IoT Security and Privacy in Financial Institutions
VerifiedAdded on 2020/04/21
|18
|3563
|84
AI Summary
The assignment delves into the crucial topic of IoT security and privacy within the context of financial institutions, focusing specifically on the Central Bank of Jordan. It investigates various aspects, such as the types of security incidents experienced, the effectiveness of implemented security controls (e.g., employee training, network monitoring), and the consequences of these incidents on the bank's operations. The case study aims to shed light on the vulnerabilities and best practices for securing IoT systems within a sensitive financial environment.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: RESEARCH PROPOSAL
Research Proposal Title: Study on IoT Security and Privacy Preservation: A case study on
Central Bank of Jordan
Name of the Student:
Name of the University:
Research Proposal Title: Study on IoT Security and Privacy Preservation: A case study on
Central Bank of Jordan
Name of the Student:
Name of the University:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
RESEARCH PROPOSAL
Table of Contents
1.0 Title............................................................................................................................................2
2.0 Brief introduction.......................................................................................................................2
3.0 Background and statement of the problem................................................................................2
4.0 Research questions, aim and objectives.....................................................................................3
5.0 Study design...............................................................................................................................4
6.0 Study population and sampling.................................................................................................5
7.0 Data collection methods and instruments..................................................................................5
8.0 Data analysis methods...............................................................................................................6
9.0 Mechanisms to assure the quality of the study..........................................................................7
10.0 Timetable for completion of the project..................................................................................7
11.0 Participants in the study...........................................................................................................9
12.0 Ethical considerations..............................................................................................................9
13.0 Resources required for the study including of budget...........................................................10
References......................................................................................................................................13
Appendix........................................................................................................................................15
1. Online Questionnaire.............................................................................................................15
RESEARCH PROPOSAL
Table of Contents
1.0 Title............................................................................................................................................2
2.0 Brief introduction.......................................................................................................................2
3.0 Background and statement of the problem................................................................................2
4.0 Research questions, aim and objectives.....................................................................................3
5.0 Study design...............................................................................................................................4
6.0 Study population and sampling.................................................................................................5
7.0 Data collection methods and instruments..................................................................................5
8.0 Data analysis methods...............................................................................................................6
9.0 Mechanisms to assure the quality of the study..........................................................................7
10.0 Timetable for completion of the project..................................................................................7
11.0 Participants in the study...........................................................................................................9
12.0 Ethical considerations..............................................................................................................9
13.0 Resources required for the study including of budget...........................................................10
References......................................................................................................................................13
Appendix........................................................................................................................................15
1. Online Questionnaire.............................................................................................................15

2
RESEARCH PROPOSAL
RESEARCH PROPOSAL

3
RESEARCH PROPOSAL
1.0 Title
“Study on IoT Security and Privacy Preservation: A case study on Central Bank of
Jordan”
2.0 Brief introduction
The internet of things (IoT) is a network of network, which is connected throughout
information as well as communication infrastructure to provide of value added services. This
research study is based on analyzing the IoT security and privacy issues for the banking sector.
The selected organization for this case is Central Bank of Jordan. Into the banking organization,
large amount of data are communicated and exchanged from one place to another. Most of the
communication includes of exchange of confidential data. Aljawarneh et al. (2014) stated that
privacy preservation is also important as no party are trusted over the public network without
investigation and verification. IoT security issues are revolved around electronic currency along
with digital cash; therefore, its security is a key significant concern into Central Bank of Jordan.
Into this bank, the customer’s data are not only used for cyber frauds but also used to be sold into
black market.
3.0 Background and statement of the problem
Kipf et al. (2016) determined that some of the banks are failed to secure their system as
they experience that security of the data is related to Information Technology. Residual risks are
caused due to inadequate control of the logical as well as physical access to the system for
containing of customer data. There is also inadequate logging along with monitoring of the
RESEARCH PROPOSAL
1.0 Title
“Study on IoT Security and Privacy Preservation: A case study on Central Bank of
Jordan”
2.0 Brief introduction
The internet of things (IoT) is a network of network, which is connected throughout
information as well as communication infrastructure to provide of value added services. This
research study is based on analyzing the IoT security and privacy issues for the banking sector.
The selected organization for this case is Central Bank of Jordan. Into the banking organization,
large amount of data are communicated and exchanged from one place to another. Most of the
communication includes of exchange of confidential data. Aljawarneh et al. (2014) stated that
privacy preservation is also important as no party are trusted over the public network without
investigation and verification. IoT security issues are revolved around electronic currency along
with digital cash; therefore, its security is a key significant concern into Central Bank of Jordan.
Into this bank, the customer’s data are not only used for cyber frauds but also used to be sold into
black market.
3.0 Background and statement of the problem
Kipf et al. (2016) determined that some of the banks are failed to secure their system as
they experience that security of the data is related to Information Technology. Residual risks are
caused due to inadequate control of the logical as well as physical access to the system for
containing of customer data. There is also inadequate logging along with monitoring of the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
RESEARCH PROPOSAL
security related incidents on banking system. Buchanan et al. (2014) argued that management of
third party service providers is a big challenge for the Central Bank of Jordon. Implementation of
security into the bank is a key success for their organization. The passwords are kept encrypted
so that no unauthorized person can able to access the customer’s data. The bank employees
always inform their customers about card transaction using encrypted email and secured
communication channel. Into the URL of the bank, the application will not send any sensitive
data and information. Barkhordari et al. (2017) investigated that Central bank of Jordon adopts
limited access to their computing resources to protect the customer’s data.
The problem statement is that IoT components consist of minimal functionality, limited
computer power with storage along with lower energy resources. Therefore, it is difficult to
deploy of security and privacy preservation into the banking sector for securing the customer’s
data. Such type of deployments take advantage of the new protocols and design of system as it is
equipped to control into resource lack environments (Leverett, Clayton and Anderson 2017). Due
to continuous increase into security and privacy concerns, identification of theft and verification
of the customers are also increased. It becomes critical for the bank to verify each customer
based on his or her background and history of crime. Failure of IoT system causes damage and
there are implications for the physical safety.
