ITNET202A Enterprise Security Report: Analyzing the Stuxnet Worm
VerifiedAdded on 2023/06/04
|16
|3876
|328
Report
AI Summary
This report provides a comprehensive analysis of the Stuxnet worm, a sophisticated cyber weapon targeting programmable logic controllers (PLCs). It explores Stuxnet's functionalities, including access control, identity verification, crypto security, and network security. The report delves into the worm's operational mechanisms, such as identifying and exploiting vulnerabilities in Siemens code to disrupt industrial processes, specifically focusing on the Iranian nuclear research program. Furthermore, it presents a qualitative risk analysis, addressing potential threats such as strong opposition from various nations, environmental risks, and the risk of military attacks. The report also examines preventative measures based on enterprise architecture principles and discusses relevant articles from the UN charter. The report concludes with a discussion on the significance of cryptography, network security, and the importance of risk assessment to secure systems against cyber threats.

STUXNET WORM 1
STUXNET COMPUTER MALWARE
By
Author’s Name
Class
Professor
Institution
City, State
Date of submission
STUXNET COMPUTER MALWARE
By
Author’s Name
Class
Professor
Institution
City, State
Date of submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STUXNET WORM 2
Table of Contents
What Stuxnet does...........................................................................................................................3
Executive summary.........................................................................................................................3
Access control..............................................................................................................................3
Introduction......................................................................................................................................3
Identity.........................................................................................................................................3
Crypto security and network security..........................................................................................4
Qualitative risk analysis and risks of the programme......................................................................5
Strong opposition.........................................................................................................................5
Environmental risk.......................................................................................................................5
Risk of a military attack...............................................................................................................5
Preventing Stuxnet attack................................................................................................................6
Article 2(4) and article 51 of UN charter.........................................................................................7
Security..........................................................................................................................................10
Software Development..................................................................................................................12
Conclusion.....................................................................................................................................13
References......................................................................................................................................14
Table of Contents
What Stuxnet does...........................................................................................................................3
Executive summary.........................................................................................................................3
Access control..............................................................................................................................3
Introduction......................................................................................................................................3
Identity.........................................................................................................................................3
Crypto security and network security..........................................................................................4
Qualitative risk analysis and risks of the programme......................................................................5
Strong opposition.........................................................................................................................5
Environmental risk.......................................................................................................................5
Risk of a military attack...............................................................................................................5
Preventing Stuxnet attack................................................................................................................6
Article 2(4) and article 51 of UN charter.........................................................................................7
Security..........................................................................................................................................10
Software Development..................................................................................................................12
Conclusion.....................................................................................................................................13
References......................................................................................................................................14

STUXNET WORM 3
What Stuxnet does
Executive summary
Access control
Stuxnet was designed with the aim of controlling and checking whether a specified
computer is enabled to certified connections that are distinct of logic controllers that are
programmable activities. The programmable logic controllers involve the interaction of
computers and the controlling of the machinery of industries like those of centrifuges of uranium
(Chen and Abu-Nimeh, 2011: 91). Upon infecting a computer, Stuxnet worm gains controls of
the program which in turn results into the revolving of the centrifuges quickly and for more
extended periods resulting into the damage and destroying of equipment that are delicate. The
PLCs notify the computer that is used for controlling whether everything is working as planned
and makes it hard for the detection or diagnosis of whatever has gone wrong.
Introduction
Identity
Stuxnet worm has numerous routines of identifying the specific model of PLC. The
checking of the model is significant as the instructions of machine level keep on varying on
different devices of PLC (Farwell and Rohozinski, 2011: 24). Upon the identification and
infection of the device that is targeted, Stuxnet worm takes over and can intercept data that is
flowing to the inside and outside of the PLC. On top controlling, Stuxnet can also interfere with
that particular data in any way.
What Stuxnet does
Executive summary
Access control
Stuxnet was designed with the aim of controlling and checking whether a specified
computer is enabled to certified connections that are distinct of logic controllers that are
programmable activities. The programmable logic controllers involve the interaction of
computers and the controlling of the machinery of industries like those of centrifuges of uranium
(Chen and Abu-Nimeh, 2011: 91). Upon infecting a computer, Stuxnet worm gains controls of
the program which in turn results into the revolving of the centrifuges quickly and for more
extended periods resulting into the damage and destroying of equipment that are delicate. The
PLCs notify the computer that is used for controlling whether everything is working as planned
and makes it hard for the detection or diagnosis of whatever has gone wrong.
