Systems Analysis and Design Report: Total Learning System for HQI
VerifiedAdded on 2023/03/24
|17
|2883
|27
Report
AI Summary
This report provides a comprehensive analysis and design for a Total Learning System (TLS) intended for High Quality Institute. It details both functional and non-functional requirements, including media element management, attendance tracking, and security protocols. A work breakdown structure (...

Systems Analysis and
Design
Design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
1. Functional and non-functional requirements of TLS..............................................................1
2. Work Breakdown Structure (WBS)........................................................................................3
3. Develop PERT/CPM chart explaining the early and late start for each task. Identify the
critical path and the total time to finish the project.....................................................................8
4. Use the class diagram to represent the student registration by drawing the data model
diagram. ....................................................................................................................................10
5.The net present value, the payback period, and the return on investment by using a discount
rate of 6 percent.........................................................................................................................11
6. Covered in poster..................................................................................................................12
CONCLUSION AND RECOMMENDATION.............................................................................12
INTRODUCTION...........................................................................................................................1
1. Functional and non-functional requirements of TLS..............................................................1
2. Work Breakdown Structure (WBS)........................................................................................3
3. Develop PERT/CPM chart explaining the early and late start for each task. Identify the
critical path and the total time to finish the project.....................................................................8
4. Use the class diagram to represent the student registration by drawing the data model
diagram. ....................................................................................................................................10
5.The net present value, the payback period, and the return on investment by using a discount
rate of 6 percent.........................................................................................................................11
6. Covered in poster..................................................................................................................12
CONCLUSION AND RECOMMENDATION.............................................................................12

INTRODUCTION
Teaching and learning system is a deliberate intervention that assists in effective planning
and implementation of educational activities and experiences of teaching that helps in meeting
the expected outcomes according to the plan (Sung, Chang & Liu, 2016). The present report is
based on a case study in which a Total Learning System (TLS) is to be prepared for High Quality
Institute, a technological educational establishment that provided different courses in
Information Technology. In order to accomplish this aim, a work breakdown system will be
described in this study. In addition to this, PERT/CPM chart will also be developed to identify
the starting, ending and time consumption of a task. Besides this, a class diagram will be
prepared with the help of data model diagram to represent the student registration. Further, the
development cost of the overall project will be calculated.
1. Functional and non-functional requirements of TLS.
Functional Requirements: It deals with the ability of the system to perform the operations. It
includes the description of the required functions and details of the data that are to be held in the
system (Coronel, & Morris, 2016). It is a set of inputs, behaviours and outputs. In designing of
TLS, the functional requirements are as follows:
Import and organise media elements: It is required in TLS to import various type of files
such as video, image, HTML, etc. It works on the specifications provided by the user. In
addition to this they should then convert the selected elements into a compatible format.
Synchronising the media element: TLS also performs the synchronisation of the files that
are converted in the user compatible format (Al-Samarraie, Selim & Zaqout, 2016).
Preview: This tool will assist the users to preview the presentation at any point when it
will be created. It is required in a TLS to have a preview tab, selecting which the user can
reach the preview screen.
Publish: With the help of this tactic, the system will be able to generate a HTML page
hosting the multimedia presentation.
Attendance: TLS should provide the measurement and reporting of attendance of the
students and staff.
Coursework management: The system is demanded to have the calibre of managing
coursework (Al-Samarraie, Selim, & Zaqout, 2016).
1
Teaching and learning system is a deliberate intervention that assists in effective planning
and implementation of educational activities and experiences of teaching that helps in meeting
the expected outcomes according to the plan (Sung, Chang & Liu, 2016). The present report is
based on a case study in which a Total Learning System (TLS) is to be prepared for High Quality
Institute, a technological educational establishment that provided different courses in
Information Technology. In order to accomplish this aim, a work breakdown system will be
described in this study. In addition to this, PERT/CPM chart will also be developed to identify
the starting, ending and time consumption of a task. Besides this, a class diagram will be
prepared with the help of data model diagram to represent the student registration. Further, the
development cost of the overall project will be calculated.
1. Functional and non-functional requirements of TLS.
Functional Requirements: It deals with the ability of the system to perform the operations. It
includes the description of the required functions and details of the data that are to be held in the
system (Coronel, & Morris, 2016). It is a set of inputs, behaviours and outputs. In designing of
TLS, the functional requirements are as follows:
Import and organise media elements: It is required in TLS to import various type of files
such as video, image, HTML, etc. It works on the specifications provided by the user. In
addition to this they should then convert the selected elements into a compatible format.
Synchronising the media element: TLS also performs the synchronisation of the files that
are converted in the user compatible format (Al-Samarraie, Selim & Zaqout, 2016).
Preview: This tool will assist the users to preview the presentation at any point when it
will be created. It is required in a TLS to have a preview tab, selecting which the user can
reach the preview screen.
Publish: With the help of this tactic, the system will be able to generate a HTML page
hosting the multimedia presentation.
Attendance: TLS should provide the measurement and reporting of attendance of the
students and staff.
Coursework management: The system is demanded to have the calibre of managing
coursework (Al-Samarraie, Selim, & Zaqout, 2016).
1
You're viewing a preview
Unlock full access by subscribing today!