4.0 Research questions, aim and objectives
4.1 Research Questions
Following are the research questions for this particular study:
RESEARCH PROPOSAL
security related incidents on banking system. Buchanan et al. (2014) argued that management of
third party service providers is a big challenge for the Central Bank of Jordon. Implementation of
security into the bank is a key success for their organization. The passwords are kept encrypted
so that no unauthorized person can able to access the customer’s data. The bank employees
always inform their customers about card transaction using encrypted email and secured
communication channel. Into the URL of the bank, the application will not send any sensitive
data and information. Barkhordari et al. (2017) investigated that Central bank of Jordon adopts
limited access to their computing resources to protect the customer’s data.
The problem statement is that IoT components consist of minimal functionality, limited
computer power with storage along with lower energy resources. Therefore, it is difficult to
deploy of security and privacy preservation into the banking sector for securing the customer’s
data. Such type of deployments take advantage of the new protocols and design of system as it is
equipped to control into resource lack environments (Leverett, Clayton and Anderson 2017). Due
to continuous increase into security and privacy concerns, identification of theft and verification
of the customers are also increased. It becomes critical for the bank to verify each customer
based on his or her background and history of crime. Failure of IoT system causes damage and
there are implications for the physical safety.
4.0 Research questions, aim and objectives
4.1 Research Questions
Following are the research questions for this particular study:

5
RESEARCH PROPOSAL
1. How can IoT become useful tool for Central Bank of Jordon to provide value added
financial services?
2. What impacts will IoT security and privacy issues have on Central Bank of Jordon?
3. What are possible security and privacy preservation strategies to mitigate the issues?
4.2 Research aims
The aim of this research study is to protect the banking data from IoT security and
privacy threats for the Central Bank of Jordon to enhance the future IoT applications. This study
also addresses the current security and privacy issues into IoT for the selected bank. Collection
of data throughout IoT solutions as well as analyze them into significant value offers protection
strategies against the security and privacy. It is significantly impact the productivity of the bank
and their financial resources.
4.3 Research objectives
Following are the objectives of the research study:
To study the benefit of IoT used into the Central Bank of Jordon to address their financial
needs
To analyze the impacts of IoT security and privacy issues into banking organization
To provide preservation solutions against the identified security and privacy issues
5.0 Study design
A cross sectional study is done for this research study on the bank employees and bank
managers into the Central Bank of Jordan. It is an observational study conducted to analyze the
data, which are collected from the population of the selected bank. It is type of descriptive study
RESEARCH PROPOSAL
1. How can IoT become useful tool for Central Bank of Jordon to provide value added
financial services?
2. What impacts will IoT security and privacy issues have on Central Bank of Jordon?
3. What are possible security and privacy preservation strategies to mitigate the issues?
4.2 Research aims
The aim of this research study is to protect the banking data from IoT security and
privacy threats for the Central Bank of Jordon to enhance the future IoT applications. This study
also addresses the current security and privacy issues into IoT for the selected bank. Collection
of data throughout IoT solutions as well as analyze them into significant value offers protection
strategies against the security and privacy. It is significantly impact the productivity of the bank
and their financial resources.
4.3 Research objectives
Following are the objectives of the research study:
To study the benefit of IoT used into the Central Bank of Jordon to address their financial
needs
To analyze the impacts of IoT security and privacy issues into banking organization
To provide preservation solutions against the identified security and privacy issues
5.0 Study design
A cross sectional study is done for this research study on the bank employees and bank
managers into the Central Bank of Jordan. It is an observational study conducted to analyze the
data, which are collected from the population of the selected bank. It is type of descriptive study

6
RESEARCH PROPOSAL
which is done to analyze determine occurrence of data thefts and frauds. It collects of data at
defined time (Metalidou et al. 2014). At this study stage, security of information, privacy as well
as protection of data is addressed. Throughout this study, the researcher assesses the causes of
the IoT security and privacy issues. It involves of data collection about the past and present data
thefts and frauds incidents and relies in originated of collected data (Roman, Zhou and Lopez
2013). The target populations for this research study are the bank employees and managers. In
order to conduct this study, Jordon is mainly focused for this particular research study.
6.0 Study population and sampling
The populations selected for this study are bank employees and bank managers. Random
sampling procedure is selected for this study to select of required participants. Central bank of
Jordon is selected as the organization where the entire research study has taken place, which is
grouped into both workers and managers. The selected sampling method is unbiased presentation
of the group (Sicari et al. 2015). Using simple random sample method, the employees are
selected from large population. There are total of 50 employees are selected from a large
population as they are interested into the study along with 3 bank managers.
7.0 Data collection methods and instruments
Yan, Zhang and Vasilakos (2014) stated that data are useful for collecting of information
to study of the research topic. It provides with accurate results of the research process. Data are
collected from the peer reviewed articles which addressed IoT security and privacy preservation
information. Based on the title, various articles are identified. The articles, which are published
IoT security and privacy preservation, are taken for this research study (Li et al. 2016). Google
RESEARCH PROPOSAL
which is done to analyze determine occurrence of data thefts and frauds. It collects of data at
defined time (Metalidou et al. 2014). At this study stage, security of information, privacy as well
as protection of data is addressed. Throughout this study, the researcher assesses the causes of
the IoT security and privacy issues. It involves of data collection about the past and present data
thefts and frauds incidents and relies in originated of collected data (Roman, Zhou and Lopez
2013). The target populations for this research study are the bank employees and managers. In
order to conduct this study, Jordon is mainly focused for this particular research study.
6.0 Study population and sampling
The populations selected for this study are bank employees and bank managers. Random
sampling procedure is selected for this study to select of required participants. Central bank of
Jordon is selected as the organization where the entire research study has taken place, which is
grouped into both workers and managers. The selected sampling method is unbiased presentation
of the group (Sicari et al. 2015). Using simple random sample method, the employees are
selected from large population. There are total of 50 employees are selected from a large
population as they are interested into the study along with 3 bank managers.
