Analysis of Strong Authentication and Authorization in System Design
VerifiedAdded on 2020/03/28
|4
|803
|52
Report
AI Summary
This report examines strong authentication and authorization within the context of a multi-tier client-server architecture. It highlights the advantages of this architecture, including enhanced security, elimination of single points of failure, and improved data management. The report details the functionalities of application services, data services, and business services within this framework. It emphasizes how the separation of modules and the use of load balancers contribute to increased security and scalability. Furthermore, the report discusses the influence of diverse network security needs, such as firewalls, on authentication processes. The study references several academic sources to support its findings, providing a comprehensive analysis of strong authentication and authorization in modern system design.

Running head: Strong authentication and authorization 1
Strong authentication and authorization
Name
Affiliated Institution
Strong authentication and authorization
Name
Affiliated Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Strong authentication and authorization 2
Strong authentication and authorization
When a system is proposed that requires strong authentication and authorization then multi-tier
client server architecture is most preferred and effective. In this model handling of application is
done at the client and functions data management is done at the server. Management of data is
performed right-on and thus, interaction handling between application processing and the clients
is not necessary. In multi-tier architecture application modules are separated and subdivided into
several tiers depending on their functionalities. Every tier basically executes on different
systems. This offers distribution and, therefore, doing away with the disadvantage of single point
failure. As compared to single or two-tier, security of applications and data is higher in multi-tier
architecture (Helmer, Poulovassilis, & Xhafa, 2011).
Single point of failures is eliminated in the application. Utilization of load balancer in the
distribution of traffic across several web servers’ aids in removal of single point failure. Provides
high level security: deployment of many tiers assists in enhancing data and application security.
Attackers are limited by the absence of point of failures, therefore, their ability to take control
over data and applications have been narrowed. The possibility of clients interacting with
unauthorized data has been greatly reduced as clients don’t to access the database directly.
Diverse networks have distinctive security needs which limits how an end user interacts with the
server. For instance, if an end user is connected to the internet, their communication with the
servers is regulated by a firewall. The existence of a firewall that is not under the manipulation of
a client restricts the selection of the protocols to use. several firewalls are set up to enable HTTP
(hypertext transfer protocol) to go through them and not IIOP (internet inter-orb protocol).
(Singh, 2011).
Authentication is also influenced by security requirements. Authentication of users if a client and
server are within similar security domain like an intranet of company as compared where they
are on different domains like over the internet which requires more sophisticated scheme for
logging in (Vogel, Arnold, Chughtai, & Kehrer, 2011).
According to Qian (2010), functionality of the multi-tier Architecture is considered unique as it
is subdivided into 3 logical modules including; application, business and data services. These
logical modules can be mapped into three or several physical nodules.
Strong authentication and authorization
When a system is proposed that requires strong authentication and authorization then multi-tier
client server architecture is most preferred and effective. In this model handling of application is
done at the client and functions data management is done at the server. Management of data is
performed right-on and thus, interaction handling between application processing and the clients
is not necessary. In multi-tier architecture application modules are separated and subdivided into
several tiers depending on their functionalities. Every tier basically executes on different
systems. This offers distribution and, therefore, doing away with the disadvantage of single point
failure. As compared to single or two-tier, security of applications and data is higher in multi-tier
architecture (Helmer, Poulovassilis, & Xhafa, 2011).
Single point of failures is eliminated in the application. Utilization of load balancer in the
distribution of traffic across several web servers’ aids in removal of single point failure. Provides
high level security: deployment of many tiers assists in enhancing data and application security.
Attackers are limited by the absence of point of failures, therefore, their ability to take control
over data and applications have been narrowed. The possibility of clients interacting with
unauthorized data has been greatly reduced as clients don’t to access the database directly.
Diverse networks have distinctive security needs which limits how an end user interacts with the
server. For instance, if an end user is connected to the internet, their communication with the
servers is regulated by a firewall. The existence of a firewall that is not under the manipulation of
a client restricts the selection of the protocols to use. several firewalls are set up to enable HTTP
(hypertext transfer protocol) to go through them and not IIOP (internet inter-orb protocol).