Introduction
Identity
Stuxnet worm has numerous routines of identifying the specific model of PLC. The
checking of the model is significant as the instructions of machine level keep on varying on
different devices of PLC (Farwell and Rohozinski, 2011: 24). Upon the identification and
infection of the device that is targeted, Stuxnet worm takes over and can intercept data that is
flowing to the inside and outside of the PLC. On top controlling, Stuxnet can also interfere with
that particular data in any way.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STUXNET WORM 4
Crypto security and network security
When Stuxnet has made the identification of the target, it institutes a change to the to the
Siemens code that is referred to as organizational block 35. This component of the Siemens
complements the purpose of monitoring the operations of the factories that are critical for
instance activities that need to respond in a shortest time possible such as 100 milliseconds
(Chen and Abu-Nimeh, 2011: 92). Stuxnet operates without being detected on windows. In the
system of SCADA, the windows machine does communication with PLCs through a program
that is referred to as PS7.
Figure showing installed RPC server with the latest Stuxnet version
Essentially, there is a translation of user command that is useful for the PLCs through the
use of library sets. One of the libraries containing translations that are used to read and write
processes that are new for PLC is targeted by Stuxnet (Farwell and Rohozinski, 2011: 27). It
takes advantage of exploiting the database, renaming and replacing the library that was original
Crypto security and network security
When Stuxnet has made the identification of the target, it institutes a change to the to the
Siemens code that is referred to as organizational block 35. This component of the Siemens
complements the purpose of monitoring the operations of the factories that are critical for
instance activities that need to respond in a shortest time possible such as 100 milliseconds
(Chen and Abu-Nimeh, 2011: 92). Stuxnet operates without being detected on windows. In the
system of SCADA, the windows machine does communication with PLCs through a program
that is referred to as PS7.
Figure showing installed RPC server with the latest Stuxnet version
Essentially, there is a translation of user command that is useful for the PLCs through the
use of library sets. One of the libraries containing translations that are used to read and write
processes that are new for PLC is targeted by Stuxnet (Farwell and Rohozinski, 2011: 27). It
takes advantage of exploiting the database, renaming and replacing the library that was original
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STUXNET WORM 5
with a new version that has been modified (Leau, 2017:162-167). The new commands that are
modified include those that are used to read and write the codes of the PLC. This results in the
interception and changing of the controls to suit the demands of Stuxnet.
Qualitative risk analysis and risks of the programme
Strong opposition
Iran is poised to receive strong opposition from various countries across the world
especially from the United States and its allies. This is because of the fear that Iran might help
Palestine in unleashing the nuclear weapons on Israel (Jewell, 2011:1043). The nuclear plant of
Iran may also pose a great threat to global security, and this is according to the United Nations
Security Council. This implies that the opposition is going to be stronger. This is because of Iran
not adhering to the Security Council laws and regulations. Therefore, the probability risk of Iran
facing war threats is high. This can be witnessed by the threats being issued mainly by the United
States and its allies.
Environmental risk
The Iranian nuclear research asset poses a considerable ecological risk to the people of
Iran. This is as a result of the process that is involved in the plant (Jewell, 2011:1045). The
chemicals that are used are highly reactive and highly explosive. The chemicals are also highly
toxic. If they are not handled properly and are as a result released to the environment, they are
poised to cause a great risk to the people of Iran. Inhaling of the toxic gases can result in the
death of humans as well as animals. The gases can cause a great risk to the environment by
polluting it, and this may result in the threatening of existing life.
with a new version that has been modified (Leau, 2017:162-167). The new commands that are
modified include those that are used to read and write the codes of the PLC. This results in the
interception and changing of the controls to suit the demands of Stuxnet.
Qualitative risk analysis and risks of the programme
Strong opposition
Iran is poised to receive strong opposition from various countries across the world
especially from the United States and its allies. This is because of the fear that Iran might help
Palestine in unleashing the nuclear weapons on Israel (Jewell, 2011:1043). The nuclear plant of
Iran may also pose a great threat to global security, and this is according to the United Nations
Security Council. This implies that the opposition is going to be stronger. This is because of Iran
not adhering to the Security Council laws and regulations. Therefore, the probability risk of Iran
facing war threats is high. This can be witnessed by the threats being issued mainly by the United
States and its allies.