Risk Plan: A risk plan will be prepared to deal with the situations in which the plan fails.
For instance: The preview option does not work or any virus attacks the system. This is
the most important phase of development of a system. It helps in providing alternatives
that can reduce the challenges.
Option: Options for learners should be managed. For different levels, namely
Undergraduate and postgraduate, these choices should be recorded appropriately.
Authentication: TLS should identify all the students uniquely and verified. For this, it is
needed to insert the registration number along with a security question.
Installing and configuring email: The learning system should be equipped with the option
of mailing so that students can ask their doubts through them. Also, they are helpful in
transmitting the important messages and a good tool communicate.
Web services: The system should be capable of supporting web services protocols.
Information management: The teaching and learning system should consist sorted form
of information. The details are required to match the course title. Also, proper
representation is needed to prevent the situation of vague.
Course Details Management: In this, following things will be checked: does the course
code and content matches, the relevancy of the course. Further, depending upon two
different segments that is ULS and PLS, it will be sorted.
Non functional requirements describes the method in which the software will perform the
tasks. These requirements in TLS involves the following:
Performance Requirements: It is required that the software should perform its tasks in a
consistent manner despite of the environment of Operating System. It is needed that the
time consumption for importing the files and publishing the multimedia presentation
should be nominal (Kulik, & Fletcher, 2016).
Safety Requirements: The present system does not pose threat in any way and thus, it is
not applied in TLS.
Security Requirements: To prevent any risk striking the system, a security plan is
essential. This plan will involve the methods of troubleshooting various errors that may
arise while using the system. In addition to this, passwords and Student IDs will also
developed in this phase so that their personal information can not be accessed by any one.
In present system, a security question will be asked along with registration details.
2
For instance: The preview option does not work or any virus attacks the system. This is
the most important phase of development of a system. It helps in providing alternatives
that can reduce the challenges.
Option: Options for learners should be managed. For different levels, namely
Undergraduate and postgraduate, these choices should be recorded appropriately.
Authentication: TLS should identify all the students uniquely and verified. For this, it is
needed to insert the registration number along with a security question.
Installing and configuring email: The learning system should be equipped with the option
of mailing so that students can ask their doubts through them. Also, they are helpful in
transmitting the important messages and a good tool communicate.
Web services: The system should be capable of supporting web services protocols.
Information management: The teaching and learning system should consist sorted form
of information. The details are required to match the course title. Also, proper
representation is needed to prevent the situation of vague.
Course Details Management: In this, following things will be checked: does the course
code and content matches, the relevancy of the course. Further, depending upon two
different segments that is ULS and PLS, it will be sorted.
Non functional requirements describes the method in which the software will perform the
tasks. These requirements in TLS involves the following:
Performance Requirements: It is required that the software should perform its tasks in a
consistent manner despite of the environment of Operating System. It is needed that the
time consumption for importing the files and publishing the multimedia presentation
should be nominal (Kulik, & Fletcher, 2016).
Safety Requirements: The present system does not pose threat in any way and thus, it is
not applied in TLS.
Security Requirements: To prevent any risk striking the system, a security plan is
essential. This plan will involve the methods of troubleshooting various errors that may
arise while using the system. In addition to this, passwords and Student IDs will also
developed in this phase so that their personal information can not be accessed by any one.
In present system, a security question will be asked along with registration details.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Quality Requirements:There are numerous attributes of this requirement, some major
among them are as follows:
Portability- This software will have to work on different platforms. Thus, in this case,
portability is a major dimension that is required to be consider. Thus, to ensure this, the
programming language that will be used is JAVA.
User Training: The instruction will be provided at the home page of the system. this will
help users in getting a proper and effective access to the system. All important details will
be explained with the help of brief statements. Further, the method of the software will
also be mentioned here.
All these functional and non-functional specifications mentioned are important in the
development of a teaching and learning system.
2. Work Breakdown Structure (WBS)
Task Activities I Time I Activities II Time II Total Time
Project Information 15 days - - 4 months
3
Illustration 1: Work Breakdown Structure
among them are as follows:
Portability- This software will have to work on different platforms. Thus, in this case,
portability is a major dimension that is required to be consider. Thus, to ensure this, the
programming language that will be used is JAVA.
User Training: The instruction will be provided at the home page of the system. this will
help users in getting a proper and effective access to the system. All important details will
be explained with the help of brief statements. Further, the method of the software will
also be mentioned here.
All these functional and non-functional specifications mentioned are important in the
development of a teaching and learning system.
2. Work Breakdown Structure (WBS)
Task Activities I Time I Activities II Time II Total Time
Project Information 15 days - - 4 months
3
Illustration 1: Work Breakdown Structure

