System Analysis and Design: HND Computing & Systems Development Report
VerifiedAdded on 2023/06/13
|24
|5055
|304
Report
AI Summary
This document presents a system analysis and design report, covering various aspects of the system development lifecycle (SDLC). It evaluates different SDLC models like Waterfall, Iterative, Spiral, Prototype, and Agile, highlighting their merits and demerits. The report emphasizes the importance of a procedural lifecycle in system investigation and details the components of a feasibility report, including economic, technical, operational, time, legal, and social feasibility. Furthermore, it investigates a system to meet business requirements, utilizing tools and techniques such as ERDs and Data Flow Diagrams. The report also addresses specific requirements related to external, software, hardware, and user interfaces, along with functional and non-functional aspects, concluding with verification and validation processes. This comprehensive analysis aims to provide a structured approach to system development and ensure alignment with business goals.

System Analysis and Design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Task 1................................................................................................................................................2
1.1 System lifecycle model evaluation.....................................................................................2
1.2 Importance of procedural/staged lifecycle in a system investigation:......................7
2. Task 2................................................................................................................................................8
2.1 Feasibility report component:..............................................................................................8
2.2 Different feasibility criteria impact on a systems investigation..................................9
3. Task 3..............................................................................................................................................11
3.1 Investigating the system, for meeting the business....................................................11
3.1.1 Introduction....................................................................................................................11
3.1.2 Definitions and Abbreviations...................................................................................12
3.1.3 Overview.........................................................................................................................12
3.1.4 Overall Description.......................................................................................................12
3.1.5 Product capabilities......................................................................................................13
3.2 Investigating the system by using various tools and techniques............................14
3.2.1 ERD...................................................................................................................................14
3.2.2 Context Level DFD........................................................................................................14
3.2.3 Data flow Diagram.........................................................................................................15
3.3 Investigating the Specific Requirements........................................................................19
3.3.1 External Interfaces........................................................................................................19
3.3.2 Software Interfaces Requirement..............................................................................20
3.3.3 Hardware Interfaces Requirement............................................................................20
3.3.4 User Interfaces Requirement.....................................................................................20
3.3.5 Functional Requirements............................................................................................20
3.3.6 Non-functional Requirements....................................................................................21
3.4 Verification and Validation.................................................................................................21
1
1. Task 1................................................................................................................................................2
1.1 System lifecycle model evaluation.....................................................................................2
1.2 Importance of procedural/staged lifecycle in a system investigation:......................7
2. Task 2................................................................................................................................................8
2.1 Feasibility report component:..............................................................................................8
2.2 Different feasibility criteria impact on a systems investigation..................................9
3. Task 3..............................................................................................................................................11
3.1 Investigating the system, for meeting the business....................................................11
