Analysis of Security Issues and Solutions in Cloud Computing Systems
VerifiedAdded on 2020/12/10
|10
|2709
|111
Report
AI Summary
This report provides a comprehensive overview of system and network security within the context of cloud computing. It begins by introducing cloud computing and its applications, emphasizing its cost-effectiveness and scalability. The report then delves into the various security issues and threats associated with cloud environments, including data loss, malware injection, account hijacking, system vulnerabilities, and insecure APIs. To address these concerns, the report explores several solutions, such as encryption techniques (attribute-based, fully homomorphic, and searchable encryption), security protocols (TLS, SSH, IPSec, UIDM), and authentication and authorization approaches (Kerberos and novel mutual authentication protocols). Furthermore, it highlights measures to improve internet security, including using updated antivirus software, employing strong passwords, avoiding suspicious links, and regularly backing up data. The report concludes by emphasizing the importance of proactive security measures in mitigating the risks associated with cloud computing.

SYSTEM AND NETWORK
SECURITY
SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
SECURITY ISSUES........................................................................................................................1
SOLUTIONS FOR SECURITY CONCERNS................................................................................3
CONCLUSION................................................................................................................................5
REFERENCES................................................................................................................................7
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
SECURITY ISSUES........................................................................................................................1
SOLUTIONS FOR SECURITY CONCERNS................................................................................3
CONCLUSION................................................................................................................................5
REFERENCES................................................................................................................................7

INTRODUCTION
System and network security concepts are essential to sustain the usability and benefits of
technological developments. Cloud computing is defined as the technique to provide storage,
application and other computing services via internet. This enable users to customize services as
per their requirements.
The report will describe applications and benefits of cloud computing application area. It
will explain security aspects of network and networking threats associated with them. The
document will focus on security protocols, encryption methods and authorization approaches
which can enhance the network security. This will also analyse the implementation of techniques
which can improve network security on internet.
MAIN BODY
APPLICATIONS OF CLOUD COMPUTING
Cloud Computing is one of the most widely used technical applications. It allows users to
manage their data through internet. Thus, cloud computing can be defined as a way to provide
computing services such as database, software, servers and network through a server or system
located on remote location.. It is cost effective and innovative strategy. Cloud computing enables
organisations to store their data on hardware devices of vendors. This eliminates the requirement
of physical space in front end. The major advantage of this methodology is that it eliminates the
cost involved in purchasing of hardware and software. It delivers required bandwidth, resources
and power requirements so that business activities can be made more flexible and efficient.
This technical aspect has played a major role in global expansion of business activities. It
permits its users to share their data and resources with great speed and security policies [1].
Cloud Computing back end is managed entirely by the vendor. It allows the client to utilise the
processing power of complete network. Hence more data can be stored and processed at higher
speed The users pay only for services as they use memory, bandwidth and processing time. The
on demand services and easy scalability are key features which makes it efficient. With the help
of this, it is possible for small enterprises to access those services which were earlier accessible
to only large sized business groups. Thus, it provides opportunities to achieve business goals by
efficient use of internet and technology.
1
System and network security concepts are essential to sustain the usability and benefits of
technological developments. Cloud computing is defined as the technique to provide storage,
application and other computing services via internet. This enable users to customize services as
per their requirements.
The report will describe applications and benefits of cloud computing application area. It
will explain security aspects of network and networking threats associated with them. The
document will focus on security protocols, encryption methods and authorization approaches
which can enhance the network security. This will also analyse the implementation of techniques
which can improve network security on internet.
MAIN BODY
APPLICATIONS OF CLOUD COMPUTING
Cloud Computing is one of the most widely used technical applications. It allows users to
manage their data through internet. Thus, cloud computing can be defined as a way to provide
computing services such as database, software, servers and network through a server or system
located on remote location.. It is cost effective and innovative strategy. Cloud computing enables
organisations to store their data on hardware devices of vendors. This eliminates the requirement
of physical space in front end. The major advantage of this methodology is that it eliminates the
cost involved in purchasing of hardware and software. It delivers required bandwidth, resources
and power requirements so that business activities can be made more flexible and efficient.
