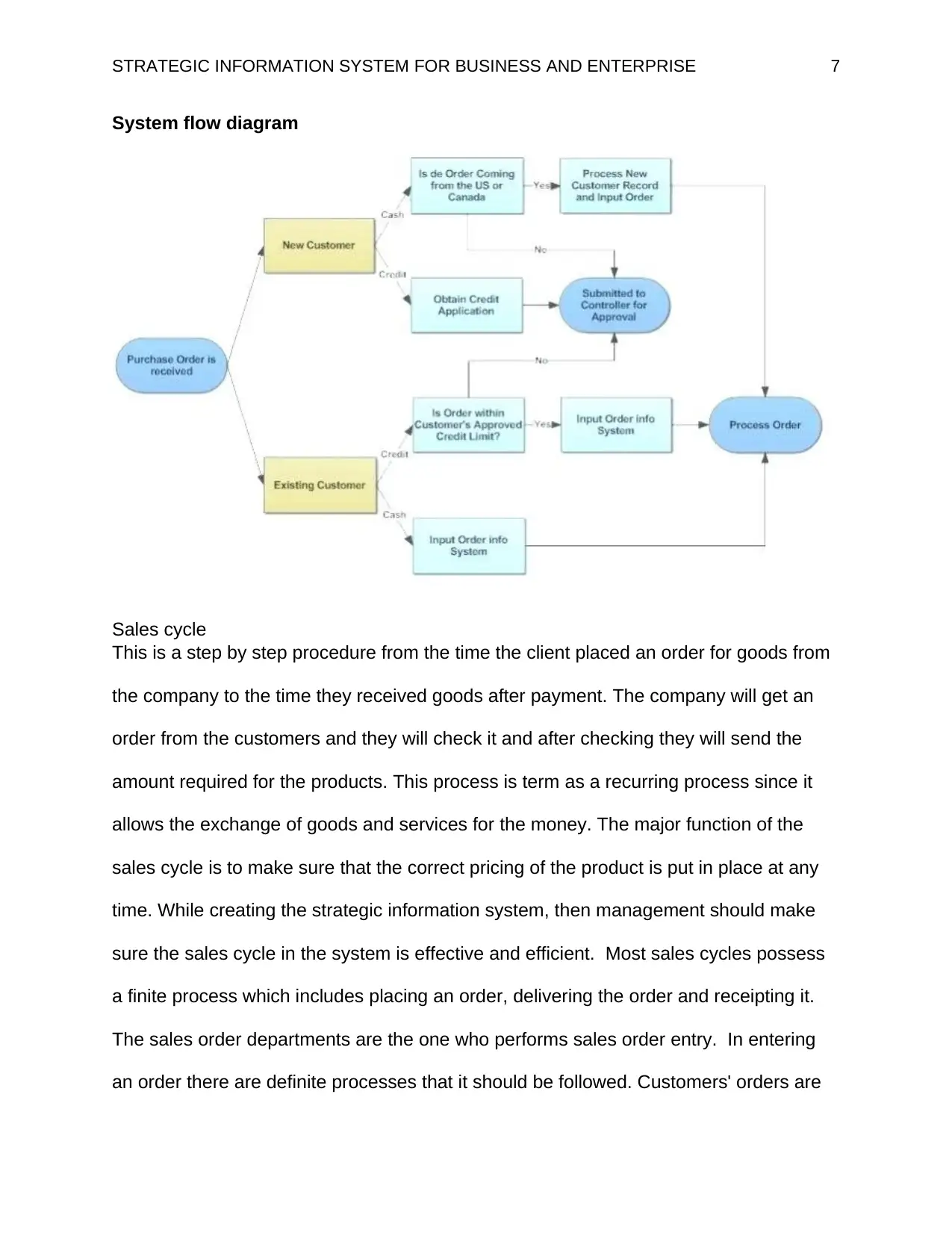
System flow diagram
Sales cycle
This is a step by step procedure from the time the client placed an order for goods from
the company to the time they received goods after payment. The company will get an
order from the customers and they will check it and after checking they will send the
amount required for the products. This process is term as a recurring process since it
allows the exchange of goods and services for the money. The major function of the
sales cycle is to make sure that the correct pricing of the product is put in place at any
time. While creating the strategic information system, then management should make
sure the sales cycle in the system is effective and efficient. Most sales cycles possess
a finite process which includes placing an order, delivering the order and receipting it.
The sales order departments are the one who performs sales order entry. In entering
an order there are definite processes that it should be followed. Customers' orders are
System flow diagram
Sales cycle
This is a step by step procedure from the time the client placed an order for goods from
the company to the time they received goods after payment. The company will get an
order from the customers and they will check it and after checking they will send the
amount required for the products. This process is term as a recurring process since it
allows the exchange of goods and services for the money. The major function of the
sales cycle is to make sure that the correct pricing of the product is put in place at any
time. While creating the strategic information system, then management should make
sure the sales cycle in the system is effective and efficient. Most sales cycles possess
a finite process which includes placing an order, delivering the order and receipting it.