Environmental risk
The Iranian nuclear research asset poses a considerable ecological risk to the people of
Iran. This is as a result of the process that is involved in the plant (Jewell, 2011:1045). The
chemicals that are used are highly reactive and highly explosive. The chemicals are also highly
toxic. If they are not handled properly and are as a result released to the environment, they are
poised to cause a great risk to the people of Iran. Inhaling of the toxic gases can result in the
death of humans as well as animals. The gases can cause a great risk to the environment by
polluting it, and this may result in the threatening of existing life.

STUXNET WORM 6
Risk of a military attack
The nuclear programme puts Iran in the risk of being attacked by the opposing nations.
This is especially America and its allies such as some of the European countries (Jewell,
2011:1051). This is evident going by the threats that are being given by America. America
believes that the solution to the Iran nuclear programme and attacking it, destroying the plants
and overthrowing the government. This will ensure that the nuclear power plants are eradicated,
and a new regime or government is instituted that is not pro-nuclear weapons. The probability of
the risk of an attack being unleashed upon Iran by the U.S and its allies is very high.
Preventing Stuxnet attack
The most appropriate way of Iran protecting itself is through the framework of enterprise
architecture. This framework contains principles of security, artifacts that are related to security
and metrics of security (Chen and Abu-Nimeh, 2011: 92). This gives room to the architects of
security to evaluate the security of an enterprise easily. This will allow them to improve their
principles of security easily. Stuxnet attacks and infects a computer causing the alterations by
gaining control and changing the codes.
Risk of a military attack
The nuclear programme puts Iran in the risk of being attacked by the opposing nations.
This is especially America and its allies such as some of the European countries (Jewell,
2011:1051). This is evident going by the threats that are being given by America. America
believes that the solution to the Iran nuclear programme and attacking it, destroying the plants
and overthrowing the government. This will ensure that the nuclear power plants are eradicated,
and a new regime or government is instituted that is not pro-nuclear weapons. The probability of
the risk of an attack being unleashed upon Iran by the U.S and its allies is very high.
Preventing Stuxnet attack
The most appropriate way of Iran protecting itself is through the framework of enterprise
architecture. This framework contains principles of security, artifacts that are related to security
and metrics of security (Chen and Abu-Nimeh, 2011: 92). This gives room to the architects of
security to evaluate the security of an enterprise easily. This will allow them to improve their
principles of security easily. Stuxnet attacks and infects a computer causing the alterations by
gaining control and changing the codes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
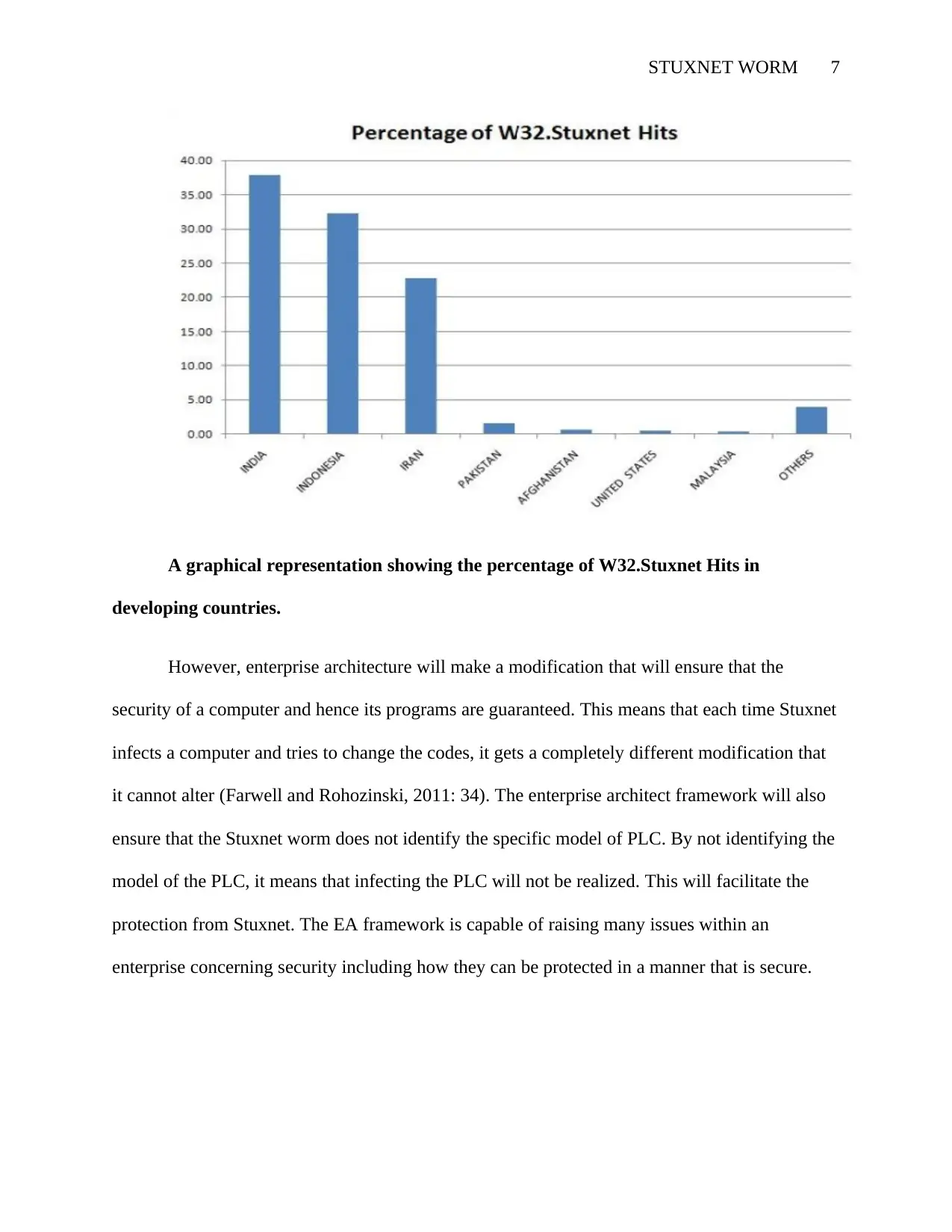
STUXNET WORM 7
A graphical representation showing the percentage of W32.Stuxnet Hits in
developing countries.
However, enterprise architecture will make a modification that will ensure that the