This technical aspect has played a major role in global expansion of business activities. It
permits its users to share their data and resources with great speed and security policies [1].
Cloud Computing back end is managed entirely by the vendor. It allows the client to utilise the
processing power of complete network. Hence more data can be stored and processed at higher
speed The users pay only for services as they use memory, bandwidth and processing time. The
on demand services and easy scalability are key features which makes it efficient. With the help
of this, it is possible for small enterprises to access those services which were earlier accessible
to only large sized business groups. Thus, it provides opportunities to achieve business goals by
efficient use of internet and technology.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY ISSUES
Cloud computing has emerged as a new platform in today’s technological world. It has
allowed business to operate in different areas effectively. For this, use of third parties that
provide cloud computing services at large level have been intervened. Businesses do not have
their own information technology infrastructure. This led to effective data sharing. But in recent
times ,there has been a lot of issues and problems that has occurred in cloud computing, which
has affected the entire network through which network is connected.
These security threats have been a major problem for business. Thus, it is important to
protect systems and network from different types of security threats. It will help in proper and
secured sharing of confidential data over network. There are various security threats and issues
in cloud computing that must be solved by implementation of applications and software. It will
allow in encrypted sharing of data and information [2].
Various threats are described below: -
Data loss – This is the most common security issue that occurs in cloud computing. In this, the
data that is stored in server or system of third party gets lose due to cyber-attack, natural
disaster or data wipe by service provider. The data is lost when external entities attack on
network. This is done by some malicious activities or sending messages that are known as
ransomware. If confidential data is loss, it can be devastating for business. Besides this, it is
difficult to retrieve data when it is lost. Security of data has to be considered in cloud
computing [12]. This can also lead to downfall in share prices which will result in decrease
in brand value of company.
Malware injection – There are some codes or scripts that are embedded into cloud computing
services which can led to misuse of confidential data. These malwares are specially
developed to steal information. Cloud computing is usually based on SaaS service platform,
so it becomes easy for attacker to inject malware in network. Malware can enter in any part
of software or service that can ruin cloud servers as well.
Hijacking of accounts- This is a new type of security threat in which hacker uses employee ID
to enter into network and steal information. Here, attacker manipulates the user by using
scripting bugs and reused passwords [3]. It allows hacker to steal data without any
credentials. This type of security threat is difficult to detect. Hijacking of accounts can be
done by applying various security threats such as phishing, keylogging, buffer overflow, etc.
2
Cloud computing has emerged as a new platform in today’s technological world. It has
allowed business to operate in different areas effectively. For this, use of third parties that
provide cloud computing services at large level have been intervened. Businesses do not have
their own information technology infrastructure. This led to effective data sharing. But in recent
times ,there has been a lot of issues and problems that has occurred in cloud computing, which
has affected the entire network through which network is connected.
These security threats have been a major problem for business. Thus, it is important to
protect systems and network from different types of security threats. It will help in proper and
secured sharing of confidential data over network. There are various security threats and issues
in cloud computing that must be solved by implementation of applications and software. It will
allow in encrypted sharing of data and information [2].
Various threats are described below: -
Data loss – This is the most common security issue that occurs in cloud computing. In this, the
data that is stored in server or system of third party gets lose due to cyber-attack, natural
disaster or data wipe by service provider. The data is lost when external entities attack on
network. This is done by some malicious activities or sending messages that are known as
ransomware. If confidential data is loss, it can be devastating for business. Besides this, it is
difficult to retrieve data when it is lost. Security of data has to be considered in cloud
computing [12]. This can also lead to downfall in share prices which will result in decrease
in brand value of company.
Malware injection – There are some codes or scripts that are embedded into cloud computing
services which can led to misuse of confidential data. These malwares are specially
developed to steal information. Cloud computing is usually based on SaaS service platform,
so it becomes easy for attacker to inject malware in network. Malware can enter in any part
of software or service that can ruin cloud servers as well.