The sales order departments are the one who performs sales order entry. In entering
an order there are definite processes that it should be followed. Customers' orders are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 8
taken and being check. And the availability of the product is being checked and the
customer will receive feedback. As integrating this service into the online platform, then
customers are the one who is supposed to enter their details into the system, this tends
to reduce the human error.
Payroll cycle
This process occurs at the company and this involves their employees. The company
will check the number of hours in which the employees have worked in the company.
And the time is examined based on the full time and per time. The employees are then
paid according to total hours they have worked in full time and per time within the
company. The payment is usually paid after the advances and taxes have been
deducted. Below is the data flow diagram and system flow chart for payroll at Bell studio
system.
Data flow diagram
System flow chart for payroll system
taken and being check. And the availability of the product is being checked and the
customer will receive feedback. As integrating this service into the online platform, then
customers are the one who is supposed to enter their details into the system, this tends
to reduce the human error.
Payroll cycle
This process occurs at the company and this involves their employees. The company
will check the number of hours in which the employees have worked in the company.
And the time is examined based on the full time and per time. The employees are then
paid according to total hours they have worked in full time and per time within the
company. The payment is usually paid after the advances and taxes have been
deducted. Below is the data flow diagram and system flow chart for payroll at Bell studio
system.
Data flow diagram
System flow chart for payroll system
STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 9
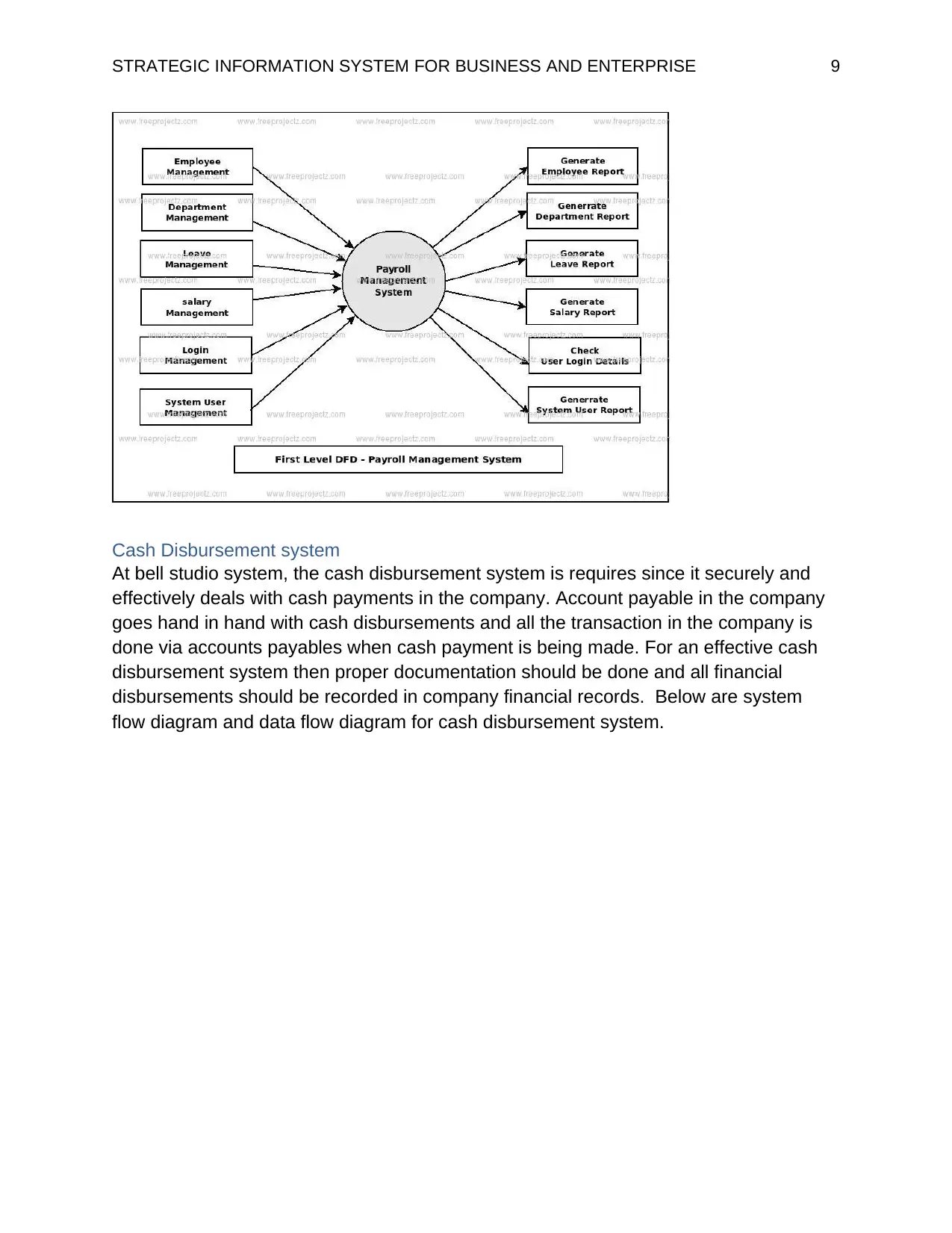
Cash Disbursement system
At bell studio system, the cash disbursement system is requires since it securely and
effectively deals with cash payments in the company. Account payable in the company
goes hand in hand with cash disbursements and all the transaction in the company is
done via accounts payables when cash payment is being made. For an effective cash
disbursement system then proper documentation should be done and all financial
disbursements should be recorded in company financial records. Below are system
flow diagram and data flow diagram for cash disbursement system.