3.1.1 Introduction....................................................................................................................11
3.1.2 Definitions and Abbreviations...................................................................................12
3.1.3 Overview.........................................................................................................................12
3.1.4 Overall Description.......................................................................................................12
3.1.5 Product capabilities......................................................................................................13
3.2 Investigating the system by using various tools and techniques............................14
3.2.1 ERD...................................................................................................................................14
3.2.2 Context Level DFD........................................................................................................14
3.2.3 Data flow Diagram.........................................................................................................15
3.3 Investigating the Specific Requirements........................................................................19
3.3.1 External Interfaces........................................................................................................19
3.3.2 Software Interfaces Requirement..............................................................................20
3.3.3 Hardware Interfaces Requirement............................................................................20
3.3.4 User Interfaces Requirement.....................................................................................20
3.3.5 Functional Requirements............................................................................................20
3.3.6 Non-functional Requirements....................................................................................21
3.4 Verification and Validation.................................................................................................21
1
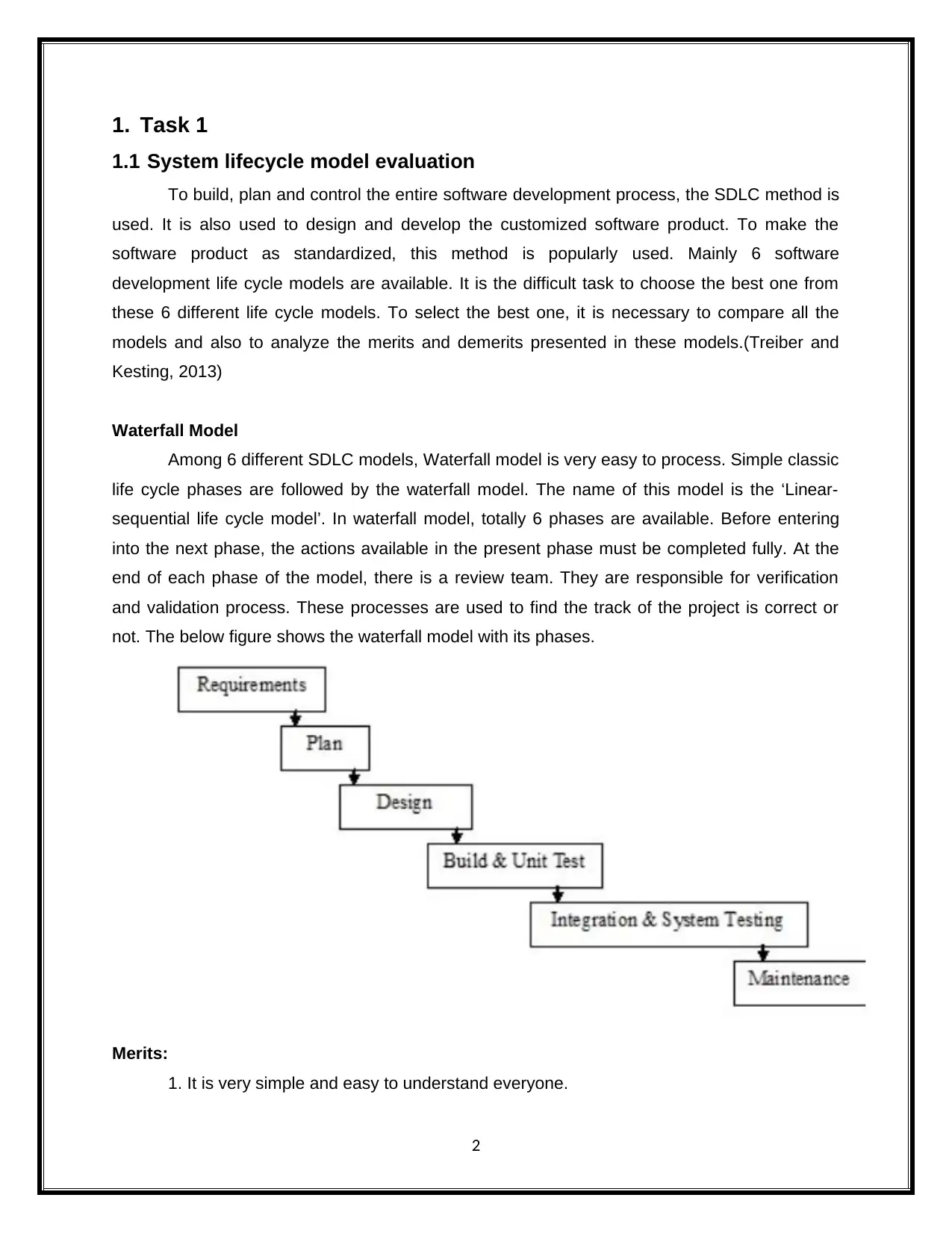
1. Task 1
1.1 System lifecycle model evaluation
To build, plan and control the entire software development process, the SDLC method is
used. It is also used to design and develop the customized software product. To make the
software product as standardized, this method is popularly used. Mainly 6 software
development life cycle models are available. It is the difficult task to choose the best one from
these 6 different life cycle models. To select the best one, it is necessary to compare all the
models and also to analyze the merits and demerits presented in these models.(Treiber and
Kesting, 2013)
Waterfall Model
Among 6 different SDLC models, Waterfall model is very easy to process. Simple classic
life cycle phases are followed by the waterfall model. The name of this model is the ‘Linear-
sequential life cycle model’. In waterfall model, totally 6 phases are available. Before entering
into the next phase, the actions available in the present phase must be completed fully. At the
end of each phase of the model, there is a review team. They are responsible for verification
and validation process. These processes are used to find the track of the project is correct or
not. The below figure shows the waterfall model with its phases.
Merits:
1. It is very simple and easy to understand everyone.
2
1.1 System lifecycle model evaluation
To build, plan and control the entire software development process, the SDLC method is
used. It is also used to design and develop the customized software product. To make the
software product as standardized, this method is popularly used. Mainly 6 software
development life cycle models are available. It is the difficult task to choose the best one from
these 6 different life cycle models. To select the best one, it is necessary to compare all the
models and also to analyze the merits and demerits presented in these models.(Treiber and
Kesting, 2013)
Waterfall Model
Among 6 different SDLC models, Waterfall model is very easy to process. Simple classic
life cycle phases are followed by the waterfall model. The name of this model is the ‘Linear-
sequential life cycle model’. In waterfall model, totally 6 phases are available. Before entering
into the next phase, the actions available in the present phase must be completed fully. At the
end of each phase of the model, there is a review team. They are responsible for verification
and validation process. These processes are used to find the track of the project is correct or
not. The below figure shows the waterfall model with its phases.
Merits:
1. It is very simple and easy to understand everyone.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
2. Each phases presented in the waterfall model is independent to each other. So the
result of each product is developed separately.
3. Small project with clear requirement, the waterfall model is used for that project.
Demerits:
1. If the phases are integrated with each other, the error or no output will be obtained
because each phase is independent to each other. So risk involved in this model is high.