security of a computer and hence its programs are guaranteed. This means that each time Stuxnet
infects a computer and tries to change the codes, it gets a completely different modification that
it cannot alter (Farwell and Rohozinski, 2011: 34). The enterprise architect framework will also
ensure that the Stuxnet worm does not identify the specific model of PLC. By not identifying the
model of the PLC, it means that infecting the PLC will not be realized. This will facilitate the
protection from Stuxnet. The EA framework is capable of raising many issues within an
enterprise concerning security including how they can be protected in a manner that is secure.
A graphical representation showing the percentage of W32.Stuxnet Hits in
developing countries.
However, enterprise architecture will make a modification that will ensure that the
security of a computer and hence its programs are guaranteed. This means that each time Stuxnet
infects a computer and tries to change the codes, it gets a completely different modification that
it cannot alter (Farwell and Rohozinski, 2011: 34). The enterprise architect framework will also
ensure that the Stuxnet worm does not identify the specific model of PLC. By not identifying the
model of the PLC, it means that infecting the PLC will not be realized. This will facilitate the
protection from Stuxnet. The EA framework is capable of raising many issues within an
enterprise concerning security including how they can be protected in a manner that is secure.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STUXNET WORM 8
Article 2(4) and article 51 of UN charter
These articles spell out how a country can defend itself upon an attack. Article 2(4) spells
out that a nation cannot interfere with another country that is sovereign for instance by attacking
it. This means that a nation is protected from any attack by another government (McDonald and
Patrick, 2010: 65). For instance, according to this article, U.S cannot proceed to attack Iran
unless the UN Security Council has authorized it. This implies that Iran is fully protected from
any attack by the laws of the UN Security Council.
Article 51 of the UN charter spells out that a nation is supposed to use self-defense only
after it has been attacked and after the UN Security Council has allowed it to. The article is
vague in allowing the states in asserting their right to defend themselves while reducing the
probability of causing a conflict (McDonald and Patrick, 2010: 74). One side cannot determine if
it has been attacked offensively. The determination is left upon the UN Security Council.
However, the attack is not specified by the article as to whether it is military or cyberattacks. In
this case, Iran was attacked by the U.S in conjunction with Israel, but it cannot attack back to
defend itself without approval from the Security Council.
The application of network security has gone through tremendous changes recently. In
the earlier days, people used physical means to protect information. However, the advent of
computer usage in the various fields has resulted in need of creating software files that are to be
utilized in the protection of data and relevant information stored in the computers (Morrow B.,
2012: 5-8). The tool designed for protecting data and illegal users is what is termed as computer
security.