Cash Disbursement system
At bell studio system, the cash disbursement system is requires since it securely and
effectively deals with cash payments in the company. Account payable in the company
goes hand in hand with cash disbursements and all the transaction in the company is
done via accounts payables when cash payment is being made. For an effective cash
disbursement system then proper documentation should be done and all financial
disbursements should be recorded in company financial records. Below are system
flow diagram and data flow diagram for cash disbursement system.
STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 10
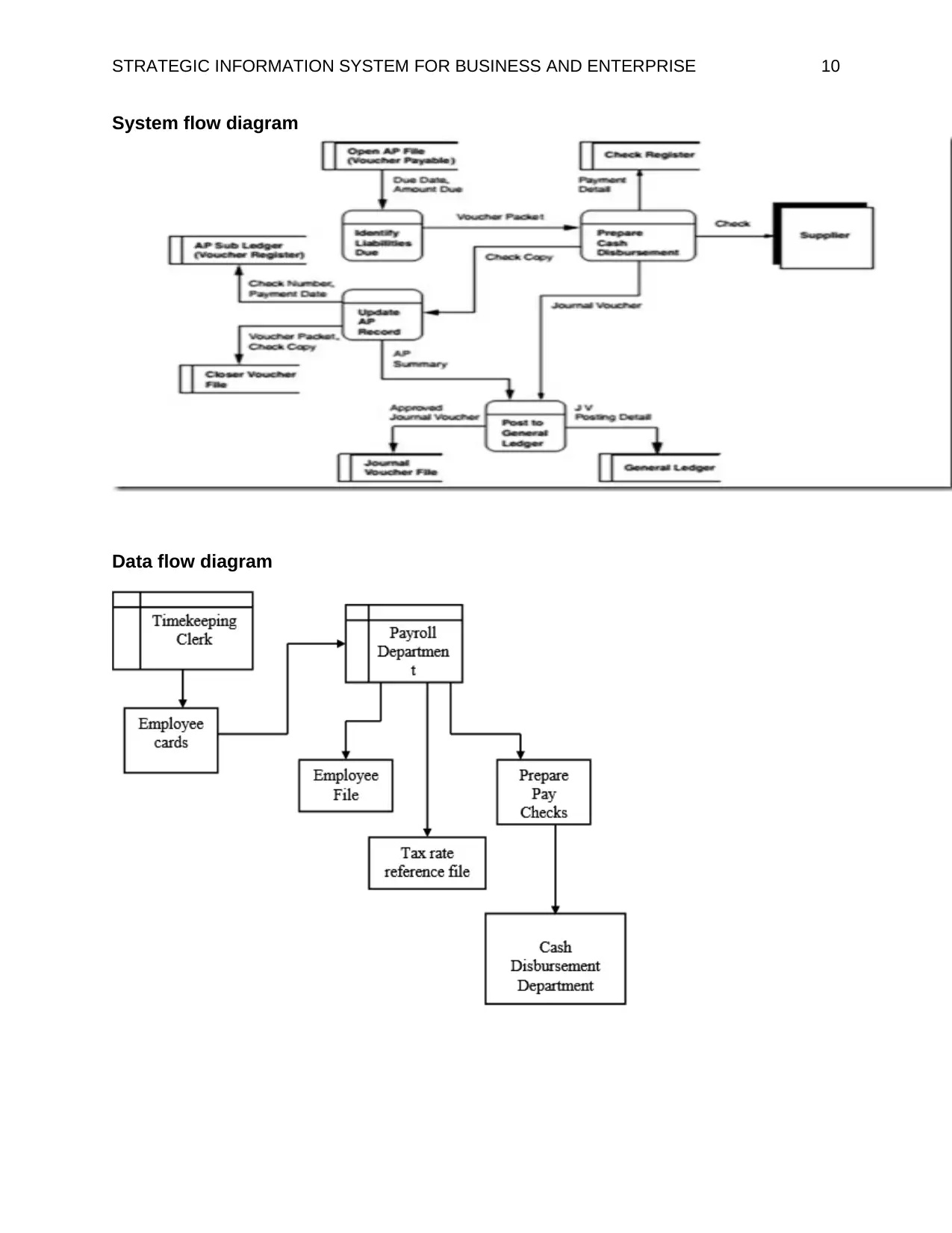
System flow diagram
Data flow diagram
System flow diagram
Data flow diagram
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 11
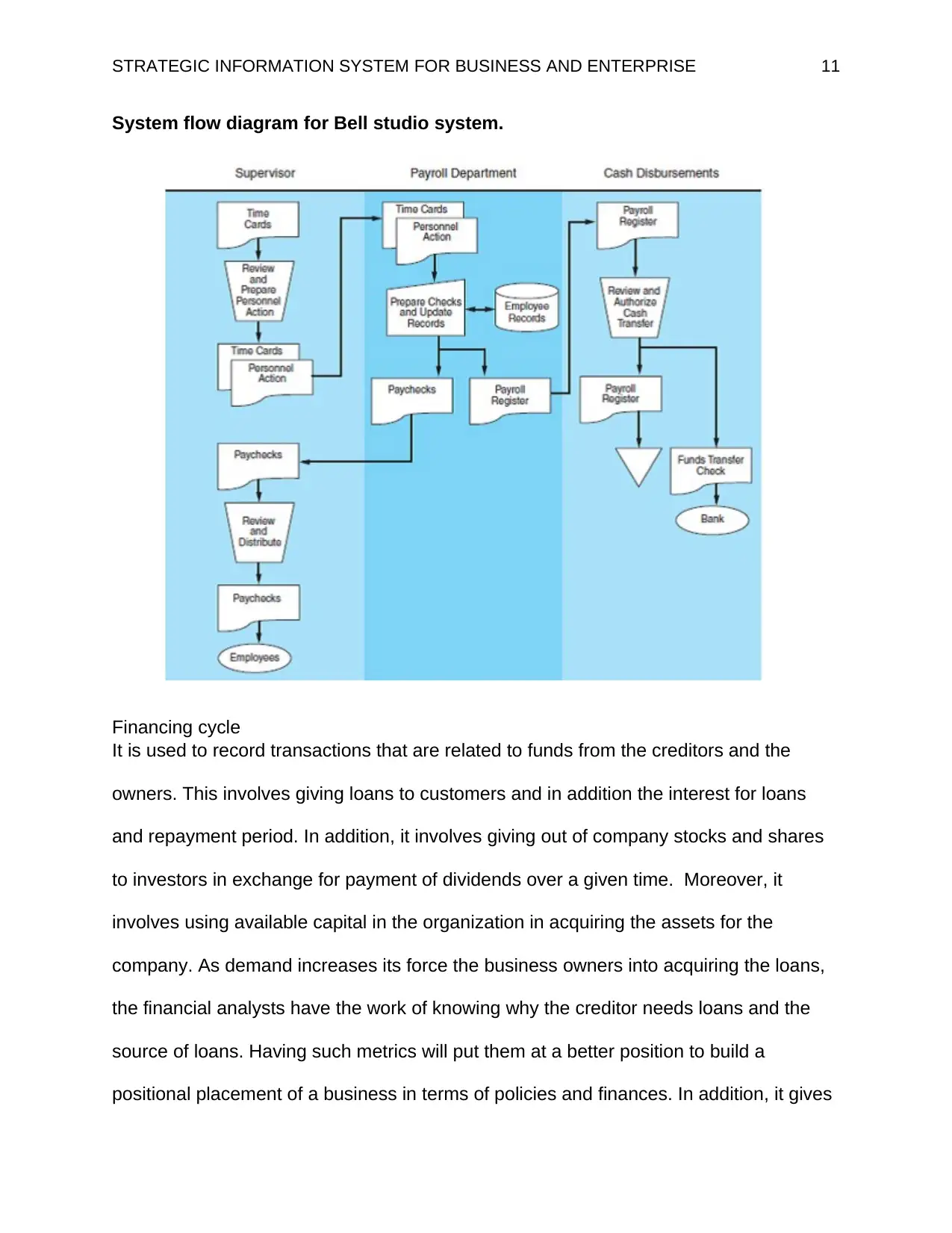
System flow diagram for Bell studio system.
Financing cycle
It is used to record transactions that are related to funds from the creditors and the
owners. This involves giving loans to customers and in addition the interest for loans
and repayment period. In addition, it involves giving out of company stocks and shares
to investors in exchange for payment of dividends over a given time. Moreover, it
involves using available capital in the organization in acquiring the assets for the
company. As demand increases its force the business owners into acquiring the loans,
the financial analysts have the work of knowing why the creditor needs loans and the
source of loans. Having such metrics will put them at a better position to build a
positional placement of a business in terms of policies and finances. In addition, it gives
System flow diagram for Bell studio system.
Financing cycle
It is used to record transactions that are related to funds from the creditors and the
owners. This involves giving loans to customers and in addition the interest for loans
and repayment period. In addition, it involves giving out of company stocks and shares
to investors in exchange for payment of dividends over a given time. Moreover, it