7.0 Data collection methods and instruments
Yan, Zhang and Vasilakos (2014) stated that data are useful for collecting of information
to study of the research topic. It provides with accurate results of the research process. Data are
collected from the peer reviewed articles which addressed IoT security and privacy preservation
information. Based on the title, various articles are identified. The articles, which are published
IoT security and privacy preservation, are taken for this research study (Li et al. 2016). Google
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
RESEARCH PROPOSAL
scholar and university website is used to search for the required data. The keywords used for this
study are IoT, privacy, security. An online survey is also conducted using questionnaire. The
participants involved in this study are bank employees those are facing IoT security and privacy
issues (Zhou et al. 2017). Using their feedback, the bank managers take proper IoT security
preservation steps to overcome the identified data threats and frauds issues.
Research Instrument considered for this particular research study is demographic
information of the employees and managers. Under the demographic information, the factors are
age, educational status and economic status (Tonyali et al. 2018). Online questionnaire is also
taken to take survey of the employees and managers to determine the occurrence of data thefts
and frauds. The survey also helps to determine the solutions against the security and privacy
issues.
8.0 Data analysis methods
There are two types of data analysis method selected for this particular research study is
qualitative and quantitative data analysis method. Qualitative data is used to record the data,
which will better describe the selected research topic in detailed form. It provides with
theoretical concept into practical form, which will better describe and help to understand the
topic. On the other hand, quantitative data analysis method is used to apply of statistical data,
which help to record of the data with larger sample size. In this particular study, quantitative data
analysis method is used to do the survey of bank employees (Lowry, Dinev and Willison 2017).
The researcher uses this particular technique to convert the data into numerical forms. It is
subject to the statistical analysis of the collected data. The primary findings of this study are
required to analyze and interpret throughout comparing it with other research findings. Based on
RESEARCH PROPOSAL
scholar and university website is used to search for the required data. The keywords used for this
study are IoT, privacy, security. An online survey is also conducted using questionnaire. The
participants involved in this study are bank employees those are facing IoT security and privacy
issues (Zhou et al. 2017). Using their feedback, the bank managers take proper IoT security
preservation steps to overcome the identified data threats and frauds issues.
Research Instrument considered for this particular research study is demographic
information of the employees and managers. Under the demographic information, the factors are
age, educational status and economic status (Tonyali et al. 2018). Online questionnaire is also
taken to take survey of the employees and managers to determine the occurrence of data thefts
and frauds. The survey also helps to determine the solutions against the security and privacy
issues.
8.0 Data analysis methods
There are two types of data analysis method selected for this particular research study is
qualitative and quantitative data analysis method. Qualitative data is used to record the data,
which will better describe the selected research topic in detailed form. It provides with
theoretical concept into practical form, which will better describe and help to understand the
topic. On the other hand, quantitative data analysis method is used to apply of statistical data,
which help to record of the data with larger sample size. In this particular study, quantitative data
analysis method is used to do the survey of bank employees (Lowry, Dinev and Willison 2017).
The researcher uses this particular technique to convert the data into numerical forms. It is
subject to the statistical analysis of the collected data. The primary findings of this study are
required to analyze and interpret throughout comparing it with other research findings. Based on

8
RESEARCH PROPOSAL
quantitative data analysis method, it is expected to turn of raw materials into meaningful data
throughout application of critical thinking (Zhang et al. 2014). The primary data findings are
critically analyzed and interpreted throughout use of questionnaire survey. Literature review
findings are also conducted from the peer review journal articles reflected viewpoints of the
authors regarding causes of IoT security and privacy issues.
9.0 Mechanisms to assure the quality of the study
The researcher assured about excellence of the gathered data and said that all the quality
data are helpful for conducting the study. Into the research community, quality assurance as well
as assessment plays a key important role. It informs about crucial decisions regarding project
funding as well as project team members. Assured about the quality of the research increases the
volume of research, competition among the researcher and provides with effective research
outputs. Barkhordari et al. (2017) mentioned that into the research process, assurance of quality
and assessment is critical for each stages of the research study. The researcher collects of data
from scholarly publications and peer reviewed journal articles, which provide quality
information and data to the researcher. The journal in addition to research sources are searched
and the papers are included if it addressed the quality assurance into quantitative paradigm.
Narrative approach is used to review as well as syntheses of the literature.
10.0 Timetable for completion of the project
This research study is cross sectional, which is dependent on the time scheduled for the
research. As it is a cross sectional study, therefore it adopts of limited time which requires of
Gantt chart to complete the research work. Gantt chart helps to show all the project activities to
RESEARCH PROPOSAL
quantitative data analysis method, it is expected to turn of raw materials into meaningful data
throughout application of critical thinking (Zhang et al. 2014). The primary data findings are
critically analyzed and interpreted throughout use of questionnaire survey. Literature review
findings are also conducted from the peer review journal articles reflected viewpoints of the
authors regarding causes of IoT security and privacy issues.
9.0 Mechanisms to assure the quality of the study
The researcher assured about excellence of the gathered data and said that all the quality
data are helpful for conducting the study. Into the research community, quality assurance as well
as assessment plays a key important role. It informs about crucial decisions regarding project
funding as well as project team members. Assured about the quality of the research increases the
volume of research, competition among the researcher and provides with effective research
outputs. Barkhordari et al. (2017) mentioned that into the research process, assurance of quality
and assessment is critical for each stages of the research study. The researcher collects of data
from scholarly publications and peer reviewed journal articles, which provide quality
information and data to the researcher. The journal in addition to research sources are searched
and the papers are included if it addressed the quality assurance into quantitative paradigm.
Narrative approach is used to review as well as syntheses of the literature.