Hijacking of accounts- This is a new type of security threat in which hacker uses employee ID
to enter into network and steal information. Here, attacker manipulates the user by using
scripting bugs and reused passwords [3]. It allows hacker to steal data without any
credentials. This type of security threat is difficult to detect. Hijacking of accounts can be
done by applying various security threats such as phishing, keylogging, buffer overflow, etc.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

System vulnerabilities- Cloud Computing System are open platform for business to share and
access information and data. The infrastructure of these system is complex and contains
multiple third party platforms. Hence, it may lack some essential features that are required.
It can be drawback for system. So, if any vulnerability is known to party then it can be used
against organization. Alongside this, it can lead to impact on entire network. These
vulnerabilities can occur in system and breach data sharing. It occurs because of ineffective
security of systems.
Insecure API’s – In cloud computing, users are given authorization to customize their system.
For this, it is important to identify business needs so that features can be modified
accordingly. With change in API, risk of security risk also increases [11]. It is because
programmer develop their own applications. For this, critical and complex software are used
that can rise the security threat. Due to this, vulnerability in communication and between
application occurs.
These types of different security risk and threats occurs in cloud computing. Due
to this, it has been difficult for business to depend on third party for use of services. Besides
this, risk and threat has been a major concern which has enforced organization to develop
and implement strong protocols and policies [4]. Moreover, advance software and
applications are installed so that data and information remains confidential and protected.
SOLUTIONS FOR SECURITY CONCERNS
There are several strategies which can be used to address the system and network related
security concerns of cloud computing.
Such issues can be resolved by following approaches:
Encryption technique
It is defined as the process of encoding the transmitted information so that in networks,
only authorised users can access the sensitive data. The data is coded in such a way that only
authorities have decoding permission. This is one of the most important features which provide
end-to-end data security. In cloud computing, the following types of encryption are used for
enhancing the security.
3
access information and data. The infrastructure of these system is complex and contains
multiple third party platforms. Hence, it may lack some essential features that are required.
It can be drawback for system. So, if any vulnerability is known to party then it can be used
against organization. Alongside this, it can lead to impact on entire network. These
vulnerabilities can occur in system and breach data sharing. It occurs because of ineffective
security of systems.
Insecure API’s – In cloud computing, users are given authorization to customize their system.
For this, it is important to identify business needs so that features can be modified
accordingly. With change in API, risk of security risk also increases [11]. It is because
programmer develop their own applications. For this, critical and complex software are used
that can rise the security threat. Due to this, vulnerability in communication and between
application occurs.
These types of different security risk and threats occurs in cloud computing. Due
to this, it has been difficult for business to depend on third party for use of services. Besides
this, risk and threat has been a major concern which has enforced organization to develop
and implement strong protocols and policies [4]. Moreover, advance software and
applications are installed so that data and information remains confidential and protected.
SOLUTIONS FOR SECURITY CONCERNS
There are several strategies which can be used to address the system and network related
security concerns of cloud computing.
Such issues can be resolved by following approaches:
Encryption technique
It is defined as the process of encoding the transmitted information so that in networks,
only authorised users can access the sensitive data. The data is coded in such a way that only
authorities have decoding permission. This is one of the most important features which provide
end-to-end data security. In cloud computing, the following types of encryption are used for
enhancing the security.