involves using available capital in the organization in acquiring the assets for the
company. As demand increases its force the business owners into acquiring the loans,
the financial analysts have the work of knowing why the creditor needs loans and the
source of loans. Having such metrics will put them at a better position to build a
positional placement of a business in terms of policies and finances. In addition, it gives

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 12
a clear amount of business working capital. As we know that the working capital is very
crucial for business operations when we are having great knowledge of the financial
cycle and it enables better decision making. The financial cycle is very crucial since
various business operations depend on finances.
Expenditure cycle
The expenditure cycle gives a clear review of monitoring the product to make sure that
the product reaches the required destination. In addition, it involves keeping records of
all the financial transactions of an organization. It integrates all the inventories and
journal that company records in the process of products from the suppliers. In order to
ensure transparency, most companies will not pay for the product until all payments
have been received. It is therefore very crucial to records every process involved in the
acquisition of the product. These processes include the request of the product, paying
up for the product and paying up for the product bought. In addition, this process can be
done digitally or manually by using the computer software and their objectives are to
reduce the cost of acquiring and maintaining inventories and other services for well-
functioning of the organization.
a clear amount of business working capital. As we know that the working capital is very
crucial for business operations when we are having great knowledge of the financial
cycle and it enables better decision making. The financial cycle is very crucial since
various business operations depend on finances.