(Singh, 2011).
Authentication is also influenced by security requirements. Authentication of users if a client and
server are within similar security domain like an intranet of company as compared where they
are on different domains like over the internet which requires more sophisticated scheme for
logging in (Vogel, Arnold, Chughtai, & Kehrer, 2011).
According to Qian (2010), functionality of the multi-tier Architecture is considered unique as it
is subdivided into 3 logical modules including; application, business and data services. These
logical modules can be mapped into three or several physical nodules.
Running head: Strong authentication and authorization 3
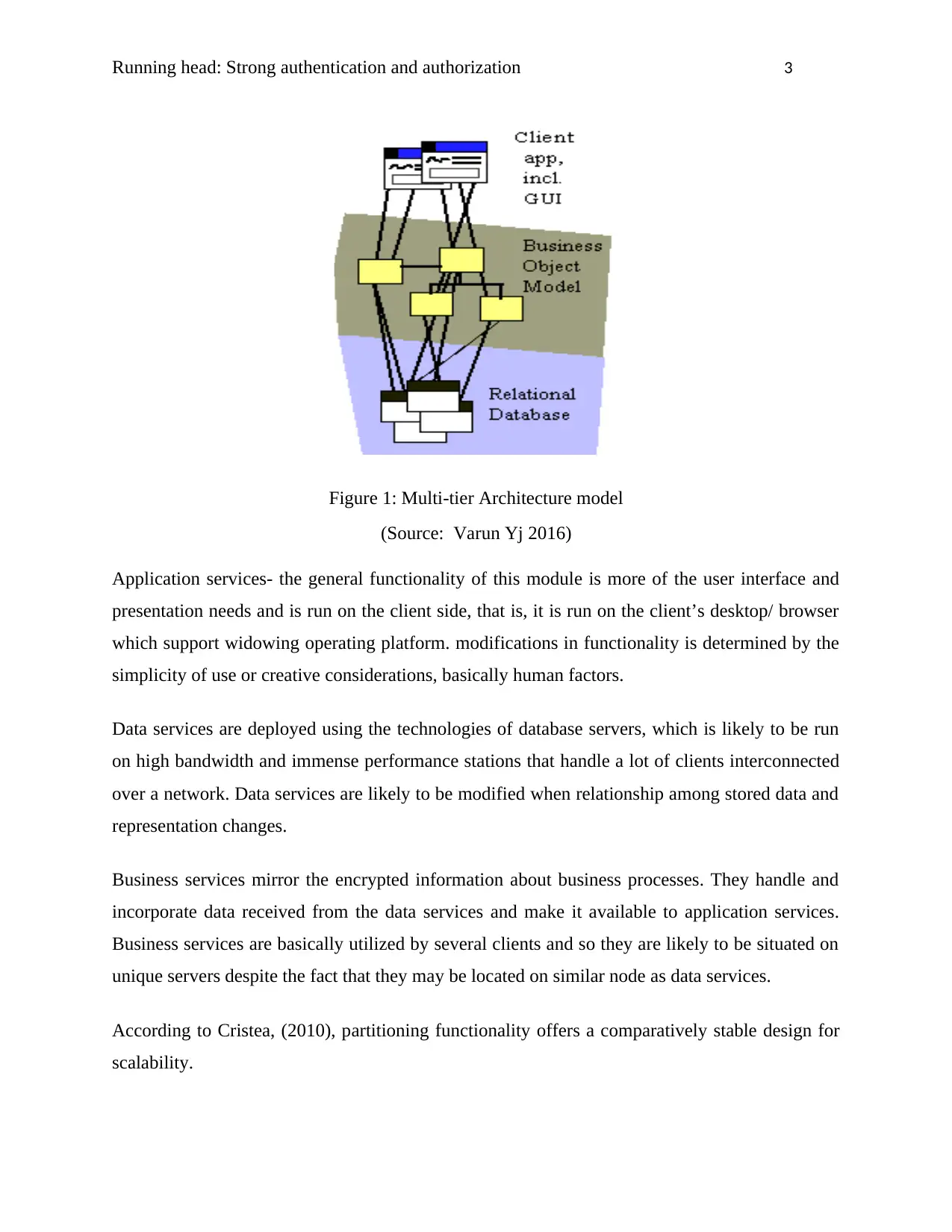
Figure 1: Multi-tier Architecture model
(Source: Varun Yj 2016)
Application services- the general functionality of this module is more of the user interface and
presentation needs and is run on the client side, that is, it is run on the client’s desktop/ browser
which support widowing operating platform. modifications in functionality is determined by the
simplicity of use or creative considerations, basically human factors.