3
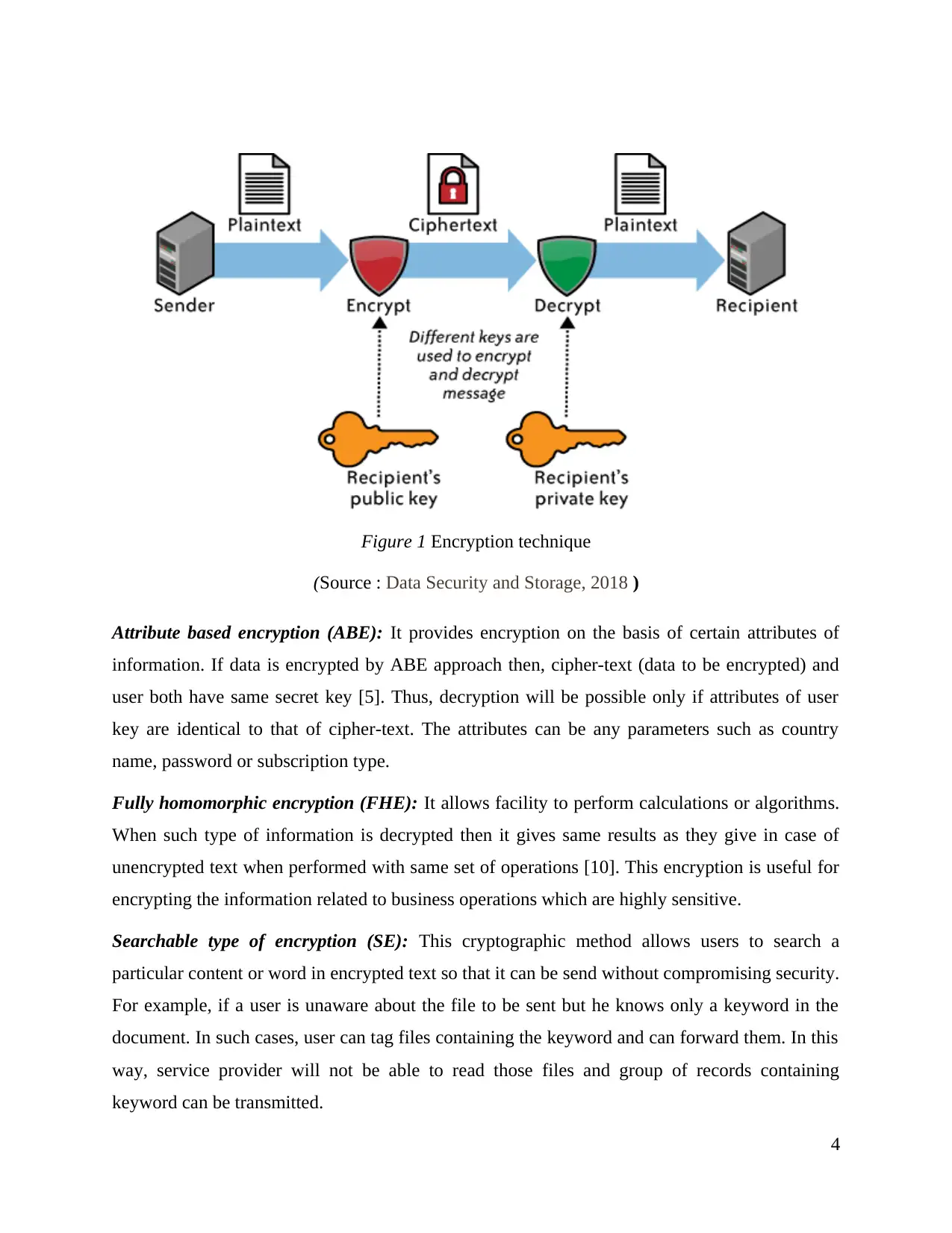
Figure 1 Encryption technique
(Source : Data Security and Storage, 2018 )
Attribute based encryption (ABE): It provides encryption on the basis of certain attributes of
information. If data is encrypted by ABE approach then, cipher-text (data to be encrypted) and
user both have same secret key [5]. Thus, decryption will be possible only if attributes of user
key are identical to that of cipher-text. The attributes can be any parameters such as country
name, password or subscription type.
Fully homomorphic encryption (FHE): It allows facility to perform calculations or algorithms.
When such type of information is decrypted then it gives same results as they give in case of
unencrypted text when performed with same set of operations [10]. This encryption is useful for
encrypting the information related to business operations which are highly sensitive.
Searchable type of encryption (SE): This cryptographic method allows users to search a
particular content or word in encrypted text so that it can be send without compromising security.
For example, if a user is unaware about the file to be sent but he knows only a keyword in the
document. In such cases, user can tag files containing the keyword and can forward them. In this
way, service provider will not be able to read those files and group of records containing
keyword can be transmitted.