Expenditure cycle
The expenditure cycle gives a clear review of monitoring the product to make sure that
the product reaches the required destination. In addition, it involves keeping records of
all the financial transactions of an organization. It integrates all the inventories and
journal that company records in the process of products from the suppliers. In order to
ensure transparency, most companies will not pay for the product until all payments
have been received. It is therefore very crucial to records every process involved in the
acquisition of the product. These processes include the request of the product, paying
up for the product and paying up for the product bought. In addition, this process can be
done digitally or manually by using the computer software and their objectives are to
reduce the cost of acquiring and maintaining inventories and other services for well-
functioning of the organization.
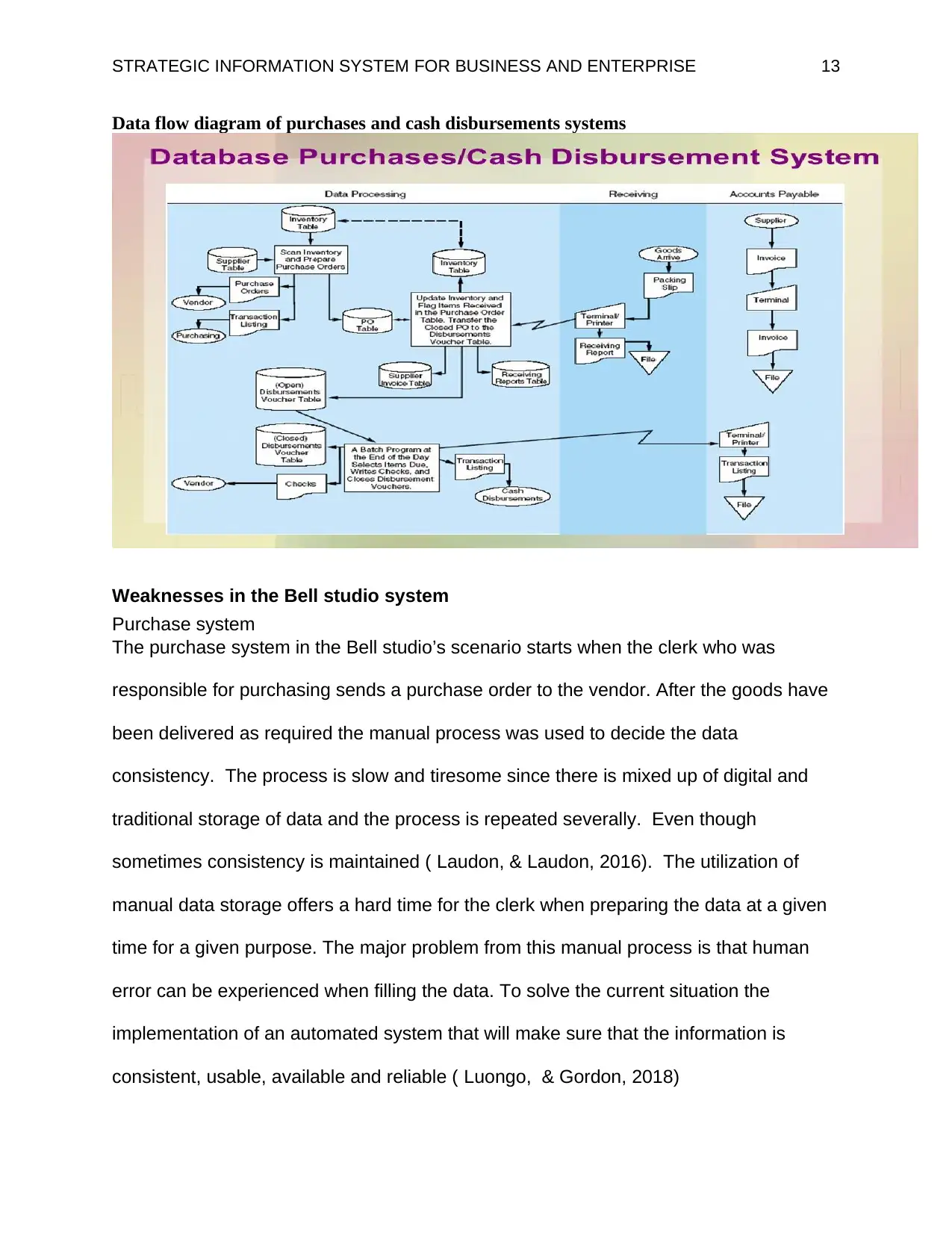
STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 13
Data flow diagram of purchases and cash disbursements systems
Weaknesses in the Bell studio system
Purchase system
The purchase system in the Bell studio’s scenario starts when the clerk who was
responsible for purchasing sends a purchase order to the vendor. After the goods have
been delivered as required the manual process was used to decide the data
consistency. The process is slow and tiresome since there is mixed up of digital and
traditional storage of data and the process is repeated severally. Even though
sometimes consistency is maintained ( Laudon, & Laudon, 2016). The utilization of
manual data storage offers a hard time for the clerk when preparing the data at a given
time for a given purpose. The major problem from this manual process is that human
error can be experienced when filling the data. To solve the current situation the
implementation of an automated system that will make sure that the information is
consistent, usable, available and reliable ( Luongo, & Gordon, 2018)
Data flow diagram of purchases and cash disbursements systems
Weaknesses in the Bell studio system
Purchase system
The purchase system in the Bell studio’s scenario starts when the clerk who was
responsible for purchasing sends a purchase order to the vendor. After the goods have
been delivered as required the manual process was used to decide the data
consistency. The process is slow and tiresome since there is mixed up of digital and
traditional storage of data and the process is repeated severally. Even though
sometimes consistency is maintained ( Laudon, & Laudon, 2016). The utilization of
manual data storage offers a hard time for the clerk when preparing the data at a given
time for a given purpose. The major problem from this manual process is that human
error can be experienced when filling the data. To solve the current situation the
implementation of an automated system that will make sure that the information is
consistent, usable, available and reliable ( Luongo, & Gordon, 2018)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 14
In addition the scenario of the Bell studio, the purchase cycle is introduced by
purchasing clerk who utilizes digital technology in determining the needs for more
stocks in the company. While ordering for stock the copy of manual purchasing order is
sent to the vendor, who then sends back a manual packing slip, which is manual as
compared with purchase order slip before it is sent to the inventory house and accounts
payable departments. The use of manual processes in the Bell studio necessities
investment in an interoperable and consolidated information system that link them to
internal systems and the vendor. This system will reduce human labor on tasks that can
be automated by adjoining these systems together.
Cash Disbursement system