10.0 Timetable for completion of the project
This research study is cross sectional, which is dependent on the time scheduled for the
research. As it is a cross sectional study, therefore it adopts of limited time which requires of
Gantt chart to complete the research work. Gantt chart helps to show all the project activities to
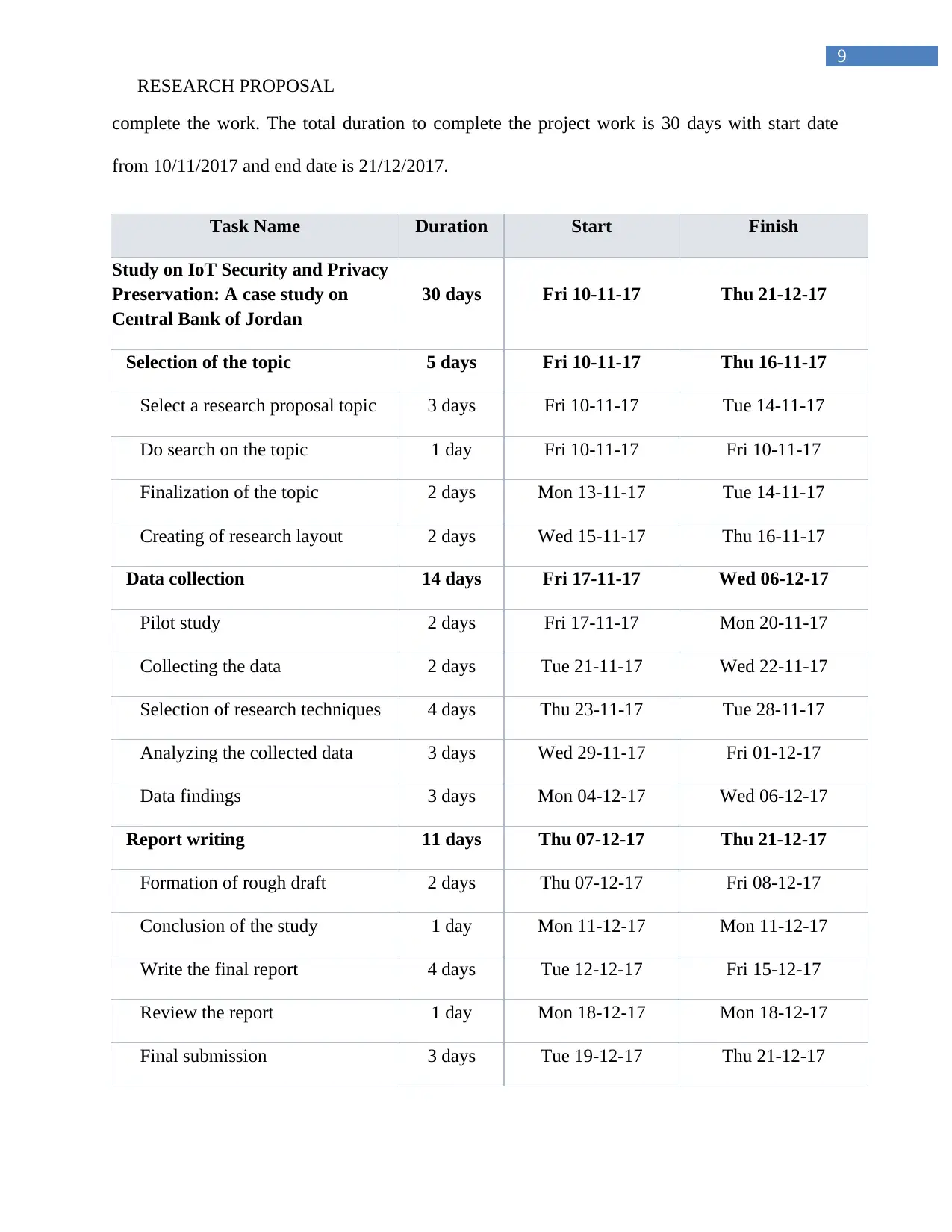
9
RESEARCH PROPOSAL
complete the work. The total duration to complete the project work is 30 days with start date
from 10/11/2017 and end date is 21/12/2017.
Task Name Duration Start Finish
Study on IoT Security and Privacy
Preservation: A case study on
Central Bank of Jordan
30 days Fri 10-11-17 Thu 21-12-17
Selection of the topic 5 days Fri 10-11-17 Thu 16-11-17
Select a research proposal topic 3 days Fri 10-11-17 Tue 14-11-17
Do search on the topic 1 day Fri 10-11-17 Fri 10-11-17
Finalization of the topic 2 days Mon 13-11-17 Tue 14-11-17
Creating of research layout 2 days Wed 15-11-17 Thu 16-11-17
Data collection 14 days Fri 17-11-17 Wed 06-12-17
Pilot study 2 days Fri 17-11-17 Mon 20-11-17
Collecting the data 2 days Tue 21-11-17 Wed 22-11-17
Selection of research techniques 4 days Thu 23-11-17 Tue 28-11-17
Analyzing the collected data 3 days Wed 29-11-17 Fri 01-12-17
Data findings 3 days Mon 04-12-17 Wed 06-12-17
Report writing 11 days Thu 07-12-17 Thu 21-12-17
Formation of rough draft 2 days Thu 07-12-17 Fri 08-12-17
Conclusion of the study 1 day Mon 11-12-17 Mon 11-12-17
Write the final report 4 days Tue 12-12-17 Fri 15-12-17
Review the report 1 day Mon 18-12-17 Mon 18-12-17
Final submission 3 days Tue 19-12-17 Thu 21-12-17
RESEARCH PROPOSAL
complete the work. The total duration to complete the project work is 30 days with start date
from 10/11/2017 and end date is 21/12/2017.
Task Name Duration Start Finish
Study on IoT Security and Privacy
Preservation: A case study on
Central Bank of Jordan
30 days Fri 10-11-17 Thu 21-12-17
Selection of the topic 5 days Fri 10-11-17 Thu 16-11-17
Select a research proposal topic 3 days Fri 10-11-17 Tue 14-11-17
Do search on the topic 1 day Fri 10-11-17 Fri 10-11-17
Finalization of the topic 2 days Mon 13-11-17 Tue 14-11-17
Creating of research layout 2 days Wed 15-11-17 Thu 16-11-17
Data collection 14 days Fri 17-11-17 Wed 06-12-17
Pilot study 2 days Fri 17-11-17 Mon 20-11-17
Collecting the data 2 days Tue 21-11-17 Wed 22-11-17
Selection of research techniques 4 days Thu 23-11-17 Tue 28-11-17
Analyzing the collected data 3 days Wed 29-11-17 Fri 01-12-17
Data findings 3 days Mon 04-12-17 Wed 06-12-17
Report writing 11 days Thu 07-12-17 Thu 21-12-17
Formation of rough draft 2 days Thu 07-12-17 Fri 08-12-17
Conclusion of the study 1 day Mon 11-12-17 Mon 11-12-17
Write the final report 4 days Tue 12-12-17 Fri 15-12-17
Review the report 1 day Mon 18-12-17 Mon 18-12-17
Final submission 3 days Tue 19-12-17 Thu 21-12-17
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
RESEARCH PROPOSAL
11.0 Participants in the study
Central bank of Jordon provides financial services to the customers in Jordon. The study
is conducted to analyze IoT security and privacy preservation into the bank sector. For this
particular study, the selected participants are the bank employees who are facing the data threats
and the bank managers those are providing solutions against the threats. The participants provide
answers to the questions related to selected research study. The participants can contract the
researcher with the questions at all time before and during the study. They discussed the benefits
as well as risks which are associated with IoT.