The introduction and the revolution of communication have led to the formulation of
distribution systems that require the carrying of information from the terminal user to the other
Article 2(4) and article 51 of UN charter
These articles spell out how a country can defend itself upon an attack. Article 2(4) spells
out that a nation cannot interfere with another country that is sovereign for instance by attacking
it. This means that a nation is protected from any attack by another government (McDonald and
Patrick, 2010: 65). For instance, according to this article, U.S cannot proceed to attack Iran
unless the UN Security Council has authorized it. This implies that Iran is fully protected from
any attack by the laws of the UN Security Council.
Article 51 of the UN charter spells out that a nation is supposed to use self-defense only
after it has been attacked and after the UN Security Council has allowed it to. The article is
vague in allowing the states in asserting their right to defend themselves while reducing the
probability of causing a conflict (McDonald and Patrick, 2010: 74). One side cannot determine if
it has been attacked offensively. The determination is left upon the UN Security Council.
However, the attack is not specified by the article as to whether it is military or cyberattacks. In
this case, Iran was attacked by the U.S in conjunction with Israel, but it cannot attack back to
defend itself without approval from the Security Council.
The application of network security has gone through tremendous changes recently. In
the earlier days, people used physical means to protect information. However, the advent of
computer usage in the various fields has resulted in need of creating software files that are to be
utilized in the protection of data and relevant information stored in the computers (Morrow B.,
2012: 5-8). The tool designed for protecting data and illegal users is what is termed as computer
security.
The introduction and the revolution of communication have led to the formulation of
distribution systems that require the carrying of information from the terminal user to the other

STUXNET WORM 9
sets of computers. Network security, therefore, is fundamental in protecting the data during the
process of transmission (Moore T. C., 2009: 3-20). The various mechanisms established to meet
such specification for instance authentication or confidentiality proves to be quite difficult.
Therefore an individual must consider developing specific measures when incorporating the
security mechanisms. These mechanisms include not only algorithms and protocols but the
people involved must have secret information hence extends doubts on the creation of the
dissemination and protection of this information (Perlman, 2016). Therefore becoming important
to create a model where the security services may be viewed.
Conversely, for the management of an organization to understand the security needs,
there should be a systematic way for the system to be at a sufficient level. The approach that may
be used is to consider some aspects of information security that is the security service,
mechanism and security attacks (Morrow, 2012: 5-8). The security attack aims to identify the
ways through which intruders may get unauthorized data using several mechanisms in providing
such services.
The network security involves the practices and policies that are adopted to monitor the
misuse, unauthorized access or denial of the computer networks. It incorporates the authorization
on the access to data, and the users may be assigned password for authenticating hence allowing
them to access the information at their disposal. The security of information covers both the
private and public networks which are used in conducting transactions between the various
agencies, business enterprises, and individuals (Brownlie, 2012: 157). The security management
system for specific networks depends on the situation at hand. For instance, the security of small
offices requires primary systems while for the large organization it involves advanced software
and high maintenance to prevent malicious attacks that are hacking or spamming.
sets of computers. Network security, therefore, is fundamental in protecting the data during the
process of transmission (Moore T. C., 2009: 3-20). The various mechanisms established to meet
such specification for instance authentication or confidentiality proves to be quite difficult.
Therefore an individual must consider developing specific measures when incorporating the
security mechanisms. These mechanisms include not only algorithms and protocols but the
people involved must have secret information hence extends doubts on the creation of the
dissemination and protection of this information (Perlman, 2016). Therefore becoming important
to create a model where the security services may be viewed.
Conversely, for the management of an organization to understand the security needs,
there should be a systematic way for the system to be at a sufficient level. The approach that may
be used is to consider some aspects of information security that is the security service,
mechanism and security attacks (Morrow, 2012: 5-8). The security attack aims to identify the
ways through which intruders may get unauthorized data using several mechanisms in providing
such services.