The cash disbursement system is a significant operational system in the bell studio.
Thus this system needs a high level of strictness and keenness should be applied in this
system. The systems are consists of paper-based transactions and manual labor. This
creates a high risk of system confidentiality. In addition, human error can occur in this
case (Sobek, 2016). The Bell studio system possesses a manual process for the
expenditure cycle. And since the procedure is to ensure the correct flow of the
expenditure cycle, then the clerk has to match the trustworthiness of the slips and
receipts in orders to decide whether the goods are the correct ones. A strategic
information system can be used to ensure more fast services which are automated
(Ogiela, 2015).
Payroll system
Bell studio’s employee’s records always record the hours they have worked on the time
card each day. The supervisors have the responsibility to check the time cards filled by
In addition the scenario of the Bell studio, the purchase cycle is introduced by
purchasing clerk who utilizes digital technology in determining the needs for more
stocks in the company. While ordering for stock the copy of manual purchasing order is
sent to the vendor, who then sends back a manual packing slip, which is manual as
compared with purchase order slip before it is sent to the inventory house and accounts
payable departments. The use of manual processes in the Bell studio necessities
investment in an interoperable and consolidated information system that link them to
internal systems and the vendor. This system will reduce human labor on tasks that can
be automated by adjoining these systems together.
Cash Disbursement system
The cash disbursement system is a significant operational system in the bell studio.
Thus this system needs a high level of strictness and keenness should be applied in this
system. The systems are consists of paper-based transactions and manual labor. This
creates a high risk of system confidentiality. In addition, human error can occur in this
case (Sobek, 2016). The Bell studio system possesses a manual process for the
expenditure cycle. And since the procedure is to ensure the correct flow of the
expenditure cycle, then the clerk has to match the trustworthiness of the slips and
receipts in orders to decide whether the goods are the correct ones. A strategic
information system can be used to ensure more fast services which are automated
(Ogiela, 2015).
Payroll system
Bell studio’s employee’s records always record the hours they have worked on the time
card each day. The supervisors have the responsibility to check the time cards filled by

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 15
employees and submit it to the payroll department every week. Sometimes employees
may fill wrong information about the hours which they have worked. Thus the
supervisors will have a great task in confirming the attendance of the employees to work
(Rajnoha, Štefko, Merková, & Dobrovič, 2016). The computer terminal is connected to
the central of the payroll system. This weakness can be used by employees who are not
honest to increase their wages for themselves and this may pose a great threat of
information loss in the case of a computer virus infection. And since the all process
involves the manual process then the human error may be experience and data
inconstancy may also be experienced.
Risks associated with the weaknesses in the Bell Studio system
Bell studio has generally a weak system that can pose risks to the company through
computer-based threats and various attacks. The risks usually associated with the
complexity and prominence of the information that has been exposed and there are
needs to measure to avoid them. The following are risks associated with the
weaknesses in the bell studio system (Sun, Strang, & Firmin, 2017).