2. For big project, it is not suitable.
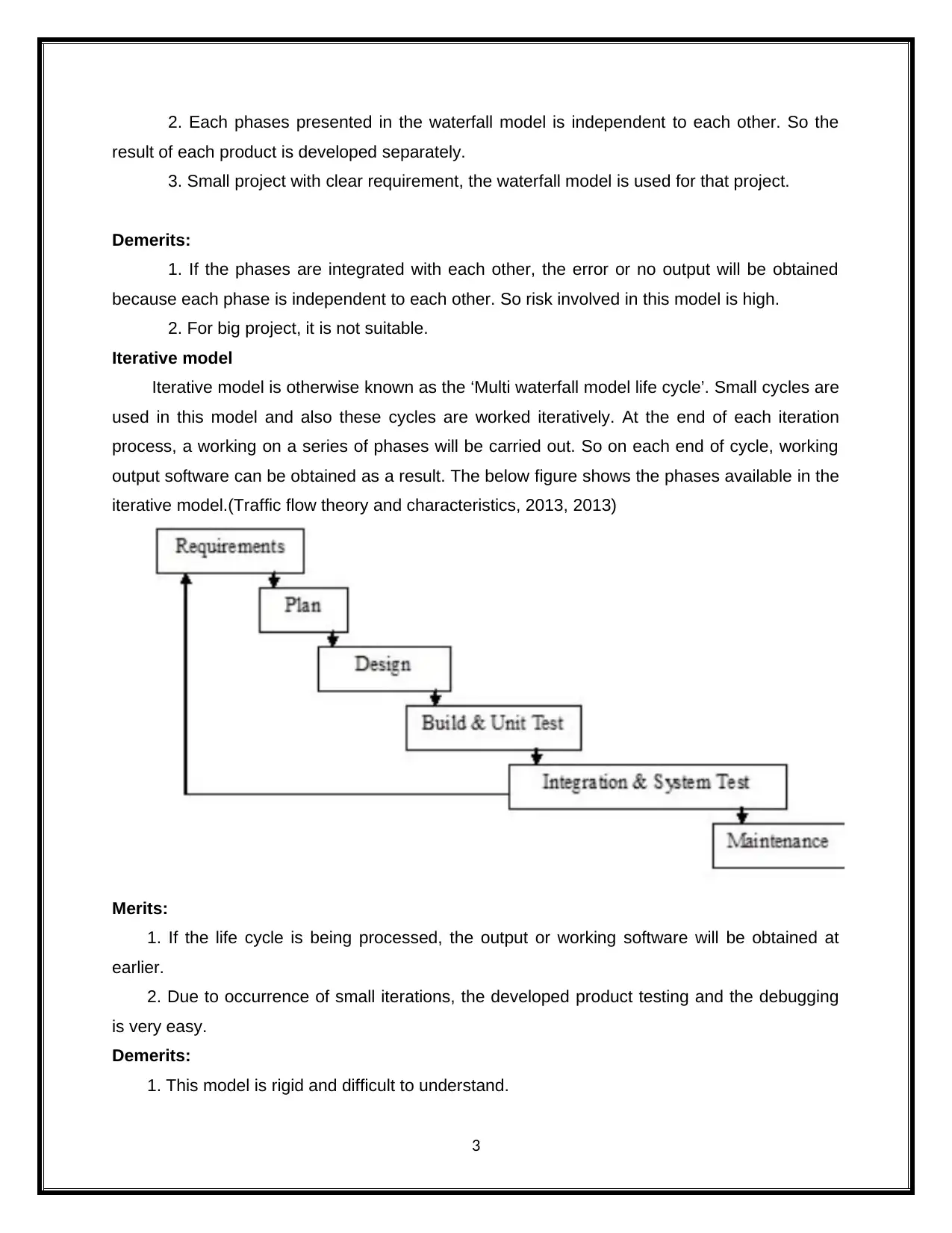
Iterative model
Iterative model is otherwise known as the ‘Multi waterfall model life cycle’. Small cycles are
used in this model and also these cycles are worked iteratively. At the end of each iteration
process, a working on a series of phases will be carried out. So on each end of cycle, working
output software can be obtained as a result. The below figure shows the phases available in the
iterative model.(Traffic flow theory and characteristics, 2013, 2013)
Merits:
1. If the life cycle is being processed, the output or working software will be obtained at
earlier.
2. Due to occurrence of small iterations, the developed product testing and the debugging
is very easy.
Demerits:
1. This model is rigid and difficult to understand.
3
result of each product is developed separately.
3. Small project with clear requirement, the waterfall model is used for that project.
Demerits:
1. If the phases are integrated with each other, the error or no output will be obtained
because each phase is independent to each other. So risk involved in this model is high.
2. For big project, it is not suitable.
Iterative model
Iterative model is otherwise known as the ‘Multi waterfall model life cycle’. Small cycles are
used in this model and also these cycles are worked iteratively. At the end of each iteration
process, a working on a series of phases will be carried out. So on each end of cycle, working
output software can be obtained as a result. The below figure shows the phases available in the
iterative model.(Traffic flow theory and characteristics, 2013, 2013)
Merits:
1. If the life cycle is being processed, the output or working software will be obtained at
earlier.
2. Due to occurrence of small iterations, the developed product testing and the debugging
is very easy.
Demerits:
1. This model is rigid and difficult to understand.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. At the end of each iteration cycle, there is architectural problem. The main reason for this
problem is that the requirements are not collected properly at the starting stage of the
development process.