4
(Source : Data Security and Storage, 2018 )
Attribute based encryption (ABE): It provides encryption on the basis of certain attributes of
information. If data is encrypted by ABE approach then, cipher-text (data to be encrypted) and
user both have same secret key [5]. Thus, decryption will be possible only if attributes of user
key are identical to that of cipher-text. The attributes can be any parameters such as country
name, password or subscription type.
Fully homomorphic encryption (FHE): It allows facility to perform calculations or algorithms.
When such type of information is decrypted then it gives same results as they give in case of
unencrypted text when performed with same set of operations [10]. This encryption is useful for
encrypting the information related to business operations which are highly sensitive.
Searchable type of encryption (SE): This cryptographic method allows users to search a
particular content or word in encrypted text so that it can be send without compromising security.
For example, if a user is unaware about the file to be sent but he knows only a keyword in the
document. In such cases, user can tag files containing the keyword and can forward them. In this
way, service provider will not be able to read those files and group of records containing
keyword can be transmitted.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security protocols used in Cloud Computing
In order to sustain highly secured cloud environment, various cryptographic security
protocols are used.
Some of the most important of these protocols are as follows:
Security layer for transport protocol: These protocols allows client server of cloud network to
communicate with other devices [6]. It prevents data theft from hackers and avoids data loss by
providing secure encryption.
Secure shell protocol: It allows multiple functioning so that multiple access and remote login are
possible in cloud computing securely. It ensures that network services are operated only within
secure environment.
Internet protocol security (IPSec): This set of rules is known as the transmission protocol for
secure communication within cloud. It supports functions such as peer authentication of data
origin and network level as well as replay protection.
User identity management protocol (UIDM): This set of rules deals with issues related to
authentication and accessing [9]. It determines mechanisms by which highly privileged accounts
are managed and protected from hacking and other threats.
Authentication protocols and authorization approach for enhancing network security
Cloud computing includes effective guidelines and rules for preventing unauthorised
access. These approaches enable the users to share their resources with only authorised clients.
Kerberos protocols: This authentication protocol permits nodes to communicate over insecure
network to validate their identity to each other in secure mechanism. It requires participation of
trusted user or client and is based on symmetric cryptography.
Novel mutual authentication protocol for cloud computing: This approach of network
authorisation uses steganography scheme of encryption. It achieves authentication by dividing
secrets into parts between all participating parties [7]. The message is decrypted only when all
parts of message are combined. In this way an unauthorised entity is not allowed to interact.
These authorization approaches avoid unauthenticated practices as well as the threats
such as denial of services and passwords cloning.
5
In order to sustain highly secured cloud environment, various cryptographic security
protocols are used.
Some of the most important of these protocols are as follows:
Security layer for transport protocol: These protocols allows client server of cloud network to
communicate with other devices [6]. It prevents data theft from hackers and avoids data loss by
providing secure encryption.
Secure shell protocol: It allows multiple functioning so that multiple access and remote login are
possible in cloud computing securely. It ensures that network services are operated only within
secure environment.
Internet protocol security (IPSec): This set of rules is known as the transmission protocol for
secure communication within cloud. It supports functions such as peer authentication of data
origin and network level as well as replay protection.
User identity management protocol (UIDM): This set of rules deals with issues related to
authentication and accessing [9]. It determines mechanisms by which highly privileged accounts
are managed and protected from hacking and other threats.
Authentication protocols and authorization approach for enhancing network security
Cloud computing includes effective guidelines and rules for preventing unauthorised
access. These approaches enable the users to share their resources with only authorised clients.
Kerberos protocols: This authentication protocol permits nodes to communicate over insecure
network to validate their identity to each other in secure mechanism. It requires participation of
trusted user or client and is based on symmetric cryptography.
Novel mutual authentication protocol for cloud computing: This approach of network
authorisation uses steganography scheme of encryption. It achieves authentication by dividing
secrets into parts between all participating parties [7]. The message is decrypted only when all
parts of message are combined. In this way an unauthorised entity is not allowed to interact.