12.0 Ethical considerations
For commencement of this research study, ethical approval from the Central bank of
Jordon is required in which the cross-sectional survey is conducted. The researcher is trained to
take data on the security threats and frauds. Ethical considerations are addressed to seek
permission from the participants ahead of they are allowed to involve in the research study.
Sicari et al. (2015) indicated that consent form provides the participants with detailed
information such as study purpose, details of researcher, information about nature of participants
and their role, period of the study and privacy of the provided data. The employees are educated
that they are participating into the study as volunteer and they are asked to sign agreement to
point to their willingness of participation (Leverett, Clayton and Anderson 2017). Other
participants such as managers are also invited to contribute into the study. The collected data for
the research study are not shared with any third party and no other unauthorized person can able
to access the data. All the involved participants are educated that they can remove from the
RESEARCH PROPOSAL
11.0 Participants in the study
Central bank of Jordon provides financial services to the customers in Jordon. The study
is conducted to analyze IoT security and privacy preservation into the bank sector. For this
particular study, the selected participants are the bank employees who are facing the data threats
and the bank managers those are providing solutions against the threats. The participants provide
answers to the questions related to selected research study. The participants can contract the
researcher with the questions at all time before and during the study. They discussed the benefits
as well as risks which are associated with IoT.
12.0 Ethical considerations
For commencement of this research study, ethical approval from the Central bank of
Jordon is required in which the cross-sectional survey is conducted. The researcher is trained to
take data on the security threats and frauds. Ethical considerations are addressed to seek
permission from the participants ahead of they are allowed to involve in the research study.
Sicari et al. (2015) indicated that consent form provides the participants with detailed
information such as study purpose, details of researcher, information about nature of participants
and their role, period of the study and privacy of the provided data. The employees are educated
that they are participating into the study as volunteer and they are asked to sign agreement to
point to their willingness of participation (Leverett, Clayton and Anderson 2017). Other
participants such as managers are also invited to contribute into the study. The collected data for
the research study are not shared with any third party and no other unauthorized person can able
to access the data. All the involved participants are educated that they can remove from the
11
RESEARCH PROPOSAL
learning anytime. Codes are used to label the questionnaires throughout the data collection in the
study to make sure that privacy of the participants is appreciated into research process.
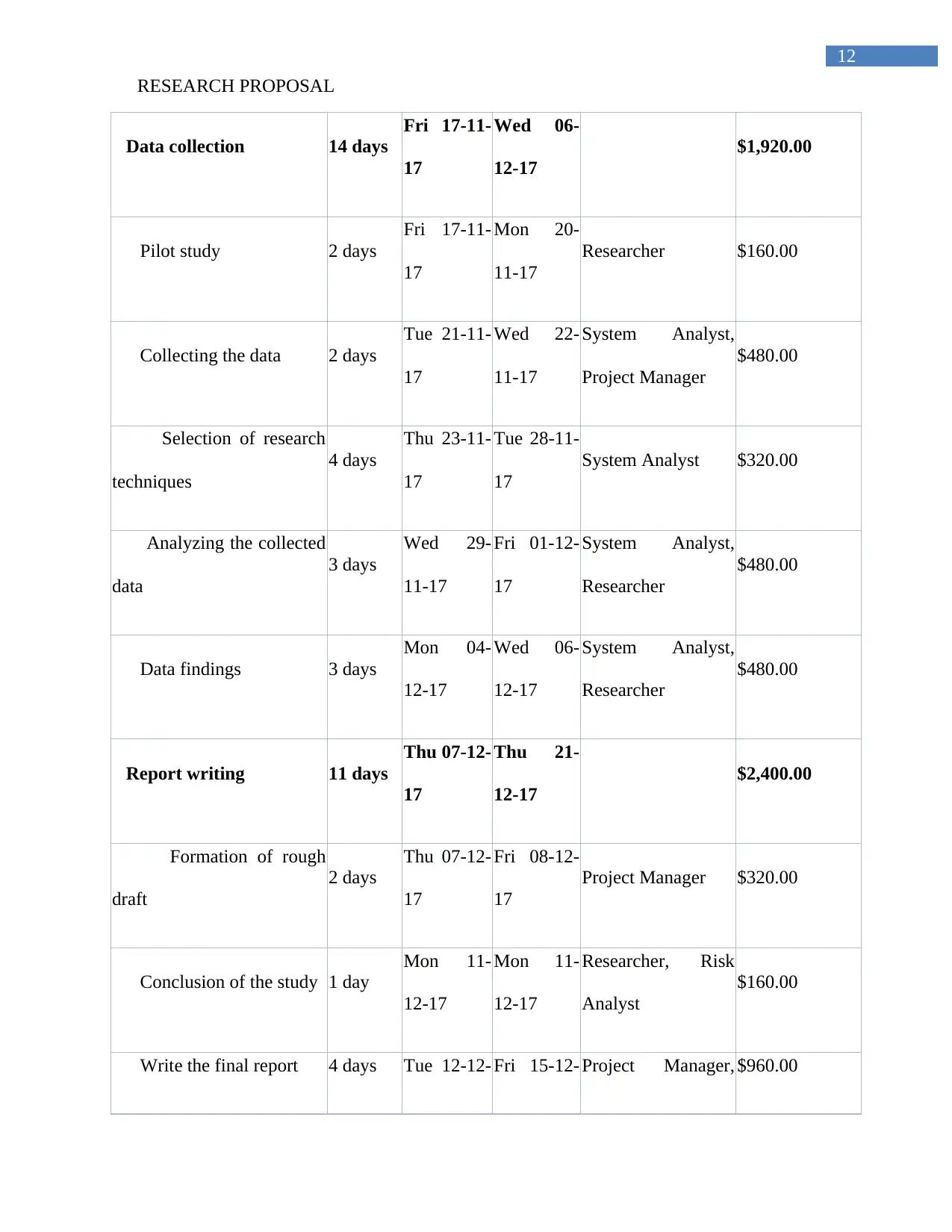
13.0 Resources required for the study including of budget
Task Name Duration Start Finish Resource Names Cost
Study on IoT Security and
Privacy Preservation: A
case study on Central
Bank of Jordan
30 days
Fri 10-11-
17
Thu 21-
12-17
$6,080.00
Selection of the topic 5 days
Fri 10-11-
17
Thu 16-
11-17
$1,760.00
Select a research
proposal topic
3 days
Fri 10-11-
17
Tue 14-11-
17
Project Manager,
Researcher
$720.00
Do search on the topic 1 day
Fri 10-11-
17
Fri 10-11-
17
Researcher $80.00
Finalization of the topic 2 days
Mon 13-
11-17
Tue 14-11-
17
Project Manager $320.00
Creating of research
layout
2 days
Wed 15-
11-17
Thu 16-11-
17
System Analyst,
Project Manager,
Developer
$640.00
RESEARCH PROPOSAL
learning anytime. Codes are used to label the questionnaires throughout the data collection in the
study to make sure that privacy of the participants is appreciated into research process.