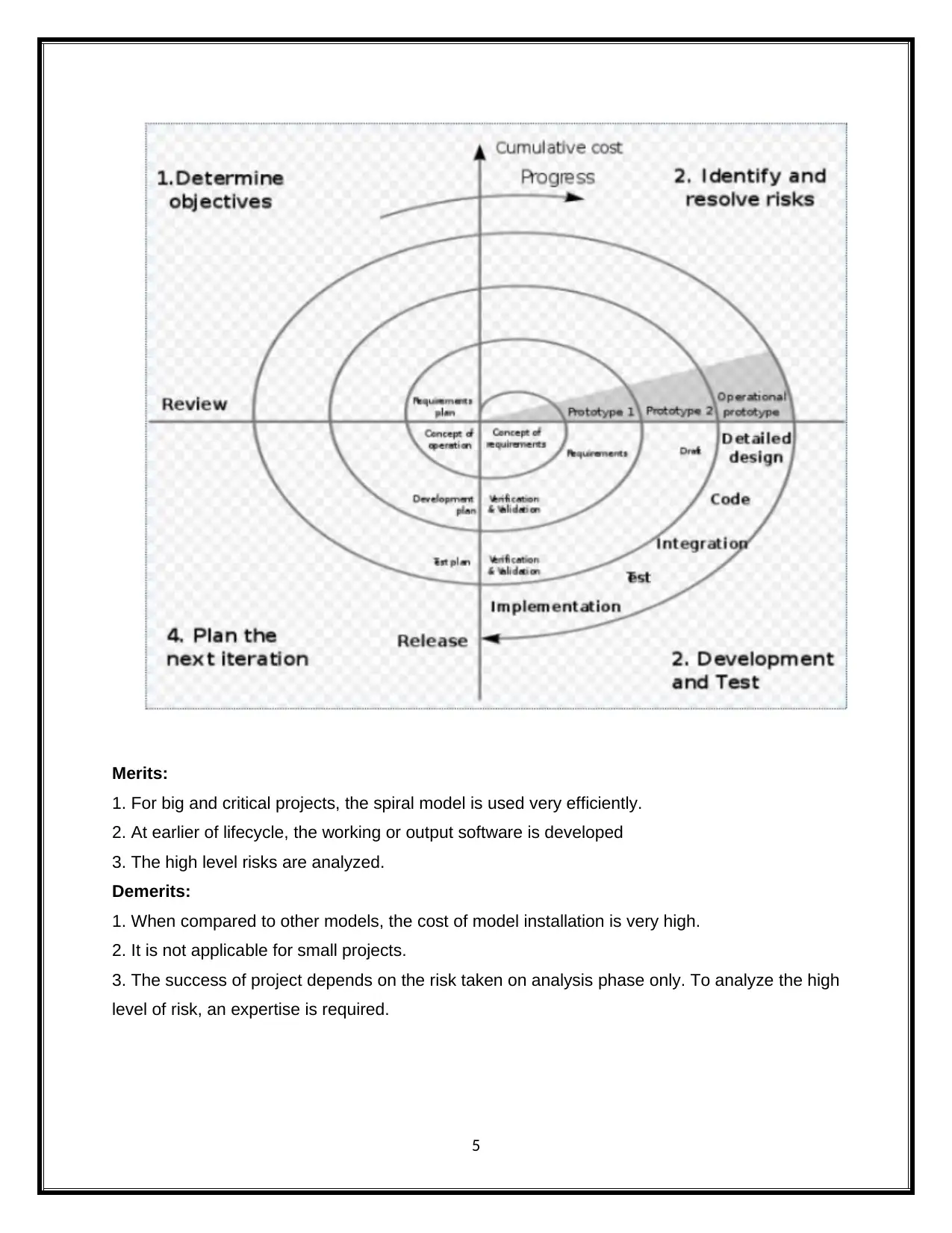
Spiral Model
Spiral model is the simplest model without risk analysis. The spiral model plays the vital
role in SDLC. The following steps are used for spiral model.
This model allows the various type of users to use the software product and the system
requirements are well explained and it is used to identify the system aspects.
Preliminary design is the one of the most important step in the spiral model. This spiral
model is used to make a cost effective strategies to work on a project. The new system is
developed in this phase. The characteristics of the final output are represented as the scaled
down system.
We can easily evaluate the strength, weakness and risk involved in the system.
For new prototype, Functional and non-functional requirements are well defined.
plan and design of newly developing prototype can be started
Testing process will be carried out for developing the project.
4
problem is that the requirements are not collected properly at the starting stage of the
development process.
Spiral Model
Spiral model is the simplest model without risk analysis. The spiral model plays the vital
role in SDLC. The following steps are used for spiral model.
This model allows the various type of users to use the software product and the system
requirements are well explained and it is used to identify the system aspects.
Preliminary design is the one of the most important step in the spiral model. This spiral
model is used to make a cost effective strategies to work on a project. The new system is
developed in this phase. The characteristics of the final output are represented as the scaled
down system.
We can easily evaluate the strength, weakness and risk involved in the system.
For new prototype, Functional and non-functional requirements are well defined.
plan and design of newly developing prototype can be started
Testing process will be carried out for developing the project.
4
Merits:
1. For big and critical projects, the spiral model is used very efficiently.
2. At earlier of lifecycle, the working or output software is developed
3. The high level risks are analyzed.
Demerits:
1. When compared to other models, the cost of model installation is very high.
2. It is not applicable for small projects.
3. The success of project depends on the risk taken on analysis phase only. To analyze the high
level of risk, an expertise is required.
5
1. For big and critical projects, the spiral model is used very efficiently.
2. At earlier of lifecycle, the working or output software is developed
3. The high level risks are analyzed.
Demerits:
1. When compared to other models, the cost of model installation is very high.
2. It is not applicable for small projects.
3. The success of project depends on the risk taken on analysis phase only. To analyze the high
level of risk, an expertise is required.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
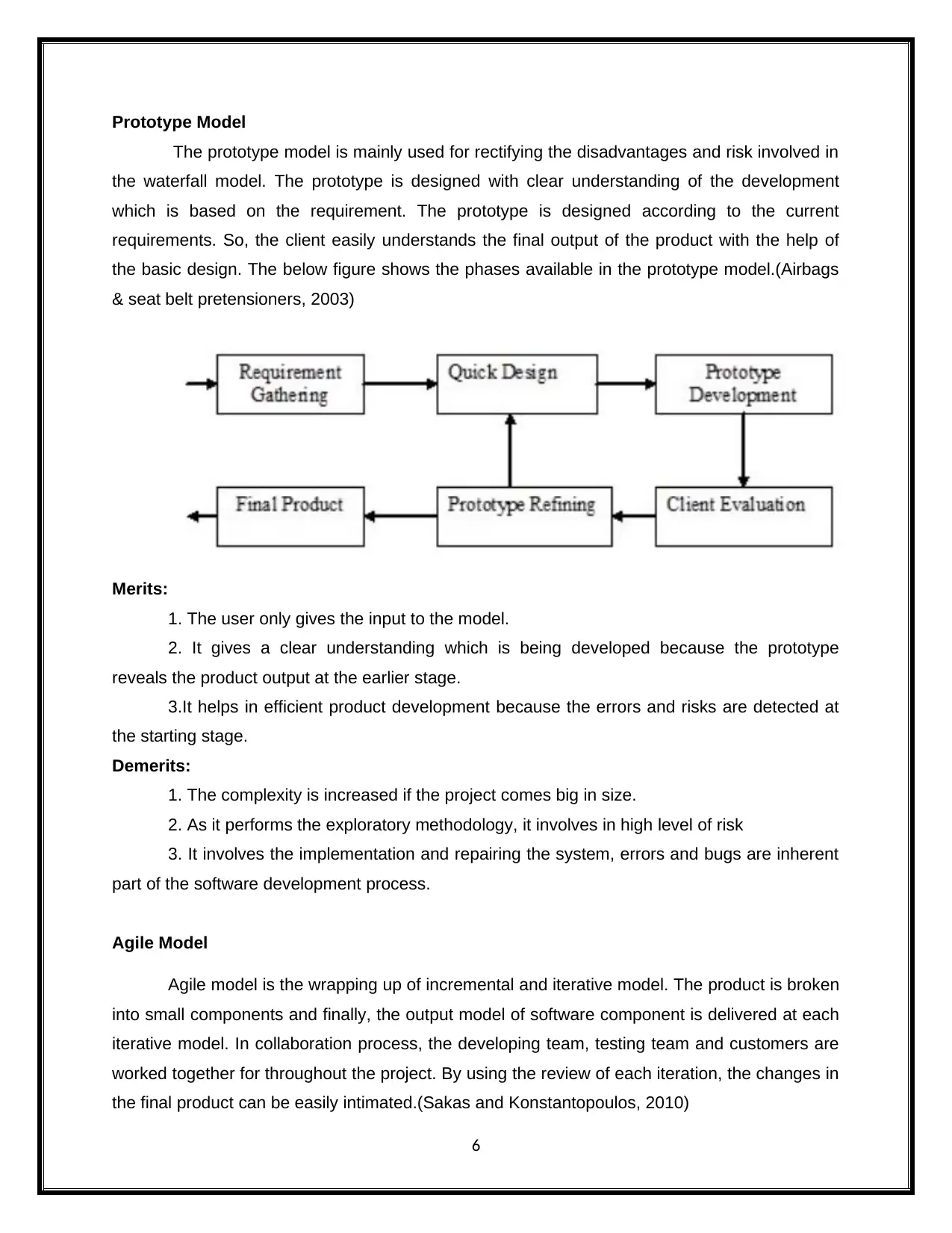
Prototype Model
The prototype model is mainly used for rectifying the disadvantages and risk involved in
the waterfall model. The prototype is designed with clear understanding of the development
which is based on the requirement. The prototype is designed according to the current
requirements. So, the client easily understands the final output of the product with the help of
the basic design. The below figure shows the phases available in the prototype model.(Airbags
& seat belt pretensioners, 2003)
Merits:
1. The user only gives the input to the model.
2. It gives a clear understanding which is being developed because the prototype
reveals the product output at the earlier stage.
3.It helps in efficient product development because the errors and risks are detected at
the starting stage.
Demerits:
1. The complexity is increased if the project comes big in size.
2. As it performs the exploratory methodology, it involves in high level of risk
3. It involves the implementation and repairing the system, errors and bugs are inherent
part of the software development process.
Agile Model
Agile model is the wrapping up of incremental and iterative model. The product is broken
into small components and finally, the output model of software component is delivered at each
iterative model. In collaboration process, the developing team, testing team and customers are
worked together for throughout the project. By using the review of each iteration, the changes in
the final product can be easily intimated.(Sakas and Konstantopoulos, 2010)
6
The prototype model is mainly used for rectifying the disadvantages and risk involved in
the waterfall model. The prototype is designed with clear understanding of the development
which is based on the requirement. The prototype is designed according to the current
requirements. So, the client easily understands the final output of the product with the help of
the basic design. The below figure shows the phases available in the prototype model.(Airbags
& seat belt pretensioners, 2003)
Merits:
1. The user only gives the input to the model.
2. It gives a clear understanding which is being developed because the prototype
reveals the product output at the earlier stage.
3.It helps in efficient product development because the errors and risks are detected at
the starting stage.
Demerits:
1. The complexity is increased if the project comes big in size.
2. As it performs the exploratory methodology, it involves in high level of risk
3. It involves the implementation and repairing the system, errors and bugs are inherent
part of the software development process.
Agile Model
Agile model is the wrapping up of incremental and iterative model. The product is broken
into small components and finally, the output model of software component is delivered at each
iterative model. In collaboration process, the developing team, testing team and customers are
worked together for throughout the project. By using the review of each iteration, the changes in
the final product can be easily intimated.(Sakas and Konstantopoulos, 2010)
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Merits:
The product is delivered very quickly.
When compared to other models, it is very realistic approach for software development.
Demerits:
The final output could not be delivered efficiently when the customer is not clear about
their requirement.
1.2 Importance of procedural/staged lifecycle in a system investigation:
The importance of utilizing the framework improvement is the step by step procedure. It
has various accompanying stages (Monden, 2013).