Hardware and software failure
In the bell studio system, it is possible to have hardware failing without external
cause. In addition, the software can also fail due to various upgrading issues. This act
may bring greater stress to the business manager. It is advisable for any company to
put in place various measure which can be used in preventing data loss through
ensuring the presence of alternatives to the using electricity. Moreover, the software
should be tested, forecasted and vetted to avoid failures( Pearlson, Saunders,&
Galletta, 2016).
employees and submit it to the payroll department every week. Sometimes employees
may fill wrong information about the hours which they have worked. Thus the
supervisors will have a great task in confirming the attendance of the employees to work
(Rajnoha, Štefko, Merková, & Dobrovič, 2016). The computer terminal is connected to
the central of the payroll system. This weakness can be used by employees who are not
honest to increase their wages for themselves and this may pose a great threat of
information loss in the case of a computer virus infection. And since the all process
involves the manual process then the human error may be experience and data
inconstancy may also be experienced.
Risks associated with the weaknesses in the Bell Studio system
Bell studio has generally a weak system that can pose risks to the company through
computer-based threats and various attacks. The risks usually associated with the
complexity and prominence of the information that has been exposed and there are
needs to measure to avoid them. The following are risks associated with the
weaknesses in the bell studio system (Sun, Strang, & Firmin, 2017).
Hardware and software failure
In the bell studio system, it is possible to have hardware failing without external
cause. In addition, the software can also fail due to various upgrading issues. This act
may bring greater stress to the business manager. It is advisable for any company to
put in place various measure which can be used in preventing data loss through
ensuring the presence of alternatives to the using electricity. Moreover, the software
should be tested, forecasted and vetted to avoid failures( Pearlson, Saunders,&
Galletta, 2016).

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 16
Computer Viruses and Malware
This is programs that are written in order to alter the normal functioning of the system.
These programs can also replicate themselves and as results, this can cause damaging
of computers (Anaya, Dulaimi, & Abdallah, 2015). It is very crucial for bell studio
management to consider in downloading free software and other similar software before
installing them into any computer system. In addition, antivirus from a reliable provider
should be installing and make sure that it can be updated every time. Also, strict policies
should be included in dealing with computer viruses. The virus can also cause various
damages and this may pose a great threat to the computer. Thus critical systems
should be given maximum prevention against any threat. Malware is malicious
programs that experience for the intention of damaging the computers without the
knowledge of the user. Some malware sometimes may appear as the actual programs
and as a result, this may confuse the user in installing software which will cause harm to
the computer( DeVan, Markwell, & Myers,2015).
Human error
Human beings are always prone to many errors. Even in a humble and goods working
environment then the error can also occur during the data entry. Errors can occur due to
careless handling of data (Koeppel, & Niderberg, 2018).
Hacking, fraud, denial-of-service
Hacking is always a major trend in an IT system. The hackers have the behavior of
hacking the system and making sure that they fully gain what they needed for the
system. The hacking process is not only performed by the professional individual it is
also performed by non-professional by using the available software tools. Hacking can
be prevented through employees’ high skills personalize who will be responsible in
Computer Viruses and Malware
This is programs that are written in order to alter the normal functioning of the system.
These programs can also replicate themselves and as results, this can cause damaging
of computers (Anaya, Dulaimi, & Abdallah, 2015). It is very crucial for bell studio
management to consider in downloading free software and other similar software before
installing them into any computer system. In addition, antivirus from a reliable provider
should be installing and make sure that it can be updated every time. Also, strict policies
should be included in dealing with computer viruses. The virus can also cause various
damages and this may pose a great threat to the computer. Thus critical systems
should be given maximum prevention against any threat. Malware is malicious
programs that experience for the intention of damaging the computers without the
knowledge of the user. Some malware sometimes may appear as the actual programs
and as a result, this may confuse the user in installing software which will cause harm to
the computer( DeVan, Markwell, & Myers,2015).
Human error
Human beings are always prone to many errors. Even in a humble and goods working
environment then the error can also occur during the data entry. Errors can occur due to
careless handling of data (Koeppel, & Niderberg, 2018).
Hacking, fraud, denial-of-service
Hacking is always a major trend in an IT system. The hackers have the behavior of
hacking the system and making sure that they fully gain what they needed for the
system. The hacking process is not only performed by the professional individual it is
also performed by non-professional by using the available software tools. Hacking can
be prevented through employees’ high skills personalize who will be responsible in
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 17
monitoring the system and also cryptographic techniques should be utilized in the
organization so that computer security is always enhanced (Chorafas,2016).
Denial of service attacks occurs when certain network traffic is diverted to a certain
website simultaneously, for it to fail the server from function in the organization. In this
attack, various hackers use various computers to launch it. The real users are denied to
get access to online services. The denial of service attacks take advantages of the
limited number of requests a server can handle, and this can be prevented by using
anti-virus software, following the required security practices and by using firewalls
(Parento, Hynes, & Sahgal, 2017).
Conclusion
The strategic information system will assist in improving the efficiency and performance
process for any business. If these systems are included in the day by day operation in
the organization then it will save the expenditure cost, reduce human error, automation
of services, reducing of computer attacks, and lastly customer experience
improvements. At since at some point there is a risk associated with the implementation
of these systems in the business, then every organization should come up with various
ways of reducing such issues (Mettler, & Winter,2016). Moreover, security policies
should be incorporated while using the system so that the security of the system is
always in place by making sure that systems work in appropriate ways. Lastly, strict
measures should be adjusted to governance every individual concerning taking note of
security issues in the organization (Gillett, 2016).
monitoring the system and also cryptographic techniques should be utilized in the
organization so that computer security is always enhanced (Chorafas,2016).