13.0 Resources required for the study including of budget
Task Name Duration Start Finish Resource Names Cost
Study on IoT Security and
Privacy Preservation: A
case study on Central
Bank of Jordan
30 days
Fri 10-11-
17
Thu 21-
12-17
$6,080.00
Selection of the topic 5 days
Fri 10-11-
17
Thu 16-
11-17
$1,760.00
Select a research
proposal topic
3 days
Fri 10-11-
17
Tue 14-11-
17
Project Manager,
Researcher
$720.00
Do search on the topic 1 day
Fri 10-11-
17
Fri 10-11-
17
Researcher $80.00
Finalization of the topic 2 days
Mon 13-
11-17
Tue 14-11-
17
Project Manager $320.00
Creating of research
layout
2 days
Wed 15-
11-17
Thu 16-11-
17
System Analyst,
Project Manager,
Developer
$640.00
12
RESEARCH PROPOSAL
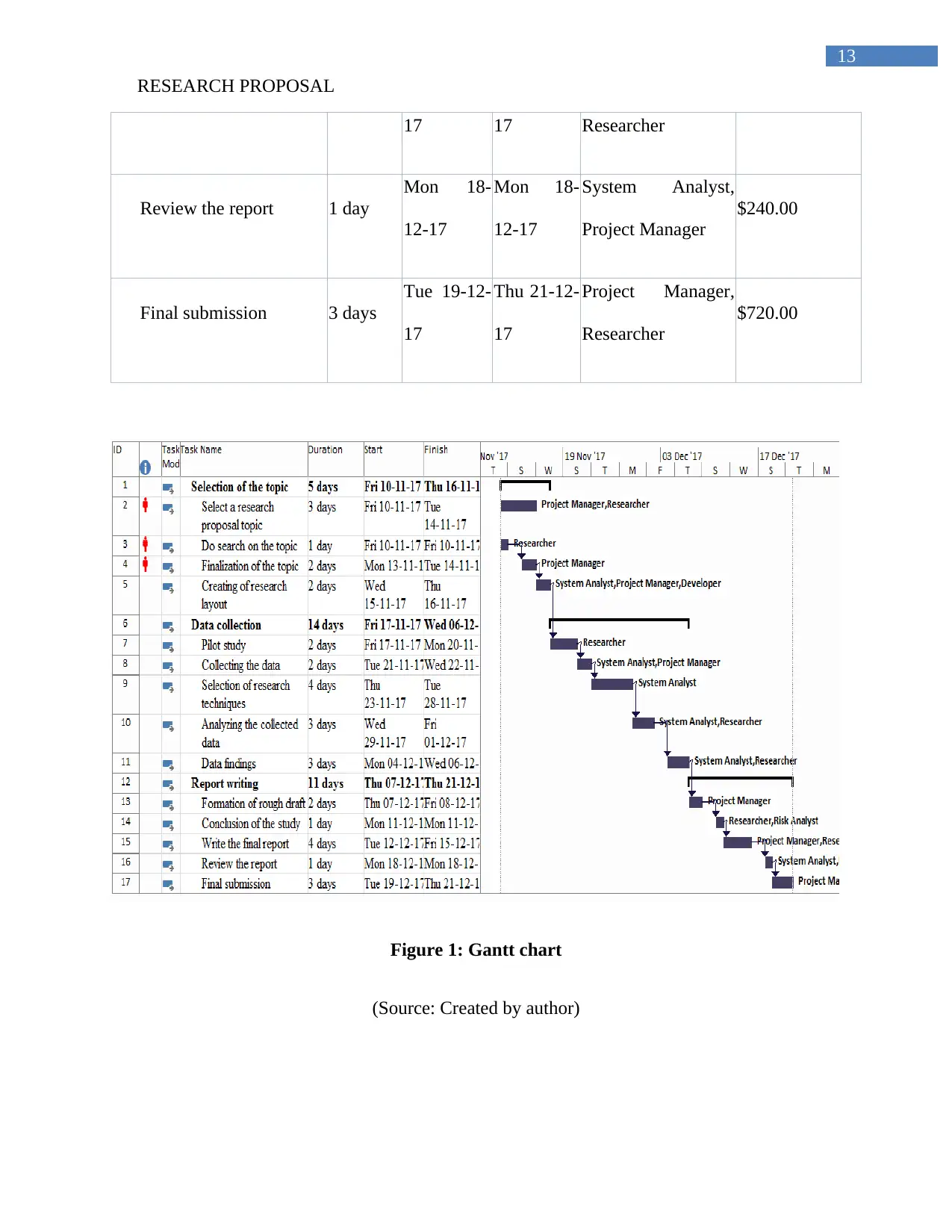
Data collection 14 days
Fri 17-11-
17
Wed 06-
12-17
$1,920.00
Pilot study 2 days
Fri 17-11-
17
Mon 20-
11-17
Researcher $160.00
Collecting the data 2 days
Tue 21-11-
17
Wed 22-
11-17
System Analyst,
Project Manager
$480.00
Selection of research
techniques
4 days
Thu 23-11-
17
Tue 28-11-
17
System Analyst $320.00
Analyzing the collected
data
3 days
Wed 29-
11-17
Fri 01-12-
17
System Analyst,
Researcher
$480.00
Data findings 3 days
Mon 04-
12-17
Wed 06-
12-17
System Analyst,
Researcher
$480.00
Report writing 11 days
Thu 07-12-
17
Thu 21-
12-17
$2,400.00
Formation of rough
draft
2 days
Thu 07-12-
17
Fri 08-12-
17
Project Manager $320.00
Conclusion of the study 1 day
Mon 11-
12-17
Mon 11-
12-17
Researcher, Risk
Analyst
$160.00
Write the final report 4 days Tue 12-12- Fri 15-12- Project Manager, $960.00
RESEARCH PROPOSAL
Data collection 14 days
Fri 17-11-
17
Wed 06-
12-17
$1,920.00
Pilot study 2 days
Fri 17-11-
17
Mon 20-
11-17
Researcher $160.00
Collecting the data 2 days
Tue 21-11-
17
Wed 22-
11-17
System Analyst,
Project Manager
$480.00
Selection of research
techniques
4 days
Thu 23-11-
17
Tue 28-11-
17
System Analyst $320.00
Analyzing the collected
data
3 days
Wed 29-
11-17
Fri 01-12-
17
System Analyst,
Researcher
$480.00
Data findings 3 days
Mon 04-
12-17
Wed 06-
12-17
System Analyst,
Researcher
$480.00
Report writing 11 days
Thu 07-12-
17
Thu 21-
12-17
$2,400.00
Formation of rough
draft
2 days
Thu 07-12-
17
Fri 08-12-
17
Project Manager $320.00
Conclusion of the study 1 day
Mon 11-
12-17
Mon 11-
12-17
Researcher, Risk
Analyst
$160.00
Write the final report 4 days Tue 12-12- Fri 15-12- Project Manager, $960.00
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13
RESEARCH PROPOSAL
17 17 Researcher
Review the report 1 day
Mon 18-
12-17
Mon 18-
12-17
System Analyst,
Project Manager
$240.00
Final submission 3 days
Tue 19-12-
17
Thu 21-12-
17
Project Manager,
Researcher
$720.00
Figure 1: Gantt chart
(Source: Created by author)
RESEARCH PROPOSAL
17 17 Researcher
Review the report 1 day
Mon 18-
12-17
Mon 18-
12-17
System Analyst,