Management Management
Course Details
Management
15 days
Risk Plan 15 days
Security Plan 15 days
Change Plan 2 months
Analysis Glossary 15 days Functional 15 days 1.5 month
Requirement
Specifications
1 month Non-
functional
15 days
Design 3 months 3 months
Implementatio
n
1 month 1 month
Testing 15 days 15 days
Description of tasks:
Activities I Description Activities II Description
Information
Management
In this, the information related to
the different course programmes
will be managed so that, students
can avail correct knowledge. This
management will cover so many
steps for completion such as the
data will be gathered from all the
relevant sources, then they will
be tested to prevent any error,
etc. (Hunsu, Adesope & Bayly,
2016).
-
4
Course Details
Management
15 days
Risk Plan 15 days
Security Plan 15 days
Change Plan 2 months
Analysis Glossary 15 days Functional 15 days 1.5 month
Requirement
Specifications
1 month Non-
functional
15 days
Design 3 months 3 months
Implementatio
n
1 month 1 month
Testing 15 days 15 days
Description of tasks:
Activities I Description Activities II Description
Information
Management
In this, the information related to
the different course programmes
will be managed so that, students
can avail correct knowledge. This
management will cover so many
steps for completion such as the
data will be gathered from all the
relevant sources, then they will
be tested to prevent any error,
etc. (Hunsu, Adesope & Bayly,
2016).
-
4
You're viewing a preview
Unlock full access by subscribing today!

Course Details
Management
In this, the details of the courses
will be managed to prevent any
vague situation while teaching
and learning. In this, following
things will be checked: does the
course code and content matches,
the relevancy of the course.
Further, depending upon two
different segments that is ULS
and PLS, it will be sorted.
Risk Plan A risk plan will be prepared to
deal with the situations in which
the plan fails. For instance: The
preview option does not work or
any virus attacks the system. This
is the most important phase of
development of a system. It helps
in providing alternatives that can
reduce the challenges.
Security Plan To prevent any risk striking the
system, a security plan is
essential. This plan will involve
the methods of troubleshooting
various errors that may arise
while using the system. In
addition to this, passwords and
Student IDs will also developed
in this phase so that their
personal information can not be
accessed by any one. In present
5
Management
In this, the details of the courses
will be managed to prevent any
vague situation while teaching
and learning. In this, following
things will be checked: does the
course code and content matches,
the relevancy of the course.
Further, depending upon two
different segments that is ULS
and PLS, it will be sorted.
Risk Plan A risk plan will be prepared to
deal with the situations in which
the plan fails. For instance: The
preview option does not work or
any virus attacks the system. This
is the most important phase of
development of a system. It helps
in providing alternatives that can
reduce the challenges.
Security Plan To prevent any risk striking the
system, a security plan is
essential. This plan will involve
the methods of troubleshooting
various errors that may arise
while using the system. In
addition to this, passwords and
Student IDs will also developed
in this phase so that their
personal information can not be
accessed by any one. In present
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