. Preparatory examination: The most important tedious errand is to recognize the
genuine issue of the past introduced framework. To understand the blame in the framework, the
examination requires more hours and days. In this stage, the examiner creates an overview by
the social affair all the required data for the framework components and distribution of the
prerequisites to the product.
Examination of the necessity: The investigator comprehends the working of the data
and the elements of the product which is required for the framework. The investigator makes a
concise report of the prerequisites and tries to break down the execution of the framework which
is to be created.
Framework outline: The investigator creates the number of plan of the framework on
the paper or on the PC and sees the unpleasant picture made of the framework involves the all
prerequisites or not. Once the process is done, the expert will select the best plan.
Framework coding: The expert deciphers the code or the projects such that they
progress toward becoming in machine intelligible shape. The coding step is extremely tedious
and includes number of spaces for mistakes.
Framework testing: Once the investigation is through with the coding stage. First, he
starts to test the framework and also makes sure that it is filling in according to the desires or
not.
Framework usage: This is a standout amongst the most fundamental stages as in this
stage the examiner really gives the framework to the client and expects for a positive criticism.
Framework support: Now we can see the last phase of the SDLC. In this phase, the
investigator needs to keep up the framework and make sure that it working inside the gauges
set.
7
The product is delivered very quickly.
When compared to other models, it is very realistic approach for software development.
Demerits:
The final output could not be delivered efficiently when the customer is not clear about
their requirement.
1.2 Importance of procedural/staged lifecycle in a system investigation:
The importance of utilizing the framework improvement is the step by step procedure. It
has various accompanying stages (Monden, 2013).
. Preparatory examination: The most important tedious errand is to recognize the
genuine issue of the past introduced framework. To understand the blame in the framework, the
examination requires more hours and days. In this stage, the examiner creates an overview by
the social affair all the required data for the framework components and distribution of the
prerequisites to the product.
Examination of the necessity: The investigator comprehends the working of the data
and the elements of the product which is required for the framework. The investigator makes a
concise report of the prerequisites and tries to break down the execution of the framework which
is to be created.
Framework outline: The investigator creates the number of plan of the framework on
the paper or on the PC and sees the unpleasant picture made of the framework involves the all
prerequisites or not. Once the process is done, the expert will select the best plan.
Framework coding: The expert deciphers the code or the projects such that they
progress toward becoming in machine intelligible shape. The coding step is extremely tedious
and includes number of spaces for mistakes.
Framework testing: Once the investigation is through with the coding stage. First, he
starts to test the framework and also makes sure that it is filling in according to the desires or
not.
Framework usage: This is a standout amongst the most fundamental stages as in this
stage the examiner really gives the framework to the client and expects for a positive criticism.
Framework support: Now we can see the last phase of the SDLC. In this phase, the
investigator needs to keep up the framework and make sure that it working inside the gauges
set.
7

2. Task 2
2.1 Feasibility report component:
Feasibility in Economics
The name of studying the fee advantage exploration of the assignment/software is called
Economic Feasibility. As an example personnel value, the efficiency of a triumphing system is
checked by this kind of feasibility.
This forms of have a examine which can be generally taken into consideration
responsibilities as they may gain extra than unique from computerization and non-functional
characteristics which include the time delay among the real world and the wonderful parts of the
system. The device charges need to additionally be predicted in terms of primary belongings of
coins, people and time.
Technical Feasibility
The technical feasibility principle is to take a look to ensure that the path of movement is
feasible or not. This is nothing to show that to check the model works properly? A technical
feasibility assessment ought to be carried out to all tasks being considered as a way to higher
recognize if the project may be carried out “technically” and if it may be performed “proper here
and now.”moreover, the early degrees of technical evaluation will help apprehend regions of
fortes and vulnerable point inside the proposed challenge in order that we recognize wherein to
direct similarly thought, planning, sources or assistance.(Sakas and Konstantopoulos, 2010)
Operational Feasibility
Operational feasibility have a test which is used to investigate the factors which include
the personnel probably response and changes in the proposed organization. This also involves
to show how properly a deliberate system solves the problems of the assignment and the
manner properly it sincerely works at the usage of the opportunities of the mission.
In much other feasibility, the operational feasibility is one of the important factors. As an
instance, if the worker are glad with the proposed system and find out no purpose to change
then there may be an excessive degree of resistance to the current day gadget. Applicable
elements proper right here problem if the task has cutting-edge management assist and
whether or not or no longer or no longer the customers were worried inside the improvement of
the perception.(Groff, 2011)
8
2.1 Feasibility report component:
Feasibility in Economics
The name of studying the fee advantage exploration of the assignment/software is called
Economic Feasibility. As an example personnel value, the efficiency of a triumphing system is
checked by this kind of feasibility.
This forms of have a examine which can be generally taken into consideration
responsibilities as they may gain extra than unique from computerization and non-functional
characteristics which include the time delay among the real world and the wonderful parts of the
system. The device charges need to additionally be predicted in terms of primary belongings of
coins, people and time.
Technical Feasibility
The technical feasibility principle is to take a look to ensure that the path of movement is
feasible or not. This is nothing to show that to check the model works properly? A technical
feasibility assessment ought to be carried out to all tasks being considered as a way to higher
recognize if the project may be carried out “technically” and if it may be performed “proper here
and now.”moreover, the early degrees of technical evaluation will help apprehend regions of
fortes and vulnerable point inside the proposed challenge in order that we recognize wherein to
direct similarly thought, planning, sources or assistance.(Sakas and Konstantopoulos, 2010)
Operational Feasibility
Operational feasibility have a test which is used to investigate the factors which include
the personnel probably response and changes in the proposed organization. This also involves
to show how properly a deliberate system solves the problems of the assignment and the
manner properly it sincerely works at the usage of the opportunities of the mission.