The network security involves the practices and policies that are adopted to monitor the
misuse, unauthorized access or denial of the computer networks. It incorporates the authorization
on the access to data, and the users may be assigned password for authenticating hence allowing
them to access the information at their disposal. The security of information covers both the
private and public networks which are used in conducting transactions between the various
agencies, business enterprises, and individuals (Brownlie, 2012: 157). The security management
system for specific networks depends on the situation at hand. For instance, the security of small
offices requires primary systems while for the large organization it involves advanced software
and high maintenance to prevent malicious attacks that are hacking or spamming.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STUXNET WORM 10
With the increase of cyber-crimes worldwide, businesses have to invest in the
improvement of their network security to protect their data from unauthorized access. This global
problem needs to be acted upon to close the loopholes that exist in their networks. The paper will
discuss innovative and most recent products/measures that can be adopted by businesses. This
paper will focus on a single company for specificity (Smith, 2016: 224-234). Due to the
changing trends in the business world, many enterprises rely heavily on networking and security
to offer their services. Fast, efficient, and secure networks improve on work efficiency and
overall productivity.
Enterprises such as banks, Sacco's, manufacturing and production companies and other
firms cannot operate without a good networking system. In the past few years, the range of
threats that the computer network face by sophisticated intruders and attackers has increased
considerably across all societal boundaries and has enforced difficult economic burden on
businesses, well-being and different organizations (Moore, 2009). Therefore, taking risk
assessment is a fundamental issue in the computer network. This paper discusses the risk that
may occur in the networking field, risk assessment, mitigation measures, and strategic control.
Cryptography is highly essential in this technological era. The technology significance
can be seen by many since it helps with the protection of the information which travels over the
internet. Cryptology has managed to offer security since this technological era has been
vulnerable to hackers, viruses and electronic fraud (Kraemer-Mbula, 2013). In my opinion,
cryptography will involve the use of encryption which will offer protection to the content found
on the internet. The material will include emails, telephone calls which uses the internet as the
main medium and any transaction which may occur on the internet.
With the increase of cyber-crimes worldwide, businesses have to invest in the
improvement of their network security to protect their data from unauthorized access. This global
problem needs to be acted upon to close the loopholes that exist in their networks. The paper will
discuss innovative and most recent products/measures that can be adopted by businesses. This
paper will focus on a single company for specificity (Smith, 2016: 224-234). Due to the
changing trends in the business world, many enterprises rely heavily on networking and security
to offer their services. Fast, efficient, and secure networks improve on work efficiency and
overall productivity.
Enterprises such as banks, Sacco's, manufacturing and production companies and other
firms cannot operate without a good networking system. In the past few years, the range of
threats that the computer network face by sophisticated intruders and attackers has increased
considerably across all societal boundaries and has enforced difficult economic burden on
businesses, well-being and different organizations (Moore, 2009). Therefore, taking risk
assessment is a fundamental issue in the computer network. This paper discusses the risk that
may occur in the networking field, risk assessment, mitigation measures, and strategic control.
Cryptography is highly essential in this technological era. The technology significance
can be seen by many since it helps with the protection of the information which travels over the
internet. Cryptology has managed to offer security since this technological era has been
vulnerable to hackers, viruses and electronic fraud (Kraemer-Mbula, 2013). In my opinion,
cryptography will involve the use of encryption which will offer protection to the content found
on the internet. The material will include emails, telephone calls which uses the internet as the
main medium and any transaction which may occur on the internet.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STUXNET WORM 11
Security
The Web 2.0 technology allows better collaboration and interactivity while accessing the
web. Web 2.0 ushered in a new way of online socializing regarding networking and making
friends. These benefits made it easier for people to become victims of malware attacks (Web 2.
0, 2012). Since more people preferred to use Web 2.0 then because of social networking sites,
RSS feeds and blogs, security was bound to become an issue of concern (Shih, 2011: 27). Social
networking websites are normally faced by two main threats broadly categorized as technical and
social. Technically, while Web 2.0 allows people to post content, it also allows malicious users
to post malware. Socially, the security threats primary lie in the information shared by people on
social media (Stallings, 2006). The availability of this information on social networking sites
makes people more vulnerable to cyber-attacks such as phishing.
Considering the popularity of social networking sites, Web 2.0 allows malicious users to
access personal information that could not have been obtained previously. Most individuals who
are active on social networking sites tend to publish information about their lives including jobs,
friends, hobbies and even work. Notably, this information is essential in identifying burglars
(Kamel Boulos, 2013:2-23). Users of Web 2.0 do not realize the significance of information
posted or the people accessing the data. Consequently, fraudsters can manipulate this information
to steal the identity of a person and even go to the extent of opening accounts in their name
(Kamel Boulos, 2007). Although Web 2.0 introduced higher levels of interactivity for users, it
also resulted in increased vulnerabilities due to data leaks and other inherent security threats.
These security threats threaten the confidentiality of data, especially in organizations.