system, a security question will
be asked along with registration
details (Laudon, & Laudon,
2016).
Change Plan If the security plan fails in
evacuating the risks, then it is
required to have a back-up plan
to support the system. For
instance: If the security feature
will not work then it will become
mandatory to change the
Glossary This is the wordbook containing
all the information of the system.
The title of the different course
will also present in this according
to the division, wither PLS or
ULS.
Functional Import and
organise media
elements,
Synchronising the
media element,
Preview and
Publish options
will be designed.
This will represent'
"What to do".
Requirement
Specifications
It is the most crucial elements in
creation of software systems.
These specifications will allow
user in identifying, "What to do"
and "How to do". All the
important tabs such as preview,
publish, etc. will be designed in
it.
Non-
functional
User Training,
Portability, Quality
Requirements,
Security
Requirements,
Safety
Requirements and
Performance
Requirements will
6
be asked along with registration
details (Laudon, & Laudon,
2016).
Change Plan If the security plan fails in
evacuating the risks, then it is
required to have a back-up plan
to support the system. For
instance: If the security feature
will not work then it will become
mandatory to change the
Glossary This is the wordbook containing
all the information of the system.
The title of the different course
will also present in this according
to the division, wither PLS or
ULS.
Functional Import and
organise media
elements,
Synchronising the
media element,
Preview and
Publish options
will be designed.
This will represent'
"What to do".
Requirement
Specifications
It is the most crucial elements in
creation of software systems.
These specifications will allow
user in identifying, "What to do"
and "How to do". All the
important tabs such as preview,
publish, etc. will be designed in
it.
Non-
functional
User Training,
Portability, Quality
Requirements,
Security
Requirements,
Safety
Requirements and
Performance
Requirements will
6

be included in the
plan. This will
represent the
method.
Design After collecting all the
information, the system will be
designed. All the features of
management will be merged and
the final outcome will be the
teaching and learning system.
Implementation After designing the teaching and
learning system it will be
implemented for the use of
students.
Testing In a specific time, the TLS
system will be first tested. It will
be first launched for staff use so
that they can identify any flaws
in it. Depending upon the
weaknesses, modifications will
be done.
7
plan. This will
represent the
method.
Design After collecting all the
information, the system will be
designed. All the features of
management will be merged and
the final outcome will be the
teaching and learning system.
Implementation After designing the teaching and
learning system it will be
implemented for the use of
students.
Testing In a specific time, the TLS
system will be first tested. It will
be first launched for staff use so
that they can identify any flaws
in it. Depending upon the
weaknesses, modifications will
be done.
7
You're viewing a preview
Unlock full access by subscribing today!