In much other feasibility, the operational feasibility is one of the important factors. As an
instance, if the worker are glad with the proposed system and find out no purpose to change
then there may be an excessive degree of resistance to the current day gadget. Applicable
elements proper right here problem if the task has cutting-edge management assist and
whether or not or no longer or no longer the customers were worried inside the improvement of
the perception.(Groff, 2011)
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Feasibility in Time
Time feasibility is used to show that the give task must be completed within the time limit
or no longer. This study can assist mitigate the hazard that a task is losing its time. In addition, it
is used to show the task to be completed in orderly and perfectly.
Time Viability has a look at enables to understand the numerous constraints on the task
agenda and whether or not they are probably fairly met, so that letter there couldn't be any
hassle to meet the mission purpose.
Legal Feasibility
Legal feasibility is used to define whether the proposed model struggle with prison necessities,
for example a records processing gadget have to take a look at the local information protection
Acts. Many reviews are preferred even the business enterprise has both internal and outside
felony suggest. But, a venture can also additionally face jail troubles after of entirety if this
element isn't taken into consideration at this level.It also decide whether or now not the
proposed undertaking conflicts with legal necessities along with diagnosed Acts, Statutes, or
any pending law.(Recommendations for Design and Analysis of Earth Structures Using
Geosynthetic Reinforcements, 2011)
Social Feasibility
The social feasibility is used to test whether the designed software system can be
wonderful with the people or now not.This assumption could in standard have a look at the
possibility that the project could need to be stated via the use of the group of humans which are
without delay tormented by the Designed system.
Management Feasibility
The organizational chart and the qualification of the people are concerned by the
management feasibility. This feasibility is used to check if the workers ofthe corporation are
capable of taking walks and preserving the designed system.(Pernia and Quising, 2003)
2.2 Different feasibility criteria impact on a systems investigation
The Feasibility check is an assessment of possible possibility solutions to a trouble and
an advice on the satisfying possibility. It is able to determine whether or not a manner be
finished with the aid of a cutting-edge software development product extra successfully than the
triumphing one.
The feasibility examine need to observe 3 principal areas;
- Market troubles,
- Technical and organizational requirements,
9
Time feasibility is used to show that the give task must be completed within the time limit
or no longer. This study can assist mitigate the hazard that a task is losing its time. In addition, it
is used to show the task to be completed in orderly and perfectly.
Time Viability has a look at enables to understand the numerous constraints on the task
agenda and whether or not they are probably fairly met, so that letter there couldn't be any
hassle to meet the mission purpose.
Legal Feasibility
Legal feasibility is used to define whether the proposed model struggle with prison necessities,
for example a records processing gadget have to take a look at the local information protection
Acts. Many reviews are preferred even the business enterprise has both internal and outside
felony suggest. But, a venture can also additionally face jail troubles after of entirety if this
element isn't taken into consideration at this level.It also decide whether or now not the
proposed undertaking conflicts with legal necessities along with diagnosed Acts, Statutes, or
any pending law.(Recommendations for Design and Analysis of Earth Structures Using
Geosynthetic Reinforcements, 2011)
Social Feasibility
The social feasibility is used to test whether the designed software system can be
wonderful with the people or now not.This assumption could in standard have a look at the
possibility that the project could need to be stated via the use of the group of humans which are
without delay tormented by the Designed system.
Management Feasibility
The organizational chart and the qualification of the people are concerned by the
management feasibility. This feasibility is used to check if the workers ofthe corporation are
capable of taking walks and preserving the designed system.(Pernia and Quising, 2003)
2.2 Different feasibility criteria impact on a systems investigation
The Feasibility check is an assessment of possible possibility solutions to a trouble and
an advice on the satisfying possibility. It is able to determine whether or not a manner be
finished with the aid of a cutting-edge software development product extra successfully than the
triumphing one.
The feasibility examine need to observe 3 principal areas;
- Market troubles,
- Technical and organizational requirements,
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

- Financial review.
The effort of time feasibility is used to show that the give task must be completed within
the time limit or no longer. This study can assist mitigate the hazard that a task is losing its time.
In addition, it is used to show the task to be completed in orderly and perfectly.
At the end of the society expertise, there is paved the way for the statistics growth and
the dependency. A fact has typically been high thing for the improvement of society and is
regularly appeared as a vital countrywide beneficial useful aid. This goal is met by offering the
information. Information plays a crucial part in our lives. The usage of new tools and strategies
to facilitate the proper customers to the right information is achieved by the information source.
The statistics technology was implemented inside the library which has introduced new
kinds of library offerings to get more person pride. Digital library provides more facilities after the
implementation of IT inside the library. Information generation has a big impact and has
successfully modified the characteristics of records offerings being created in libraries.The
technological improvement have made substantial effect on the boom of records and unlocking
of human potential. In library, the effect is genuinely seen on records property, offerings, and
those.
Operational Impact
Organizations which might be lean of their competitive race are folks who excel of their
operations in methods which are probably honestly tuned with their strategic intents. The
operational is used to increase the operational effect of their technique and to advantage
sustained excessive overall performance.
Economic Impact
Economic impact research generally searching for to installation the net alternate in
more than a few financial systems - in specific terms, coins inflows and outflows are used to
measure and also to establish the internet outcome. The 'monetary impact' of a primary
occasion refers to the full quantity of greater expenditure generated inner defined vicinity, as an
immediate end result of staging the event. For max events, spending thru site traffic in the
neighborhood vicinity is the maximum essential component in producing economic impact; but,
spending by using occasion organizers is each different vital attention.