These authorization approaches avoid unauthenticated practices as well as the threats
such as denial of services and passwords cloning.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Measures to improve internet security
The users must take following measurements so that they can meet the security standards
in the cloud environment.
Antivirus, firewalls and other applications must be used with their latest version so that
they can deal with the advancing nature of cyber threats.
The passwords must be strong and must be change periodically. The business groups
must share passwords only with valid users through encryption.
The suspicious mails or links must be avoided and reported as spam. This awareness can
reduce the risk of security threats to a great extent. The business companies must
organize training sessions for developing awareness regarding such threats.
Information must be exchanged on internet only after validation from the authentication
protocols. Backing up data regularly will also minimise losses in case of networking
attacks. So users must back up their data regularly.
For organisations or open networks which allow remote and multiple access the network
traffic must be monitored regularly [8]. There are possibilities that within network some
users create a loophole for the security. In such cases, traffic analysis and monitoring will
identify suspicious activities to eliminate them as soon as possible.
The social networking tools are becoming integral part of the business. These tools have
ability to access the good amount of information. Thus, it is necessary for the companies
and users that with the use of these tool privacy settings must be monitored. The excess
information available for public mode can encourage the adverse impacts.
It is essential to develop knowledge regarding advancing technology so that appropriate
measurements can be taken to improve the security.
These measurements are helpful in enhancing network security on internet. It may be
possible that with advancements in cyber risks, user may not be able to deal with it but such
measurements will minimise the impact of networking security concerns.
CONCLUSION
From the report, it can be concluded that network security concerns must be resolved at
the priority. Despite several advantages, network systems and cloud computing are always
6
The users must take following measurements so that they can meet the security standards
in the cloud environment.
Antivirus, firewalls and other applications must be used with their latest version so that
they can deal with the advancing nature of cyber threats.
The passwords must be strong and must be change periodically. The business groups
must share passwords only with valid users through encryption.
The suspicious mails or links must be avoided and reported as spam. This awareness can
reduce the risk of security threats to a great extent. The business companies must
organize training sessions for developing awareness regarding such threats.
Information must be exchanged on internet only after validation from the authentication
protocols. Backing up data regularly will also minimise losses in case of networking
attacks. So users must back up their data regularly.
For organisations or open networks which allow remote and multiple access the network
traffic must be monitored regularly [8]. There are possibilities that within network some
users create a loophole for the security. In such cases, traffic analysis and monitoring will
identify suspicious activities to eliminate them as soon as possible.
The social networking tools are becoming integral part of the business. These tools have
ability to access the good amount of information. Thus, it is necessary for the companies
and users that with the use of these tool privacy settings must be monitored. The excess
information available for public mode can encourage the adverse impacts.
It is essential to develop knowledge regarding advancing technology so that appropriate
measurements can be taken to improve the security.
These measurements are helpful in enhancing network security on internet. It may be
possible that with advancements in cyber risks, user may not be able to deal with it but such
measurements will minimise the impact of networking security concerns.
CONCLUSION
From the report, it can be concluded that network security concerns must be resolved at
the priority. Despite several advantages, network systems and cloud computing are always
6

vulnerable to security risks. Thus, essential measures must be taken by the users to prevent
information from theft or unauthorised access. This report has explained various applications and
security concerns associated with cloud computing.
It has analysed the impact of these security threats on performance of network and
system. This document has also evaluated different mechanism which can help organisations and
individuals to increase security standards of their entire network assembling. Hence, it can be
summarised that for smooth functioning of cloud network to gain benefits in context of
networking security must be strictly implemented and monitored regularly.
7
information from theft or unauthorised access. This report has explained various applications and
security concerns associated with cloud computing.
It has analysed the impact of these security threats on performance of network and
system. This document has also evaluated different mechanism which can help organisations and
individuals to increase security standards of their entire network assembling. Hence, it can be
summarised that for smooth functioning of cloud network to gain benefits in context of
networking security must be strictly implemented and monitored regularly.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
[1].Books and Journals
[2].Ali M, Khan SU, Vasilakos AV. Security in cloud computing: Opportunities and
challenges. Information sciences. 2015 Jun 1; 305:357-83.