All this operations explained in the work breakdown structure will be performed within
the mentioned time period. This structure represents the entire steps that will take place in the
designing of TLS, total time that will be consumed and segregated period based on the divided
activities.
3. Develop PERT/CPM chart explaining the early and late start for each task. Identify the critical
path and the total time to finish the project.
8
the mentioned time period. This structure represents the entire steps that will take place in the
designing of TLS, total time that will be consumed and segregated period based on the divided
activities.
3. Develop PERT/CPM chart explaining the early and late start for each task. Identify the critical
path and the total time to finish the project.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task Activit
y
Numb
er
Reason Activities Reason Activity
Number
Time
period
Proje
ct
Mana
geme
nt
(I) Project management
is the first phase of
any project. It will
cover all the
elements that will
Information
Management
Information
can be manage
only after the
course details
are entered.
1(ii) 15 days
15 Jan- 30
Jan
Course Details
Management
For managing
the project,
firstly proper
organisation of
course is
required.
1(i) 15 days
1 Jan-15
Jan
Risk Plan It is performed
after
evaluating all
the associated
risks
1(iii) 15 days
31 Jan- 14
Feb
Security Plan After assessing
the risks, a
security plan is
prepared.
1 (iv) 15 days
14 Feb.- 1
Mar
Change Plan In case, if any
flaws are
observed even
after security
then the plan is
changed.
1(v) 2 months
2 Mar - 2
April
9
y
Numb
er
Reason Activities Reason Activity
Number
Time
period
Proje
ct
Mana
geme
nt
(I) Project management
is the first phase of
any project. It will
cover all the
elements that will
Information
Management
Information
can be manage
only after the
course details
are entered.
1(ii) 15 days
15 Jan- 30
Jan
Course Details
Management
For managing
the project,
firstly proper
organisation of
course is
required.
1(i) 15 days
1 Jan-15
Jan
Risk Plan It is performed
after
evaluating all
the associated
risks
1(iii) 15 days
31 Jan- 14
Feb
Security Plan After assessing
the risks, a
security plan is
prepared.
1 (iv) 15 days
14 Feb.- 1
Mar
Change Plan In case, if any
flaws are
observed even
after security
then the plan is
changed.
1(v) 2 months
2 Mar - 2
April
9
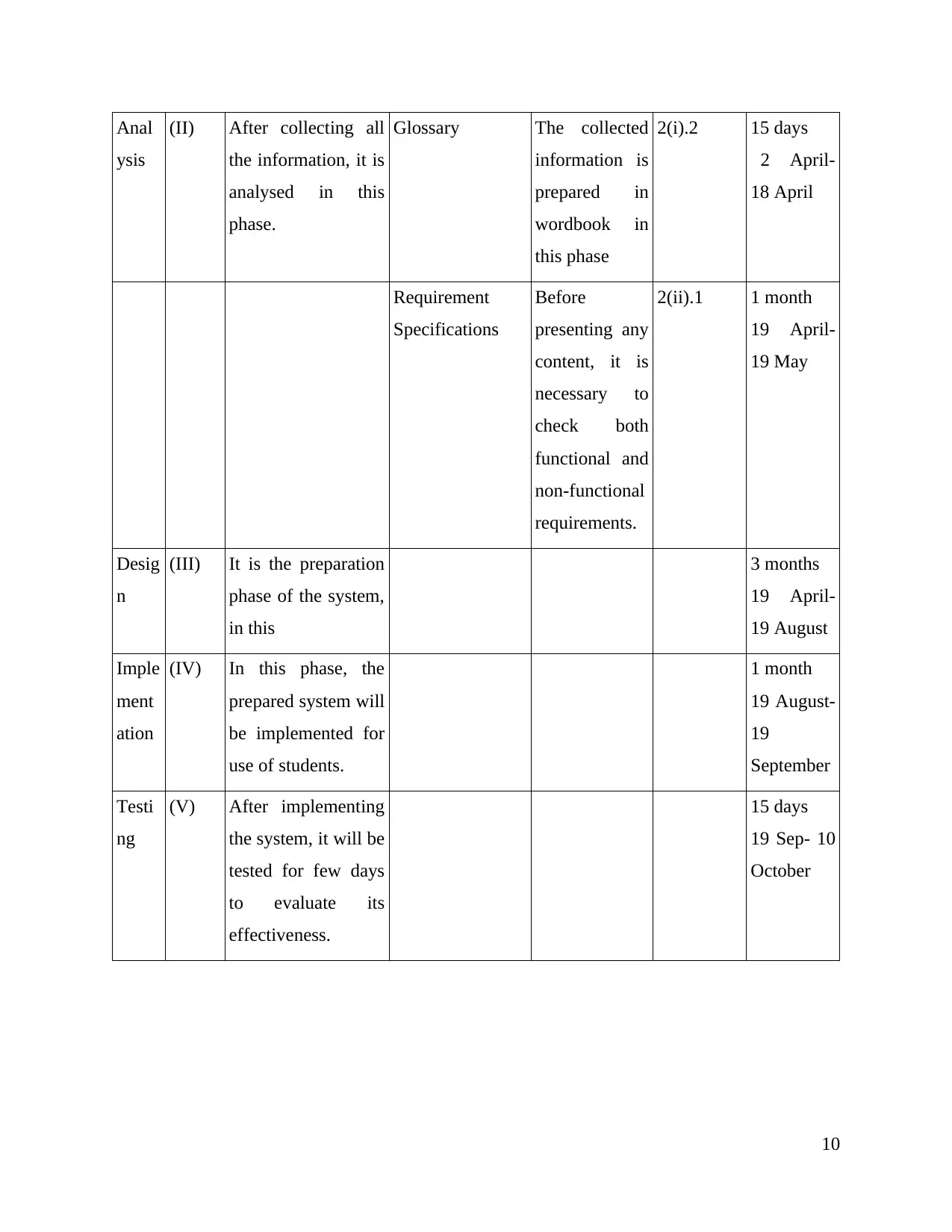
Anal
ysis
(II) After collecting all
the information, it is
analysed in this
phase.
Glossary The collected
information is
prepared in
wordbook in
this phase
2(i).2 15 days
2 April-
18 April
Requirement
Specifications
Before
presenting any
content, it is
necessary to
check both
functional and
non-functional
requirements.
2(ii).1 1 month
19 April-
19 May
Desig
n
(III) It is the preparation
phase of the system,
in this
3 months
19 April-
19 August
Imple
ment
ation
(IV) In this phase, the
prepared system will
be implemented for
use of students.
1 month
19 August-
19
September
Testi
ng
(V) After implementing
the system, it will be
tested for few days
to evaluate its
effectiveness.
15 days
19 Sep- 10
October
10
ysis
(II) After collecting all
the information, it is
analysed in this
phase.
Glossary The collected
information is
prepared in
wordbook in
this phase
2(i).2 15 days
2 April-
18 April
Requirement
Specifications
Before
presenting any
content, it is
necessary to
check both
functional and
non-functional
requirements.
2(ii).1 1 month
19 April-
19 May
Desig
n
(III) It is the preparation
phase of the system,
in this
3 months
19 April-
19 August
Imple
ment
ation
(IV) In this phase, the
prepared system will
be implemented for
use of students.
1 month
19 August-
19
September
Testi
ng
(V) After implementing
the system, it will be
tested for few days
to evaluate its
effectiveness.
15 days
19 Sep- 10
October
10
You're viewing a preview
Unlock full access by subscribing today!