Technically, Web 2.0 platforms are prone to cyber-attacks because they allow higher
levels of interaction between the user and the browsers. The majority of Web 2.0 applications do
Security
The Web 2.0 technology allows better collaboration and interactivity while accessing the
web. Web 2.0 ushered in a new way of online socializing regarding networking and making
friends. These benefits made it easier for people to become victims of malware attacks (Web 2.
0, 2012). Since more people preferred to use Web 2.0 then because of social networking sites,
RSS feeds and blogs, security was bound to become an issue of concern (Shih, 2011: 27). Social
networking websites are normally faced by two main threats broadly categorized as technical and
social. Technically, while Web 2.0 allows people to post content, it also allows malicious users
to post malware. Socially, the security threats primary lie in the information shared by people on
social media (Stallings, 2006). The availability of this information on social networking sites
makes people more vulnerable to cyber-attacks such as phishing.
Considering the popularity of social networking sites, Web 2.0 allows malicious users to
access personal information that could not have been obtained previously. Most individuals who
are active on social networking sites tend to publish information about their lives including jobs,
friends, hobbies and even work. Notably, this information is essential in identifying burglars
(Kamel Boulos, 2013:2-23). Users of Web 2.0 do not realize the significance of information
posted or the people accessing the data. Consequently, fraudsters can manipulate this information
to steal the identity of a person and even go to the extent of opening accounts in their name
(Kamel Boulos, 2007). Although Web 2.0 introduced higher levels of interactivity for users, it
also resulted in increased vulnerabilities due to data leaks and other inherent security threats.
These security threats threaten the confidentiality of data, especially in organizations.
Technically, Web 2.0 platforms are prone to cyber-attacks because they allow higher
levels of interaction between the user and the browsers. The majority of Web 2.0 applications do

STUXNET WORM 12
not have sufficient authentication controls such as brute-force controls allowing hackers to easily
exploit them. Also, the programmatic interface implemented in Web 2.0 applications allows
malicious users to automate attacks easily (Wasserman, 2010: 397-400). The majority of
business that operates on the internet does not block users from accessing Web 2.0 hence
creating additional security risks because malicious code might be embedded in these sites.
To understand the security risk presented by Web 2.0, consider the Facebook situation in
2011 where users were click-jacked into announcing the ‘Twilight’ link. During the same period,
twitter as infected by a rapidly spreading viral worm who objective was to scam people into
viewing an advertisement. In 2010, unsuspecting LinkedIn users were infected with malware and
malicious users attempted to access personal information. On YouTube, booby-trapped links
have been set up in some sections because it allows users to add and modify the content of the
site.
Software Development
The concept of software security attempts to explain architects and developers have
adopted a systematic way of building more secure software solutions. Knowledge of secure
software development practices provides a contextual understanding of security mechanisms
such as hashing, password, load balancing which can help in securing applications from security
risks and threats (Leau, 2012). Secure web development requires applications to be compliant to
privacy, governance, and regulations which basically the first step of securing applications
against known and unknown threats.
During the design and architectural stage of software development, it is important to
ensure that the application takes into account security principles. In application development, the
not have sufficient authentication controls such as brute-force controls allowing hackers to easily
exploit them. Also, the programmatic interface implemented in Web 2.0 applications allows
malicious users to automate attacks easily (Wasserman, 2010: 397-400). The majority of
business that operates on the internet does not block users from accessing Web 2.0 hence
creating additional security risks because malicious code might be embedded in these sites.
To understand the security risk presented by Web 2.0, consider the Facebook situation in
2011 where users were click-jacked into announcing the ‘Twilight’ link. During the same period,
twitter as infected by a rapidly spreading viral worm who objective was to scam people into
viewing an advertisement. In 2010, unsuspecting LinkedIn users were infected with malware and
malicious users attempted to access personal information. On YouTube, booby-trapped links
have been set up in some sections because it allows users to add and modify the content of the
site.
Software Development
The concept of software security attempts to explain architects and developers have
adopted a systematic way of building more secure software solutions. Knowledge of secure
software development practices provides a contextual understanding of security mechanisms
such as hashing, password, load balancing which can help in securing applications from security
risks and threats (Leau, 2012). Secure web development requires applications to be compliant to
privacy, governance, and regulations which basically the first step of securing applications
against known and unknown threats.
During the design and architectural stage of software development, it is important to
ensure that the application takes into account security principles. In application development, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