Denial of service attacks occurs when certain network traffic is diverted to a certain
website simultaneously, for it to fail the server from function in the organization. In this
attack, various hackers use various computers to launch it. The real users are denied to
get access to online services. The denial of service attacks take advantages of the
limited number of requests a server can handle, and this can be prevented by using
anti-virus software, following the required security practices and by using firewalls
(Parento, Hynes, & Sahgal, 2017).
Conclusion
The strategic information system will assist in improving the efficiency and performance
process for any business. If these systems are included in the day by day operation in
the organization then it will save the expenditure cost, reduce human error, automation
of services, reducing of computer attacks, and lastly customer experience
improvements. At since at some point there is a risk associated with the implementation
of these systems in the business, then every organization should come up with various
ways of reducing such issues (Mettler, & Winter,2016). Moreover, security policies
should be incorporated while using the system so that the security of the system is
always in place by making sure that systems work in appropriate ways. Lastly, strict
measures should be adjusted to governance every individual concerning taking note of
security issues in the organization (Gillett, 2016).

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 18
References
Anaya, L., Dulaimi, M., & Abdallah, S. 2015. An investigation into the role of enterprise
information systems in enabling business innovation. Business Process Management
Journal, 21(4), 771-790.
Chorafas, D. N. 2016. Enterprise architecture and new generation information systems.
CRC Press.
DeVan, S. M., Markwell, S., & Myers, D. 2015. U.S. Patent Application No. 14/106,999.
Gillett, P. R. 2016. Accounting Information Systems. John Wiley & Sons, Incorporated.
Koeppel, A. R., & Niderberg, A. L. 2018. U.S. Patent Application No. 15/897,401.
Laudon, K. C., & Laudon, J. P. 2016. Management information system. Pearson
Education India.
Luongo, P., & Gordon, W. 2018. U.S. Patent Application No. 10/032,153.
Mettler, T., & Winter, R. 2016. Are business users social? A design experiment
exploring information sharing in enterprise social systems. Journal of Information
Technology, 31(2), 101-114.
Ogiela, L. 2015. Advanced techniques for knowledge management and access to
strategic information. International Journal of Information Management, 35(2), 154-159.
Parento, S. A., Hynes, R. C., & Sahgal, S. 2017 U.S. Patent Application No.
15/439,254.
References
Anaya, L., Dulaimi, M., & Abdallah, S. 2015. An investigation into the role of enterprise
information systems in enabling business innovation. Business Process Management
Journal, 21(4), 771-790.
Chorafas, D. N. 2016. Enterprise architecture and new generation information systems.
CRC Press.
DeVan, S. M., Markwell, S., & Myers, D. 2015. U.S. Patent Application No. 14/106,999.
Gillett, P. R. 2016. Accounting Information Systems. John Wiley & Sons, Incorporated.
Koeppel, A. R., & Niderberg, A. L. 2018. U.S. Patent Application No. 15/897,401.
Laudon, K. C., & Laudon, J. P. 2016. Management information system. Pearson
Education India.
Luongo, P., & Gordon, W. 2018. U.S. Patent Application No. 10/032,153.
Mettler, T., & Winter, R. 2016. Are business users social? A design experiment
exploring information sharing in enterprise social systems. Journal of Information
Technology, 31(2), 101-114.
Ogiela, L. 2015. Advanced techniques for knowledge management and access to
strategic information. International Journal of Information Management, 35(2), 154-159.
Parento, S. A., Hynes, R. C., & Sahgal, S. 2017 U.S. Patent Application No.
15/439,254.

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 19
Parento, S. A., Hynes, R. C., & Sahgal, S. 2017. U.S. Patent Application No.
15/439,254.
Pearlson, K. E., Saunders, C. S., & Galletta, D. F. 2016. Managing and using
information systems, binder-ready version: a strategic approach. John Wiley & Sons.
Rajnoha, R., Štefko, R., Merková, M., & Dobrovič, J. 2016. Business intelligence as key
information and knowledge tool for strategic business performance management. E+ M
Ekonomie a Management.
Sobek, M. 2016. U.S. Patent Application No. 15/001,209.
Sun, Z., Strang, K., & Firmin, S. 2017. Business analytics-based enterprise information
systems. Journal of Computer Information Systems, 57(2), 169-178.
Parento, S. A., Hynes, R. C., & Sahgal, S. 2017. U.S. Patent Application No.
15/439,254.
Pearlson, K. E., Saunders, C. S., & Galletta, D. F. 2016. Managing and using
information systems, binder-ready version: a strategic approach. John Wiley & Sons.
Rajnoha, R., Štefko, R., Merková, M., & Dobrovič, J. 2016. Business intelligence as key
information and knowledge tool for strategic business performance management. E+ M
Ekonomie a Management.
Sobek, M. 2016. U.S. Patent Application No. 15/001,209.
Sun, Z., Strang, K., & Firmin, S. 2017. Business analytics-based enterprise information
systems. Journal of Computer Information Systems, 57(2), 169-178.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE 20
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