4. Use the class diagram to represent the student registration by drawing the data model diagram.
11
11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

As per the net present value, estimated in above table, the project is expected to be
profitable in nature. A positive net present value indicates that the investment option is feasible
for High Quality Institute
Year Net cash flow Cumulative cash flow
0 -20000 -20000
1 5000 -15000
2 5000 -10000
3 5000 -5000
4 15000 10000
5 5000 15000
Payback period (in years)
3.3
3
The above table indicates that investment option is going to plough back the initial outlay
in duration of approximately 3 year & 5 months.
Year Net cash flow
0 -20000
1 5000
2 5000
12
Illustration 2: Student registration class diagram
5.The net present value, the payback period, and the return on investment by using a discount
rate of 6 percent.
Yea
r Costs/expenses net cash flow
PV factor
@6% Present value
0 -20000 -20000 1 -20000
1 7000 -2000 5000 0.943396226 4716.981132
2 7000 -2000 5000 0.88999644 4449.9822
3 7000 -2000 5000 0.839619283 4198.096415
4
1700
0 -2000 15000 0.792093663 11881.40495
5 7000 -2000 5000 0.747258173 3736.290864
Net present value 8982.75556
profitable in nature. A positive net present value indicates that the investment option is feasible
for High Quality Institute
Year Net cash flow Cumulative cash flow
0 -20000 -20000
1 5000 -15000
2 5000 -10000
3 5000 -5000
4 15000 10000
5 5000 15000
Payback period (in years)
3.3
3
The above table indicates that investment option is going to plough back the initial outlay
in duration of approximately 3 year & 5 months.
Year Net cash flow
0 -20000
1 5000
2 5000
12
Illustration 2: Student registration class diagram
5.The net present value, the payback period, and the return on investment by using a discount
rate of 6 percent.
Yea
r Costs/expenses net cash flow
PV factor
@6% Present value
0 -20000 -20000 1 -20000
1 7000 -2000 5000 0.943396226 4716.981132
2 7000 -2000 5000 0.88999644 4449.9822
3 7000 -2000 5000 0.839619283 4198.096415
4
1700
0 -2000 15000 0.792093663 11881.40495
5 7000 -2000 5000 0.747258173 3736.290864
Net present value 8982.75556