Project Manager
$240.00
Final submission 3 days
Tue 19-12-
17
Thu 21-12-
17
Project Manager,
Researcher
$720.00
Figure 1: Gantt chart
(Source: Created by author)

14
RESEARCH PROPOSAL
References
Aljawarneh, S., Al-Rousan, T., Maatuk, A.M. and Akour, M., 2014. Usage of data validation
techniques in online banking: A perspective and case study. Security Journal, 27(1), pp.27-35.
Barkhordari, M., Nourollah, Z., Mashayekhi, H., Mashayekhi, Y. and Ahangar, M.S., 2017.
Factors influencing adoption of e-payment systems: an empirical study on Iranian
customers. Information Systems and e-Business Management, 15(1), pp.89-116.
Buchanan, F.R., Buchanan, F.R., Ahmad, S.Z. and Ahmad, S.Z., 2014. Business in developing
countries: globalization of a large emerging market bank. Emerald Emerging Markets Case
Studies, 4(6), pp.1-16.
Kipf, A., Brunette, W., Kellerstrass, J., Podolsky, M., Rosa, J., Sundt, M., Wilson, D., Borriello,
G., Brewer, E. and Thomas, E., 2016. A proposed integrated data collection, analysis and sharing
platform for impact evaluation. Development Engineering, 1, pp.36-44.
Leverett, É., Clayton, R. and Anderson, R., 2017. Standardisation and Certification of the
‘Internet of Things’.
Li, Y., Zhou, L., Zhu, H. and Sun, L., 2016. Privacy-preserving location proof for securing large-
scale database-driven cognitive radio networks. IEEE Internet of Things Journal, 3(4), pp.563-
571.
Lowry, P.B., Dinev, T. and Willison, R., 2017. Why Security and Privacy Research Lies at the
Centre of the Information Systems (is) Artefact: Proposing a Bold Research Agenda.
RESEARCH PROPOSAL
References
Aljawarneh, S., Al-Rousan, T., Maatuk, A.M. and Akour, M., 2014. Usage of data validation
techniques in online banking: A perspective and case study. Security Journal, 27(1), pp.27-35.
Barkhordari, M., Nourollah, Z., Mashayekhi, H., Mashayekhi, Y. and Ahangar, M.S., 2017.
Factors influencing adoption of e-payment systems: an empirical study on Iranian
customers. Information Systems and e-Business Management, 15(1), pp.89-116.
Buchanan, F.R., Buchanan, F.R., Ahmad, S.Z. and Ahmad, S.Z., 2014. Business in developing
countries: globalization of a large emerging market bank. Emerald Emerging Markets Case
Studies, 4(6), pp.1-16.
Kipf, A., Brunette, W., Kellerstrass, J., Podolsky, M., Rosa, J., Sundt, M., Wilson, D., Borriello,
G., Brewer, E. and Thomas, E., 2016. A proposed integrated data collection, analysis and sharing
platform for impact evaluation. Development Engineering, 1, pp.36-44.
Leverett, É., Clayton, R. and Anderson, R., 2017. Standardisation and Certification of the
‘Internet of Things’.
Li, Y., Zhou, L., Zhu, H. and Sun, L., 2016. Privacy-preserving location proof for securing large-
scale database-driven cognitive radio networks. IEEE Internet of Things Journal, 3(4), pp.563-
571.