[3].Almorsy M, Grundy J, Müller I. An analysis of the cloud computing security problem.
arXiv preprint arXiv:1609.01107. 2016 Sep 5.
[4].Han B, Gopalakrishnan V, Ji L, Lee S. Network function virtualization: Challenges and
opportunities for innovations. IEEE Communications Magazine. 2015 Feb;53(2):90-7.
[5].How to improve your online security and privacy in 10 easy steps, 2016 [Online]
Accessed through <https://elie.net/blog/security/how-to-improve-your-online-security-
and-privacy-in-10-easy-steps>
[6].Knapp ED, Langill JT. Industrial Network Security: Securing critical infrastructure
networks for smart grid, SCADA, and other Industrial Control Systems. Syngress; 2014
Dec 9.
[7].Li L, Sun J, Liu Y, Dong JS. Verifying parameterized timed security protocols.
InInternational Symposium on Formal Methods 2015 Jun 24 (pp. 342-359). Springer,
Cham.
[8].Paul S, Kumar S. Comparative Analysis of Various PPP Authentication Protocols.
[9].Perlman R, Kaufman C, Speciner M. Network security: private communication in a
public world. Pearson Education India; 2016.
[10]. Rittinghouse JW, Ransome JF. Cloud computing: implementation, management,
and security. CRC press; 2016 Apr 19.
[11]. Sandberg H, Amin S, Johansson KH. Cyberphysical security in networked control
systems: An introduction to the issue. IEEE Control Systems. 2015 Feb;35(1):20-3.
[12]. Singh S, Jeong YS, Park JH. A survey on cloud computing security: Issues,
threats, and solutions. Journal of Network and Computer Applications. 2016 Nov 1;
75:200-22.
[13]. Sprenger C, Basin D. Refining security protocols. Journal of Computer Security.
2018 Jan 1(Preprint):1-52.
8
[1].Books and Journals
[2].Ali M, Khan SU, Vasilakos AV. Security in cloud computing: Opportunities and
challenges. Information sciences. 2015 Jun 1; 305:357-83.
[3].Almorsy M, Grundy J, Müller I. An analysis of the cloud computing security problem.
arXiv preprint arXiv:1609.01107. 2016 Sep 5.
[4].Han B, Gopalakrishnan V, Ji L, Lee S. Network function virtualization: Challenges and
opportunities for innovations. IEEE Communications Magazine. 2015 Feb;53(2):90-7.
[5].How to improve your online security and privacy in 10 easy steps, 2016 [Online]
Accessed through <https://elie.net/blog/security/how-to-improve-your-online-security-
and-privacy-in-10-easy-steps>
[6].Knapp ED, Langill JT. Industrial Network Security: Securing critical infrastructure
networks for smart grid, SCADA, and other Industrial Control Systems. Syngress; 2014
Dec 9.
[7].Li L, Sun J, Liu Y, Dong JS. Verifying parameterized timed security protocols.
InInternational Symposium on Formal Methods 2015 Jun 24 (pp. 342-359). Springer,
Cham.
[8].Paul S, Kumar S. Comparative Analysis of Various PPP Authentication Protocols.
[9].Perlman R, Kaufman C, Speciner M. Network security: private communication in a
public world. Pearson Education India; 2016.
[10]. Rittinghouse JW, Ransome JF. Cloud computing: implementation, management,
and security. CRC press; 2016 Apr 19.
[11]. Sandberg H, Amin S, Johansson KH. Cyberphysical security in networked control
systems: An introduction to the issue. IEEE Control Systems. 2015 Feb;35(1):20-3.
[12]. Singh S, Jeong YS, Park JH. A survey on cloud computing security: Issues,
threats, and solutions. Journal of Network and Computer Applications. 2016 Nov 1;
75:200-22.
[13]. Sprenger C, Basin D. Refining security protocols. Journal of Computer Security.
2018 Jan 1(Preprint):1-52.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