3 5000
4 15000
5 5000
Internal rate of return (in %) 20%
IRR of 20% indicates that the project into consideration is capable enough to generate
sufficient return in long run.
The technique of NPV & IRR takes into consideration time value of money & cost of
capital. Henceforth, the decision as per them is considered to be viable in nature. As per the
values estimated, the project into consideration is feasible in nature. The business unit should
make investment since it not helps in improving learning skills of students; but also generate
positive cash flow.
6. Covered in poster.
CONCLUSION AND RECOMMENDATION
From the present report, it has been observed that installation of a teaching and learning
system requires Work Breakdown Structure for segregating the tasks and accomplishing them in
effective time period. Further, The net present value, the payback period, and the return on
investment is calculated for estimating the budget. Also, PERT/CPM chart is prepared to state
the time period of each task.
It is recommended that the institute should all these steps for designing an effective
teaching and learning system. This plan will help from planning to cost management.
13
4 15000
5 5000
Internal rate of return (in %) 20%
IRR of 20% indicates that the project into consideration is capable enough to generate
sufficient return in long run.
The technique of NPV & IRR takes into consideration time value of money & cost of
capital. Henceforth, the decision as per them is considered to be viable in nature. As per the
values estimated, the project into consideration is feasible in nature. The business unit should
make investment since it not helps in improving learning skills of students; but also generate
positive cash flow.
6. Covered in poster.
CONCLUSION AND RECOMMENDATION
From the present report, it has been observed that installation of a teaching and learning
system requires Work Breakdown Structure for segregating the tasks and accomplishing them in
effective time period. Further, The net present value, the payback period, and the return on
investment is calculated for estimating the budget. Also, PERT/CPM chart is prepared to state
the time period of each task.
It is recommended that the institute should all these steps for designing an effective
teaching and learning system. This plan will help from planning to cost management.
13
You're viewing a preview
Unlock full access by subscribing today!

REFERENCES
Sung, Y. T., Chang, K. E., & Liu, T. C. (2016). The effects of integrating mobile devices with
teaching and learning on students' learning performance: A meta-analysis and research
synthesis. Computers & Education, 94, 252-275.
Coronel, C., & Morris, S. (2016). Database systems: design, implementation, & management.
Cengage Learning.
Al-Samarraie, H., Selim, H., & Zaqout, F. (2016). The effect of content representation design
principles on users’ intuitive beliefs and use of e-learning systems. Interactive Learning
Environments, 24(8), 1758-1777.
Al-Samarraie, H., Selim, H., & Zaqout, F. (2016). The effect of content representation design
principles on users’ intuitive beliefs and use of e-learning systems. Interactive Learning
Environments, 24(8), 1758-1777.
Kulik, J. A., & Fletcher, J. D. (2016). Effectiveness of intelligent tutoring systems: a meta-
analytic review. Review of Educational Research, 86(1), 42-78.
Hunsu, N. J., Adesope, O., & Bayly, D. J. (2016). A meta-analysis of the effects of audience
response systems (clicker-based technologies) on cognition and affect. Computers &
Education, 94, 102-119.
Laudon, K. C., & Laudon, J. P. (2016). Management information system. Pearson Education
India.
14
Sung, Y. T., Chang, K. E., & Liu, T. C. (2016). The effects of integrating mobile devices with
teaching and learning on students' learning performance: A meta-analysis and research
synthesis. Computers & Education, 94, 252-275.
Coronel, C., & Morris, S. (2016). Database systems: design, implementation, & management.
Cengage Learning.
Al-Samarraie, H., Selim, H., & Zaqout, F. (2016). The effect of content representation design
principles on users’ intuitive beliefs and use of e-learning systems. Interactive Learning
Environments, 24(8), 1758-1777.
Al-Samarraie, H., Selim, H., & Zaqout, F. (2016). The effect of content representation design
principles on users’ intuitive beliefs and use of e-learning systems. Interactive Learning
Environments, 24(8), 1758-1777.
Kulik, J. A., & Fletcher, J. D. (2016). Effectiveness of intelligent tutoring systems: a meta-
analytic review. Review of Educational Research, 86(1), 42-78.
Hunsu, N. J., Adesope, O., & Bayly, D. J. (2016). A meta-analysis of the effects of audience
response systems (clicker-based technologies) on cognition and affect. Computers &
Education, 94, 102-119.
Laudon, K. C., & Laudon, J. P. (2016). Management information system. Pearson Education
India.
14
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

15
1 out of 17
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