Lowry, P.B., Dinev, T. and Willison, R., 2017. Why Security and Privacy Research Lies at the
Centre of the Information Systems (is) Artefact: Proposing a Bold Research Agenda.

15
RESEARCH PROPOSAL
Metalidou, E., Marinagi, C., Trivellas, P., Eberhagen, N., Giannakopoulos, G. and Skourlas, C.,
2014. Human factor and information security in higher education. Journal of Systems and
Information Technology, 16(3), pp.210-221.
Roman, R., Zhou, J. and Lopez, J., 2013. On the features and challenges of security and privacy
in distributed internet of things. Computer Networks, 57(10), pp.2266-2279.
Sicari, S., Rizzardi, A., Grieco, L.A. and Coen-Porisini, A., 2015. Security, privacy and trust in
Internet of Things: The road ahead. Computer Networks, 76, pp.146-164.
Tonyali, S., Akkaya, K., Saputro, N., Uluagac, A.S. and Nojoumian, M., 2018. Privacy-
preserving protocols for secure and reliable data aggregation in IoT-enabled smart metering
systems. Future Generation Computer Systems, 78, pp.547-557.
Yan, Z., Zhang, P. and Vasilakos, A.V., 2014. A survey on trust management for Internet of
Things. Journal of network and computer applications, 42, pp.120-134.
Zhang, Z.K., Cho, M.C.Y., Wang, C.W., Hsu, C.W., Chen, C.K. and Shieh, S., 2014, November.
IoT security: ongoing challenges and research opportunities. In Service-Oriented Computing and
Applications (SOCA), 2014 IEEE 7th International Conference on (pp. 230-234). IEEE.
Zhou, J., Cao, Z., Dong, X. and Vasilakos, A.V., 2017. Security and privacy for cloud-based IoT:
challenges. IEEE Communications Magazine, 55(1), pp.26-33.
RESEARCH PROPOSAL
Metalidou, E., Marinagi, C., Trivellas, P., Eberhagen, N., Giannakopoulos, G. and Skourlas, C.,
2014. Human factor and information security in higher education. Journal of Systems and
Information Technology, 16(3), pp.210-221.
Roman, R., Zhou, J. and Lopez, J., 2013. On the features and challenges of security and privacy
in distributed internet of things. Computer Networks, 57(10), pp.2266-2279.
Sicari, S., Rizzardi, A., Grieco, L.A. and Coen-Porisini, A., 2015. Security, privacy and trust in
Internet of Things: The road ahead. Computer Networks, 76, pp.146-164.
Tonyali, S., Akkaya, K., Saputro, N., Uluagac, A.S. and Nojoumian, M., 2018. Privacy-
preserving protocols for secure and reliable data aggregation in IoT-enabled smart metering
systems. Future Generation Computer Systems, 78, pp.547-557.
Yan, Z., Zhang, P. and Vasilakos, A.V., 2014. A survey on trust management for Internet of
Things. Journal of network and computer applications, 42, pp.120-134.
Zhang, Z.K., Cho, M.C.Y., Wang, C.W., Hsu, C.W., Chen, C.K. and Shieh, S., 2014, November.
IoT security: ongoing challenges and research opportunities. In Service-Oriented Computing and
Applications (SOCA), 2014 IEEE 7th International Conference on (pp. 230-234). IEEE.
Zhou, J., Cao, Z., Dong, X. and Vasilakos, A.V., 2017. Security and privacy for cloud-based IoT:
challenges. IEEE Communications Magazine, 55(1), pp.26-33.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16
RESEARCH PROPOSAL
Appendix
1. Online Questionnaire
Research title: Study on IoT Security and Privacy Preservation: A case study on Central Bank
of Jordan
1. What is the role of your organization into the financial industry?
a. Banking-retail
b. Banking-commercial
c. Accountancy
d. Banking-Investment
2. What is the size of the workforce at your organization?
a. Fewer than 100
b. 1001-2000
c. 2001-5000
d. 5001-10,000
3. Has your organization suffered from any IoT security and privacy incidents, which affect
your financial organization?
a. Yes
b. Do not know
c. Do not know and do not suspect
d. No, we do not have
4. Does decrease of IoT security incidents affect the bank organization?
a. Significant affect
RESEARCH PROPOSAL
Appendix
1. Online Questionnaire
Research title: Study on IoT Security and Privacy Preservation: A case study on Central Bank
of Jordan
1. What is the role of your organization into the financial industry?
a. Banking-retail
b. Banking-commercial
c. Accountancy
d. Banking-Investment
2. What is the size of the workforce at your organization?
a. Fewer than 100
b. 1001-2000
c. 2001-5000
d. 5001-10,000
3. Has your organization suffered from any IoT security and privacy incidents, which affect
your financial organization?
a. Yes
b. Do not know
c. Do not know and do not suspect
d. No, we do not have
4. Does decrease of IoT security incidents affect the bank organization?
a. Significant affect

17
RESEARCH PROPOSAL
b. Slightly affect
c. No change
5. What types of attacks were involved?
a. Advanced attack
b. Denial of service attack
c. Web application attack
d. Targeted attack of financial processing
6. What are the controls do you feel are effective to protect against data threats and frauds?
a. Monitoring of email security
b. Awareness of the employee training and proper testing
c. Monitoring of network and visibility
d. Administrative control
7. What are the outcomes of the incidents?
a. Deployment of new technologies not budgeted
b. Loss of the customers
c. Movement towards cloud security controls
d. Damage of brand reputation
RESEARCH PROPOSAL
b. Slightly affect
c. No change
5. What types of attacks were involved?
a. Advanced attack
b. Denial of service attack
c. Web application attack
d. Targeted attack of financial processing
6. What are the controls do you feel are effective to protect against data threats and frauds?
a. Monitoring of email security
b. Awareness of the employee training and proper testing
c. Monitoring of network and visibility
d. Administrative control
7. What are the outcomes of the incidents?
a. Deployment of new technologies not budgeted
b. Loss of the customers
c. Movement towards cloud security controls
d. Damage of brand reputation
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