Data services are deployed using the technologies of database servers, which is likely to be run
on high bandwidth and immense performance stations that handle a lot of clients interconnected
over a network. Data services are likely to be modified when relationship among stored data and
representation changes.
Business services mirror the encrypted information about business processes. They handle and
incorporate data received from the data services and make it available to application services.
Business services are basically utilized by several clients and so they are likely to be situated on
unique servers despite the fact that they may be located on similar node as data services.
According to Cristea, (2010), partitioning functionality offers a comparatively stable design for
scalability.
Figure 1: Multi-tier Architecture model
(Source: Varun Yj 2016)
Application services- the general functionality of this module is more of the user interface and
presentation needs and is run on the client side, that is, it is run on the client’s desktop/ browser
which support widowing operating platform. modifications in functionality is determined by the
simplicity of use or creative considerations, basically human factors.
Data services are deployed using the technologies of database servers, which is likely to be run
on high bandwidth and immense performance stations that handle a lot of clients interconnected
over a network. Data services are likely to be modified when relationship among stored data and
representation changes.
Business services mirror the encrypted information about business processes. They handle and
incorporate data received from the data services and make it available to application services.
Business services are basically utilized by several clients and so they are likely to be situated on
unique servers despite the fact that they may be located on similar node as data services.
According to Cristea, (2010), partitioning functionality offers a comparatively stable design for
scalability.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Strong authentication and authorization 4
Reference List
HELMER, S., POULOVASSILIS, A., & XHAFA, F. (2011). Reasoning in event-based
distributed systems. Berlin, Springer. http://public.eblib.com/choice/publicfullrecord.aspx?
p=3066610.
SINGH, S. K. (2011). Database systems: concepts, design and applications. Delhi, Dorling
Kindersley (India). http://proquest.safaribooksonline.com/?fpi=9788131760925.
QIAN, K. (2010). Software architecture and design illuminated. Sudbury, Mass, Jones and
Bartlett Publishers.
CRISTEA, V. (2010). Large-scale distributed computing and applications: models and trends.
Hershey, PA, Information Science Reference.
VOGEL, O., ARNOLD, I., CHUGHTAI, A., & KEHRER, T. (2011). Software architecture a
comprehensive framework and guide for practitioners. Berlin, Springer.
Reference List
HELMER, S., POULOVASSILIS, A., & XHAFA, F. (2011). Reasoning in event-based
distributed systems. Berlin, Springer. http://public.eblib.com/choice/publicfullrecord.aspx?
p=3066610.
SINGH, S. K. (2011). Database systems: concepts, design and applications. Delhi, Dorling
Kindersley (India). http://proquest.safaribooksonline.com/?fpi=9788131760925.
QIAN, K. (2010). Software architecture and design illuminated. Sudbury, Mass, Jones and
Bartlett Publishers.
CRISTEA, V. (2010). Large-scale distributed computing and applications: models and trends.
Hershey, PA, Information Science Reference.
VOGEL, O., ARNOLD, I., CHUGHTAI, A., & KEHRER, T. (2011). Software architecture a
comprehensive framework and guide for practitioners. Berlin, Springer.
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