Social Impact
The region to start in delivering specific social influences is for an occasion to have
actually said targets and objectives that describe the shipping mechanisms via which the
10
The effort of time feasibility is used to show that the give task must be completed within
the time limit or no longer. This study can assist mitigate the hazard that a task is losing its time.
In addition, it is used to show the task to be completed in orderly and perfectly.
At the end of the society expertise, there is paved the way for the statistics growth and
the dependency. A fact has typically been high thing for the improvement of society and is
regularly appeared as a vital countrywide beneficial useful aid. This goal is met by offering the
information. Information plays a crucial part in our lives. The usage of new tools and strategies
to facilitate the proper customers to the right information is achieved by the information source.
The statistics technology was implemented inside the library which has introduced new
kinds of library offerings to get more person pride. Digital library provides more facilities after the
implementation of IT inside the library. Information generation has a big impact and has
successfully modified the characteristics of records offerings being created in libraries.The
technological improvement have made substantial effect on the boom of records and unlocking
of human potential. In library, the effect is genuinely seen on records property, offerings, and
those.
Operational Impact
Organizations which might be lean of their competitive race are folks who excel of their
operations in methods which are probably honestly tuned with their strategic intents. The
operational is used to increase the operational effect of their technique and to advantage
sustained excessive overall performance.
Economic Impact
Economic impact research generally searching for to installation the net alternate in
more than a few financial systems - in specific terms, coins inflows and outflows are used to
measure and also to establish the internet outcome. The 'monetary impact' of a primary
occasion refers to the full quantity of greater expenditure generated inner defined vicinity, as an
immediate end result of staging the event. For max events, spending thru site traffic in the
neighborhood vicinity is the maximum essential component in producing economic impact; but,
spending by using occasion organizers is each different vital attention.
Social Impact
The region to start in delivering specific social influences is for an occasion to have
actually said targets and objectives that describe the shipping mechanisms via which the
10

deliberate influences will arise.Social impacts aren't in all likelihood to manifest with the aid of
risk and want to be managed if they're to arise.
3. Task 3
3.1 Investigating the system, for meeting the business
3.1.1 Introduction
The main objective of this project is to analyze and study the given requirements to
prepare the SRS document for Himilayan Hotel.
Aim
SRS document is generally called as Software Requirement specification. This
requirement document is about the detailed description about requirement specifications of
Himilayan Hotel. It helps in building the hotel management system explained in the given case
study. The requirements areprepared based on how its benefits to the system user and how the
administrator manages all operations of hotel simply(Hotelogix.com, 2018). Based on the
requirements specified in this document, the Himilayan hotel management system will be
planned, designed. Developed and finally tested based on usability test. This requirement
document will help in future improvisation of this project at various level.
Importance
To automate the foremost motel operations, the Himilayan hotel management system is
decided to produce this software product. Reservation is the number one system and also to
preserve the required room which the user asked for (Jinisyssoftware.com, 2018). The
reservation system like movie ticket booking, train ticket or bus ticket reservation is widely used
and it facilitates the user (Prologicfirst.com, 2018). The tracing or retrieving details is the second
subsystem. The contemporary room is expensed by using the selling meals mechanism. The
management service is probably referred to as zero subsystem. Critiques are generated by the
automatic work system to review all in operations and also permits alternate of subsystem
information. The element in 2-wide spread description is used to define the above mentioned
three subsystem’s capacity. There are surrender customers for the HMS. The resort personnel
(customer support representative) and managers are the quit clients (Iqbal, 2016).
Allows the client to book the rooms through internet ( Rooms availability, price of the
rooms and also different facilities available in the hotel can be viewed by the client)
Rooms are reserved through on-line
11
risk and want to be managed if they're to arise.
3. Task 3
3.1 Investigating the system, for meeting the business
3.1.1 Introduction
The main objective of this project is to analyze and study the given requirements to
prepare the SRS document for Himilayan Hotel.
Aim
SRS document is generally called as Software Requirement specification. This
requirement document is about the detailed description about requirement specifications of
Himilayan Hotel. It helps in building the hotel management system explained in the given case
study. The requirements areprepared based on how its benefits to the system user and how the
administrator manages all operations of hotel simply(Hotelogix.com, 2018). Based on the
requirements specified in this document, the Himilayan hotel management system will be
planned, designed. Developed and finally tested based on usability test. This requirement
document will help in future improvisation of this project at various level.
Importance
To automate the foremost motel operations, the Himilayan hotel management system is
decided to produce this software product. Reservation is the number one system and also to
preserve the required room which the user asked for (Jinisyssoftware.com, 2018). The
reservation system like movie ticket booking, train ticket or bus ticket reservation is widely used
and it facilitates the user (Prologicfirst.com, 2018). The tracing or retrieving details is the second
subsystem. The contemporary room is expensed by using the selling meals mechanism. The
management service is probably referred to as zero subsystem. Critiques are generated by the
automatic work system to review all in operations and also permits alternate of subsystem
information. The element in 2-wide spread description is used to define the above mentioned
three subsystem’s capacity. There are surrender customers for the HMS. The resort personnel
(customer support representative) and managers are the quit clients (Iqbal, 2016).
Allows the client to book the rooms through internet ( Rooms availability, price of the
rooms and also different facilities available in the hotel can be viewed by the client)
Rooms are reserved through on-line
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





